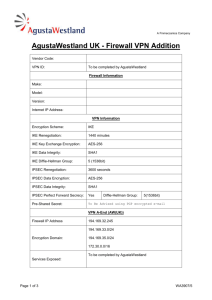
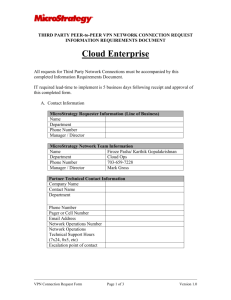
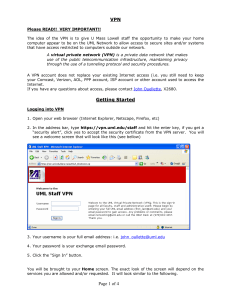
SonicOS Log Event Reference Guide
advertisement

Using the SonicOS Log Event Reference Guide This reference guide lists and describes SonicOS log event messages. Reference a log event message by using the alphabetical index of log event messages. This document contains the following sections: • “Log > View” section on page 2 • “Log > Categories” section on page 5 • “Log > Syslog” section on page 9 • “Log > Automation” section on page 10 • “Log > Name Resolution” section on page 14 • “Log > Reports” section on page 16 • “Log > ViewPoint” section on page 17 • “Index of Log Event Messages” section on page 19 • “Index of Syslog Tag Field Description” section on page 57 SonicOS Log Event Reference Guide 1 Log > View Log > View The SonicWALL security appliance maintains an Event log for tracking potential security threats. This log can be viewed in the Log > View page, or it can be automatically sent to an e-mail address for convenience and archiving. The log is displayed in a table and can be sorted by column. The SonicWALL security appliance can alert you of important events, such as an attack to the SonicWALL security appliance. Alerts are immediately e-mailed, either to an e-mail address or to an e-mail pager. Each log entry contains the date and time of the event and a brief message describing the event. Log View Table The log is displayed in a table and is sortable by column. The log table columns include: • Time - the date and time of the event. • Priority - the level of priority associated with your log event. Syslog uses eight categories to characterize messages – in descending order of severity, the categories include: – Emergency – Alert – Critical – Error – Warning – Notice – Informational – Debug Specify a priority level on a SonicWALL security appliance on the Log > Categories page to log messages for that priority level, plus all messages tagged with a higher severity. For example, select ‘error’ as the priority level to log all messages tagged as ‘error,’ as well as any messages tagged with ‘critical,’ ‘alert,’ and ‘emergency.’ Select ‘debug’ to log all messages. Note 2 Refer to Log Event Messages section for more information on your specific log event. • Category - the type of traffic, such as Network Access or Authenticated Access. • Message - provides description of the event. • Source - displays source network and IP address. • Destination - displays the destination network and IP address. • Notes - provides additional information about the event. • Rule - notes Network Access Rule affected by event. SonicOS Log Event Reference Guide Log > View Navigating and Sorting Log View Table Entries The Log View table provides easy pagination for viewing large numbers of log events. You can navigate these log events by using the navigation control bar located at the top right of the Log View table. Navigation control bar includes four buttons. The far left button displays the first page of the table. The far right button displays the last page. The inside left and right arrow buttons moved the previous or next page respectively. You can sort the entries in the table by clicking on the column header. The entries are sorted by ascending or descending order. The arrow to the right of the column entry indicates the sorting status. A down arrow means ascending order. An up arrow indicates a descending order. Refresh To update log messages, clicking the Refresh button near the top right corner of the page. Clear Log To delete the contents of the log, click the Clear Log button near the top right corner of the page. Export Log To export the contents of the log to a defined destination, click the Export Log button below the filter table.You can export log content to two formats: • Plain text format--Used in log and alert e-mail. • Comma-separated value (CSV) format--Used for importing into Excel or other presentation development applications. E-mail Log If you have configured the SonicWALL security appliance to e-mail log files, clicking E-mail Log near the top right corner of the page sends the current log files to the e-mail address specified in the Log > Automation > E-mail section. Note The SonicWALL security appliance can alert you of important events, such as an attack to the SonicWALL security appliance. Alerts are immediately sent via e-mail, either to an e-mail address or to an e-mail pager. For sending alerts, you must enter your e-mail address and server information in the Log > Automation page. SonicOS Log Event Reference Guide 3 Log > View Filtering Log Records Viewed You can filter the results to display only event logs matching certain criteria. You can filter by Priority, Category, Source (IP or Interface), and Destination (IP or Interface). Step 1 Enter your filter criteria in the Log View Settings table. Step 2 The fields you enter values into are combined into a search string with a logical AND. For example, if you select an interface for Source and for Destination, the search string will look for connections matching: Source interface AND Destination interface Step 3 Check the Group Filters box next to any two or more criteria to combine them with a logical OR. For example, if you enter values for Source IP, Destination IP, and Protocol, and check Group Filters next to Source IP and Destination IP, the search string will look for connections matching: (Source IP OR Destination IP) AND Protocol Step 4 Click Apply Filter to apply the filter immediately to the Log View Settings table. Click Reset to clear the filter and display the unfiltered results again. The following example filters for log events resulting from traffic from the WAN to the LAN: Log Event Messages For a complete reference guide of log event messages, refer to the “Log Event Message Index” section on page 20. 4 SonicOS Log Event Reference Guide Log > Categories Log > Categories This guide provides configuration tasks to enable you to categorize and customize the logging functions on your SonicWALL security appliance for troubleshooting and diagnostics. Note You can extend your SonicWALL security appliance log reporting capabilities by using SonicWALL ViewPoint. ViewPoint is a Web-based graphical reporting tool for detailed and comprehensive reports. For more information on the SonicWALL ViewPoint reporting tool, refer to www.sonicwall.com. Log Severity/Priority This section provides information on configuring the level of priority log messages are captured and corresponding alert messages are sent through e-mail for notification. Logging Level The Logging Level control filters events by priority. Events of equal of greater priority are passed, and events of lower priority are dropped. The Logging Level menu includes the following priority scale items from highest to lowest priority: • Emergency (highest priority) • Alert • Critical • Error • Warning • Notice • Informational • Debug (lowest priority) Alert Level The Alert Level control determines how E-mail Alerts are sent. An event of equal or greater priority causes an E-mail alert to be issued. Lower priority events do not cause an alert to be sent. Events are pre-filtered by the Logging Level control, so if the Logging Level control is set to a higher priority than that of the Alert Level control, only alerts at the Logging Level or higher are sent. Alert levels include: • None (disables e-mail alerts) • Emergency (highest priority) • Alert • Critical • Error • Warning (lowest priority) SonicOS Log Event Reference Guide 5 Log > Categories Log Redundancy Filter The Log Redundancy Filter allows you to define the time in seconds that the same attack is logged on the Log > View page as a single entry in the SonicWALL log. Various attacks are often rapidly repeated, which can quickly fill up a log if each attack is logged. The Log Redundancy Filter has a default setting of 60 seconds. Alert Redundancy Filter The Alert Redundancy Filter allows you to define the time in seconds that the same attack is logged on the Log > View page as a single entry in the SonicWALL log before an alert is issued. The Alert Redundancy Filter has a default setting of 900 seconds. Log Categories SonicWALL security appliances provide automatic attack protection against well known exploits. The majority of these legacy attacks were identified by telltale IP or TCP/UDP characteristics, and recognition was limited to a set of fixed layer 3 and layer 4 values. As the breadth and sophistication of attacks evolved, it has become essential to dig deeper into the traffic, and to develop the sort of adaptability that could keep pace with the new threats. All SonicWALL security appliances, even those running SonicWALL IPS, continue to recognize these legacy port and protocol types of attacks. The current behavior on all SonicWALL security appliances devices is to automatically and holistically prevent these legacy attacks, meaning that it is not possible to disable prevention of these attacks either individually or globally. SonicWALL security appliances now include an expanded list of attack categories that can be logged. The View Style menu provides the following three log category views: • All Categories - Displays both Legacy Categories and Expanded Categories. • Legacy Categories - Displays log categories carried over from earlier SonicWALL log event categories. • Expanded Categories - Displays the expanded listing of categories that includes the older Legacy Categories log events rearranged into the new structure. The following table describes both the Legacy and Extended log categories. Log Type Category Description 802.11 Management Legacy Logs WLAN IEEE 802.11 connections. Advanced Routing Expanded Logs messages related to RIPv2 and OSPF routing events. Attacks Legacy Logs messages showing Denial of Service attacks, such as SYN Flood, Ping of Death, and IP spoofing Authenticated Access Expanded Logs administrator, user, and guest account activity Blocked Java, etc. Legacy Logs Java, ActiveX, and Cookies blocked by the SonicWALL security appliance. Blocked Web Sites Legacy Logs Web sites or newsgroups blocked by the Content Filter List or by customized filtering. BOOTP Expanded Logs BOOTP activity Crypto Test Expanded Logs crypto algorithm and hardware testing 6 SonicOS Log Event Reference Guide Log > Categories Log Type Category Description DDNS Expanded Logs Dynamic DNS activity Denied LAN IP Legacy Logs all LAN IP addresses denied by the SonicWALL security appliance. DHCP Client Expanded Logs DHCP client protocol activity DHCP Relay Expanded Logs DHCP central and remote gateway activity Dropped ICMP Legacy Logs blocked incoming ICMP packets. Dropped TCP Legacy Logs blocked incoming TCP connections. Dropped UDP Legacy Logs blocked incoming UDP packets. Firewall Event Extended Logs internal firewall activity Firewall Hardware Extended Logs firewall hardware error events Firewall Logging Extended Logs general events and errors Firewall Rule Extended Logs firewall rule modifications GMS Extended Logs GMS status event High Availability Extended Logs High Availability activity IPcomp Extended Logs IP compression activity Intrusion Prevention Extended Logs intrusion prevention related activity L2TP Client Extended Logs L2TP client activity L2TP Server Extended Logs L2TP server activity Multicast Extended Logs multicast IGMP activity Network Extended Logs network ARP, fragmentation, and MTU activity Network Access Extended Logs network and firewall protocol access activity Network Debug Legacy Logs NetBIOS broadcasts, ARP resolution problems, and NAT resolution problems. Also, detailed messages for VPN connections are displayed to assist the network administrator with troubleshooting problems with active VPN tunnels. Network Debug information is intended for experienced network administrators. Network Traffic Expanded Logs network traffic reporting events PPP Extended Logs generic PPP activity PPP Dial-Up Extended Logs PPP dial-up activity PPPoE Extended Logs PPPoE activity PPTP Extended Logs PPTP activity RBL Extended Logs real-time black list activity RIP Extended Logs RIP activity Remote Authentication Extended Logs RADIUS and LDAP server activity Security Services Extended Logs security services activity SonicPoint Extended Logs SonicPoint activity System Errors Legacy Logs problems with DNS or e-mail. System Maintenance Legacy Logs general system activity, such as system activations. User Activity Legacy Logs successful and unsuccessful log in attempts. VOIP Extended Logs VoIP H.323/RAS, H.323/H.225, and H.323/H.245 activity SonicOS Log Event Reference Guide 7 Log > Categories Log Type Category Description VPN Extended Logs VPN activity VPN Client Extended Logs VPN client activity VPN IKE Extended Logs VPN IKE activity VPN IPsec Extended Logs VPN IPSec activity VPN PKI Extended Logs VPN PKI activity VPN Tunnel Status Legacy Logs status information on VPN tunnels. WAN Failover Extended Logs WAN failover activity Wireless Extended Logs wireless activity Wlan IDS Extended Logs WLAN IDS activity Managing Log Categories The Log Categories table displays log category information organized into the following columns: • Category - Displays log category name. • Description - Provides description of the log category activity type. • Log - Provides checkbox for enabling/disabling the display of the log events in on the Log > View page. • Alerts - Provides checkbox for enabling/disabling the sending of alerts for the category. • Syslog - Provides checkbox for enabling/disabling the capture of the log events into the SonicWALL security appliance Syslog. • Event Count - Displays the number of events for that category. Clicking the Refresh button updates these numbers. You can sort the log categories in the Log Categories table by clicking on the column header. For example, clicking on the Category header sorts the log categories in descending order from the default ascending order. An up or down arrow to the left of the column name indicates whether the column is assorted in ascending or descending order. You can enable or disable Log, Alerts, and Syslog on a category by category basis by clicking on the check box for the category in the table. You can enable or disable Log, Alerts, and Syslog for all categories by clicking the checkbox on the column header. 