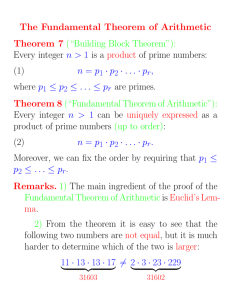
Arithmetic Complexity - UCLA Department of Mathematics
advertisement

Arithmetic Complexity
LOU VAN DEN DRIES
University of Illinois, Urbana-Champaign
and
YIANNIS N. MOSCHOVAKIS
University of California, Los Angeles and Graduate Program in Logic and Algorithms,
University of Athens, Greece
We obtain lower bounds on the cost of computing various arithmetic functions and deciding various arithmetic relations from specified primitives. This includes lower bounds for computing the
greatest common divisor and deciding coprimeness of two integers, from primitives like addition,
subtraction, division with remainder and multiplication. Some of our results are in terms of recursive programs, but they generalize directly to most (plausibly all) algorithms from the specified
primitives. Our methods involve some elementary number theory as well as the development of
some basic notions and facts about recursive algorithms.
Categories and Subject Descriptors: F.1.3 [Complexity measures and classes]: Machineindependent complexity; F.2.1. [Numerical algorithms and problems]: Number-theoretic
computations
General Terms: Lower bounds for arithmetical problems
Additional Key Words and Phrases: Recursive programs, greatest common divisor, coprimeness
1.
INTRODUCTION
Motivating question
To what extent is the euclidean algorithm optimal with respect to the number of
steps? Are there algorithms that compute the greatest common divisor of two
integers in many fewer arithmetic steps?
It is well-known that there are real constants c1 > c2 > 0 such that the euclidean
algorithm takes at most c1 log a steps on all integer inputs (a, b) with a > b > 0
and at least c2 log a steps on infinitely many integer inputs (a, b) with a > b > 0,
Authors’ addresses. Lou van den Dries, Department of Mathematics, University of Illinois, 1409
W. Green Street, Urbana, IL 61801, email: vddries@math.uiuc.edu. Yiannis N. Moschovakis,
Department of Mathematics, University of California, Los Angeles, CA 90095-1555, email:
ynm@math.ucla.edu.
The research for this article was co-funded by the European Social Fund and National Resources
- (EPEAEK II) PYTHAGORAS in Greece.
Permission to make digital/hard copy of all or part of this material without fee for personal
or classroom use provided that the copies are not made or distributed for profit or commercial
advantage, the ACM copyright/server notice, the title of the publication, and its date appear, and
notice is given that copying is by permission of the ACM, Inc. To copy otherwise, to republish,
to post on servers, or to redistribute to lists requires prior specific permission and/or a fee.
c 2007 ACM 1529-3785/07/0500-0001 $5.00
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007, Pages 1–48.
2
·
L. van den Dries and Y. N. Moschovakis
where each step consists of taking a remainder in an integer division.
One typical result in this paper, Theorem 3.8, is roughly as follows:
Any algorithm computing the greatest common divisor and using addition, subtraction, and integer division with remainder as given, will take more than 14 log log a
steps on infinitely many integer inputs (a, b) with a > b > 1.
“Using . . . as given” means that in each arithmetic step we add, subtract, divide
with remainder, and compare integers obtained at earlier steps. (There are also
logical steps.)
We prove similar results for the arithmetic complexity of other problems such
as deciding coprimeness of two integers, deciding whether an integer is a perfect
square, a power of two, or a prime number. In some results we restrict to Presburger
(piecewise linear) operations as given, or, in the other direction, allow multiplication
among the primitives as well. Thus we vary both the function to be computed, and
the set of primitives.
With only Presburger operations as given, we obtain single logarithmic lower
bounds for a large class of arithmetic functions; when we also allow integer division
with remainder, we get double logarithmic (log log) bounds√(as in the statement
above), and when we allow multiplication as well, we obtain log log-bounds. (All
logarithms are with respect to base 2.)
The following features add extra strength to some of our bounds:
(i) explicit inputs (characterized by natural arithmetic conditions) that witness
the lower bounds;
(ii) lower bounds on just the number of arithmetic steps, not counting logical steps
(equality tests and boolean operations);
(iii) allowing parallelism in the algorithms;
(iv) local (non-uniform) lower bounds for term-complexity with terms using arithmetic and boolean operations as well as equality tests.
