AS_Revision_Guide_wjec
advertisement

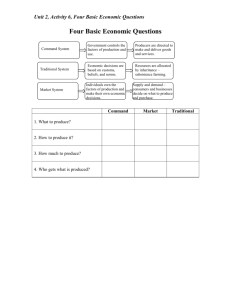
AS Level ICT Revision Guide CONTENTS CONTENTS ............................................................................................................................... 2 BASIC EXAMINATION TECHNIQUE ........................................................................................ 3 UNIT 1 ....................................................................................................................................... 4 Unit 1_1 Data Information and Knowledge ................................................................................................................ 4 Unit 1_2 The Value and Importance of Information ................................................................................................... 5 Unit 1_3 Quality of Information .................................................................................................................................. 6 Unit 1_4 Validation and Verification ........................................................................................................................... 7 Unit 1_5 Capabilities and Limitations of ICT .............................................................................................................. 8 Unit 1_6 1_6_1 1_6_2 1_6_3 1_6_4 Uses of ICT ................................................................................................................................... 9 Business .............................................................................................................................................. 9 Education........................................................................................................................................... 10 Healthcare ......................................................................................................................................... 10 The Home .......................................................................................................................................... 13 Unit 1_7 Presenting Information ................................................................................................................ 15 Unit 1_8 Networks ..................................................................................................................................... 17 Unit 1_9 Human Computer Interface ........................................................................................................ 20 Unit 1_10 Social Issues ............................................................................................................................... 22 Unit 1_11 Databases .................................................................................................................................. 24 2 Basic Examination Technique Anything in the specification can be used as a question. Get a copy of the specification and use it as a revision checklist. Specification can be obtained from www.aqa.org.uk Answer all the questions on the paper in the right order. Fill in the question numbers on the front page of the exam paper. Use correct English and not "text message language." readable. Don't use correction fluid. Make sure your handwriting is The best way to calm yourself down at the start of the exam is to read each question twice. Every word in the question is there for a reason. If the question asks you about a certain scenario, make sure that your answer is relevant to this scenario. All answers require more than a single word or phrase. Use correct technical terms. Do not use trade names e.g. talk about a "Database Management System" not "Access". Talk about a "Spreadsheet Package" and not "Excel". Look at the mark allocation for each question. When asked for an example, use ICT examples. It might be a good idea to start every answer on a different piece of paper. Think about what the examiners are asking you to do: Name List Define Outline Describe Explain Suggest State Give the name of something Give several names What is meant by A brief summary of the main points Give a description (requires several sentences) You have to show your understanding of something There are several possible correct answers and you have to make a suggestion and explain why your answer is a good one List but give reasons 3 Unit 1 Unit 1_1 Data Information and Knowledge Data are strings of raw facts and figures that have no meaning e.g. manu3nor5qpr2arn3 Information is processed data that has been given meaning e.g. Manchester United Queens Park Rangers 3 2 v v 2 Norwich City 3 Arsenal Knowledge is information that has had rules applied to it and is used to aid decision making e.g. Manchester United’s and Arsenal’s wins mean that they will now face each other in the FA cup semi-final Data, Information and Knowledge have specific meaning in this subject and it is a common mistake to use them interchangeably! e.g. Explain, with examples, two ways that make information valuable to an organisation. [4] “Organisations need data to make sure that they make the correct decisions. An example of this is data that is on time.” This candidate has answered the question using the term Data and therefore gains now marks! Coding / Encoding Shortening data so that it is represented by a code e.g. LCD32LG54ER (an 32 inch LCD TV, made by LG) – it is NOT deliberately hiding or disguising data (that’s encryption) Why Encode Quicker data entry Less storage space Less likely to make data entry errors Easier to validate Disadvantages Loses meaning Loses precision Can lead to value judgements 4 Unit 1_2 The Value and Importance of Information Managers need Information because: • • • • • • • • Decision making Strategic planning Day to day managing (monitoring progress) Directing Controlling Forecasting Competitive advantage