8 SonicOS Log Event Reference Guide Log > Syslog Log > Syslog In addition to the standard event log, the SonicWALL security appliance can send a detailed log to an external Syslog server. The SonicWALL Syslog captures all log activity and includes every connection source and destination IP address, IP service, and number of bytes transferred. The SonicWALL Syslog support requires an external server running a Syslog daemon on UDP Port 514. Syslog Analyzers such as SonicWALL ViewPoint or WebTrends Firewall Suite can be used to sort, analyze, and graph the Syslog data. Messages from the SonicWALL security appliance are then sent to the server(s). Up to three Syslog server IP addresses can be added.Syslog Settings Syslog Facility • Note See RCF 3164 - The BSD Syslog Protocol for more information. • Note Syslog Facility - Allows you to select the facilities and severities of the messages based on the syslog protocol. Override Syslog Settings with ViewPoint Settings - Check this box to override Syslog settings, if you’re using SonicWALL ViewPoint for your reporting solution. For more information on SonicWALL ViewPoint, go to http://www.sonicwall.com. – Syslog Event Redundancy Filter (seconds) - This setting prevents repetitive messages from being written to Syslog. If duplicate events occur during the period specified in the Syslog Event Redundancy Rate field, they are not written to Syslog as unique events. Instead, the additional events are counted, and then at the end of the period, a message is written to the Syslog that includes the number of times the event occurred. The Syslog Event Redundancy Filter default value is 60 seconds and the maximum value is 86,400 seconds (24 hours). Setting this value to 0 seconds sends all Syslog messages without filtering. – Syslog Format - You can choose the format of the Syslog to be Default or WebTrends. If you select WebTrends, however, you must have WebTrends software installed on your system. Note If the SonicWALL security appliance is managed by SonicWALL GMS, the Syslog Server fields cannot be configured by the administrator of the SonicWALL security appliance. • Enable Event Rate Limiting - This control allows you to enable rate limiting of events to prevent the internal or external logging mechanism from being overwhelmed by log events. • Enable Data Rate Limiting - This control allows you to enable rate limiting of data to prevent the internal or external logging mechanism from being overwhelmed by log events. SonicOS Log Event Reference Guide 9 Log > Automation Syslog Servers Adding a Syslog Server To add syslog servers to the SonicWALL security appliance Step 1 Click Add. The Add Syslog Server window is displayed. Step 2 Type the Syslog server name or IP address in the Name or IP Address field. Messages from the SonicWALL security appliance are then sent to the servers. Step 3 If your syslog is not using the default port of 514, type the port number in the Port Number field. Step 4 Click OK. Step 5 Click Accept to save all Syslog Server settings. Log > Automation The Log > Automation page includes settings for configuring the SonicWALL to send log files using e-mail and configuring mail server settings. E-mail Log Automation • Send Log to E-mail address - Enter your e-mail address (username@mydomain.com) in this field to receive the event log via e-mail. Once sent, the log is cleared from the SonicWALL memory. If this field is left blank, the log is not e-mailed. • Send Alerts to E-mail address - Enter your e-mail address (username@mydomain.com) in the Send alerts to field to be immediately e-mailed when attacks or system errors occur. Type a standard e-mail address or an e-mail paging service. If this field is left blank, e-mail alert messages are not sent. • Send Log - Determines the frequency of sending log files. The options are When Full, Weekly, or Daily. If the Weekly or Daily option is selected, then select the day of the week the log is sent in the every menu and the time of day in 24-hour format in the At field. • Email Format - Specifies whether log emails will be sent in Plain Text or HTML format. Mail Server Settings The mail server settings allow you to specify the name or IP address of your mail server, the from e-mail address, and authentication method. Note 10 • Mail Server (name or IP address) - Enter the IP address or FQDN of the e-mail server used to send your log e-mails in this field. • From E-mail Address - Enter the E-mail address you want to display in the From field of the message. • Authentication Method - You can use the default None item or select POP Before SMTP. If the Mail Server (name or IP address) is left blank, log and alert messages are not emailed. SonicOS Log Event Reference Guide Log > Automation Deep Packet Forensics SonicWALL UTM appliances have configurable deep-packet classification capabilities that intersect with forensic and content-management products. While the SonicWALL can reliably detect and prevent any ‘interesting-content’ events, it can only provide a record of the occurrence, but not the actual data of the event. Of equal importance are diagnostic applications where the interesting-content is traffic that is being unpredictably handled or inexplicably dropped. Although the SonicWALL can achieve interesting-content using our Enhanced packet capture diagnostic tool, data-recorders are application-specific appliances designed to record all the packets on a network. They are highly optimized for this task, and can record network traffic without dropping a single packet. While data-recorders are good at recording data, they lack the sort of deep-packet inspection intelligence afforded by IPS/GAV/ASPY/AF. Consider the minimal requirements of effective data analysis: • Reliable storage of data • Effective indexing of data • Classification of interesting-content Together, a UTM device (a SonicWALL appliance) and data-recorder (a Solera Networks appliance) satisfy the requirements to offer outstanding forensic and data-leakage capabilities. Distributed Event Detection and Replay The Solera appliance can search its data-repository, while also allowing the administrator to define “interesting-content” events on the SonicWALL. The level of logging detail and frequency of the logging can be configured by the administrator. Nearly all events include Source IP, Source Port, Destination IP, Destination Port, and Time. SonicOS Enhanced has an extensive set of log events, including: • Debug/Informational Events—Connection setup/tear down • User-events—Administrative access, single sign-on activity, user logins, content filtering details • Firewall Rule/Policy Events—Access to and from particular IP:Port combinations, also identifiable by time • Interesting-content at the Network or Application Layer—Port-scans, SYN floods, DPI or AF signature/policy hits The following is an example of the process of distributed event detection and replay: 1. The administrator defines the event trigger. For example, an Application Firewall policy is defined to detect and log the transmission of an official document: SonicOS Log Event Reference Guide 11 Log > Automation 2. A user (at IP address 192.168.19.1) on the network retrieves the file. 3. The event is logged by the SonicWALL. 4. The administrator selects the Recorder icon from the left column of the log entry. Icon/link only appears in the logs when a NPCS is defined on the SonicWALL (e.g. IP: [192.168.169.100], Port: [443]). The defined NPCS appliance will be the link’s target. The link will include the query string parameters defining the desired connection. 5. The NPCS will (optionally) authenticate the user session. 6. The requested data will be presented to the client as a .cap file, and can be saved or viewed on the local machine. Methods of Access The client and NPCS must be able to reach one another. Usually, this means the client and the NPCS will be in the same physical location, both connected to the SonicWALL appliance. In any case, the client will be able to directly reach the NPCS, or will be able to reach the NPCS through the SonicWALL. Administrators in a remote location will require some method of VPN connectivity to the internal network. Access from a centralized GMS console will have similar requirements. Log Persistence SonicOS currently allocates 32K to a rolling log buffer. When the log becomes full, it can be emailed to a defined recipient and flushed, or it can simply be flushed. Emailing provides a simple version of logging persistence, while GMS provides a more reliable and scalable method. By offering the administrator the option to deliver logs as either plain-text or HTML, the administrator has an easy method to review and replay events logged. 12 SonicOS Log Event Reference Guide Log > Automation GMS To provide the ability to identify and view events across an entire enterprise, a GMS update will be required. Device-specific interesting-content events at the GMS console appear in Reports > Log Viewer Search page, but are also found throughout the various reports, such as Top Intrusions Over Time. Solera Capture Stack Solera Networks makes a series of appliances of varying capacities and speeds designed to capture, archive, and regenerate network traffic. The Solera Networks Network Packet Capture System (NPCS) provides utilities that allow the captured data to be accessed in time sequenced playback, that is, analysis of captured data can be performed on a live network via NPCS while the device is actively capturing and archiving data. SonicOS Log Event Reference Guide 13 Log > Name Resolution To configure your SonicWALL appliance with Solera select the Enable Solera Capture Stack Integration option. Configure the following options: • Server - Select the host for the Solera server. You can dynamically create the host by selecting Create New Host... • Protocol - Select either HTTP or HTTPS. • Port - Specify the port number for connecting to the Solera server. • Interface(s) - Specify which interfaces you want to transmit data for to the Solera server. • User (optional) - Enter the username, if required. • Password (optional) - Enter the password, if required. • Confirm Password - Confirm the password. – Mask Password - Leave this enabled to send the password as encrypted text. Log > Name Resolution The Log > Name Resolution page includes settings for configuring the name servers used to resolve IP addresses and server names in the log reports. The security appliance uses a DNS server or NetBIOS to resolve all IP addresses in log reports into server names. It stores the names/address pairs in a cache, to assist with future lookups. You can clear the cache by clicking Reset Name Cache in the top of the Log > Name Resolution page. 14 SonicOS Log Event Reference Guide Log > Name Resolution Selecting Name Resolution Settings The security appliance can use DNS, NetBIOS, or both to resolve IP addresses and server names. In the Name Resolution Method list, select: • None: The security appliance will not attempt to resolve IP addresses and Names in the log reports. • DNS: The security appliance will use the DNS server you specify to resolve addresses and names. • NetBIOS: The security appliance will use NetBIOS to resolve addresses and names. If you select NetBIOS, no further configuration is necessary. • DNS then NetBIOS: The security appliance will first use the DNS server you specify to resolve addresses and names. If it cannot resolve the name, it will try again with NetBIOS. Specifying the DNS Server To choose specific DNS servers or use the same servers as the WAN zone, perform the following steps: Step 1 Select Specify DNS Servers Manually or Inherit DNS Settings Dynamically from WAN Zone. The second choice is selected by default. Step 2 If you selected to specify a DNS server, enter the IP address for at least one DNS server on your network. You can enter up to three servers. Step 3 Click Accept in the top right corner of the Log > Name Resolution page to make your changes take effect. SonicOS Log Event Reference Guide 15 Log > Reports Log > Reports The SonicWALL security appliance can perform a rolling analysis of the event log to show the top 25 most frequently accessed Web sites, the top 25 users of bandwidth by IP address, and the top 25 services consuming the most bandwidth. You can generate these reports from the Log > Reports page. Note SonicWALL ViewPoint provides a comprehensive Web-based reporting solution for SonicWALL security appliances. For more information on SonicWALL ViewPoint, go to http://www.sonicwall.com Data Collection The Reports window includes the following functions and commands: • Start Data Collection Click Start Data Collection to begin log analysis. When log analysis is enabled, the button label changes to Stop Data Collection. • Reset Data Click Reset Data to clear the report statistics and begin a new sample period. The sample period is also reset when data collection is stopped or started, and when the SonicWALL security appliance is restarted. View Data Select the desired report from the Report to view menu. The options are Web Site Hits, Bandwidth Usage by IP Address, and Bandwidth Usage by Service. These reports are explained below. Click Refresh Data to update the report. The length of time analyzed by the report is displayed in the Current Sample Period. Web Site Hits Selecting Web Site Hits from the Report to view menu displays a table showing the URLs for the 25 most frequently accessed Web sites and the number of hits to a site during the current sample period. The Web Site Hits report ensures that the majority of Web access is to appropriate Web sites. If leisure, sports, or other inappropriate sites appear in the Web Site Hits Report, you can choose to block the sites. For information on blocking inappropriate Web sites, see . Click on the name of a Web site to open that site in a new window. Bandwidth Usage by IP Address Selecting Bandwidth Usage by IP Address from the Report to view menu displays a table showing the IP address of the 25 top users of Internet bandwidth and the number of megabytes transmitted during the current sample period. 16 SonicOS Log Event Reference Guide Log > ViewPoint Bandwidth Usage by Service Selecting Bandwidth Usage by Service from the Report to view menu displays a table showing the name of the 25 top Internet services, such as HTTP, FTP, RealAudio, etc., and the number of megabytes received from the service during the current sample period. The Bandwidth Usage by Service report shows whether the services being used are appropriate for your organization. If services such as video or push broadcasts are consuming a large portion of the available bandwidth, you can choose to block these services. Log > ViewPoint SonicWALL ViewPoint is a Web-based graphical reporting tool that provides unprecedented security awareness and control over your network environment through detailed and comprehensive reports of your security and network activities. ViewPoint’s broad reporting capabilities allow administrators to easily monitor network access and Internet usage, enhance security, assess risks, understand more about employee Internet use and productivity, and anticipate future bandwidth needs. ViewPoint creates dynamic, real-time and historical network summaries, providing a flexible, comprehensive view of network events and activities. Reports are based on syslog data streams received from each SonicWALL appliance through LAN, Wireless LAN, WAN or VPN connections. With ViewPoint, your organization can generate individual or aggregate reports about virtually any aspect of appliance activity, including individual user or group usage patterns, evens on specific appliances or groups of appliances, types and times of attacks, resource consumption and constraints, and more. For more information on SonicWALL ViewPoint, go to http://www.sonicwall.com. For complete SonicWALL ViewPoint documentation, go to the SonicWALL documentation Web site at http://www.sonicwall.com/us/support/3340.html. SonicOS Log Event Reference Guide 17 Log > ViewPoint Activating ViewPoint The Log > ViewPoint page allows you to activate the ViewPoint license directly from the SonicWALL Management Interface using two methods. If you received a license activation key, enter the activation key in the Enter upgrade key field, and click Accept. Warning You must have a mysonicwall.com account and your SonicWALL security appliance must be registered to activate SonicWALL ViewPoint for your SonicWALl security appliance. Step 1 Click the Upgrade link in Click here to Upgrade on the Log > ViewPoint page. The mysonicwall.com Login page is displayed. Step 2 Enter your mysonicwall.com account username and password in the User Name and Password fields, then click Submit. The System > Licenses page is displayed. If your SonicWALL security appliance is already connected to your mysonicwall.com account, the System > Licenses page appears after you click the SonicWALL Content Filtering Subscription link. Step 3 Click Activate or Renew in the Manage Service column in the Manage Services Online table. Type in the Activation Key in the New License Key field and click Submit. Step 4 If you activated SonicWALL ViewPoint at mysonicwall.com, the SonicWALL ViewPoint activation is automatically enabled on your SonicWALL within 24-hours or you can click the Synchronize button on the Security Services > Summary page to update your SonicWALL. Enabling ViewPoint Settings Once you have installed the SonicWALL ViewPoint software, you can point the SonicWALL security appliance to the server running ViewPoint, perform the following steps: Step 1 Check the Enable ViewPoint Settings checkbox in the Syslog Servers section of the Log > ViewPoint page. Step 2 Click the Add button. The Add Syslog Server window is displayed. Step 3 Enter the IP address or FQDN of the SonicWALL ViewPoint server in the Name or IP Address field. Step 4 Enter the port number for the SonicWALL ViewPoint server traffic in the Port field or use the default port number. Step 5 Click Accept. Note The Override Syslog Settings with ViewPoint Settings control on the Log > Syslog page is automatically checked when you enable ViewPoint from the Log > ViewPoint page. The IP address or FQDN you entered in the Add Syslog Server window is also displayed on the Log > Syslog page as well as in the Syslog Servers table on the Log > ViewPoint page. Clicking the Edit icon displays the Add Syslog Server window for editing the ViewPoint server information. Clicking the Delete icon, deletes the ViewPoint syslog server entry. 