CHAPTER 5 SIMULATION RESULT
advertisement

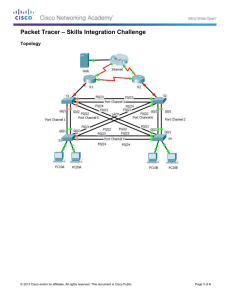
36 CHAPTER 5 SIMULATION RESULT In order to have a better network traffic system run in the PT. Bukit Makmur Mandiri Utama, the author has designed some system that can be implemented in the company. As the current network system in BUMA has no VLAN, which means that less security and high broadcast traffic; the author intended to use VLAN, because it is important in the company to keep the security in each department and to have better network performance. Author will prove that the new design will have a better result than the current system. Because of the project is for giving PT. Bukit Makmur Mandiri Utama a network traffic solution and it is not yet granted by the company itself, the author cannot add switch by author’s will and cannot change the system in the company, that is why author choose to have a simulation. Author did a simulation using a Packet Tracer by made a topology similar with the current topology. The meaning of similar that, author did not use as many Personal Computer (host / PC) as in the real situation of the company, but author made it as a parable. The meaning of parable in the simulation to pretend that: • 45 - 50 users = 5 users • 35 - 44 users = 4 users • 25 - 34 users = 3 users • 15 - 24 users = 2 users • < 15 users = 1 user 37 The reason why author have to pretend the number of personal computer because, it is a simulation that pretend to be the real system, the system cannot be run using an application because it is simulated in Packet Tracer, and the look can be so messy if keep using the real number of Personal Computers in the company. The Simulation is to do comparison between the current network systems and the design made by author that use of VLAN implementation and the addition of clustering switch in the PT. Bukit Makmur Mandiri Utama Network System. 5.1 Simulation Process As mentioned above that the simulation is being used to simulate the current network system and the “designed” system. The designed term is the solution design that author has made. The application that is used for simulation is CISCO Packet Tracer. In Packet Tracer, the type of devices has already provided without need to install the IOS image of the device. There are three types of devices that are used for simulation in Packet Tracer: • Core switch = 2960TT – 24 • Distribution / Access switch = 2950TT – 24 • Personal Computer = PC All those devices will fill the network topology of PT. Bukit Makmur Mandiri Utama network. 38 5.2 Current Network The current network of BUMA has no VLAN, so every device in all departments connects with others. Here is the simulation topology of the current network: Figure 5.1 Simulation of current network system IP Address: 192.168.12.11 – 192.168.12.61 The simulation in here represents the current network system in BUMA like in figure 3.2. In the context of conceptual switch, switch A and switch B are being the core switch that is connected to the distribution switch. The switch E in here become a distribution switch and distribute the packet to the switch below it, which is switch L, switch R, and switch H. The switch M connected to switch L and switch I connected to switch H. It can become a problem in the performance, because there are too many hops for switch M and switch I that 39 they have to pass through switch L and switch H to get access to switch E and then to switch B; too many hops means less performance. Each switch representing each division, except for switch G, Y, I and switch O, P, Q and switch V, W that handle 1 division. In here, all devices use a same network of IP Address and they connect with others, so less security in the system because, nobody knows if there is an inside intruders in the company that can use some application to sniff and look around the data in other division. High broadcast traffic can occurred because each node broadcasting to others, there is no broadcast domain. The real data can be seen in the figure 3.3. 5.3 VLAN Simulation Author has designed the VLAN topology like in the figure 4.4 that there are 3 clustering core switches, which are switch A, switch B, and switch E. The distribution switches that connected will follow them to the ports of switch. Here is the VLAN topology that is simulated using Packet Tracer: Figure 5.2 VLAN Simulation 40 Figure 5.3 Show VLAN Brief (Switch A) Figure 5.4 Show VLAN Brief (Switch B) 41 Figure 5.5 Show VLAN Brief (Switch E) In the Figure 5.2 above, there is only core switch and distribution switch, this design minimize the number of hops that previously occurs in the existing system of the Switch E to improve the performance of the traffic. The VLAN that has been configured makes no division can have connection to other divisions, in other words no connection in every division that makes the security inside the network