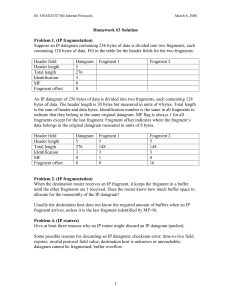
Lecture 3: IPv4 cont'd, ICMP, and UDP

lecture_3
Internetworking
Lecture 3: IPv4 cont’d, ICMP, and
UDP
Literature:
Forouzan, TCP/IP Protocol Suite: Ch 8-9, 11
IPv4 Options
• IPv4 options are intended for network testing or debugging
• Options are variable size and comes after the fixed header.
• Contiguous – no separators
• Not required fields, but all IP implementations must include processing of options
– In practice many implementations do not!
• Max 40 bytes - very limited use
– Max header length is 60 bytes (fixed part is 20 bytes) lecture_3
IP Options Encoding
• Two styles
– Single byte (only code)
– Multiple byte
• Option Code: 1 byte
– Copy (to fragments) (1 bit)
– Class (2 bits)
• 0 (00): Datagram or network control
• 2 (10): Debugging and measurement
– Number (5 bits)
• Option Length (len): 1 byte, defines total length of option
(including code and len fields)
• Data: option specific lecture_3 code len data copy class option number
lecture_3
Categories of IP Options
©The McGraw-Hill Companies, Inc., 2000
lecture_3
IP options types
Number
0
1
3
4
7
9
Option
End of option
No option
Loose source route
Timestamp
Record route
Strict source route
IP Options: Record Route
• Each router records its address
• The destination processes the trace
– E.g. sends the result back to the sender
• Pointer is ”next available slot”
• Source creates an empty list
• Every router adds its address.
– Increments pointer
• Limited to nine hops – IP header size limit code len
First IPv4 addr
Second IPv4 addr
...
pointer
Second IPv4 addr
First IPv4 addr lecture_3
IP Options: Record Route Example
lecture_3
©The McGraw-Hill Companies, Inc., 2000
Note that pointer is an index, starting with code at index 1
IP Options: Source Route
• The sender dictates a path through the network
• Strict Source Routing
– The path is exactly as specified.
• Loose Source Routing
– Allows multiple hops between successive addresses.
• The routers records their addresses
– Just like record route code len pointer
First IPv4 addr
Second IPv4 addr
...
Second IPv4 addr
First IPv4 addr lecture_3
lecture_3
IP Options: Source Route Example
©The McGraw-Hill Companies, Inc., 2000
IP Options: Timestamp
• Similar to record route, but also adds a timestamp
• Source creates an empty list
• Every router adds its address and a timestamp .
• An overflow field (O-flow) specifies how many routers could not specify a timestamp.
• A flags field specifies the visited router responsibilities
– E.g., add only timestamp or add timestamp + outgoing IP address
Code: 68 Length (total)
Data
Pointer O-flow Flags lecture_3
lecture_3
IP Options: Timestamp cont’d
©The McGraw-Hill Companies, Inc., 2000
lecture_3
ICMP
Internet Control Message Protocol - RFC 792
ICMP
• ICMP is a signalling protocol for IPv4.
– Report IP problems back to sender
– Control and Management
– Considered a part of IP, but uses IP for transfers.
• Query ICMPs
– Control purposes
– Examples: Echo, Router advertisement, Timestamp, etc.
• Error ICMPs
– Sent when an error in IP detected
– Includes the first 8 bytes of the data field of the original datagram which caused the error.
– Not sent for: icmp errors, broadcasts, fragments, etc .
– Examples: Dest unreachable, Redirect, etc.
lecture_3
ICMP Messages
Type
3
4
11
12
5
Message
Destination unreachable
Source quench
Time exceeded
Parameter problem
Redirection lecture_3
Type
8/0
13/14
17/18
10/9
Message
Echo request/reply
Timestamp request/reply
Address mask request/reply
Router solicitation/advertisement
General Format of ICMP Messages
©The McGraw-Hill Companies, Inc., 2000
• Type: specifies type of message
• Code: specifies reason for the particular message type lecture_3
ICMP Header
• ICMP error messages returns original IP datagram
• Original IP header (+ options) and 8 bytes of payload
• Example: ICMP Destination Unreachable (UDP packet)
ICMP Message
Ethernet header
IP header
ICMP header
IP header of datagram that generated the error
UDP header
• ICMP Header varies depending on type
– Example: ICMP Destination Unreachable (type 3)
0 7 8 15 16 31 type (3) code (0-15) checksum Common for all types
Unused (all 0s)
IP header (including options) + first 8 bytes of original IP data lecture_3
ICMP Error Reporting
• One of the main responsibilities of ICMP
– Recall that IP is an unreliable protocol, and errors may occur
• ICMP does not correct errors
– Left to higher level protocols
• Error messages are always sent back to the original source
– Because the only information available in the datagram about the route is the source and destination IP addresses
• ICMP uses the source address of the IP packet to send the error message back to the source (originator) lecture_3
ICMP Error Restrictions
An ICMP Error is not returned in response to:
– A datagram carrying another ICMP Error
– A datagram destined to IP broadcast or multicast address
– A datagram sent as link-layer broadcast (e.g., Ethernet)
– An IP fragment other than the first
– A datagram whose source address does not define a single host
(e.g., 0.0.0.0)
• Reason is the risk of creating:
– Loops
– Packet explosions (broadcast storms) lecture_3
lecture_3
ICMP Error Reporting Messages
©The McGraw-Hill Companies, Inc., 2000
ICMP Destination Unreachable
Different types (Code 0-15):
• Code 0 – network unreachable
– Returned by routers
• Code 1 – host unreachable
– Returned by routers
• Code 3 – port unreachable
– Returned by hosts when UDP/TCP port does not exist
• ... (Code 0 – 15 are defined) lecture_3
ICMP Source Quench Error
• Attempt to add a kind of flow control to IP!
