cicayda's IS security layered data protection
advertisement

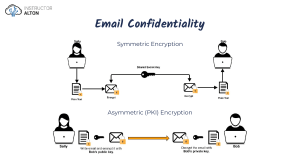
IS Layered Data Protection cicayda Data security threats and incidents can be harmful to any organization and data breaches can negatively impact organizations in a variety of ways including increased costs, loss of brand reputation and revenue, and loss of ‘secrets.’ In order to protect private and confidential information, we use encryption to improve our defense-in-depth controls around these data assets and comply with regulations such as Safe harbor, PCI DSS, HITECH Act, and more. For an integrated encryption strategy, we use access controls to ensure data is only decrypted for authorized requests. This includes the ability to protect both structured and unstructured data stores that include database and file server files, documents etc. In designing a data security plan at cicayda, we have a two-pronged strategy: secured data overlaid with layers of peripheral security in the four "touch points" (data access, data in transit, data at rest, and data in use). For each "touch point", there are a variety of technologies to ensure security such as authentication and access control schemes to control access to data, multi-layered security zones and storage security policies which address issues specific to storage data. cicayda’s storage security policy state the format in which different types of data (as shown in figure 1), has to be kept in storage. For example, sensitive data must be encrypted (in transit & at rest). FIGURE 1: Data in Use: Data in Motion: Active data which is under use. Data that is traversing between networks or temporarily residing in the memory of a computer Data at Rest: Inactive data stored physically in databases, data warehouses, spreadsheets, archives, tapes, off-site backups, etc. cicayda.com To work best, information security must be holistic and fit into an organization seamlessly. Information security practice should take into account personnel security, user access control, network security and regulatory aspects. At cicayda, our holistic security framework integrates technology, people and processes. Data protection controls based on the value of data and its importance are introduced in the policy and the design of databases. This takes into consideration the Principle of Least Privilege, Data classification, The Separation of Duties principle, Integrity, Availability, Identification and Defense in depth, and this became part of enterprise security architecture depicted in figure 2. FIGURE 2: cicayda’s Security Architecture Framework defines: Network Security (Authentication, Authorization, IP segmentations, Antivirus, VPN, Firewalls, IPS / IDS, Platform hardening, and Internet Security) LAN / WAN Security, Application Security, Data Security, Enterprise Security Management, Risk Analysis and Risk Acceptance, Incident Handling and Response, Disaster Recovery, Plan PKI - Public Key Infrastructure, Integrated Security Controls and Compliance. Information Security Policies, Standards and Procedures Used for the Implementation of the Framework and Allow Integration of People, Process, and Technology. Encryption Encryption is a critical security feature for thriving networks. This security mechanism uses mathematical schemes and algorithms to scramble data into unreadable text. It can only by decoded or decrypted by the party that possesses the associated key. At cicayda, your data is encrypted while in transit and at rest. While your data is at rest, we use Full-disk encryption (FDE) and thus offer some of the best protection available. This technology enables us to encrypt every piece of data on a disk or hard disk drive in conjunction with software components. This combination is referred to as end-point or end-based full disk encryption. Strong User Authentication Authentication is another part of data security that we encounter with everyday computer usage. That authentication process allows you to log into applications, files, folders, and you (the customer) are in control of your authentication process and whom to grant access to your data. Backup Solutions Data security wouldn't be complete without a solution to backup your critical information. At cicayda, we have an elaborate backup scheme which is replicated and monitored 24/7. cicayda.com