ADSL System Enhancement with Multiuser Detection
advertisement

ADSL System Enhancement with Multiuser Detection
A Thesis Presented to
The Faculty of the Division of Graduate Studies
By
Liang C. Chu
In Partial Fulfillment of the Requirements for the Degree of
Doctor of Philosophy in Electrical and Computer Engineering
School of Electrical and Computer Engineering
Georgia Institute of Technology
Atlanta Georgia 30332
July 2001
ACKNOWLEDGEMENTS
There are a number of people that should be recognized for their help and assistance
during my thesis work. First of all I want to express my sincere gratitude to my thesis
advisor professor Martin A. Brooke, who has given me the opportunity to complete my
Ph.D. study at school of Electrical and Computer Engineering in Georgia Institute of
Technology. I really appreciate the time for his advising and it is very rewarding and
inspiring to discuss questions with professor Brooke. I also want to thank professor Nikil
Jayant and professor John Copeland, who have taken an active part in advising and
guiding me in my research and education.
Furthermore, I gratefully acknowledge professor Donald L. Schilling, who always
encourages my study during these years, since I was studying in my Master’s degree with
him at the City College of New York, CUNY. Also, I would like to thank professor
Russell M. Mersereau and professor Zhong L. Wang for their supporting to serve in my
thesis committee, and all my colleagues at school of Electrical and Computer
Engineering, Georgia Tech.
Finally, and most importantly, I sincerely thank my wife, Dr. Jing Li, who help and
support me in my graduate study at Georgia Tech during these years, and deeply love and
care about me always. Also, I greatly thank my parents, Mr. Hsun C. Chu, Ms. Sai Y.
Feng, and my bother, Dr. Liang T. Chu, for their continuing care and encouragement all
the times in my life. I would like to show my great appreciation to my families for their
constant help, support and encouragement.
ii
ADSL System Enhancement with Multiuser Detection
Approved:
Dr. Martin A. Brooke, Chairman
Dr. John A. Copeland
Dr. Nikil Jayant
Date Approved
iii
Table of the Contents
Chapter One: Introduction
1
Chapter Two: Background
5
2. Problem on the DSL Spectral Compatibility with Crosstalk
5
2.1. Current Crosstalk Model and Distribution
6
2.1.1 NEXT and FEXT Modeling
8
2.1.2 Crosstalk Noise Distribution
10
2.2 Spectral Compatibility between Asymmetric and Symmetric DSL Systems
10
2.2.1 Symmetric DSL Systems
11
2.2.2 Studies on Crosstalk Noise between ADSL and SDSL
11
2.2.3 Current Deployment Plan and Proposed Enhancement
15
Chapter Three: DMT-ADSL Channel Modulation and Characteristics
16
3. Multiuser Multitone Modulation System and ADSL
16
3.1 Overview of Discrete Multitone
17
3.2. Analysis of Discrete Multitone
22
3.2.1 Channel Gap Analysis
22
3.2.2 Margin of the DMT
23
3.2.3 Performance Calculation
25
3.2.4 Bit-loading and DMT-ADSL System
26
Chapter Four: Channel Model and Multiuser Transmission
32
4.1 Twisted Wire Pairs Characteristics
32
4.1.1 Electrical Characteristics of Twisted-pair Wires
33
iv
4.1.2 Telephone Channel
35
4.2. Multiuser Transmission System
37
4.2.1 Basic on Multiuser Detection
37
4.2.2 Optimum Multiuser Detection
38
4.2.2.1 Linear Multiuser Detection in AWGA Channel
42
Chapter Five: ADSL System Enhancement
45
5.1. Multiuser Detection on DMT-ADSL System
45
5.1.1 Theoretic Bounds on DMT-ADSL Channel
49
5.1.2 Spectral Distribution on the Multiuser Channel Capacity
49
5.1.3 Examples on Capacity Bound Analysis
58
5.2. Joint Maximum-likelihood Sequence Estimation (JMLSE)
60
5.2.1 DSL Co-channel Signal Model
60
5.2.2 MLSE Receiver Design
62
5.2.3 T/2-spaced MLSE Receiver
69
5.2.4 Analyzing MLSE Receiver Structures
72
5.2.5 Reduced Complexity Receiver Structures
76
5.3.6 Joint MLSE for DMT-ADSL Receiver
78
5.3 Preliminary Performance Studies
81
Chapter Six: Low Complexity Enhancement on ADSL Receiver
85
6.1 Tone-zeroing Method
85
6.2. Low Complexity Joint MLSE
90
6.2.1 Multi-stage JVA
90
6.2.2 Multi-stage JVA with Feedback
95
v
6.2.3 Practical Enhanced ADSL Receiver
98
6.2.4 Example and Comparison
101
Chapter Seven: Performance Evaluations and Simulation Results on Enhanced ADSL
Receivers
104
7.1 Test Environment
105
7.2 Test Channel Conditions
105
7.3 Loop Characteristics
106
7.4 Capacity Improvement
107
7.5 Reach Improvement
107
7.6 Disturber Scenarios
107
7.7 Co-channel Transfer Functions
110
7.8 Simulation Results
110
Chapter Eight: Conclusions
115
Chapter Nine: Recommendations
117
Reference
119
vi
LIST OF FIGURES
Figure
Page
2.1.1 Near-end Crosstalk (NEXT)
7
2.1.2 Far-end Crosstalk (FEXT)
7
2.1.3 NEXT Power Sum Losses for 25 Pairs of PIC Cable Binder Group
9
2.2.2.1 PSD of 2B1Q SDSL at 1168, 1552 and 2320 kbps
13
2.2.2.2 Downstream ADSL Bit Rate with 1552 & 2320 kbps SDSL NEXT
14
3.1.1
Basic Multitone Modulation Transmission
18
3.1.2
Illustration of Frequency Bands for Multitone Transmission System
19
3.2.4.1 DMT Bit-Loading Concept
29
3.2.4.2 DMT-ADSL Frequency Spectrum
31
4.1.1.1 Transmission Line Segment
34
4.1.2.1 Basic Multiuser Transmission System
38
5.1.1
48
ADSL Channel Model with k-l Crosstalk Signals
5.1.2.1 TPC Attenuation Function with Difference Length
50
5.1.2.2 Channel Attenuation and NEXT Coupling Characteristic
50
5.1.2.3 Channel Capacity – Single vs. Multiuser Channels
56
5.2.1.1 Co-channel System Model
61
5.2.4.1 Basic Receiver Structure
77
5.2.4.2 Sophisticated Receiver Structure
77
5.2.4.3 Carrier Recovery in the Noise-free AWGN Channel
78
vii
5.2.5.1 Joint ML Sequence Detection between Adjacent Pair
80
5.3.1 BER for ADSL System with Single-user Detector and JMLSE
83
5.3.2
ADSL System with SDSL Crosstalk on Single-user Detector and JMLSE 84
6.1.1
Joint ML Crosstalk Signal Canceller with Tone Zeroing
87
6.1.2 Margin on DMT-ADSL with Tone-zeroing Crosstalk Noise Cancellation 88
6.2.1.1 Two-stage JVA (without Feedback Section)
92
6.2.1.2 Single-user MLSE Computational Flow Structure
94
6.2.2.1 Two-stage JVA (with Feedback Section)
95
6.2.4.1 Desired Channel Performance with Three Methods
103
7.3.1
Testing Loops
106
7.6.1
Scatter Plot of Downstream ADSL Throughput with Mixed SDSL Crosstalk 108
7.8.1 Rate-reach Curves for Test Loop #1
111
7.8.2 Rate-reach Curves for Test Loop #2
112
7.8.3 Rate-reach Curves for Test Loop #3
113
9.1
118
Channel Attenuation and NEXT Characteristic
viii
LIST OF TABLES
Table
Page
4.1.2.1
Worst-case Measurement for Telephone Channels
36
7.6.1
Disturber Scenarios
109
ix
Summary
In this thesis, a new approach on mitigating the cochannel interference (CCI), also
called crosstalk, in the Asymmetric Digital Subscriber Line (ADSL) transmission system
has been studied. This implementation ensures the spectral compatibility in the DMTADSL system together with other DSL services in a same binder cable.
The major part of this thesis concerns a modified technique for high-speed
communication over the ADSL telephone network. Discrete Multitone (DMT)-ADSL
has been standardized in American National Standards Institute (ANSI) [1]. It offers bit
rate up to 8 Mbps downstream and 1 Mbps upstream, depending on the deployment
coverage ranges. A modified method based on multiuser detection is presented herein,
which can mitigate the crosstalk interference in DMT-ADSL receiver.
An important issue for ADSL is the problem with crosstalk, which is a major threat in
ADSL receiver with other DSL services in a same binder. The performance on the
mitigation of ADSL channel crosstalk impairment is the most important criteria for
guaranteeing the Quality of Service (QoS) in an ADSL system. The essential issue of this
thesis on optimizing the ADSL system transmission throughput is to modify its channel
transceiver design. Treating an ADSL channel as a multiple-input and single-output
(MISO) system with desired ADSL signal and cochannel interference signals is just like a
multiuser communication channel model. Our modified ADSL multiuser detection can
greatly outperform the currently deployed single-user receiver with either increasing
transmission data rates, or extending deployment rages in impairment environments.
Joint Maximum Likelihood Sequence Estimation (JMLSE) gives very good performance
x
in our proposed model, but known as a computationally complex technique. The last part
of this thesis deals with low complexity multiuser detection to balance the ADSL system
performance and computational complexity with a reasonable VLSI capability, which can
be implemented in a sub-optimum solution.
With these approaches to the mitigation of ADSL impairments, the performance of
the ADSL system is greatly enhanced; for example, the ADSL service can be either
extended more than 2-kft from the current limit, or has more than 30% transmission data
rate improvement, depending on the cost requirement. Under these circumstances, the
capacity of the network is utilized to a near sub-optimum solution.
[1]Asymmetric Digital Subscriber Line (ADSL) Metallic Interface, ANSI Standard T.4131995, ANSI, New York.
xi
CHAPTER ONE
INTRODUCTION
This thesis deals with an enhancement approach on the DMT-ADSL twisted-pair
wires communication system. Our implementation ensures the spectral compatibility
between different DSL systems in a same binder cable. Therefore, the capacity of the
DMT-ADSL telephone network to support fast Internet access can be better utilized than
current solutions.
Today, an increasing number of people use the telephone access network for digital
data communication. Even if the speed of an analog modem has increased to 54 kbps, it
is still frustratingly slow for the next generation fast Internet multimedia services. Highspeed access to Internet service with various kinds of multimedia content has become an
emerging technology that is needed by all telecommunications end users. One of the best
solutions is Digital Subscriber Lines (DSL) access, which is targeted for residential users,
and has recently received much attention by many telephone companies.
The
architecture of DSL systems allows telephone companies to use existing twisted-pair
infrastructures for their next-generation broadband access networks. The sheer inertia of
the worldwide installed copper base means that it could take many years for access
networks to migrate from copper to fiber.
A combination of the existing copper
1
infrastructure and digital subscriber line transmission technologies means that a new era
of universal broadband access can now begin at a fraction of the cost and in a fraction of
the time required for optical access networks. Even with fiber optical network, the DSL
technologies will still exist in the last-mile access transmission. Over the past ten years,
DSL technologies have been developed and use larger parts of the available TCP
bandwidth. Normally, xDSL use 1 to 15 MHz bandwidth. To be able to use this large
bandwidth, the telephone lines interface in the center office (CO) and customer premise
end (CPE) need to be exchanged when employing xDSL techniques.
However, there is a serious threat to this vision of the future: a variety of impairments
in the access systems. The reason is when trying to reach higher bit rates, there is no
problem on the channel capacity of the twisted copper pair (TCP), but rather high
frequency digital signal interfaces between the lines inside a same telephone binder. As
we know that the telephone access networks were originally built for analog voice
communication, carrying voice-band signals up to 4 kHz in the frequency bandwidth and
not for digital data communication. It is relatively simple to design transmission systems
that work well in simulations and some specific laboratory tests, but more difficult to
deliver useful capacity when subjected to the hostile environment of the real network.
The uncontrolled deployment of such advanced transmission systems in multipair cables
can result in server degradation due to cochannel interference. This interference is a
linear coupling among multiple channels, also called crosstalk [1]. Even though this
problem has been studied in the past [2], [3],[4], [5], solutions for real-world DSL
services deployment are not currently available. Even low data rate implementation, such
as ISDN service, can significantly pollute the copper network. The current DSL systems
2
are modeled as single-user channel models and crosstalk is treated as white Gaussian
noise [6]. This approach is usually conservative, as the true crosstalk signal distributions
are bounded in amplitude. However, the Gaussian assumption reduces the attainable
channel capacity, but hold for the case of current practical interests [6]. It is well known
that the spectral compatibility has become a major issue for all DSL services, especially
in the transmission of symmetric and asymmetric services in the same binder group [7],
[8], [9], [10]. It is likely that as the DSL services reach significant penetration, their
crosstalk between different services will become an important factor to the success of
DSL services.
The objective of this thesis research is to understand the spectral compatibility issues
for various DSL variants [11], in order to determine a more accurate DMT-ADSL
channel model and implement with digital signal processing techniques that realize the
true broadband potential of the existing copper access network. Currently, a study [12]
has demonstrated that crosstalk effects on VDSL might be mitigated; essentially, treated
crosstalk is not exactly Gaussian. The drawback of this approach is computational
complexity in realization. It is well known to us on accurate models for the case of a
single type of crosstalk, where all crosstalk signals have the same power spectral density.
The model is called the 1% worst-case crosstalk power-sum. It is described that no more
than 1% of all pairs in all binders can receiver more crosstalk than this model [13].
However, crosstalk from multiple different types of DSL services is a relatively new area
of study. In this thesis, we focus on a study of the DMT-ADSL system enhancement
coupling with the SDSL services in a same binder cable. Our studies can apply to any
cases of DSL application, where coexists asymmetric and symmetric services.
A
3
proposed multiuser channel model has been derived, and the enhancement on the DMTADSL receiver is introduced to mitigate crosstalk from the SDSL services.
Some
important simplification algorithms, such as tone zeroing [14], and multi-stage joint
maximum-likelihood detection for multiuser DMT-ADSL are derived, which can largely
reduce the multiuser DMT-ADSL receiver complexity.
Our proposed sub-optimal
approach, multi-stage JMLSE with feedback section has a reasonable computational
complexity, and also improves Signal-to-Noise-Ratio (SNR) about 8 dB at a Bit-Error
Rate (BER) of 10-7 in the DMT-ADSL channel. This enhancement gives us a core
method on either increasing signal constellation sizes of each DMT sub-channel, or
extending the deployment ranges with a fixed transmission rate, or compensating on a
poor BER channel in achieving better throughput.
In the following sections of this thesis, the origin of the spectral compatibility
problem and its current solutions are covered; a new approach technique for mitigation
on crosstalk interference is presented; and simulation procedures and results are
addressed. Finally, discussions and conclusion of this thesis are presented.
4
CHAPTER TWO
BACKGROUND
2.
Problem of DSL Spectral Compatibility with Crosstalk
Digital subscriber line technology provides transport of high-bit rate digital
information over telephone lines. High-speed digital transmission via telephone lines
requires advanced signal processing to overcome transmission impairments resulting
from crosstalk noise from the signals present on the other wires in the same binder, radio
noise, and impulse noise.
Fortunately, amateur radio signals are narrowband and
transmission methods attempt to notch the relatively few and narrow bands occupied by
this noise, which avoids the noise rather than transmitting through it. Impulse noise is
nonstationary crosstalk from temporary electromagnetic events in the vicinity of phone
lines. The effects are temporary and typically at much lower frequencies. The channelcoding algorithm in ADSL overcomes this effect [15]. As increasing number of DSL
services are deployed, the concern is that assumptions made in the design of modem
equipment for one type of service will lead to errors in another type of modem
equipment, which also share the cable. This is the crosstalk noise. Crosstalk can be the
biggest noise impairment in a twisted pair and substantially reduces DSL performance
when it cannot be circumvented.
In this thesis, we focus on the ADSL receiver
5
enhancement design to mitigate the crosstalk from the other DSL services (mainly
targeting on SDSL service). In general, this approach can be applied to any other DSL
systems, such as VDSL, with their related channel characteristics.
2.1
Current Crosstalk Model and Distribution
The primary impairment to sending digital information through the twisted-pair loop
is crosstalk noise from similar digital services of adjacent loops. In the current situation,
DSL transmission is treated as a single-user channel with crosstalk noise as loose
Gaussian distribution [6].
The crosstalk noise can be categorized into two types.
Crosstalk to a receiver from a neighboring transmitter is called near-end crosstalk
(NEXT), as shown in Fig. 2.1.1, and crosstalk to a receiver from a transmitter at the
opposite end is called far-end crosstalk (FEXT), as shown in Fig. 2.1.2.
6
Same Binder Group
Transmit
NEXT
Receive
Fig. 2.1.1: Near-end Crosstalk (NEXT)
Same Binder Group
Transmit
FEXT
Receive
Fig. 2.1.2: Far-end Crosstalk (FEXT)
7
2.1.1
NEXT and FEXT Modeling
In the case of the NEXT model, it uses Unger’s NEXT model [16], which states, as
expected, 1% worst-case power sum crosstalk as a function of frequency [17]. NEXT is
dependent on frequency as well as on the relative location of the pairs in the binder
group. Thus, to find the crosstalk noise from a contributing circuit into another twisted
pair in a 50-pair binder, the power spectral density (psd) on any line in the binder is
modeled by
Sn = (
N 6
) ⋅ 10 −13 ⋅ f 1.5 ⋅ S xtalk _ cont ( f ),
49
(2.1.1.1)
where N is the number of crosstalk-contributing circuits in the binder, Sxtalk_cont is the psd
of crosstalk-contributing circuits.
FEXT is usually characterized in terms of 1% worst-power sum loss from all signals
on other pairs in the binder group [17]. FEXT is less severe than NEXT because the
FEXT noise is attenuated by traversing the full length of the cable.