Targeting resources What makes Information Expensive? • • • • • • • Employing someone to create data collection forms Setting up questionnaires On-line forms Travelling costs Collation costs Costs to collect from other systems Buying in the data (information) Data Entry • • • Human resources Time costs Hardware costs Processing • • • • • • Keeping systems up-to-date Backups Maintenance Technical staff Hardware Software 5 Unit 1_3 Quality of Information What makes Information Valuable? • • • • • • Up-to-date Relevant Accurate Complete Timely Correct format How to find Information Internal sources Observation Result of an action Questionnaire Work Study Interview External Online Sources CD-ROMs Non-ICT Sources Bought-in Media Government Statistics Demographics 6 Unit 1_4 Validation and Verification VERIFICATION means checking to see if something is correct e.g. that the customers title is “Mr” VALIDATION means checking to see if it is reasonable e.g. that Sam did really get 106 out of 100 in a Maths test. When you fill in a form on a web site they want your real e-mail address. There is usually a validation check on the e-mail address, which means that anyone@anything.com will usually be accepted. However, some clever companies then send an e-mail to the address given to VERIFY its accuracy. The double entry method is a common form of verification e.g. typing in a password twice. The last form is to proof read data. You need to be able to name and describe different validation checks (i.e. you must know what each one does): Presence check Range check Format check Uniqueness check Look-up list Length check Type check Check digit check What are the problems with inaccurate data? Can lead to incorrect decisions being made Loss of trust Unprofessional image Loss of goodwill Prosecution How do errors occur? Processing errors Transmission errors Transcription errors Transposition errors 7 Unit 1_5 Capabilities and Limitations of ICT Benefits Increased speed of processing Vast storage capacity Ability to search data in different ways Instant response Accurate and consistent results Communication Improved company image Work 24/7 Ability to search and combine Improved security (Backups) Disadvantages Job losses Faults in software GIGO Information overload Computer crime Lack of hard and software standards The Nature of Software Changes in circumstances during development Organisations constantly changing Speed of Implementation Compatibility Insufficient testing Poor communication with user Abilities of user Poor-post implementation procedures Maintenance Procedures Cost Hardware Support Why do IT projects fail? Latest technology Focused on cost alone Human resources ignored Users aren’t involved in design phase Users given unrealistic outcomes Managers not IT literate Focus on technology not people Lack of consultation Underestimation of cost Underestimate of time Over ambitious 8 Unit 1_6 Uses of ICT 1_6_1 Business Telephone and Internet banking Allows 24/7 access Transfer funds, pay bills, access statements ATMs Allow people to access cash 24/7 with a PIN (Personal Identification Number). Now you can access funds even abroad! Debit cards (switch) Using the Chip and PIN you can pay for things without having to have access to cash. Cheques Using MICR Direct Debit Allow people to be paid automatically, or even pay theory bills without thinking about it! Downsides Identity theft No need for identity to have goods Fraud Theft of PIN and Magnetic strip (via ATMS and at retail outlets, Petrol Stations) (TK Max) E-Commerce – Benefits to Organisation No need for high street presence saving costs From personnel and shop. Much wider audience Just in time delivery Storage of customers’ details is a valuable marketing tool. No need for high street presence saving costs From personnel and shop. Much wider audience Just in time delivery Storage of customers’ details is a valuable marketing tool. E-Commerce – Benefits to Consumer Allows 24/7 access Shop from anywhere I world from home No need to leave home Can have good delivered (to a friend) Specialist items easier to source Goods are often cheaper Comparison is easy Downsides Fraud You can’t feel or see the goods May have to wait for delivery Substitutes can be made 9 Manufacture Project management software Expert systems CAD/CAM (more in a minute) Robots Order entry and processing systems Computer Aided Design Can produce 3-D models Cheap to make adjustments Used for calculations Can be used for walk-through Models can be viewed fro any angle Drawings can be enlarged indefinitely (vector graphics) Computer Aided Manufacture 1_6_2 1_6_3 Much quicker than humans Much more accurate that humans Can work 24/7 Reproduces the same thing every time Can be used in hostile environments Don’t need to be paid Education Increased use of DB/SS/WP/DTP Interactive teaching aids The internet Distance learning Interactive boards Special facilities for students with disabilities. MIS Electronic registration Cashless catering Mini Laptops E-Learning CAL (Computer Assisted Learning) CBT (Computer based Training) Authoring Software Healthcare Medical records stored on databases Donor databases Computer controlled devices (pacemakers, organs) Monitoring devices Expert systems Remote operations Key hole surgery 10 Computer modelling for drugs Booking online Electronic Patient record keeping (EPR) Many staff may need access to a patients records at the same time Huge number of paper based records are now stored electronically Clarity – handwritten notes can be difficult to read Loss of records is reduced Misplaced records is reduced Mobile access to records (PDAs etc) Data consistency Backups No need to transport paper based files Blood tracking Used when a patient donates blood Taken from donor, grouped into blood type Stored at the National Blood Transfusion Service – given a coded