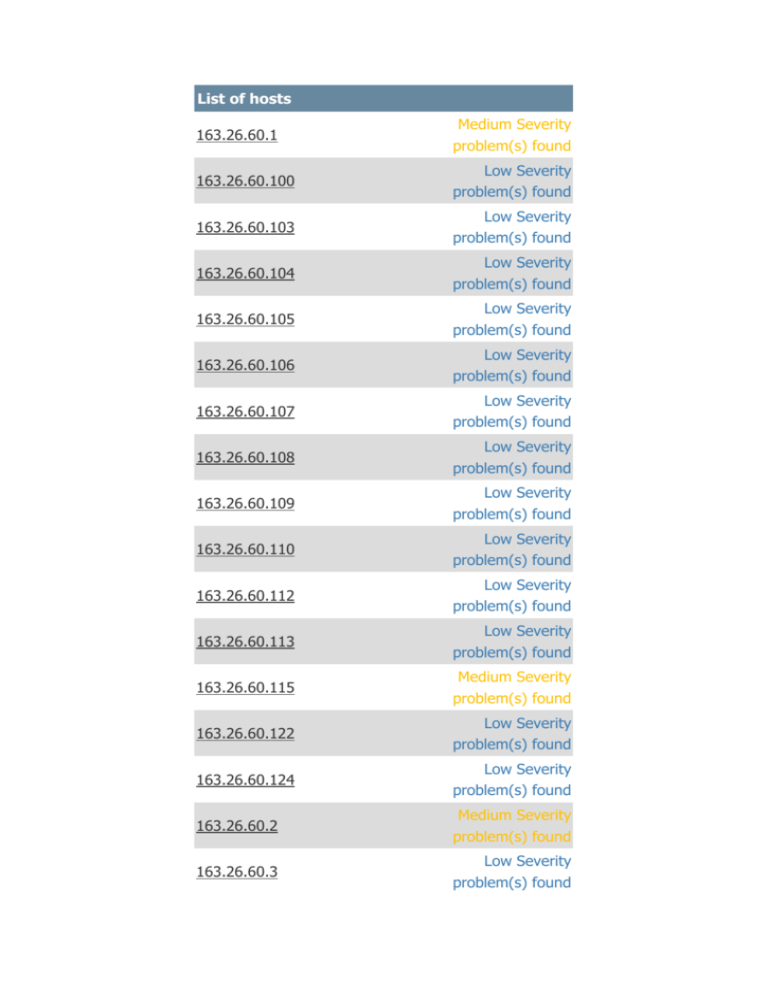
List of hosts
163.26.60.1
Medium Severity
problem(s) found
163.26.60.100
Low Severity
problem(s) found
163.26.60.103
Low Severity
problem(s) found
163.26.60.104
Low Severity
problem(s) found
163.26.60.105
Low Severity
problem(s) found
163.26.60.106
Low Severity
problem(s) found
163.26.60.107
Low Severity
problem(s) found
163.26.60.108
Low Severity
problem(s) found
163.26.60.109
Low Severity
problem(s) found
163.26.60.110
Low Severity
problem(s) found
163.26.60.112
Low Severity
problem(s) found
163.26.60.113
Low Severity
problem(s) found
163.26.60.115
Medium Severity
problem(s) found
163.26.60.122
Low Severity
problem(s) found
163.26.60.124
Low Severity
problem(s) found
163.26.60.2
Medium Severity
problem(s) found
163.26.60.3
Low Severity
problem(s) found
Low Severity
163.26.60.44
problem(s) found
163.26.60.49
Low Severity
problem(s) found
163.26.60.65
Low Severity
problem(s) found
163.26.60.74
Low Severity
problem(s) found
163.26.60.80
Low Severity
problem(s) found
163.26.60.84
Low Severity
problem(s) found
163.26.60.88
Low Severity
problem(s) found
163.26.60.89
Low Severity
problem(s) found
163.26.60.90
Low Severity
problem(s) found
163.26.60.93
Low Severity
problem(s) found
163.26.60.96
Low Severity
problem(s) found
163.26.60.97
Low Severity
problem(s) found
SCAN-ERROR
High Severity
problem(s) found
[^] Back
163.26.60.1
Scan Time
Start
time :
Fri Oct 1 07:13:15
2013
End time :
Fri Oct 1 07:15:55
2013
Number of vulnerabilities
Open ports :
7
High :
0
Medium :
7
Low :
36
Remote host information
Operating
System :
Microsoft Windows
Server 2008
Enterprise Service
Pack 2
NetBIOS
name :
DNS
name :
ABRAHAM5
Abraham5
[^] Back to 163.26.60.1
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.1 : 163.26.60.115
163.26.60.1
[-/+]
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
160 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched on
the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the best
possible CPE based on the information available from
the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE :
cpe:/o:microsoft:windows_server_2008::sp2:enterprise
Following application CPE matched on the remote
system : cpe:/a:microsoft:iis:7.0 -> Microsoft Internet
Information Services (IIS) 7.0
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 99
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Microsoft Windows Server
2008 Enterprise Service Pack 2 Confidence Level : 99
Method : MSRPC The remote host is running Microsoft
Windows Server 2008 Enterprise Service Pack 2
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1d:60:d7:d5:d5 : ASUSTek COMPUTER INC.
Plugin ID:
35716
Host Fully Qualified Domain Name (FQDN)
Resolution
Synopsis:
It was possible to resolve the name of the remote
host.
Description:
Nessus was able to resolve the FQDN of the remote
host.
Risk factor:
None
Solution:
n/a
Plugin output:
163.26.60.1 resolves as Abraham5.
Plugin ID:
12053
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The ICMP timestamps seem to be in little endian
format (not in network format) The difference
between the local and remote clocks is -166 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port epmap (135/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available locally :
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : dsrole Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : protected_storage Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : audit Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : LRPC-373ac753e54d6b59ad Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : tapsrvlpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : unimdmsvc Object UUID :
c3353b16-e70a-48ac-9707-0cc50a30768a UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-ff7fc4db011da682bc Object
UUID : 65eb02bd-9353-4e29-a4b3-1b49fd47e7ef
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC-ff7fc4db011da682bc
Object UUID :
95b4bde4-0c07-4e22-9c8d-e9fd1f1f7441 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-ff7fc4db011da682bc Object
UUID : 36b91ba5-6fec-45d8-933d-a78c98e196fc
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC-ff7fc4db011da682bc
Object UUID :
471a1a06-1d72-42d6-86a4-e270ce678d6a UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : OLEF2775CAF76454689BC92D9E6DEC3
Object UUID :
471a1a06-1d72-42d6-86a4-e270ce678d6a UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-be1aaee8ca227aeb62 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab,
version 1.0 Description : IPsec Services (Windows XP
& 2003) Windows process : lsass.exe Annotation :
IPSec Policy agent endpoint Type : Local RPC service
Named pipe : LRPC-e7a46f2d0fd7e1a92e Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 0b6edbfa-4a24-4fc6-8a23-942b1eca65d1,
version 1.0 Description : Unknown RPC service
Annotation : Spooler function endpoint Type : Local
RPC service Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
ae33069b-a2a8-46ee-a235-ddfd339be281, version
1.0 Description : Unknown RPC service Annotation :
Spooler base remote object endpoint Type : Local RPC
service Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service Annotation :
Spooler function endpoint Type : Local RPC service
Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
dd490425-5325-4565-b774-7e27d6c09c24, version
1.0 Description : Unknown RPC service Annotation :
Base Firewall Engine API Type : Local RPC service
Named pipe : LRPC-036ab8fdf5a97ed0a4 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03,
version 1.0 Description : Unknown RPC service
Annotation : Fw APIs Type : Local RPC service Named
pipe : LRPC-036ab8fdf5a97ed0a4 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service Annotation : Fw
APIs Type : Local RPC service Named pipe :
LRPC-036ab8fdf5a97ed0a4 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
OLE6F660BFA621448E0B5EEDE0F6873 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
LRPC-349e38e20dfcb9fe45 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : OLE6F660BFA621448E0B5EEDE0F6873
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : LRPC-349e38e20dfcb9fe45 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3473dd4d-2e88-4006-9cba-22570909dd10,
version 5.0 Description : Unknown RPC service
Annotation : WinHttp Auto-Proxy Service Type : Local
RPC service Named pipe : W32TIME_ALT Object
UUID : 3bdb59a0-d736-4d44-9074-c1ee00000001
UUID : 24019106-a203-4642-b88d-82dae9158929,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe :
LRPC-f860754232f40367d9 Object UUID :
666f7270-6c69-7365-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : IUserProfile2 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe :
OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511,
version 1.0 Description : Unknown RPC service
Annotation : IKE/Authip API Type : Local RPC service
Named pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : IUserProfile2 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe :
OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : SECLOGON Object
UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : IUserProfile2 Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : senssvc Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : OLEB19BA455B9B34AB7BA0155B32DF8 Object
UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : SECLOGON Object UUID :
6c637067-6569-746e-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-a78b06005cad3d53e0 Object UUID :
24d1f7c7-76af-4f28-9ccd-7f6cb6468601 UUID :
2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : LRPC-a78b06005cad3d53e0
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Local RPC service Named pipe :
eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : eventlog Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Local RPC service Named pipe :
dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : dhcpcsvc
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000001 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WMsgKRpc0A7BC1 Object
UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : LRPC-121efb8413c77076d2
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000000 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WMsgKRpc0A4FD0 Object
UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WindowsShutdown
Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : WMsgKRpc0A4FD0 Object
UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WindowsShutdown
Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-373ac753e54d6b59ad Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : audit Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : securityevent Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : protected_storage Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : dsrole
Plugin ID:
10736
Port netbios-ns (137/udp)
[-/+]
Windows NetBIOS / SMB Remote Host
Information Disclosure
Synopsis:
It is possible to obtain the network name of the
remote host.
Description:
The remote host listens on UDP port 137 or TCP port
445 and replies to NetBIOS nbtscan or SMB requests.
Note that this plugin gathers information to be used in
other plugins but does not itself generate a report.
Risk factor:
None
Solution:
n/a
Plugin output:
The following 3 NetBIOS names have been gathered :
ABRAHAM5 = Computer name WORKGROUP =
Workgroup / Domain name ABRAHAM5 = File Server
Service The remote host has the following MAC
address on its adapter : 00:1d:60:d7:d5:d5
Plugin ID:
10150
Port smb (139/tcp)
[-/+]
Microsoft Windows SMB Service Detection
Synopsis:
A file / print sharing service is listening on the remote
host.
Description:
The remote service understands the CIFS (Common
Internet File System) or Server Message Block (SMB)
protocol, used to provide shared access to files,
printers, etc between nodes on a network.
Risk factor:
None
Solution:
n/a
Plugin output:
An SMB server is running on this port.
Plugin ID:
11011
Port dce-rpc (1688/tcp)
[-/+]
MSRPC Service Detection
Synopsis:
A DCE/RPC server is listening on the remote host.
Description:
The remote host is running a Windows RPC service.
This service replies to the RPC Bind Request with a
Bind Ack response. However it is not possible to
determine the uuid of this service.
Risk factor:
None
Solution:
n/a
Plugin ID:
22319
Port msrdp (3389/tcp)
[-/+]
Terminal Services Doesn't Use Network Level
Authentication (NLA)
Synopsis:
The remote Terminal Services doesn't use Network Level
Authentication.
Description:
The remote Terminal Services is not configured to use
Network Level Authentication (NLA). NLA uses the
Credential Security Support Provider (CredSSP) protocol to
perform strong server authentication either through
TLS/SSL or Kerberos mechanisms, which protect against
man-in-the-middle attacks. In addition to improving
authentication, NLA also helps protect the remote
computer from malicious users and software by
completing user authentication before a full RDP
connection is established.
Risk factor:
Medium
CVSS Base Score:4.3
CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
See also:
http://technet.microsoft.com/en-us/library/cc732713.aspx
See also:
http://www.nessus.org/u?e2628096
Solution:
Enable Network Level Authentication (NLA) on the remote
RDP server. This is generally done on the 'Remote' tab of
the 'System' settings on Windows.
Plugin ID:
58453
Microsoft Windows Remote Desktop Protocol
Server Man-in-the-Middle Weakness
Synopsis:
It may be possible to get access to the remote host.
Description:
The remote version of the Remote Desktop Protocol
Server (Terminal Service) is vulnerable to a
man-in-the-middle (MiTM) attack. The RDP client makes
no effort to validate the identity of the server when setting
up encryption. An attacker with the ability to intercept
traffic from the RDP server can establish encryption with
the client and server without being detected. A MiTM
attack of this nature would allow the attacker to obtain any
sensitive information transmitted, including authentication
credentials. This flaw exists because the RDP server stores
a hardcoded RSA private key in the mstlsapi.dll library. Any
local user with access to this file (on any Windows system)
can retrieve the key and use it for this attack.
Risk factor:
Medium
CVSS Base Score:5.1
CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:P
See also:
http://www.oxid.it/downloads/rdp-gbu.pdf
See also:
http://www.nessus.org/u?e2628096
See also:
http://technet.microsoft.com/en-us/library/cc782610.aspx
Solution:
- Force the use of SSL as a transport layer for this service if
supported, or/and - Select the 'Allow connections only
from computers running Remote Desktop with Network
Level Authentication' setting if it is available.
Plugin ID:
18405
CVE:
CVE-2005-1794
BID:
13818
Other references:
OSVDB:17131
Terminal Services Encryption Level is Medium or
Low
Synopsis:
The remote host is using weak cryptography.
Description:
The remote Terminal Services service is not configured
to use strong cryptography. Using weak cryptography
with this service may allow an attacker to eavesdrop
on the communications more easily and obtain
screenshots and/or keystrokes.
Risk factor:
Medium
CVSS Base Score:4.3
CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
Solution:
Change RDP encryption level to one of : 3. High 4.
FIPS Compliant
Plugin output:
The terminal services encryption level is set to : 2.
Medium
Plugin ID:
57690
Terminal Services Encryption Level is not
FIPS-140 Compliant
Synopsis:
The remote host is not FIPS-140 compliant.
Description:
The encryption setting used by the remote Terminal
Services service is not FIPS-140 compliant.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Change RDP encryption level to : 4. FIPS Compliant
Plugin output:
The terminal services encryption level is set to : 2.
Medium (Client Compatible)
Plugin ID:
30218
Windows Terminal Services Enabled
Synopsis:
The remote Windows host has Terminal Services
enabled.
Description:
Terminal Services allows a Windows user to remotely
obtain a graphical login (and therefore act as a local
user on the remote host). If an attacker gains a valid
login and password, he may be able to use this service
to gain further access on the remote host. An attacker
may also use this service to mount a dictionary attack
against the remote host to try to log in remotely. Note
that RDP (the Remote Desktop Protocol) is vulnerable
to Man-in-the-middle attacks, making it easy for
attackers to steal the credentials of legitimate users by
impersonating the Windows server.
Risk factor:
None
Solution:
Disable Terminal Services if you do not use it, and do
not allow this service to run across the Internet.
Plugin ID:
10940
Port cifs (445/tcp)
[-/+]
SMB Signing Disabled
Synopsis:
Signing is disabled on the remote SMB server.
Description:
Signing is disabled on the remote SMB server. This can allow
man-in-the-middle attacks against the SMB server.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
See also:
http://support.microsoft.com/kb/887429
See also:
http://www.nessus.org/u?74b80723
See also:
http://www.samba.org/samba/docs/man/manpages-3/smb.conf.5.html
Solution:
Enforce message signing in the host's configuration. On Windows, this
is found in the Local Security Policy. On Samba, the setting is called
'server signing'. See the 'see also' links for further details.
Plugin ID:
57608
Microsoft Windows SMB Registry : Nessus
Cannot Access the Windows Registry
Synopsis:
Nessus is not able to access the remote Windows
Registry.
Description:
It was not possible to connect to PIPE\winreg on the
remote host. If you intend to use Nessus to perform
registry-based checks, the registry checks will not
work because the 'Remote Registry Access' service
(winreg) has been disabled on the remote host or can
not be connected to with the supplied credentials.
Risk factor:
None
Solution:
n/a
Plugin output:
Could not connect to the registry because: Could not
connect to \winreg
Plugin ID:
26917
Microsoft Windows SMB Log In Possible
Synopsis:
It is possible to log into the remote host.
Description:
The remote host is running Microsoft Windows operating system
or Samba, a CIFS/SMB server for Unix. It was possible to log into
it using one of the following accounts : - NULL session - Guest
account - Given Credentials
Risk factor:
None
See also:
http://support.microsoft.com/support/kb/articles/Q143/4/74.ASP
See also:
http://support.microsoft.com/support/kb/articles/Q246/2/61.ASP
Solution:
n/a
Plugin output:
- NULL sessions are enabled on the remote host
Plugin ID:
10394
Microsoft Windows SMB NativeLanManager
Remote System Information Disclosure
Synopsis:
It is possible to obtain information about the remote
operating system.
Description:
It is possible to get the remote operating system name
and version (Windows and/or Samba) by sending an
authentication request to port 139 or 445.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote Operating System is : Windows Server (R)
2008 Enterprise 6002 Service Pack 2 The remote
native lan manager is : Windows Server (R) 2008
Enterprise 6.0 The remote SMB Domain Name is :
ABRAHAM5
Plugin ID:
10785
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available
remotely : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \PIPE\protected_storage Netbios name :
\\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name : \\ABRAHAM5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db,
version 1.0 Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint Type : Remote
RPC service Named pipe : \pipe\tapsrv Netbios name :
\\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\wkssvc Netbios name :
\\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\W32TIME_ALT Netbios
name : \\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\ABRAHAM5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Remote RPC service Named
pipe : \PIPE\atsvc Netbios name : \\ABRAHAM5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1,
version 1.0 Description : Unknown RPC service Type :
Remote RPC service Named pipe : \PIPE\atsvc Netbios
name : \\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\srvsvc Netbios name :
\\ABRAHAM5 Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \PIPE\atsvc Netbios name : \\ABRAHAM5 Object
UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Remote RPC
service Named pipe : \PIPE\srvsvc Netbios name :
\\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\ABRAHAM5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6,
version 1.0 Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint Type :
Remote RPC service Named pipe : \pipe\eventlog
Netbios name : \\ABRAHAM5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\ABRAHAM5 Object
UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af,
version 1.0 Description : Unknown RPC service Type :
Remote RPC service Named pipe : \PIPE\InitShutdown
Netbios name : \\ABRAHAM5 Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\InitShutdown Netbios
name : \\ABRAHAM5 Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name : \\ABRAHAM5 Object
UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Remote RPC
service Named pipe : \PIPE\protected_storage Netbios
name : \\ABRAHAM5
Plugin ID:
10736
Microsoft Windows SMB Service Detection
Synopsis:
A file / print sharing service is listening on the remote
host.