We have tried to make this paper easily accessible to anyone interested in computational complexity, including those with no background knowledge in this subject.
To achieve this goal we have provided explicit definitions of notions that might be
less familiar to some readers, with brief summaries of basic facts as needed.
After a short preliminary section, this paper divides naturally into three parts,
with the last two largely independent of the first, except that some of the results
of Part 1 are given a more clearly algorithmic interpretation in Parts 2 and 3.
In Part 1 (Sections 3 and 4) we focus on the connection
greatest common divisor – irrationality,
improving results from [van den Dries 2003] and [van den Dries and Moschovakis
2004].
In Part 2 (Sections 5 – 10), we first develop a local (non-uniform) notion of arithmetic term-complexity, which measures for each N > 0 the minimum complexity
of a term t(~x) that computes a given function f : Nn → N for all n-tuples of numbers ≤ N . We formulate and prove a whole array of further results, including in
Section 7 the optimality of the binary gcd algorithm among algorithms that only
allow Presburger operations as arithmetic primitives, and in Section 9 a log log
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
3
lower bound for terms which decide coprimeness on initial segments of N, from
Presburger operations and division with remainder—the same primitives used by
the euclidean algorithm.
In Part 3 we review briefly the basic theory of recursive programs, and establish
lower bounds for global (uniform) algorithms corresponding to the non-uniform
lower bounds of Part 2. Many of these results have appeared in [van den Dries and
Moschovakis 2004], but they are easy to derive here from the results of Part 2.
The proofs in Part 1 depend on minimal and widely accepted assumptions about
“algorithms”, and so they are completely general. To derive lower bounds for
decision problems in Parts 2 and 3 we must make some assumptions about the
structure of algorithms, but these too are rather innocuous and we can argue that
these lower bounds also hold for all algorithms.
In the last section of the paper we have included a list of upper bounds in the
literature for the complexity of the functions and relations we consider, as we know
them.
The subject in this paper has deep historical roots, but the lower bounds are
recent. To our knowledge, the earliest substantial lower bounds close to ours are
about fifteen years old and are due to Mansour, Schieber and Tiwari [1991a; 1991b].
They use decision-tree complexity.
In another vein, Moschovakis [2003] considers primitive recursive algorithms with
piecewise linear functions as given, proves a linear lower bound on the complexity of
any such algorithm that computes the greatest common divisor function, and asks
if this result persists when the remainder function is included among the primitives.
Van den Dries [2003] answers this question affirmatively. However, these results on
primitive recursion have a negative character, by showing that all such algorithms
are very inefficient compared to known algorithms like the euclidean.
We soon noticed that some ideas in [van den Dries 2003] were relevant beyond
primitive recursion, to essentially all algorithms that compute the greatest common
divisor. We also saw how to improve the bounds in [van den Dries 2003] and extend
its methods to other functions and to decision problems, e.g., coprimeness. This
led to non-trivial lower bounds on algorithms computing various familiar arithmetic functions and using various combinations of arithmetic operations as given.
A communication with an outline of our methods and some of these results was
published in [van den Dries and Moschovakis 2004]. The present paper is intended
to give a more complete account of these improvements and extensions, and their
applications to lower bounds.
Articles [Moschovakis 2003; van den Dries 2003] were written in ignorance of
[Mansour et al. 1991a; 1991b] and use different methods. Here we recover most
of the lower bounds of [Mansour et al. 1991a; 1991b] in a stronger form by allowing more liberal notions of computation enjoying one or more of the features
(i)–(iv) above. But we do not know whether the triple logarithmic lower bound
of [Mansour et al. 1991a] on the decision-tree complexity for deciding coprimeness
is also valid for our term-complexity (and the same arithmetic primitives); we do
obtain in Theorem 4.1 a better lower bound for computing the gcd using these same
primitives.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
4
·
L. van den Dries and Y. N. Moschovakis
Conventions and notations
Throughout, m and n range over N := {0, 1, 2, . . . }. We define the floor or integer
part of x ∈ R by
bxc := largest integer ≤ x.
For positive x ∈ R, log x := log2 x is the base 2 logarithm of x. For a, b ∈ R, b 6= 0
we write
a
a = qb + r, q = b c ∈ Z
b
and we view the integer quotient q and the remainder r as functions of (a, b):
iq(a, b) := q and rem(a, b) := r. It is convenient to extend iq and rem to all
of R2 by setting iq(a, 0) := a and rem(a, 0) := a, so for all a, b ∈ R we have
a = iq(a, b)b + rem(a, b), with 0 ≤ rem(a, b) < b if b > 0.