18 SonicOS Log Event Reference Guide Index of Log Event Messages Index of Log Event Messages This section contains a list of log event messages for all SonicWALL Firmware and SonicOS Software Releases, ordered alphabetically. Use your web browser’s Find function to search for a command. Log Event Message Symbols Key Log Event Message Symbol Description Context %s Ethernet Port Down Represents a character string. [WAN | LAN | DMZ] Ethernet Port Down The cache is full; %u open connections; some will be dropped Represents a numerical string. The cache is full; [40,000] open connections; some will be dropped TCP IP Layered-Data Packet Processing and SonicOS Log Event Handling In specific cases of multi-layer packet processing, a TCP connection initially logged as "open," will be rejected by a deeper layer of packet processing. In these cases, the connection request has not been forwarded by the SonicWALL security appliance, and the initial Connection Open SonicOS log event message should be ignored in favor of the TCP Connection Dropped log event message. Each log event message described in the following table provides the following log event details: • SonicOS Category—Displays the SonicOS Software category event type. • Legacy Category—Displays the SonicWALL Firmware Software category event type. • Priority Level—Displays the level of urgency of the log event message. • Log Message ID Number—Displays the ID number of the log event message. • SNMP Trap Type—Displays the SNMP Trap ID number of the log event message. SonicOS Log Event Reference Guide 19 Index of Log Event Messages Log Event Message Index Log Event Message Network Security Appliance activated Log cleared Log successfully sent via email Log full; deactivating Network Security Appliance New URL List loaded No new URL List available Problem loading the URL List; check Filter settings Problem loading the URL List; check your DNS server Problem sending log email; check log settings Restarting Network Security Appliance; dumping log to email Web site access denied Newsgroup access denied Web site access allowed Newsgroup access allowed ActiveX access denied Java access denied ActiveX or Java archive access denied Cookie removed Ping of death dropped IP spoof dropped User logged out - user disconnect detected (heartbeat timer expired) Possible SYN flood attack detected Land attack dropped Fragmented packet dropped Administrator login allowed Administrator login denied due to bad credentials User login from an internal zone allowed User login denied due to bad credentials User login denied due to bad credentials Login screen timed out 20 SonicOS Log Event Reference Guide New Category Firewall Event Firewall Logging Firewall Logging Firewall Logging Legacy Category Maintenance Maintenance Maintenance System Error Priority Alert Information Information Error ID 4 5 6 7 SNMP Trap Type ------601 Security Services Security Services Security Services Maintenance Maintenance System Error Information Information Error 8 9 10 ----602 Security Services System Error Error 11 603 Firewall Logging System Error Warning 12 604 Firewall Event Maintenance Information 13 --- Network Access Network Access Network Access Network Access Network Access Network Access Network Access Network Access Intrusion Detection Intrusion Detection Authenticate Access Intrusion Detection Intrusion Detection Network Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Blocked Sites Blocked Sites Blocked Sites Blocked Sites Blocked Code Blocked Code Blocked Code Blocked Code Attack Attack User Activity Error Notice Notice Notice Notice Notice Notice Notice Alert Alert Information 14 15 16 17 18 19 20 21 22 23 24 701 702 703 704 --------501 502 --- Attack Attack TCP | UDP | ICMP User Activity Warning Alert Notice Information 25 27 28 29 503 505 ----- Attack Alert 30 560 User Activity Information 31 --- User Activity Information 32 --- User Activity Information 33 --- User Activity Information 34 --- Index of Log Event Messages Log Event Message Administrator login denied from %s; logins disabled from this interface TCP connection dropped UDP packet dropped ICMP packet dropped due to policy PPTP packet dropped IPsec packet dropped Unknown protocol dropped IPsec packet dropped; waiting for pending IPsec connection IPsec connection interrupt NAT could not remap incoming packet ARP timeout Broadcast packet dropped No ICMP redirect sent Out-of-order command packet dropped Failure to add data channel RealAudio decode failure Duplicate packet dropped No HOST tag found in HTTP request The cache is full; %u open connections; some will be dropped License exceeded: Connection dropped because too many IP addresses are in use on your LAN Access to proxy server denied Diagnostic Code E Dynamic IPsec client connected Received fragmented packet or fragmentation needed Diagnostic Code D Illegal IPsec SPI Unknown IPsec SPI IPsec Authentication Failed IPsec Decryption Failed Incompatible IPsec Security Association IPsec packet from or to an illegal host NetBus attack dropped Back Orifice attack dropped Net Spy attack dropped Sub Seven attack dropped Ripper attack dropped Striker attack dropped Senna Spy attack dropped New Category Authenticate Access Network Access Network Access Network Access Network Access Network Access Network Access Network Access Legacy Category Priority Attack Alert ID 35 SNMP Trap Type 506 TCP UDP ICMP TCP | UDP | ICMP TCP | UDP | ICMP Debug Debug Notice Notice Notice Notice Notice Notice Debug 36 37 38 39 40 41 42 --------------- Network Access Unused Network Network Access Unused Network Access Unused Unused Network Access Network Access Firewall Event Debug System Error Debug Debug Debug Debug Debug Debug Debug Debug System Error Debug Error Debug Debug Debug Debug Debug Debug Debug Debug Error 43 44 45 46 47 48 49 50 51 52 53 --606 ----------------607 Firewall Event System Error Error 58 608 Network Access VPN IPsec VPN IPsec Network Blocked Sites System Error User Activity Debug Notice Error Information Debug 60 61 62 63 705 609 ----- Firewall Hardware VPN IPsec VPN IPsec VPN IPsec VPN IPsec VPN IPsec VPN IPsec Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection System Error User Activity Attack Attack Attack User Activity Attack Attack Attack Attack Attack Attack Attack Attack Error Information Error Error Error Information Error Alert Alert Alert Alert Alert Alert Alert 64 65 66 67 68 69 70 72 73 74 75 76 77 78 610 --507 508 509 --510 511 512 513 514 515 516 517 SonicOS Log Event Reference Guide 21 Index of Log Event Messages Log Event Message Priority attack dropped Ini Killer attack dropped Smurf Amplification attack dropped Possible port scan detected Probable port scan detected Failed to resolve name IKE Responder: Accepting IPsec proposal (Phase 2) IKE Responder: IPsec proposal does not match (Phase 2) IKE negotiation complete. Adding IPsec SA. (Phase 2) Starting IKE negotiation Deleting IPsec SA for destination Deleting IPsec SA Diagnostic Code A Diagnostic Code B Diagnostic Code C Status #Web site hit Connection Opened Retransmitting DHCP DISCOVER. Retransmitting DHCP REQUEST (Requesting). Retransmitting DHCP REQUEST (Renewing). Retransmitting DHCP REQUEST (Rebinding). Retransmitting DHCP REQUEST (Rebooting). Retransmitting DHCP REQUEST (Verifying). Sending DHCP DISCOVER. DHCP Server not available. Did not get any DHCP OFFER. Got DHCP OFFER. Selecting. Sending DHCP REQUEST. DHCP Client did not get DHCP ACK. DHCP Client got NACK. DHCP Client got ACK from server. DHCP Client is declining address offered by the server. DHCP Client sending REQUEST and going to REBIND state. 22 SonicOS Log Event Reference Guide New Category Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Network VPN IKE Legacy Category Attack Attack Attack Attack Attack Maintenance User Activity Priority Alert Alert Alert Alert Alert Information Information ID 79 80 81 82 83 84 87 SNMP Trap Type 518 519 520 521 522 ----- VPN IKE User Activity Warning 88 523 VPN IKE User Activity Information 89 --- VPN IKE VPN IKE VPN IKE Firewall Hardware Firewall Hardware Firewall Hardware GMS Network Traffic Network Traffic DHCP Client DHCP Client User Activity User Activity User Activity System Error System Error System Error Maintenance Connection Traffic Connection Maintenance Maintenance Information Information Information Error Error Error Emergency Information Information Information Information 90 91 92 93 94 95 96 97 98 99 100 ------611 612 613 ----------- DHCP Client Maintenance Information 101 --- DHCP Client Maintenance Information 102 --- DHCP Client Maintenance Information 103 --- DHCP Client DHCP Client DHCP Client Maintenance Maintenance Maintenance Information Information Information 104 105 106 ------- DHCP Client DHCP Client DHCP Client DHCP Client DHCP Client DHCP Client Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Information Information Information Information Information Information 107 108 109 110 111 112 ------------- DHCP Client Maintenance Information 113 --- Index of Log Event Messages Log Event Message DHCP Client sending REQUEST and going to RENEW state. Sending DHCP REQUEST (Renewing). Sending DHCP REQUEST (Rebinding). Sending DHCP REQUEST (Rebooting). Sending DHCP REQUEST (Verifying). DHCP Client failed to verify and lease has expired. Go to INIT state. DHCP Client failed to verify and lease is still valid. Go to BOUND state. DHCP Client got a new IP address lease. Sending DHCP RELEASE. Access attempt from host without Anti-Virus agent installed Anti-Virus agent out-of-date on host Received AV Alert: %s Starting PPPoE discovery PPPoE LCP Link Up PPPoE LCP Link Down PPPoE terminated PPPoE Network Connected PPPoE Network Disconnected PPPoE discovery process complete PPPoE starting CHAP Authentication PPPoE starting PAP Authentication PPPoE CHAP Authentication Failed PPPoE PAP Authentication Failed Wan IP Changed XAUTH Succeeded with VPN client XAUTH Failed with VPN client, Authentication failure XAUTH Failed with VPN client, Cannot Contact RADIUS Server Log Debug Add an attack message Primary firewall has transitioned to Active Backup firewall has transitioned to Active Primary firewall has transitioned to Idle Backup firewall has transitioned to Idle Primary missed heartbeats from Backup Backup missed heartbeats from Primary Primary received error signal from Backup Backup received error signal from Primary Backup firewall being preempted by Primary New Category DHCP Client Legacy Category Priority Maintenance Information ID 114 SNMP Trap Type --- DHCP Client DHCP Client DHCP Client DHCP Client DHCP Client Maintenance Maintenance Maintenance Maintenance Maintenance Information Information Information Information Information 115 116 117 118 119 ----------- DHCP Client Maintenance Information 120 --- DHCP Client DHCP Client Security Services Maintenance Maintenance Maintenance Information Information Information 121 122 123 ------- Security Services Security Services PPPoE PPPoE PPPoE PPPoE PPPoE PPPoE PPPoE PPPoE PPPoE PPPoE PPPoE Firewall Event VPN Client VPN Client Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance System Error User Activity User Activity Information Warning Information Information Information Information Information Information Information Information Information Information Information Warning Information Error 124 125 127 128 129 130 131 132 133 134 135 136 137 138 139 140 --524 ----------------------636 ----- VPN Client User Activity Information 141 --- Firewall Event Firewall Event High Availability High Availability High Availability High Availability High Availability High Availability High Availability High Availability High Availability Debug Attack Maintenance Maintenance System Error Maintenance System Error System Error System Error System Error System Error Error Error Alert Alert Alert Alert Error Error Error Error Error 142 143 144 145 146 147 148 149 150 151 152 --525 ----614 --615 616 617 618 619 SonicOS Log Event Reference Guide 23 Index of Log Event Messages New Category High Availability High Availability Legacy Category Priority System Error Error Maintenance Information ID 153 154 SNMP Trap Type 620 --- High Availability Maintenance Information 155 --- High Availability High Availability High Availability Security Services Maintenance Maintenance System Error Maintenance Information Information Error Warning 156 157 158 159 ----662 526 High Availability Maintenance Information 160 --- High Availability Maintenance Information 161 --- High Availability High Availability Firewall Hardware Intrusion Detection PPPoE PPPoE Maintenance Maintenance System Error Attack Maintenance Maintenance Information Information Error Alert Information Information 162 163 164 165 166 167 ----621 527 ----- PPPoE PPPoE Maintenance Maintenance Information Information 168 169 ----- High Availability System Error Error 170 622 VPN IKE Network Access Network Access Information Notice Notice 172 173 174 ------- Notice 175 --- Intrusion Detection Intrusion Detection Intrusion Detection VPN IPsec Network Network Debug LAN TCP LAN UDP | LAN TCP LAN ICMP | LAN TCP Attack Attack Attack Attack Debug User Activity Alert Alert Alert Alert Debug Information 177 178 179 180 181 182 528 529 530 531 ----- Security Services System Error Error 183 623 Security Services System Error Error 184 624 Security Services System Error Error 185 625 Log Event Message Primary firewall preempting Backup Active Backup detects Active Primary: Backup going Idle Imported HA hardware ID did not match this firewall Discovered HA Backup Firewall HA Peer Firewall Synchronized Error synchronizing HA peer firewall (%s) Received AV Alert: Your Network Anti-Virus subscription has expired. %s Primary received heartbeat from wrong source Backup received heartbeat from wrong source HA packet processing error Heartbeat received from incompatible source Diagnostic Code F Forbidden E-Mail attachment disabled PPPoE PAP Authentication success. PPPoE PAP Authentication Failed. Please verify PPPoE username and password Disconnecting PPPoE due to traffic timeout No response from ISP Disconnecting PPPoE. Backup going Active in preempt mode after reboot VPN Log Debug TCP connection from LAN denied UDP packet from LAN dropped ICMP packet from LAN dropped Network Access Probable TCP FIN scan detected Probable TCP XMAS scan detected Probable TCP NULL scan detected IPsec Replay Detected TCP FIN packet dropped Received a path MTU icmp message from router/gateway Problem loading the URL List; Appliance not registered. Problem loading the URL List; Subscription expired. Problem loading the URL List; Try loading it again. 24 SonicOS Log Event Reference Guide Index of Log Event Messages Log Event Message Problem loading the URL List; Retrying later. Problem loading the URL List; Flash write failure. Received a path MTU icmp message from router/gateway The loaded content URL List has expired. Error setting the IP address of the backup, please manually set to backup LAN IP Error updating HA peer configuration Fraudulent Microsoft certificate found; access denied VPN TCP SYN VPN TCP FIN VPN TCP PSH Content filter subscription expired. New firmware available. CLI administrator login allowed CLI administrator login denied due to bad credentials L2TP Tunnel Negotiation Started L2TP Session Negotiation Started L2TP Max Retransmission Exceeded L2TP Tunnel Established L2TP Tunnel Disconnect from Remote L2TP Session Established L2TP Session Disconnect from Remote L2TP PPP Negotiation Started L2TP LCP Down L2TP PPP Session Up L2TP PPP Down L2TP PPP Authentication Failed L2TP LCP Up L2TP Disconnect Initiated by the User Disconnecting L2TP Tunnel due to traffic timeout L2TP Connect Initiated by the User L2TP PPP link down Primary WAN link down, Primary going Idle Backup WAN link down, Primary going Active Primary WAN link down, Backup going Active Primary WAN link up, preempting Backup New Category Security Services Security Services Legacy Category Priority System Error Error System Error Error ID 186 187 SNMP Trap Type 626 627 Network User Activity Information 188 --- Security Services High Availability System Error System Error Error Error 190 191 628 629 High Availability Intrusion Detection System Error Attack Error Error 192 193 630 532 VPN VPN VPN Security Services Firewall Event Authenticate Access Authenticate Access L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client L2TP Client VPN Statistics VPN Statistics VPN Statistics System Error Maintenance User Activity Information Information Information Error Information Information 194 195 196 197 198 199 ------631 ----- User Activity Warning 200 --- Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Information Information Information Information Information Information Information Information Information Information Information Information Information Information Information 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 ------------------------------- L2TP Client L2TP Client High Availability High Availability Maintenance Maintenance Maintenance System Error Information Information Information Error 216 217 218 219 ------633 High Availability System Error Error 220 634 High Availability Maintenance Information 221 --- SonicOS Log Event Reference Guide 25 Index of Log Event Messages Log Event Message DHCP RELEASE relayed to Central Gateway DHCP