Description:
The remote service understands the CIFS (Common
Internet File System) or Server Message Block (SMB)
protocol, used to provide shared access to files,
printers, etc between nodes on a network.
Risk factor:
None
Solution:
n/a
Plugin output:
A CIFS server is running on this port.
Plugin ID:
11011
Port dce-rpc (49152/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49152 : Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49152 IP : 163.26.60.1
Plugin ID:
10736
Port dce-rpc (49153/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49153 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.1 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Remote RPC
service TCP Port : 49153 IP : 163.26.60.1 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.1
Plugin ID:
10736
Port dce-rpc (49154/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49154 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service TCP
Port : 49154 IP : 163.26.60.1
Plugin ID:
10736
Port dce-rpc (49155/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49155 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49155 IP : 163.26.60.1 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511,
version 1.0 Description : Unknown RPC service
Annotation : IKE/Authip API Type : Remote RPC
service TCP Port : 49155 IP : 163.26.60.1 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1,
version 1.0 Description : Unknown RPC service Type :
Remote RPC service TCP Port : 49155 IP : 163.26.60.1
Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service TCP
Port : 49155 IP : 163.26.60.1
Plugin ID:
10736
Port dce-rpc (49156/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49156 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
50abc2a4-574d-40b3-9d66-ee4fd5fba076, version 5.0
Description : DNS Server Windows process : dns.exe
Type : Remote RPC service TCP Port : 49156 IP :
163.26.60.1
Plugin ID:
10736
Port dce-rpc (49157/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49157 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service Annotation :
Remote Fw APIs Type : Remote RPC service TCP Port :
49157 IP : 163.26.60.1 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service TCP Port :
49157 IP : 163.26.60.1
Plugin ID:
10736
Port dce-rpc (49158/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49158 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49158 IP : 163.26.60.1
Plugin ID:
10736
Port dce-rpc (49159/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49159 : Object UUID :
c3353b16-e70a-48ac-9707-0cc50a30768a UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Remote RPC
service TCP Port : 49159 IP : 163.26.60.1 Object
UUID : 65eb02bd-9353-4e29-a4b3-1b49fd47e7ef
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type :
Remote RPC service TCP Port : 49159 IP : 163.26.60.1
Object UUID :
95b4bde4-0c07-4e22-9c8d-e9fd1f1f7441 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Remote RPC
service TCP Port : 49159 IP : 163.26.60.1 Object
UUID : 36b91ba5-6fec-45d8-933d-a78c98e196fc
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type :
Remote RPC service TCP Port : 49159 IP : 163.26.60.1
Plugin ID:
10736
Port dns (53/tcp)
[-/+]
DNS Server Cache Snooping Remote Information Disclosure
Synopsis:
The remote DNS server is vulnerable to cache snooping attacks.
Description:
The remote DNS server responds to queries for third-party domains that do
not have the recursion bit set. This may allow a remote attacker to determine
which domains have recently been resolved via this name server, and
therefore which hosts have been recently visited. For instance, if an attacker
was interested in whether your company utilizes the online services of a
particular financial institution, they would be able to use this attack to build a
statistical model regarding company usage of that financial institution. Of
course, the attack can also be used to find B2B partners, web-surfing
patterns, external mail servers, and more. Note: If this is an internal DNS
server not accessable to outside networks, attacks would be limited to the
internal network. This may include employees, consultants and potentially
users on a guest network or WiFi connection if supported.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.rootsecure.net/content/downloads/pdf/dns_cache_snooping.pdf
Solution:
Contact the vendor of the DNS software for a fix.
Plugin output:
Nessus sent a non-recursive query for example.com and received 1 answer :
192.0.43.10
Plugin ID:
12217
DNS Server Recursive Query Cache Poisoning
Weakness
Synopsis:
The remote name server allows recursive queries to be
performed by the host running nessusd.
Description:
It is possible to query the remote name server for third
party names. If this is your internal nameserver, then
the attack vector may be limited to employees or guest
access if allowed. If you are probing a remote
nameserver, then it allows anyone to use it to resolve
third party names (such as www.nessus.org). This
allows attackers to perform cache poisoning attacks
against this nameserver. If the host allows these
recursive queries via UDP, then the host can be used
to 'bounce' Denial of Service attacks against another
network or system.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
See also:
http://www.cert.org/advisories/CA-1997-22.html
See also:
http://www.nessus.org/u?c4dcf24a
Solution:
Restrict recursive queries to the hosts that should use
this nameserver (such as those of the LAN connected
to it). If you are using bind 8, you can do this by using
the instruction 'allow-recursion' in the 'options' section
of your named.conf. If you are using bind 9, you can
define a grouping of internal addresses using the 'acl'
command. Then, within the options block, you can
explicitly state: 'allow-recursion
{ hosts_defined_in_acl }' If you are using another
name server, consult its documentation.
Plugin ID:
10539
CVE:
CVE-1999-0024
BID:
136, 678
Other references:
OSVDB:438
DNS Server Spoofed Request Amplification
DDoS
Synopsis:
The remote DNS server could be used in a distributed
denial of service attack.
Description:
The remote DNS server answers to any request. It is
possible to query the name servers (NS) of the root
zone ('.') and get an answer which is bigger than the
original request. By spoofing the source IP address, a
remote attacker can leverage this 'amplification' to
launch a denial of service attack against a third-party
host using the remote DNS server.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:P
See also:
http://isc.sans.org/diary.html?storyid=5713
Solution:
Restrict access to your DNS server from public network
or reconfigure it to reject such queries.
Plugin output:
The DNS query was 17 bytes long, the answer is 449
bytes long.
Plugin ID:
35450
CVE:
CVE-2006-0987
DNS Server DNSSEC Aware Resolver
Synopsis:
The remote DNS resolver is DNSSEC-aware.
Description:
The remote DNS resolver accepts DNSSEC options.
This means that it may verify the authenticity of
DNSSEC protected zones if it is configured to trust
their keys.
Risk factor:
None
Solution:
n/a
Plugin ID:
35373
DNS Server Detection
Synopsis:
A DNS server is listening on the remote host.
Description:
The remote service is a Domain Name System (DNS)
server, which provides a mapping between hostnames
and IP addresses.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Domain_Name_System
Solution:
Disable this service if it is not needed or restrict access
to internal hosts only if the service is available
externally.
Plugin ID:
11002
DNS Server Detection
Synopsis:
A DNS server is listening on the remote host.
Description:
The remote service is a Domain Name System (DNS)
server, which provides a mapping between hostnames
and IP addresses.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Domain_Name_System
Solution:
Disable this service if it is not needed or restrict access
to internal hosts only if the service is available
externally.
Plugin ID:
11002
Port llmnr (5355/udp)
[-/+]
Link-Local Multicast Name Resolution (LLMNR)
Detection
Synopsis:
The remote device supports LLMNR.
Description:
The remote device answered to a Link-local Multicast
Name Resolution (LLMNR) request. This protocol provides
a name lookup service similar to NetBIOS or DNS. It is
enabled by default on modern Windows versions.
Risk factor:
None
See also:
http://www.nessus.org/u?85beb421
See also:
http://technet.microsoft.com/en-us/library/bb878128.aspx
Solution:
Make sure that use of this software conforms to your
organization's acceptable use and security policies.
Plugin output:
According to LLMNR, the name of the remote host is
'Abraham5'.
Plugin ID:
53513
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : OPTIONS, TRACE, GET, HEAD,
POST Headers : Content-Type: text/html
Last-Modified: Fri, 21 Feb 2003 11:33:58 GMT
Accept-Ranges: bytes ETag: "0176b1f9dd9c21:0"
Server: Microsoft-IIS/7.0 X-Powered-By: ASP.NET
Date: Thu, 11 Oct 2012 23:17:53 GMT
Content-Length: 1194
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : Microsoft-IIS/7.0
Plugin ID:
10107
HTTP Methods Allowed (per directory)
Synopsis:
This plugin determines which HTTP methods are
allowed on various CGI directories.
Description:
By calling the OPTIONS method, it is possible to
determine which HTTP methods are allowed on each
directory. As this list may be incomplete, the plugin
also tests - if 'Thorough tests' are enabled or 'Enable
web applications tests' is set to 'yes' in the scan policy
- various known HTTP methods on each directory and
considers them as unsupported if it receives a
response code of 400, 403, 405, or 501. Note that the
plugin output is only informational and does not
necessarily indicate the presence of any security
vulnerabilities.
Risk factor:
None
Solution:
n/a
Plugin output:
Based on the response to an OPTIONS request : HTTP methods GET HEAD POST TRACE OPTIONS are
allowed on : /
Plugin ID:
43111
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.1
[^] Back
163.26.60.100
Scan Time
Start
time :
Fri Oct 1 07:15:27
2013
Fri Oct 1 07:18:33
End time :
2013
Number of vulnerabilities
Open ports :
2
High :
0
Medium :
0
Low :
23
Remote host information
Operating
System :
Microsoft Windows
Server 2008
NetBIOS
name :
DNS
name :
WIN-45HMMSEJL9Q
[^] Back to 163.26.60.100
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
[-/+]
163.26.60.115 to 163.26.60.100 : 163.26.60.115
163.26.60.100
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:15 Scan duration :
186 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:microsoft:windows_server_2008
Following application CPE matched on the remote
system : cpe:/a:microsoft:iis:7.0 -> Microsoft Internet
Information Services (IIS) 7.0
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 75
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Microsoft Windows Server
2008 Confidence Level : 75 Method : HTTP The remote
host is running Microsoft Windows Server 2008
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1f:d0:12:c0:80 : GIGA-BYTE TECHNOLOGY
CO.,LTD.
Plugin ID:
35716
Host Fully Qualified Domain Name (FQDN)
Resolution
Synopsis:
It was possible to resolve the name of the remote
host.
Description:
Nessus was able to resolve the FQDN of the remote
host.
Risk factor:
None
Solution:
n/a
Plugin output:
163.26.60.100 resolves as WIN-45HMMSEJL9Q.
Plugin ID:
12053
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
This host returns non-standard timestamps (high bit is
set) The ICMP timestamps might be in little endian
format (not in network format) The difference
between the local and remote clocks is -866 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port epmap (135/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available locally :
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : dsrole Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : protected_storage Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : audit Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : LRPC-b4249551155e0c284b Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : tapsrvlpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : unimdmsvc Object UUID :
b25ab805-c75d-4d73-bb51-e8d3f12e29f7 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-c1b160f010140dbc14 Object
UUID : 36f46f33-d3b9-4283-81ea-b3eb70de5ebd
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC-c1b160f010140dbc14
Object UUID :
f373b35e-3596-44e0-a3a9-0a083328438c UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-c1b160f010140dbc14 Object
UUID : 309893b3-1f93-4928-9e08-0a241b027981
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC-c1b160f010140dbc14
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Local RPC service Named pipe :
LRPC-6d4e972560f3f5f619 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0b6edbfa-4a24-4fc6-8a23-942b1eca65d1, version 1.0
Description : Unknown RPC service Annotation :
Spooler function endpoint Type : Local RPC service
Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
ae33069b-a2a8-46ee-a235-ddfd339be281, version
1.0 Description : Unknown RPC service Annotation :
Spooler base remote object endpoint Type : Local RPC
service Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service Annotation :
Spooler function endpoint Type : Local RPC service
Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
dd490425-5325-4565-b774-7e27d6c09c24, version
1.0 Description : Unknown RPC service Annotation :
Base Firewall Engine API Type : Local RPC service
Named pipe : LRPC-59c5772168f3a87b41 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03,
version 1.0 Description : Unknown RPC service
Annotation : Fw APIs Type : Local RPC service Named
pipe : LRPC-59c5772168f3a87b41 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service Annotation : Fw
APIs Type : Local RPC service Named pipe :
LRPC-59c5772168f3a87b41 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
OLE508ABA8858E748BBB0ED98936668 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
LRPC-1426b1e33c91e26e58 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : OLE508ABA8858E748BBB0ED98936668
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : LRPC-1426b1e33c91e26e58 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3473dd4d-2e88-4006-9cba-22570909dd10,
version 5.0 Description : Unknown RPC service
Annotation : WinHttp Auto-Proxy Service Type : Local
RPC service Named pipe : W32TIME_ALT Object
UUID : 3bdb59a0-d736-4d44-9074-c1ee00000001
UUID : 24019106-a203-4642-b88d-82dae9158929,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe :
LRPC-9b4f06bb99b9cab1af Object UUID :
666f7270-6c69-7365-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLEB821FB3C5D24431B91A8E1A188C8 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
SECLOGON Object UUID :
6c637067-6569-746e-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-e961ca3f48f0dd0328 Object UUID :
24d1f7c7-76af-4f28-9ccd-7f6cb6468601 UUID :
2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : LRPC-e961ca3f48f0dd0328
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Local RPC service Named pipe :
eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : eventlog Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Local RPC service Named pipe :
dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : dhcpcsvc
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000001 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WMsgKRpc0D68F1 Object
UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WMsgKRpc0D1A60
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000000 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WindowsShutdown Object
UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WMsgKRpc0D1A60
Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : WindowsShutdown Object
UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : LRPC-a3ef276fc2686d72c0
Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-b4249551155e0c284b Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : audit Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : securityevent Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : protected_storage Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : dsrole
Plugin ID:
10736
Port microsoft-ds? (445/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available
remotely : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \PIPE\protected_storage Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Remote RPC service
Named pipe : \pipe\tapsrv Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\wkssvc Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\W32TIME_ALT Netbios
name : \\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\atsvc Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Remote RPC service Named
pipe : \PIPE\atsvc Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Remote RPC
service Named pipe : \pipe\eventlog Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\WIN-45HMMSEJL9Q
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000000 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\InitShutdown Netbios
name : \\WIN-45HMMSEJL9Q Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\InitShutdown Netbios
name : \\WIN-45HMMSEJL9Q Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name :
\\WIN-45HMMSEJL9Q Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \PIPE\protected_storage Netbios name :
\\WIN-45HMMSEJL9Q
Plugin ID:
10736
Port dce-rpc (49152/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49152 : Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49152 IP : 163.26.60.100
Plugin ID:
10736
Port dce-rpc (49153/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49153 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.100 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Remote RPC
service TCP Port : 49153 IP : 163.26.60.100 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.100
Plugin ID:
10736
Port dce-rpc (49154/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49154 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service TCP
Port : 49154 IP : 163.26.60.100
Plugin ID:
10736
Port dce-rpc (49155/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49155 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49155 IP : 163.26.60.100
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Remote RPC service TCP Port :
49155 IP : 163.26.60.100 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.100 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.100 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.100
Plugin ID:
10736
Port dce-rpc (49156/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49156 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service Annotation :
Remote Fw APIs Type : Remote RPC service TCP Port :
49156 IP : 163.26.60.100 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service TCP Port :
49156 IP : 163.26.60.100
Plugin ID:
10736
Port dce-rpc (49157/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49157 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49157 IP : 163.26.60.100
Plugin ID:
10736
Port llmnr (5355/udp)
[-/+]
Link-Local Multicast Name Resolution (LLMNR)
Detection
Synopsis:
The remote device supports LLMNR.
Description:
The remote device answered to a Link-local Multicast
Name Resolution (LLMNR) request. This protocol provides
a name lookup service similar to NetBIOS or DNS. It is
enabled by default on modern Windows versions.
Risk factor:
None
See also:
http://www.nessus.org/u?85beb421
See also:
http://technet.microsoft.com/en-us/library/bb878128.aspx
Solution:
Make sure that use of this software conforms to your
organization's acceptable use and security policies.
Plugin output:
According to LLMNR, the name of the remote host is
'WIN-45HMMSEJL9Q'.
Plugin ID:
53513
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : OPTIONS, TRACE, GET, HEAD,
POST Headers : Content-Type: text/html
Last-Modified: Thu, 04 Oct 2012 06:46:07 GMT
Accept-Ranges: bytes ETag: "3bd4c8eefba1cd1:0"
Server: Microsoft-IIS/7.0 Date: Thu, 11 Oct 2012
23:20:34 GMT Content-Length: 689
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : Microsoft-IIS/7.0
Plugin ID:
10107
HTTP Methods Allowed (per directory)
Synopsis:
This plugin determines which HTTP methods are
allowed on various CGI directories.
Description:
By calling the OPTIONS method, it is possible to
determine which HTTP methods are allowed on each
directory. As this list may be incomplete, the plugin
also tests - if 'Thorough tests' are enabled or 'Enable
web applications tests' is set to 'yes' in the scan policy
- various known HTTP methods on each directory and
considers them as unsupported if it receives a
response code of 400, 403, 405, or 501. Note that the
plugin output is only informational and does not
necessarily indicate the presence of any security
vulnerabilities.
Risk factor:
None
Solution:
n/a
Plugin output:
Based on the response to an OPTIONS request : HTTP methods GET HEAD POST TRACE OPTIONS are
allowed on : /
Plugin ID:
43111
Web Server Unconfigured - Default Install Page
Present
Synopsis:
The remote web server is not configured or is not
properly configured.
Description:
The remote web server uses its default welcome page.
It probably means that this server is not used at all or
is serving content that is meant to be hidden.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin output:
The default welcome page is from IIS.
Plugin ID:
11422
Other references:
OSVDB:2117
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.100
[^] Back
163.26.60.103
Scan Time
Start
time :
Fri Oct 1 07:16:07
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
7
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.103
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.103 : 163.26.60.115
163.26.60.103
Plugin ID:
[-/+]
10287
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
Multiple Ethernet Driver Frame Padding
Information Disclosure (Etherleak)
Synopsis:
The remote host appears to leak memory in network
packets.
Description:
The remote host uses a network device driver that
pads ethernet frames with data which vary from one
packet to another, likely taken from kernel memory,
system memory allocated to the device driver, or a
hardware buffer on its network interface card. Known
as 'Etherleak', this information disclosure vulnerability
may allow an attacker to collect sensitive information
from the affected host provided he is on the same
physical subnet as that host.
Risk factor:
Low
CVSS Base Score:3.3
CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.nessus.org/u?719c90b4
Solution:
Contact the network device driver's vendor for a fix.
Plugin output:
Padding observed in one frame : 0x00: 10 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 ................ 0x10:
00 . Padding observed in another frame : 0x00: 50 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00
P............... 0x10: 00 .
Plugin ID:
11197
CVE:
CVE-2003-0001
BID:
6535
Other references:
OSVDB:3873
Port sip? (5060/tcp)
[-/+]
Session Initiation Protocol Detection
Synopsis:
The remote system is a SIP signaling device.