Let a, b ∈ Z. We say that a divides b (notation: a|b) if ax = b for some x ∈ Z.
The greatest common divisor of a, b is by definition the unique nonnegative integer
c =: gcd(a, b) such that cZ = aZ + bZ. (So gcd(a, b) is indeed the largest integer
dividing both a and b, if a 6= 0 or b 6= 0.) We say that a and b are coprime (notation:
a ⊥ b) if gcd(a, b) = 1.
2.
THE EUCLIDEAN AND THE BINARY ALGORITHMS FOR THE GCD
This paper is about lower bounds for classes of algorithms computing a given function; the closer we can get such a lower bound to an upper bound for some known
algorithm in the class, the better. This is why we briefly discuss here upper bounds
for some specific algorithms.
The euclidean algorithm
Some historians believe that this algorithm lies behind the discovery of incommensurable magnitudes by the Pythagoreans. Whether or not this belief is correct,
the notions of greatest common divisor and incommensurability fit into a common
algorithmic setting, and we find this illuminating. It helps to understand why the
number of steps needed to decide coprimeness of two integers goes to infinity as
their ratio approximates a fixed irrational number, as we show in several variants
in later sections. Here we summarize the euclidean algorithm in a way that highlights this common context. We refer to [Knuth 1973] for more details on this
“granddaddy of all algorithms”.
Let a, b ∈ R, a > b > 0. We define a strictly decreasing (finite or infinite)
sequence of real numbers
r0 > r1 > r2 > . . .
by r0 := a, r1 := b, ri+1 := rem(ri−1 , ri ) for i > 0 as long as ri 6= 0. The
sequence stops with last term rl+1 = 0 as soon as this value is reached. We then
put l(a, b) := l = the euclidean length of (a, b).
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
5
Key properties
(i) The sequence is finite if and only if a and b are commensurable, that is, a/b is
rational.
(ii) ri+1 < (1/2)ri−1 for i > 0.
In particular, if a, b ∈ Z, then the sequence is finite with last term rl+1 = 0 with
gcd(a, b) = rl and l = l(a, b) ≤ 2 log b.
This bound is good enough for us. A logarithmic upper bound is indeed realistic
in view of an old result by Lamé which says that the “worst case” occurs when the
inputs are consecutive Fibonacci numbers; see [Knuth 1973]. A precise formulation
is as follows.
Let Fn := nth Fibonacci number: F0 = 0, F1 = 1 and Fn+1 := Fn + Fn−1 for
n > 0. For n > 0, let a, b be integers such that a > b > 0, l(a, b) = n and a is
minimal with these properties. Then a = Fn+1 , b = Fn .
Above we mentioned only the remainders ri , but in actual implementations of
the algorithm the integer quotients qi := iq(ri , ri+1 ) get computed as well, and are
also significant: they are the partial quotients of the continued fraction expansion
of a/b.
The binary (Stein) algorithm
(See Section 4.5.2 of [Knuth 1973]). This algorithm computes (recursively) gcd(a, b)
for positive integers a, b as follows: if a, b are both even, use gcd(a, b) = 2gcd(a/2, b/2);
if a is even and b is odd, use gcd(a, b) = gcd(a/2, b); if a and b are both odd, and
a > b, use gcd(a, b) = gcd((a − b)/2, b); the remaining cases are treated by interchanging a and b, and using gcd(a, b) = a if a = b.
The basic arithmetic relations and operations used here are: parity, comparison,
subtraction, multiplication by 2 and division by 2. The binary algorithm is simpler
than the euclidean algorithm, in the sense that each step involves only a linear operation. (Another contrast to the euclidean algorithm is that the binary algorithm
does not extend naturally to real numbers.) In practice, this algorithm can be
competitive with the euclidean algorithm on suitable inputs, especially when these
inputs are given in binary notation.
An easy induction shows that it takes at most 2(log a + log b) steps to compute
gcd(a, b) via the binary algorithm. For a precise statement to this effect we refer
to the beginning of Section 7, which contains an optimality result about the binary
algorithm.
PART 1. THE GREATEST COMMON DIVISOR
Here1 we obtain in a purely arithmetic setting lower bounds on the depth of greatest
common divisor computations. Parts 2 and 3 are needed to deal with relations such
as coprimeness.