• ICMP source quench may be generated if the system receives data faster than it can process it
• New Router Requirements RFC: routers should not generate source quench errors
– Consumes network bandwidth
– An ineffective and unfair fix for congestion
• Thus, for reliability you have to do end-to-end (transport level) flow control, error checking, and use acknowledgements
– TCP lecture_3
ICMP Time Exceeded
This type (11) of error message is sent in 2 cases
• Code 0: when TTL is zero after decrementation, the router discards the datagram and sends an ICMP Time Exceed back to the source
• Code 1: when all fragments of a datagram do not arrive at the destination host within a certain time limit
– Timer is started at reception of first fragment lecture_3
Tool Using ICMP: Traceroute
• Traceroute traces a path to a destination by exploring every
IP hop on the way
– Note: only receiving interfaces are traced, not sendig.
• Traceroute algorithm uses two steps:
1. Set small TTL fields and receive ICMP time exceeded incrementally
2. When final host reached, use unlikely UDP port and get ICMP port unreachable back
• Alternative: use an IP datagram with record route option
– But this is not always implemented
– Limited number of hops can be traced due to maximum size of IP options
– (Record route records IP addresses if outgoing interfaces) lecture_3
ICMP Parameter Problem
• Code 0: Main IP header field problem
– Pointer points to byte with problem
• Code 1: Problem in IP option field
– Pointer not used
• IP routers and hosts do sanity checks on IP header lecture_3 ©The McGraw-Hill Companies, Inc., 2000
ICMP Redirect – concept
• ICMP Redirect is sent by a router (R1) to the sender of an
IP datagram (host) when the datagram should have been sent to a different router (R2)
R
1
(1) IP datagram
(3) ICMP Redirect
(4) Subsequent IP datagrams
(2) IP datagram R
2 lecture_3
ICMP Redirect – message format
• Code 0: Redirection for network specific route
• Code 1: Redirection for host specific route
• ...
©The McGraw-Hill Companies, Inc., 2000 lecture_3
lecture_3
ICMP Query Messages
©The McGraw-Hill Companies, Inc., 2000
Echo Request and Reply
©The McGraw-Hill Companies, Inc., 2000
• Can you think of a widely used program that uses ICMP
Echo request/reply?
lecture_3
Ping uses ICMP Echo Request/Reply
• Ping tests host reachability.
• Uses ICMP echo request/response,
– Almost all IP implementations support Ping server.
• Sends an ICMP echo request to a node
• Server replies with ICMP echo response
• With IP record route (RR) option, the route of the ping datagram can be traced
ICMP Echo
Request ...
ICMP Echo
Respond lecture_3
Timestamp Request and Reply
©The McGraw-Hill Companies, Inc., 2000
• Can be used to calculate round-trip time
– Even if clocks are not synchronized
• Can be used to synchronize clocks if one-way duration is known lecture_3
Address-Mask Request and Reply
©The McGraw-Hill Companies, Inc., 2000
• Can be used by diskless clients to find out the address mask
– Recall that RARP gives only the IP address
• Not used very much
– Other protocols (DHCP, BOOTP) are used for autoconfiguration
(later lecture) lecture_3
Router Solicitation/Advertisement
• On booting, hosts send ~3 ICMP router solicitation messages (~3 seconds apart) to find a default router.
– Dynamic discovery of the default router.
• Routers periodically broadcast or multicast advertisements of their existence and desire to provide routing service
• Advertisements typically every 450 - 600 seconds
• Advertisements have a stated lifetime (typically 30 minutes)
• Seldom implemented
– Mobile IP discovery mechanisms
– IPv6 lecture_3
ICMP Summary
• Destination Unreachable
– Network/Host/Protocol/Port/...
• Time Exceeded
– TTL expired
– Used in the traceroute tool
• Parameter problem
– IP header error
• Source Quench
– Requests source to decrease its data rate.