Description:
The remote system is running software that speaks the Session Initiation
Protocol. SIP is a messaging protocol to initiate communication sessions
between systems. It is a protocol used mostly in IP Telephony networks /
systems to setup, control, and teardown sessions between two or more
systems.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Session_Initiation_Protocol
Solution:
If possible, filter incoming connections to the port so that it is used by trusted
sources only.
Plugin output:
The remote service was identified as : VOIP P104SLD 02.11.14 It supports the
following options :
ACK,BYE,CANCEL,INVITE,NOTIFY,REFER,DO,UPDATE,OPTIONS,SUBSCRIBE,P
RACK,INFO
Plugin ID:
21642
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port echo (7/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An echo server is running on this port.
Plugin ID:
22964
Port www (9999/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.103
[^] Back
163.26.60.104
Scan Time
Start
time :
Fri Oct 1 07:16:41
2013
End time :
Fri Oct 1 07:20:09
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
9
Remote host information
EPSON Stylus
Printer Linksys
Operating
System :
Wireless Access
Point Oracle
Integrated Lights
Out Manager
NetBIOS
name :
DNS
name :
[^] Back to 163.26.60.104
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
[-/+]
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.104 : 163.26.60.115
163.26.60.104
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:16 Scan duration :
208 sec
Plugin ID:
19506
Open Port Re-check
Synopsis:
Previously open ports are now closed.
Description:
One of several ports that were previously open are
now closed or unresponsive. There are numerous
possible causes for this failure : - The scan may have
caused a service to freeze or stop running. - An
administrator may have stopped a particular service
during the scanning process. This might be an
availability problem related to the following reasons : A network outage has been experienced during the
scan, and the remote network cannot be reached from
the Vulnerability Scanner anymore. - This Vulnerability
Scanner has been blacklisted by the system
administrator or by automatic intrusion
detection/prevention systems which have detected the
vulnerability assessment. - The remote host is now
down, either because a user turned it off during the
scan or because a select denial of service was
effective. In any case, the audit of the remote host
might be incomplete and may need to be done again
Risk factor:
None
Solution:
- increase checks_read_timeout and/or reduce
max_checks - disable your IPS during the Nessus scan
Plugin output:
Port 443 was detected as being open but is now closed
Port 5060 was detected as being open but is now
closed Port 80 was detected as being open but is now
closed
Plugin ID:
10919
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : EPSON Stylus Printer
Linksys Wireless Access Point Oracle Integrated Lights
Out Manager Confidence Level : 59 Method : SinFP
The remote host is running one of these operating
systems : EPSON Stylus Printer Linksys Wireless
Access Point Oracle Integrated Lights Out Manager
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:18:e7:d6:d5:e3 : Cameo Communications, INC.
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10595 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.104
[^] Back
163.26.60.105
Scan Time
Start
time :
Fri Oct 1 07:18:16
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
7
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.105
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.105 : 163.26.60.115
163.26.60.105
Plugin ID:
10287
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
[-/+]
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
Multiple Ethernet Driver Frame Padding
Information Disclosure (Etherleak)
Synopsis:
The remote host appears to leak memory in network
packets.
Description:
The remote host uses a network device driver that
pads ethernet frames with data which vary from one
packet to another, likely taken from kernel memory,
system memory allocated to the device driver, or a
hardware buffer on its network interface card. Known
as 'Etherleak', this information disclosure vulnerability
may allow an attacker to collect sensitive information
from the affected host provided he is on the same
physical subnet as that host.
Risk factor:
Low
CVSS Base Score:3.3
CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.nessus.org/u?719c90b4
Solution:
Contact the network device driver's vendor for a fix.
Plugin output:
Padding observed in one frame : 0x00: 3D 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 =............... 0x10:
00 . Padding observed in another frame : 0x00: 5E 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00
^............... 0x10: 00 .
Plugin ID:
11197
CVE:
CVE-2003-0001
BID:
6535
Other references:
OSVDB:3873
Port sip? (5060/tcp)
Session Initiation Protocol Detection
[-/+]
Synopsis:
The remote system is a SIP signaling device.
Description:
The remote system is running software that speaks the Session Initiation
Protocol. SIP is a messaging protocol to initiate communication sessions
between systems. It is a protocol used mostly in IP Telephony networks /
systems to setup, control, and teardown sessions between two or more
systems.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Session_Initiation_Protocol
Solution:
If possible, filter incoming connections to the port so that it is used by trusted
sources only.
Plugin output:
The remote service was identified as : VOIP P104SLD 02.11.14 It supports the
following options :
ACK,BYE,CANCEL,INVITE,NOTIFY,REFER,DO,UPDATE,OPTIONS,SUBSCRIBE,P
RACK,INFO
Plugin ID:
21642
Port tftp (69/udp)
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
[-/+]
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port echo (7/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An echo server is running on this port.
Plugin ID:
22964
Port www (9999/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.105
[^] Back
163.26.60.106
Scan Time
Start
time :
Fri Oct 1 07:18:35
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
13
Remote host information
Operating System :
AIX 5.2
NetBIOS name :
DNS name :
[^] Back to 163.26.60.106
Port general (0/udp)
[-/+]
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.106 : 163.26.60.115
163.26.60.106
Plugin ID:
10287
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:ibm:aix:5.2 -> IBM AIX 5.2
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 65
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : AIX 5.2 Confidence Level :
65 Method : SinFP The remote host is running AIX 5.2
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:d0:e9:01:77:3d : Advantage Century
Telecommunication Corp.
Plugin ID:
35716
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
Multiple Ethernet Driver Frame Padding
Information Disclosure (Etherleak)
Synopsis:
The remote host appears to leak memory in network
packets.
Description:
The remote host uses a network device driver that
pads ethernet frames with data which vary from one
packet to another, likely taken from kernel memory,
system memory allocated to the device driver, or a
hardware buffer on its network interface card. Known
as 'Etherleak', this information disclosure vulnerability
may allow an attacker to collect sensitive information
from the affected host provided he is on the same
physical subnet as that host.
Risk factor:
Low
CVSS Base Score:3.3
CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.nessus.org/u?719c90b4
Solution:
Contact the network device driver's vendor for a fix.
Plugin output:
Padding observed in one frame : 0x00: E0 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 ................ 0x10:
00 . Padding observed in another frame : 0x00: 76 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 v...............
0x10: 00 .
Plugin ID:
11197
CVE:
CVE-2003-0001
BID:
6535
Other references:
OSVDB:3873
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port echo (7/tcp)
[-/+]
Echo Service Detection
Synopsis:
An echo service is running on the remote host.
Description:
The remote host is running the 'echo' service. This service echoes any data
which is sent to it. This service is unused these days, so it is strongly advised
that you disable it, as it may be used by attackers to set up denial of services
attacks against this host.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'echo' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
key to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpEc
ho
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpEc
ho Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
10061
CVE:
CVE-1999-0103, CVE-1999-0635
Other references:
OSVDB:150
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An echo server is running on this port.
Plugin ID:
22964
Port www (9999/tcp)
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
[-/+]
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Headers : Server: VOIP WWW-Authenticate: Digest
realm="VOIP",
nonce="e866bacb50b82d08514a8a2b187c437d",
opaque="e94e7b2da163c3228fb1357a786d586c",
stale=false, algorithm=MD5, qop="auth,auth-int"
WWW-Authenticate: Basic realm="VOIP"
Content-Type: text/html Content-Length: 23
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : VOIP
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.106
[^] Back
163.26.60.107
Scan Time
Start
time :
End time :
Fri Oct 1 07:18:53
2013
Fri Oct 1 07:23:17
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
13
Remote host information
Operating System :
AIX 5.2
NetBIOS name :
DNS name :
[^] Back to 163.26.60.107
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.107 : 163.26.60.115
163.26.60.107
Plugin ID:
10287
[-/+]
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:ibm:aix:5.2 -> IBM AIX 5.2
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 65
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : AIX 5.2 Confidence Level :
65 Method : SinFP The remote host is running AIX 5.2
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:d0:e9:40:0a:5e : Advantage Century
Telecommunication Corp.
Plugin ID:
35716
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
Multiple Ethernet Driver Frame Padding
Information Disclosure (Etherleak)
Synopsis:
The remote host appears to leak memory in network
packets.
Description:
The remote host uses a network device driver that
pads ethernet frames with data which vary from one
packet to another, likely taken from kernel memory,
system memory allocated to the device driver, or a
hardware buffer on its network interface card. Known
as 'Etherleak', this information disclosure vulnerability
may allow an attacker to collect sensitive information
from the affected host provided he is on the same
physical subnet as that host.
Risk factor:
Low
CVSS Base Score:3.3
CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.nessus.org/u?719c90b4
Solution:
Contact the network device driver's vendor for a fix.
Plugin output:
Padding observed in one frame : 0x00: 9E 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 ................ 0x10:
00 . Padding observed in another frame : 0x00: 42 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00
B............... 0x10: 00 .
Plugin ID:
11197
CVE:
CVE-2003-0001
BID:
6535
Other references:
OSVDB:3873
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port echo (7/tcp)
[-/+]
Echo Service Detection
Synopsis:
An echo service is running on the remote host.
Description:
The remote host is running the 'echo' service. This service echoes any data
which is sent to it. This service is unused these days, so it is strongly advised
that you disable it, as it may be used by attackers to set up denial of services
attacks against this host.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'echo' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
key to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpEc
ho
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpEc
ho Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
10061
CVE:
CVE-1999-0103, CVE-1999-0635
Other references:
OSVDB:150
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An echo server is running on this port.
Plugin ID:
22964
Port www (9999/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Headers : Server: VOIP WWW-Authenticate: Digest
realm="VOIP",
nonce="83a2de072437544ed0d8521022df0027",
opaque="6894a9f32d9cbfd5a010d8c64fc1c7c9",
stale=false, algorithm=MD5, qop="auth,auth-int"
WWW-Authenticate: Basic realm="VOIP"
Content-Type: text/html Content-Length: 23
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : VOIP
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.107
[^] Back
163.26.60.108
Scan Time
Start
time :
Fri Oct 1 07:19:02
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
7
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.108
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
[-/+]
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.108 : 163.26.60.115
163.26.60.108
Plugin ID:
10287
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
Multiple Ethernet Driver Frame Padding
Information Disclosure (Etherleak)
Synopsis:
The remote host appears to leak memory in network
packets.
Description:
The remote host uses a network device driver that
pads ethernet frames with data which vary from one
packet to another, likely taken from kernel memory,
system memory allocated to the device driver, or a
hardware buffer on its network interface card. Known
as 'Etherleak', this information disclosure vulnerability
may allow an attacker to collect sensitive information
from the affected host provided he is on the same
physical subnet as that host.
Risk factor:
Low
CVSS Base Score:3.3
CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.nessus.org/u?719c90b4
Solution:
Contact the network device driver's vendor for a fix.
Plugin output:
Padding observed in one frame : 0x00: A3 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 ................ 0x10:
00 . Padding observed in another frame : 0x00: 77 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00
w............... 0x10: 00 .
Plugin ID:
11197
CVE:
CVE-2003-0001
BID:
6535
Other references:
OSVDB:3873
Port sip? (5060/tcp)
[-/+]
Session Initiation Protocol Detection
Synopsis:
The remote system is a SIP signaling device.
Description:
The remote system is running software that speaks the Session Initiation
Protocol. SIP is a messaging protocol to initiate communication sessions
between systems. It is a protocol used mostly in IP Telephony networks /
systems to setup, control, and teardown sessions between two or more
systems.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Session_Initiation_Protocol
Solution:
If possible, filter incoming connections to the port so that it is used by trusted
sources only.
Plugin output:
The remote service was identified as : VOIP P104SLD 02.11.14 It supports the
following options :
ACK,BYE,CANCEL,INVITE,NOTIFY,REFER,DO,UPDATE,OPTIONS,SUBSCRIBE,P
RACK,INFO
Plugin ID:
21642
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port echo (7/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An echo server is running on this port.
Plugin ID:
22964
Port www (9999/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.108
[^] Back
163.26.60.109
Scan Time
Start
time :
Fri Oct 1 07:20:10
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
7
Remote host information
Operating
System :
EPSON Stylus
Printer Linksys
Wireless Access
Point Oracle
Integrated Lights
Out Manager
NetBIOS
name :
DNS
name :
[^] Back to 163.26.60.109
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
[-/+]
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.109 : 163.26.60.115
163.26.60.109
Plugin ID:
10287
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : EPSON Stylus Printer
Linksys Wireless Access Point Oracle Integrated Lights
Out Manager Confidence Level : 59 Method : SinFP
The remote host is running one of these operating
systems : EPSON Stylus Printer Linksys Wireless
Access Point Oracle Integrated Lights Out Manager
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:26:5a:c1:0a:e5 : D-Link Corporation
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10587 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.109
[^] Back
163.26.60.110
Scan Time
Start
time :
Fri Oct 1 07:20:40
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
7
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.110
Port general (0/udp)
[-/+]
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.110 : 163.26.60.115
163.26.60.110
Plugin ID:
10287
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:26:5a:c1:0a:f1 : D-Link Corporation
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10596 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Multiple Ethernet Driver Frame Padding
Information Disclosure (Etherleak)
Synopsis:
The remote host appears to leak memory in network
packets.
Description:
The remote host uses a network device driver that
pads ethernet frames with data which vary from one
packet to another, likely taken from kernel memory,
system memory allocated to the device driver, or a
hardware buffer on its network interface card. Known
as 'Etherleak', this information disclosure vulnerability
may allow an attacker to collect sensitive information
from the affected host provided he is on the same
physical subnet as that host.
Risk factor:
Low
CVSS Base Score:3.3
CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N
See also:
http://www.nessus.org/u?719c90b4
Solution:
Contact the network device driver's vendor for a fix.
Plugin output:
Padding observed in one frame : 0x00: 00 00 00 00 00
00 00 80 3A 09 00 00 8D 27 00 00 ........:....'.. 0x10:
00 . Padding observed in another frame : 0x00: 00 00
00 00 00 00 00 80 3A 09 00 00 8D 27 00
AA ........:....'.. 0x10: 55 U
Plugin ID:
11197
CVE:
CVE-2003-0001
BID:
6535
Other references:
OSVDB:3873
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.110
[^] Back
163.26.60.112
Scan Time
Start
time :
Fri Oct 1 07:21:04
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
6
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.112
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.112 : 163.26.60.115
163.26.60.112
Plugin ID:
10287
[-/+]
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10586 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Session Initiation Protocol Detection
Synopsis:
The remote system is a SIP signaling device.
Description:
The remote system is running software that speaks the Session Initiation
Protocol. SIP is a messaging protocol to initiate communication sessions
between systems. It is a protocol used mostly in IP Telephony networks /
systems to setup, control, and teardown sessions between two or more
systems.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Session_Initiation_Protocol
Solution:
If possible, filter incoming connections to the port so that it is used by trusted
sources only.
Plugin output:
The remote service was identified as : DPH-150SE 01.02 It supports the
following options :
ACK,BYE,CANCEL,INVITE,NOTIFY,REFER,DO,UPDATE,OPTIONS,SUBSCRIBE,I
NFO
Plugin ID:
21642
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.112
[^] Back
163.26.60.113
Scan Time
Start
time :
Fri Oct 1 07:21:04
2013
End time :
Fri Oct 1 07:23:13
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
9
Remote host information
Operating
System :
EPSON Stylus
Printer Linksys
Wireless Access
Point Oracle
Integrated Lights
Out Manager
NetBIOS
name :
DNS
name :
[^] Back to 163.26.60.113
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.113 : 163.26.60.115
163.26.60.113
[-/+]
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:21 Scan duration :
129 sec
Plugin ID:
19506
Open Port Re-check
Synopsis:
Previously open ports are now closed.
Description:
One of several ports that were previously open are
now closed or unresponsive. There are numerous
possible causes for this failure : - The scan may have
caused a service to freeze or stop running. - An
administrator may have stopped a particular service
during the scanning process. This might be an
availability problem related to the following reasons : A network outage has been experienced during the
scan, and the remote network cannot be reached from
the Vulnerability Scanner anymore. - This Vulnerability
Scanner has been blacklisted by the system
administrator or by automatic intrusion
detection/prevention systems which have detected the
vulnerability assessment. - The remote host is now
down, either because a user turned it off during the
scan or because a select denial of service was
effective. In any case, the audit of the remote host
might be incomplete and may need to be done again
Risk factor:
None
Solution:
- increase checks_read_timeout and/or reduce
max_checks - disable your IPS during the Nessus scan
Plugin output:
Port 443 was detected as being open but is now closed
Port 5060 was detected as being open but is now
closed Port 80 was detected as being open but is now
closed
Plugin ID:
10919
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : EPSON Stylus Printer
Linksys Wireless Access Point Oracle Integrated Lights
Out Manager Confidence Level : 59 Method : SinFP
The remote host is running one of these operating
systems : EPSON Stylus Printer Linksys Wireless
Access Point Oracle Integrated Lights Out Manager
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:26:5a:c0:fd:d2 : D-Link Corporation
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
-1108 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.113
[^] Back
163.26.60.115
Scan Time
Start
time :
Fri Oct 1 07:21:08
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
16
High :
0
Medium :
7
Low :
42
Remote host information
Operating
System :
Microsoft
Windows Vista
Business
NetBIOS
name :
ELISHA169
DNS name :
ELISHA169
[^] Back to 163.26.60.115
Port general (0/tcp)
[-/+]
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:microsoft:windows_vista:::business
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 99
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Microsoft Windows Vista
Business Confidence Level : 99 Method : MSRPC The
remote host is running Microsoft Windows Vista
Business
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:26:22:1d:38:b2 : COMPAL INFORMATION
(KUNSHAN) CO., LTD.
Plugin ID:
35716
Host Fully Qualified Domain Name (FQDN)
Resolution
Synopsis:
It was possible to resolve the name of the remote
host.
Description:
Nessus was able to resolve the FQDN of the remote
host.
Risk factor:
None
Solution:
n/a
Plugin output:
163.26.60.115 resolves as ELISHA169.
Plugin ID:
12053
Port nessus (1241/tcp)
[-/+]
SSL Self-Signed Certificate
Synopsis:
The SSL certificate chain for this service ends in an
unrecognized self-signed certificate.
Description:
The X.509 certificate chain for this service is not
signed by a recognized certificate authority. If the
remote host is a public host in production, this nullifies
the use of SSL as anyone could establish a man in the
middle attack against the remote host. Note that this
plugin does not check for certificate chains that end in
a certificate that is not self-signed, but is signed by an
unrecognized certificate authority.
Risk factor:
Medium
CVSS Base Score:6.4
CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
Solution:
Purchase or generate a proper certificate for this
service.
