g11 practice questions True/False ____ 1. Some e
advertisement

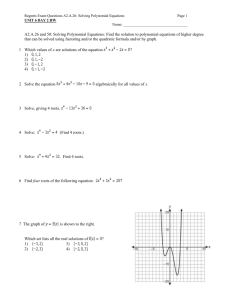
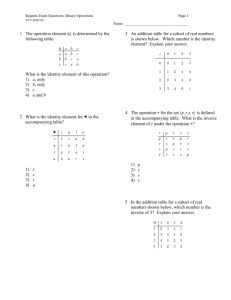
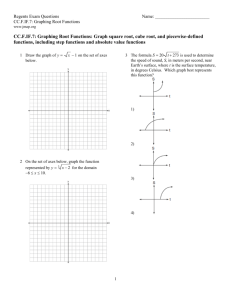
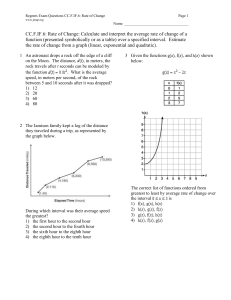
g11 practice questions True/False ____ 1. Some e-mail providers limit the size of attachments to e-mail messages. ____ 2. Chat rooms permit a group of individuals in many different places to have a secure meeting online. ____ 3. In a browser, you can click the Go button to connect to the address displayed in the Address bar. ____ 4. Broadband connections allow multiple channels of information to be transmitted over a single link. ____ 5. A LAN is a network that covers a large geographical area. ____ 6. A hub is a card that enables a laptop computer to send and receive data over a network. ____ 7. The Reading pane displays the full text of an e-mail message. ____ 8. You can organize appointments, tasks, and address lists, as well as e-mail, using Outlook. ____ 9. Deleted e-mail messages are automatically moved to the Deleted Items folder in Outlook and will stay in that folder until deleted permanently. ____ 10. The Internet is never the same place twice, and it is always changing and reshaping itself. Multiple Choice ____ 11. Which is the least expensive type of cable? a. twisted-pair b. coaxial c. shielded d. unshielded ____ 12. The geometric arrangement in which a network is set up is known as its ____. a. client c. topology b. peer-to-peer d. bottleneck ____ 13. Because they are placed in orbit 22,300 feet above Earth and rotate at the same speed as the Earth, ____ can maintain a constant position above the surface for communication transmission. a. satellites c. fiber-optic networks b. wireless networks d. modems ____ 14. You use the Inbox folder to ____. a. set up appointments b. store information about your work c. manage e-mail messages d. create a to-do list ____ 15. As you insert new information about a contact, Outlook creates a(n) ____. a. address card c. contact slip b. contact card d. address record ____ 16. Which of the following is NOT a guideline for writing professional and effective e-mail messages? a. Avoid jokes and keyboard symbols that could be misinterpreted. b. Use all capital letters to emphasize parts of your message. c. Be polite and keep the message short and to the point. d. Limit each message to a single subject. ____ 17. The ____ pane displays message headers for any new messages you receive in Outlook. a. Reading c. Navigation b. Message d. Notes Done by Mrs. Bashaer Al Kilani ____ 18. Saving an e-mail attachment to disk is called ____. a. uploading c. archiving b. downloading d. unattaching ____ 19. ____ allows you to send and receive messages in “real time” while you and your correspondent are both on the Internet. a. Instant messaging c. Hot Mail b. E-talking d. Packeting ____ 20. On the Internet, ____ allow(s) all brands, models, and makes of computers to communicate with each other. a. protocol enhancement c. interoperability b. transmitters d. coaxial connections ____ 21. Which statement about URLs is true? a. The second part of it indicates what domain name to use. b. The first part of it indicates what domain name to use. c. The second part of it indicates what protocol to use. d. The first part of it indicates what protocol to use. ____ 22. A(n) ____ is a discussion forum in which each “board” is dedicated to discussion on a particular topic. a. subscriber c. e-mail message b. newsgroup d. posting ____ 23. The transmission of data from one location to another is known as data ____. a. communications c. networking b. authentications d. modeming ____ 24. ____ determines the amount of data that can be sent at one time. a. Modem c. Demodulation b. Modulation d. Bandwidth ____ 25. In a peer-to-peer network, no computer is designated as the ____. a. application c. peer b. server d. client ____ 26. If you want to schedule a meeting, you would use the ____ folder in Outlook. a. Inbox c. Contacts b. Calendar d. Tasks ____ 27. Computers on the Internet communicate using the ____ protocol. a. TRANSMIT c. MODEM b. INTEROP/ROM d. TCP/IP ____ 28. ____ protocol is understood by Web servers and browsers and defines how messages are formatted, sent, and received on the Web. a. Hypertext markup c. TCP b. Hypertext transfer d. Navigator ____ 29. ____ is the Internet standard that allows users to download and upload files with other computers on the Internet. a. TCP c. FTP b. HTTP d. TCP/IP Completion 30. Software and hardware devices that protect a network from unauthorized entry are called ____________________. Done by Mrs. Bashaer Al Kilani 31. The ____________________ folder is used to hold completed e-mail messages that have not yet been sent. 32. When you save an important e-mail message for future reference, you ____________________ it. 33. A(n) ____________________ is a standard format for transferring data between two devices. 