• Redirect
– Tell source to send its messages to a “better address”
• Echo Request/Echo reply
– For testing (e.g., “ping” program sends an Echo request)
• Timestamp Request/Reply
– Clock synchronization
– RTT
• Address Mask Request/Reply
– Diskless systems
• Router Solicitation and
Advertisment
– Hosts query routers
– Routers advertise presence and routes lecture_3
IP and ICMP Summary
• IPv4 is engineered to solve problems encountered at the network level
• Each field in the IPv4 header addresses a networking issue
– Logical addressing
– Different L2 characteristics (MTUs)
– QoS
– Bit errors
– Multiplexing
• The control and error mechanism of IP is provided by ICMP
• IPv4 is a very successful protocol, but there are many flaws and unused features
– IPv6 has cleaned up the IP layer considerably lecture_3
lecture_3
Transport Layer
Transport Layer
Responsible for end-to-end delivery of entire messages
– Service-point addressing (Protocol Port or Port Number)
• Address the specific running process on a computer
– Segmentation and Reassembly
• Divide message into transmittable segments and reassemble message at receiver
– Connection Control
• For connection-oriented transport protocols
– End-to-end Flow Control (in contrast to link level flow control)
– End-to-end Error Control (in contrast to link level error control) lecture_3
TCP/IP Transport Layer Protocols
2 transport layer protocols in the TCP/IP stack
• UDP – User Datagram Protocol
– Connectionless unreliable service
• TCP – Transmission Control Protocol
– Connection-oriented reliable stream service
Telnet
TCP
FTP
. . .
DNS
UDP
ICMP IP
Underlying link technology
ARP lecture_3
Protocol Ports
Ultimate source/destination of/for a transport level message is a protocol port
• A process sends/listens to a protocol port (identified with an integer)
• Most operating systems provide synchronous access to ports
– A process gets blocked if it attempts to extract data from a port prior to arrival of data
• In general, ports are buffered
– Data arriving before a process is ready to accept is placed in a (finite) queue
• To communicate with a port, sender needs to know both the IP address of the machine and the protocol port number within the machine
• The combination of an IP address and a port number is called a socket
• Each message must carry destination port and source port lecture_3
Port Numbers in Three Groups
Range
0 .. 1023
1024 .. 49151
49152 .. 65535
Purpose
Well-known ports
Registered ports
Dynamic ports
• Servers are normally known by their well-known port number (e.g., 80 for HTTP). Assigned and controlled by
IANA
• Dynamic ports are ephemeral and can be used by any process (normally used by client processes) lecture_3
lecture_3
UDP
User Datagram Protocol - RFC 768
UDP – User Datagram Protocol
UDP
• Datagram-oriented transport layer protocol
• Provides connectionless unreliable service
• Provides optional end-to-end checksum covering header and data
• Provides no feedback to control data rate
• An UDP datagram is silently discarded if checksum errors
• UDP messages can be lost, duplicated, or arrive out of order
• Application programs using UDP must deal with reliability problems
– DNS, DHCP, SNMP, NFS, VoIP, etc. use UDP
– An advantage of UDP is that it is a base to build your own protocols on lecture_3
UDP Message Format
8 byte header + possible data
0 15 16
16 bit source port number 16 bit destination port number
31
16 bit UDP length 16 bit UDP checksum data (if any) lecture_3
• UDP length field is redundant, since the IP software can pass this info to UDP
IP header
20 bytes
IP datagram
UDP datagram
UDP header UDP data
8 bytes 0..(2 16 – 1) – (20 + 8 ) = 65507 bytes
UDP Checksum and Pseudo-header
• UDP checksum covers
– application data, UDP header,a pseudoheader, and pad byte (if needed)
• Purpose with pseudo-header:
– double-check that packet arrived to correct destination
– check that IP delivered the packet to the correct protocol (UDP/TCP)
• Pseudoheader and pad byte not transmitted, only used for computation
Pseudoheader
UDP header
32-bit src IP addr
All 0s
32-bit dst IP addr
8-bit protocol
16-bit src port number
16-bit UDP total length
16-bit dst port number
16-bit UDP total length 16-bit checksum
Data, padded to multiple of 2 bytes (16 bits) lecture_3
Maximum UDP Datagram Size
• Theoretical limit: 65,535 bytes - due to (IP’s) 16-bit total length field
– with 20 bytes of IP header + 8 bytes of UDP header ⇒ 65,507 bytes of user data
• Two limitations:
– sockets API limits size of send and receive buffer; generally 8 kbytes, but you can call a routine to change this
– TCP/IP implementation - Stevens found various limits to the sizes - even with loopback interface
• Hosts are required to handle at least 576 byte IP datagrams Æ lots of protocols limit themselves to 512 bytes or less of data to avoid fragmentation
– DNS, TFTP, BOOTP, and SNMP lecture_3
UDP Summary
• Transport Layer Basics
– end-to-end delivery of messages
• UDP
– a fairly simple connectionless protocol lecture_3