Measurement study on a number of pairwise coupling transfer functions in a 50-pair
binder cable by C. Valenti [17] has been shown in Fig. 2.1.3. There are two interesting
issues as shown in Fig. 2.1.3. First, it shows that the NEXT increases as f1.5 with
frequency, but with significant variation in coupling with frequency.
8
NEXT POWER SUM LOSS(dB)
1000 FT, 24 AWG PIC
70
60
50
40
30
20
10
0
0.1
1
10
FREQUENCY(MHz)
100
1% Case
Fig. 2.1.3: NEXT Power Sum Losses for 25 Pairs of PIC Cable Binder Group
Note: Power Sum Loss is expressed as −10 log10 ( Power Sum Transfer Function )
9
Second, at any given frequency, only few other pairs may contribute significantly to
crosstalk, but over all frequencies, many wire lines contribute randomly. As a practical
convenience, many telecommunication engineers who work on DSL, average the
coupling over many pairs. They assume that the sum of many coupling functions is
constant. Therefore, as shown in Eq. (2.1.1.1), this constant has been determined by
ANSI as (
2.1.2
N 6
) ⋅ 10 −13 in a 50-pair binder.
49
Crosstalk Noise Distribution
It has been widely used that in the time-domain, crosstalk noise at the DSL receivers
is treated as a Gaussian distribution [6]. Obviously, this statement is not true for single
crosstalk interference, because of the highly-frequency-dependent nature of the crosstalk.
When summed over all frequencies from different contributors on different lines, the
central limit theorem of statistics loosely applies to this statement. Practically, it has been
validated that this does hold for the case of practical interest [6]. The drawback of such
an analysis may strongly depend on the size error between a Gaussian distribution and its
true distribution. When background thermal noise is small, this error can actually be
large with respect to such noise.
2.2
Spectral Compatibility between Asymmetric and Symmetric DSL Systems
Determining spectral compatibility between new and existing DSL services is a
significant challenge. Recently, a number of studies have been conducted on spectral
compatibility between DSL systems [18], [19], [20], [21]. Spectral compatibility has
become a major issue for all DSL systems, especially with respect to transmission of
10
asymmetric and symmetric services in the same binder group. When DSL deployment
reaches significant penetration, crosstalk between the various DSL services will become
the dominant performance-limiting factor to QoS of DSL systems.
The spectral
compatibility of the ADSL service with the deployment of SDSL services is the main
focus of this thesis.
2.2.1 Symmetric DSL Systems
In 1996, ETSI has made the single-pair HDSL (early version of SDSL) in standard.
This service transmits a full E1 payload on a single copper pair with a variable line rate
up to 2320 kbps [22]. The technique that enables this superior performance of a singlepair SDSL service, uses the same 2B1Q modulation, (as in HDSL, and ISDN), but with a
modified maximum likelihood detection on its receiver. There is no error correction
coding in SDSL systems.
SDSL transmits the same data rate in the upstream and downstream directions and
same transmit PSD in the upstream and downstream directions. It is bi-directional and
echo-canceled system.
2B1Q SDSL transmits a 4-level baseband pulse amplitude
modulation signals. 2B1Q SDSL systems operating at different bit rates have different
transmit PSDs. More detailed information about SDSL can be found in [22], [23], [24].
2.2.2
Studies on Crosstalk Noise between ADSL and SDSL
The spectral compatibility of high-rate SDSL services with the ADSL service in the
same binder is studied herein. We focus on SDSL services interfere ADSL service,
because of the following two reasons. First, The SDAL services are high in demand for
11
the future deployment and run on a single twisted pair telephone line together with ADSL
service in a same binder. Second, the PSDs of SDSL services, shown in Fig. 2.2.2.1, are
overlapped in most areas with ADSL PSD, which is from DC to 1.104MHz.
Spectral compatibility results are calculated for same-binder NEXT with the standard
Unger 1% NEXT model. The maximum achievable bit-rate of T1.413 full-rate DMT
ADSL in the presence of NEXT from SDSL systems was calculated. The DMT tones are
separated by 4.3125 kHz, and the received SNR of each tone was calculated. The
maximum bit-rate that each tone can carry with a 6dB SNR margin was found and then
summed across all tones to get the total achievable T1.413 bit rate. The average transmit
power of downstream ADSL is -40 dBm/Hz, and the average transmit power of upstream
ADSL is -38 dBm/Hz, within the passband. T1.413 ADSL is assumed to have trellis
coding gain of 3dB and 2dB ripple, and is FDD with non-overlapping upstream and
downstream spectra. Downstream T1.413 ADSL is assumed to transmit from 160 kHz to
1104 kHz, and upstream T1.413 ADSL transmits from 26 kHz to 138 kHz. The pilot
tones carry no data. A maximum of 12 bits per Hz can be transmitted by any tone in the
T1.413 simulations here, allowing a maximum constellation size of 4096 points. ADSL
bit rates are rounded down to the nearest integer multiple of 32 kbps. Cyclic prefix
redundancy (6.66%) and a minimal 32 kbps EOC redundancy was removed before
presenting the bit rates here.
Achievable downstream ADSL bit rates in the presence of SDSL crosstalk is obtained
as a function of loop length and SDSL data transmission rates. The simulation studies
have shown that high rate, such as 1552 and 2320 kbps SDSL NEXT, largely reduces the
ADSL downstream transmission data rates below its required minimum target rate, which
12
is 6 Mbps (low bound) up to 9 kft and 1.5.Mbps (low bound) between 9 to 18 kft. The
results are shown in Fig. 2.2.2.2. It is obvious that the higher the data rate of the SDSL
transmission, the poorer the performance of the ADSL achievable rate. The degradation
of the ADSL achievable rates can also be caused by the other DSL services in a same
binder with the similar manner. Therefore, it is necessary for us to modify the ADSL
system to suppressing crosstalk noise from the SDSL services (also to the other DSL
services) to utilize its optimal capacity at reasonable cost. (Meanwhile, the preliminary
enhancement studies on the SDSL systems can be found in [25], [26].)
1168, 1552 and 2320 kbps SDSL
PSD (dBm/Hz)
-30
-40
1168 kbps
1552 kbps
-50
2320 kbps
-60
-70
-80
-90
-100
-110
0
400000
800000
1200000
1600000
2000000
Frequency (Hz)
Fig. 2.2.2.1: PSD of 2B1Q SDSL at 1168, 1552 and 2320 kbps
13
Downstream Bit Rate in kbps
DMT-ADSL System with 24-SDSL Crosstalk
8000
7000
6000
1552 kbps SDSL crosstalk
5000
4000
3000
2000
2320 kbps SDSL Crosstalk
1000
6
8
10
12
14
16
18
26-AWG Loop Length in kft
Fig. 2.2.2.2: Downstream ADSL Bit Rate with 1552 & 2320 kbps SDSL NEXT.
14
2.2.3
Current Deployment Plan and Proposed Enhancement
For the telephone companies deploying the ADSL and SDSL services in their loops,
they use a so-called loop plan, which is basically testing and estimating of their
deployment loops with limitation on the coverage and numbers of the customer
subscribers.
Therefore, the ADSL achievable rates degradation resulting from the
crosstalk can be loosely controlled with various DSL services in the same binder groups.
The drawbacks of this method are inconvenience for deployment management; limit on
the transmission data rate; not rejecting out-of-band signal (crosstalk) by receivers, and
trading off the loop coverage and subscriber numbers.
Our studies on the crosstalk characteristics show that the crosstalk channel
characteristics change very slowly over the time and can be modeled as static. Moreover,
the type of crosstalk on each line, say on ADSL service line, does not change, as there are
fixed DSL services in the same binder from the CO to CPE sides. Therefore, mitigating
the crosstalk between DSL systems, we use a technique to enhance the ADSL receiver
that “filters” the crosstalk noise. Without loss generality, this approach can be applied to
the other DSL systems as well.
15
CHAPTER THREE
DMT-ADSL CHANNEL MODULATION AND CHARACTERISTICS
3. Discrete Multitone Modulation System and ADSL
Discrete Multitone (DMT) is a common form of multicarrier modulation. It has been
introduced by IBM [27] to take advantage of digital signal processing and the FFT. It
was later refined to a very high-performance form [28], [29]. That later form is used in
the most recent multicarrier voiceband modems, such as ADSL [30]. DMT is a method
to approximate the channel complex filters by simpler operations, which are to exploit the
knowledge of the channel information matrices, tend to discrete Fourier transforms
(DFT) algorithm [31].
It is similar to orthogonal frequency division multiplexing
(OFDM), which is widely used in wireless communications systems. A DMT system
transmits data in parallel over narrowband channels. The subchannels carry a different
number of bits, depending on their SNR. A DMT system transmits data using a twodimensional QAM on each channel.
DMT-ADSL has been standardized by ANSI [15]. Herein, we only focus our study
in DMT-ADSL. We are going to have an overview on DMT system first, before landing
on the details of the DMT-ADSL system.
16
3.1
Overview of Discrete Multitone
The principle of multitone transmission is by using two or more coordinated passband
(like QAM) signals to carry a single bit stream over the communication channel. The
passband signal are independently demodulated in the receiver and then remultiplexed
into the original bit stream. The motivation for multitone is that if the bandwidth of each
the sub-channel (tone) is sufficiently narrow, then no ISI occurs on any sub-channel. The
individual passband signals may carry data equally or unequally. Usually, the passband
signals with largest channel output SNR carry a proportionately larger fraction of the
digital information.
Fig. 3.1.1 shows the simplest multitone system to understand. N QAM (or like)
modulators, along with possibly one DC/baseband PAM modulator, transmit N+1
subsymbol components X n , n = 0, 1, …, N, where N = N / 2 and N is assumed to be
even number. X 0 and X N are real one-dimensional subsymbols while X n , n = 1, 2, … ,
N-1 can be two-dimensional complex subsymbols. Each subsymbol represents one of
2 bn messages that can be transmitted on sub-channel n. The carrier frequencies for the
corresponding sub-channels are f n =
equivalent basis functions are ϕ n =
n
, where T is the symbol period. The basebandT
1
t
⋅ sinc( ) , ∀n . The entire transmitted signal can
T
T
be viewed as N+1 independent transmission sub-channels as indicated by the frequency
band of Fig. 3.1.2.
17
X0
X1
ϕ 0 (t )
e − j 2πf1t
e j 2πf1t
ϕ1 (t )
+
ϕ1 (−t )
+
real part
n(t)
.
.
.
XN-1
XN
ϕ N −1 (t )
ϕ N (t )
e
j 2πf N −1t
+
e j 2πf N t
+
+
h(t)
+
phase
split
N = 2N
ϕ 0 ( −t )
e − j 2πf N −1t
+
e − j 2π f N t
Yn = H n ⋅ X n + N n
+
Y0
Y1
.
.
.
ϕ N −1 (−t )
YN-1
YN
ϕ N ( −t )
Fig. 3.1.1 Basic Multitone Modulation Transmission
18
Input
X(f )
X0
X1
X2
...
H( f )
XN
Yn ≈ H n ⋅ X n
Y( f )
Y0
XN-1
Output
Y1
...
Y2
YN-1
Fig. 3.1.2: Illustration of Frequency Bands for Multitone Transmission System
19
The multitone-modulated signal is transmitted over an ISI/AWGN channel with the
corresponding demodulator structure also shown in Fig. 3.1.1.
First quadrature
decoupling with a phase splitter and then baseband demodulating with a matchedfilter/sampler combination separately demodulates each sub-channel. With this particular
ideal choice of basis functions, the channel output basis function ϕ p ,n ( t ) is an
orthonormal basis set. Each sub-channel may have ISI, bit as N → ∞ , this ISI vanishes.
Thus, symbol-by-symbol detection independently applied to each sub-channel
implements an overall maximum-likelihood (ML) detector. No equalizer (nor Viterbi
detector) is necessary to implement the maximum-likelihood detector with large N.
Therefore, ML detection is more easily achieved with multitone modulation on an ISI
channel than it is on a single QAM or PAM signal, the latter of which would require
sequence detection with the Viterbi algorithm for a large number of states. Equalization
is also unnecessary if the bandwidth of each tone is sufficiently narrow to make the ISI
on that sub-channel negligible.
Multitone modulation typically uses a value for N that ensures that the pulse response
of
the
ISI
channel
appears
almost
constant
at
H (n / T ) ≡ H n = H ( f )
for
| f − n / T |< 1 / 2T . In practice, this means that the symbol period T greatly exceeds the
length of the channel pulse response. The scaled matched filters simply become the
bandpass filters ϕ p ,n (t ) = ϕ n (t ) = 1 / T sinc(t / T ) ⋅ e j ( 2π / T ) nt and the sampled outputs
become
Yn ≈ H n ⋅ X n + N n
(3.1.1)
20
The accuracy of this approximation becomes increasing exact as N → ∞ . Fig. 3.1.2
illustrates the scaling of H n at the channel output on each of the sub-channels. Each subchannel scales the input X n by the pulse-response gain H n .
Each sub-channel in the multitone system carriers bn bits per symbol. The total
number of bits carried by the multitone system is then
N
b = ∑ bn
(3.1.2)
n =0
and the corresponding data rate is then
R=
N
b
= ∑ Rn
T n =0
(3.1.3)
where Rn ≡ bn / T . Thus, the aggregate data rate R is divided, possibly unequally, among
the sub-channels.
With sufficiently larger N , an optimum ML detector is easily implemented as N+1
simple symbol-by-symbol detectors. This detector need not search all combinations of
m = 2 b possible transmit symbols. Each sub-channel is symbol-by-symbol detected.
The reason for this ML detector is so easily constructed is because of the choice of the
basis function: multitone basis functions are generically well suited to transmission over
ISI channels.
21
3.2.
Analysis of Discrete Multitone
The multitone transmission system is construed as N subchannels (tones). The most
importance is performance analysis and optimization of performance for the entire set of
subchannels.
3.2.1. Channel Gap Analysis
The probability of error for a multicarrier system is the average of the probabilities of
error on each sub-channel.
We assume that the probability of subsymbol error to be equal on all sub-channels
and to be equal to Pe / 2 = 10 −7 . We also assume that the gap Γ , is a constant value for
all the sub-channels, which is defined for any coded QAM system as
Γ = 9.8 + γ m − γ c ( dB )
(3.2.1.1)
where γ m is the margin and γ c is the coding gain.
We derive for an individual i th sub-channel that having
3Γ =
2
d min,
i
4δ i2
=
| H i |2 d i2
4δ i2
(3.2.1.2)
22
For any sub-channel, we have
bi = log 2 (1 +
SNRi
)
Γ
(3.2.1.3)
as the maximum number of bits per symbol that can be carried on that sub-channel with
margin γ m and coding gain γ c . The quantity SNRi is computed by
SNRi =
| H i |2 ε i
2δ i2
(3.2.1.4)
in this thesis, we assume that ε i = ε , a constant value on the sub-channels used and zero
on else. This is called on/off energy distribution. In practice, a better solution on the
energy distribution, which is called “water-pouring” can be found in [32]. Moreover, in a
DMT system, the sub-channels carry a different number of bits, depending on their
respective SNRi , this is referred to as a bit-loading algorithm. Several techniques on how
to perform bit-loading in a DMT system has been studied [33], [34], [35], [36] and [59].
3.2.2. Margin of the DMT
The total number of bits that is transported in one symbol is the sum of the number of
bits on each of the sub-channels, that is
N
N
i =1
i =1
b = ∑ bi = ∑ log 2 (1 +
SNRi
)
Γ
(3.2.2.1)
23
Therefore, the data rate is
R=
b
T
(3.2.2.2)
Eq. (3.2.2.1) can also be derived as
N
b = log 2 [∏ (1 +
i =1
SNRi
)]
Γ
(3.2.2.3)
We can define an average SNR as
N
SNR = Γ{[∏ (1 +
i =1
1
SNRi N
)] − 1}
Γ
(3.2.2.4)
Therefore, Eq.(3.2.1.1) can be written as
b = N ⋅ log 2 (1 +
SNR
)
Γ
(3.2.2.5)
From Eq. (3.2.2.5), it permits direct computation of a margin for a multicarrier system
with fixed data rate and probability of error. Normally, the “-1” term in Eq. (3.2.2.4) can
be ignored, and the average SNR becomes the geometric average
N
SNR ≈ [∏ ( SNRi )]
1
N
(3.2.2.6)
i −1
24
The definition of margin, γ m , for transmission on an AWGN subchannel with a given
SNR, a given number of bits per dimension b, and a given coding-scheme/target-Pe with
gap Γ is the amount by which the SNR can be reduced and still maintain a probability of
error at or below that target Pe [37].
We may compute the margin of the DMT with Eq. (3.2.2.5) as
γ m = [10 log10 (
SNR
) + γ c − 9.8]dB
b
N
(3.2.2.7)
2 −1
3.2.3. Performance Calculation
The procedure to analyze the multicarrier system is summarized in [37] as:
1. From the power budget, compute a preliminary subsymbol energy allocation
according to ε = ε i =
PT
.
N
2. Compute the sub-channel SNR’s according to
SNRi =
ε | H i |2
δ i2
(3.2.3.1)
3. Compute the number of bits that can be transmitted on each sub-channel with
given margin and given error correction code
bi = log 2 (1 +
SNRi
)
Γ
(3.2.3.2)
25
4. For those sub-channels with bi < 0.5 , reset ε i = 0 and reallocate their energy to
the other sub-channels equally. Then, we need re-compute bi .
5. Compute b by summing the bi , and then compute the maximum data rate R = b/T.
A margin can be computed using any number of used sub-channels. For data rates
considerably below theoretical optimums, the number of used sub-channels often
decreases with respect to the bandwidth used for the maximum data rate. The bandwidth
with the best margin is used for a target rate, which is lower than maximum data rate.
3.2.4
Bit-loading and DMT-ADSL System
In this subsection, we review the concept on the DMT-ADSL system characteristics.
Fig. 3.2.4.1, illustrates the concept of the bit-loading algorithm in the DMT-ADSL
system. Bit-loading is a technique that is used for multicarrier systems (DMT in this
thesis) operating on a stationary channel [33]. A stationary channel makes it possible to
measure the SNR on each subchannel and assign individual numbers of transmitted bits.