Plugin output:
The following certificate was found at the top of the
certificate chain sent by the remote host, but is
self-signed and was not found in the list of known
certificate authorities : |-Subject : O=Nessus Users
United/OU=Nessus Certification Authority/L=New
York/C=US/ST=NY/CN=Nessus Certification Authority
Plugin ID:
57582
SSL / TLS Renegotiation DoS
Synopsis:
The remote service allows repeated renegotiation of TLS / SSL
connections.
Description:
The remote service encrypts traffic using TLS / SSL and permits
clients to renegotiate connections. The computational
requirements for renegotiating a connection are asymmetrical
between the client and the server, with the server performing
several times more work. Since the remote host does not appear
to limit the number of renegotiations for a single TLS / SSL
connection, this permits a client to open several simultaneous
connections and repeatedly renegotiate them, possibly leading to
a denial of service condition.
Risk factor:
Medium
CVSS Base Score:4.3
CVSS2#AV:N/AC:M/Au:N/C:N/I:N/A:P
See also:
http://orchilles.com/2011/03/ssl-renegotiation-dos.html
See also:
http://www.ietf.org/mail-archive/web/tls/current/msg07553.html
Solution:
Contact the vendor for specific patch information.
Plugin output:
The remote host is vulnerable to renegotiation DoS over TLSv1.
Plugin ID:
53491
CVE:
CVE-2011-1473
BID:
48626
Other references:
OSVDB:73894
SSL Certificate Cannot Be Trusted
Synopsis:
The SSL certificate for this service cannot be trusted.
Description:
The server's X.509 certificate does not have a
signature from a known public certificate authority.
This situation can occur in three different ways, each
of which results in a break in the chain below which
certificates cannot be trusted. First, the top of the
certificate chain sent by the server might not be
descended from a known public certificate authority.
This can occur either when the top of the chain is an
unrecognized, self-signed certificate, or when
intermediate certificates are missing that would
connect the top of the certificate chain to a known
public certificate authority. Second, the certificate
chain may contain a certificate that is not valid at the
time of the scan. This can occur either when the scan
occurs before one of the certificate's 'notBefore' dates,
or after one of the certificate's 'notAfter' dates. Third,
the certificate chain may contain a signature that
either didn't match the certificate's information, or was
not possible to verify. Bad signatures can be fixed by
getting the certificate with the bad signature to be
re-signed by its issuer. Signatures that could not be
verified are the result of the certificate's issuer using a
signing algorithm that Nessus either does not support
or does not recognize. If the remote host is a public
host in production, any break in the chain nullifies the
use of SSL as anyone could establish a man in the
middle attack against the remote host.
Risk factor:
Medium
CVSS Base Score:6.4
CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
Solution:
Purchase or generate a proper certificate for this
service.
Plugin output:
The following certificates were at the top of the
certificate chain sent by the remote host, but are
signed by an unknown certificate authority :
|-Subject : O=Nessus Users United/OU=Nessus
Certification Authority/L=New
York/C=US/ST=NY/CN=Nessus Certification Authority
|-Issuer : O=Nessus Users United/OU=Nessus
Certification Authority/L=New
York/C=US/ST=NY/CN=Nessus Certification Authority
Plugin ID:
51192
SSL Certificate Information
Synopsis:
This plugin displays the SSL certificate.
Description:
This plugin connects to every SSL-related port and
attempts to extract and dump the X.509 certificate.
Risk factor:
None
Solution:
n/a
Plugin output:
Subject Name: Organization: Nessus Users United
Organization Unit: Nessus Server Locality: New York
Country: US State/Province: NY Common Name:
ELISHA169 Issuer Name: Organization: Nessus Users
United Organization Unit: Nessus Certification
Authority Locality: New York Country: US
State/Province: NY Common Name: Nessus
Certification Authority Serial Number: 00 AA 0B
Version: 3 Signature Algorithm: SHA-1 With RSA
Encryption Not Valid Before: Jan 26 06:01:46 2012
GMT Not Valid After: Jan 25 06:01:46 2016 GMT Public
Key Info: Algorithm: RSA Encryption Public Key: 00 BB
76 77 E9 59 61 01 F3 AD 15 42 8A AA 9A EA 0A 61 6E
1F B2 12 37 F3 3D 8D 87 25 79 1B 34 3A 70 08 10 5E
05 B4 31 9F 06 74 3F 89 ED 21 C7 A5 D0 F7 09 09 16
92 C8 8F 0A D8 7D 3D B6 29 8C 35 36 88 D4 4E FE 2F
5B 11 EB 5B A0 45 BD 9B C6 8C 36 2A 2C 9F 19 47 26
90 85 3E 21 92 CF D1 F5 BE 62 96 75 FF C6 B1 81 36
9C 14 B5 E9 35 89 ED 94 1F 6C CF C2 E1 5A 20 4F C1
EE 5A E7 07 48 07 15 73 Exponent: 01 00 01
Signature: 00 A2 A4 0F D2 CF B7 4A 70 1D 50 73 5B
B0 2E 6B E6 14 88 B4 22 49 33 81 B0 56 F3 B4 98 EF
DA 6F 08 56 FC 59 2B 96 E0 34 DF 14 47 F7 F0 C7 EB
2F E6 16 C0 D4 50 95 9C 70 00 26 CF 53 D1 EC 51 B4
35 C1 D8 5B EB 37 BE E8 81 F1 8B CB 4F 1B B8 E1 2E
3C FF E3 F7 AA 63 91 B7 16 66 8E 14 17 31 6E D8 13
B9 97 07 74 E8 D5 9B 1C 37 66 1E 33 20 66 7C 7E FB
E1 5B FC 8C 4B C5 A3 5A 52 90 BD 83 38 7B
Extension: 2.16.840.1.113730.1.1 Critical: 0 Data: 03
02 06 40 Extension: Key Usage (2.5.29.15) Critical: 1
Key Usage: Digital Signature, Non Repudiation, Key
Encipherment
Plugin ID:
10863
SSL / TLS Versions Supported
Synopsis:
The remote service encrypts communications.
Description:
This script detects which SSL and TLS versions are
supported by the remote service for encrypting
communications.
Risk factor:
None
Solution:
n/a
Plugin output:
This port supports TLSv1.0.
Plugin ID:
56984
Nessus Server Detection
Synopsis:
A Nessus daemon is listening on the remote port.
Description:
A Nessus daemon is listening on the remote port. It is
not recommended to let anyone connect to this port.
Also, make sure that the remote Nessus installation
has been authorized.
Risk factor:
None
Solution:
Filter incoming traffic to this port.
Plugin ID:
10147
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A TLSv1 server answered on this port.
Plugin ID:
22964
Port www (12882/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers :
Connection: close Content-Type: image/gif
Content-Length: 28 Cache-control: no-cache Pragma:
no-cache
Plugin ID:
24260
Web Site Cross-Domain Policy File Detection
Synopsis:
The remote web server contains a 'crossdomain.xml' file.
Description:
The remote web server contains a cross-domain policy file. This is a simple
XML file used by Adobe's Flash Player to allow access to data that resides
outside the exact web domain from which a Flash movie file originated.
Risk factor:
None
See also:
http://www.adobe.com/devnet/flashplayer/articles/cross_domain_policy.html
See also:
http://www.adobe.com/go/tn_14213
See also:
http://www.nessus.org/u?74a6a9a5
See also:
http://www.nessus.org/u?50ee6db2
Solution:
Review the contents of the policy file carefully. Improper policies, especially
an unrestricted one with just '*', could allow for cross- site request forgery and
cross-site scripting attacks against the web server.
Plugin output:
Nessus was able to obtain a cross-domain policy file from the remote host
using the following URL : http://ELISHA169:12882/crossdomain.xml
Plugin ID:
32318
Web Server No 404 Error Code Check
Synopsis:
The remote web server does not return 404 error
codes.
Description:
The remote web server is configured such that it does
not return '404 Not Found' error codes when a
nonexistent file is requested, perhaps returning
instead a site map, search page or authentication
page. Nessus has enabled some counter measures for
this. However, they might be insufficient. If a great
number of security holes are produced for this port,
they might not all be accurate.
Risk factor:
None
Solution:
n/a
Plugin output:
Unfortunately, Nessus has been unable to find a way
to recognize this page so some CGI-related checks
have been disabled.
Plugin ID:
10386
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
Port epmap (135/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available locally :
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Local RPC service Named pipe : samss
lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Local RPC service Named pipe :
protected_storage Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Local RPC service Named pipe :
securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Local RPC service Named pipe : audit
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Local RPC service Named pipe :
LRPC-32e26f163fce83233a Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : DNSResolver Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : keysvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : keysvc2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : OLE770126BF46EB49BDBA92273FC3D0
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : nlaplg Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : nlaapi Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : tapsrvlpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : unimdmsvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Local RPC service Named pipe :
LRPC-8226a95a7d93a37552 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
dd490425-5325-4565-b774-7e27d6c09c24, version
1.0 Description : Unknown RPC service Annotation :
Base Firewall Engine API Type : Local RPC service
Named pipe : LRPC-e384ddd06c2d67143d Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03,
version 1.0 Description : Unknown RPC service
Annotation : Fw APIs Type : Local RPC service Named
pipe : LRPC-e384ddd06c2d67143d Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service Annotation : Fw
APIs Type : Local RPC service Named pipe :
LRPC-e384ddd06c2d67143d Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0b6edbfa-4a24-4fc6-8a23-942b1eca65d1, version 1.0
Description : Unknown RPC service Annotation :
Spooler function endpoint Type : Local RPC service
Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
ae33069b-a2a8-46ee-a235-ddfd339be281, version
1.0 Description : Unknown RPC service Annotation :
Spooler base remote object endpoint Type : Local RPC
service Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service Annotation :
Spooler function endpoint Type : Local RPC service
Named pipe : spoolss Object UUID :
e6a48980-943e-403f-8f76-fc9d58ba5294 UUID :
98e96949-bc59-47f1-92d1-8c25b46f85c7, version 1.0
Description : Unknown RPC service Annotation :
IhvExtRpcServer Type : Local RPC service Named
pipe : LRPC-700a5ed01539beb74e Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
25952c5d-7976-4aa1-a3cb-c35f7ae79d1b, version 1.0
Description : Unknown RPC service Annotation :
Wireless Diagnostics Type : Local RPC service Named
pipe : OLE48E14A6342BA4B3F8FD41CAA56E3 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 25952c5d-7976-4aa1-a3cb-c35f7ae79d1b,
version 1.0 Description : Unknown RPC service
Annotation : Wireless Diagnostics Type : Local RPC
service Named pipe : LRPC-43487dc9c77b5d4c5a
Object UUID :
6e616c77-7673-0063-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : OLE48E14A6342BA4B3F8FD41CAA56E3 Object
UUID : 6e616c77-7673-0063-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : LRPC-43487dc9c77b5d4c5a
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
266f33b4-c7c1-4bd1-8f52-ddb8f2214ea9, version 1.0
Description : Unknown RPC service Annotation : Wlan
Service Type : Local RPC service Named pipe :
OLE48E14A6342BA4B3F8FD41CAA56E3 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
266f33b4-c7c1-4bd1-8f52-ddb8f2214ea9, version 1.0
Description : Unknown RPC service Annotation : Wlan
Service Type : Local RPC service Named pipe :
LRPC-43487dc9c77b5d4c5a Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
c3f42c6e-d4cc-4e5a-938b-9c5e8a5d8c2e, version 1.0
Description : Unknown RPC service Annotation :
IhvExtRpcServer Type : Local RPC service Named
pipe : OLE48E14A6342BA4B3F8FD41CAA56E3 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : c3f42c6e-d4cc-4e5a-938b-9c5e8a5d8c2e,
version 1.0 Description : Unknown RPC service
Annotation : IhvExtRpcServer Type : Local RPC service
Named pipe : LRPC-43487dc9c77b5d4c5a Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 654976df-1498-4056-a15e-cb4e87584bd8,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe :
OLE48E14A6342BA4B3F8FD41CAA56E3 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
654976df-1498-4056-a15e-cb4e87584bd8, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : LRPC-43487dc9c77b5d4c5a
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0767a036-0d22-48aa-ba69-b619480f38cb, version
1.0 Description : Unknown RPC service Annotation :
PcaSvc Type : Local RPC service Named pipe :
OLE48E14A6342BA4B3F8FD41CAA56E3 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0767a036-0d22-48aa-ba69-b619480f38cb, version
1.0 Description : Unknown RPC service Annotation :
PcaSvc Type : Local RPC service Named pipe :
LRPC-43487dc9c77b5d4c5a Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b58aa02e-2884-4e97-8176-4ee06d794184, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe :
OLE48E14A6342BA4B3F8FD41CAA56E3 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b58aa02e-2884-4e97-8176-4ee06d794184, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : LRPC-43487dc9c77b5d4c5a
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b58aa02e-2884-4e97-8176-4ee06d794184, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : trkwks Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
OLED12D1E1581AE46FBAD830E879E76 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa,
version 1.0 Description : Unknown RPC service
Annotation : NSI server endpoint Type : Local RPC
service Named pipe : LRPC-45cd871bca7d6ca2c5
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4b112204-0e19-11d3-b42b-0000f81feb9f, version 1.0
Description : SSDP service Windows process : unknow
Type : Local RPC service Named pipe :
OLED12D1E1581AE46FBAD830E879E76 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 4b112204-0e19-11d3-b42b-0000f81feb9f,
version 1.0 Description : SSDP service Windows
process : unknow Type : Local RPC service Named
pipe : LRPC-45cd871bca7d6ca2c5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4b112204-0e19-11d3-b42b-0000f81feb9f, version 1.0
Description : SSDP service Windows process : unknow
Type : Local RPC service Named pipe : W32TIME_ALT
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : OLED12D1E1581AE46FBAD830E879E76
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : LRPC-45cd871bca7d6ca2c5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3473dd4d-2e88-4006-9cba-22570909dd10,
version 5.0 Description : Unknown RPC service
Annotation : WinHttp Auto-Proxy Service Type : Local
RPC service Named pipe : W32TIME_ALT Object
UUID : 666f7270-6c69-7365-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : IUserProfile2 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511,
version 1.0 Description : Unknown RPC service
Annotation : IKE/Authip API Type : Local RPC service
Named pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Local RPC service Named
pipe : SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Local RPC service Named
pipe : SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLE9DA3C386242C481CBF789DF65C63 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Local RPC service Named
pipe : SECLOGON Object UUID :
6c637067-6569-746e-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-5761a2ac26bed76106 Object UUID :
24d1f7c7-76af-4f28-9ccd-7f6cb6468601 UUID :
2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : LRPC-5761a2ac26bed76106
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Local RPC service Named pipe :
eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : AudioClientRpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : Audiosrv Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe :
OLEAA8A3DBA76A04330BEE0D97AAD85 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6,
version 1.0 Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint Type :
Local RPC service Named pipe : dhcpcsvc6 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Local RPC service Named pipe :
eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : AudioClientRpc
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : Audiosrv Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Local RPC service Named pipe :
OLEAA8A3DBA76A04330BEE0D97AAD85 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Local RPC service Named pipe :
dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : dhcpcsvc
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service Annotation :
Security Center Type : Local RPC service Named pipe :
eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service Annotation :
Security Center Type : Local RPC service Named pipe :
AudioClientRpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service Annotation :
Security Center Type : Local RPC service Named pipe :
Audiosrv Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service Annotation :
Security Center Type : Local RPC service Named pipe :
OLEAA8A3DBA76A04330BEE0D97AAD85 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023,
version 1.0 Description : Unknown RPC service
Annotation : Security Center Type : Local RPC service
Named pipe : dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service Annotation :
Security Center Type : Local RPC service Named pipe :
dhcpcsvc Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000001 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WMsgKRpc0FF9F1 Object UUID :
52ef130c-08fd-4388-86b3-6edf00000001 UUID :
12e65dd8-887f-41ef-91bf-8d816c42c2e7, version 1.0
Description : Unknown RPC service Annotation :
Secure Desktop LRPC interface Type : Local RPC
service Named pipe : WMsgKRpc0FF9F1 Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000000 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WMsgKRpc0FCEC0 Object
UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WindowsShutdown
Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : WMsgKRpc0FCEC0 Object
UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WindowsShutdown
Object UUID :
6d726574-7273-0076-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-8b556f6392d2bcc250 Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-32e26f163fce83233a Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : audit Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : securityevent Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : protected_storage Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : LRPC-32e26f163fce83233a Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : audit Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : protected_storage
Plugin ID:
10736
Port netbios-ns (137/udp)
[-/+]
Windows NetBIOS / SMB Remote Host
Information Disclosure
Synopsis:
It is possible to obtain the network name of the
remote host.
Description:
The remote host listens on UDP port 137 or TCP port
445 and replies to NetBIOS nbtscan or SMB requests.
Note that this plugin gathers information to be used in
other plugins but does not itself generate a report.
Risk factor:
None
Solution:
n/a
Plugin output:
The following 4 NetBIOS names have been gathered :
ELISHA169 = Computer name WORKGROUP =
Workgroup / Domain name ELISHA169 = File Server
Service WORKGROUP = Browser Service Elections The
remote host has the following MAC address on its
adapter : 00:26:22:1d:38:b2
Plugin ID:
10150
Port smb (139/tcp)
Microsoft Windows SMB Service Detection
[-/+]
Synopsis:
A file / print sharing service is listening on the remote
host.
Description:
The remote service understands the CIFS (Common
Internet File System) or Server Message Block (SMB)
protocol, used to provide shared access to files,
printers, etc between nodes on a network.
Risk factor:
None
Solution:
n/a
Plugin output:
An SMB server is running on this port.
Plugin ID:
11011
Port dce-rpc (1688/tcp)
[-/+]
MSRPC Service Detection
Synopsis:
A DCE/RPC server is listening on the remote host.
Description:
The remote host is running a Windows RPC service.
This service replies to the RPC Bind Request with a
Bind Ack response. However it is not possible to
determine the uuid of this service.
Risk factor:
None
Solution:
n/a
Plugin ID:
22319
Port rtmp (1935/tcp)
[-/+]
RTMP Server Detection
Synopsis:
A Flash media server is listening on the remote host.
Description:
The remote service supports Real Time Messaging Protocol
(RTMP), a proprietary protocol used by Flash Player for
streaming real-time audio, video, and objects using a binary
connection.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Real_Time_Messaging_Protocol
Solution:
Limit incoming traffic to this port if desired.
Plugin ID:
31097
Port cifs (445/tcp)
SMB Signing Disabled
Synopsis:
Signing is disabled on the remote SMB server.
[-/+]
Description:
Signing is disabled on the remote SMB server. This can allow
man-in-the-middle attacks against the SMB server.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N
See also:
http://support.microsoft.com/kb/887429
See also:
http://www.nessus.org/u?74b80723
See also:
http://www.samba.org/samba/docs/man/manpages-3/smb.conf.5.html
Solution:
Enforce message signing in the host's configuration. On Windows, this
is found in the Local Security Policy. On Samba, the setting is called
'server signing'. See the 'see also' links for further details.