lease relayed to local device DHCP RELEASE received from remote device DHCP lease relayed to remote device DHCP lease to LAN device conflicts with remote device, deleting remote IP entry WARNING: DHCP lease relayed from Central Gateway conflicts with IP in Static Devices list DHCP lease dropped. Lease from Central Gateway conflicts with Relay IP IP spoof detected on packet to Central Gateway, packet dropped Request for Relay IP Table from Central Gateway Requesting Relay IP Table from Remote Gateway Sent Relay IP Table to Central Gateway Obtained Relay IP Table from Remote Gateway Failed to synchronize Relay IP Table VPN zone administrator login allowed WAN zone administrator login allowed VPN zone remote user login allowed WAN zone remote user login allowed NAT Discovery : Peer IPsec Security Gateway behind a NAT/NAPT Device NAT Discovery : Local IPsec Security Gateway behind a NAT/NAPT Device NAT Discovery : No NAT/NAPT device detected between IPsec Security gateways NAT Discovery : Peer IPsec Security Gateway doesn't support VPN NAT Traversal User login denied - RADIUS authentication failure User login denied - RADIUS server timeout User login denied - RADIUS configuration error 26 SonicOS Log Event Reference Guide New Category DHCP Relay Legacy Category Priority Maintenance Information ID 222 SNMP Trap Type --- DHCP Relay DHCP Relay Maintenance Debug Information Information 223 224 ----- DHCP Relay DHCP Relay Debug Maintenance Information Information 225 226 ----- DHCP Relay Maintenance Information 227 --- DHCP Relay Maintenance Warning 228 --- DHCP Relay Attack Error 229 533 DHCP Relay Maintenance Information 230 --- DHCP Relay Maintenance Information 231 --- DHCP Relay DHCP Relay Maintenance Maintenance Information Information 232 233 ----- DHCP Relay Authenticate Access Authenticate Access Authenticate Access Authenticate Access VPN IKE System Error User Activity Warning Information 234 235 632 --- User Activity Information 236 --- User Activity Information 237 --- User Activity Information 238 --- User Activity Information 239 --- VPN IKE User Activity Information 240 --- VPN IKE User Activity Information 241 --- VPN IKE User Activity Information 242 --- RADIUS User Activity Information 243 --- RADIUS RADIUS User Activity User Activity Warning Warning 244 245 ----- Index of Log Event Messages Log Event Message User login denied - User has no privileges for login from that location IPsec packet from an illegal host Forbidden E-Mail attachment deleted IKE Responder: Mode %d - not tunnel mode IKE Responder: No matching Phase 1 ID found for proposed remote network IKE Responder: Proposed remote network is 0.0.0.0 but not DHCP relay nor default route IKE Responder: No match for proposed remote network address IKE Responder: Default LAN gateway is set but peer is not proposing to use this SA as a default route IKE Responder: Tunnel terminates outside firewall but proposed local network is not NAT public address IKE Responder: Tunnel terminates inside firewall but proposed local network is not inside firewall IKE Responder: Tunnel terminates on DMZ but proposed local network is on LAN IKE Responder: Tunnel terminates on LAN but proposed local network is on DMZ IKE Responder: AH Perfect Forward Secrecy mismatch IKE Responder: ESP Perfect Forward Secrecy mismatch IKE Responder: Algorithms and/or keys do not match Administrator logged out Administrator logged out - inactivity timer expired User logged out User logged out - max session time exceeded User logged out - inactivity timer expired NAT device may not support IPsec AH passthrough TCP Xmas Tree dropped CFL auto-download disabled, time problem detected Requesting CRL from New Category Authenticate Access VPN IPsec Intrusion Detection VPN IKE VPN IKE Legacy Category Priority User Activity Information ID 246 SNMP Trap Type --- Maintenance Attack User Activity User Activity Information Error Warning Warning 247 248 249 250 --534 535 536 VPN IKE User Activity Warning 251 537 VPN IKE User Activity Warning 252 538 VPN IKE User Activity Warning 253 539 VPN IKE User Activity Warning 254 540 VPN IKE User Activity Warning 255 541 VPN IKE User Activity Warning 256 542 VPN IKE User Activity Warning 257 543 VPN IKE User Activity Warning 258 544 VPN IKE User Activity Warning 259 545 VPN IKE User Activity Warning 260 546 Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access VPN IPsec User Activity Information 261 --- User Activity Information 262 --- User Activity Information 263 --- User Activity Information 264 --- User Activity Information 265 --- Maintenance Information 266 --- Intrusion Detection Security Services Attack Maintenance Alert Information 267 268 547 --- VPN PKI User Activity Information 269 --- SonicOS Log Event Reference Guide 27 Index of Log Event Messages Log Event Message CRL loaded from Failed to get CRL from Not enough memory to hold the CRL Connection timed out Cannot connect to the CRL server Unknown reason Failed to Process CRL from Bad CRL format Issuer match failed Certificate on Revoked list(CRL) No Certificate for PPP Dial-Up: Dialing: %s PPP Dial-Up: No dialtone detected - check phone-line connection PPP Dial-Up: No link carrier detected - check phone number PPP Dial-Up: Dialed number is busy PPP Dial-Up: Dialed number did not answer PPP Dial-Up: Connected at %s bps - starting PPP PPP Dial-Up: Unknown dialing failure PPP Dial-Up: Link carrier lost PPP: Authentication successful PPP: PAP Authentication failed - check username / password PPP: CHAP authentication failed - check username / password PPP: MS-CHAP authentication failed - check username / password PPP: Starting MS-CHAP authentication PPP: Starting CHAP authentication PPP: Starting PAP authentication PPP Dial-Up: PPP negotiation failed disconnecting PPP Dial-Up: Idle time limit exceeded disconnecting PPP Dial-Up: Failed to get IP address PPP Dial-Up: Received new IP address PPP Dial-Up: PPP link established PPP Dial-Up: PPP link down PPP Dial-Up: Shutting down link PPP Dial-Up: Initialization : %s PPP Dial-Up: User requested disconnect PPP Dial-Up: User requested connect 28 SonicOS Log Event Reference Guide New Category VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI PPP Dial Up PPP Dial Up Legacy Category User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity Priority Information Alert Warning Alert Alert Error Alert Alert Alert Alert Alert Information Information ID 270 271 272 273 274 275 276 277 278 279 280 281 282 SNMP Trap Type --------------------------- PPP Dial Up User Activity Information 283 --- PPP Dial Up PPP Dial Up PPP Dial Up User Activity User Activity User Activity Information Information Information 284 285 286 ------- PPP Dial Up PPP Dial Up PPP PPP User Activity User Activity ----- Information Information Information Information 287 288 289 290 --------- PPP --- Information 291 --- PPP --- Information 292 --- PPP PPP PPP PPP Dial Up ------User Activity Information Information Information Information 293 294 295 296 --------- PPP Dial Up User Activity Information 297 --- PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up User Activity User Activity User Activity User Activity User Activity User Activity User Activity User Activity Information Information Information Information Information Information Information Information 298 299 300 301 302 303 304 305 ----------------- Index of Log Event Messages New Category PPP Dial Up WAN Failover L2TP Server L2TP Server L2TP Server Legacy Category User Activity System Error Maintenance Maintenance Maintenance Priority Information Warning Information Information Information ID 306 307 308 309 310 SNMP Trap Type --639 ------- L2TP Server Maintenance Information 311 --- L2TP Server L2TP Server Maintenance Maintenance Information Information 312 313 ----- L2TP Server Maintenance Information 314 --- L2TP Server Maintenance Information 315 --- L2TP Server Maintenance Information 316 --- L2TP Server Maintenance Information 317 --- L2TP Server Maintenance Information 318 --- L2TP Server Maintenance Information 319 --- L2TP Server Maintenance Information 320 --- PPP Dial Up User Activity Information 321 --- PPP Dial Up User Activity Information 322 --- PPP Dial Up User Activity Information 323 --- PPP Dial Up Firewall Event Maintenance System Error Information Error 324 325 --635 WAN Failover PPP Dial Up System Error User Activity Alert Information 326 327 637 --- Authenticate Access User login failure rate exceeded - logins from Authenticate user IP address denied Access PPP Dial-Up: The profile in use disabled PPP Dial Up VPN networking. PPP Dial-Up: VPN networking restored. PPP Dial Up %s Ethernet Port Up Firewall Event %s Ethernet Port Down Firewall Event Maintenance Information 328 --- Attack Error 329 561 Maintenance Information 330 --- Maintenance System Error System Error Information Warning Error 331 332 333 --640 641 Log Event Message PPP Dial-Up: Connect request canceled The network connection in use is %s L2TP Server : L2TP Tunnel Established. L2TP Server : L2TP Session Established. L2TP Server : L2TP PPP Session Established. L2TP Server: RADIUS/LDAP reports Authentication Failure L2TP Server: Local Authentication Failure L2TP Server: RADIUS/LDAP server not assigned IP address L2TP Server: No IP address available in the Local IP Pool L2TP Server: L2TP Tunnel Disconnect from the Remote. L2TP Server: L2TP Session Disconnect from the Remote. L2TP Server: L2TP Remote terminated the PPP session L2TP Server: Local Authentication Success. L2TP Server: RADIUS/LDAP Authentication Success L2TP Server: Keep alive Failure. Closing Tunnel PPP Dial-Up: Manual intervention needed. Check Primary Profile or Profile details PPP Dial-Up: Trying to failover but Primary Profile is manual PPP Dial-Up: Startup without Ethernet cable, will try to dial on outbound traffic PPP Dial-Up: Dial initiated by %s The current WAN interface is not ready to route packets. Probing failure on %s PPP Dial-Up: Maximum connection time exceeded - disconnecting Administrator name changed SonicOS Log Event Reference Guide 29 Index of Log Event Messages Log Event Message L2TP Server: Call Disconnect from Remote. L2TP Server: Tunnel Disconnect from Remote. L2TP Server : Deleting the Tunnel L2TP Server : Deleting the L2TP active Session L2TP Server : Retransmission Timeout, Deleting the Tunnel NAT translated packet exceeds size limit, packet dropped HTTP management port has changed HTTPS management port has changed IKE Responder: Mode %d - not transport mode. Xauth is required but not supported by peer. L2TP Server : Access from L2TP VPN Client Privilege not enabled for Radius Users. L2TP Server : User Name authentication Failure locally. IKE Responder: Tunnel terminates outside firewall but proposed remote network is not NAT public address IKE Initiator: Start Quick Mode (Phase 2). Port configured to receive IPsec protocol ONLY; drop packet received in the clear Imported VPN SA is invalid - disabled IPsec SA lifetime expired. IKE SA lifetime expired. IKE Initiator: Start Main Mode negotiation (Phase 1) IKE Responder: Received Quick Mode Request (Phase 2) IKE Initiator: Main Mode complete (Phase 1) IKE Initiator: Aggressive Mode complete (Phase 1). IKE Responder: Received Main Mode request (Phase 1) IKE Responder: Received Aggressive Mode request (Phase 1) IKE Responder: Main Mode complete (Phase 1) IKE Initiator: Start Aggressive Mode negotiation (Phase 1) Entering FIPS ERROR state Crypto DES test failed Crypto DH test failed 30 SonicOS Log Event Reference Guide New Category L2TP Server L2TP Server Legacy Category Priority Maintenance Information Maintenance Information ID 334 335 SNMP Trap Type ----- L2TP Server L2TP Server Maintenance Maintenance Information Information 336 337 ----- L2TP Server Maintenance Information 338 --- Network Debug Debug 339 --- Firewall Event Firewall Event VPN IKE Maintenance Maintenance Debug Information Information Warning 340 341 342 ------- L2TP Server Maintenance Information 343 --- L2TP Server Maintenance Information 344 --- VPN IKE User Activity Warning 345 548 VPN IKE Network Access User Activity Information TCP | UDP | ICMP Warning 346 347 ----- Firewall Event VPN IPsec VPN IKE VPN IKE Maintenance User Activity User Activity User Activity Warning Information Information Information 348 349 350 351 --------- VPN IKE User Activity Information 352 --- VPN IKE VPN IKE User Activity User Activity Information Information 353 354 ----- VPN IKE User Activity Information 355 --- VPN IKE User Activity Information 356 --- VPN IKE User Activity Information 357 --- VPN IKE User Activity Information 358 --- Crypto Test Crypto Test Crypto Test Maintenance Maintenance Maintenance Error Error Error 359 360 361 ------- Index of Log Event Messages Log Event Message Crypto Hmac-MD5 fest failed Crypto Hmac-Sha1 test failed Crypto RSA test failed Crypto Sha1 test failed Crypto hardware DES test failed Crypto hardware 3DES test failed Crypto hardware DES with SHA test failed Crypto Hardware 3DES with SHA test failed Crypto MD5 test failed VPN Client Policy Provisioning IKE Initiator: Accepting IPsec proposal (Phase 2) IKE Responder: Aggressive Mode complete (Phase 1) Error initializing Hardware acceleration for VPN PPTP Control Connection Negotiation Started PPTP Session Negotiation Started PPTP Max Retransmission Exceeded PPTP Control Connection Established PPTP Tunnel Disconnect from Remote PPTP Session Established PPTP Session Disconnect from Remote PPTP PPP Negotiation Started PPTP LCP Down PPTP PPP Session Up PPTP PPP Down PPTP PPP Authentication Failed PPTP LCP Up PPTP Disconnect Initiated by the User Disconnecting PPTP Tunnel due to traffic timeout PPTP Connect Initiated by the User PPTP PPP link down PPTP starting CHAP Authentication PPTP starting PAP Authentication PPTP CHAP Authentication Failed. Please verify PPTP username and password PPTP PAP Authentication Failed PPTP PAP Authentication success. PPTP PAP Authentication Failed. Please verify PPTP username and password PPTP PPP Link Up New Category Crypto Test Crypto Test Crypto Test Crypto Test Crypto Test Crypto Test Crypto Test Crypto Test Crypto Test VPN Client VPN IKE Legacy Category Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance User Activity User Activity Priority Error Error Error Error Error Error Error Error Error Information Information ID 362 363 364 365 366 367 368 369 370 371 372 SNMP Trap Type ----------------------- VPN IKE User Activity Information 373 --- Firewall Hardware Maintenance Error 374 --- PPTP Maintenance Information 375 --- PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP PPTP Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Information Information Information Information Information Information Information Information Information Information Information Information Information Information 376 377 378 379 380 381 382 383 384 385 386 387 388 389 ----------------------------- PPTP PPTP PPTP PPTP PPTP Maintenance Maintenance Maintenance Maintenance Maintenance Information Information Information Information Information 390 391 392 393 394 ----------- PPTP PPTP PPTP Maintenance Maintenance Maintenance Information Information Information 395 396 397 ------- PPTP Maintenance Information 398 --- SonicOS Log Event Reference Guide 31 Index of Log Event Messages Log Event Message PPTP PPP Link down PPTP PPP Link Finished Received notify. NO_PROPOSAL_CHOSEN IKE Responder: IKE proposal does not match (Phase 1) IKE negotiation aborted due to timeout Failed payload verification after decryption; possible preshared key mismatch Failed payload validation Received packet retransmission. Drop duplicate packet SA is disabled. Check VPN SA settings Anti-Virus Licenses Exceeded Received notify: ISAKMP_AUTH_FAILED Computed hash does not match hash received from peer; preshared key mismatch Received notify: PAYLOAD_MALFORMED Received IPsec SA delete request Received IKE SA delete request Received notify: INVALID_COOKIES Received notify: RESPONDER_LIFETIME Received notify: INVALID_SPI PKI Error: IKE Responder: Proposed local network is 0.0.0.0 but SA has no LAN Default Gateway RIP disabled on interface %s RIPv1 enabled on interface %s RIPv2 enabled on interface %s RIPv2 compatibility (broadcast) mode enabled on interface %s RIP disabled on DMZ interface RIPv1 enabled on DMZ interface RIPv2 enabled on DMZ interface RIPv2 compatibility (broadcast) mode enabled on DMZ interface IPsecTunnel status changed Source routed IP packet dropped No response from server to Echo Requests, disconnecting PPTP Tunnel No response from PPTP server to control connection requests No response from PPTP server to call requests 32 SonicOS Log Event Reference Guide New Category PPTP PPTP VPN IKE VPN IKE Legacy Category Maintenance Maintenance User Activity User Activity Priority