A subchannel with high SNR transmitted more bits than a subchannel with low SNR.
Fig. 3.2.4.1 shows a schematic picture of SNR and how the numbers of bits on each
subchannel vary accordingly.
When performing bit loading, one usually optimizes for either high data rate, or low
average transmitting energy, or low error probability. Typically two of these are kept in
constant, and the third parameter is the goal for the optimization. The parameter is
optimized depending on the system, its environment, and its application.
26
In a multi-system environment, where there are several DSL systems transmitting in
the same binder, the problem is complicated, since this kind of system experience
crosstalk. The level of crosstalk is proportional to the transmitting power in the systems,
as shown in Eq.(2.1.1.1). It is therefore desirable to have an equal transmission power in
all systems, to obtain equal distribution. In a multi-system environment, the average
transmitting power is usually fixed, and the optimization is for either high data rate or
low BER.
There are several techniques for bit loading in DMT systems and some of these are
described [33], [38], [39], [40]. As mentioned earlier, there are several parameters that
one can optimize for. Most algorithms optimize for high data rate or low BER.
Given a certain data rate and energy constraint, the algorithm to achieve minimal
BER is to assign one bit at a time to the subchannels. The algorithm calculates the
energy cost to send one bit more on each subchannel. The subchannel with smallest
energy cost then assigned the bit. This procedure is repeated until a desired bit rate is
obtained. In [38], it has shown that complexity of this algorithm is proportional to the
number of subchannels and the number of bits transmitted in a DMT frame. It also
suggests a suboptimal algorithm of low complexity.
An algorithm that maintains an equal bit-error probability over all subchannels, given
a data rate and an energy constraint, is presented in [39].
A suboptimal way of performing bit loading to achieve a high data rate, while
maintaining a constant BER across all subchannels is shown in [40]. In this algorithm,
the bit-loading are calculated by
27
bk = log 2 (
3E k g k γ d
+ 1) − log 2 C
2 Kδ k2
(3.2.4.1)
where bk is the number of bits carried on subcarrier k, Ek is the average symbol
transmission energy, gk is the channel attenuation, and δ k2 is the noise variance. The
coding gain is denoted γ d and the constellation expansion factor, due to coding is
denoted C. To obtain a desired symbol error rate of Pe, the design constant K is chosen to
K = [Q −1 (
Pe 2
)]
Ne
(3.2.4.2)
where Ne is the number of nearest neighbors.
Expression Eq. (3.2.4.1) can be viewed as the union bound for a QAM constellation,
with some modification for coding, where K is the SNR required obtaining an error
probability Pe. The channel SNR,
3E k g k γ d
, is divided by the SNR required to transmit
2 Kδ k2
one bit. The number of bits needed in the coding, log2C is subtracted to get the number
of bits carried by subchannel k.
Finally, to handle the situation where the numbers of transmitting systems vary one
can either do the bit loading for a worst case or employ adaptive bit loading. In [38], it
has presented such an adaptive algorithm, which called bit-swap algorithm, designed for
the case when a fixed data rate is specified. For detailed information on the bit-loading
for DMT-ADSL system, it can be found in [41], [42].
28
The ANSI T1.413 and ITU g.dmt ADSL system are standardized in the DMT system
[15]. The standards of the characteristic of the DMT-ADSL system are addressed in the
rest of the section.
Bits/channel
Attenuation
AM
Crosstalk
Frequency
Frequency
Frequency
Fig. 3.2.4.1: DMT Bit-Loading Concept.
29
As shown in Fig. 3.2.4.2, the DMT-ADSL system has two traffic channels. One is
downstream transmission, which signals from CO to CPEs side; the revised traffic is
called upstream transmission. They occupy different bandwidths. In a downstream
transmission, the system employs a sampling rate of 2.208 MHz, a block size of 512
(FFT) with conjugate symmetry, meaning 256 tones (subchannels) from 0 to 1.104MHz.
The actual downstream symbol rate is 4 kHz and the width of a tone is 4.3125 kHz. The
average downstream psd is –40 dBm/Hz. The upstream transmission employs a sampling
rate of 276 kHz, a block size 64, with conjugate symmetry, meaning 32 tones from 0 to
138 kHz. The symbol rate for the upstream transmission is 4 kHz and the width of the
tone remains 4.3125 kHz. The average upstream psd is –38 dBm/Hz. The detailed state
of the DMT-ADSL system can be found in [15], [43].
30
# of Bits
Upstream Channel
Downstream Channel
14
POTS
Frequency in kHz
0
4
30
138
240
1104
Fig. 3.2.4.2: DMT-ADSL Frequency Spectrum
31
CHAPTER FOUR
CHANNEL MODEL AND MULTIUSER TRANSMISSION
The investigation of crosstalk testing results [17], in Fig. 3, shows that the crosstalk
coupling function generally increases as f1.5 with frequency, but with significant (about
10 to 20 dB) variation in coupling with frequency. At any given frequency, only a few
other pairs may contribute significantly to crosstalk. Over all frequencies range, many
lines contribute crosstalk affect. Plus, the crosstalk psd is significantly high than the
background psd of AWGN. Otherwise, the crosstalk would not dominate the effect on
DSLs. With these conditions, we propose multiuser detection [44] for the DMT-ADSL
receiver that significantly outperforms the single-user detection, which treats crosstalk as
a Gaussian distribution. In the following section 4 and 5, we derive the twisted-pair
channel model and introduce the multiuser transmission systems.
4.1 Twisted Wire Pairs Characteristics
Twisted wire pairs are the dominating cable type in telephone access networks that
are built for point-to-point two-way communication. The copper wire pair does not
change its physical behavior significantly with time and is considered a stationary
channel [55]. This makes it possible to use a technique called bit loading [33], as shown
in section 3.2.4. for DMT transmission system, which also makes good use of the
32
spectrally shaped channel. Since DMT with bit loading makes efficient use of available
bandwidth, it has become a good candidate for DSL systems.
The characteristics of the wire pair channel have been studied in number of the papers
[45], [55], [11]. In this thesis, twisted pair cable transfer function is derived from lab
measurements using an HP 89410A spectrum analyzer. The transfer function can be
modeled as
att
H (d , f ) = 10 10 ⋅ e −
RCf d
(4.1.1)
where d is the cable length, att is the maximum attenuation, and RC is the cable constant.
The corresponding impulse response is given by
att
10
h(d , t ) = 10
0
RC
e
4πt 3
− RCd 2
4t
t>0
(4.1.2)
t<0
This model is often used when DSL systems are analyzed [54], [46].
As DSL services carry on the telephone network, we discuss the characteristics of the
telephone channel in the following subsection.
4.1.1 Electrical Characteristics of Twisted-pair Wires
The details of twisted-pair wire line electrical characteristics can be found in [47] and
[48]. According to standard transmission line theory, a wire line can be thought of as a
succession of many small sections of the kind shown in Fig. 4.1.1. The inductance and
33
capacitance of the line section are given in L and C per unit length, and the line
dissipation losses are R1 ohms per unit length down the line and R2 ohms per unit length
across the line. For any sections, the characteristic impendence, defined as the ratio of
voltage to current, is
Z0 =
R1 + jωL
R2 + jωL
and ω = 2πf
(4.1.1.1)
I
R1 dy
L dy
+
R2 dy
C dy
V
_
dy
Fig. 4.1.1.1: Transmission Line Segment
Another wire line parameter, called propagation constant is defined as
γ = ( R1 + jωL)( R2 + jωC )
(4.1.1.2)
34
If a voltage V ( jω ) or a current I ( jω ) enters the telephone line, it can be decayed
along the line as V ( jω ) exp( −γy ) or I ( jω ) exp( −γy ) . In particular, amplitudes decay as
e ( −αy ) , where α is the real part of γ , called the attenuation constant. Normally, it is
expressed as
20αy log10 e
(dB/length)
(4.1.1.3)
The wave velocity along the line is ω / β , where β is the imaginary part of γ .
We need stress that all these parameters depend on the frequency. In particular R is
approximately
4.1.2
f , because of the skin effect in conductors.
Telephone Channel
The telephone is an analog medium with a certain character, roughly speaking as a
linear channel with a voice passband of 300 to 3300 Hz initially. There are many kinds
of actual physical telephone channels, due to several telephone network connections in
the world. In fact, it is necessary to define the telephone channel statistically, because no
fixed definition is practical. Extensive studies of the telephone network have been made
in different parts of the world. In North America, the telephone channel has been studied
in [49], and [50]. In Table 4.1.2.1, we summarize some of its main conclusions.
35
Table 4.1.2.1
Worst-case Measurement for Telephone Channels
Attenuation, end to end, at 1 kHz
27 dB
SNR, with special weighting
20 dB
Frequency offset
3 Hz
Peak-to-peak phase jitter, 20-300 Hz
13o
Phase jumps greater than 20o
1/per minute
Noise impulses, 4 dB below mean signal or 4/per minute
higher
Delay
50 ms
Different wire line definitions need be pointed out here for a better understanding on
the telephone loops. The term on leased line refers to a connection that is permanently
allocated to a customer, rather than dialed at each use. A connection is entirely within a
local switching area, called central office, has a much better behavior than a toll wire line,
called a local loop. In a local loop, sometimes, there are a simple wire pair and have
quite a wide bandwidth.
The sources of noise in the telephone channel are digital quantization noise, thermal
noise in detectors, crosstalk between adjacent lines, impulse, etc. Both thermal and
quantization noise can be viewed as a Gaussian noise. Therefore, the telephone channel
is normally treated as a Gaussian channel.
36
4.2
Multiuser Transmission System
The fundamental limit of multiuser detection is to mitigate the interference among
different modulated signals, called crosstalk. We focus our study in telephone cables.
4.2.1 Basic on Multiuser Detection
The basic model for a multiuser channel and transmission system is shown in Fig.
4.2.1.1, where L different data symbols, xl, l = 1, 2,…,L, share a channel with joint
probability distribution p Y . The channel input can be considered to be one large vector
X
L
X of dimension N x = ∑ N x ,l and the output vector is of dimension N. The set of users
l =1
can be viewed as a single user with a larger signal set and a corresponding larger number
of possible messages to be transmitted. Optimum detection of the entire set will be
addressed in the late of this section. However, a receiver observing Y may not desire all
the messages, and likely is attempting to attempting to detect messages from one user.
In the most general form, the multiuser channel is described by the conditional
probability distribution p X . Normally, many channels fit in the linear AWGN model,
Y
that is
Y = HX + N
(4.2.1.1)
where N is a vector of uncorrelated additive Gaussian noise values that each have
variance
No
per dimension.
2
37
x1
X
x2
xL
.
.
.
multiuser
channel
pY
Y
X
Fig. 4.1.2.1: Basic Multiuser Transmission System
4.2.2 Optimum Multiuser Detection
The optimum detector for a multiuser channel is a generalization form of the
optimum single-user channel detector. The set of all possible multiuser channel inputs
will be denoted CX, and contain M =| C X | possible distinct N-dimensional symbols,
which may be a large number that typically grows exponentially with L, the number of
users. CX is a signal constellation, equivalently a code, for the set of all users. The
details of the optimum multiuser detection have been addressed in [52], and [51]. We
review some topics related to our research works.
38
Theorem 4.2.2.1 (Optimum Multiuser Detection) The Probability of multiuser
ˆ ∈ C to maximize p and is
symbol error is minimum when the detector selects X
X
X
Y
known as the maximum a posteriori multiuser detector. When all possible multipleuser input symbol values are equally likely, this optimum detector simplifies to
ˆ ∈ C , and is
maximization of the conditional probability p X over the choice for X
X
Y
called the maximum likelihood multiuser detector [51].
The probability of error for such a system reflects the likelihood that any of the users
may been incorrectly detected
M
Pe = 1 − Pc = 1 − ∑ Pc / i ⋅ p i
(4.2.2.1)
i =1
where Pc/i is the probability that the ith possible multiuser message set is correctly
received.
The users are often modeled as being independent in their choice of transmit message so
that
L
PX = ∏ PX (l )
(4.2.2.2)
l =1
A MAP decoder simplifies to a ML decoder, when each of the users is distributed
uniformly and independently.
39
The ML decoder for the AWGN channel has a probability of error that is
Pe ≤ N e Q(
d min
)
2δ
(4.2.2.3)
where the number of nearest neighbors, Ne, now includes all mutiuser-symbol values in
the calculation and similarly the minimum distance is over the entire set of all multiuser
symbol values.
The co-channel interference in multiuser channel is defined in the
following [51].
Definition 4.2.2.1 (Co-channel Interference Free Channel) A co-channel
interference free multiuser channel (IFC) has a conditional probability distribution
that satisfies
L
p Y = ∏ p y l / xl
X
(4.2.2.4)
l =1
This is the channel probability distribution factor into independent terms for each of
the users. When the channel is not IFC, it is called co-channel interference (CCI)
channel.
With this definition, a lemma trivially follows
40
Theorem 4.2.2.2 (Independent Detection (ID)) The optimum decoder for the IFC is
equivalent to a set of independent optimum decoders for each individual user.
Independent detection means that we can use a separate receiver for each user,
potentially then enormously simplifying the detector implementation. Such systems are
the norm in early multiuser transmission designs, but the assumption of an IFC may not
be true especially when users are not well coordinated or channels are not completely
known during design.
The probability of being correct on the IFC channel is
L
Pe = 1 − ∏ Pc ,l
(4.2.2.5)
l =1
from which one notes that the overall probability of error can never be less than the
probability of error for any one of the users
Pe ≥ Pe ,l
∀l
(4.2.2.6)
a result that also holds true for any multiuser channel, ID or not because maximization of
the probability distribution Pxl / Y is the minimum-probability of error detector for the
symbol xl given the observation Y.
The individual user probability distribution can be computed directly from the overall
conditional distribution according to
41
Pxl / Y = ∫
X / xl
PX d ( X / xl )
(4.2.2.7)
Y
where the integral for any specific value of xl is simply the set of values for X/xl with xl
held constant at the specific value, and it can be computed from known quantities, such
as
PY ⋅ PX
PX =
Y
X
(4.2.2.8)
PY
Equivalently, the individual ML detector for xl given Y uses this distribution
PY / xl =
∫
PY ⋅ PX / x l ⋅ d ( X / x l )
X / xl
(4.2.2.9)
X
Next, we will review the linear multiuser detection with AWGN channel [51], [52],
which is the communication channel for the telephone transmission system.
4.2.2.1 Linear Multiuser Detection in AWGN Channel
The linear multiuser AWGN channel has been described in Eq. (4.2.1.1) as
Y = HX + N
(4.2.1.1)
42
In this channel, when desired input xl = 0 on the set of values for X/xl, in this case, the
channel output contains all the contributions from the other users, except xl.
The
probability of error is as in Eq. (4.2.2.3), when all the other users are simultaneously
detected.
For detection of desired input user xl, it may be that the overall minimum distance is
too small. That is a single fixed value for xl may corresponding to the two multiuser
codewords that determine the overall dmin. This can be defined as,
d min,l =
min
X ≠ X ' ∧ xl ≠ xl'
H (X − X ' )
(4.2.2.1.1)
It is easy to see that,
d min, l ≥ d min
(4.2.2.1.2)
with the equality if and only if any codewords in CX corresponding to the overall dmin also
corresponding to different values for the lth desired users symbol contribution. That has,
min d min,l = d min
l
(4.2.2.1.3)
This illustrates how it is possible for a detector extracting a single user to have better
performance on one that extracts all other users. However, there is always at least one
user that has a d min, l that is no longer than the dmin of the overall detector.
43
Symbol sequences can be handled as the following
Y ( D ) = H ( D ) X( D ) + N ( D )
(4.2.2.1.4)
where all the vector or matrix D-transforms are defined by sampling finding the D
transform of each element and D corresponding to a delay of a symbol period.
44
CHAPTER FIVE
ADSL SYSTEM ENHANCEMENT
5.1
Multiuser Detection on DMT-ADSL System
Last section, we reviewed the concept of multiuser detection [51], [52], where
optimum linear detectors and structures for telephone transmission channel has been
investigated. This method is very successfully used in the wireless network to combat
cochannel signals with employing frequency reuse where one or more secondary signals
from nearby cells can interfere with the desired signal. It has also been studied in the
VDSL system; together with the Home-Phone LANs (HPL) [53] and showing very little
degradation from the HPL crosstalk with multiuser detection, while large degradation
with a single-user detector.
This thesis employs multiuser detection for the DMT-ADSL system to mitigate
crosstalk from SDSL systems in the same binder. The goal of this thesis is to apply this
approach and algorithm to all DSL systems to suppress crosstalk between their services
in the same binder. The ADSL multi-access channel model can be derived in Fig. 5.1.1,
in a binder group with k pairs of wire lines. The transmitted ADSL signals are denoted as
x1 and the crosstalk data signals are xk, where K = 2,3,…,k, (can be various DSL signals in
this proposal assuming all with the SDSL). The ADSL channel transfer function is
45
represented as Hc(f), and the attenuation characteristic of the ADSL channel is
approximated by
| H c ( f ) | 2 = e −α
where α = m
f
,
(5.1.1)
l
, l = length of the channel in fleet, l0 = a reference length, f in kHz, and m
l0
= a constant of the physical channel = 1.158, as in Ref. [54]. The spectral distribution of
the NEXT interference coupling to the ADSL line channel is as in Eq. (5.1.1). A key
issue, which differs from the Gaussian model, is that each crosstalking data signal
undergoes filtering by a crosstalk coupling function before effectively being added at the
channel output to the AWGN. With multiuser detection, our proposal will ensure the
performance of telephone systems employing the ADSL loops in the presence of the
SDSL crosstalk.
At the receiver side, the received output is then
K
r (i ) = ∑ hk (i ) ∗ x k (i ) + n(i )
(5.1.2)
k =1
where xk is the transmitted signals, hk is the channel impulse response when k=1, and
together with crosstalk coupling function when k>1, n is AWGN, and K-1 is the total
number of the crosstalk signals in a binder.
The best detector for the multiuser channel is a joint maximum-likelihood detector.