Plugin ID:
57608
Microsoft Windows SMB Registry : Nessus
Cannot Access the Windows Registry
Synopsis:
Nessus is not able to access the remote Windows
Registry.
Description:
It was not possible to connect to PIPE\winreg on the
remote host. If you intend to use Nessus to perform
registry-based checks, the registry checks will not
work because the 'Remote Registry Access' service
(winreg) has been disabled on the remote host or can
not be connected to with the supplied credentials.
Risk factor:
None
Solution:
n/a
Plugin output:
Could not connect to the registry because: Could not
connect to \winreg
Plugin ID:
26917
Microsoft Windows SMB Log In Possible
Synopsis:
It is possible to log into the remote host.
Description:
The remote host is running Microsoft Windows operating system
or Samba, a CIFS/SMB server for Unix. It was possible to log into
it using one of the following accounts : - NULL session - Guest
account - Given Credentials
Risk factor:
None
See also:
http://support.microsoft.com/support/kb/articles/Q143/4/74.ASP
See also:
http://support.microsoft.com/support/kb/articles/Q246/2/61.ASP
Solution:
n/a
Plugin output:
- NULL sessions are enabled on the remote host
Plugin ID:
10394
Microsoft Windows SMB NativeLanManager
Remote System Information Disclosure
Synopsis:
It is possible to obtain information about the remote
operating system.
Description:
It is possible to get the remote operating system name
and version (Windows and/or Samba) by sending an
authentication request to port 139 or 445.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote Operating System is : Windows Vista (TM)
Business 6001 Service Pack 1 The remote native lan
manager is : Windows Vista (TM) Business 6.0 The
remote SMB Domain Name is : ELISHA169
Plugin ID:
10785
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available
remotely : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Remote RPC service Named pipe :
\PIPE\protected_storage Netbios name : \\ELISHA169
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Remote RPC service Named pipe :
\pipe\lsass Netbios name : \\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Remote RPC service
Named pipe : \pipe\keysvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Remote RPC service
Named pipe : \pipe\tapsrv Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b58aa02e-2884-4e97-8176-4ee06d794184, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \pipe\trkwks Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4b112204-0e19-11d3-b42b-0000f81feb9f, version 1.0
Description : SSDP service Windows process : unknow
Type : Remote RPC service Named pipe :
\PIPE\wkssvc Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 4b112204-0e19-11d3-b42b-0000f81feb9f,
version 1.0 Description : SSDP service Windows
process : unknow Type : Remote RPC service Named
pipe : \PIPE\DAV RPC SERVICE Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4b112204-0e19-11d3-b42b-0000f81feb9f, version 1.0
Description : SSDP service Windows process : unknow
Type : Remote RPC service Named pipe :
\PIPE\W32TIME_ALT Netbios name : \\ELISHA169
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\wkssvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\DAV RPC SERVICE Netbios
name : \\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\W32TIME_ALT Netbios
name : \\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\atsvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Remote RPC service Named
pipe : \PIPE\atsvc Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511,
version 1.0 Description : Unknown RPC service
Annotation : IKE/Authip API Type : Remote RPC
service Named pipe : \PIPE\srvsvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\srvsvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\browser Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\browser Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\srvsvc Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\browser Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c,
version 1.0 Description : Unknown RPC service
Annotation : Event log TCPIP Type : Remote RPC
service Named pipe : \pipe\eventlog Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Remote RPC
service Named pipe : \pipe\eventlog Netbios name :
\\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023,
version 1.0 Description : Unknown RPC service
Annotation : Security Center Type : Remote RPC
service Named pipe : \pipe\eventlog Netbios name :
\\ELISHA169 Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000000 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\InitShutdown Netbios
name : \\ELISHA169 Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\InitShutdown Netbios
name : \\ELISHA169 Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name : \\ELISHA169 Object
UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Remote RPC
service Named pipe : \PIPE\protected_storage Netbios
name : \\ELISHA169 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name : \\ELISHA169 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac,
version 1.0 Description : Security Account Manager
Windows process : lsass.exe Type : Remote RPC
service Named pipe : \PIPE\protected_storage Netbios
name : \\ELISHA169
Plugin ID:
10736
Microsoft Windows SMB Service Detection
Synopsis:
A file / print sharing service is listening on the remote
host.
Description:
The remote service understands the CIFS (Common
Internet File System) or Server Message Block (SMB)
protocol, used to provide shared access to files,
printers, etc between nodes on a network.
Risk factor:
None
Solution:
n/a
Plugin output:
A CIFS server is running on this port.
Plugin ID:
11011
Port dce-rpc (49152/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49152 : Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49152 IP : 163.26.60.115
Plugin ID:
10736
Port dce-rpc (49153/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49153 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Remote RPC
service TCP Port : 49153 IP : 163.26.60.115 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service Annotation :
Security Center Type : Remote RPC service TCP Port :
49153 IP : 163.26.60.115
Plugin ID:
10736
Port dce-rpc (49154/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49154 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86, version 1.0
Description : Unknown RPC service Annotation :
KeyIso Type : Remote RPC service TCP Port : 49154
IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service TCP
Port : 49154 IP : 163.26.60.115
Plugin ID:
10736
Port dce-rpc (49155/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49155 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49155 IP : 163.26.60.115
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Remote RPC service TCP Port :
49155 IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.115
Plugin ID:
10736
Port dce-rpc (49156/tcp)
DCE Services Enumeration
[-/+]
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49156 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service Annotation :
Remote Fw APIs Type : Remote RPC service TCP Port :
49156 IP : 163.26.60.115 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service TCP Port :
49156 IP : 163.26.60.115
Plugin ID:
10736
Port www (49157/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers :
SERVER: 6.0.6001 2/Service Pack 1, UPnP/1.0,
Portable SDK for UPnP devices/1.4.7 CONNECTION:
close CONTENT-LENGTH: 60 CONTENT-TYPE:
text/html
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : 6.0.6001 2/Service
Pack 1, UPnP/1.0, Portable SDK for UPnP
devices/1.4.7
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
Port dce-rpc (49166/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49166 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49166 IP : 163.26.60.115
Plugin ID:
10736
Port www (7955/tcp)
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
[-/+]
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers : Date:
2012/10/12 W 07:22:02 Server: Pandora TV Media
Server
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : Pandora TV Media
Server
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
Port www (8834/tcp)
[-/+]
SSL Self-Signed Certificate
Synopsis:
The SSL certificate chain for this service ends in an
unrecognized self-signed certificate.
Description:
The X.509 certificate chain for this service is not
signed by a recognized certificate authority. If the
remote host is a public host in production, this nullifies
the use of SSL as anyone could establish a man in the
middle attack against the remote host. Note that this
plugin does not check for certificate chains that end in
a certificate that is not self-signed, but is signed by an
unrecognized certificate authority.
Risk factor:
Medium
CVSS Base Score:6.4
CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
Solution:
Purchase or generate a proper certificate for this
service.
Plugin output:
The following certificate was found at the top of the
certificate chain sent by the remote host, but is
self-signed and was not found in the list of known
certificate authorities : |-Subject : O=Nessus Users
United/OU=Nessus Certification Authority/L=New
York/C=US/ST=NY/CN=Nessus Certification Authority
Plugin ID:
57582
SSL / TLS Renegotiation DoS
Synopsis:
The remote service allows repeated renegotiation of TLS / SSL
connections.
Description:
The remote service encrypts traffic using TLS / SSL and permits
clients to renegotiate connections. The computational
requirements for renegotiating a connection are asymmetrical
between the client and the server, with the server performing
several times more work. Since the remote host does not appear
to limit the number of renegotiations for a single TLS / SSL
connection, this permits a client to open several simultaneous
connections and repeatedly renegotiate them, possibly leading to
a denial of service condition.
Risk factor:
Medium
CVSS Base Score:4.3
CVSS2#AV:N/AC:M/Au:N/C:N/I:N/A:P
See also:
http://orchilles.com/2011/03/ssl-renegotiation-dos.html
See also:
http://www.ietf.org/mail-archive/web/tls/current/msg07553.html
Solution:
Contact the vendor for specific patch information.
Plugin output:
The remote host is vulnerable to renegotiation DoS over TLSv1 /
SSLv3.
Plugin ID:
53491
CVE:
CVE-2011-1473
BID:
48626
Other references:
OSVDB:73894
SSL Certificate Cannot Be Trusted
Synopsis:
The SSL certificate for this service cannot be trusted.
Description:
The server's X.509 certificate does not have a
signature from a known public certificate authority.
This situation can occur in three different ways, each
of which results in a break in the chain below which
certificates cannot be trusted. First, the top of the
certificate chain sent by the server might not be
descended from a known public certificate authority.
This can occur either when the top of the chain is an
unrecognized, self-signed certificate, or when
intermediate certificates are missing that would
connect the top of the certificate chain to a known
public certificate authority. Second, the certificate
chain may contain a certificate that is not valid at the
time of the scan. This can occur either when the scan
occurs before one of the certificate's 'notBefore' dates,
or after one of the certificate's 'notAfter' dates. Third,
the certificate chain may contain a signature that
either didn't match the certificate's information, or was
not possible to verify. Bad signatures can be fixed by
getting the certificate with the bad signature to be
re-signed by its issuer. Signatures that could not be
verified are the result of the certificate's issuer using a
signing algorithm that Nessus either does not support
or does not recognize. If the remote host is a public
host in production, any break in the chain nullifies the
use of SSL as anyone could establish a man in the
middle attack against the remote host.
Risk factor:
Medium
CVSS Base Score:6.4
CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N
Solution:
Purchase or generate a proper certificate for this
service.
Plugin output:
The following certificates were at the top of the
certificate chain sent by the remote host, but are
signed by an unknown certificate authority :
|-Subject : O=Nessus Users United/OU=Nessus
Certification Authority/L=New
York/C=US/ST=NY/CN=Nessus Certification Authority
|-Issuer : O=Nessus Users United/OU=Nessus
Certification Authority/L=New
York/C=US/ST=NY/CN=Nessus Certification Authority
Plugin ID:
51192
SSL Certificate Information
Synopsis:
This plugin displays the SSL certificate.
Description:
This plugin connects to every SSL-related port and
attempts to extract and dump the X.509 certificate.
Risk factor:
None
Solution:
n/a
Plugin output:
Subject Name: Organization: Nessus Users United
Organization Unit: Nessus Server Locality: New York
Country: US State/Province: NY Common Name:
ELISHA169 Issuer Name: Organization: Nessus Users
United Organization Unit: Nessus Certification
Authority Locality: New York Country: US
State/Province: NY Common Name: Nessus
Certification Authority Serial Number: 00 AA 0B
Version: 3 Signature Algorithm: SHA-1 With RSA
Encryption Not Valid Before: Jan 26 06:01:46 2012
GMT Not Valid After: Jan 25 06:01:46 2016 GMT Public
Key Info: Algorithm: RSA Encryption Public Key: 00 BB
76 77 E9 59 61 01 F3 AD 15 42 8A AA 9A EA 0A 61 6E
1F B2 12 37 F3 3D 8D 87 25 79 1B 34 3A 70 08 10 5E
05 B4 31 9F 06 74 3F 89 ED 21 C7 A5 D0 F7 09 09 16
92 C8 8F 0A D8 7D 3D B6 29 8C 35 36 88 D4 4E FE 2F
5B 11 EB 5B A0 45 BD 9B C6 8C 36 2A 2C 9F 19 47 26
90 85 3E 21 92 CF D1 F5 BE 62 96 75 FF C6 B1 81 36
9C 14 B5 E9 35 89 ED 94 1F 6C CF C2 E1 5A 20 4F C1
EE 5A E7 07 48 07 15 73 Exponent: 01 00 01
Signature: 00 A2 A4 0F D2 CF B7 4A 70 1D 50 73 5B
B0 2E 6B E6 14 88 B4 22 49 33 81 B0 56 F3 B4 98 EF
DA 6F 08 56 FC 59 2B 96 E0 34 DF 14 47 F7 F0 C7 EB
2F E6 16 C0 D4 50 95 9C 70 00 26 CF 53 D1 EC 51 B4
35 C1 D8 5B EB 37 BE E8 81 F1 8B CB 4F 1B B8 E1 2E
3C FF E3 F7 AA 63 91 B7 16 66 8E 14 17 31 6E D8 13
B9 97 07 74 E8 D5 9B 1C 37 66 1E 33 20 66 7C 7E FB
E1 5B FC 8C 4B C5 A3 5A 52 90 BD 83 38 7B
Extension: 2.16.840.1.113730.1.1 Critical: 0 Data: 03
02 06 40 Extension: Key Usage (2.5.29.15) Critical: 1
Key Usage: Digital Signature, Non Repudiation, Key
Encipherment
Plugin ID:
10863
Web Server / Application favicon.ico Vendor
Fingerprinting
Synopsis:
The remote web server contains a graphic image that
is prone to information disclosure.
Description:
The 'favicon.ico' file found on the remote web server
belongs to a popular web server. This may be used to
fingerprint the web server.
Risk factor:
None
Solution:
Remove the 'favicon.ico' file or create a custom one for
your site.
Plugin output:
The MD5 fingerprint for 'favicon.ico' suggests the web
server is Nessus 4.x Web Client.
Plugin ID:
20108
Other references:
OSVDB:39272
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : yes Keep-Alive : no
Options allowed : (Not implemented) Headers : Date:
Thu, 11 Oct 2012 23:22:02 GMT Server: NessusWWW
Connection: close Expires: Thu, 11 Oct 2012 23:22:02
GMT Content-Length: 6525 Content-Type: text/html
X-Frame-Options: DENY Cache-Control: Expires: 0
Pragma :
Plugin ID:
24260
SSL / TLS Versions Supported
Synopsis:
The remote service encrypts communications.
Description:
This script detects which SSL and TLS versions are
supported by the remote service for encrypting
communications.
Risk factor:
None
Solution:
n/a
Plugin output:
This port supports SSLv3/TLSv1.0.
Plugin ID:
56984
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : NessusWWW
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port through TLSv1.
Plugin ID:
22964
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A TLSv1 server answered on this port.
Plugin ID:
22964
[^] Back to 163.26.60.115
[^] Back
163.26.60.122
Scan Time
Start
time :
Fri Oct 1 07:21:27
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
6
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.122
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.122 : 163.26.60.115
163.26.60.122
Plugin ID:
10287
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
[-/+]
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10582 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Session Initiation Protocol Detection
Synopsis:
The remote system is a SIP signaling device.
Description:
The remote system is running software that speaks the Session Initiation
Protocol. SIP is a messaging protocol to initiate communication sessions
between systems. It is a protocol used mostly in IP Telephony networks /
systems to setup, control, and teardown sessions between two or more
systems.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Session_Initiation_Protocol
Solution:
If possible, filter incoming connections to the port so that it is used by trusted
sources only.
Plugin output:
The remote service was identified as : DPH-150SE 01.02 It supports the
following options :
ACK,BYE,CANCEL,INVITE,NOTIFY,REFER,DO,UPDATE,OPTIONS,SUBSCRIBE,I
NFO
Plugin ID:
21642
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
Service Detection
Synopsis:
[-/+]
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.122
[^] Back
163.26.60.124
Scan Time
Start
time :
Fri Oct 1 07:21:32
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
5
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.124
Port general (0/udp)
[-/+]
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.124 : 163.26.60.115
163.26.60.124
Plugin ID:
10287
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10593 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port https? (443/tcp)
[-/+]
Port sip? (5060/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.124
[^] Back
163.26.60.2
Scan Time
Start
time :
Fri Oct 1 07:13:15
2013
End time :
Fri Oct 1 07:16:39
2013
Number of vulnerabilities
Open ports :
10
High :
0
Medium :
3
Low :
35
Remote host information
Operating
System :
Microsoft
Windows Server
2008
NetBIOS
name :
DNS name :
ABRAHAM7
[^] Back to 163.26.60.2
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.2 : 163.26.60.115
163.26.60.2
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
[-/+]
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
204 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:microsoft:windows_server_2008
Following application CPE matched on the remote
system : cpe:/a:microsoft:iis:7.0 -> Microsoft Internet
Information Services (IIS) 7.0
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 75
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Microsoft Windows Server
2008 Confidence Level : 75 Method : HTTP The remote
host is running Microsoft Windows Server 2008
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
e0:cb:4e:7f:d7:63 : ASUSTek COMPUTER INC.
Plugin ID:
35716
Host Fully Qualified Domain Name (FQDN)
Resolution
Synopsis:
It was possible to resolve the name of the remote
host.
Description:
Nessus was able to resolve the FQDN of the remote
host.
Risk factor:
None
Solution:
n/a
Plugin output:
163.26.60.2 resolves as ABRAHAM7.
Plugin ID:
12053
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The ICMP timestamps seem to be in little endian
format (not in network format) The difference
between the local and remote clocks is -374 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port daytime (13/tcp)
[-/+]
Daytime Service Detection
Synopsis:
A daytime service is running on the remote host.
Description:
The remote host is running a 'daytime' service. This service is designed to give
the local time of the day of this host to whoever connects to this port. The date
format issued by this service may sometimes help an attacker to guess the
operating system type of this host, or to set up timed authentication attacks
against the remote host. In addition, if the daytime service is running on a UDP
port, an attacker may link it to the echo port of a third-party host using
spoofing, thus creating a possible denial of service condition between this host
and the third party.
Risk factor:
None
Solution:
- On Unix systems, comment out the 'daytime' line in /etc/inetd.conf and
restart the inetd process. - On Windows systems, set the following registry
keys to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpDa
ytime
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpDa
ytime Next, launch cmd.exe and type : net stop simptcp net start simptcp This
will restart the service.
Plugin ID:
10052
Daytime Service Detection
Synopsis:
A daytime service is running on the remote host.
Description:
The remote host is running a 'daytime' service. This service is designed to give
the local time of the day of this host to whoever connects to this port. The date
format issued by this service may sometimes help an attacker to guess the
operating system type of this host, or to set up timed authentication attacks
against the remote host. In addition, if the daytime service is running on a UDP
port, an attacker may link it to the echo port of a third-party host using
spoofing, thus creating a possible denial of service condition between this host
and the third party.
Risk factor:
None
Solution:
- On Unix systems, comment out the 'daytime' line in /etc/inetd.conf and
restart the inetd process. - On Windows systems, set the following registry
keys to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpDa
ytime
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpDa
ytime Next, launch cmd.exe and type : net stop simptcp net start simptcp This
will restart the service.