1 The
material in this part improves results of [van den Dries 2003] and is due to van den Dries.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
6
·
L. van den Dries and Y. N. Moschovakis
Let a, b ∈ Z. We define a sequence (Gn (a, b)) of finite subsets of Z:
G0 (a, b) ⊆ G1 (a, b) ⊆ G2 (a, b) ⊆ . . .
G0 (a, b) := {0, 1, a, b}
Gn+1 (a, b) := Gn (a, b) ∪ {x + y, x − y, iq(x, y), rem(x, y) : x, y ∈ Gn (a, b)}.
We set
g(a, b) := least n such that gcd(a, b) ∈ Gn (a, b).
By Section 2 we have g(a, b) ≤ 2 log b when a > b > 0. In Section 3 we obtain a double√
logarithmic lower bound for g on an explicit sequence of rational approximations
to 2.
Next we define an increasing sequence of finite subsets of Z,
×
×
G×
0 (a, b) ⊆ G1 (a, b) ⊆ G2 (a, b) ⊆ . . .
in the same way as we defined the Gn (a, b), with G×
0 (a, b) = {0, 1, a, b}, except that
G×
(a,
b)
contains
also
all
products
xy
with
x,
y
∈
G×
n (a, b). We set
n+1
g× (a, b) := least n such that gcd(a, b) ∈ G×
n (a, b).
We have a crude upper bound: g× (a, b) ≤ 2 log √
log b for a ≥ b ≥ 4, see Section 4 of
[van den Dries 2003].2 In Section 4 we prove a log log lower bound for g× .
Notice that g(a, b) counts the number of steps needed to generate gcd(a, b) from
a, b, 0, 1 where at each step we apply +, −, iq and rem to all integers obtained at
earlier steps; and so it can be argued that every algorithm which computes gcd(a, b)
from these operations will take at least that many steps to produce its output. And
similarly with g× (a, b) when we add multiplication to the given operations: any
algorithm which computes gcd(a, b) from +, −, iq, rem and × will need at least
g× (a, b) steps to produce its output.
3.
A LOWER BOUND FOR THE GCD FROM +, −, ÷
Throughout this section a, b and h denote positive integers. We prove here the
following lower bound for g at certain inputs:
Theorem 3.1. If a2 − 2b2 = 1, b > 2, then
1
log log a.
6
In this connection we recall (see for example [Rose 1994]) that the positive integer
solutions of the Pell equation x2 − 2y 2 = 1 grow exponentially: if (an , bn ) is the
nth positive integer solution of this equation (n ≥ 1), then
g(a + 1, b) >
(a1 , b1 ) = (3, 2),
(a2 , b2 ) = (17, 12),
and in general
√
√
(3 + 2 2)n + (3 − 2 2)n
an =
,
2
2 Note
√
√
(3 + 2 2)n − (3 − 2 2)n
√
bn =
.
2 2
that g× differs slightly from the function g × in [van den Dries 2003].
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
7
The proof of the theorem proceeds in several lemmas, most of which do not
depend on (a, b) satisfying a2 − 2b2 = 1. The full hypothesis comes in through the
following, easy number-theoretic fact, which is even more important in the next
section:
Lemma 3.2. Suppose that a2 − 2b2 = 1. Then
p
(i) either a ≡ 1 mod 4 and gcd(a + 1, b) = 2(a + 1), or
√
(ii) a ≡ 3 mod 4 and gcd(a + 1, b) = a + 1.
Proof. Clearly a is odd and b is even. We first consider the case that a ≡ 1
mod 4. Then we have the factorization b2 = (a − 1) · (a + 1)/2, with coprime factors
a − 1 (which is even), and (a + 1)/2 (which is odd). Thus a − 1 = u2 , (a + 1)/2 = v 2 ,
and
p b = uv, with coprime positive integers u, v. Hence gcd(a + 1, b) = 2v =
2(a + 1). The case a ≡ 3 mod 4 is treated similarly.
What we really use from this lemma is the following consequence:
√
√
a2 − 2b2 = 1 =⇒ b ≤ gcd(a + 1, b) ≤ 2 b.
Another key fact we need is an effective measure of irrationality of
from a theorem of Liouville [Rose 1994]: for all a and b:
a √
1
| − 2| > 2 .
b
5b
Note also that if a2 − 2b2 = 1, then
a √
1
1
√ < 2.