Information Information Warning Warning ID 399 400 401 402 SNMP Trap Type --------- VPN IKE VPN IKE User Activity User Activity Information Warning 403 404 ----- VPN IKE VPN IKE User Activity User Activity Warning Warning 405 406 ----- VPN IKE Security Services VPN IKE VPN IKE User Activity Maintenance User Activity User Activity Information Information Warning Warning 407 408 409 410 --------- VPN IKE VPN IKE VPN IKE VPN IKE VPN IKE VPN IKE VPN PKI VPN IKE User Activity User Activity User Activity User Activity User Activity User Activity Maintenance User Activity Warning Information Information Information Information Information Error Warning 411 412 413 414 415 416 417 418 --------------549 RIP RIP RIP RIP Maintenance Maintenance Maintenance Maintenance Information Information Information Information 419 420 421 422 8401 8402 8403 8404 RIP RIP RIP RIP Maintenance Maintenance Maintenance Maintenance Information Information Information Information 423 424 425 426 8405 8406 8407 8408 VPN Information 427 801 Intrusion Detection PPTP VPN Tunnel Status Debug Maintenance Warning Information 428 429 ----- PPTP Maintenance Information 430 --- PPTP Maintenance Information 431 --- Index of Log Event Messages Log Event Message PPTP server rejected control connection PPTP server rejected the call request PPP Dial-Up: Trying to failover but Alternate Profile is manual WLB Failback initiated by %s Probing succeeded on %s E-Mail fragment dropped Locked-out user logins allowed - lockout period expired Locked-out user logins allowed by administrator Access rule added Access rule modified Access rule deleted Access rules restored to defaults PPTP Server is not responding, check if the server is UP and running. IKE Initiator: Accepting peer lifetime. (Phase 1) FTP: PASV response spoof attack dropped PKI Failure PKI Failure: Output buffer too small PKI Failure: Cannot alloc memory PKI Failure: Reached the limit for local certs, cant load any more PKI Failure: Import failed PKI Failure: Incorrect admin password PKI Failure: CA certificates store exceeded. Cannot verify this Local Certificate PKI Failure: Improper file format. Please select PKCS#12 (*.p12) file PKI Failure: Certificate's ID does not match this Network Security Appliance PKI Failure: public-private key mismatch PKI Failure: Duplicate local certificate name PKI Failure: Duplicate local certificate PKI Failure: No CA certificates yet loaded PKI Failure: Internal error PKI Failure: Temporary memory shortage, try again PKI Failure: The certificate chain is circular PKI Failure: The certificate chain is incomplete PKI Failure: The certificate chain has no root New Category PPTP PPTP WAN Failover Legacy Category Maintenance Maintenance User Activity Priority Information Information Information ID 432 433 434 SNMP Trap Type ------- WAN Failover WAN Failover Intrusion Detection Authenticate Access Authenticate Access Firewall Rule Firewall Rule Firewall Rule Firewall Rule PPTP System Error System Error Attack User Activity Alert Alert Error Information 435 436 437 438 652 638 550 --- User Activity Information 439 --- User Activity User Activity User Activity User Activity Maintenance Information Information Information Information Information 440 441 442 443 444 ----------- VPN IKE User Activity Information 445 --- Intrusion Detection VPN PKI VPN PKI VPN PKI VPN PKI Attack Maintenance Maintenance Maintenance Maintenance Error Error Error Error Error 446 447 448 449 450 551 --------- VPN PKI VPN PKI VPN PKI Maintenance Maintenance Maintenance Error Error Error 451 452 453 ------- VPN PKI Maintenance Error 454 --- VPN PKI Maintenance Error 455 --- VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Error Error Error Error Error Error 456 457 458 459 460 461 ------------- VPN PKI VPN PKI Maintenance Maintenance Error Error 462 463 ----- VPN PKI Maintenance Error 464 --- SonicOS Log Event Reference Guide 33 Index of Log Event Messages Log Event Message PKI Failure: The certificate or a certificate in the chain has expired PKI Failure: The certificate or a certificate in the chain has a validity period in the future PKI Failure: The certificate or a certificate in the chain is corrupt PKI Failure: The certificate or a certificate in the chain has a bad signature PKI Failure: Loaded but could not verify certificate PKI Failure: Loaded the certificate but could not verify it's chain VPN Cleanup: Dynamic network settings change WARNING: Central Gateway does not have a Relay IP Address. DHCP message dropped. DHCP REQUEST received from remote device DHCP DISCOVER received from remote device DHCP DECLINE received from remote device DHCP OFFER received from server DHCP NACK received from server ERROR: DHCP over VPN policy is not defined. Cannot start IKE. DHCP DISCOVER received from local device DHCP REQUEST received from local device PPP Dial-Up: No peer IP address from DialUp ISP, local and remote IPs will be the same Received AV Alert: Your Network Anti-Virus subscription will expire in 7 days. %s Received notify: INVALID_ID_INFO DHCP lease dropped. Lease from Central Gateway conflicts with Remote Management IP Category: User login denied - User has no privileges for guest service WLAN firmware image has been updated Packet dropped by guest check Received CFS Alert: Your Content Filtering subscription will expire in 7 days. 34 SonicOS Log Event Reference Guide New Category VPN PKI Legacy Category Priority Maintenance Error ID 465 SNMP Trap Type --- VPN PKI Maintenance Error 466 --- VPN PKI Maintenance Error 467 --- VPN PKI Maintenance Error 468 --- VPN PKI Maintenance Error 469 --- VPN PKI Maintenance Error 470 --- VPN User Activity Information 471 --- DHCP Relay Maintenance Information 472 --- DHCP Relay Debug Information 473 --- DHCP Relay Debug Information 474 --- DHCP Relay Debug Information 475 --- DHCP Relay DHCP Relay DHCP Relay Debug Debug Maintenance Information Information Information 476 477 478 ------- DHCP Relay Debug Information 479 --- DHCP Relay PPP Dial Up Debug Maintenance Information Information 480 481 ----- Security Services Maintenance Warning 482 552 VPN IPsec DHCP Relay User Activity Maintenance Warning Warning 483 484 ----- None Authenticate Access Wireless Network Access Security Services --User Activity Debug Information 485 486 ----- Maintenance Information TCP | UDP | ICMP Warning Maintenance Warning 487 488 489 ----562 Index of Log Event Messages Log Event Message Received CFS Alert: Your Content Filtering subscription has expired. Received E-Mail Filter Alert: Your E-Mail Filtering subscription will expire in 7 days. Received E-Mail Filter Alert: Your E-Mail Filtering subscription has expired. ISDN Driver Firmware successfully updated Global VPN Client License Exceeded: Connection denied. Packet dropped by WLAN vpn traversal check Registration Update Needed: Restore your existing security service subscriptions by clicking here. Entering FIPS Error State. WAN Interface not setup PPPoE enabled but not ready L2TP enabled but not ready PPTP enabled but not ready WAN not ready VPN disabled for active dial up DHCP client enabled but not ready Blocked Quick Mode for Client using Default KeyId VPN disabled by administrator New Category Security Services Legacy Category Priority Maintenance Warning ID 490 SNMP Trap Type 563 Security Services Maintenance Warning 491 564 Security Services Maintenance Warning 492 565 Firewall Event VPN Client Maintenance System Error Information Information 493 494 --658 Wireless TCP | UDP | ICMP Warning 495 --- Security Services Maintenance Warning 496 --- Crypto Test Firewall Event PPPoE Unused PPTP Firewall Event Unused DHCP Client VPN Client System Error Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance System Error Error Information Information Information Information Information Information Information Error 497 498 499 500 501 502 503 504 505 659 --------------660 Maintenance Information 506 --- Maintenance Information 507 --- Maintenance Information 508 --- Maintenance Information 509 --- Maintenance Information 510 --- Maintenance Information 511 --- Maintenance Information 512 --- Maintenance Information 513 --- User Activity Information 514 --- User Activity Information 515 --- Authenticate Access VPN enabled by administrator Authenticate Access WLAN disabled by administrator Authenticate Access WLAN enabled by administrator Authenticate Access WiFiSec Enforcement disabled by Authenticate administrator Access WiFiSec Enforcement enabled by Authenticate administrator Access Wireless MAC Filter List enabled by Authenticate administrator Access Wireless MAC Filter List disabled by Authenticate administrator Access PPPoE user name changed by Administrator Authenticate Access PPPoE password changed by Administrator Authenticate Access SonicOS Log Event Reference Guide 35 Index of Log Event Messages Log Event Message IKE Responder: Default LAN gateway is not set but peer is proposing to use this SA as a default route WLAN Reboot 802.11 Management New Category VPN IKE Legacy Category Priority Attack Error ID 516 SNMP Trap Type 553 Firewall Hardware Wireless Error Information 517 518 642 --- WLAN recovery CLI administrator logged out Wireless Authenticate Access Firewall Event Network Access Network Access Network Access Network Access Intrusion Detection Intrusion Detection System Error 802.11b Management Maintenance User Activity Information Information 519 520 ----- Maintenance Debug ICMP TCP User Activity Attack Attack Information Alert Notice Notice Notice Alert Alert 521 522 523 524 526 527 528 --554 ------555 556 VPN Client System Error Information 529 643 PPP Dial Up Maintenance Information 530 --- PPP Dial Up Maintenance Information 531 --- Wireless TCP | UDP | ICMP Warning 532 --- VPN IPsec VPN IPsec VPN IPsec TCP | UDP | ICMP Notice TCP | UDP | ICMP Notice Debug Debug 533 534 535 ------- VPN IPsec Debug 536 --- Network Traffic Network Access Connection Traffic Information Attack Alert 537 538 --557 Firewall Hardware System Error Warning 539 644 Firewall Hardware System Error Warning 540 645 Firewall Event Maintenance Notice 541 --- PPP Dial Up User Activity Information 542 --- VPN IKE User Activity Information 543 --- Network Security Appliance initializing Malformed or unhandled IP packet dropped ICMP packet dropped no match Web access request dropped Web management request allowed FTP: PORT bounce attack dropped. FTP: PASV response bounce attack dropped. Global VPN Client connection is not allowed. Appliance is not registered. Network Modem Mode Enabled: turning off NAT Network Modem Mode Disabled: re-enabling NAT Internet Access restricted to authorized users. Dropped packet received in the clear. IPsec (ESP) packet dropped IPsec (AH) packet dropped IPsec (ESP) packet dropped; waiting for pending IPsec connection IPsec (AH) packet dropped; waiting for pending IPsec connection Connection Closed FTP: Data connection from non default port dropped Real time clock battery failure Time values may be incorrect If not already enabled, enabling NTP is recommended Maximum number of Bandwidth Managed rules exceeded upon upgrade to this version. Some Bandwith settings ignored. PPP Dial-Up: Previous session was connected for %s IKE Initiator: Using secondary gateway to negotiate 36 SonicOS Log Event Reference Guide Debug Index of Log Event Messages Log Event Message IKE Initiator drop: VPN tunnel end point does not match configured VPN Policy Bound to scope IKE Responder drop: VPN tunnel end point does not match configured VPN Policy Bound to scope Found Rogue Access Point WLAN sequence number out of order Association Flood from WLAN station User login failed - Guest service limit reached Guest Session Timeout Guest Account Timeout RIP disabled on WAN interface RIPv1 enabled on WAN interface RIPv2 enabled on WAN interface RIPv2 compatibility (broadcast) mode enabled on WAN interface Found Rogue Access Point Guest login denied. Guest '%s' is already logged in. Please try again later. Guest account '%s' created Guest account '%s' deleted Guest account '%s' disabled Guest account '%s' re-enabled Guest account '%s' pruned Guest account '%s' re-generated Guest Idle Timeout Interface %s Link Is Up Interface %s Link Is Down Interface IP Assignment changed: Shutting down %s Interface IP Assignment : Binding and initializing %s Network for interface %s overlaps with another interface. New Category VPN IKE Legacy Category Priority User Activity Information ID 544 SNMP Trap Type --- VPN IKE User Activity Information 545 --- WLAN IDS WLAN IDS WLAN IDS Authenticate Access Authenticate Access Authenticate Access RIP RIP RIP RIP WLAN IDS WLAN IDS WLAN IDS User Activity Alert Warning Alert Information 546 547 548 549 901 902 903 --- User Activity Information 550 --- User Activity Information 551 --- Maintenance Maintenance Maintenance Maintenance Information Information Information Information 552 553 554 555 8409 8410 8411 8412 WLAN IDS Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Firewall Event Firewall Event Firewall Event WLAN IDS User Activity Alert Information 556 557 10804 --- User Activity Information 558 --- User Activity Information 559 --- User Activity Information 560 --- User Activity Information 561 --- User Activity Information 562 --- User Activity Information 563 --- User Activity Information 564 --- System Error System Error Maintenance Warning Error Information 565 566 567 646 647 --- Firewall Event Maintenance Information 568 --- Firewall Event Maintenance Information 569 --- SonicOS Log Event Reference Guide 37 Index of Log Event Messages Log Event Message Please connect interface %s to another network to function properly RIP Broadcasts for LAN Network %s are being broadcast over dialup-connection A prior version of preferences was loaded because the most recent preferences file was inaccessible The preferences file is too large to be saved in available flash memory All preference values have been set to factory default values Voltages Out of Tolerance New Category Firewall Event Legacy Category Priority Maintenance Information ID 570 SNMP Trap Type --- RIP Maintenance Information 571 8413 Firewall Event System Error Warning 572 648 Firewall Event System Error Warning 573 649 Firewall Event System Error Warning 574 650 Firewall Hardware Error 575 101 Fan Failure Firewall Hardware Alert 576 102 Thermal Yellow Firewall Hardware Alert 577 103 Thermal Red Firewall Hardware Alert 578 104 Thermal Red Timer Exceeded Firewall Hardware Alert 579 105 TCP Syn/Fin packet dropped WLB Spill-over started, configured threshold exceeded WLB Spill-over stopped User login disabled from %s Network Access WAN Failover System Environment System Environment System Environment System Environment System Environment Attack Maintenance Alert Warning 580 581 558 --- Maintenance Attack Warning Error 582 583 --559 System Error System Error System Error User Activity Maintenance Maintenance Alert Alert Alert Warning Information Information 584 585 586 587 588 589 651 653 654 ------- Notice 590 --- PPP Dial Up LAN UDP | LAN TCP Attack Error 591 566 PPP Dial Up Attack Error 592 567 PPPoE PPPoE Maintenance Maintenance Information Information 593 594 ----- PPPoE PPTP Network Access Maintenance Debug Debug Information Debug Information 595 596 597 ------- WAN Failover Authenticate Access WLB Failover in progress WAN Failover WLB Resource is now available WAN Failover WLB Resource failed WAN Failover Header verification failed VPN IKE Received DHCP offer packet has errors DHCP Client Received response packet for DHCP request DHCP Client has errors IP type %s packet dropped Network Access Maximum sequential failed dial attempts (10) to a single dial-up number: %s Regulatory requirements prohibit %s from being re-dialed for 30 minutes Received PPPoE Active Discovery Offer Received PPPoE Active Discovery Session_confirmation Sending PPPoE Active Discovery Request PPTP decode failure ICMP packet allowed 38 SonicOS Log Event Reference Guide Index of Log Event Messages Log Event Message ICMP packet from LAN allowed Diagnostic Code G Diagnostic Code H Diagnostic Code I DNS packet allowed Adding L2TP IP pool Address object Failed. Global VPN Client version cannot enforce personal firewall. Minimum Version required is 2.1 Received unencrypted packet in crypto active state Spank attack multicast packet dropped Received ISAKMP packet destined to port %s IPS Detection Alert: %s IPS Prevention Alert: %s Crypto Hardware AES test failed A SonicOS Standard to Enhanced Upgrade was performed Not all configurations may have been completely upgraded Please manually check all system configurations for correctness of Upgrade Received IPS Alert: Your Intrusion Prevention (IDP) subscription has expired. WLAN client null probing Payload processing failed WLAN not in AP mode, DHCP