Plugin ID:
10052
Service Detection (GET request)
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A DAYTIME server is running on this port
Plugin ID:
17975
Port epmap (135/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available locally :
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : dsrole Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : protected_storage Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : audit Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : LRPC-741d9e24c8f0f176ce Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : samss lpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : tapsrvlpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : unimdmsvc Object UUID :
09924ef7-288d-4f95-958d-378bd55e855e UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-3af348828c45d29dae Object
UUID : ea282ca6-9079-47c2-902f-9df1ec3ce5c7
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC-3af348828c45d29dae
Object UUID :
9e85bcd2-25db-4a1b-bec8-31853d1419c3 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-3af348828c45d29dae Object
UUID : b85e5f5d-ae59-4846-b399-c53324f86942
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC-3af348828c45d29dae
Object UUID :
8eb4a442-6f37-400d-b19c-224a210ca7af UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : OLE4280EA2DE3E440F89B9B7E0219AE
Object UUID :
8eb4a442-6f37-400d-b19c-224a210ca7af UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC-9af2396a1c24acd681 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab,
version 1.0 Description : IPsec Services (Windows XP
& 2003) Windows process : lsass.exe Annotation :
IPSec Policy agent endpoint Type : Local RPC service
Named pipe : LRPC-7dcd427efd95b720e6 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 0b6edbfa-4a24-4fc6-8a23-942b1eca65d1,
version 1.0 Description : Unknown RPC service
Annotation : Spooler function endpoint Type : Local
RPC service Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
ae33069b-a2a8-46ee-a235-ddfd339be281, version
1.0 Description : Unknown RPC service Annotation :
Spooler base remote object endpoint Type : Local RPC
service Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service Annotation :
Spooler function endpoint Type : Local RPC service
Named pipe : spoolss Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
dd490425-5325-4565-b774-7e27d6c09c24, version
1.0 Description : Unknown RPC service Annotation :
Base Firewall Engine API Type : Local RPC service
Named pipe : LRPC-236b52b92cca55e32b Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03,
version 1.0 Description : Unknown RPC service
Annotation : Fw APIs Type : Local RPC service Named
pipe : LRPC-236b52b92cca55e32b Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service Annotation : Fw
APIs Type : Local RPC service Named pipe :
LRPC-236b52b92cca55e32b Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
OLE9EAEE9F3E2AC44F9B087A4B02BB5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service Annotation : NSI
server endpoint Type : Local RPC service Named pipe :
LRPC-a32ffa01b0f60568ff Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : OLE9EAEE9F3E2AC44F9B087A4B02BB5
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : LRPC-a32ffa01b0f60568ff Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : W32TIME_ALT Object UUID :
3bdb59a0-d736-4d44-9074-c1ee00000001 UUID :
24019106-a203-4642-b88d-82dae9158929, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : LRPC-7ec5c64e1ef349cd97
Object UUID :
666f7270-6c69-7365-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
736e6573-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Local RPC service Named pipe :
SECLOGON Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : IUserProfile2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : senssvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe :
OLE65651F6309864B069411B2F5AF8D Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : SECLOGON Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : IUserProfile2 Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : senssvc Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : OLE65651F6309864B069411B2F5AF8D Object
UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : SECLOGON Object UUID :
6c637067-6569-746e-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-77f5054acfdca9e033 Object UUID :
24d1f7c7-76af-4f28-9ccd-7f6cb6468601 UUID :
2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : LRPC-77f5054acfdca9e033
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Local RPC service Named pipe :
eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : eventlog Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Local RPC service
Named pipe : dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : eventlog Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Local RPC service Named pipe :
dhcpcsvc6 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : dhcpcsvc
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000001 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WMsgKRpc0140D81 Object
UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WMsgKRpc0CBB60
Object UUID :
b08669ee-8cb5-43a5-a017-84fe00000000 UUID :
76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service Type : Local RPC
service Named pipe : WindowsShutdown Object
UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d,
version 1.0 Description : Unknown RPC service Type :
Local RPC service Named pipe : WMsgKRpc0CBB60
Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Local
RPC service Named pipe : WindowsShutdown Object
UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Local RPC
service Named pipe : LRPC-e53f453fa9cfc11157
Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : LRPC-741d9e24c8f0f176ce Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : audit Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : securityevent Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : protected_storage Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Local RPC service Named
pipe : dsrole
Plugin ID:
10736
Port nsjtp-data? (1688/tcp)
[-/+]
Port qotd (17/tcp)
[-/+]
Quote of the Day (QOTD) Service Detection
Synopsis:
The quote service (qotd) is running on this host.
Description:
A server listens for TCP connections on TCP port 17. Once a connection is
established a short message is sent out the connection (and any data received
is thrown away). The service closes the connection after sending the quote.
Another quote of the day service is defined as a datagram based application on
UDP. A server listens for UDP datagrams on UDP port 17. When a datagram is
received, an answering datagram is sent containing a quote (the data in the
received datagram is ignored). An easy attack is 'pingpong' which IP spoofs a
packet between two machines running qotd. This will cause them to spew
characters at each other, slowing the machines down and saturating the
network.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'qotd' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
keys to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpQo
td
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpQ
otd Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
10198
CVE:
CVE-1999-0103
Other references:
OSVDB:150
Quote of the Day (QOTD) Service Detection
Synopsis:
The quote service (qotd) is running on this host.
Description:
A server listens for TCP connections on TCP port 17. Once a connection is
established a short message is sent out the connection (and any data received
is thrown away). The service closes the connection after sending the quote.
Another quote of the day service is defined as a datagram based application on
UDP. A server listens for UDP datagrams on UDP port 17. When a datagram is
received, an answering datagram is sent containing a quote (the data in the
received datagram is ignored). An easy attack is 'pingpong' which IP spoofs a
packet between two machines running qotd. This will cause them to spew
characters at each other, slowing the machines down and saturating the
network.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'qotd' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
keys to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpQo
td
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpQ
otd Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
10198
CVE:
CVE-1999-0103
Other references:
OSVDB:150
Service Detection (GET request)
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
qotd seems to be running on this port
Plugin ID:
17975
Port chargen (19/tcp)
Service Detection
Synopsis:
The remote service could be identified.
[-/+]
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A chargen server is running on this port.
Plugin ID:
22964
Port msrdp (3389/tcp)
[-/+]
Terminal Services Doesn't Use Network Level
Authentication (NLA)
Synopsis:
The remote Terminal Services doesn't use Network Level
Authentication.
Description:
The remote Terminal Services is not configured to use
Network Level Authentication (NLA). NLA uses the
Credential Security Support Provider (CredSSP) protocol to
perform strong server authentication either through
TLS/SSL or Kerberos mechanisms, which protect against
man-in-the-middle attacks. In addition to improving
authentication, NLA also helps protect the remote
computer from malicious users and software by
completing user authentication before a full RDP
connection is established.
Risk factor:
Medium
CVSS Base Score:4.3
CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
See also:
http://technet.microsoft.com/en-us/library/cc732713.aspx
See also:
http://www.nessus.org/u?e2628096
Solution:
Enable Network Level Authentication (NLA) on the remote
RDP server. This is generally done on the 'Remote' tab of
the 'System' settings on Windows.
Plugin ID:
58453
Microsoft Windows Remote Desktop Protocol
Server Man-in-the-Middle Weakness
Synopsis:
It may be possible to get access to the remote host.
Description:
The remote version of the Remote Desktop Protocol
Server (Terminal Service) is vulnerable to a
man-in-the-middle (MiTM) attack. The RDP client makes
no effort to validate the identity of the server when setting
up encryption. An attacker with the ability to intercept
traffic from the RDP server can establish encryption with
the client and server without being detected. A MiTM
attack of this nature would allow the attacker to obtain any
sensitive information transmitted, including authentication
credentials. This flaw exists because the RDP server stores
a hardcoded RSA private key in the mstlsapi.dll library. Any
local user with access to this file (on any Windows system)
can retrieve the key and use it for this attack.
Risk factor:
Medium
CVSS Base Score:5.1
CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:P
See also:
http://www.oxid.it/downloads/rdp-gbu.pdf
See also:
http://www.nessus.org/u?e2628096
See also:
http://technet.microsoft.com/en-us/library/cc782610.aspx
Solution:
- Force the use of SSL as a transport layer for this service if
supported, or/and - Select the 'Allow connections only
from computers running Remote Desktop with Network
Level Authentication' setting if it is available.
Plugin ID:
18405
CVE:
CVE-2005-1794
BID:
13818
Other references:
OSVDB:17131
Terminal Services Encryption Level is Medium or
Low
Synopsis:
The remote host is using weak cryptography.
Description:
The remote Terminal Services service is not configured
to use strong cryptography. Using weak cryptography
with this service may allow an attacker to eavesdrop
on the communications more easily and obtain
screenshots and/or keystrokes.
Risk factor:
Medium
CVSS Base Score:4.3
CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N
Solution:
Change RDP encryption level to one of : 3. High 4.
FIPS Compliant
Plugin output:
The terminal services encryption level is set to : 2.
Medium
Plugin ID:
57690
Terminal Services Encryption Level is not
FIPS-140 Compliant
Synopsis:
The remote host is not FIPS-140 compliant.
Description:
The encryption setting used by the remote Terminal
Services service is not FIPS-140 compliant.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Change RDP encryption level to : 4. FIPS Compliant
Plugin output:
The terminal services encryption level is set to : 2.
Medium (Client Compatible)
Plugin ID:
30218
Windows Terminal Services Enabled
Synopsis:
The remote Windows host has Terminal Services
enabled.
Description:
Terminal Services allows a Windows user to remotely
obtain a graphical login (and therefore act as a local
user on the remote host). If an attacker gains a valid
login and password, he may be able to use this service
to gain further access on the remote host. An attacker
may also use this service to mount a dictionary attack
against the remote host to try to log in remotely. Note
that RDP (the Remote Desktop Protocol) is vulnerable
to Man-in-the-middle attacks, making it easy for
attackers to steal the credentials of legitimate users by
impersonating the Windows server.
Risk factor:
None
Solution:
Disable Terminal Services if you do not use it, and do
not allow this service to run across the Internet.
Plugin ID:
10940
Port microsoft-ds? (445/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available
remotely : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \PIPE\protected_storage Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db,
version 1.0 Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint Type : Remote
RPC service Named pipe : \pipe\tapsrv Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\wkssvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\W32TIME_ALT Netbios
name : \\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f,
version 1.0 Description : Scheduler Service Windows
process : svchost.exe Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
a398e520-d59a-4bdd-aa7a-3c1e0303a511, version
1.0 Description : Unknown RPC service Annotation :
IKE/Authip API Type : Remote RPC service Named
pipe : \PIPE\atsvc Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service
Named pipe : \PIPE\atsvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service Named pipe :
\PIPE\srvsvc Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1,
version 1.0 Description : Unknown RPC service Type :
Remote RPC service Named pipe : \PIPE\atsvc Netbios
name : \\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\srvsvc Netbios name :
\\ABRAHAM7 Object UUID :
73736573-6f69-656e-6e76-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \PIPE\atsvc Netbios name : \\ABRAHAM7 Object
UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Remote RPC
service Named pipe : \PIPE\srvsvc Netbios name :
\\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\ABRAHAM7 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6,
version 1.0 Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint Type :
Remote RPC service Named pipe : \pipe\eventlog
Netbios name : \\ABRAHAM7 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service Named pipe :
\pipe\eventlog Netbios name : \\ABRAHAM7 Object
UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af,
version 1.0 Description : Unknown RPC service Type :
Remote RPC service Named pipe : \PIPE\InitShutdown
Netbios name : \\ABRAHAM7 Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service Named pipe : \PIPE\InitShutdown Netbios
name : \\ABRAHAM7 Object UUID :
00736665-0000-0000-0000-000000000000 UUID :
c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version
1.0 Description : Unknown RPC service Annotation :
Impl friendly name Type : Remote RPC service Named
pipe : \pipe\lsass Netbios name : \\ABRAHAM7 Object
UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Remote RPC
service Named pipe : \PIPE\protected_storage Netbios
name : \\ABRAHAM7
Plugin ID:
10736
Port dce-rpc (49152/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49152 : Object UUID :
765294ba-60bc-48b8-92e9-89fd77769d91 UUID :
d95afe70-a6d5-4259-822e-2c84da1ddb0d, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49152 IP : 163.26.60.2
Plugin ID:
10736
Port dce-rpc (49153/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49153 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service Annotation : Event
log TCPIP Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service Annotation :
DHCPv6 Client LRPC Endpoint Type : Remote RPC
service TCP Port : 49153 IP : 163.26.60.2 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5,
version 1.0 Description : DHCP Client Service Windows
process : svchost.exe Annotation : DHCP Client LRPC
Endpoint Type : Remote RPC service TCP Port : 49153
IP : 163.26.60.2
Plugin ID:
10736
Port dce-rpc (49154/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49154 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service TCP
Port : 49154 IP : 163.26.60.2
Plugin ID:
10736
Port dce-rpc (49155/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49155 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
86d35949-83c9-4044-b424-db363231fd0c, version
1.0 Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49155 IP : 163.26.60.2 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511,
version 1.0 Description : Unknown RPC service
Annotation : IKE/Authip API Type : Remote RPC
service TCP Port : 49155 IP : 163.26.60.2 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a,
version 1.0 Description : Unknown RPC service
Annotation : AppInfo Type : Remote RPC service TCP
Port : 49155 IP : 163.26.60.2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version
1.0 Description : Unknown RPC service Annotation :
AppInfo Type : Remote RPC service TCP Port : 49155
IP : 163.26.60.2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49155 IP : 163.26.60.2 Object
UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277,
version 1.0 Description : Unknown RPC service
Annotation : Impl friendly name Type : Remote RPC
service TCP Port : 49155 IP : 163.26.60.2
Plugin ID:
10736
Port dce-rpc (49156/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49156 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service Annotation :
Remote Fw APIs Type : Remote RPC service TCP Port :
49156 IP : 163.26.60.2 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service TCP Port :
49156 IP : 163.26.60.2
Plugin ID:
10736
Port dce-rpc (49157/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 49157 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service Type : Remote
RPC service TCP Port : 49157 IP : 163.26.60.2
Plugin ID:
10736
Port llmnr (5355/udp)
[-/+]
Link-Local Multicast Name Resolution (LLMNR)
Detection
Synopsis:
The remote device supports LLMNR.
Description:
The remote device answered to a Link-local Multicast
Name Resolution (LLMNR) request. This protocol provides
a name lookup service similar to NetBIOS or DNS. It is
enabled by default on modern Windows versions.
Risk factor:
None
See also:
http://www.nessus.org/u?85beb421
See also:
http://technet.microsoft.com/en-us/library/bb878128.aspx
Solution:
Make sure that use of this software conforms to your
organization's acceptable use and security policies.
Plugin output:
According to LLMNR, the name of the remote host is
'ABRAHAM7'.
Plugin ID:
53513
Port echo (7/tcp)
[-/+]
Echo Service Detection
Synopsis:
An echo service is running on the remote host.
Description:
The remote host is running the 'echo' service. This service echoes any data
which is sent to it. This service is unused these days, so it is strongly advised
that you disable it, as it may be used by attackers to set up denial of services
attacks against this host.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'echo' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
key to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpEc
ho
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpEc
ho Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
10061
CVE:
CVE-1999-0103, CVE-1999-0635
Other references:
OSVDB:150
Echo Service Detection
Synopsis:
An echo service is running on the remote host.
Description:
The remote host is running the 'echo' service. This service echoes any data
which is sent to it. This service is unused these days, so it is strongly advised
that you disable it, as it may be used by attackers to set up denial of services
attacks against this host.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'echo' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
key to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpEc
ho
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpEc
ho Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
10061
CVE:
CVE-1999-0103, CVE-1999-0635
Other references:
OSVDB:150
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An echo server is running on this port.
Plugin ID:
22964
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : OPTIONS, TRACE, GET, HEAD,
POST Headers : Content-Type: text/html
Last-Modified: Tue, 09 Oct 2012 08:45:22 GMT
Accept-Ranges: bytes ETag: "d0c67e6bfaa5cd1:0"
Server: Microsoft-IIS/7.0 X-Powered-By: ASP.NET
Date: Thu, 11 Oct 2012 23:18:40 GMT
Content-Length: 19247
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : Microsoft-IIS/7.0
Plugin ID:
10107
HTTP Methods Allowed (per directory)
Synopsis:
This plugin determines which HTTP methods are
allowed on various CGI directories.
Description:
By calling the OPTIONS method, it is possible to
determine which HTTP methods are allowed on each
directory. As this list may be incomplete, the plugin
also tests - if 'Thorough tests' are enabled or 'Enable
web applications tests' is set to 'yes' in the scan policy
- various known HTTP methods on each directory and
considers them as unsupported if it receives a
response code of 400, 403, 405, or 501. Note that the
plugin output is only informational and does not
necessarily indicate the presence of any security
vulnerabilities.
Risk factor:
None
Solution:
n/a
Plugin output:
Based on the response to an OPTIONS request : HTTP methods GET HEAD POST TRACE OPTIONS are
allowed on : /
Plugin ID:
43111
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
Port discard (9/tcp)
[-/+]
Discard Service Detection
Synopsis:
A discard service is running on the remote host.
Description:
The remote host is running a 'discard' service. This service typically sets up a
listening socket and will ignore all the data which it receives. This service is
unused these days, so it is advised that you disable it.
Risk factor:
None
Solution:
- Under Unix systems, comment out the 'discard' line in /etc/inetd.conf and
restart the inetd process - Under Windows systems, set the following registry
key to 0 :
HKLM\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpDis
card Then launch cmd.exe and type : net stop simptcp net start simptcp To
restart the service.
Plugin ID:
11367
Port sd? (9876/tcp)
[-/+]
[^] Back to 163.26.60.2
[^] Back
163.26.60.3
Scan Time
Start
Fri Oct 1 07:13:16
time :
End time :
2013
Fri Oct 1 07:15:25
2013
Number of vulnerabilities
Open ports :
4
High :
0
Medium :
0
Low :
16
Remote host information
Operating
System :
Microsoft
Windows Server
2003
NetBIOS
name :
DNS name :
[^] Back to 163.26.60.3
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
[-/+]
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.3 : 163.26.60.115
163.26.60.3
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
129 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:microsoft:windows_2003_server
Following application CPE matched on the remote
system : cpe:/a:microsoft:iis:6.0 -> Microsoft Internet
Information Services (IIS) 6.0
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 75
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Microsoft Windows Server
2003 Confidence Level : 75 Method : HTTP The remote
host is running Microsoft Windows Server 2003
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1f:c6:7c:a2:91 : ASUSTek COMPUTER INC.