0< − 2=
2
b
b
ab + b 2
However, the next four Lemmas 3.3 – 3.6 only use the much weaker
a √
1
| − 2| <
b
b
and refer to multiples
α := κa,
(1)
√
2 coming
(2)
β := κb,
where κ is any positive integer. For the proof of Theorem 3.1 we just need the case
κ = 1 of the next four lemmas, but other uses of these lemmas require higher values
of κ.
Lemma 3.3. Suppose (2) holds, h ≥ 2, b ≥ 10h2 and f = x + yα + zβ with
integers x, y, z such that |x|, |y|, |z| ≤ h, and y and z not both zero. Then
√
√
2h
< |y 2 + z|.
f = β y 2 + z + , || <
b
√
In particular, f 6= 0 and f has the same sign as y 2 + z.
Proof. We have
√
f
x
a
x
a √
= + y + z = + y( − 2) + y 2 + z
β
β
b
β
b
√
x
a √
= y 2 + z + ,
:= + y( − 2),
β
b
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
8
·
L. van den Dries and Y. N. Moschovakis
√
1
so || < 2h
b . If y 6= 0, then |y 2 + z| > 5|y| by Liouville’s inequality, which in view
of b ≥ 10h2 yields
√
1
2h
|y 2 + z| >
≥
> ||,
5h
b
√
1
> ||.
If y = 0 and z 6= 0, then obviously |y 2 + z| = |z| ≥ 1 > 5h
Lemma 3.4. Suppose (2) holds, h ≥ 2, b ≥ 10h4 , f = x1 + y1 α + z1 β, g =
x2 + y2 α + z2 β, where xi , yi , zi ∈ Z, |xi |, |y1 |, |zi | ≤ h for i = 1, 2 and y2 and z2 are
not both 0 (so g 6= 0 by the lemma above). Then
√
f
(y1 z2 − y2 z1 ) 2 + (z1 z2 − 2y1 y2 )
+ , || ≤ 7.
=
g
z22 − 2y22
Proof. Decomposing f and g as in the previous lemma yields
√
2h
f = β y1 2 + z1 + 1 , |1 | <
b
√
2h
g = β y2 2 + z2 + 2 , |2 | <
.
b
Hence
√
√
√
y1 2 + z1 + 1
(−y2 2 + z2 )(y1 2 + z1 + 1 )
f
√
√
= √
=
g
y2 2 + z2 + 2
(−y2 2 + z2 )(y2 2 + z2 + 2 )
√
F + δ1
=
, F := (y1 z2 − y2 z1 ) 2 + (z1 z2 − 2y1 y2 ), G := z22 − 2y22 ,
G + δ2
√
√
δ1 := (−y2 2 + z2 )1 , δ2 := (−y2 2 + z2 )2 .
With δ3 :=
−δ2
G+δ2
we have 1 + δ3 =
G
G+δ2 ,
F
f
=
+ ,
g
G
:=
so
f
g
=
(F +δ1 )(1+δ3 )
,
G
hence
δ1 (1 + δ3 ) + F δ3
.
G
It remains to show that || ≤ 7. Clearly,
|δ1 | ≤ (1 +
√
2)h|1 | ≤ (1 +
√
2)
2h2
5h2
1
<
≤ ,
b
b
2
2
and similarly, |δ2 | < 5hb ≤ 1/2. Since G is a nonzero integer we have |G| ≥ 1, so
√
|G + δ2 | > 1/2, and thus |δ3 | < 2|δ2 |. Also, |F | ≤ 2h2 2 + 3h2 ≤ 6h2 . Hence
|| ≤ 2δ1 + |F δ3 | ≤ 1 + 6h2
10h2
60h4
=1+
≤ 7.
b
b
With α = κa, β = κb as above, let
n x + yα + zβ
o
A(κ; h) := Z ∩
: x, y, z, w ∈ Z, |x|, |y|, |z| ≤ h, 0 < w ≤ h
w
and set A(h) := A(1; h).
Lemma 3.5. If (2) holds, h ≥ 2, b ≥ 10h8 , and f, g ∈ A(κ; h), then the numbers
f + g, f − g, iq(f, g), rem(f, g) belong to A(κ; h8 ).
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
9
It follows that for all a, b satisfying (2) and all ν ∈ N,
[h = 22
3ν
& b ≥ 10h] =⇒ [Gν (a + 1, b) ⊆ A(h) & Gν (α, β) ⊆ A(κ; h)].