34. The ____________________ is the first page that displays when you launch your browser. 35. The row of icons at the top of your browser is known as the ____________________. 36. The Web is the ____________________ portion of the Internet. 37. ____________________ is software to gather information about your Web browsing habits that is installed on your computer without your knowledge. 38. A(n) ____________________ is a computer that manages network resources. 39. An endpoint of a network connection, such as a computer terminal or printer, is called a(n) ____________________. 40. A(n) ____________________ directs network traffic, connecting multiple networks and determining the fastest available path to send packets to their destination. 41. Network ____________________ describes how a network of computers communicates, either directly or through a server. 42. A network requires _________________________ software, which runs on the server and provides administration, security, and management services to client computers. 43. To send an e-mail message more securely, the information in it can be ____________________ before it is sent, which scrambles the data so it cannot be understood without a key. 44. You can use the ____________________ button on the Outlook toolbar to search for a message from a particular person or received on a specific date. 45. A(n) ____________________ is an electronic list of contact information you can use with your e-mail program. 46. ___________________ communication allows you to send and receive e-mail using a cell phone with email capabilities. 47. The Address bar of the browser contains the ____________________ of the current page. 48. ____________________ are small text files that include information about your site preferences, which are created by some Web pages when you visit the site. 49. Some Internet files are temporarily stored in a location on your hard disk called a(n) ____________________ to speed up the display of pages you frequently visit. 50. The ____________________ pane at the left of the Internet Explorer window keeps track of Web sites you have visited for the past few weeks. Done by Mrs. Bashaer Al Kilani g11 practice questions Answer Section TRUE/FALSE 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: T F T T F F T T T T PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: 1 1 1 1 1 1 1 1 1 1 REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: 509 542 534 531 488 494-495 507 504 511 529 PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: PTS: 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: REF: 490 495 492 507 518 515 507 508 520 529 538 541 488 494 496 505 529 538 542 MULTIPLE CHOICE 11. 12. 13. 14. 15. 16. 17. 18. 19. 20. 21. 22. 23. 24. 25. 26. 27. 28. 29. ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: ANS: A C A C A B C B A C D B A D B B D B C COMPLETION 30. ANS: firewalls PTS: 1 31. ANS: Outbox REF: 488 Done by Mrs. Bashaer Al Kilani PTS: 1 32. ANS: archive REF: 506 PTS: 1 33. ANS: protocol REF: 510 PTS: 1 34. ANS: home page REF: 529 PTS: 1 35. ANS: toolbar REF: 534 PTS: 1 36. ANS: graphical graphic REF: 533 PTS: 1 37. ANS: Spyware REF: 531 PTS: 1 38. ANS: server REF: 545 PTS: 1 39. ANS: node REF: 489 PTS: 1 40. ANS: router REF: 488 PTS: 1 41. ANS: architecture REF: 495 PTS: 1 REF: 495 42. ANS: network operating system NOS PTS: 1 43. ANS: encrypted REF: 498 PTS: 1 44. ANS: Find REF: 510 PTS: 1 REF: 514 45. ANS: address book PTS: 1 46. ANS: Wireless REF: 517 Done by Mrs. Bashaer Al Kilani PTS: 1 47. ANS: address URL location REF: 504 PTS: 1 48. ANS: Cookies REF: 533 PTS: 1 49. ANS: cache REF: 536 PTS: 1 50. ANS: History REF: 536 PTS: 1 REF: 543 Done by Mrs. Bashaer Al Kilani