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The ICMP timestamps seem to be in little endian
format (not in network format) The difference
between the local and remote clocks is -150 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port dce-rpc (1025/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 1025 : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service TCP Port :
1025 IP : 163.26.60.3 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service TCP
Port : 1025 IP : 163.26.60.3
Plugin ID:
10736
Port dce-rpc (1026/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available on TCP
port 1026 : Object UUID :
a81947b2-4f02-4d17-b04a-f763f5b55c07 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Remote RPC
service TCP Port : 1026 IP : 163.26.60.3 Object UUID :
fbc2df9e-2c02-463b-894c-b14bef185d29 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Remote RPC
service TCP Port : 1026 IP : 163.26.60.3 Object UUID :
be04b764-8e1b-45dc-be6b-fcb4adabb938 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Remote RPC
service TCP Port : 1026 IP : 163.26.60.3 Object UUID :
963647fc-c042-484c-9b51-5e4e096539eb UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Remote RPC
service TCP Port : 1026 IP : 163.26.60.3
Plugin ID:
10736
Port epmap (135/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available locally :
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : dhcpcsvc
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service Windows process :
svchost.exe Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service Named pipe : DNSResolver
Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Local RPC service Named pipe :
dsrole Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Local RPC service Named pipe :
protected_storage Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Local RPC service Named pipe :
securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Local RPC service Named pipe :
audit Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : tapsrvlpc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service Annotation :
Unimodem LRPC Endpoint Type : Local RPC service
Named pipe : unimdmsvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Local RPC service
Named pipe : W32TIME_ALT Object UUID :
23cb5420-4496-463d-bbc4-dd4e82e58da2 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe :
OLEB6D72FF6C93E4AE8AAAFBD64E5BD Object
UUID : 23cb5420-4496-463d-bbc4-dd4e82e58da2
UUID : 906b0ce0-c70b-1067-b317-00dd010662da,
version 1.0 Description : Distributed Transaction
Coordinator Windows process : msdtc.exe Type : Local
RPC service Named pipe : LRPC00000af0.00000001
Object UUID :
a81947b2-4f02-4d17-b04a-f763f5b55c07 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC00000570.00000001 Object UUID :
fbc2df9e-2c02-463b-894c-b14bef185d29 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC00000570.00000001 Object UUID :
be04b764-8e1b-45dc-be6b-fcb4adabb938 UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC00000570.00000001 Object UUID :
963647fc-c042-484c-9b51-5e4e096539eb UUID :
906b0ce0-c70b-1067-b317-00dd010662da, version
1.0 Description : Distributed Transaction Coordinator
Windows process : msdtc.exe Type : Local RPC service
Named pipe : LRPC00000570.00000001 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
wzcsvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEF26F56FC22A74DD3A7E811EE8C7F Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
wzcsvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEF26F56FC22A74DD3A7E811EE8C7F Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
wzcsvc Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Local RPC service Named pipe :
OLEF26F56FC22A74DD3A7E811EE8C7F Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : audit Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : securityevent Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : protected_storage Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Local RPC service Named
pipe : dsrole
Plugin ID:
10736
Port microsoft-ds? (445/tcp)
[-/+]
DCE Services Enumeration
Synopsis:
A DCE/RPC service is running on the remote host.
Description:
By sending a Lookup request to the portmapper (TCP
135 or epmapper PIPE) it was possible to enumerate
the Distributed Computing Environment (DCE)
services running on the remote port. Using this
information it is possible to connect and bind to each
service by sending an RPC request to the remote
port/pipe.
Risk factor:
None
Solution:
n/a
Plugin output:
The following DCERPC services are available
remotely : Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service Named
pipe : \PIPE\protected_storage Netbios name :
\\SAMUEL5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345678-1234-abcd-ef00-0123456789ab, version
1.0 Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe Annotation : IPSec Policy
agent endpoint Type : Remote RPC service Named
pipe : \PIPE\lsass Netbios name : \\SAMUEL5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db,
version 1.0 Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint Type : Remote
RPC service Named pipe : \pipe\tapsrv Netbios name :
\\SAMUEL5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
3473dd4d-2e88-4006-9cba-22570909dd10, version
5.0 Description : Unknown RPC service Annotation :
WinHttp Auto-Proxy Service Type : Remote RPC
service Named pipe : \PIPE\W32TIME_ALT Netbios
name : \\SAMUEL5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\SAMUEL5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\SAMUEL5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service Windows process :
svchost.exe Type : Remote RPC service Named pipe :
\PIPE\atsvc Netbios name : \\SAMUEL5 Object UUID :
00000000-0000-0000-0000-000000000000 UUID :
12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager Windows
process : lsass.exe Type : Remote RPC service Named
pipe : \PIPE\lsass Netbios name : \\SAMUEL5 Object
UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac,
version 1.0 Description : Security Account Manager
Windows process : lsass.exe Type : Remote RPC
service Named pipe : \PIPE\protected_storage Netbios
name : \\SAMUEL5
Plugin ID:
10736
Port www (80/tcp)
[-/+]
Microsoft SharePoint Server Detection
Synopsis:
The remote web server contains a document sharing
software
Description:
The remote web server is running SharePoint, a web
interface for document management. As this interface
is likely to contain sensitive information, make sure
only authorized personel can log into this site
Risk factor:
None
See also:
http://www.microsoft.com/Sharepoint/default.mspx
Solution:
Make sure the proper access controls are put in place
Plugin output:
The following instance of SharePoint was detected on
the remote host : Version : 6.0.2.6568 URL :
http://163.26.60.3/
Plugin ID:
38157
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : OPTIONS, TRACE, GET, HEAD,
POST Headers : Date: Thu, 11 Oct 2012 23:17:42 GMT
Server: Microsoft-IIS/6.0
MicrosoftSharePointTeamServices: 6.0.2.6568
X-Powered-By: ASP.NET Location: /default.aspx
Cache-Control: private Content-Length: 9
Public-Extension:
http://schemas.microsoft.com/repl-2
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : Microsoft-IIS/6.0
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.3
[^] Back
163.26.60.44
Scan Time
Start
Fri Oct 1 07:13:31
time :
End time :
2013
Fri Oct 1 07:20:39
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
2
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.44
Port general (0/tcp)
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
[-/+]
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
428 sec
Plugin ID:
19506
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
8c:89:a5:98:f9:26 : Micro-Star INT'L CO., LTD
Plugin ID:
35716
[^] Back to 163.26.60.44
[^] Back
163.26.60.49
Scan Time
Start
time :
Fri Oct 1 07:13:31
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
2
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.49
Port smb (139/tcp)
[-/+]
Microsoft Windows SMB Service Detection
Synopsis:
A file / print sharing service is listening on the remote
host.
Description:
The remote service understands the CIFS (Common
Internet File System) or Server Message Block (SMB)
protocol, used to provide shared access to files,
printers, etc between nodes on a network.
Risk factor:
None
Solution:
n/a
Plugin output:
An SMB server is running on this port.
Plugin ID:
11011
Port snmp (161/udp)
[-/+]
SNMP Protocol Version Detection
Synopsis:
This plugin reports the protocol version negotiated with the remote
SNMP agent.
Description:
By sending an SNMP 'get-next-request', it is possible to determine
the protocol version of the remote SNMP agent.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Simple_Network_Management_Protocol
Solution:
Disable the SNMP service on the remote host if you do not use it, or
filter incoming UDP packets going to this port.
Plugin output:
Nessus has negotiated SNMP communications at SNMPv1.
Plugin ID:
35296
[^] Back to 163.26.60.49
[^] Back
163.26.60.65
Scan Time
Start
Fri Oct 1 07:13:36
time :
End time :
2013
Fri Oct 1 07:18:52
2013
Number of vulnerabilities
Open ports :
4
High :
0
Medium :
0
Low :
10
Remote host information
Operating
System :
Fortigate Linux
Kernel 2.4 Linux
Kernel 2.6
NetBIOS
name :
DNS name :
[^] Back to 163.26.60.65
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.65 : 163.26.60.115
163.26.60.65
Plugin ID:
10287
[-/+]
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
316 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE's : cpe:/o:linux:linux_kernel:2.4
cpe:/o:linux:linux_kernel:2.6
Plugin ID:
45590
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Fortigate Linux Kernel 2.4
Linux Kernel 2.6 Confidence Level : 54 Method : SinFP
The remote host is running one of these operating
systems : Fortigate Linux Kernel 2.4 Linux Kernel 2.6
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:0d:e0:64:02:ff : ICPDAS Co.,LTD
Plugin ID:
35716
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
Port ndmp? (10000/tcp)
[-/+]
Unknown Service Detection: Banner Retrieval
Synopsis:
There is an unknown service running on the remote
host.
Description:
Nessus was unable to identify a service on the remote
host even though it returned a banner of some type.
Risk factor:
None
Solution:
n/a
Plugin output:
If you know what this service is and think the banner
could be used to identify it, please send a description
of the service along with the following output to
svc-signatures@nessus.org : Port : 10000 Type :
get_http Banner : 0x00: 45 72 72 6F 72 20 43 6F 6D
6D 61 6E 64 0D 0A Error Command..
Plugin ID:
11154
Port asa-appl-proto? (502/tcp)
[-/+]
Unknown Service Detection: Banner Retrieval
Synopsis:
There is an unknown service running on the remote
host.
Description:
Nessus was unable to identify a service on the remote
host even though it returned a banner of some type.
Risk factor:
None
Solution:
n/a
Plugin output:
If you know what this service is and think the banner
could be used to identify it, please send a description
of the service along with the following output to
svc-signatures@nessus.org : Port : 502 Type : help
Banner : 0x00: 48 45 4C 50 0D 04 01 01 01 00
HELP......
Plugin ID:
11154
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.0 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers :
WWW-Authenticate: Basic realm="ET-7044"
Plugin ID:
24260
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
Port distinct? (9999/tcp)
[-/+]
[^] Back to 163.26.60.65
[^] Back
163.26.60.70
Scan Time
Start
time :
Fri Oct 1 07:13:41
2013
End time :
Fri Oct 1 07:19:01
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
2
Low :
16
Remote host information
Operating
System :
NetBIOS
name :
EthernetBoard
OkiLAN 8100e
KM25BB2B
DNS name :
[^] Back to 163.26.60.70
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
[-/+]
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.70 : 163.26.60.115
163.26.60.70
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
320 sec
Plugin ID:
19506
Additional DNS Hostnames
Synopsis:
Potential virtual hosts have been detected.
Description:
Hostnames different from the current hostname have
been collected by miscellaneous plugins. Different web
servers may be hosted on name- based virtual hosts.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Virtual_hosting
Solution:
If you want to test them, re-scan using the special
vhost syntax, such as :
www.example.com[192.0.32.10]
Plugin output:
- km25bb2b
Plugin ID:
46180
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : switch Confidence level : 65
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : EthernetBoard OkiLAN
8100e Confidence Level : 65 Method : SinFP The
remote host is running EthernetBoard OkiLAN 8100e
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:c0:ee:25:bb:2b : KYOCERA CORPORATION
Plugin ID:
35716
Port netbios-ns (137/udp)
[-/+]
Windows NetBIOS / SMB Remote Host
Information Disclosure
Synopsis:
It is possible to obtain the network name of the
remote host.
Description:
The remote host listens on UDP port 137 or TCP port
445 and replies to NetBIOS nbtscan or SMB requests.
Note that this plugin gathers information to be used in
other plugins but does not itself generate a report.
Risk factor:
None
Solution:
n/a
Plugin output:
The following 5 NetBIOS names have been gathered :
KM25BB2B = Computer name KM25BB2B =
Messenger Service KM25BB2B = File Server Service
NetPrinters = Workgroup / Domain name NetPrinters
= Browser Service Elections The remote host has the
following MAC address on its adapter :
00:c0:ee:25:bb:2b
Plugin ID:
10150
Port ftp (21/tcp)
FTP Privileged Port Bounce Scan
[-/+]
Synopsis:
The remote FTP server is vulnerable to a FTP server bounce attack.
Description:
It is possible to force the remote FTP server to connect to third
parties using the PORT command. The problem allows intruders to
use your network resources to scan other hosts, making them think
the attack comes from your network.
Risk factor:
High
CVSS Base Score:7.5
CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
See also:
http://archives.neohapsis.com/archives/bugtraq/1995_3/0047.html
See also:
http://www.cert.org/advisories/CA-1997-27.html
Solution:
See the CERT advisory in the references for solutions and
workarounds .
Plugin output:
The following command, telling the server to connect to
169.254.175.112 on port 10794: PORT 169,254,175,112,42,42
produced the following output: 200 PORT command Ok.
Plugin ID:
10081
CVE:
CVE-1999-0017
BID:
126
Other references:
OSVDB:71
Anonymous FTP Enabled
Synopsis:
Anonymous logins are allowed on the remote FTP
server.
Description:
This FTP service allows anonymous logins. Any remote
user may connect and authenticate without providing
a password or unique credentials. This allows a user to
access any files made available on the FTP server.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
Solution:
Disable anonymous FTP if it is not required. Routinely
check the FTP server to ensure sensitive content is not
available.
Plugin output:
The contents of the remote FTP root are : total 0
Plugin ID:
10079
CVE:
CVE-1999-0497
Other references:
OSVDB:69
Multiple Vendor Embedded FTP Service Any
Username Authentication Bypass
Synopsis:
A random username and password can be used to
authenticate to the remote FTP server.
Description:
The FTP server running on the remote host can be
accessed using a random username and password.
Nessus has enabled some countermeasures to prevent
other plugins from reporting vulnerabilities incorrectly
because of this.
Risk factor:
Medium
CVSS Base Score:5.0
CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N
Solution:
Contact the FTP server's documentation so that the
service handles authentication requests properly.
Plugin ID:
10990
Other references:
OSVDB:813
FTP Supports Clear Text Authentication
Synopsis:
Authentication credentials might be intercepted.
Description:
The remote FTP server allows the user's name and
password to be transmitted in clear text, which could
be intercepted by a network sniffer or a
man-in-the-middle attack.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Switch to SFTP (part of the SSH suite) or FTPS (FTP
over SSL/TLS). In the latter case, configure the server
so that control connections are encrypted.
Plugin output:
This FTP server does not support 'AUTH TLS'.
Plugin ID:
34324
Other references:
CWE:522, CWE:523
FTP Server Detection
Synopsis:
An FTP server is listening on this port.
Description:
It is possible to obtain the banner of the remote FTP
server by connecting to the remote port.
Risk factor:
None
Solution:
N/A
Plugin output:
The remote FTP banner is : 220 NS-30 Ver 1.4.02 FTP
server.
Plugin ID:
10092
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An FTP server is running on this port.
Plugin ID:
22964
Port telnet (23/tcp)
[-/+]
Unencrypted Telnet Server
Synopsis:
The remote Telnet server transmits traffic in cleartext.
Description:
The remote host is running a Telnet server over an
unencrypted channel. Using Telnet over an
unencrypted channel is not recommended as logins,
passwords and commands are transferred in cleartext.
An attacker may eavesdrop on a Telnet session and
obtain credentials or other sensitive information. Use
of SSH is prefered nowadays as it protects credentials
from eavesdropping and can tunnel additional data
streams such as the X11 session.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Disable this service and use SSH instead.
Plugin output:
Nessus collected the following banner from the remote
Telnet server : ------------------------------ snip
------------------------------ NS-30 Ver 1.4.02 TELNET
server. Copyright(C)2001 KYOCERA MITA Corporation
Copyright(C)2006 Revised Edition KYOCERA MITA
Corporation All Rights Reserved. login:
------------------------------ snip
-----------------------------Plugin ID:
42263
Telnet Server Detection
Synopsis:
A Telnet server is listening on the remote port.
Description:
The remote host is running a Telnet server, a remote
terminal server.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin output:
Here is the banner from the remote Telnet server :
------------------------------ snip
------------------------------ NS-30 Ver 1.4.02 TELNET
server. Copyright(C)2001 KYOCERA MITA Corporation
Copyright(C)2006 Revised Edition KYOCERA MITA
Corporation All Rights Reserved. login:
------------------------------ snip
-----------------------------Plugin ID:
10281
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A telnet server is running on this port.
Plugin ID:
22964
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers :
Connection: close Server: NetworkScanner WebServer
Ver1.0 Cache-Control: no-cache Content-Type:
TEXT/HTML
Plugin ID:
24260
HTTP Server Type and Version
Synopsis:
A web server is running on the remote host.
Description:
This plugin attempts to determine the type and the
version of the remote web server.
Risk factor:
None
Solution:
n/a
Plugin output:
The remote web server type is : NetworkScanner
WebServer Ver1.0
Plugin ID:
10107
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.70
[^] Back
163.26.60.74
Scan Time
Start
time :
Fri Oct 1 07:13:41
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
3
High :
0
Medium :
0
Low :
15
Remote host information
Operating
System :
Linux Kernel
2.4
NetBIOS name :
DNS name :
[^] Back to 163.26.60.74
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
[-/+]
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.74 : 163.26.60.115
163.26.60.74
Plugin ID:
10287
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:linux:linux_kernel:2.4
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 70
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Linux Kernel 2.4
Confidence Level : 70 Method : SinFP The remote host
is running Linux Kernel 2.4
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:0c:2a:02:af:e6 : OCTTEL Communication Co., Ltd.
Plugin ID:
35716
IP Forwarding Enabled
Synopsis:
The remote host has IP forwarding enabled.
Description:
The remote host has IP forwarding enabled. An attacker may use this flaw to
use the to route packets through this host and potentially bypass some
firewalls / routers / NAC filtering. Unless the remote host is a router, it is
recommended that you disable IP forwarding.
Risk factor:
Low
CVSS Base Score:3.2
CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N
Solution:
On Linux, you can disable IP forwarding by doing : echo 0 >
/proc/sys/net/ipv4/ip_forward On Windows, set the key 'IPEnableRouter' to 0
under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0 For other systems, check with your vendor.
Plugin ID:
50686
CVE:
CVE-1999-0511
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
10854 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port telnet (23/tcp)
[-/+]
Unencrypted Telnet Server
Synopsis:
The remote Telnet server transmits traffic in cleartext.
Description:
The remote host is running a Telnet server over an
unencrypted channel. Using Telnet over an
unencrypted channel is not recommended as logins,
passwords and commands are transferred in cleartext.
An attacker may eavesdrop on a Telnet session and
obtain credentials or other sensitive information. Use
of SSH is prefered nowadays as it protects credentials
from eavesdropping and can tunnel additional data
streams such as the X11 session.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Disable this service and use SSH instead.
Plugin output:
Nessus collected the following banner from the remote
Telnet server : ------------------------------ snip
------------------------------ << Command Line Interface
V 2.1.7.5 >> User: ------------------------------ snip
-----------------------------Plugin ID:
42263
Telnet Server Detection
Synopsis:
A Telnet server is listening on the remote port.