(3)
Proof. Assume (2), h ≥ 2, b ≥ 10h8 , and f, g ∈ A(κ; h), g 6= 0. Write
f=
x1 + y1 α + z1 β
w1
and
g=
x2 + y2 α + z2 β
w2
where xi , yi , zi , wi ∈ Z, |xi |, |yi |, |zi | ≤ h, 0 < wi ≤ h for i = 1, 2. Adding these
fractions in the usual way shows that f + g, f − g ∈ A(κ; 2h2 ) ⊆ A(κ; h8 ). As to
iq(f, g) and rem(f, g), consider first the case that y2 6= 0 or z2 6= 0. Since
w2 x1 + w2 y1 α + w2 z1 β
f
=
,
g
w1 x2 + w1 y2 α + w1 z2 β
the previous lemma with h2 for h yields
√
f
w2 (y2 z1 − y1 z2 ) 2 + (2y1 y2 − z1 z2 )
+ ,
=
g
w1
2y22 − z22
Hence
|| ≤ 7.
√
|iq(f, g)| ≤ |w2 | |y2 z1 − y1 z2 | 2 + |2y1 y2 − z1 z2 | + 8
√
≤ h(2 2 + 3)h2 + 8 ≤ 7h3 .
In particular, iq(f, g) ∈ A(h8 ). Also
X + Y α + Zβ
, with
w1 w2
X = w2 x1 − iq(f, g)w1 x2
Y = w2 y1 − iq(f, g)w1 y2
Z = w2 z1 − iq(f, g)w1 z2 .
rem(f, g) = f − iq(f, g)g =
Hence |X|, |Y |, |Z| ≤ h2 + 7h5 ≤ h8 . Thus rem(f, g) ∈ A(κ; h8 ).
Next, suppose that y2 = z2 = 0, so |rem(f, g)| < |g| ≤ h, in particular rem(f, g) ∈
A(κ; h) ⊆ A(κ; h8 ). Also
iq(f, g) =
(x1 − rem(f, g)w1 ) + y1 α + z1 β
f − rem(f, g)
=
,
g
gw1
which yields iq(f, g) ∈ A(κ; h + h2 ) ⊆ A(κ; h8 ).
Now (3) follows by an easy induction on ν.
Lemma 3.6. Suppose (2) holds, h ≥ 2, b ≥ 400h4 , and f ∈ A(κ; h). Then
√
√
|f | < b or |f | > 2 b.
Proof. Write f = x+yα+zβ
w √ with x, y, z, w ∈ Z, |x|, |y|, |z| ≤ h, 0 < w ≤ h. If
y =√z = 0, then |f | ≤ h < b. Suppose
x + yα + zβ =
√ y 6= 0 1or z 6= 0. Then
1
and || ≤ 2h
<
β(y 2 + z + ) as in lemma 3.3, so |y 2 + z| > 5h
b
10h . Hence
√
√
β(y 2 + z + )
b
|f | = |
|>
≥2 b
2
w
10h
4
where the last inequality uses b ≥ 400h .
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
10
·
L. van den Dries and Y. N. Moschovakis
Proof of Theorem 3.1. Suppose a2 − 2b2 = 1, b > 2, and for any ν ∈ N, let
3ν
h := 22 . By Lemma 3.5,
b ≥ 10h =⇒ Gν (a + 1, b) ⊆ A(h).
With the key inequality (1), Lemma 3.6, and b > a/2, this gives
a ≥ 800h4 =⇒ gcd(a + 1, b) ∈
/ Gν (a + 1, b) =⇒ g(a + 1, b) > ν.
Thus with ν := g(a + 1, b) we have a < 800h4 . Since b > 2 we have ν ≥ 1. Taking
logarithms, the inequality a < 800h4 yields
log a < log 800 + 4 log h = log 800 + 4 · 23ν < 10 + 4 · 23ν < 26ν ,
hence log log a < 6ν, which completes the proof of Theorem 3.1.
Other inputs.
The next theorem gives a similar lower bound for g on a much bigger set of inputs.
The inputs of Theorem 3.1 grow exponentially and are thus very sparse, while those
in Theorem 3.8 have subquadratic growth. We also need the inputs of Theorem 3.8
in Section 9 to deal with coprimeness.