server will not provide lease to clients on WLAN BOOTP server response relayed to remote device BOOTP Client IP address on LAN conflicts with remote device IP, deleting IP address from remote table BOOTP reply relayed to local device BOOTP Request received from remote device VoIP Call Connected VoIP Call Disconnected H.323/RAS Admission Reject H.323/RAS Admission Confirm H.323/RAS Admission Request H.323/RAS Bandwidth Reject H.323/RAS Disengage Confirm H.323/RAS Gatekeeper Reject New Category Network Access Firewall Hardware Firewall Hardware Firewall Hardware Network Access L2TP Server VPN Client Legacy Category Debug System Error System Error System Error Debug System Error User Activity Priority Information Error Error Error Information Error Information ID 598 599 600 601 602 603 604 SNMP Trap Type --655 656 657 --661 --- VPN IKE User Activity Warning 605 --- Intrusion Detection VPN IKE Attack Debug | UDP Alert Information 606 607 568 --- Intrusion Detection Intrusion Detection Crypto Test Firewall Event Attack Attack Maintenance Maintenance Alert Alert Error Information 608 609 610 611 569 570 ----- Firewall Event Maintenance Information 612 --- Firewall Event Maintenance Information 613 --- Security Services Maintenance Warning 614 571 WLAN IDS VPN IKE Wireless WLAN IDS Debug Maintenance Warning Error Information 615 616 617 904 ----- BOOTP Debug Debug 618 --- BOOTP Maintenance Information 619 --- BOOTP BOOTP Maintenance Debug Information Debug 620 621 ----- VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP Information Information Debug Debug Debug Debug Debug Debug 622 623 624 625 626 627 628 629 ----------------- SonicOS Log Event Reference Guide 39 Index of Log Event Messages Log Event Message H.323/RAS Location Confirm H.323/RAS Location Reject H.323/RAS Registration Reject H.323/H.225 Setup H.323/H.225 Connect H.323/H.245 Address H.323/H.245 End Session VoIP %s Endpoint added VoIP %s Endpoint removed VoIP %s Endpoint not added - configured 'public' endpoint limit reached H.323/RAS Unknown Message Response H.323/RAS Disengage Reject H.323/RAS Unregistration Reject SIP Request SIP Response SIP Register expiration exceeds configured Signaling inactivity time out Packet dropped; connection limit for this source IP address has been reached Packet dropped; connection limit for this destination IP address has been reached Packet destination not in VPN Access list Application Filters Block Alert: %s Application Filter Detection Alert: %s IPComp connection interrupt IPComp packet dropped IPComp packet dropped; waiting for pending IPComp connection Maximum events per second threshold exceeded Maximum syslog data per second threshold exceeded SMTP POP-Before-SMTP authentication failed Syslog Server cannot be reached IKE Responder: Proposed IKE ID mismatch IKE Responder: IP Address already exists in the DHCP relay table. Client traffic not allowed. IKE Responder: %s policy does not allow static IP for Virtual Adapter. Received notify: INVALID_PAYLOAD Drop WLAN traffic from non-SonicPoint devices 40 SonicOS Log Event Reference Guide New Category VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP Legacy Category VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP Priority Debug Debug Debug Debug Debug Debug Debug Debug Debug Warning ID 630 631 632 633 634 635 636 637 638 639 SNMP Trap Type --------------------- VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP VoIP Debug Debug Debug Debug Debug Warning 640 641 642 643 644 645 ------------- Firewall Event System Error Alert 646 5238 Firewall Event System Error Alert 647 5239 VPN IPsec Intrusion Detection Intrusion Detection IPComp IPComp IPComp Attack Attack Attack Debug TCP | UDP | ICMP Debug Error Alert Alert Debug Notice Debug 648 649 650 651 652 653 572 ----------- Firewall Logging System Error Critical 654 --- Firewall Logging System Error Critical 655 --- Firewall Logging System Error Warning 656 --- Network VPN IKE VPN Client Maintenance System Error System Error Information Warning Error 657 658 659 ------- VPN Client System Error Error 660 --- VPN IKE Intrusion Detection User Activity Attack Error Error 661 662 --6434 Index of Log Event Messages Priority Warning ID 663 Information 664 --- PPP Dial Up Legacy Category 802.11b Management 802.11b Management --- SNMP Trap Type --- Information 665 --- PPP Dial Up --- Information 666 --- SonicPoint High Availability High Availability High Availability High Availability High Availability High Availability SonicPoint Maintenance System Error System Error System Error System Error Maintenance Information Information Error Error Error Error Information 667 668 669 670 671 672 673 ----663 664 665 666 --- High Availability High Availability Multicast Multicast Multicast System Error System Error ------- Information Error Information Information Debug 674 675 676 677 678 --6234 ------- Multicast --- Debug 679 --- Multicast --- Debug 680 --- Multicast --- Debug 681 --- Multicast --- Information 682 --- Multicast --- Notice 683 --- Multicast --- Alert 684 --- Multicast --- Alert 685 --- Multicast Multicast Multicast ------- Notice Notice Notice 686 687 688 ------- Multicast Multicast ----- Debug Notice 689 690 ----- Multicast --- Notice 691 --- Log Event Message WPA MIC Failure New Category Wireless WPA Radius Server Timeout Wireless PPP Dial-Up: Dialing not allowed by schedule. %s PPP Dial-Up: Connection disconnected as scheduled. SonicPoint Status HA Peer Firewall Rebooted Error Rebooting HA Peer Firewall License of HA pair doesn't match: %s Primary received reboot signal from Backup Backup received reboot signal from Primary Synchronizing preferences to HA Peer Firewall Success to reach Interface %s probe Failure to reach Interface %s probe IGMP V2 client joined multicast Group : %s IGMP V3 client joined multicast Group : %s IGMP V3 Membership report received from interface %s IGMP V2 Membership report received from interface %s Router IGMP General query received on interface %s Router IGMP Membership query received on interface %s IGMP Leave group message Received on interface %s IGMP packet dropped, wrong checksum received on interface %s Multicast packet dropped, wrong MAC address received on interface : %s Multicast packet dropped, Invalid src IP received on interface : %s IGMP packet dropped, decoding error IGMP Packet Not handled. Packet type : %s IGMP V3 packet dropped, unsupported Record type : %s IGMP V3 reord type : %s not Handled Multicast UDP packet dropped, no state entry Multicast TCP packet dropped SonicOS Log Event Reference Guide 41 Index of Log Event Messages Log Event Message IGMP state table entry time out,deleting interface : %s for multicast address : %s IGMP state table entry time out,deleting VPN SPI :%s for Multicast address : %s Multicast UDP packet dropped, RTP stateful failed Multicast UDP packet dropped, RTCP stateful failed Multicast application %s not supported Adding to multicast policyList , interface : %s Deleting from Multicast policy list, interface : %s Adding to Multicast policyList , VPN SPI : %s Deleting from Multicast policy list, VPN SPI : %s IGMP querier Router detected on interface %s IGMP querier Router detected on VPN tunnel , SPI %S Exceeded Max multicast address limit Invalid Product Code Upgrade request received: %s Overriding Product Code Upgrade to: %s Network Monitor: Host %s is offline Network Monitor: Host %s is online TCP packet received with invalid SEQ number; TCP packet dropped TCP packet received with invalid ACK number; TCP packet dropped TCP stateful inspection: Invalid flag; TCP packet dropped TCP stateful inspection: Bad header; TCP packet dropped TCP connection reject received; TCP connection dropped TCP connection abort received; TCP connection dropped EIGRP packet dropped ARP request packet sent ARP response packet received ARP request packet received ARP response packet sent VPN policy count received exceeds the limit; %s Sending LCP Echo Request 42 SonicOS Log Event Reference Guide New Category Multicast Legacy Category Priority --Debug ID 692 SNMP Trap Type --- Multicast --- Debug 693 --- Multicast --- Warning 694 --- Multicast --- Warning 695 --- Multicast Multicast Multicast ------- Information Debug Debug 696 697 698 ------- Multicast Multicast ----- Debug Debug 699 700 ----- Multicast --- Debug 701 --- Multicast --- Debug 702 --- Multicast Firewall Event ----- Warning Error 703 704 ----- Firewall Event Network Monitor Network Monitor Network ------Debug Error Alert Alert Debug 705 706 707 708 --14005 14006 --- Network Debug Debug 709 --- Network Debug Information 710 --- Network Debug Debug 711 --- Network Debug Debug 712 --- Network Debug Debug 713 --- Network Access Network Network Network Network VPN Debug --------System Error Notice Information Information Information Information Error 714 715 716 717 718 719 ------------- PPPoE Maintenance Information 720 --- Index of Log Event Messages New Category PPPoE PPPoE PPPoE Network Access Network Access Legacy Category Maintenance Maintenance Maintenance ----- Priority Information Information Information Information Information ID 721 722 723 724 725 SNMP Trap Type ----------- Network Access --- Information 726 --- SonicPoint Maintenance Information Information 727 728 ----- Maintenance Information 729 --- Virtual Access Point is enabled SonicPoint Authenticate Access Authenticate Access SonicPoint 730 --- Virtual Access Point is disabled SonicPoint 731 --- Packet dropped by WLAN SSL-VPN enforcement check SSL-VPN enforcement Source IP address connection status: %s Destination IP address connection status: %s SMTP authentication problem:%s PPPoE Client: Previous session was connected for %s Packet dropped. No firewall rule associated with VPN policy. NetBIOS settings were not upgraded. Use Network>IP Helper to configure NetBIOS support LAN Subnet configurations were not upgraded. Time of day settings for firewall policies were not upgraded. Hardware Failover settings were not upgraded. User login denied - RADIUS communication problem User login denied - LDAP authentication failure User login denied - LDAP server timeout User login denied - LDAP server down or misconfigured User login denied - LDAP communication problem Wireless 802.11b Information Management 802.11b Information Management TCP | UDP | ICMP Warning 732 --- Wireless Firewall Event Firewall Event Maintenance ----- Information Information Information 733 734 735 ------- Firewall Logging PPPoE System Error Maintenance Warning Information 737 738 ----- VPN System Error Alert 739 --- Firewall Event Maintenance Information 740 --- Firewall Event Maintenance Information 741 --- Firewall Event Maintenance Information 742 --- Firewall Event Maintenance Information 743 --- RADIUS User Activity Warning 744 --- RADIUS User Activity Information 745 --- RADIUS RADIUS User Activity User Activity Warning Warning 746 747 ----- RADIUS User Activity Warning 748 --- Log Event Message Received LCP Echo Request Sending LCP Echo Reply Received LCP Echo Reply Guest Services drop traffic to deny network Guest Services pass traffic to access allow network WLAN max concurrent users reached already SonicPoint Provision WLAN disabled by schedule WLAN enabled by schedule SonicOS Log Event Reference Guide 43 Index of Log Event Messages Log Event Message User login denied - invalid credentials on LDAP server User login denied - insufficient access on LDAP server User login denied - LDAP schema mismatch Allowed LDAP server certificate with wrong host name User login denied - LDAP server name resolution failed User login denied - RADIUS server name resolution failed User login denied - LDAP server certificate not valid User login denied - TLS or local certificate problem User login denied - LDAP directory mismatch LDAP server does not allow CHAP User login denied - user already logged in TCP handshake violation detected; TCP connection dropped Access attempt from host out of compliance with GSC policy GSC policy out-of-date on host Access attempt from host without GSC installed Failed to synchronize license information with Licensing Server. Please see http:// help.mysonicwall.com/licsyncfail.html (code: %s) ADConnector %s response timed-out; applying caching policy DDNS Failure: Provider %s DDNS Failure: Provider %s DDNS Failure: Provider %s DDNS Update success for domain %s DDNS Warning: Provider %s DDNS association %s taken Offline locally DDNS association %s added DDNS association %s enabled DDNS association %s disabled DDNS Association %s put on line All DDNS associations have been deleted DDNS association %s deactivated DDNS association %s deleted 44 SonicOS Log Event Reference Guide New Category RADIUS Legacy Category Priority User Activity Warning ID 749 SNMP Trap Type --- RADIUS User Activity Warning 750 --- RADIUS RADIUS User Activity User Activity Warning Warning 751 752 ----- RADIUS User Activity Warning 753 --- RADIUS User Activity Warning 754 --- RADIUS User Activity Warning 755 --- RADIUS User Activity Warning 756 --- RADIUS RADIUS Authenticate Access Network Access User Activity User Activity User Activity Warning Warning Information 757 758 759 ------- --- Notice 760 --- Security Services Maintenance Information 761 --- Security Services Security Services Maintenance Maintenance Information Information 762 763 --8627 Security Services Maintenance Warning 766 8628 Microsoft AD --- Error 769 --- DDNS DDNS DDNS DDNS DDNS DDNS DDNS DDNS DDNS DDNS DDNS DDNS DDNS System Error System Error System Error Maintenance System Error Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Maintenance Error Error Error Information Warning Information Information Information Information Information Information Information Information 773 774 775 776 777 778 779 780 781 782 783 784 785 --------------------------- Index of Log Event Messages Log Event Message DDNS association %s updated IPS Detection Alert: %s IPS Prevention Alert: %s DPI-SSL: %s Application Firewall Alert: %s Anti-Spyware Prevention Alert: %s Anti-Spyware Detection Alert: %s Anti-Spyware Service Expired Outbound connection to RBL-listed SMTP server dropped Inbound connection from RBL-listed SMTP server dropped SMTP server found on RBL blacklist No valid DNS server specified for RBL lookups Interface statistics report SonicPoint statistics report Gateway Anti-Virus Alert: %s Gateway Anti-Virus Service expired PPP Dial-Up: Invalid DNS IP address returned from Dial-Up ISP; overriding using dial-up profile settings WAN node exceeded: Connection dropped because too many IP addresses are in use on your LAN Adding Dynamic Entry for Bound MAC Address MAC address collides with Static ARP Entry with Bound MAC address; packet dropped Too many gratuitous ARPs detected ARP unused/spare Incoming call received for Remotely Triggered Dial-out session Remotely Triggered Dial-out session started. Requesting authentication Incorrect authentication received for Remotely Triggered Dial-out Successful authentication received for Remotely Triggered Dial-out Authentication timeout during Remotely Triggered Dial-out session Remotely Triggered Dial-out session ended. Valid WAN bound data found. Normal dialup sequence will commence Backup will be shut down in %s minutes New Category DDNS Intrusion Detection Intrusion Detection DPI SSL Application Firewall Intrusion Detection Intrusion Detection Security Services RBL Legacy Category --Attack Attack Network Access User Activity Attack Attack Maintenance --- Priority Information Alert Alert Information Alert Alert Alert Warning Notice ID 786 789 790 791 793 794 795 796 797 SNMP Trap Type --6435 6436 --13201 6437 6438 8631 --- RBL --- Notice 798 --- RBL RBL ----- Notice Error 799 800 ----- GMS GMS Security Services Security Services PPP Dial Up ----Attack Maintenance Maintenance Information Information Alert Warning Information 805 806 809 810 811 ----8632 8633 --- Firewall Event System Error Error 812 --- Network --- Information 813 --- Network --- Notice 814 --- Network Network Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access ----User Activity Warning Debug Information 815 816 817 ------- User Activity Information 818 --- User Activity Information 819 --- User Activity Information 820 --- User Activity Information 821 --- User Activity Information 822 --- System Error Error 823 --- High Availability SonicOS Log Event Reference Guide 45 Index of Log Event Messages Log Event Message Backup shut down because license is expired Backup active DHCP Scopes altered automatically due to change in network settings for interface %s DHCP lease file in the flash is corrupted; read failed Failed to write DHCP leases to flash DHCP leases written to flash Invalid VLAN packet dropped IP address conflict detected from ethernet address %s OCSP sending request. OCSP send request message