Mid-Term #1 Solutions
advertisement
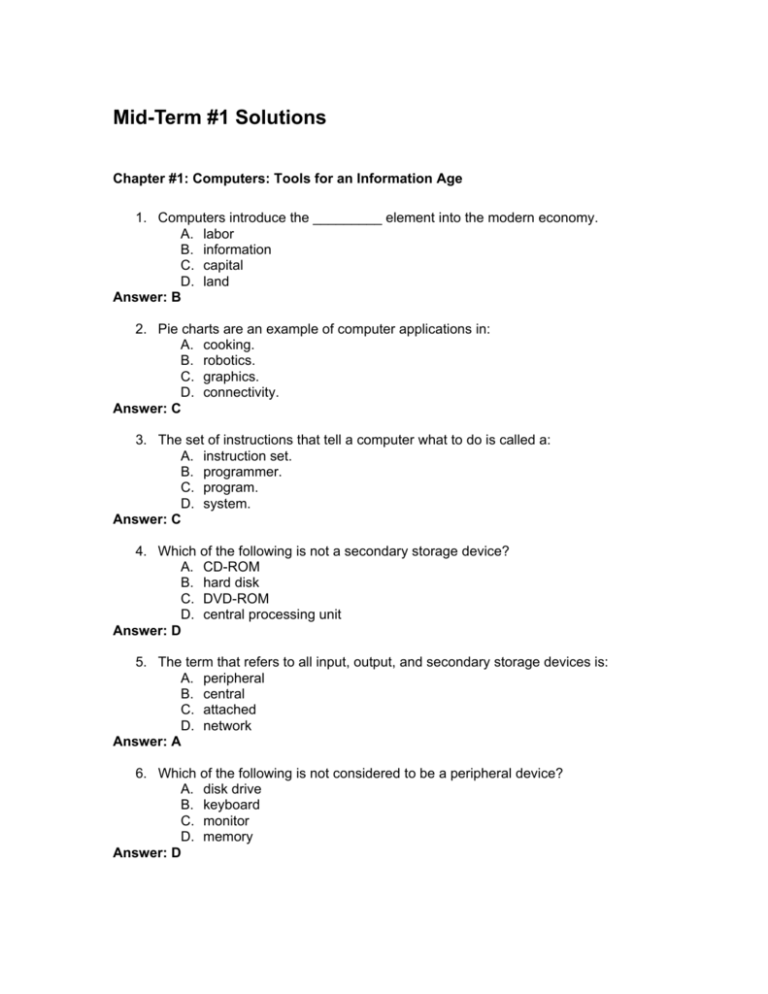
Mid-Term #1 Solutions Chapter #1: Computers: Tools for an Information Age 1. Computers introduce the _________ element into the modern economy. A. labor B. information C. capital D. land Answer: B 2. Pie charts are an example of computer applications in: A. cooking. B. robotics. C. graphics. D. connectivity. Answer: C 3. The set of instructions that tell a computer what to do is called a: A. instruction set. B. programmer. C. program. D. system. Answer: C 4. Which of the following is not a secondary storage device? A. CD-ROM B. hard disk C. DVD-ROM D. central processing unit Answer: D 5. The term that refers to all input, output, and secondary storage devices is: A. peripheral B. central C. attached D. network Answer: A 6. Which of the following is not considered to be a peripheral device? A. disk drive B. keyboard C. monitor D. memory Answer: D 7. The Internet is owned by: A. the U.S. government. B. a private business. C. an international consortium of universities. D. nobody. Answer: D 8. A computer that operates as a connection point in a network for other computers to connect to is called a(n): A. server. B. browser. C. modem. D. ISP. Answer: A 9. The protocol describing standard rules for Internet communication is: A. ISP. B. Web browser. C. TCP/IP. D. LAN. Answer: C 10. The term “Internet Service Provider” refers to: A. a computer that contains shared software. B. a company that provides Internet connectivity for users. C. software that enables communications between computers. D. a Web site containing a home page. Answer: B 11. The type of software you will typically use to explore the Web is a(n): A. ISP. B. home page. C. browser. D. Web site. Answer: C 12. Which type of computer is least likely to have its own secondary storage? A. PDA B. workstation C. mainframe D. thin client Answer: D Chapter 2: Applications Software: Getting the Work Done 13. The general term used for describing software that helps solve everyday personal or business tasks is: A. custom software. B. system software. C. application software. D. vertical software. Answer: C 14. Software that a company’s computer programmers write specifically for the company’s own use is: A. custom software. B. system software. C. application software. D. vertical software. Answer: A 15. A program that includes the opportunity for programmers to modify or enhance its code is called: A. open source. B. public domain. C. freeware. D. custom software. Answer: A 16. Database management software is most appropriate for: A. performing complex mathematical calculations. B. keeping a catalog of all inventory in stock. C. preparing high-quality advertisements and informational brochures. D. downloading important data files from the Internet. Answer: B 17. If you wanted to calculate your budget and play what-if games based on different assumptions of income and expenditures, you would be most likely to use: A. database management software. B. spreadsheet software. C. communications software. D. graphics software. Answer: B 18. Communications software is most appropriate for: A. performing complex mathematical calculations. B. storing a list of important phone numbers. C. preparing high-quality advertisements and informational brochures. D. downloading important data files from the Internet. Answer: D 19. The term vertical market software refers to: A. business software that is primarily used by marketing companies. B. software used primarily in tower computers. C. business software geared to a particular industry of business function. D. volume discount software licenses with steadily declining costs. Answer: C 20. Another term for groupware is: A. integrated application. B. vertical market software. C. collaborative software. D. help desk software. Answer: C 21. A help desk is a(n): A. ergonomically designed workspace for doing computer work. B. online documentation file that comes with software. C. instructor’s manual. D. company’s information and support center. Answer: D 22. Which of the following would not be considered to be software piracy? A. A company buys a single-user copy of software and distributes it to all its employees. B. A student copies software from the school’s computer lab in order to install it on his own computer at home. C. A person buys a copy of software and copies it to another CD for backup purposes. D. A person buys a CD, installs it on her own computer, and then gives the CD to her friend to install on the friend’s computer. Answer: C 23. Which of the following people is responsible for ensuring that computers in an organization can connect with and communicate effectively with each other? A. Computer programmer B. CIO C. Data entry operator D. Network manager Answer: D 24. Which of the following people plans, oversees, and manages all the information technology functions for an organization? A. Computer programmer B. Systems analyst C. Computer operator D. CIO Answer: D Chapter 3: Operating Systems: Software in the Background 25. An operating system is considered to be: A. computer hardware. B. application software. C. system software. D. memory. Answer: C 26. Which of the