Lemma 3.7. Suppose (2) holds, b ≥ 12h2 and κ > h. Then κ ∈
/ A(κ; h).
with
Proof. Towards a contradiction, assume κ ∈ A(κ; h), so κ = x+yα+zβ
w
w, x, y, z ∈ Z, w 6= 0 and |w|, |x|, |y|, |z| ≤ h. Then (x − κw) + yα + zβ = 0, so, as
in the proof of Lemma 3.3,
√
w
a √
x
− + y( − 2) + y 2 + z = 0,
κb
b
b
x
w
a √
1 2h
1
| − + y( − 2)| < +
<
.
κb
b
b
b
b
5h
√
1
if y 6= 0 or z 6= 0. Therefore y = z = 0, hence x = κw, so
But |y 2 + z| > 5h
|x| > h, a contradiction.
Theorem 3.8. Suppose (2) holds with a ⊥ b and a ≥ 2256 . Let ν ∈ N be
3ν
maximal with a ≥ 20h2 where h := 22 . Then
1
g(α, β) > log log α,
4
where κ := h + 1, α := κa, and β := κb.
Proof. We have a ≥ 20 · 216 , so ν ≥ 1 and b ≥ 12h2 . From gcd(α, β) = κ, and
κ∈
/ A(κ; h), we conclude g(α, β) ≥ ν + 1 by Lemma 3.5. Also,
3(ν+1) 2
3ν+4
a < 20 · 22
= 20 · 22
,
3ν
3ν+4
so α = κa < 20 · 22 + 1 · 22
, so
log α < log 20 + 23ν + 1 + 23ν+4 ,
hence log log α < 3ν + 5, so
2
1
1
log log α − ≥ log log α
3
3
4
where the last inequality uses that a ≥ 2256 .
g(α, β) ≥ ν + 1 >
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
11
We claim that the inputs α in this theorem have subquadratic growth. To √
see this,
let a be any sufficiently large prime number, and then take b such that |a−b 2| < 1,
so a ⊥ b. It remains to observe that
p
α = aκ ≤ a(1 + a/20) ≤ a3/2 ,
and that the nth prime number is ≤ n11/10 for large enough n.
We can increase the set of inputs further by allowing a real parameter ρ:
Theorem 3.9.
√ Let 0 < ρ ≤ 1. Then there is a b(ρ) > 0 such that for all a, b, if
a > b > b(ρ), | 2 − a/b| < 1/bρ , and a ⊥ b, then
p
1
g(α, β) > log log α, where α = κa, β = κb, κ := 1 + b aρ /20c.
4
Sketch of Proof. First extend the lemmas in this section by taking bρ instead of b
in the inequalities that involve b; next, for large enough a, b as in the hypothesis of
3ν
the theorem, take ν ∈ N maximal with aρ ≥ 20h2 where h := 22 , and then follow
the proof of Theorem 3.8.
Open problem
Do there exist sequences (αn ) and (βn ) of positive integers and a real C > 0 such
that αn → ∞ and g(αn , βn ) > C log αn for all n? A positive solution would answer
one version of the motivating question in the introduction.
4.
A LOWER BOUND FOR THE GCD FROM +, −, ÷, ×
In this section we shall prove the following result:
Theorem 4.1. If a and b are positive integers such that a2 − 2b2 = 1, then
1p
log log b.
g× (a + 1, b) ≥
4
For a polynomial f (Y ) = a0 + a1 Y + · · · + an Y n ∈ R[Y ] (all ai ∈ R) we put
kf k = max |ai |.
i
Note that then for f, g ∈ R[Y ] with deg f ≤ n or deg g ≤ n we have
kf + gk ≤ kf k + kgk,
kf gk ≤ (n + 1) · kf k · kgk.
For the proof of the theorem we introduce distinct indeterminates X and Y as place
holders for numbers a and b as above. Consider the integral domain
R := R[X, Y ]/(X 2 − 2Y 2 − 1),
so R is the coordinate ring over R of the hyperbola X 2 − 2Y 2 = 1. Let x and y
denote the images of X and Y in R. The canonical map R[X, Y ] → R maps the
subring R[Y ] of R[X, Y ] isomorphically onto the subring R[y] of R, and
R = R[x, y] = R[y] + R[y]x,
x2 = 2y 2 + 1.
For F ∈ R, take the unique f, g ∈ R[Y ] with F = f (y) + g(y)x, and set
kF k = max(kf k, kgk).