This kind of detector is complex, but theoretically provides bounding of improvement
46
from a multiuser detector. Based on ADSL and SDSL environment studies, a suboptimal solution has been introduced to reduce the computational complexity.
47
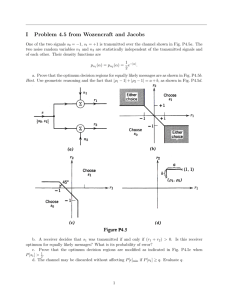
x
Transmit1 (x1)
Noise, σ
2
R
ADSL Channel
+
ADSL Receiver
y
Transmit2 (x2)
Transmitk (xk)
Crosstalk Filtering
+
Crosstalk Filtering
Fig. 5.1.1: ADSL Channel Model with k-1 Crosstalk Signals
48
5.1.1
Theoretic Bounds on Multiuser DMT-ADSL Channel
The maximum possible capacities for the individual users in multiuser transmission
system help provide bounds and goals that guide the design. We have investigated a
sophisticated and more convincing theoretic argument on the achievable performance
bounds by using the multiuse DMT-ADSL channel with the SDSL crosstalk noise. It
shows that data rate of the DMT-ADSL system, which is modeled as a multiuser channel
together with the SDSL crosstalk, is higher than the data rate as the single-user channel
that modeled the crosstalk as Gaussian noise with the same PSD. The later Gaussian
modeling is what is being used today in projections that the SDSL crosstalk defeats the
DMT-ADSL transmission, but is grossly pessimistic inaccurately modeling the SDSL
crosstalk
5.1.2
Spectral Distribution on the Multiuser Channel Capacity
The spectral distribution in twisted pair channels is not distributed linearly within the
width of the frequency band. The reason is that the signal amplitude attenuates as the
frequency and loop length increase, and thus for the voice band, the useful spectrum of
the TPC is located at low frequencies, as discussed in [55]. Fig. 5.1.2.1 shows a typical
TPC attenuation characteristic at low frequencies, which is from DC to 3300Hz with the
difference measurement point from the center office (CO). Fig. 5.1.2.2 shows a typical
attenuation characteristic of a TPC, which is up to 1500 kHz, and also shows the NEXT
attenuation (or the channel transfer function) from low frequencies to high frequencies.
49
0
TPC Attenuation in dB
60 0 fe et from CO
-50
60 00 feet from CO
-100
-150
-200
-250
18 000 fee t fro m CO
-300
0
500
1000
1500
2000
2500
3000
3500
Frequency in Hz
Fig. 5.1.2.1: TPC Attenuation Function with Difference Length
0
-10
-20
analytic channel model, in Eq.(2)
Gain in dB
-30
-40
-50
squared crosstalk coupling function
-60
-70
-80
-90
0
500
1000
1500
Frequency in kHz
Fig.5.1.2.2: Channel Attenuation and NEXT Coupling Characteristic
50
Based on Fig. 5.1.2.2, we can see that at higher frequencies, there is higher attenuation
and higher NEXT crosstalk coupling, which results in smaller the SNR and the channel
capacity per unit spectrum decreases in TPC. We derive these issues in the following and
also address a comparison on channel capacity performance with our multiuser channel
model to current single-user channel, treating crosstalk as Gaussian distribution.
For the DMT-ADSL system shown in Fig.5.1.1, basic information theory can be used
to determine a maximum data rate between the set of channel inputs containing desired
DMT-ADSL signal and crosstalk signals, {x: (x1, x2,…,xk)} and the channel output y,
which is called mutual information [56]. This mutual information can be represented as
I ( x; y ) = H ( x ) − H ( x / y )
(5.1.2.1)
where H(x) is called the entropy of the source x and defined as
k
H (x) = −∑ p ( x i ) log 2 p ( x i ) (bits/outcome)
(5.1.2.2)
i =1
and H(x/y) is called the conditional entropy of x, which defined as
H (x / y ) = −∑ p ( x / y ) log 2 p ( x / y )
(5.1.2.3)
x
The mutual information can be viewed as the reduction in the uncertainty in x, on the
average, if y is known. Hence, the mutual information is a function of the crosstalk
signal contributions, which are often given and not necessarily alterable by optimization,
51
for example using a coding scheme. Therefore, the Shannon’s paper [58] is an assertion
of the channel capacity on our study. Shannon asserted that there was a largest measure
of information that a given noisy channel can carry with vanishing small error
probability; it is called the channel capacity, which is
C = max I ( X , O)
p( X )
(bits/channel used)
(5.1.2.4)
Therefore, C is the largest possible mutual information between the input source, X,
and the output O. The capacity, C is the largest measure of information that can be
learned about X through this channel. In the following, we derive the capacity for the
conventional single-user and our proposed multiuser ADSL channel models.
Fig. 5.1.2.2 illustrates the channel transfer function, and NEXT coupling transfer
function, denoted by H c ( f ) , and H NEXT ( f ) , respectively. We assume that the channel
can be characterized as a linear time-invariant system. In DMT system, we can divide
the transmission bandwidth B of the channel onto K narrow frequency sub-channels
(bins); each of width W Hz and assume that the channel, noise and the crosstalk
characteristic vary slowly enough with frequency that they can be approximated as
constant over each bin.
In the conventional single-user ADSL receiver, it is a fact that at higher frequencies,
there is higher attenuation and higher NEXT results in smaller the SNR and the channel
capacity per unit spectrum decreases.
The reason is we sum all the crosstalk
interferences and background noise (Gaussian distribution) to get the total Gaussian
noise. Consider the case of two neighboring lines carrying an ADSL service (desired
52
channel) and a SDSL service (crosstalk channel), under the Gaussian channel
assumption, we can write the single-user ADSL receiver capacity as
∞
Csin gle−user
| H c ( f ) |2 Pdesired ( f )
= sup ∫ log 2 [1 +
]df
N o ( f ) + | H NEXT ( f ) |2 Pint erference ( f )
Pdesired , Pint erference 0
(5.1.2.5)
The supermum is taken over all possible Pdesired ( f ) and Pint erference ( f ) satisfying:
Pdesired ( f ) ≥ 0, Pint erference ( f ) ≥ 0,
∀f
(5.1.2.6)
and the average power constraints for the two directions
∞
∞
0
0
2 ∫ P desired ( f )df ≤ Pdesired _ max , 2 ∫ Pint erference ( f )df ≤ Pint erference _ max
(5.1.2.7)
The denominator of Eq. (5.1.2.5) is dominated usually by the lager NEXT,
| H NEXT ( f ) |2 Pint erference ( f ) . This NEXT is much lager than background noise, which
usually in –140 dBm/Hz.
In our enhanced multiuser ADSL receiver shown in Fig. 5.1.1, we use a joint ML
detector, which is the best detector for the optimal solution. The objective of the JMLSE
is based on the single output available in a single ADSL, it selects over all possible
crosstalk channel inputs and main desired channel inputs (herein, as ADSL channel
inputs) that particular set of input, which minimizes the distance from the received single
53
channel output. In another word, JMLSE decode the desired vector x1 , and possible the
interfering signal vectors x K = x 2 ,..., x k , based on received signal R.
The signal
component H K ⋅ x K is treated as an interfering signal matrix, which prevents the
decoding of the desired signal x1 .
Rather than treating this interfering signal as a
background Gaussian noise, the JMLSE can significantly improve performance by jointly
detecting the desired signal vector x1 with crosstalk signals. Thus, we can write the
ADSL channel capacity as
∞
Cmultiuser
| H c ( f ) |2 Pdesired ( f )
= sup ∫ log 2 [1 +
]df
No ( f )
Pdesired 0
(5.1.2.8)
Obviously, we can conclude that Eq. (5.1.2.8) has much higher throughput that Eq.
(5.1.2.5).
Shown in Fig. 5.1.1, multi-user access channel capacity considers the problem where the
received signal Y consists of a superposition of signals X i , received with power Pi and
bandwidth B , in the presence of additive white Gaussian noise N with sample power n
Y = ∑ Xi + N
(5.1.2.9)
i
As an example, consider the two user case, Y = X 1 + X 2 + N , and assume without loss of
generality that is X 1 the signal of interest and X 2 is an interfere.
An intuitively
straightforward way to deal with this case is to think of X 2 as another noise term and
54
lump it into N. This "single user" approach does not take advantage of the structure of the
interfering term and results in a significant penalty in the achievable capacity. It can be
shown [56], and [57]) that in this case the achievable capacity for user 1 is
P1
C1* = B log1 +
P2 + nB
(5.1.2.10)
and similarly for user 2
P2
C 2* = B log1 +
P1 + nB
(5.1.2.11)
In Figure 4 below, the achievable capacity region is depicted in the square formed by the
dotted lines. If however, X 1 and X 2 are considered jointly, then the achievable capacity
is given by
P
P + P2
Ri ≤ B log 1 + i , R1 + R2 ≤ B log 1 + 1
nB
nB
(5.1.2.12)
which is depicted in Figure 5.1.2.3 below by convex hull formed by the solid lines.
Notice the considerable capacity improvement when the interference structure is taken
into account.
55
P
C i = B log 1 + i
nB
(5.1.2.13)
Rate
(User 1)
C1
Multiuser
C1*
Single
User
Rate
(User 2)
C2*
C2
Figure 5.1.2.3: Channel Capacity – Single vs. Multiuser Channels
An alternate, we can derive the same conclusion of a better performance in
multiuser DMT-ADSL model using [14]. As shown in Fig. 5.1.1, the signal y represents
the sum of all the data signals and R is the signal at the ADSL receiver. The mutual
information I(x, y) cannot exceed the mutual information between the aggregate data
signal R and the channel output y, I(R, y) [58] ,[59]. Also, if each user has data rate Ri, i
= 1,2,…K, then we have
56
L
`
∑R
i =1
i
≤ I ( X, R )
(5.1.2.14)
Now, we start with: I ( x, y ) ≤ I ( R , y ) , with equality if x ↔ R is a one-to-one
mapping. The mapping is one-to-one in all but degenerate cases when the discrete
distribution of x is considered. The case of the mapping being close to singular, not oneto-one, is accommodated tacitly in the following analysis by the assumption attached to
the level of the power spectral density of the AWGN that is added to R from y. This later
mutual information is between a single channel input and a signal channel output and is
easily computed for an ADSL channel. The number attached to I(R, y) strongly depends
on the level of AWGN, which does not include crosstalk signal impairments. This level
can be very low for an ADSL and is often determined by receiver thermal noise or
analog-to-digital converter quantization levels, which are often controllable by design.
Any larger noise is likely to be crosstalk, and it spans a substantial bandwidth. If it is a
crosstalk signal, then this proposal will distinguish it from the noise.
Computing the mutual information I(R, y) for an ADSL system is straightforward.
This number will be high, often an order of magnitude more or higher than data rates
normally projected for an ADSL. This large value is because the AWGN is small
compared with the crosstalk signals.
The achievable data rate for the desired channel, i =1, is then bounded by the
achievable limit [60]
K
R1 ≤ I ( R, y ) − ∑ I ( xi , y ).
(5.1.2.15)
i=2
57
The limit in Eq. (5.2.1.10) can be a much larger number than the data rate based on
Gaussian crosstalk assumptions. The sum of data rates subtracted on the right can be a
much smaller number than might be initially computed by summing the data rates of all
crosstalk signals. The smaller number will occur because of the frequency-selective
crosstalk coupling function in Fig. 5.1.1 The effective data rate or information of a highly
bandlimited random process is essentially zero when its power spectral density is less
than the AWGN level [61].
5.1.3
Examples on Capacity Bound Analysis
As an example, assume that we are interested in the pairwise crosstalk interference from
an adjacent neighboring the SDSL has psd of –38dBm/Hz to the desired DMT-ADSL
system. Each DMT-ADSL tone has a bandwidth of 4.3125 kHz. The center frequency of
the downstream DMT-ADSL is 690 kHz. The SDSL crosstalk coupling function to the
ADSL channel can be calculated with 10-9f1.5 [54].
A psd of –38 dBm/Hz SDSL
transmitted energy will have a psd of –86.8 dBm/Hz at the ADSL receiver. As we know,
the background white noise is –140 dBm/Hz in the commonly used case. The mutual
information of a SDSL crosstalk on the ADSL circuit line is
I ( x 2 , y ) = BW each _ tone log 2 (1 + 10 ( psd _ awgn − psd _ coupling _ signal ) / 10 )
= 4.3125kHz log 2 (1 + 1014 −8.68 ) = 78.5kbps.
This means, it is possible to sufficiently detect a 1552 kbps SDSL signal with 20 tones in
the worst case with the right code. Moreover, though it is a pairwise result, this capacity
is very closed to an ADSL line in a binder group with many wire lines together, because
58
our study [62] has also shown that the major dominant effect of the crosstalk is from an
adjacent neighboring pair DSL service in the same binder group.
Therefore, -86.8
dBm/Hz is quite closed to the total 50-pair crosstalk degradation in the binder, but only 2
or 3 dBm worse than that [62].
Assume that a maximum instantaneous data rate of 2320 kbps SDSL signal is coupling
with an ADSL system; thus, the maximum mutual information from the SDSL signal into
the ADSL line is limited to 2320 kbps. An ADSL signal has an average attenuation of
about 43 dB in its downstream bandwidth, with psd of –40dB/Hz. Therefore, it should
have a residual capacity of
I ( x1 , y ) = I ( R, y ) − 2320kbps
= 1.104 MHz log 2 (1 + 10[ − ( 40 + 43) −( −140 )] / 10 ) = 21Mbps.
In theoretic bound, there is enough room for the ADSL signal to transmit much faster
than the current limit. Though additional SDSL and other DSL signals would reduce this
21 Mbps rate a bit, it will always be possible to detect the ADSL signal even with some
large impractical interference signal levels, which may never exist in DSL line channel.
Finally, if the SDSL crosstalk coupling were modeled as a white Gaussian noise with the
same psd, the ADSL data rate then becomes
R ADSL = 1.104 MHz log 2 (1 + 10 8.68−8 ) = 330kbps,
59
which is almost a complete loss. Therefore, it is too pessimistic to model the crosstalk as
a white Gaussian noise, as currently used.
5.2
Joint Maximum-likelihood Sequence Estimation (JMLSE)
This technique is based on maximum-likelihood sequence estimation (MLSE) [63],
[64]. Since the cochannel signals are jointly recovered, this kind of method is referred to
as joint maximum-likelihood estimation (JMLSE) [65].
5.2.1
DSL Co-channel Signal Model
A general multi-access UTP channel model is shown in Fig.5.1.1. As our study
shows, the adjacent neighboring pair has the dominating contribution on the NEXT
interference [62]. The block of N pairs wire line channel model can be illustrated in as
Fig. 5.2.1.1. The transmitted low-pass equivalent waveforms can be represented by
x m (t ) =
∞
∑d
k = −∞
m
( k ) g (t − kT ), m = 1,2,...N
(5.2.1.1)
where T is the symbol duration, {d1(k)} is the primary source symbol and {dm(k)},m =
2,3,…,N, is interference source symbols, and g(t) is the shaping function.
DSL systems use twisted-pair copper cable as their transmission media. The
transfer function of the twisted-pair copper cable can be modeled as [66], [67]
H (d , f ) = 10
max_ atten
10
e−
RCf d
,
(5.2.1.2)
60
where d is the cable length, max_atten is the maximum attenuation, and RC is the cable
constant.
The corresponding impulse response is given by
att
10
h(d , t ) = 10
0
RC
e
4πt 3
− RCd 2
4t
t>0
t<0
Primary Channel
d1(k)
d2(k)
g(t)
x1(t)
(5.2.1.3)
Ν(t)
h1(t)
+
g(t)
x2(t)
h2(t)
R
E
C
r(t)
T/2 Sampler
g(t)
dN(t)
hN(t)
xN(t)
CrosstalkChannel
Fig. 5.2.1.1: Co-channel System Model
The discrete measurement samples of the received signal r(t) at the output of the T/2spaced sampler in Fig. 8 are given by
61
N
Lm
r (kT + jT / 2) = ∑∑ hm ,n (kT + jT / 2)d m
m =1 n =0
(5.2.1.4)
+ N (kT + jT / 2), j = 0,1,..., N − 1
where the noise sequences {N(kT+jT/2)} are assumed to be independent, white and
Gaussian with zero mean and equal variance. The reasons on choosing the T / 2 -spaced
Joint MLSE are to eliminate the whitening matched filter, and also less sensitive to
sampling time offsets.
As an example on each adjacent pair line, the delay spreads of the primary and secondary
channels are L1T and L2 T . The 2( Lm + 1) channel coefficients { hm ,n (kT + jT / 2) }
represent the convolution of the frequency selective channels with the transmit filter g(t),
sampled at T/2 second. The goal for our proposed receiver is to accurately recover the
sequences {d1(k)} and {d2(k)}, given reliable estimates of the channel impulse response
h1 (k ) and h2 (k ) , where hm ( k ) = [ hm ,0 ( k ), hm ,1 ( k ),..., hm , Lm ( k )] . Here, we assume the UTP
channel is a Gaussian channel, which has mutually uncorrelated, white Gaussian
background noise, with zero mean and equal likely spectral density, δ 2 / 2 .
As the JMLSE is based on the technique of MLSE, we are going to review the MLSE
receiver in the following sub-sections.
This helps us on better understanding how
JMLSE works on ADSL receiver enhancement.
5.2.2 MLSE Receiver Design
The maximum-likelihood sequence estimator [68], [69], [70] has shown the best
performance among all the equalizers and detectors, which called an “optimal” receiver
in the communication systems.
62
The optimum receiver selects the most probable transmitted sequence, using all
available information fully. The a posteriori probability is the probability that the symbol
sequence, { α } was transmitted, given that r(t) was received, as
pα r (t ) ({α }r (t ))
(5.2.2.1)
The statistically optimum receiver computes a posteriori probabilities for all
transmitted sequences, and then chooses the sequence with the greatest a posteriori
probability. This receiver structure is called maximum a posteriori probability (MAP).