label Matched blood sent to hospital ID badge scanned and used when needed Patients wristband is scanned and matched with bloods ID Sensors There are two major types of sensors, analogue and digital. Analogue are able to measure gradiations between two figures and digital are only able to measure specific values (DON’T say whole numbers!) Data measures by sensors Temperature Blood pressure Central venous pressure Pulse Blood gases Blood sugar Brain activity Electrical activity (electrocardiogram) Respiratory rate Advantages of sensors Measurements never missed Real-time monitoring Medical staff are freed up Reduction of costs Trends can be spotted More accurate readings Scanning devices Magnetic resonance image (MRI) Uses the natural electromagnetic nature of bodies to produce scans of the insides opf patients, without doing harm, unlike x-rays. Used for heart and blood vessels, examining joints, checking organ function 11 Computerised axial tomography (CAT) Uses x-rays at differing angles in order to produce a much more detailed image than an ordinary x-ray. Advantages of scanners High cure rate You don’t have to cut someone up Helps the planning of operations Faster diagnosis Scans can be done routinely MRI scans are safe (scary, but safe) Disadvantages It’s expensive They can break down CAT scans use x-rays and are therefore dangerous The patient needs to be very still for MRI scans Backups MUST be taken for critical systems such as the data taken from sensors – backups can be onsite (RAID drives, backup servers) or offsite complete mirror systems. UPS – an uninterrupted power supply. These can be used to make sure that computer equipment continues even if there are power fluctuations or even power failure. Expert Systems An expert system is an ICT system that uses artificial intelligence to make decisions based on data supplied in the form of questions. Meaning that the system models the processes of consulting an expert in the field. Expert systems contain the following elements Knowledge base – a set of knowledge about a particular subject Inference engine – a set of rules on which to base decisions (usually an if-then structure) User Interface – users ask questions and are provided with answers by the system You can create an expert system from scratch or you can use a piece of software that will help you to build one. This is called an EXPERT SYSTEM SHELL. The expert system shell consists on the Inference engine and the user interface, but NOT the knowledge base. The knowledge base needs to be supplied by the user. Some examples of software languages are PROLOG and ASPRIN. Some medical expert systems are MYCIN and NEOMYCIN. Advantages Consistency – you always get the same answer to the same question Cheaper – than employing experts Large pool of knowledge Uses ALL the information that it has Disadvantages No common sense 12 Can make really daft errors – remember GIGO for example Not able to be intuitive Unable to tell you when it doesn’t know The rules and knowledge MUST be correct Artificial Intelligence Intelligence is very difficult to define, but a definition of artificial intelligence isA reasoning process performed by computers which allows computers to draw deductions, produce new information and modify or write new rules. Neural networks are biological computer systems you brain! Advantages Good at circumstances when rules are difficult to apply or not understood When there are plenty of examples to learn from Structure can be identified from existing data Disadvantages They are only suited to certain tasks Examples used to teach the system need to be chosen carefully, otherwise anomonlies can arise Neural networks can learn from their own ”experience” Parallel processing is what we do – we are able to process many parts of data at the same time. Most computers are unable to achieve this. They process data so fast, one bit at a time, that for most circumstances it makes no odds. However, when a vast amount of data is being processed, i.e. in a super computer predicting weather or a computer buying and selling shares, then they can use parallel processing and process bits of data simultaneously. Ordinary ICT systems are good at: Fast processing Obeying a set of rules They are not good at Adapting to circumstances Dealing with data in parallel – the like to deal with each circumstance one after the other Dealing with data that may be incorrect 1_6_4 The Home Games Photography Music MIDI Interactive TV Home Shopping On-line Booking Email Dating Gambling 13 Mobile Phones 14 Unit 1_7 Presenting Information You should make sure that you are familiar with the common features of each type of software. Format Text Tabular Graphics Audio Animations Video How to choose the format Needs of user Target audience Complexity of the information How to present the information (face to face, online, downloadable) Word Processing Templates Mail Merge Indexing Macros Thesaurus Spellchecker Grammar checker Desktop Publishing The difference – a good rule of thumb is that a document that includes images is DTP. DTP is used for high quality, one off documents. Advantages More control over appearance Easier to integrate files from other packages, such as images, charts etc Text and graphic frames mean easier positioning Files that are compatible with publishing can be produced CSS (Cascading Style Sheet) – style and formats are contained in a separate file and therefore if a change is made it becomes a global change in the document (or webpage) Presentation Software More professional Summaries Information Printed versions available Multimedia Stored and can be edited 15 Presented using different hardware (TV, computer, projector) Databases (see below Unit 1_11) Web Authoring Software The name for software that allows users to create websites. Key features Text and images Formatting Tables, to organise the look of webpages Hyperlinks Anchors (a kind of internal hyperlink that goes to a point in the page) Mailto links Preview the website Multimedia and animation such as Flash Keywords Hyperlinks Formatting Templates Frames HTML CSS Forms (to collect data) Cascading Style Sheets This allows the look of a website to be controlled at one single point. Each part of the website (the size, format, font, colour etc) is stored in one file and then when a change is made to this file it runs throughout the whole website. 