following types of software would not be considered to be system software? A. operating system. B. utility programs. C. program language translators. D. spreadsheet software. Answer: D 27. The main part of an operating system is called a(n): A. computer operator. B. kernel. C. utility program. D. operations manager. Answer: B 28. When we refer to software as “resident,” this means: A. it is installed on the hard drive. B. it controls the hardware. C. it resides in the home of the user. D. it remains in memory. Answer: D 29. The term that refers to allocation of resources to programs for limited amounts of time is called: A. time events. B. response timing. C. time-sharing. D. time allocation. Answer: C 30. Which is the most likely cause of degradation in a system’s performance? A. Queueing B. Interruptions C. Thrashing D. Time slicing Answer: C 31. Which of the following would not be considered to be a utility program? A. A file manager B. A defragmenter C. A device driver D. An operating system Answer: D 32. What will the operating system do if a file needs to be saved to disk, but there is not enough contiguous space on the disk to accommodate the file’s size? A. The operating system will display an error message to the user. B. The system will freeze up. C. The file will be fragmented and placed in noncontiguous locations. D. The file will be loaded into virtual storage. Answer: C 33. Manufacturers of peripheral hardware devices include special software utilities to help the operating system send commands to the hardware devices. This software is referred to as: A. B. C. D. Answer: C managers directories drivers compressors Chapter 8: The Internet at Home and in the Workplace 34. The precursor to the Internet, which connected four university computer systems, was called: A. Intranet. B. ARPANET. C. NSFNet. D. CERNNet. Answer: B 35. Navigation in the World Wide Web is accomplished by clicking on: A. Windows menus. B. hyperlinks. C. TCP packets. D. browsers. Answer: B 36. The type of software that provides users with the capability to navigate through the Web is called: A. navigation software. B. a browser. C. an ISP. D. a hyperlink. Answer: B 37. A message sent over the Internet is composed of uniformly sized: A. packets. B. browsers. C. links. D. protocols. Answer: A 38. A plug-in is: A. a computer program that plugs into an expansion card or port. B. a special Web site that allows users to gain additional services. C. a software component that enhances the browser’s functionality. D. a small program embedded in a Web page that runs when the browser loads the page. Answer: C 39. An applet is: A. a special feature of Web site activation provided by Apple Corporation. B. a small WAP-enabled device for providing mobile access to the Web. C. a software component that enhances the browser’s functionality. D. a small program embedded in a Web page that runs when the browser loads the page. Answer: D 40. If you want to log onto a computer over the Internet and allow your PC to emulate a terminal on that computer, you would use: A. Usenet. B. FTP. C. Telnet. D. e-mail. Answer: C 41. You will use FTP to: A. send email attachments to other users over the Internet. B. upload or download files over the Internet. C. remotely log into a host computer via the Internet. D. post and read newsgroup messages via the Internet. Answer: B 42. Which type of address will include an @ symbol before the domain? A. IP address. B. e-mail address. C. http Web address. D. intranet portal address. Answer: B 43. The category of e-commerce that takes place between a construction company and its materials supplier is called: A. bricks-and-clicks. B. B2C. C. intranets. D. B2B. Answer: D 44. The term portal refers to: A. a special form of banner ad that links to the Web site for the company being advertised. B. a personalized Web page that provides access to Web sites of interest and presents customized advertisements to the user. C. a dedicated Internet connection between a company and its suppliers. D. a secure firewall, which is like a doorway that needs a special key in order to open. Answer: B 45. The most intrusive and distracting form of Internet advertisement is: A. banner. B. pop-over. C. context-sensitive. D. portal. Answer: B 46. A(n) ________ is a private network typically used internally by a single company, that utilizes tunneling technology to create private channels of communication through the Internet. A. WAN B. intranet C. VPN D. extranet Answer: C 47. What was the first computer bug? A. A burned out tube B. A broken wire C. A moth caught in a relay D. A misplaced punch card Answer: C 48. The first commercially successful GUI was part of the Mac OS and was introduced in A. 1978 B. 1984 C. 1987 D. 1990 Answer: B 49. The three fundamental characteristics of computers are: A. speed, storage capability, variety of applications. B. reliability, speed, storage capability. C. cost effectiveness, speed, variety of applications. D. cost effectiveness, reliability, storage capability. Answer: B 50. The most important program in the operating system, that manages the operating system, is called A. the kernel. B. DOS. C. systems software. D. bootstrapping. Answer: A