failed. OCSP received response. OCSP received response error. OCSP Resolved Domain Name. OCSP Failed to Resolve Domain Name. OCSP Internal error handling received response. SYN Flood Mode changed by user to: Watch and report possible SYN floods SYN Flood Mode changed by user to: Watch and proxy WAN connections when under attack SYN Flood Mode changed by user to: Always proxy WAN connections Possible SYN flood detected on WAN IF %s - switching to connection-proxy mode Possible SYN Flood on IF %s SYN flood ceased or flooding machines blacklisted - connection proxy disabled SYN Flood blacklisting enabled by user SYN Flood blacklisting disabled by user SYN-Flooding machine %s blacklisted Machine %s removed from SYN flood blacklist Possible SYN Flood on IF %s continues Possible SYN Flood on IF %s has ceased SYN Flood Blacklist on IF %s continues TCP SYN received CRL has expired Failed to find certificate CRL missing - Issuer requires CRL checking. CRL validation failure for Root Certificate 46 SonicOS Log Event Reference Guide New Category High Availability Legacy Category Priority System Error Error ID 824 SNMP Trap Type --- High Availability Firewall Event System Error --- Information Information 825 832 ----- Firewall Event System Error Warning 833 --- Firewall Event Firewall Event Network Network System Error Maintenance --Maintenance Warning Information Alert Warning 834 835 836 847 --------- VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI VPN PKI User Activity User Activity User Activity User Activity User Activity User Activity User Activity Information Error Information Error Information Error Error 848 849 850 851 852 853 854 --------------- Intrusion Detection Debug Warning 856 --- Intrusion Detection Debug Warning 857 --- Intrusion Detection Debug Warning 858 --- Intrusion Detection Debug Alert 859 --- Intrusion Detection Intrusion Detection Debug Debug Alert Alert 860 861 ----- Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Debug Debug Debug Debug Warning Warning Alert Alert 862 863 864 865 --------- Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection VPN PKI VPN PKI VPN PKI VPN PKI Debug Debug Debug Debug User Activity User Activity User Activity User Activity Warning Alert Warning Debug Alert Alert Alert Alert 866 867 868 869 874 875 876 877 ----------------- Index of Log Event Messages Log Event Message Cannot Validate Issuer Path WLAN radio frequency threat detected Unable to resolve dynamic address object System clock manually updated HTTP method detected; examining stream for host header IP Header checksum error; packet dropped TCP checksum error; packet dropped UDP checksum error; packet dropped ICMP checksum error; packet dropped TCP packet received with invalid header length; TCP packet dropped TCP packet received on non-existent/closed connection; TCP packet dropped TCP packet received without mandatory SYN flag; TCP packet dropped TCP packet received without mandatory ACK flag; TCP packet dropped TCP packet received on a closing connection; TCP packet dropped TCP packet received with SYN flag on an existing connection; TCP packet dropped TCP packet received with invalid SACK option length; TCP packet dropped TCP packet received with invalid MSS option length; TCP packet dropped TCP packet received with invalid option length; TCP packet dropped TCP packet received with invalid source port; TCP packet dropped TCP packet received with invalid SYN Flood cookie; TCP packet dropped RST-Flooding machine %s blacklisted RST Flood Blacklist on IF %s continues Machine %s removed from RST flood blacklist FIN-Flooding machine %s blacklisted FIN Flood Blacklist on IF %s continues Machine %s removed from FIN flood blacklist Possible RST Flood on IF %s Possible FIN Flood on IF %s Possible RST Flood on IF %s has ceased Possible FIN Flood on IF %s has ceased New Category VPN PKI RF Management Dynamic Address Objects Firewall Logging Network Access Legacy Category User Activity --Maintenance Priority Alert Warning Information ID 878 879 880 SNMP Trap Type ------- --TCP Notice Debug 881 882 ----- Network Access Network Access Network Access Network Access Network TCP|UDP TCP UDP UDP Debug Notice Notice Notice Notice Debug 883 884 885 886 887 ----------- Network Debug Debug 888 --- Network Debug Debug 889 --- Network Debug Debug 890 --- Network Debug Debug 891 --- Network Debug Information 892 --- Network Debug Debug 893 --- Network Debug Debug 894 --- Network Debug Debug 895 --- Network Debug Debug 896 --- Network Debug Information 897 --- Intrusion Detection Intrusion Detection Intrusion Detection Debug Debug Debug Alert Warning Alert 898 899 900 ------- Intrusion Detection Intrusion Detection Intrusion Detection Debug Debug Debug Alert Warning Alert 901 902 903 ------- Intrusion Detection Intrusion Detection Intrusion Detection Intrusion Detection Debug Debug Debug Debug Alert Alert Alert Alert 904 905 906 907 --------- SonicOS Log Event Reference Guide 47 Index of Log Event Messages Log Event Message Possible RST Flood on IF %s continues Possible FIN Flood on IF %s continues Packet Dropped - IP TTL expired Added host entry to dynamic address object Removed host entry from dynamic address object IKE Responder: Phase 1 Authentication Method does not match IKE Responder: Phase 1 encryption algorithm does not match IKE Responder: Phase 1 encryption algorithm keylength does not match IKE Responder: Phase 1 hash algorithm does not match IKE Responder: Phase 1 XAUTH required but policy has no user name IKE Responder: Phase 1 XAUTH required but policy has no user password IKE Responder: Phase 1 DH Group does not match IKE Responder: AH authentication algorithm does not match IKE Responder: ESP encryption algorithm does not match IKE Responder: ESP authentication algorithm does not match IKE Responder: AH authentication key length does not match IKE Responder: ESP encryption key length does not match IKE Responder: ESP authentication key length does not match IKE Responder: AH authentication key rounds does not match IKE Responder: ESP encryption key rounds does not match IKE Responder: ESP authentication key rounds does not match IKE Responder: IP Compression algorithm does not match IKE Initiator: Remote party timeout Retransmitting IKE request. IKE Responder: Remote party timeout Retransmitting IKE request. IKE Responder: IPsec protocol mismatch 48 SonicOS Log Event Reference Guide New Category Intrusion Detection Intrusion Detection Network Dynamic Address Objects Dynamic Address Objects VPN IKE Legacy Category Debug Debug Debug Maintenance Priority Warning Warning Warning Information ID 908 909 910 911 SNMP Trap Type --------- Maintenance Information 912 --- User Activity Warning 913 --- VPN IKE User Activity Warning 914 --- VPN IKE User Activity Warning 915 --- VPN IKE User Activity Warning 916 --- VPN IKE User Activity Warning 917 --- VPN IKE User Activity Warning 918 --- VPN IKE User Activity Warning 919 --- VPN IKE User Activity Warning 920 --- VPN IKE User Activity Warning 921 --- VPN IKE User Activity Warning 922 --- VPN IKE User Activity Warning 923 --- VPN IKE User Activity Warning 924 --- VPN IKE User Activity Warning 925 --- VPN IKE User Activity Warning 926 --- VPN IKE User Activity Warning 927 --- VPN IKE User Activity Warning 928 --- VPN IKE User Activity Warning 929 --- VPN IKE User Activity Information 930 --- VPN IKE User Activity Information 931 --- VPN IKE User Activity Warning 932 --- Index of Log Event Messages Log Event Message IKE Initiator: Proposed IKE ID mismatch IKE Responder: Peer's local network does not match VPN policy's <b>Destination Network</b> IKE Responder: Peer's destination network does not match VPN policy's <b>Local Network</b> IKE Responder: Route table overrides VPN policy IKE Initiator: IKE proposal does not match (Phase 1) IKEv2 Initiator: Send IKE_SA_INIT request IKEv2 Responder: Received IKE_SA_INIT request IKEv2 Initiator: Send IKE_AUTH request IKEv2 Responder: Received IKE_AUTH request IKEv2 Authentication successful IKEv2 Accept IKE SA Proposal IKEv2 Accept IPsec SA Proposal IKEv2 Initiator: Send CREATE_CHILD_SA request IKEv2 Responder: Received CREATE_CHILD_SA request IKEv2 Send delete IKE SA request IKEv2 Received delete IKE SA request IKEv2 Send delete IPsec SA request IKEv2 Received delete IPsec SA request IKEv2 Responder: Peer's destination network does not match VPN policy's <b>Local Network</b> IKEv2 Responder: Peer's local network does not match VPN policy's <b>Destination Network</b> IKEv2 Payload processing error IKEv2 Initiator: Negotiations failed. Extra payloads present. IKEv2 Initiator: Negotiations failed. Missing required payloads. IKEv2 Initiator: Negotiations failed. Invalid input state. IKEv2 Initiator: Negotiations failed. Invalid output state. IKEv2 Payload validation failed. IKEv2 Unable to find IKE SA IKEv2 Decrypt packet failed New Category VPN IKE VPN IKE Legacy Category Priority User Activity Warning User Activity Warning ID 933 934 SNMP Trap Type ----- VPN IKE User Activity Warning 935 --- VPN IKE User Activity Warning 936 --- VPN IKE User Activity Warning 937 --- VPN IKE VPN IKE User Activity User Activity Information Information 938 939 ----- VPN IKE VPN IKE User Activity User Activity Information Information 940 941 ----- VPN IKE VPN IKE VPN IKE VPN IKE User Activity User Activity User Activity User Activity Information Information Information Information 942 943 944 945 --------- VPN IKE User Activity Information 946 --- VPN IKE VPN IKE VPN IKE VPN IKE VPN IKE User Activity User Activity User Activity User Activity User Activity Information Information Information Information Information 947 948 949 950 951 ----------- VPN IKE User Activity Information 952 --- VPN IKE VPN IKE User Activity User Activity Warning Warning 953 954 ----- VPN IKE User Activity Warning 955 --- VPN IKE User Activity Warning 956 --- VPN IKE User Activity Warning 957 --- VPN IKE VPN IKE VPN IKE User Activity User Activity User Activity Warning Warning Warning 958 959 960 ------- SonicOS Log Event Reference Guide 49 Index of Log Event Messages Log Event Message IKEv2 Out of memory IKEv2 Responder: Policy for remote IKE ID not found IKEv2 Process Message queue failed IKEv2 Invalid state IKE Responder: Client Policy has no VPN Access Networks assigned. Check Configuration. IKEv2 Invalid SPI size IKEv2 VPN Policy not found IKEv2 IPsec proposal does not match IKEv2 IPsec attribute not found IKEv2 IKE attribute not found IKEv2 Peer is not responding. Negotiation aborted. IKEv2 Initiator: Remote party timeout Retransmitting IKEv2 request. IKEv2 Initiator: Received IKE_SA_INT response IKEv2 Initiator: Received IKE_AUTH response IKEv2 Initiator: Received CREATE_CHILD_SA response IKEv2 Responder: Send IKE_SA_INIT response IKEv2 Responder: Send IKE_AUTH response IKEv2 negotiation complete IKEv2 Function sendto() failed to transmit packet. IKEv2 Initiator: Proposed IKE ID mismatch IKEv2 IKE proposal does not match IKEv2 Received notify status payload IKEv2 Received notify error payload IKEv2 No NAT device detected between negotiating peers IKEv2 NAT device detected between negotiating peers User login denied - not allowed by policy rule User login denied - not found locally User login denied - SSO agent timeout 50 SonicOS Log Event Reference Guide New Category VPN IKE VPN IKE Legacy Category Priority User Activity Warning User Activity Error ID 961 962 SNMP Trap Type ----- VPN IKE VPN IKE VPN IKE User Activity User Activity System Error Warning Warning Error 963 964 965 ------- VPN IKE VPN IKE VPN IKE VPN IKE VPN IKE VPN IKE User Activity User Activity User Activity User Activity User Activity User Activity Warning Warning Warning Warning Warning Warning 966 967 968 969 970 971 ------------- VPN IKE User Activity Information 972 --- VPN IKE User Activity Information 973 --- VPN IKE User Activity Information 974 --- VPN IKE User Activity Information 975 --- VPN IKE User Activity Information 976 --- VPN IKE User Activity Information 977 --- VPN IKE VPN IKE User Activity User Activity Information Error 978 979 ----- VPN IKE VPN IKE VPN IKE VPN IKE VPN IKE User Activity User Activity User Activity User Activity User Activity Warning Warning Information Warning Information 980 981 982 983 984 ----------- VPN IKE User Activity Information 985 --- Authenticate Access Authenticate Access Authenticate Access User Activity Information 986 --- User Activity Information 987 --- User Activity Warning 988 --- Index of Log Event Messages Log Event Message User login denied - SSO agent configuration error User login denied - SSO agent communication problem User login denied - SSO agent name resolution failed SSO returned a user name that is too long SSO returned a domain name that is too long Configuration mode administration session started Configuration mode administration session ended Read-only mode GUI administration session started Non-config mode GUI administration session started GUI administration session ended SSL Control: Website found in blacklist SSL Control: Website found in whitelist SSL Control: HTTPS via SSL2 SSL Control: Certificate with invalid date SSL Control: Self-signed certificate SSL Control: Weak cipher being used SSL Control: Untrusted CA SSL Control: Certificate chain not complete SSL Control: Failed to decode Server Hello User logged out - logout detected by SSO Bind to LDAP server failed Using LDAP without TLS - highly insecure LDAP using non-administrative account VPN client user will not be able to change passwords IKEv2 Responder: Send CREATE_CHILD_SA response IKEv2 Send delete IKE SA response IKEv2 Send delete IPsec SA response IKEv2 Received delete IKE SA response IKEv2 Received delete IPsec SA response 3G %s device detected PPP message: %s Chat started Legacy Category Priority User Activity Warning ID 989 SNMP Trap Type --- User Activity Warning 990 --- User Activity Warning 991 --- User Activity User Activity Warning Warning 992 993 ----- User Activity Information 994 --- User Activity Information 995 --- User Activity Information 996 --- User Activity Information 997 --- User Activity Information 998 --- Blocked Sites Blocked Sites Blocked Sites Blocked Sites Blocked Sites Blocked Sites Blocked Sites Blocked Sites Blocked Sites User Activity Information Information Information Information Information Information Information Information Information Information 999 1000 1001 1002 1003 1004 1005 1006 1007 1008 --------------------- System Error System Error System Error Error Alert Warning 1009 --1010 --1011 --- VPN IKE User Activity Information 1012 --- VPN IKE VPN IKE VPN IKE VPN IKE Firewall Hardware User Activity User Activity User Activity User Activity System Environment --User Activity Information Information Information Information Information 1013 1014 1015 1016 1017 Information Information 1018 --1019 --- New Category Authenticate Access Authenticate Access Authenticate Access SSO SSO Authenticate Access Authenticate Access Authenticate Access Authenticate Access Authenticate Access Network Access Network Access Network Access Network Access Network Access Network Access Network Access Network Access Network Access Authenticate Access RADIUS RADIUS RADIUS PPP PPP Dial Up SonicOS Log Event Reference Guide ----------- 51 Index of Log Event Messages Log Event Message Chat completed Chat wrote '%s' Chat %s Chat failed: %s Unable to send message to dial-up task Diagnostic Code J 3G Dial-up: %s. 3G Dial-up: data usage limit reached for the '%s' billing cycle. Disconnecting the 3G session. %s auto-dial failed: Current Connection Model is configured as Ethernet Only TCP packet received with non-permitted option; TCP packet dropped TCP packet received with invalid Window Scale option length; TCP packet dropped TCP packet received with invalid Window Scale option value; TCP packet dropped Chat started by '%s' Problem occurred during user group membership retrieval Received AF Alert: Your Application Firewall (AF) subscription has expired. User login denied - password expired New Category PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up PPP Dial Up Firewall Hardware PPP Dial Up PPP Dial Up Legacy Category User Activity User Activity User Activity User Activity System Error System Error User Activity User Activity Priority Information Information Information Information Error Error Alert Alert ID 1020 1021 1022 1023 1024 1025 1026 1027 PPP Dial Up System Error Alert 1028 --- Network Debug Debug 1029 --- Network Debug Debug 1030 --- Network Debug Debug 1031 --- PPP Dial Up Authenticate Access Security Services User Activity User Activity Information Warning 1032 --1033 --- Maintenance Warning 1034 8635 User Activity Information 1035 --- User Activity Error 1036 --- ----------- Information Information Information Alert Alert 1037 1038 1039 1040 1041 ----------- --------- Information Error Information Information 1042 1043 1044 1045 5424 5425 ----- ----- Information Information 1046 --1047 --- --- Information 1048 --- ----- Information Information 1049 --1050 --- Authenticate Access IKE Responder: IKE Phase 1 exchange does VPN IKE not match PPP Dial-Up: Starting PPP PPP Dial Up Dial-up: Traffic generated by '%s' PPP Dial Up Dial-up: Session initiated by data packet PPP Dial Up DHCP Server: IP conflict detected Firewall Event DHCP Server: Received DHCP decline from Firewall Event client Physical environment normal Firewall Hardware Power supply without redundancy Firewall Hardware Discovered HA %s Firewall High Availability Diagnostic Auto-restart scheduled for %s Firewall Event minutes from now Diagnostic Auto-restart canceled Firewall Event "As per Diagnostic Auto-restart configuration Firewall Event request, restarting system" User login denied - password doesn't meet Authenticate constraints Access Settings Import: %s Firewall Event VPN Policy Added VPN 52 SonicOS Log Event Reference Guide SNMP Trap Type ----------5423 --7643 Index of Log Event Messages Log Event Message VPN Policy Deleted VPN Policy Modified PC Card removed. PC Card inserted. 