Using Bayes theorem, the a posteriori probability can be rearranged as
pα r (t ) ({α }r (t )) =
pα ,r (t ) ({α }, r (t ))
p r (t ) (r (t ))
=
p r (t ) α (r (t ){α })pα ({α })
p r (t ) (r (t ))
(5.2.2.2)
Ultimately the probability expression is used for decision-making, so the
denominator, p r (t ) (r (t )) , can be discarded, since it is common for all hypothesised
sequences. A goal of communications is maximizing the information rate, so source
coding (e.g. Huffman coding, arithmetic coding) is often employed. The symbol
sequence is approximately white, with equiprobable symbols. Accordingly, maximizing
the a posteriori probabilities is equivalent to maximizing the conditional probabilities,
p r (t ) α (r (t ){α })
(5.2.2.3)
63
for all symbol sequences. This is an MLSE structure, and is optimal when the symbols
are equiprobable. As written, the conditional probabilities are computed at the end of
transmission, whereas a recursive algorithm to compute the conditional probabilities is
preferred since transmission may never stop.
A continuous time version of the derivation in [71] is used. The transmission interval
begins at tB sec and ends at tE sec. These times may be finite or infinite. The received
signal in the ith symbol interval is defined as,
r (t )
ri (t ) =
0
iT ≤ t ≤ (i + 1)T
otherwise
(5.2.2.4)
The signal up to time (i+1)T is the history of ri(t)
r (t ) t B ≤ t < (i + 1)T
Ri (t ) =
otherwise
0
(5.2.2.5)
so the conditional probability can be expanded by repeated application of Bayes theorem,
as
p r (t ) α (r (t ){α }) =
t E T
∏p
i = t B T
ri (t ) Ri ,α
(r (t ) R( ) , {α })
i
i −1
(5.2.2.6)
64
Since the logarithm function is one-to-one and monotonic, choosing the transmitted
sequence with maximum log-likelihood is equivalent to choosing the transmitted
sequence with maximum conditional probability. The log-likelihood is defined as
ln p r (t ) α (r (t ){α }) =
t E T
∑ ln p
i = t B T
ri (t ) Ri ,α
(r (t ) R , {α })
i
(5.2.2.7)
i
where the product has been reduced to a sum. The sequence with the largest loglikelihood function or metric is the maximum likelihood sequence, and it is selected by
the receiver.
The sequence of complex phases, {β}, can reconstruct the symbol
sequence, {α}, so it is sufficient for a receiver to maximize the log-likelihood over {β}
instead, where the revised metric equals
ln p r (t ) β (r (t ){β }) =
t E T
∑ ln p
i = t B T
ri (t ) Rir , β
(r (t ) R , {β })
i
(5.2.2.8)
i
With linear modulations, the information phase, β
k
k −1
until t = kT+ξF, so the partial sum,
∑ ln p
i = t B T
transmitted sequence only up to β
M k − t B
T +1
(k-1).
ri (t ) Ri , β
does not arrive at the receiver
(r (t ) R , {β }),
i
i
depends on the
At the kth symbol interval, there are
distinct metrics, and in general this number grows exponentially with the
transmission duration. Thus choosing the ML sequence involves searching for the best
metric through an ever-expanding tree.
65
The kth log-likelihood, ln pri (t ) Ri , β (rk (t ) Ri , {β }) , at the kth symbol period is labeled the
branch metric. The running total of branch metrics, from t B T to k, is labeled the path
metric. A sequence of transmitted symbols is called a path, since it defines the branches
taken through the tree.
In hardware implementations of Viterbi algorithm, the log-likelihood,
ln pri (t ) Ri , β (rk (t ) Ri , {β }) are usually converted to bit metrics as,
M (ri j | β i j ) = a[log p (ri j | β i j ) + b]
(5.2.2.9)
where a and b are chosen such that the bit metrics are small positive integers that can be
easily manipulated by digital logic circuits.
Therefore, the path metric for {β } is
computed as,
M (r | β) =
k
∑ M (r
i =[ t B / T ]
i
j
| β ij )
(5.2.2.10)
Thus, the code word {β } that maximizes p r (t )| β also maximizes M (r | β) .
"Per-Sequence-Processing" is the reason for the exponentially increasing complexity.
In the general communications problem, the optimal receiver structure has no a priori
knowledge of the channel. However, knowledge of the channel and other parameters is
necessary to compute the branch metrics, and these are progressively estimated. The
estimation is normally data-dependent, since the transmitted signal must be deconvoluted from the received signal before the channel is revealed. Thus the estimated
66
channel and the branch metric depend on the whole symbol sequence history. The
number of branch metrics increases exponentially in time.
Furthermore, the log-likelihood of equation (5.2.2.8) is difficult or impossible to
compute when all random processes are considered. The transmitter carrier oscillator, the
receiver carrier oscillator, the transmitter symbol rate oscillator and the receiver symbol
rate oscillator all introduce random phase noise. The multipath channel has a random
number of paths, with a randomly time-varying path attenuations, delays, and arrival
angles. The receiver’s motion is random. When all the individual pdfs are known, it is
mathematically prohibitive to construct the joint pdf. When the pdfs are not known, it is
impossible.
Thus the MLSE receiver structure is not implementable, except when a simple
statistical model can describe the communication system and either the transmission
interval is short or the tree search simplifies to a trellis search. Trellis searches arise
when no data-dependent quantities need to be computed and the branch metric is a
function of a finite number of code states and transmitted symbols.
One example is the transmission of uncoded data through a time-invariant channel
corrupted by white noise, when the channel, the carrier’s frequency and phase, the
symbol rate oscillator’s frequency and phase, and the beginning of transmission are
completely known [72], [73]. The received pulse shape extends over L symbol periods.
The branch metric is a function of the hypothesis vector, {β (i − L +1) , K β i }. There are only
a finite number, ML, of hypothesis vectors, which can be mapped to the ML branches of
an ML-1 state trellis. At the ith symbol period, the trellis’ state is controlled by the first L-1
symbols, {β (i − L +1) , K β (i −1) }. The last symbol, βi, specifies which of the M branches are
67
selected. There are M paths arriving at each state in the (i+1)th symbol period [72] and
[73] demonstrate that the path metric can be constructed as the sum of independent
branch metrics.
Accordingly, the exhaustive comparison required to compute the
maximum likelihood sequence can be performed iteratively, before the end of
transmission. Since a path’s metric beyond the ith symbol period is independent from its
path metric before the ith symbol period, it is sufficient for each state to retain only the
path with the best metric from the M arriving paths. Thus each symbol period, the MLSE
receiver extends ML-1 surviving paths in ML ways, one for each hypothesis vector.
Immediately, these paths are pruned back to the best ML-1 surviving paths. This is the
Viterbi algorithm [72].
Ideally, the algorithm makes no decisions until the end of
transmission ("ideal Viterbi"); however, the path histories require linearly increasing
storage, and the decisions are delayed too long.
In practice, the decision delay is
truncated to some fixed value.
Herein, we choose a fractionally spaced MLSE for enhanced DMT-ADSL receiver.
It is addressed in the following sub-section. The ideal fractionally spaced MLSE receiver
has the same performance as the conventional MLSE receiver. We derive an equivalent
receiver that does not implement the matched filter, but instead uses a fixed analog filter
that is matched to the pulse shaping filter. A noise-whitening filter having a fixed
structure that does not depend on the unknown channel is used to whiten the T/2-spaced
noise samples. A Viterbi algorithm then operates on the T/2-spaced received sequence at
the output of the noise-whitening filter.
In conclusion, we summarize the Viterbi algorithm implementation processing.
68
The Viterbi decoding process begins with building the accumulated error metric for
some number of received channel symbol pairs, and the history of what states preceded
the states at each time instant t with the smallest accumulated error metric. Once this
information is built up, the Viterbi decoder is ready to recreate the sequence of bits that
were input to the channel. The detail steps are in the following.
Accomplishment steps
(1) Select the state having the smallest accumulated error metric and save the state
number of that state.
(2) Iteratively perform the following step until the beginning of the trellis is reached:
Working backward through the state history table, for the selected state, select a new
state, which is listed in the state history table as being the predecessor to that state. Save
the state number of each selected state. This second step is called traceback.
(3) Work forward through the list of selected states saved in the previous steps. Look up
what best estimated input bit corresponds to a transition from each predecessor state to its
successor state.
5.2.3 T/2-spaced MLSE Receiver
It is known to us that the optimum receiver filter, given the received signal r(t), is a
filter matched to h(t) [72]. In Ref. [72], it showed that a matched filter followed by a
symbol-rate sampler gives sufficient statistic to estimate the transmitted sequence {βl}.
69
In conventional MLSE receiver, the T-spaced samples at the output of the matched filter
must be obtained at the correct timing phase.
The signal at the output of the matched filter is
rMF (t ) = ∑ β l x(t − kT ) + v(t )
(5.2.3.1)
l
where x(t ) = h(t ) ∗ h * (−t ) , and v(t) is the response of the receiver filter to the white noise
signal n(t).
In the receiver of Eq. (5.2.3.1), the signal rMF(t) is sampled with rate 2/T. The overall
channel impulse response and the sampler can be represented by a discrete time T/2spaced transversal filter with coefficients
x ( 2) = ( x−( 22)L , x−( 22)L+1 ,..., x−( 12) , x0( 2 ) , x1( 2) ,..., x2( 2L)−1 , x2( 2L) ) .
(5.2.3.2)
In Eq. (5.2.3.2), we assume that the samples are obtained at the correct timing phase, i.e.
xl( 2 ) = x(lT / 2) and xl( 2 ) = ( x−( 2l ) )* , where (⋅) ( 2) indicates rate 2/T sampling.
The T/2-spaced noise samples at the output of the matched filter have the autocorrelation
1
E[vm* vn ] = N 0 xn( 2−)m
2
(5.2.3.3)
The z-transform of x(2), denoted as X(2)(z), has 4L roots and can be factored as
X ( 2 ) ( z ) = V ( z )V * (1 / z * )
(5.2.3.4)
70
where V(z) and V*(1/z*) are polynomials of degree 2L having conjugate reciprocal roots.
The T/2-spaced correlated noise samples are now whitened using a filter that has a
transfer function 1/V*(1/z*). Once again, V*(1/z*) is chosen such that all its roots are
insider the unit circle. The output of the noise-whitening filter is
2L
y l( 2) = ∑ vi I l(−2i) + η l( 2)
(5.2.3.5)
i =0
where { η l( 2 ) } is a T/2-spaced white Gaussian noise sequence with variance
1
E[| η l( 2) | 2 ] = N 0 and the {vk} are the coefficients of a T/2-spaced discrete-time
2
transversal filter having a transfer function V(z).
The sequence { β ( 2) } is the
corresponding T/2-spaced symbol sequence given by
, l = 0,2,4,...
β
β l( 2) = l / 2
l = 1,3,5,...
0 ,
(5.2.3.6)
Then, we have
2L
L
i =0
i =0
∑ | vi |2 = ∑ | g i |2 = x0( 2) = x0
(5.2.3.7)
Notice that the samples y 2l( 2) and y 2( 2l +) 1 correspond to the lth received baud where
L
y 2( 2l ) = ∑ v 2 i β l −i + η 2( 2l )
i =0
71
L
y 2( 2l +) 1 = ∑ v 2i +1 β l −i + η 2( 2l +)1
(5.2.3.8)
i =0
Note that y 2l( 2) is not necessarily equal to yk due to the fact that different noise-whitening
filter is used to whiten the T/2-spaced noise samples.
Maximum likelihood sequence estimation can be applied to the T/2-spaced received
samples in a very similar to that described in Ref. [72]. The Viterbi decoder searches for
the most likely path in the trellis based on the T/2-spaced received sequence. However,
two samples are fed to the Viterbi decoder for every baud, and a branch metric for each
transition in trellis is evaluated. For each transition into the state sl(+i )1 , the samples y 2l( 2)
and y 2( 2l +) 1 are used by the Viterbi algorithm to evaluate the following branch metric
L
γ l ( s lj → s li+1 ) =| y 2( 2l ) − v 0 β l ( s lj → s li+1 ) + ∑ v 2 m β l − m ( sl( j ) ) 2 |
m =1
L
+ | y 2( 2l +) 1 − v1 β l ( s lj → s li+1 ) + ∑ v 2 m +1 β l − m ( s l( j ) ) 2 |
m =1
(5.2.3.9)
We can easily see that T/2-spaced MLSE receiver has the same number of the states
as the conventional MLSE receiver, but required twice the number of computations.
5.2.4 Analyzing MLSE Receiver Structures
The BER of linear receiver structures is relatively straightforward to compute, since
symbols are processed independently and so their errors are independent too. However,
72
this is not the case for non-linear receiver structures, since consecutive errors are not
usually independent.
The exact BER can be computed as follows. Given a transmitted sequence, the joint
pdf of all hypothesized sequences’ path metrics is calculated.
This can be viewed
geometrically as a density function in a multidimensional space. Each hypothesized
sequence is assigned its own (positive only) axis. All the path metrics at the end of
transmission can be written as a coordinate vector, specifying a point in this
multidimensional space. The value of the density function at this point expresses the
likelihood of computing that set of path metrics.
The space can be divided into decision regions. Points within the same decision
region share the same largest path metric, and so detect the same maximum likelihood
sequence. In fact, a hypothesized sequence’s decision region encloses the points closer to
its axis than any other.
When the ML sequence is detected instead of the transmitted sequence, there are a
number of bit errors, unless the ML sequence is the transmitted sequence. This number,
divided by the total number of bits in the transmitted sequence, weights each region of
the joint pdf. Then the bit error rate due to the transmitted sequence is calculated by
repeatedly integrating over all the weighted joint pdf’s dimensions. The overall BER is
then this quantity, averaged across all transmitted sequences.
Clearly, this exact method has little value since it is difficult to compute. The number
of path metrics is increasing exponentially with the transmission length, so the jointly pdf
gets very complicated and the number of integrations gets very large.
73
Forney’s union bound technique is more straightforward to compute [72].
The
probability that the sequence with the largest path metric that is not the transmitted
sequence can be upper bounded by the probability that any error sequence has a larger
path metric than the transmitted sequence’s path metric. Thus a joint pdf is not needed,
only the pdf of the path metric difference, for all possible transmitted and error
sequences.
Furthermore, there is no need to compute the pdf over the whole transmission
interval. An error sequence follows the same states as the transmitted sequence until the
first error. Errors follow until the two sequences merge at a common state again. This
sequence of errors is called an error event. Any useful communications system has a low
BER, so the error events are normally short compared to the mean time between them.
Accordingly, they can be considered independent, so their probability can be calculated
by only considering the pdf of the path metric difference in the vicinity of the error event.
We point out some notations before our further discussions. The actual transmitted
sequence is denoted by {β
u,v
}. Potential error events are written as {β
u,v,w
}. The
superscript u denotes the length of the error event under consideration. The superscript v
enumerates each distinct transmitted sequence in the vicinity of the length u error event.
Each transmitted sequence can be confused with several others, so the error sequences are
enumerated by a further index, w. When an error occurs, the ML sequence is one of the
error sequences, {β u,v,w}.
The probability that the sequence, {β
u,v
( )
}, is transmitted is labeled by P β u ,v . The
probability that an error sequence has a better metric than the transmitted sequence (the
(
)
pairwise probability of error) is denoted by P β u ,v → β u ,v ,w . In general, the pairwise
74
probability of error depends on the correct symbols in the vicinity of the error event as
well as the actual erroneous symbols. The number of bit errors that arise from the error
(
)
event is written e β u ,v → β u ,v ,w .
An upper bound on the BER can be deduced from a union bound over all error
events. Since this is an infinite sum, it must be truncated. The truncated bound is a
credible upper bound if at least the dominant error events are considered; the bound is
tight if these error events are relatively disjoint.
Thus the BER bound is the union bound of the dominant error events, averaged
across the transmitted sequences in the vicinity of the error event,
(
)(
)(
P β u ,v P β u ,v → β u ,v , w e β u ,v → β u ,v , w
BER < ∑
log 2 M
u ,v , w
The form of an error sequence is {β
u,v,w
)
{
(5.2.4.1)
(
)
}
} = β u ,v exp jθ u ,v ,w + ε u ,v ,w , where the
sequences {ε u,v,w} and {θ u,v,w} specify the particular error sequence, and are constrained
so that {β
u,v,w
} is also an allowed sequence. For an error event extending from the ith to
the (i+u-1)th symbol period, ε ukr,v ,w is zero for k < i and for k > i+u-1. When the data is not
encoded rotationally-invariantly, θ ukr,v ,w is always zero; otherwise θ ukr,v ,w is zero for k < i+u
and it is constant for k ≥ i+u. This remaining phase offset allows the error event to end
when phase lock between transmitter and receiver is lost (cycle slip), since the
rotationally invariant code prevents further bit errors. By constraining {θ u,v,w} to be zero
75
until the end of the error event, the sequences, {ε u,v,w} and {θ u,v,w}, uniquely describe an
error event. Therefore the error sequence can be written as
{Kβ (
u ,v
i−2)
(
) }
, β (ui−,v1) , β iu ,v + ε iu ,v , w , K, β (ui +,vu −1) + ε (i +u −1) , β (ui +,vu ) exp jθ (ui +,vu, w) , K
(5.2.4.2)
5.2.5 Reduced Complexity Receiver Structures
Since the complexity of the MLSE receiver increases exponentially in time and the
necessary log-likelihood cannot easily be computed, reduced complexity systems are
employed. In a basic receiver with linear detection, carrier frequency, carrier phase,
channel estimation, channel equalization and symbol timing are acquired by separate subsystems, as in figure 5.2.5.1. The symbol-rate oscillators at transmitter and receiver are
assumed to be sufficiently precise and stable that the symbol rate is known a priori at the
receiver. The more sophisticated scheme of figure 5.2.5.2 uses a fractionally spaced
equalizer for joint carrier phase recovery, symbol timing estimation and channel
equalization. The carrier recovery structure in an AWGN telephone channel is shown in
Fig. 5.2.5.3.
76
Figure 5.2.5.1: Basic Receiver Structure
Figure 5.2.5.2: Sophisticated Receiver Structure
77
Many successful algorithms exist for each of these tasks, for the channels of our
interest, namely the AWGN channel.