Description:
The remote host is running a Telnet server, a remote
terminal server.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin output:
Here is the banner from the remote Telnet server :
------------------------------ snip
------------------------------ << Command Line Interface
V 2.1.7.5 >> User: ------------------------------ snip
-----------------------------Plugin ID:
10281
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A telnet server is running on this port.
Plugin ID:
22964
Port sip? (5060/tcp)
[-/+]
Session Initiation Protocol Detection
Synopsis:
The remote system is a SIP signaling device.
Description:
The remote system is running software that speaks the Session Initiation
Protocol. SIP is a messaging protocol to initiate communication sessions
between systems. It is a protocol used mostly in IP Telephony networks /
systems to setup, control, and teardown sessions between two or more
systems.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Session_Initiation_Protocol
Solution:
If possible, filter incoming connections to the port so that it is used by trusted
sources only.
Plugin output:
The remote service was identified as : 128
12-38-38929131-0.9.5.1.1818-PSTN404 It supports the following options :
Allow:INVITE,ACK,OPTIONS,BYE,CANCEL,INFO,PRACK,REFER,SUBSCRIBE,NO
TIFY,UPDATE
Plugin ID:
21642
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
The service closed the connection without sending any
data. It might be protected by some sort of TCP
wrapper.
Plugin ID:
22964
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.1 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers :
Connection: close Date: Sat, 01 Jan 2000 00:00:25
GMT Last-Modified: Thu, 01 Jan 1970 00:00:00 GMT
Content-Type: text/html Content-Length: 639
Plugin ID:
24260
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
[^] Back to 163.26.60.74
[^] Back
163.26.60.80
Scan Time
Start
time :
Fri Oct 1 07:13:46
2013
End time :
Fri Oct 1 07:18:15
2013
Number of vulnerabilities
Open ports :
6
High :
0
Medium :
0
Low :
22
Remote host information
Operating
System :
NetBIOS name :
DNS name :
Linux Kernel
2.4
[^] Back to 163.26.60.80
Port general (0/udp)
[-/+]
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.80 : 163.26.60.115
163.26.60.80
Plugin ID:
10287
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
269 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE : cpe:/o:linux:linux_kernel:2.4
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 70
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Linux Kernel 2.4
Confidence Level : 70 Method : SinFP The remote host
is running Linux Kernel 2.4
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:0f:3a:01:8b:35 : HISHARP
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
901 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
Port rpc-portmapper (111/tcp)
[-/+]
RPC Services Enumeration
Synopsis:
An ONC RPC service is running on the remote host.
Description:
By sending a DUMP request to the portmapper, it was
possible to enumerate the ONC RPC services running
on the remote port. Using this information, it is
possible to connect and bind to each service by
sending an RPC request to the remote port.
Risk factor:
None
Solution:
n/a
Plugin output:
The following RPC services are available on UDP port
111 : - program: 100000 (portmapper), version: 2
Plugin ID:
11111
RPC portmapper Service Detection
Synopsis:
An ONC RPC portmapper is running on the remote
host.
Description:
The RPC portmapper is running on this port. The
portmapper allows someone to get the port number of
each RPC service running on the remote host by
sending either multiple lookup requests or a DUMP
request.
Risk factor:
None
Solution:
n/a
Plugin ID:
10223
CVE:
CVE-1999-0632
RPC Services Enumeration
Synopsis:
An ONC RPC service is running on the remote host.
Description:
By sending a DUMP request to the portmapper, it was
possible to enumerate the ONC RPC services running
on the remote port. Using this information, it is
possible to connect and bind to each service by
sending an RPC request to the remote port.
Risk factor:
None
Solution:
n/a
Plugin output:
The following RPC services are available on TCP port
111 : - program: 100000 (portmapper), version: 2
Plugin ID:
11111
RPC portmapper (TCP)
Synopsis:
An ONC RPC portmapper is running on the remote
host.
Description:
The RPC portmapper is running on this port. The
portmapper allows someone to get the port number of
each RPC service running on the remote host by
sending either multiple lookup requests or a DUMP
request.
Risk factor:
None
Solution:
n/a
Plugin ID:
53335
Port ftp (21/tcp)
[-/+]
FTP Supports Clear Text Authentication
Synopsis:
Authentication credentials might be intercepted.
Description:
The remote FTP server allows the user's name and
password to be transmitted in clear text, which could
be intercepted by a network sniffer or a
man-in-the-middle attack.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Switch to SFTP (part of the SSH suite) or FTPS (FTP
over SSL/TLS). In the latter case, configure the server
so that control connections are encrypted.
Plugin output:
This FTP server does not support 'AUTH TLS'.
Plugin ID:
34324
Other references:
CWE:522, CWE:523
FTP Server Detection
Synopsis:
An FTP server is listening on this port.
Description:
It is possible to obtain the banner of the remote FTP
server by connecting to the remote port.
Risk factor:
None
Solution:
N/A
Plugin output:
The remote FTP banner is : 220---------- Welcome to
Pure-FTPd ---------- 220-You are user number 1 of 50
allowed. 220-Local time is now 07:00. Server port: 21.
220-This is a private system - No anonymous login 220
You will be disconnected after 15 minutes of inactivity.
Plugin ID:
10092
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
An FTP server is running on this port.
Plugin ID:
22964
Port telnet (23/tcp)
[-/+]
Unencrypted Telnet Server
Synopsis:
The remote Telnet server transmits traffic in cleartext.
Description:
The remote host is running a Telnet server over an
unencrypted channel. Using Telnet over an
unencrypted channel is not recommended as logins,
passwords and commands are transferred in cleartext.
An attacker may eavesdrop on a Telnet session and
obtain credentials or other sensitive information. Use
of SSH is prefered nowadays as it protects credentials
from eavesdropping and can tunnel additional data
streams such as the X11 session.
Risk factor:
Low
CVSS Base Score:2.6
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N
Solution:
Disable this service and use SSH instead.
Plugin output:
Nessus collected the following banner from the remote
Telnet server : ------------------------------ snip
------------------------------ Welcome to DVR-166 Board.
dvr login: ------------------------------ snip
-----------------------------Plugin ID:
42263
Telnet Server Detection
Synopsis:
A Telnet server is listening on the remote port.
Description:
The remote host is running a Telnet server, a remote
terminal server.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin output:
Here is the banner from the remote Telnet server :
------------------------------ snip
------------------------------ Welcome to DVR-166 Board.
dvr login: ------------------------------ snip
-----------------------------Plugin ID:
10281
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A telnet server is running on this port.
Plugin ID:
22964
Port irc-serv? (6666/tcp)
[-/+]
Port tftp (69/udp)
[-/+]
TFTP Daemon Detection
Synopsis:
A TFTP server is listening on the remote port.
Description:
The remote host is running a TFTP (Trivial File
Transfer Protocol) daemon. TFTP is often used by
routers and diskless hosts to retrieve their
configuration. It is also used by worms to propagate.
Risk factor:
None
Solution:
Disable this service if you do not use it.
Plugin ID:
11819
Port www (80/tcp)
[-/+]
HyperText Transfer Protocol (HTTP)
Information
Synopsis:
Some information about the remote HTTP
configuration can be extracted.
Description:
This test gives some information about the remote
HTTP protocol - the version used, whether HTTP
Keep-Alive and HTTP pipelining are enabled, etc... This
test is informational only and does not denote any
security problem.
Risk factor:
None
Solution:
n/a
Plugin output:
Protocol version : HTTP/1.0 SSL : no Keep-Alive : no
Options allowed : (Not implemented) Headers :
Content-type: text/html Date: Thu, 11 Oct 2012
23:02:26 GMT Connection: close Last-Modified: Fri, 23
Mar 2007 02:42:09 GMT Content-length: 3737
Plugin ID:
24260
Service Detection
Synopsis:
The remote service could be identified.
Description:
It was possible to identify the remote service by its
banner or by looking at the error message it sends
when it receives an HTTP request.
Risk factor:
None
Solution:
n/a
Plugin output:
A web server is running on this port.
Plugin ID:
22964
Port ddi-tcp-1? (8888/tcp)
[-/+]
Unknown Service Detection: Banner Retrieval
Synopsis:
There is an unknown service running on the remote
host.
Description:
Nessus was unable to identify a service on the remote
host even though it returned a banner of some type.
Risk factor:
None
Solution:
n/a
Plugin output:
If you know what this service is and think the banner
could be used to identify it, please send a description
of the service along with the following output to
svc-signatures@nessus.org : Port : 8888 Type :
spontaneous Banner : 0x00: 22 74 65 73 74 22 0A
"test".
Plugin ID:
11154
[^] Back to 163.26.60.80
[^] Back
163.26.60.84
Scan Time
Start
time :
Fri Oct 1 07:13:46
2013
End time :
Fri Oct 1 07:21:09
2013
Number of vulnerabilities
Open ports :
1
High :
0
Medium :
0
Low :
7
Remote host information
Operating
System :
Microsoft
Windows 2000
Microsoft
Windows XP
NetBIOS
name :
DNS name :
[^] Back to 163.26.60.84
Port general (0/udp)
Traceroute Information
Synopsis:
It was possible to obtain traceroute information.
Description:
Makes a traceroute to the remote host.
Risk factor:
None
Solution:
n/a
Plugin output:
For your information, here is the traceroute from
163.26.60.115 to 163.26.60.84 : 163.26.60.115
163.26.60.84
Plugin ID:
10287
Nessus Scan Information
Synopsis:
[-/+]
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
443 sec
Plugin ID:
19506
Common Platform Enumeration (CPE)
Synopsis:
It is possible to enumerate CPE names that matched
on the remote system.
Description:
By using information obtained from a Nessus scan, this
plugin reports CPE (Common Platform Enumeration)
matches for various hardware and software products
found on a host. Note that if an official CPE is not
available for the product, this plugin computes the
best possible CPE based on the information available
from the scan.
Risk factor:
None
See also:
http://cpe.mitre.org/
Solution:
n/a
Plugin output:
The remote operating system matched the following
CPE's : cpe:/o:microsoft:windows_2000
cpe:/o:microsoft:windows_xp
Plugin ID:
45590
Device Type
Synopsis:
It is possible to guess the remote device type.
Description:
Based on the remote operating system, it is possible to
determine what the remote system type is (eg: a
printer, router, general-purpose computer, etc).
Risk factor:
None
Solution:
n/a
Plugin output:
Remote device type : general-purpose Confidence
level : 54
Plugin ID:
54615
OS Identification
Synopsis:
It is possible to guess the remote operating system.
Description:
Using a combination of remote probes, (TCP/IP, SMB,
HTTP, NTP, SNMP, etc...) it is possible to guess the
name of the remote operating system in use, and
sometimes its version.
Risk factor:
None
Solution:
n/a
Plugin output:
Remote operating system : Microsoft Windows 2000
Microsoft Windows XP Confidence Level : 54 Method :
SinFP The remote host is running one of these
operating systems : Microsoft Windows 2000 Microsoft
Windows XP
Plugin ID:
11936
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:14:2a:69:c9:29 : Elitegroup Computer System Co.,
Ltd
Plugin ID:
35716
TCP/IP Timestamps Supported
Synopsis:
The remote service implements TCP timestamps.
Description:
The remote host implements TCP timestamps, as
defined by RFC1323. A side effect of this feature is
that the uptime of the remote host can sometimes be
computed.
Risk factor:
None
See also:
http://www.ietf.org/rfc/rfc1323.txt
Solution:
n/a
Plugin ID:
25220
Port commplex-main? (5000/tcp)
[-/+]
[^] Back to 163.26.60.84
[^] Back
163.26.60.88
Scan Time
Start
time :
Fri Oct 1 07:13:51
2013
End time :
Fri Oct 1 07:20:59
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
3
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.88
Port general (0/tcp)
[-/+]
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
428 sec
Plugin ID:
19506
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1a:1e:cc:a6:cf : Aruba Networks
Plugin ID:
35716
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
-111 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
[^] Back to 163.26.60.88
[^] Back
163.26.60.89
Scan Time
Start
time :
Fri Oct 1 07:13:51
2013
End time :
Fri Oct 1 07:21:01
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
3
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.89
Port general (0/tcp)
[-/+]
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
430 sec
Plugin ID:
19506
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1a:1e:cc:a7:9e : Aruba Networks
Plugin ID:
35716
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
-112 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
[^] Back to 163.26.60.89
[^] Back
163.26.60.90
Scan Time
Start
time :
Fri Oct 1 07:13:51
2013
End time :
Fri Oct 1 07:21:02
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
3
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.90
Port general (0/tcp)
[-/+]
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
431 sec
Plugin ID:
19506
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1a:1e:ce:e4:99 : Aruba Networks
Plugin ID:
35716
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
-111 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
[^] Back to 163.26.60.90
[^] Back
163.26.60.93
Scan Time
Start
time :
Fri Oct 1 07:13:56
2013
End time :
Fri Oct 1 07:21:06
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
3
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.93
Port general (0/tcp)
[-/+]
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:13 Scan duration :
430 sec
Plugin ID:
19506
Ethernet Card Manufacturer Detection
Synopsis:
The manufacturer can be deduced from the Ethernet
OUI.
Description:
Each ethernet MAC address starts with a 24-bit
'Organizationally Unique Identifier'. These OUI are
registered by IEEE.
Risk factor:
None
See also:
http://standards.ieee.org/faqs/OUI.html
See also:
http://standards.ieee.org/regauth/oui/index.shtml
Solution:
n/a
Plugin output:
The following card manufacturers were identified :
00:1a:1e:ce:da:a2 : Aruba Networks
Plugin ID:
35716
ICMP Timestamp Request Remote Date
Disclosure
Synopsis:
It is possible to determine the exact time set on the
remote host.
Description:
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the date that
is set on the targeted machine, which may assist an
unauthenticated, remote attacker in defeating
time-based authentication protocols. Timestamps
returned from machines running Windows Vista / 7 /
2008 / 2008 R2 are deliberately incorrect, but usually
within 1000 seconds of the actual system time.
Risk factor:
None
Solution:
Filter out the ICMP timestamp requests (13), and the
outgoing ICMP timestamp replies (14).
Plugin output:
The difference between the local and remote clocks is
-111 seconds.
Plugin ID:
10114
CVE:
CVE-1999-0524
Other references:
OSVDB:94, CWE:200
[^] Back to 163.26.60.93
[^] Back
163.26.60.96
Scan Time
Start
time :
Fri Oct 1 07:14:06
2013
End time :
Fri Oct 1 07:23:15
2013
Number of vulnerabilities
Open ports :
0
High :
0
Medium :
0
Low :
2
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.96
Port smb (139/tcp)
[-/+]
Microsoft Windows SMB Service Detection
Synopsis:
A file / print sharing service is listening on the remote
host.
Description:
The remote service understands the CIFS (Common
Internet File System) or Server Message Block (SMB)
protocol, used to provide shared access to files,
printers, etc between nodes on a network.
Risk factor:
None
Solution:
n/a
Plugin output:
An SMB server is running on this port.
Plugin ID:
11011
Port snmp (161/udp)
[-/+]
SNMP Protocol Version Detection
Synopsis:
This plugin reports the protocol version negotiated with the remote
SNMP agent.
Description:
By sending an SNMP 'get-next-request', it is possible to determine
the protocol version of the remote SNMP agent.
Risk factor:
None
See also:
http://en.wikipedia.org/wiki/Simple_Network_Management_Protocol
Solution:
Disable the SNMP service on the remote host if you do not use it, or
filter incoming UDP packets going to this port.
Plugin output:
Nessus has negotiated SNMP communications at SNMPv1.
Plugin ID:
35296
[^] Back to 163.26.60.96
[^] Back
163.26.60.97
Scan Time
Start
time :
Fri Oct 1 07:14:06
2013
End time :
Fri Oct 1 07:14:31
2013
Number of vulnerabilities
Open ports :
8
High :
0
Medium :
0
Low :
2
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to 163.26.60.97
Port general (0/tcp)
[-/+]
Nessus Scan Information
Synopsis:
Information about the Nessus scan.
Description:
This script displays, for each tested host, information
about the scan itself : - The version of the plugin set The type of plugin feed (HomeFeed or
ProfessionalFeed) - The version of the Nessus Engine The port scanner(s) used - The port range scanned Whether credentialed or third-party patch
management checks are possible - The date of the
scan - The duration of the scan - The number of hosts
scanned in parallel - The number of checks done in
parallel
Risk factor:
None
Solution:
n/a
Plugin output:
Information about this scan : Nessus version : 4.4.1
(Build 15078) (Nessus 5.0.1 is available - consider
upgrading) Plugin feed version : 201210082315 Type
of plugin feed : HomeFeed (Non-commercial use only)
Scanner IP : 163.26.60.115 Port scanner(s) :
nessus_syn_scanner Port range : default Thorough
tests : no Experimental tests : no Paranoia level : 1
Report Verbosity : 1 Safe checks : yes Optimize the
test : yes Credentialed checks : no Patch management
checks : None CGI scanning : disabled Web application
tests : disabled Max hosts : 80 Max checks : 5 Recv
timeout : 5 Backports : None Allow post-scan editing:
Yes Scan Start Date : 2012/10/12 7:14 Scan duration :
25 sec
Plugin ID:
19506
Do not scan printers
Synopsis:
The remote host appears to be a fragile device and will
not be scanned.
Description:
The remote host appears to be a network printer,
multi-function device, or other fragile device. Such
devices often react very poorly when scanned. To
avoid problems, Nessus has marked the remote host
as 'Dead' and will not scan it.
Risk factor:
None
Solution:
If you are not concerned about such behavior, enable
the 'Scan Network Printers' setting under the 'Do not
scan fragile devices' advanced settings block and
re-run the scan.
Plugin output:
SNMP reports it as KYOCERA MITA Printing.
Plugin ID:
11933
Port ftp? (21/tcp)
[-/+]
Port printer? (515/tcp)
[-/+]
Port ipp? (631/tcp)
[-/+]
Port http? (80/tcp)
[-/+]
Port pdl-datastream? (9100/tcp)
[-/+]
Port bacula-dir? (9101/tcp)
[-/+]
Port bacula-fd? (9102/tcp)
[-/+]
Port bacula-sd? (9103/tcp)
[-/+]
[^] Back to 163.26.60.97
[^] Back
SCAN-ERROR
Scan Time
Number of vulnerabilities
Open ports :
0
High :
1
Medium :
0
Low :
0
Remote host information
Operating System :
NetBIOS name :
DNS name :
[^] Back to SCAN-ERROR
Port general (0/tcp)
[-/+]
Scan Error
Too many live hosts scanned in a row while on a
HomeFeed - please upgrade to a ProfessionalFeed
Plugin ID:
19506
[^] Back to SCAN-ERROR