16 Unit 1_8 Networks You should be able to explain the difference between a LAN and a WAN and to give an example of each. The advantages of LAN networks are: File and printer sharing Communication over a network Ease of administration The disadvantages are: In a server-based network, users are reliant on a server Security problems Cost of hardware (e.g. cabling, servers, network interface cards) You should understand the difference between parallel and serial transmission (serial transfers one bit at a time). You need to understand the difference between a "server based network" and a "Peer-to-peer" network. You need to understand the advantages and disadvantages of each. You need to understand the different types of "Network Topology". You should understand the differences between a RING, BUS and STAR network. You should be able to draw a diagram of each. Key Equipment Network interface card Hub (or switch which can examine packets of data) allows several computers to communicate with each other Routers acts as a gateway (commonly known as broadband MODEM, but thers is NO SUCH THING!) Network Software Cables (fibre optic – expensive, fast, long distance, Copper – cheaper, slower only about 100m, comes in two flavours, unshielded and shielded (coaxial)) Wireless access points Networks vs Standalone Standalone is cheaper Less expertise needed for standalone Less potential for viruses when standalone Not as hardware dependant when standalone Advantages of Networks File sharing Hardware sharing Software sharing Lower software costs 17 Improved security Easier to implement usage policies Easier backups Improved communication Central maintenance and support Disadvantages Technical knowledge needed When the server fails everything fails Initial setup costs LAN – a network on one site WAN – a network across two or more sites The Internet A network of networks. Benefits Cheap communication Multimedia streaming Transfer files Research Sharing resources Shopping Video conferencing Disadvantages Inappropriate material Exploitation – particularly of children Cyber bullying Spam Loss of privacy Incorrect or inaccurate information Communications Instant messaging Webcam VOIP (voice over Internet protocol) Chat rooms SMS E-mail E-Mail Advantages Virtually instantaneous Quick direct communication e.g. LOL Attachments Cheaper than snail mail Available from different devices Environmental issues Disadvantages 18 Not everyone has email Not as formal as snail mail Junk mail and spam Security File Transfer Protocol (FTP) This sets the protocol, the rules, for transferring files across the Internet. Extranet and Intranet Extranets are opened to a select group of users outside the organisation such as customers or suppliers. Intranets are a private network of information available only to specific groups, such as employees. 19 Unit 1_9 Human Computer Interface HCI stands for both "Human-Computer Interface" and "Human-Computer Interaction". The two should not be confused. Human-Computer Interaction refers to more than just the interface. When thinking about interfaces, consider things like ATM machines, cashpoints and planes as well as computers. Interface styles are: GUI (Graphical User Interface) Command Line Interface Natural Language Interface Menu driven Form driven GUIs are increasingly popular because they have a range of features to facilitate speed of learning and ease of use including: Windows (to facilitate multi-tasking) Menus (pop-up and pull-down) Icons and buttons Pointers (although keyboard shortcuts are still needed for more experienced users) When designing a data entry form, interface design considerations could be: Forms should have a title Forms should not be too cluttered Obvious buttons for navigating records, Exit, Cancel, Help Length of data entry boxes Drop-down combo boxes Radio buttons/checkboxes Online Help/Context Sensitive Help Things to consider when designing an interface Input methods Use of colour Consistency Use of pictures/icons Use of text Sound Consistency Input Devices MICR OCR OMR Keyboard Joystick Games devices 20 Biometric devices Microphones Touch sensitive screens Output Devices Printers VDUs Speakers If applications have a "common user interface", it can increase speed of learning and, therefore, reduces training costs. The ability to import/export data between integrated applications is not an advantage of the interface! Don't confuse the operating system with the user interface! Don't confuse voice dictation systems with natural language interfaces (Interacting with a computer system using a natural spoken or written language)! 