Through, the performance of many of these
algorithms degrades substantially in the fast fading wireless channel, but not in the
telephone wireline DSL channel, which we study herein. Some of these difficulties can
be further studied to motivate the development of new receiver structures, explicitly
designed for the fast channels. Simple received signal models are used for illustrative
purposes, since the same or worse problems appear when more sophisticated signaling
formats and channel models are used.
Figure 5.2.5.3: Carrier Recovery an AWGN Channel
5.2.6 Joint MLSE for DMT-ADSL Receiver
Jointly ML receiver detects both desired ADSL signals as well as crosstalk data
signals, which showed in Fig.5.1.1. This technique has been proved an optimal receiver
78
for communication channels with co-channel interference in many wireless applications
[74], [75], and [76]. The principle of JMLSE on ADSL channel is by selecting over all
main desired channel inputs and all possible crosstalk interference channel inputs, that
finding a particular set of inputs that minimize the distance from the received single
channel output. We notice here that JMLSE across all the channels, which including
main channels and crosstalk channels. This detector is very complex, but theoretically
allows bounding of improvement from multiuser detectors.
The structure of the optimal JMLSE is a straightforward extension of the single
channel MLSE. As in a adjacent pair case, if L1+1 and L2+1 are the channel impulse
response lengths of the two co-channel signals, then the JMLSE selects the ith joint
symbol sequence { xik,1 , xik, 2 } that maximizes the metric
p(r k | x1k,i , x 2k,i ) ≥ p(r k | x1k, j , x 2k, j )
(5.2.6.1)
for all j ≠ i where r k = {r (k ), r (k − 1),..., r (1)} is the received sequence. The JMLSE can
be implemented using a joint Viterbi algorithm.
For the joint demodulation of two cochannel signals, the objective of JMLSE, which
can be illustrated in Fig. 5.2.6.1, is to determine the pair of sequences { xik,1 , x kj, 2 } that
minimizes the sum of squared errors defined by the error sequence eik, j . When the
channel has a finite impulse response (FIR), that Viterbi algorithm (VA) is a practical
way of implementing optimal single-user MLSE, as shown in [64]. The VA for JMLSE
is implemented in a method very similar to that of the single-channel VA. A joint state
79
S ik −1, L = [ sik,1−1, L1 , sik, 2−1, L2 ] is defined by appending the primary ( sik,1−1, L1 ) and secondary
( sik, 2−1, L2 ) states. Therefore, the received metric is equal to
( {
ln p r (t ) S k −1, L r (t ) S
i
k −1, L
i
t E T
}) = ∑
i = t B T
(
{
ln p r (t ) R , S k −1, L ri (t ) Ri , S ik −1, L
i
i
i
})
(5.2.6.2)
Observe that in this case, each joint state at time k-1 can have transition to M2 states at
time k and can be reached by the same number of states from time k-2. The number of
states required to implement the optimal joint VA is M L1 + L2 . For high-order signal
constellation, for example 64-QAM, the computational complexity will be very high on
joint VA.
x
k
i ,1
x 2k, j
rk
Primary Channel
Estimate f1(k)
+
Secondary Channel
Estimate f2(k)
rˆik, j
-
eik, j
+
Fig. 5.2.6.1: Joint ML Sequence Detection between Adjacent Pair
80
JMLSE for the SDSL crosstalk interference on the ADSL channel model are derived
in this thesis. The basic concept is that all the possible transmitted signals of both DMTADSL and SDSL crosstalk are searched and that group of signals that best matches the
received signals over a given symbol period is found. JMLSE is the optimum detector
for a narrowband DMT-ADSL channel with relatively small AWGN. As an example
shown in Fig. 5.2.6.1, for the joint detection of two cochannel signals (desired ADSL and
SDSL crosstalk interference), the objective of JMLSE is to determine the pair of
sequences (ADSL signal and SDSL crosstalk) that minimizes the sum of the squared
error defined by the error likelihood sequence. The squared minimum distance for
JMLSD is used to allow accurate projection of the performance of the ADSL system.
When the channel is a finite impulse response, the joint Viterbi algorithm for JMLSE is
implemented with a method similar to the standard VA, as we have derived in the above.
5.3
Preliminary Performance Studies
In the same binder group, the spectral compatibility study here is a SDSL disturber
NEXT into a T1.413 full rate DMT-ADSL system [15]. The DMT-ADSL system has a
channel coding inside, which makes the SNR gap at a very low level; we have chosen a
gap of 4 dB in our simulation. As an example, assume that both ADSL and SDSL
channels are FIR, with a total channel memory of 2L = 8. The performance of the
optimal M 2 L = 2 8 = 256 states in JMLSE is required to implement a joint VA. That is, a
associated trellis diagram has 256 nodes at each stages. Notice here, that the complexity
if the JMLSE exponentially increases with the length of the channel impulse response.
81
Fig.5.3.1, shows that the bit error rate (BER) v.s. the channel SNR on multiuser and
single-user scenarios for the DMT-ADSL receiver. For the single-user receiver, the SNR
is 21.5 dB with BER of 10-7, and it just needs 18.3 dB with multiuser detection. The
JMLSE performs better than the conventional ADSL receiver does by more than 3 dB in
SNR.
In a DSL system, it is designed conservatively to ensure that a prescribed probability
of errors occurs. The margin of a design at a given performance level, which we use
here, is the amount of additional SNR in excess of the minimum required for a given
code with a gap (= 4 in our example) [15]. The margin can be represented as
γ m arg in =
SNR
Γ ⋅ (2 2b − 1)
,
(5.3.1)
where Γ = ( Γ( Pe , C ) , which is a function of a chosen probability of symbol error Pe and
the line code, C.) is the gap, and b is the achievable bit rate on the ADSL system, which
is,
b=
SNR
1
log 2 (1 +
).
Γ
2
(5.3.2)
It has also been shown that the modified ADSL receiver can outperform the conventional
receiver much better in the margin, as in Fig. 5.3.2.
82
Bit Error Rate for ADSL
-2
10
single-user detector
-4
10
-6
10
BER
-8
10
multiuser via JMLSE
-10
10
-12
10
-14
10
-16
10
17
17.5
18
18.5
19
19.5
20
20.5
21
21.5
22
SNR in dB
Fig.5.3.1: BER for ADSL System with Single-user Detector and JMLSE
83
20
15
JMLSE
Margins in dB
10
5
0
-5
-10
-15
-20
-25
Single-user Detector with SDSL Crosstalk
-30
4
6
8
10
12
14
16
18
ADSL Service Length in kft
Fig.5.3.2: ADSL System with SDSL Crosstalk on Single-user Detector and JMLSE
84
CHAPTER SIX
LOW COMPLEXITY ENHANCEMENT ON ADSL RECEIVER
JMLSE is an “optimal,” but has a high computational complexity for any DSL
channels. This approach estimates the channels of both the desired signal (ADSL signal
here) and the cochannel interference, and then uses a vector-JMLSE equalizer to jointly
demodulate the desired signal and crosstalk. The full search for the minimum distance
requires approximately equal to (number of sub-channel)∗(set size of crosstalk)2
computations. Therefore, the complexity increases exponentially with the sum of the
channel lengths of the desired signal and the crosstalk. We use some simplification
methods to reduce the complexity of JMLSE. The technique we proposed is sort of
having feedback session between the primary and secondary sequence estimators.
Meanwhile, we also review an alternative method, called Tone-Zeroing [77], [81] for
complexity reduction. Our comments with this method have also been discussed after the
reviewing.
6.1
Tone-Zeroing Method
Using the loading algorithm [78], [79] in DMT system together with the studies on
ADSL and SDSL spectral compatibility results, a sub-optimum solution on ADSL
receiver enhancement and modified deployment plan will be proposed.
85
With the property of DMT system, a proposed scheme for the SDSL and the DMTADSL joint detection minimum distance improvement is to zero a few tones in the DMTADSL transmission that correspond to the largest instance of the SDSL crosstalk noise.
After FFT output, the crosstalk detector is used to find out the crosstalk look-up table. It
can be realizes as, the DMT-ADSL receiver decides initially the SDSL crosstalk
sequence by using the tone zeroed for the DMT on corresponding sub-channels. In
another word, by using tone zeroing, it can eliminate various crosstalk error event
sequences from consideration.
Simulation result has shown that it reduces the
complexity and also largely mitigating the crosstalk noise on DMT-ADSL system. For
some case, less than 5 tone zeroed, it can improve more than 10 dB in margin, comparing
to single-user ADSL solution.
Communications theory allows accurate projection of the performance through
the calculation of the squared-minimum distance for the joint ML detector [72], [80] as,
2
d min
=
N
min
( X n ,C i }≠{ X n' ,C 'i }n = 0
∑| H
n=0
n
( X n − X n' ) − (C ni − C ni' ) | 2 ,
(6.6.1)
The expression in Eq.(6.1.1) for jointly detection minimum distance can be increased
in value by zeroing DMT-ADSL signal on tones where the SDSL crosstalk signals are
large. As we have discussed in the previous section, the number of the tone being zeroed
is depended on the coupling DSL data rate, the ADSL transmitting throughput and its
bandwidth. In fact, in very high bit rate DSL (VDSL), just a few zeroed tones lead to a
dramatic improvement in minimum distance [81]. The choice of setting tones to zero
depends on knowledge of where crosstalk signals have the largest energy, but generally
the band of any crosstalk is known, if the various of DSL systems are co-located in a
Telco CO. Loading algorithms in DMT allow for various tones to be easily zeroed and
86
thus unused [59]. For example, in DMT-VDSL, it may be wise to zero tones in the 7 –
7.3 MHz transmission band because of radio emissions [81].
The receiver for this prototype can be derived in Fig.6.1.1 and is considerably
simplified, but slightly more performance loss, with respect to JMLSE. The receiver
decides initially the crosstalk sequence Ci by using only the tones zeroed for DMT-ADSL
system. Upon detecting the crosstalk signal, the proper crosstalk coupling function is
applied and the entire crosstalk interference on the remaining tone is reconstructed and
subtracted, leaving only desired DSL signals and background noise. This is like “EchoCancellation” type method on crosstalk noise suppression at DMT-ADSL receiver. In
another word, the DMT-ADSL system seems “orthogonal” to the crosstalk signals on
these “heavy crosstalk affected tones”. If the data rate of the crosstalk signal is low and
the SNR is excellent, only a few tones are necessary to create a detection error probability
below 10-7.
Y
y
-
FFT
Crosstalk
Detector
DMT
Decoder
+
Ci
Crosstalk
Table
Fig. 6.1.1: Joint ML Crosstalk Signal Canceller with Tone Zeroing
87
We use the same example of the SDSL coupling to the DMT-ADSL channel, in
section 5.3, and assume that the DSL channel is static and constant on crosstalk profile
table.
By zeroing about 20 tones to build up a NEXT cancellation table, we can get
about 10 dB in margin near 18kft, shown in Fig. 6.1.2. Therefore, there is a large
potential for us to delivery a high bit rate, with crosstalk profile table modifications on
receiver.
20
15
JMLSE
Margins in dB
10
5
0
-5
-10
Tone-zeroing
-15
-20
-25
Single-user Detector with SDSL Crosstalk
-30
4
6
8
10
12
14
16
18
ADSL Service Length in kft
Fig. 6.1.2: Margin on DMT-ADSL with Tone-zeroing Crosstalk Noise Cancellation
88
Surely, this method has an advantage of mitigate the NEXT and complexity
reduction (comparing with JMLSE) with asymmetric and symmetric services coexist.
The key issue for the tone zeroing is necessity of accurate modeling of noise (crosstalk),
as described in [77]. Since the feedback section is using some kind of adaptive filter
technique. The adaptive filter coefficient is largely depends on frequency components
with high power. If a frequency band making NEXT noise has small power, it can not be
modeled correctly due to high power frequency component until sufficient number of
coefficient are used [77]. Therefore, the tone zeroing modeling works well for high
frequency power noise component. If so, in a common case of the telephone channel,
many kinds of random noises often occur in any selected frequency band, it is very likely
to make an error decision on the cancellation table and induce error propagation.
As described in the above, tone zeroing technique has a deterministic co-channel
signals profiles assumption (crosstalk table), which may lead error propagation, due to
the random source signal transmissions and various random noises in any selected
frequency band on DMT-ADSL channel.
Therefore, very frequently crosstalk table
tracking and updating are needed in order to make accuracy crosstalk signals estimation.
This processing makes the receiver frequently adaptive to random channels and may
more complexes to realize in practical loops. But, we still believe that tone zeroing is a
good technique on reducing computational complexity to achieve a better throughput. It
performs a better solution for less complicated loops, especially in DMT version DSL
solutions.
The simplified technique that we use in this thesis is a multi-stage joint MLSE for
ADSL receiver.
This method is a sub-optimal to the ideal joint MLSE estimator,
89
provides an excellent way to trade a sub-optimal performance for reducing complexity.
This approach can apply to both DMT and non-DMT versions of DSL solutions in the
same manner.
6.2
Low Complexity Joint MLSE
6.2.1 Multi-stage JVA
The structure of the Joint MLSE, as derived in the previous section is a
straightforward extension of the single channel VA. The drawback for Joint MLSE is the
large computational complexity, due to the exponential increasing on the transition states.
In the Fig.5.2.5.1, as an example of only one co-channel interference case, for a M-ary
symbol alphabet, the JVA requires M L1 + L2 states, with M2 transition leaving (and
entering) every state.
In order to reduce the complexity of JMLSE (or JVA), we introduce a multi-stage
JVA method. Using the same example in Fig.5.2.5.1, we can describe a two-stage
JMLSE scheme in Fig.6.2.1.1, which can be extended, to N stages on N co-channel
interference case, without loss generality. As a first step, the complexity reduction can be
attempted by employing a two-stage JVA having only M L1 + M L2
states by
implementing a successive interference cancellation approach [52]. For N co-channel
interferences case, this computational complexity is reduced largely comparison with
JMLSE, and its ratio can be derived as
R=
M L1 + M L2 + ... + M LN
M L1 + L2 +...+ LN
(6.2.1.1)
90
As an example, assumption on all equal tap length, L, the Eq. (5.2.1) can be further
simplified as
R=
N ⋅ML
= N ⋅ M L (1− N )
N ⋅L
M
(6.2.1.2)
In Eq. (6.2.1.2), it is always true to have N > 1 in any telephone binders, thus, L(1-N) <0.
It is obvious to us that R is always (much) smaller than one. Therefore, multi-stage joint
MLSE reduces the computational complexity largely comparison with ideal joint MLSE.
This multi-stage VA technique is very similar to conventional VA receiver (section
5.2.2), instead having multi-stage inputs and outputs. The primary (strong) signal r1(k) is
estimated using low delay decisions from a single-channel VA, and r (k ) − rˆ1 (k ) is
forwarded to the second VA section to estimate the co-channel signal. This structure that
we use it here, as a category of JVA, through it likes a feed-forward multi-stage single
channel VA detectors.
We name this as multi-stage JVA (MS-JVA).
The major
advantage for this structure is largely reducing the complexity on optimal JVA as shown
in Fig. 6.2.1.1. Its computational complexity is in a similar range of a single-channel
VA, with just a scale-increasing factor by N (N is the total number of UTPs in a binder,
assuming the same length, L, for all the channels.).
91
dˆ1 ( k − L1 )
r(k)
dˆ2 ( k − L2 )
+ r ( k ) − rˆ (k )
+
_
VA
1
L1
M states
dˆ1 ( k )
1
VA
M L2 states
L1
Fig. 6.2.1.1: Two-stage JVA (without Feedback Section)
The trade-off on mitigation of the crosstalk with this method is relatively poor
performance comparing to the optimal JVA at a low signal-to-crosstalk ratios (SCRs)
channel condition. The reason for this is while the secondary section receives a relatively
CCI free signal sequence, the primary section is sensitive to the un-cancelled secondary
signal.
In practice, a viable reduced-complexity single-user MLSE receiver can retain fewer
survivor sequences, one for each combination of the latest S ≤ W hypothesized symbols.
The choice for S is a trade-off between complexity and performance [82]. Fig. 6.2.1.2
92
shows the single-user MLSE receiver computational flow structure for unknown channels
when the signal’s second order statistics are known.
93
Fig. 6.2.1.2: Single-user MLSE Computational flow structure
94
dˆ1 ( k − L1 )
s1 (k )
+
r(k)
+
_
VA
M L1 states
k ,L
dˆ1 1 ( k )
dˆ2 ( k − L2 )
+
s (k )
VA
+ 2
M states
_
ˆ
(
)
r
k
k ,L
fˆ1 ( k − 1) 1
dˆ2 2 (k)
L2
rˆ2 (k + 1)
fˆ2 ( k )
Fig. 6.2.2.1: Two-stage JVA (with Feedback Section)
6.2.2 Multi-stage JVA with Feedback
Achieving the better performance and complexity reduction on the ADSL receiver,
we introduce a multi-stage JVA with feedback section (w/FB), shown in Fig. 6.2.2.1. A
similar structure has been used by [83] on a two-stage JMAPSD detector. Hence, we use
multi-stage JVA, instead of JMAPS. The reason is that it is preferable using JVA due to
tolerate longer decoding delays, because the complexity of JMAPSD grows exponentially
with the decoding delay, while it is essentially linear for the [83]. This characteristic of
JVA fits the need of the ADSL receiver, which widely used in real-time multimedia
applications. As shown in Fig. 6.2.2.1, where at time k, the low delay causal decisions
from the secondary, namely {dˆ 2,i (k − 1),..., dˆ 2,i (k − L2 )} , are used to cancel a portion of
95
the cochannel signal r2(k) from the input to the primary VA section. This structure just
has an additional L2 tap filter on computational complexity comparing to the MS-JVA.
The performance on MS-JVA-w/FB is considerably better than MS-JVA, as the MSJVA-w/FB can cancel the secondary energy corresponding to the previous estimated
symbol dˆ 2 ( k − j ) , where j = 1,2,…,L2.