system more secure. With VLAN implemented, it will helps administrator to manage the broadcast domains, no high broadcast traffic in the network traffic that previously dominate the total traffic in BUMA. 5.4 Discussion of the Result After the topology has been designed and put into the Packet Tracer. The author configured the workstation/devices into a right configuration; one with no VLAN and just connecting all devices and one with VLAN and clustering switch. All the devices has been configured correctly, except for the clustering switch. Simulation using Packet Tracer has some limitation that need to be faced. In Packet Tracer, author cannot configure the clustering switch because of the type 42 of switch available not supported clustering. The unsupported switch because of clustering need higher version of Cisco Catalyst, which is 3500XL while in the packet tracer, the highest version of the available switch is 2960TT; that is why the clustering cannot be simulated. First thing that is done to measure the speed of connection of other device in Packet Tracer by using ping. Author choose the PC32 to ping PC36 because, they are in the same IT VLAN and to have a comparison between the ping based on figure 5.1 and figure 5.2 The command to do the ping in here is: “ping –t ip address". Here are the screenshots of ping from PC32 to PC36: Figure 5.6 Ping in the existing network 43 Figure 5.7 Ping in the VLAN network The result of statistic can be seen that ping in the VLAN network is faster than ping in the existing network, which means that VLAN improve the performance of the network traffic [21]. 5.4.1 Fault If Condition In this fault if condition, author will test the benefit of using clustering switch, that can back up the work of other switch if one switch is fail or overload or goes down [22]. To simulate this condition, author made a new topology, because there is no clustering and it is made like a mesh topology, because the concept of work quite same between the use of mesh topology and clustering switch, even though in real life, clustering switch does not need a mesh topology. 44 Author will use six switches and four PCs to simplify the testing, because the purpose of this simulation just to see how fast that the link can goes back up. If author used the topology in figure 5.2, the topology can be so mesh up and it will be hard to be seen and so complex. That is the reason of just choose a simple topology to test the clustering (mesh). Figure 5.8 Pretend to be clustering In the figure above, both switch 5 and switch 6 have 2 VLAN, which are VLAN 10 and VLAN 20. The way it was simulated to test the fault if condition that author will cut the switch one by one and let see in the ping, how the packet will react if there is a switch off. The simulation has captured that the route that has been determined by default that when PC 1 want to go to PC 3 is through switch 5 – switch 2 – switch 3 – switch 6. The route has been determined by default when PC1 has sent ARP packet to all nodes to determine the link and test how it will reroute and the time it takes to tell the other nodes about what happen and try to find a new route back. 45 First fault condition: In this first fault condition, switch 2 is cut to simulate how the packets will react with the sudden lost connection to switch 2. Figure 5.9 Switch 2 cut Figure 5.10 The ping response 46 Second fault condition: In this second fault condition, switch 1 that is cut to see how the packets will react with the lost connection to switch 1. Figure 5.11 Switch 1 cut Figure 5.12 Response of switch 1 cut 47 Third fault condition: In this third fault condition, switch 3 that is cut to see how the packets will react with the lost connection to switch 3. Figure 5.13 Switch 3 cut Figure 5.14 The response of switch 3 cut 48 Fourth Fault Condition: In this fourth fault condition, switch 4 that is cut to see how the packets will react with the lost connection to switch 4. Figure 5.15 Switch 4 Cut Figure 5.16 The Reply of ping 49 Fifth Fault Condition In this fifth fault condition, switch 1 and switch 4 are cut to see how the packets will react with the lost connection to switch 1 and switch 4. Figure 5.17 Switch 1 and Switch 4 are cut Figure 5.18 The result of switch 1 and switch 4 cut 50 Sixth Fault Condition In this sixth fault condition, switch 2 and switch 3 are cut to see how the packets will react with the lost connection to switch 2 and switch 3. Switch 2 and switch 3 is the determined path from PC 1 to PC 3. Figure 5.19 Switch 2 and Switch 3 are cut Figure 5.20 The result of switch 2 and switch 3 cut 51 Seventh Fault Condition In this fifth fault condition, switch 2 and switch 4 are cut to see how the packets will react with the lost connection to switch 2, then lost connection to switch 4. Figure 5.21 Switch 2 and switch 4 are cut Figure 5.22 The result of switch 2 and switch 4 cut