21 Unit 1_10 Social Issues Computer Misuse Act The three levels of offence are: Level One: Unauthorised access (e.g. someone who breaks into a system to be nosey or just for the hell of it). Level Two: Unauthorised access with a further intent (e.g. someone who breaks into a network to steal money). Level Three: Unauthorised access to modify data (e.g. someone who breaks into a network to plant a virus, which corrupts data). The computer misuse act is not used as much as it should be because many businesses (e.g. financial institutions) do not want to acknowledge that their systems are vulnerable. If it became public knowledge that their systems had been hacked, the bad publicity could affect their share price. Copyright, Designs and Patents Act When you buy a piece of software, you do not own the software itself. What you own is a licence to use this software on one computer at a time (a single user licence). If an organisation wants to install the software on a network, it could buy a network licence or a site licence. It is illegal to duplicate, download or transmit copyrighted software. Software companies can guard against software piracy by the use of registration numbers, dongles, or by trying to make disks or CDs "impossible" to duplicate. Organisations should have policies to ensure that they are always fully licensed. Health and Safety There are several laws governing health and safety at work. Organisations can be sued by their employees if they are guilty of not following guidelines. Consider the example of the HSBC bank. Remember to refer to IT health and safety problems only! Health and Safety problems can include: Eye-strain (breaks, brightness controls, lighting) RSI (breaks, ergonomic keyboards, adjustable chairs, software design) Stress (software design, training) Neck-Strain (tilting monitors, adjustable seating) Data Protection Act 22 Why was the data protection Act introduced? (Because of privacy concerns about large amounts of personal data being held. Because computers can store vast quantities of data and process it very quickly. Consider the case of James Wiggins) What sort of data does it cover? (personal data on living and identifiable individuals that will be automatically processed) What is the data register? Anyone wishing to hold personal data must say what data will be held, who the data will be passed on to, how long the data will be held for, the purpose for which the data is held, the sources from which it will be obtained). What is the role of the Information Commissioner? (to maintain the register, to spread information about the DPA, to encourage organisations to introduce codes of practice, to consider complaints and to prosecute offenders). What are the 8 principles of data protection? Data must be . . . 1. Obtained and processed fairly and lawfully 2. Held for a lawful purpose as described in the register 3. Adequate, relevant and not excessive in relation to registered purpose 4. Accurate and up-to-date 5. Held no longer than necessary for the registered purpose 6. Used only for the registered purpose 7. Accessible to the individual concerned 8. Surrounded by proper security What are the rights of data subjects? (the right to see information, the right to have errors corrected, the right to complain, the right to compensation) What are the Exemptions from the Act? (payrolls, pensions, national security, recreational, electoral roll, tax, credit reference agencies). Acceptable Use Policies Every organisation should have an acceptable use policy and make sure that staff do know what is and is not acceptable. This should cover: Acceptable use of hardware Acceptable use of software Appropriate use of the Internet Security Training Malpractice – is when a user does something that contravenes the acceptable use policy of an organisation. Crime – is when someone breaks the law. 23 Unit 1_11 Databases What is a database? A database is a large collection of data items and the links between them. The software that is used to access the data is called the Database Management System (DBMS). Keywords, queries, forms, fields, key field, record, relationships, sorting, reports. Advantages of Databases: Vast storage capacity The ability to search, sort and combine data The ability to share information The ability to set passwords/access levels Terminology Associated with databases Data Inconsistency – the same data appears differently throughout the system Data Redundancy – the same data appears over and over again Data Dependence – Any change in the data format or structure means that it must be changed throughout the system. Data Lacks Integrity – It’s just plain wrong! Flat File v Relational Databases Advantages Data Redundancy (the same data entered over and over again takes up unnecessary space and can slow down the performance of the database) Data Inconsistency (if the same thing is entered repeatedly, mistakes will inevitably be made Time spent entering data (faster if the same data does not have to be entered repeatedly) Ease of updating (e.g. what happens if someone changes her name?) Much easier to search for information in a relational database Much easier to combine data in a relational database Data Integrity – Data is only kept in one place, so when it’s updated it updates throughout the database Can build an application around a relational database. Relational databases are very adaptable Disadvantages Hard to set up a relational database More expensive Inappropriate for simple lists Things to remember when talking about databases: Data types (numerical, alphanumeric, alpha, Boolean) Query 24 Sort Validation Verification Data Capture Input – Process – Output Data – Information – Knowledge Key Field Links http://www.theteacher99.btinternet.co.uk/theteacher/ict/ictwjec1.htm Database Security Every organisation needs to adhere to the DPA and take reasonable precautions to protect their data. Some of the ways in which this can be achieved are: Physical protection Lock the computer in a room Provide security guards Have o a limited number of stations able to access the data Software protection Access rights (read only, read/write, full control, execute) Password protection Encryption Distributed Database A distributed database is one in which the data is spread of several servers in one or more networks. They are good for data protection, because they are on different servers not all of the data should be damages if there is an emergency such as a fire and the data is more difficult to access by hackers. Because there are several servers the speed of processing is improved. 25