A suboptimal multi-stage JMLSE rule to make a decision on the (k-L)th symbol, at
time k, is dˆ ( k − L) = d n (k − L) , where
dˆ k , L = d nk ,L ,
n = Arg[max p( d nk ,L | r k )]
(6.2.2.1)
i
In each single stage channel, the MLSE metrics are updated independently like derived in
section (5.2.2). It is shown in Eq. (5.2.2.8)
ln p r (t ) β (r (t ){β }) =
t E T
∑ ln p
i = t B T
ri (t ) Ri −1 , β
(r (t ) R( ) , {β })
i
i −1
(6.2.2.2)
In a similar to [83], the overall two-stage JVA is summarized in the following two
steps. This algorithm can be easily applied to N stage JVA with a similar extension.
96
Two-stage JVA Algorithm
Step 1: 1st JVA stage
(1): Determine 1st. input s1 (k ) = r (k ) − rˆ 2 (k )
(2): Update 1st JVA metrics with Eq. (6.2.2.2)
(3): Compute 1st decisions with Eq. (6.2.2.1)
(4): Compute total estimate of 1st. signal
L1
rˆ1 ( k + 1) = ∑ f1,l ( k − 1)dˆ1,max ( k − l )
l =0
Step 2: 2nd. JVA stage
(1): Determine 2nd input s1 (k ) = r (k ) − rˆ 2 (k )
(2): Update 2nd JVA metrics with Eq. (6.2.2.2)
(3): Compute 2nd decisions with Eq. (6.2.2.1)
(4): Compute total estimate of 2nd signal
L2
rˆ2 ( k + 1) = ∑ f 2,l ( k )dˆ 2, max ( k + 1 − l )
l =0
Step 3: Return to step 1 for a new sequence.
97
This MS-JVA-W/FB employs only an additional L2 tap filter in comparison with MSJVA. For large ADSL channel sequences, it has the same computational complexity as
the MS-JVA. Our studies have shown that the MS-JVA-w/FB has considerably better
performance than the MS-JVA.
Further more, this enhancement and reasonable
complexity are exactly suitable for our proposed DMT-ADSL receiver with crosstalk
environments, which normally above 10 dB in SCR [15].
Therefore, we choose MS-JVA-W/FB for the enhanced DMT-ADSL receiver.
Moreover, a T/2-spaced MLSE algorithm is used for this proposed receiver. In the next
sub-section, a practical T/2-spaced MLSE receiver is described, which has a great
advantage than conventional MLSE receiver for unknown channels.
6.2.3 Practical Enhanced ADSL Receiver
In Fig. 6.2.3.1, it shows the block diagram of a practical ADSL channel system.
n(t)
{β l }
Channel
c(t)
g(t)
+
g*(t)
Sampling
rate 2/T
{βˆ l }
T/2-spaced
MLSE
T/2-spaced
noise-whitening
filter
Fig. 6.2.3.1: Practical ADSL Channel System
98
Since rate 2/T sampling satisfies the sampling theorem, the two systems can be
represented by the T/2-spaced discrete-time signals. Let G(2)(z), C(2)(z) and H(2)(z) be the
z-transform of the T/2-spaced discrete-time signals that correspond to g(t), c(t) and h(t),
respectively, where g(t) is the shaping function, c(t) is the impulse response of the
telephone channel function, and h(t ) = g (t ) ∗ c(t ) . The z-transform of the autocorrelation
function of the noise samples at the output of the receiver filter g * (t ) = N 0 X g( 2) ( z ) ,
where X g( 2 ) ( z ) = g ( 2) ( z )( g ( 2) (1 / z * )) * . Using the factorization
X g( 2 ) ( z ) = V g( 2 ) ( z )(V g( 2) (1 / z * )) * ,
(6.2.3.1)
the noise can be whitened by using a filter with transfer function (V g( 2) (1 / z * )) * . The ztransform of the overall response at the output of the noise-whitening filter is
Veq( 2) ( z ) = G ( 2) ( z )C ( 2 ) ( z )(G ( 2) (1 / z * )) * /(V g( 2) (1 / z * )) *
= C ( 2) ( z )V g( 2) ( z ) .
(6.2.3.2)
On the other hand, we have
H ( 2 ) ( z ) = G ( 2 ) ( z )C ( 2) ( z )
(6.2.3.4)
and
99
X ( 2) ( z ) = G ( 2 ) ( z )(G ( 2) (1 / z * )) * C ( 2) ( z )(C ( 2 ) (1 / z * )) *
(6.2.3.5)
C ( 2) ( z )(C ( 2) (1 / z * )) * = Vc( 2) ( z )(Vc( 2) (1 / z * )) *
(6.2.3.6)
Let
be a factorization of C(2)(z)(C(2)(1/z*))* such that (Vc( 2) (1 / z * )) * has a minimum phase.
Using Eq. (6.2.3.1), Eq. (6.2.3.5) and Eq. (6.2.3.6), we have
X ( 2 ) ( z ) = V g( 2 ) ( z )(V g( 2) (1 / z * )) * Vc( 2) ( z )(Vc( 2) (1 / z * )) * .
(6.2.3.7)
The transfer function of the noise-whitening filter must be chosen as
1 /((V g( 2) (1 / z * )) * (Vc( 2) (1 / z * )) * ) . Therefore, the overall transfer function at the output of
the noise whitening filter, is equality to conventional one, V(z), which is given by
V ( z ) = V g( 2) ( z )Vc( 2 ) ( z ) .
(6.2.3.8)
The equivalent response Veq( 2) ( z ) in Eq. (6.2.3.2) has the same amplitude as V(z), but
different phase. Also,
Veq( 2) ( z )(Veq( 2) (1 / z * )) * = X ( 2 ) ( z )
(6.2.3.9)
100
Therefore, the distance between sequences of channel outputs using the system in
T/2-spaced MLSE channel is the same as in the conventional MLSE channel, that
implements the matched filter, and they have the same performance. The advantage of
the T/2-spaced system is that the noise-whitening filter does not depend on the unknown
channel and has a fixed structure. The unknown overall channel can be estimated after
the noise-whitening filter and the MS-JVA-W/FB is then implemented using the
combined metric in Eq. (5.2.3.9). Although the number of computational needed in this
practical receiver is about twice as the conventional receiver [72], the latter one cannot be
implemented for unknown channels. Moreover, for unknown channels the conventional
MLSE implemented with a matched filter has poor performance when the matched filter
is implemented using an inaccurate channel estimate.
6.2.4
Example and Comparison
We consider adjacent pair wire line co-channel interference as an example. Assume
that the channel has PAM modulation with desired channel memory of two symbols. The
trellis for VA in the desired channel section has two parallel transitions. The computer
simulation performances on the symbol error rate vs. channel signal-to-noise ratio for
ideal JMLSE, multi-stage JMLSE with feedback section and without feedback section
have been studied. As we mentioned in section 6.2.2, the SCR is normally above 10dB in
most of the DSL channels, we have chosen SCR = 10 dB in our simulation studies. The
results are shown in Fig. 6.2.4.1. From Fig. 6.2.4.1, we can see that MS-JMSE W/FB
outperform MS-JMLS WO/FB significantly when SCR is 10 dB or better. This approach
is a sub-optimal solution to ideal JMLSE with slightly degradation, but has about 90%
101
saving in computational complexity.
Therefore, multi-stage JMLSE with feedback
section is our solution for ADSL receiver enhancement.
102
0
10
-1
Symbol Error Rate
10
-2
10
+ : MS-JMLSE-WO/FB
* : MS-JMLSE-W/FB
-3
10
o : Ideal-JMLSE
-4
10
4
6
8
10
12
14
16
18
20
22
Signal-to-Noise Ratio
Fig. 6.2.4.1: Desired Channel Performance with Three Methods
103
CHAPTER SEVEN
PERFORMANCE EVALUATIONS AND SIMULATION RESULTS ON
ENHANCED ADSL RECEIVER
In current DMT-ADSL receiver, channel noise is lumped together and accommodated
by reach and rate restrictions as well as margin limits. No attempt is currently made to
take advantage of the structure of the interferers. This “single user” approach ignores the
underlying sources of noise in environments where spectral interference occurs.
However, channel capacity is inherently higher in communications channels that employ
multiuser receivers to distinguish and address discrete noise sources to effect higher
performance (e.g., rates, reach and margin), as derived in section 3.2. JMLSE technique
described here takes advantage of such principles to compensate crosstalk noise and
enable higher loop plant utilization.
The multiuser detector is completely compatible with existing DMT-ADSL standards
and is designed to be integrated into commercial DMT-ADSL transceiver chipsets with
modest computational impact. The multiuser detector technique can be inherently singleended and relies on input available in the DMT-ADSL network.
104
7.1
Test Environment
The ADSL noise compensator has been tested on simulated DSL disturbers, with a
significant margin gain demonstrated. For the purposes of this thesis, examples are
shown which illustrate this impact when the compensator is implemented in a DMTADSL CPE receiver, subject to foreign NEXT (major threat, hence from the SDSL
services and some other DSL services) in realistic deployment scenarios.
7.2
Test Channel Conditions
The ADSL receiver crosstalk compensation is single-ended, which is present at the
receive side of the ADSL link. The victim DSL service is DMT-ADSL. Disturber that
we investigate here is 2B1Q SDSL NEXT, HDSL NEXT and ISDN NEXT. Because in
the frequency band between 25 to 138 KHz, HDSL and/or ISDN services result in similar
and even slightly higher NEXT PSD level than ADSL. Therefore, in our crosstalk
simulation study, though we focus mainly on SDSL NEXT, but also with other types of
the above services. Moreover, considering the UTP binder segregation in real world is
not feasible [84], we will expect that all interfering sources to be in different types of
services. Meanwhile, the ADSL self-NEXT will not be considered as a disturber due to
the practical condition that ADSL is installed almost exclusively in FDM mode.
SNR improvement through recovery of margin depends on the particular loop
characteristics and disturber scenario. For this reason, the JMLSE receiver results are
stated in terms of margin recovery for specific scenarios, each of which include a main
channel specification, set of co-channel transfer functions, and a selected disturber set.
Three cases are shown that represent impaired DMT-ADSL loops, which are chosen from
105
G996.1 [85]. For each of these cases, the expected multiuser DMT-ADSL receivers’
performance improvement is stated in terms of margin recovery (SNR gain), bit rate
improvement, and loop reach.
For all scenarios described in this thesis, a UTP background AWGN level of –140
dBm/Hz is assumed.
7.3
Loop Characteristics
We choose three representative ADSL test loops for our simulation studies, which are
studied in [85]. They are shown in Fig. 7.3.1.
ATU -C
ATU-
Test Loop
#2
ATU-C
ATU -C
Test Loop
#3
ATU -C
ATU-C
26 AWG
26 AWG
26 AWG
Test Loop
#1
1500 ft
1500 ft
1500 ft
3000 ft
6000 ft
1500 ft
26 AWG
26 AWG
26 AWG
1500 ft
1500 ft
26 AWG
26 AWG
9000 ft
2000 ft 500 ft
500 ft
26 AWG
24 AWG
24 AWG
18000 ft
26 AWG
24 AWG
ATU -R
ATU -R
ATU -R
Fig. 7.3.1: Testing Loops
106
7.4
Capacity Improvement
To estimate capacity improvement (achievable transmission data rates) with enhanced
multiuser detection DMT-ADSL receiver, the margin is held at 6 dB and the bit loading
algorithm uses the improvement in SNR to calculate the maximum downstream ADSL
capacity.
7.5
Reach Improvement
To estimate reach improvement with enhanced multiuser detection DMT-ADSL
receiver, the margin is held at 6 dB, and the loop is extended until the simulation results
in a bit rate equivalent to the impaired bit rate.
7.6
Disturber Scenarios
The main focus on the spectrum management standard of this thesis limits the
maximum SDSL bit rate on a given loop length to assure spectral compatibility with
ADSL. As shown in Fig. 2.2.2.2, limit based on maximum SDSL bit rates is that
crosstalk from lower bit rates is always less damaging than crosstalk from higher bit
rates. This is not always obvious to all the practical cases, especially considering that
there may be mixed crosstalk from a number of lower bit rates, such as lower rate SDSL.
Our simulation results below show how the random SDSL bit rates and lower rate DSL
services implicit to downstream ANSI DMT-ADSL throughput.
To start, simulations run with randomly generated SDSL bit rates uniformly
distributed between 160 kbps and 2320 kbps. Each simulation has three clumps of SDSL
disturbers, and each clump has the same randomly generated bit rate. The total number of
107
SDSL disturbers is uniformly distributed, and the number of disturbers in each SDSL is
uniformly distributed with mean equal to one-third of the total number of SDSL
disturbers. Scatter plot of downstream ANSI DMT-ADSL bit rates on a 9 kft 26 AWG
loop as a function of the total number of SDSL disturbers with SDSL disturbers having
uncontrolled random bit-rates are presented in Fig. 7.6.1 [86].
Downstream ADSL bit ra
(kbps)
10000
9000
8000
7000
6000
5000
4000
3000
2000
1000
0
0
10
20
30
Total Number of SDSL NEXT
40
50
Fig. 7.6.1: Scatter Plot of Downstream ADSL Throughout with Mixed SDSL Crosstalk
108
Fig. 7.6.1 shows little correlation between random SDSL bit rate disturber numbers for
downstream ANSI ADSL bit rates. Our conclusion is that controlling the gross number
of SDSL disturbers has little effect on ADSL performance, without controlling the SDSL
bit rates, which is not practical in real world at all. The real solution is to modify the
DMT-ADSL receiver to mitigate crosstalk effect on the ADSL throughout.
Tables 7.6.1 list the disturber sets used in the simulation. The disturber scenarios
illustrate interference situations that might result from a predominately residential 25
pairs UTP binder that has just a few installed symmetric services to businesses. They
reflect a situation in which there is a mix of symmetric services installed prior to the
Spectral Management Standard [87], which do not conform to its’ deployment limitations
as well as Symmetric services that do conform to the Spectral Management Standard.
Table 7.6.1 Disturber Scenarios
Disturber
Pairs
Test Loop #1
Test Loop #2
Test Loop #3
3 SDSL
1 HDSL
2 SDSL
1 ISDN
18 DMT-ADSL
1.0 Mbps
784 Kbps
720 Kbps
160 Kbps
Fully Loaded
1.0 Mbps
784 Kbps
656 Kbps
160 Kbps
Fully Loaded
784 Kbps
784 Kbps
416 Kbps
160 Kbps
Fully Loaded
109
7.7
Co-Channel Transfer Functions
The NEXT co-channel transfer functions have been measured as the way in section
4.1 on real cable. These measured co-channels are similar to those found in the spectral
management draft standard [87]. These co-channels are used to simulate the coupling
between the DMT-ADSL and other DSL distributors.
7.8
Simulation Results
In the test simulation, each interference noise source in the disturber scenario (Table
7.6.1) is randomly assigned as cochannel input. Results are averaged due to the statistical
nature of the binder assignments.
The standard deviation of the improvements is
maintained and a representative case below shows the 1σ limits of the compensation
margin improvement.
It is useful to look at multiuser detection improvements from the limiting case of
when the disturbers are installed to the same equivalent working length in an intact
binder. In this case, all disturbers are assigned similar co-channel transfer functions that
represent approximate co-location of the disturbers and DMT victim.
The results of the simulation test of the compensator for DMT-ADSL CPE receiver
are shown below in Fig. 7.8.1 through Fig. 7.8.3. In these figures, we compare three
different solutions, which are conventional (currently deployed), ideal JMLSE, and multistage JMLSE with feedback section DMT-ADSL receiver.
110
Achievable Downstream Data Rate in Mbps
4
square : ideal JMLSE
x : multi-stage JMLSE
3.5
o : conventional ADSL receiver
3
2.5
2
1.5
1
0.5
0
9
10
11
12
13
14
15
16
17
18
ADSL Service Length in kft
Fig. 7.8.1: Rate-reach curves for Test Loop #1
111
Achievable Downstream Data Rate in Mbps
3.5
square : ideal JMLSE
3
x : multi-stage JMLSE
2.5
o : conventional ADSL receiver
2
1.5
1
0.5
0
9
10
11
12
13
14
15
16
17
18
ADSL Service Length in kft
Fig. 7.8.2: Rate-reach curves Test Loop #2
112
Achievable Downstream Data Rate in Mbps
10
9
square : ideal JMLSE
8
x : multi-stage JMLSE
7
o : conventional ADSL receiver
6
5
4
extension
prediction
3
2
1
0
4
6
8
10
12
14
16
18
20
ADSL Service Length in kft
Fig. 7.8.3: Rate-reach curves for Test Loop #3
113
Fig. 7.8.1 through Fig. 7.8.3 shows how the margin improvement enabled by the
enhanced multiuser ADSL receiver. This modification can be used for either increasing
the capacity, which moving achievable data rate vertically from the conventional rate to
the great improved rate, or deployment limits, which moving reach limit horizontally
from the conventional deployment rage to the further extension limits.
Furthermore, Fig. 5.1.1 show that when services strictly adhere to spectral
management deployment limits, crosstalk from the other DSL services in the channel can
affect the DMT downstream rate at points significantly removed from the coupling. In
these cases, as well as those that represent legacy disturber scenarios that may exist in the
loop plant prior to the spectrum management standard [15].
The multiuser ADSL
receiver improvement in bit rate and loop reach extensions, and represents an important
performance enhancement to the DMT type DSL receivers.
114
CHAPTER EIGHT
CONCULUSIONS
This thesis suggests that the traditional approach to DSL cochannel interference
modeling and receiver design may dramatically under-project achievable capacity level in
DMT-ADSL transmission systems. With the increasing importance of spectral
compatibility and a difficulty in surmounting the multiple problems created by the
mixture of different DSL services, the principle of multiuser detection has been used to
relieve substantially the problems created by crosstalk in ADSL system.
The use of this enhanced multiuser detection technique has a wide array of potential
benefits for spectral management and deployment in all DSL services, where interference
exists due to legacy services, and newly deployed services with heavy crosstalk noise.
This approach is a core method on improvements of either increasing transmission data
rate, or extending deployment areas, or compensating in poor BER DSL channels, based
on different requirements. In our studies, it has shown that this modified ADSL receiver
is able to achieve and sustain significantly higher data rates. Also, this enhancement on
the receivers having ability to reject the effect of interferers, the length limit on
potentially interfering services, such as SDSL services, may be relaxed without harm to
victim services (like ADSL).