3G: No SIM detected PC Card: No device detected Peer firewall rebooting (%s) Primary firewall rebooting itself as it transitioned from Active to Idle while Preempt Backup firewall rebooting itself as it transitioned from Active to Idle while Preempt Crypto SHA1 based DRNG KAT test failed Successfully sent Preference file to remote backup server Failed to send Preference file to remote backup server, Error: %s Successfully sent TSR file to remote backup server Failed to send TSR file to remote backup server, Error: %s Successfully sent %s file to remote backup server Failed to send file to remote backup server, Error: %s System shutdown by administrator. Power cycle required. Multiple DHCP Servers are detected on network External Web Server Host Resolution Failed %s Invalid DNS Server will not be accepted by the dynamic client DHCP Server sanity check passed %s DHCP Server sanity check failed %s SSO agent returned error L2TP Tunnel Negotiation %s SSO agent is down SSO agent is up SonicPointN Status SonicPointN Provision SSLVPN zone remote user login allowed SNMP Trap Type ----5418 5419 --------- New Category VPN VPN Firewall Hardware Firewall Hardware Firewall Hardware Firewall Hardware High Availability High Availability Legacy Category ----------------- Priority Information Information Alert Alert Alert Alert Information Information ID 1051 1052 1053 1054 1055 1056 1057 1058 High Availability --- Information 1059 --- Crypto Test Firewall Event --Maintenance Error Information 1060 --1061 --- Firewall Event Maintenance Information 1062 --- Firewall Event Maintenance Information 1063 --- Firewall Event Maintenance Information 1064 --- Firewall Event Maintenance Information 1065 --- Firewall Event Maintenance Information 1066 --- Firewall Event --- Alert 1067 5242 Firewall Event --- Warning 1068 --- Authenticate Access Firewall Event --- Error 1069 --- --- Information 1070 --- Firewall Event Firewall Event SSO L2TP Client SSO SSO SonicPoint-N SonicPoint-N Authenticate Access ----User Activity --User Activity User Activity ----User Activity Critical Critical Warning Information Alert Alert Information Information Information 1071 1072 1073 1074 1075 1076 1077 1078 1080 SonicOS Log Event Reference Guide ------------------- 53 Index of Log Event Messages Log Event Message SSL Control: Certificate with MD5 Digest Signature Algorithm %s is operational. %s is unavailable. Anti-Spam service is enabled by administrator. Anti-Spam service is disabled by administrator. Your Anti-Spam Service subscription has expired. SMTP connection limit is reached. Connection is dropped. Anti-Spam Startup Failure - %s Anti-Spam Teardown Failure - %s DHCP Server: Received DHCP message from untrusted relay agent Outbound connection to GRID-listed SMTP server dropped Inbound connection from GRID-listed SMTP server dropped SMTP server found on Reject List No valid DNS server specified for GRID lookups Unprocessed email received from MTA on Inbound SMTP port Processed Email received from Email Security Service SCEP Client: %s Possible DNS rebind attack detected DNS rebind attack blocked Network Monitor: Policy %s status is UP Network Monitor: Policy %s status is DOWN Network Monitor: Policy %s status is UNKNOWN Network Monitor: Host %s status is UNKNOWN Network Monitor Policy %s Added Network Monitor Policy %s Deleted Network Monitor Policy %s Modified Message blocked by Real-Time Email Scanner CSR Generation: %s Assigned IP address %s Released IP address %s Ftp server accepted the connection 54 SonicOS Log Event Reference Guide New Category Network Access Legacy Category Priority Blocked Sites Information SNMP Trap Type ID 1081 --- Anti-Spam Anti-Spam Anti-Spam ------- Warning Warning Information 1082 13801 1083 13802 1084 13803 Anti-Spam --- Information 1085 13804 Anti-Spam --- Warning 1086 13805 Anti-Spam --- Warning 1087 13806 Anti-Spam Anti-Spam Firewall Event ------- Warning Warning Notice 1088 13807 1089 13808 1090 --- Anti-Spam --- Notice 1091 13809 Anti-Spam --- Notice 1092 13810 Anti-Spam Anti-Spam ----- Notice Error 1093 13811 1094 13812 Anti-Spam --- Information 1095 13813 Anti-Spam --- Information 1096 13814 VPN PKI Intrusion Detection Intrusion Detection Network Monitor Network Monitor Network Monitor ------------- Notice Alert Alert Alert Alert Alert 1097 1098 1099 1100 1101 1102 Network Monitor --- Alert 1103 14004 Network Monitor Network Monitor Network Monitor Anti-Spam --------- Information Information Information Information 1104 1105 1106 1108 --------- VPN PKI DHCP Server DHCP Server FTP --------- Information Information Information Debug 1109 1110 1111 1112 --------- --6465 6466 14001 14002 14003 Index of Log Event Messages Log Event Message Ftp client user name was sent Ftp client user logged in successfully Ftp client user logged in failed Ftp client user logged out User login denied - SSO probe failed New Category FTP FTP FTP FTP Authenticate Access User login denied - Mail Address(From/to) or Authenticate SMTP Server is not configured Access RADIUS user cannot use One Time Authenticate Password - no mail address set for Access equivalent local user User login denied - Terminal Services agent Authenticate timeout Access User login denied - Terminal Services agent Authenticate name resolution failed Access User login denied - No name received from Authenticate Terminal Services agent Access User login denied - Terminal Services agent Authenticate communication problem Access User logged out - logout reported by Authenticate Terminal Services agent Access High Availability has been enabled and Dial- High Availability Up device(s) are not supported in High Availability processing. The High Availability monitoring IP High Availability configuration of Interface %s is incorrect. IKE Responder: ESP mode mismatch Local VPN IKE - Tunnel Remote - Transport IKE Responder: ESP mode mismatch Local VPN IKE - Transport Remote - Tunnel WAN DHCPC IP Changed Firewall Event WLAN DHCPC IP Changed Firewall Event Probe Response Success - %s Anti-Spam Probe Response Failure - %s Anti-Spam Peer HA firewall has stateful license but this High Availability firewall is not yet registered The stateful license of HA peer firewall is not High Availability activated Received unauthenticathed GRID response Anti-Spam Invalid key or serial number used for GRID Anti-Spam response Invalid key version used for GRID response Anti-Spam Host IP address not in GRID List Anti-Spam No response received from DNS server Anti-Spam Not blacklisted as per configuration Anti-Spam SNMP Trap Type ----------- Legacy Category --------User Activity Priority Debug Debug Debug Debug Warning ID 1113 1114 1115 1116 1117 User Activity Information 1118 --- User Activity Information 1119 --- User Activity Warning 1120 --- User Activity Warning 1121 --- User Activity Warning 1122 --- User Activity Warning 1123 --- User Activity Information 1124 --- --- Information 1125 --- --- Error 1126 --- User Activity Warning 1127 --- User Activity Warning 1128 --- System Error System Error ----System Error Warning Warning Debug Debug Alert 1129 1130 1131 1132 1136 System Error Alert 1137 --- ----- Debug Debug 1138 --1139 --- --------- Debug Debug Debug Debug 1140 1141 1142 1143 SonicOS Log Event Reference Guide ----------- --------- 55 Index of Log Event Messages Log Event Message Default to not blacklisted Failed to insert entry into GRID result IP cached table Resolved ES Cloud - %s Updated ES Cloud Address - %s Your Active/Active Clustering subscription has expired. Terminal Services agent is down Terminal Services agent is up Active/Active Clustering license is not activated on the following cluster units: %s SSLVPN Traffic Application Control Detection Alert: %s Application Control Prevention Alert: %s GMS or syslog server name lookup failed try again in 60 secs. User account '%s' expired and disabled User account '%s' expired and pruned Received Alert: Your Firewall Visualization Control subscription has expired. Attempt to contact Remote backup server for upload approval failed Backup remote server did not approve upload request Modules attached to HA units do not match: %s Malformed DNS packet detected A high percentage of the system packet buffers are held waiting for SSO A user has a very high number of connections waiting for SSO DOS protection on WAN begins %s DOS protection on WAN %s DOS protection on WAN %s Deleting IPsec SA (Phase 2) Delete invalid scope because port ip in the range of this DHCP scope. IKE Responder: Peer's network does not match VPN policy's Network Added new LDAP mirror user group: %s Deleted LDAP mirror user group: %s 56 SonicOS Log Event Reference Guide New Category Anti-Spam Anti-Spam Legacy Category Priority --Debug --Debug SNMP Trap Type ID 1144 --1145 --- Anti-Spam Anti-Spam High Availability ------- Debug Debug Warning 1146 --1147 --1149 --- SSO SSO High Availability User Activity User Activity --- Alert Alert Error 1150 --1151 --1152 --- SSL VPN App-Control Detection App-Control Detection Firewall Event Connection Traffic Information --Alert 1153 --1154 15001 --- Alert 1155 15002 --- Error 1156 --- Authenticate Access Authenticate Access Security Services User Activity Information 1157 --- User Activity Information 1158 --- --- Warning 1159 --- Firewall Event Maintenance Debug 1160 --- Firewall Event Maintenance Debug 1161 --- High Availability System Error Alert 1162 664 Network Access SSO Debug User Activity Alert Alert 1177 --1178 --- SSO User Activity Alert 1179 --- Intrusion Detection Intrusion Detection Intrusion Detection VPN IKE DHCP Server Debug Debug Debug User Activity --- Alert Warning Alert Debug Warning 1180 1181 1182 1183 1184 VPN IKE User Activity Warning 1189 --- RADIUS RADIUS User Activity User Activity Information Information 1190 --1191 --- ----------- Index of Syslog Tag Field Description Log Event Message Added a new member to an LDAP mirror user group Removed a member from an LDAP mirror user group Monitoring probe out interface mismatch %s New Category RADIUS Legacy Category Priority User Activity Information SNMP Trap Type ID 1192 --- RADIUS User Activity Information 1193 --- High Availability --- Error 1194 --- Index of Syslog Tag Field Description This section provides an alphabetical listing of Syslog tags and the associated field description. Tag Field Description <ddd> Syslog message prefix The beginning of each syslog message has a string of the form <ddd> where ddd is a decimal number indicating facility and priority of the message. (See [1] Section 4.1.1) arg URL Used to render a URL: arg represents the URL path name part. bcastRx Interface statistics report Displays the broadcast packets received bcastTx Interface statistics report Displays the broadcast packets transmitted bytesRx Interface statistics report Displays the bytes received bytesTx Interface statistics report Displays the bytes transmitted c Message category (legacy only) Indicates the legacy category number (Note: We are not currently sending new category information.) change Configuration change webpage Displays the basename of the firewall web page that performed the last configuration change code Blocking code Indicates the CFS block code category code ICMP type and code Indicates the ICMP code conns Firewall status report Indicates the number of connections in use cpuUtil Firewall status report Displays the CPU utilization (not in use) dst Destination Destination IP address, and optionally, port, network interface, and resolved name. dstname Destination URL Displays the URL of web site hit and other legacy destination strings dstname URL Used to render a URL: dstname represents the URL host part SonicOS Log Event Reference Guide 57 Index of Syslog Tag Field Description dyn Firewall status report Displays the HA and dialup connection state (rendered as “h.d” where “h” is “n” (not enabled), “b” (backup), or “p” (primary) and “d” is “1” (enabled) or “0” (disabled)) fw Firewall WAN IP Indicates the WAN IP Address fwlan Firewall status report Indicates the LAN zone IP address goodRxBytes SonicPoint statistics report Indicates the well formed bytes recevied goodTxBytes SonicPoint statistics report Indicates the well formed bytes transmitted i Firewall status report Displays the GMS message interval in seconds id=firewall Webtrends prefix Syntactic sugar for WebTrends (and GMS by habit) if Interface statistics report Displays the interface on which statistics are reported ipscat IPS message Displays the IPS category ipspri IPS message Displays the IPS priority lic Firewall status report Indicates the number of licenses for firewalls with limited modes m Message ID Provides the message ID number mac MAC address Provides the MAC address msg Static message Displays the event message (from spreadsheet) msg Dynamically-defined message Displays a dynamically defined message string msg Static message with dynamic string Displays a message using the predefined message string containing a “%s” and a dynamic string argument. msg Static message with dynamic number Displays a message using the predefined string string containing a “%s” and a dynamic numeric argument. msg IPS message Displays a message using the predefined message string containing a “%s” and a dynamic string argument. msg Anti-Spyware message Displays the event message (from spreadsheet) n Message count Indicates the number of times event occurs op HTTP OP code Displays the HTTP operation (GET, POST, etc.) of web site hit pri Message priority Displays the event priority level (0=emergency..7=debug) 58 SonicOS Log Event Reference Guide Index of Syslog Tag Field Description proto IP protocol Indicates the IP protocol and detail information proto Protocol and service Displays the protocol information (rendered as “proto/service”) proto Protocol and service Displays the protocol information (rendered as “proto/service”) pt Firewall status report Displays the HTTP/HTTPS management port (rendered as “hhh.sss”) radio SonicPoint statistics report Displays the SonicPoint radio on which event occurred ramUtil Firewall status report Displays the RAM utilization (not in use) rcvd Bytes received Indicates the number of bytes received within connection result HTTP Result code Displays the HTTP result code (200, 403, etc.) of web site hit rule Rule ID Displays the Access Rule number causing packet drop sent Bytes sent Displays the number of bytes sent within connection sid IPS message Provides the IPS signature ID sid Anti-Spyware message Provides the AntiSpyware signature ID sn Firewall serial number Indicates the device serial number spycat Anti-Spyware message Displays the antiSpyware category spypri Anti-Spyware message Displays the AntiSpyware priority src Source Indicates the source IP address, and optionally, port, network interface, and resolved name. station SonicPoint statistics report Displays the client (station) on which event occurred time Time Reports the time of event type ICMP type and code Indicates the ICMP type ucastRx Interface statistics report Displays the unicast packets received ucastTx Interface statistics report Displays the unicast packets transmitted unsynched Firewall status report Reports the time since last local change in seconds usesstandbysa Firewall status report Displays whether standby SA is in use (“1” or “0”) for GMS management SonicOS Log Event Reference Guide 59 Index of Syslog Tag Field Description usr (or user) User Displays the user name (“user” is the tag used by WebTrends) vpnpolicy VPN policy name Displays the VPN policy name of event 60 SonicOS Log Event Reference Guide 232-001835-00_Rev_A