115
Our simulation results show that higher rate services can be deployable further out in
the loop plant. Therefore, this approach on the ADSL receiver gives degrees of freedom,
and great overall loop plant utilization, while preserving spectral compatibility.
Finally, our enhanced ADSL system also has acceptable computational complexity
for current VLSI capability.
116
CHAPTER NINE
RECOMMENDATIONS
Without loss generality, using the multiuser detection receiver technique described
herein to mitigate the effects of crosstalk can be applicable across all existing and
contemplated DSL transceivers, including DMT/QAM/CAP ADSL, HSDL, SDSL and
future VDSL.
The benefits vary and are significant. Further more, the techniques
contained herein are extensible to fiber and wireless.
Studies of the twisted-pair channel (TPC) model and conventional crosstalk coupling
function [55], [88] show the characteristic of the TPC attenuation and NEXT function in
Fig.9.1. It is explicit that for high data rate downstream ADSL transmission between 6 to
14 kft, JMLSD is needed to suppress the SDSL NEXT interference. Other complexity
reduction methods for joint VA decoding will be further studied for this enhanced ADSL
receiver. As it reaches further, such as above 14 kft, the NEXT will be very large and
easy to detect, and then it will be easy to cancel them. Based on the ADSL downstream
data rate threshold or noise margin, a switched dual-mode of single-user and multiuser
DMT-ADSL receiver could be used for simplicity and less latency with QoS of the
transmission rates.
117
0
-10
-20
analytic channel model, in Eq.(2)
Gain in dB
-30
-40
-50
squared crosstalk coupling function
-60
-70
-80
-90
0
500
1000
1500
Frequency in kHz
Fig.9.1: Channel Attenuation and NEXT Characteristic
118
REFERENCES
[1] M. L. Honig, P. Crespo and K. Striglitz, “Suppression of Near- and Far- End
Crosstalk by Linear Pre- and Post- Filter,” IEEE J. Select. Areas in Comm., pp. 614-629,
April 1992.
[2] S. Cox and P. Adams, “An Analysis of Digital Transmission Techniques for a Local
Network,” Brit. Telecommun. Technol. J., vol. 3, no.3, July 1985.
[3] J. W. Lechleider, “Broad Signal Constraints for Management of the Spectrum in
Telephone Loop Cables,” IEEE Trans. Commun., vol. COM-34, July 1986.
[4] J. Campbell, A. Gibbs and B. Smith, “The Cyclostaionary Nature of Crosstalk
Interference from Digital Signals in Multipair Cable – Part I: Fundamentals,” IEEE
Trans. Commun., vol. COM-31, May 1983.
[5] , “The Cyclostaionary Nature of Crosstalk Interference from Digital Signals in
Multipair Cable – Part II: Application and Further Results,” IEEE Trans. Commun., vol.
31, May 1983.
[6] K. J. Kerpez, “Near End Crosstalk is Almost Gaussian,” IEEE Transactions on
Communications, Vol. 41, No. 5, May 1993.
[7] “Compromise for ADSL Performance Classed,” T1E1.4/2000-045R2, Telcordia
Technologies, February 2000.
[8] C. Valenti, “Regarding the Spectral Compatibility of 2B1Q SDSL,” ANSI
Contribution T1E1.4/99-261, Telcordia Technologies, June 7, 1999.
119
[9] “Network and Customer Installation Interfaces, Asymmetric Digital Subscriber Line
(ADSL) Metallic Interface,” T1.413-1998 (issue 2), ANSI.
[10] “ITU-T Draft G.992.2, Splitterless Asymmetric Digital Subscriber Line
Transceivers,” ITU-T, Draft Recommendation G.992.2, February 4, 1999.
[11] G. Young, K. T. Forster and J. W. Cook, “Broadband Multimedia Delivery over
Copper,” BT Tech. J., vol. 13, no. 4, Oct. 1995.
[12] J. Cioffi, “ Mitigation of DSL Crosstalk via Multiuser Detection and CDMA,”
ANSI, T1E1.4/98-253, August 1998.
[13] J. H. Unger, “Near-End Crosstalk Model for Line Code Studies,” ECSA
Contribution, T1D1.3/85-244, November 12, 1985.
[14] K. W. Cheong, J. M. Cioffi, “Coexistence of 1 Mbps HPNA and DMT VDSL via
Multiuser Detection and Code Division Multiplexing,” T1E1.4/99-120, March 8, 1999.
[15] Asymmetric Digital Subscriber Line (ADSL) Metallic Interface, ANSI Standard
T.413-1995, ANSI, New York.
[16] J. H. W. Unger, “ NEXT Model for Line Code Studies,” Bellcore T1D1.3/85-244,
November 1985.
[17] C. Valenti, “Cable Crosstalk Parameters and Models”, Bellcore T1E1.4/9730September 1997.
[18] G. Zimmerman, “Spectral Compatibility of 260, 384 and 768 kbps 2B1Q DSLs,”
T1E1.4/96-226, July 1996.
[19] K. J. Kerpez, “Variable Bit-Rate 2B1Q Spectral Compatibility within CSA Range,”
T1E1.4/98-029, March 1998.
120
[20] K. J. Kerpez, “ The Spectral Compatibility of SDSL with T1.413 ADSL and
G.992.2-G.lite” T1E1.4/99-031, February 1999.
[21] Qi Wang, “The Spectral Compatibility of High Rate 2B1Q SDSL with T1.413
ADSL and G.992.2-G.lite” T1E1.4/99-097, March 1999.
[22] M. Steenstra, J. Yang, and M. Rushing, “Specifications for Sub-rate HDSL,”
T1E1.4/98-343, November 30, 1998.
[23] G. Zimmerman, “Spectral Compatibility of 260, 384, and 768 2B1Q DSLs,”
T1E1.4/96-226, July 1996.
[24] K. J. Kerpez, “Variable Bit-Rate 2B1Q Spectral Compatibity within CSA Range,”
T1E1.4/98-029, March 4, 1998.
[25] Liang C. Chu, and Martin A. Brooke, “An enhancement study on the SDSL
upstream receiver,” Proc. on IEEE International Symposium on Circuits and Systems,
Volume: 4 , 6-9 May 2001, pp.: 442 –445.
[26] Liang C. Chu, and Martin A. Brooke, “Mitigation of Crosstalk on The SDSL
Upstream Transmission With Vector Equalization,” Proc. on IEEE International
Conference on Communications, June 11-14, 2001.
[27] A. Peled and A. Ruiz, “Frequency Domain Data Transmission Using Reduces
Computational Complexity Algorithms,” International Conference on Acoustics, Speech,
and Signal Processing, April 1980, pp. 964-967.
[28] A. Ruiz, J. M. Cioffi, and S. Kasturia, “Discrete Multiple Tone Modulation with
Coset
Coding
for
the
Spectrally Shaped
Channel,”
IEEE
Transactions
on
Communications, 1991.
121
[29] A. Ruiz and J. M. Cioffi, “A Frequency-Domain Approach to Combined Sprectral
Shaping and Coding,” ICC’87, June 1987, pp. 1711-1715.
[30] P. S. Chow, J. Tu, and J. M. Cioffi, “Performance Evaluation of a Multichannel
Transceiver System for ADSL and VHDSL Services,” IEEE Journal on Selected Area in
Communications, August 1991.
[31] A. Ruiz, J. Cioffi, and S. Kasturia, “Discrete Multiple Tone Modulation with Coset
Coding for the Spectrally Shaped Channel,” IEEE Transactions on Communications, Vol.
40, No. 6, June 1992.
[32] R. G. Gallager, “Information Theory and Reliable Communication,” Wiley, New
York, NY, 1968.
[33] John Bingham, “Multicarrier Modulation for Data Transmission: an idea of whose
time has come,” IEEE Communication Magazine, vol. 28, no. 5, pp. 5-14, 1990.
[34] J. C. Tu and J. Cioffi, “A Loading Algorithm for the Concatenation of Coset Codes
with Multichannel Modulation Methods,” Global Telecommunications Conference, pp.
1183-1187, December 1990.
[35] T. N. Zogakis, J. T. Aslanis Jr., and J. Cioffi, “Analysis of a Concatenated Coding
Scheme for a Discrete Multitone Modulation System,” IEEE MILCOM, vol. 2 pp. 433437, 1994.
[36] Ranjan V. Sonalker, Richard R. Shively, “An Efficient Bit-Loading Algorithm for
DMT Applications,” IEEE Communications Letters, Vol. 4, No. 3, March 2000.
[37] J. M. Cioffi, “A Multicarrier Primer,” Stanford University.
[38] P. S. Chow, “Bandwidth Optimized Digital Transmission Techniques for Spectrally
Shaped Channels with Impulse Noise,” Ph.D. thesis, Stanford University, CA May 1993.
122
[39] R. F. Fisher and J. B. Huber, “A New Loading Algorithm for Discrete Multitone
Transmission,” Proc. IEEE/Globecom, London, UK, 1996.
[40] J. C. Tu, “ Theory, Design and Application of Multi-channel Modulation for Digital
Communications,” Ph.D. thesis, Stanford University, CA, June 1991.
[41] J. Cioffi, “A Multicarrier Primer,” ANSI Contribution T1E1.4/91-157, November
1991.
[42] John Bingham, ADSL, VDSL and Multicarrier Modulation, John Wiley and Son,
Inc. 2000.
[43] ITU-T g.992.2 Standard, “Digital Transmission System for ADSL Transmission on
Metallic Local Loops with Provisioning to Facilitate Installation and Operation in
Conjunction with Other Services.”
[44] S. Verdu, “ Adaptive Multiuser Detection,” from Coder Division Multiple Access
Systems, Kluwer, 1995, pp. 97-116.
[45] J. W. Cook, “Wideband Impulsive Noise Survey of the access network,” BT
Technol. Journ., 11(3):155-162, July 1993.
[46] I. Kalet, “The Multitone Channel,” IEEE Trans. Commun., pp. 119-124, Feb. 1989.
[47] W. D. Reeve, “Subscriber Loop Signaling and Transmission Handbook,” IEEE
Press, New York, 1995.
[48] Bell Laboratories Staff, “Transmission Systems for Communication,” ATT, New
York.
[49] F. P. Duffy and T. W. Thatcher, Jr., “1969-70 Connection Survey: Analog
Transmission Performance on the Switched Telecommunications Network,” Bell Sys.
Tech. J., vol. 50, 1971, pp. 1311-1347.
123
[50] M. B. Carey, H. T. Chen, A. Descloux, J. F. Ingle, and K. I. Park, “1982-83 End
Office Connection Study: Analog Voice and Voiceband Data Transmission Performance
Characterization of the Public Switched Network,” ATT Bell Lab. Tech. J., vol. 63, 1984,
pp. 2059-2119.
[51] J. Cioffi, Electrical Engineering Class Notes at Stanford University, Fall 2000.
[52] S. Verdu, “Multiuser Detection,” Cambridge Press, 1998.
[53] J. M. Cioffi, K. W. Cheong, “Coexistence of 2- 10 Mbps Home-Phone LANS and
DMT VDSL via Multiuser Detection,” T1E1.4/99-333, June 1999.
[54] I. Kalet, and S. Shamai, “On the Capacity of a Twisted-Wire Pair: Gaussian Model,”
IEEE Trans. on Communications, Vol. 38, No. 3, March 1990, pp 379-383.
[55] J. J. Werner, “The HDSL Environment,” IEEE Journal on Selected Areas in
Commun., Vol. 9, No. 6, August 1991.
[56] T. Cover and J. Thomas, “Elements of Information Theory,” Wiley, NY, 1991.
[57] Andrea Goldsmith, Wireless Communications, Class Notes, Fall 1999, Stanford
University.
[58] C. E. Shannon, “A Mathematical Theory of Communication,” Bell Systems
Technical Journal, vol.27, 1948.
[59] T. Starr, J. Cioffi, and P. Silverman, “Understanding DSL Technology,” PrenticeHall, NJ, 1999.
[60] R. Blahut, “Theory and Practice of Error Control Codes,” Addison-Wesley, NY,
1983.
[61] K. Jacobsen, “Spectral Compatibility of ADSL and VDSL,” ANSI T1E1.4/97404R1, December 1997.
124
[62] Liang C. Chu and Martin Brooke, “A Study on Multiaccess xDSL Channels
Transmission Capacity,” Proc. IEEE PACRIM 2001.
[63] G. D. Forney, “Maximum-Likelihood Sequence Estimation of Digital Sequences in
the Presence of Intersymbol Interference,” IEEE Trans. Information Theory, Vol. IT-18,
May 1972.
[64] J. Proakis, Digital Communications, McGraw-Hill, New York, 3rd Ed., 1995.
[65] K. Giridhar, S. Chari, J. J. Shynk and R. P. Gooch, “Joint Demodulation of
Cochannel Signals Using MLSE and MAPSD Algorithms,” Proc. IEEE ICASSP, April
1993.
[66] P. A. Gresh, “Physical and Transmission Characteristics of Customer Loop Plant,”
Bell Syst. Tech. J., pp 3337-3385, Dec. 1969.
[67] R. L. Freeman, Telecommunication Transmission Handbook, Wiley, New York,
1981.
[68] H.L.Van Trees, "Detection, Estimation, and Modulation Theory, Part I," New York,
John Wiley and Sons, 1969
[69] D.Verdin, T.C.Tozer, "Generating a Fading Process for the Simulation of LandMobile Radio Communications," Electronics Letters, vol. 29, no. 23, pp2011-2012, 11
Nov. 1993
[70] G.M.Vitetta, D.P.Taylor, "Maximum Likelihood Detection of Differentially
Encoded PSK Signals Transmitted over Rayleigh, Frequency-Flat Fading Channels," in
Globecom, San Francisco, 1994, pp1889-1893
125
[71] J.H.Lodge, M.J.Moher, "Maximum Likelihood Sequence Estimation of CPM
Signals Transmitted over Rayleigh Flat-Fading Channels," IEEE Trans. Commun., vol.
38, no. 6, pp787-794, June 1990.
[72] G.D.Forney, "Maximum-Likelihood sequence Estimation of Digital Sequences in
the Presence of Intersymbol Interference," IEEE Trans. Inf. Theory, vol. 18, no. 3,
pp363-378, May 1972
[73] G.Ungerboeck, "Adaptive Maximum-Likelihood Receiver for Carrier-Modulated
Data-Transmission Systems," IEEE Trans. Commun., vol 22, no. 5, pp624-636, May
1974.
[74] B. Ottersten, R. Roy, and T. Kailath, “Signal Waveform Estimation in Sensor Array
Processing,” Proc. 23rd Asilomar Conf. Signals, System, Computer, Nov. 1989, pp. 787791.
[75] G. Xu, Y. Cho, A. Paulraj, and T. Kailath, “Maximum Likelihood Detection of Cochannel Communication Signal via Exploitation of Spatial Diversity,” Proc. 26th
Asilomar Conf. Signals, System, Computer, Nov. 1992, pp. 1142-1146.
[76] K. Ishida, I. Oka, and I. Endo, “Cochannel Interference Canceling Effects of MSE
Processing and Viterbi Decoding for On-board Processing Satellites,” IEEE Trans.
Commun., vol. COM-34, pp. 1049-1053, Oct. 1986.
[77] Jun Mo Koo, etc., “Frequency Selective NEXT Cancellation,” IEEE ICASSP 2000,
Vol. 5 pp. 2841-2844.
[78] P. Chow and J. Cioffi, “Method and Apparatus for Adaptive, Variable-Bandwidth,
High-Speed Data Transmission of a Multiuser Signal over Digital Subscriber Lines,”
U.S. patent 5,479,447, December 29, 1995.
126
[79] J. Campello, “Optimal Discrete Bit Loading for Multiuser Modulation Systems,”
IEEE International Symposium on Information Theory, August 1998.
[80] Edward A. Lee and David G. Messerschmitt, Digital Communication, Second
Edition, Kluwer, 1994.
[81] J. Cioffi and K. Cheong, “Coexistence of 2-10 Mbps Home-Phone LANS and DMT
VDSL via Multiuser Detection,” T1E1.4 June 1999.
[82] G.Vitetta, D.P.Taylor, "Maximum Likelihood Sequence Estimation of Uncoded and
Coded
PSK
Signals
Transmitted
over
Rayleigh,
Frequency-Flat
Channels,"
Supercomm/ICC, New Orleans, 1994, pp1-7.
[83] K. Giridhar, J. J. Shynk, A. Mathur, S. Chari, and R. P. Gooch, “Nonlinear
Techniques for the Joint Estimation of Cochannel Signals,” IEEE Trans. On
Communications, vol. 45, pp. 473-484, April 1997.
[84] Bell Atlantic, “Binder Group Segregation is not Feasible,” T1E1.4/99-018.
[85] G996.1 “Test Procedures for DSL Transceivers,” ITU June 1999.
[86] Ken Kerpez, “2B1Q SDSL Crosstalk: Mixed Bit Rates and Numbers of Disturbers,”
T1E1.4/2000-219R1.
[87] “Draft Proposed American National Standard, Spectrum Management for Loop
Transmission Systems,” T1E1.4, 2000-002R6.
[88] R. Conte, “ A Crosstalk Model for Balanced Digital Transmission in Multipair
Cables,” AT&T Tech. J., vol. 65, no. 3, May-June, 1986.
127
128
BIOGRAPHY
Liang C. Chu was born in Shanghai, China at January 29, 1965. He received his M.S.
in electrical engineering at the City College of New York, CUNY, in 1990. He worked
with Science and Technology, Bell South Inc., Atlanta, GA and SCS Telecom. Inc., Port
Washington, NY. He also taught undergraduate and graduate courses in the Department
of Electrical and Computer Engineering, Manhattan College, Riverdale, NY.
His research interests include multiuser detection and communication theory, wireless
communications, broadband access technologies, and digital signal processing.
He has received Regent's Scholarship at Georgia Institute of Technology and
University Merit Fellowship at the City University of New York for his graduate studies.
He is a student member of IEEE.
129