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
12
·
L. van den Dries and Y. N. Moschovakis
We equip the fraction field R(x, y) of R with the unique ordering that makes it an
ordered field with y > R and x > 0. Note that then
√
x = y 2(1 + y −1 ),
where ∈ R(x, y) is an infinitesimal, that is, || < 1/n for all n > 0. We are
actually going to work inside the subring Q[x, y] = Q[y] + Q[y]x of R, and on this
subring the ordering is easy to make explicit: let F ∈ Q[x, y], F 6= 0, and write
F = f (y) + g(y)x with f, g ∈ Q[Y ]. Let d := max(deg f, 1 + deg g) ∈ N, and let
r, s ∈ Q be the coefficients of Y d in f and Y d−1 √
in g, respectively. (So d = 0 means
f = r 6= 0 and g = s = 0.) Then F = (r + s 2)y d (1 + y −1 ) with infinitesimal
∈ R(x, y), so
√
F > 0 ⇐⇒ r + s 2 > 0.
This suggests defining a degree function on Q[x, y] by
deg F := max(deg f, 1 + deg g) ∈ N for F 6= 0,
deg 0 := −∞.
Note that then, for F, G ∈ Q[x, y]:
deg(F G) = deg F + deg G,
deg F ≤ 0 ⇐⇒ F ∈ Q.
We define the set P (n, h) ⊆ Q[x, y] as follows:
nF
o
P (n, h) :=
: F ∈ Z[x, y], deg F ≤ n, kF k ≤ h, c ∈ Z, 0 < c ≤ h .
c
Below, h is a positive integer, and a, b are positive integers such that a2 −2b2 = 1.
Then, writing F ∈ R as F = f (y) + g(y)x with f, g ∈ R[Y ], we have the evaluation
map F 7→ F (a, b) := f (b) + g(b)a : R → R. This map respects the ring operations;
it also respects the ordering when restricted to P (n, h) with h small compared to
a:
Lemma 4.2. If b ≥ 20h2 and F ∈ P (n, h), F > 0, then F (a, b) > 0. If b ≥ 80h4 ,
then the evaluation map F 7→ F (a, b) : P (n, h) → Q is injective and preserves
order: F, G ∈ P (n, h), F < G =⇒ F (a, b) < G(a, b).
Proof. Assume that b ≥ 20h2 . We begin with an easy bound:
Suppose r, s ∈ Z are not both zero, and |r|, |s| ≤ h. Then
√
a
1
a
< |r + s | < 3h,
r + s 2 > 0 =⇒ r + s > 0.
6h
b
b
√
1
a
1
To see this, note that 5b2 < | 2 − b | < 2b2 , so
√
√
a
a
|r + s | ≤ |r + s 2| + |s|| 2 − | < 3h.
b
b
2
2
Hence |(r + s ab )(r − s ab | = |r2 − s2 ab2 | = |r2 − 2s2 − sb2 | > 12 , since |r2 − 2s2 | ≥ 1.
1
1
Thus |r + s ab | > 2|r−sa/b|
> 6h
. The remaining implication follows from
√
√
a
a
h
1
a
|(r + s 2) − (r + s )| = |s|| 2 − | ≤ 2 <
< |r + s |.
b
b
2b
6h
b
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
13
Next, let 0 < F ∈ Z[y] + Z[y]x, with kF k ≤ h, and put d := deg F . The case
d = 0 is trivial, so we assume d > 0. Write F = f (y) + g(y)x, with
f = rd Y d + · · · + r0 ∈ Z[Y ],
g = sd−1 Y d−1 + · · · + s0 ∈ Z[Y ].
√
From F > 0 we obtain rd + sd−1 2 > 0, and hence rd + sd−1 ab > 0. Setting
s−1 := 0, we have:
F (a, b) =
d
X
ci bi ,
ci := ri + si−1
i=0
a
for i = 0, . . . , d.
b
The polynomial
ci Y i ∈ R[Y ] has leading coefficient cd = rd + sd−1 ab , which is
positive, so this polynomial takes only positive values for real arguments > 1 +
|ci |
: 0 ≤ i < d}; this last quantity is by the bound above ≤ 1 + 18h2 < 20h2 ,
max{ |c
d|
Pd
so F (a, b) = i=0 ci bi > 0.
The second part of the lemma follows from the first part by noting that P (n, h)+
P (n, h) ⊆ P (n, 2h2 ), and 20(2h2 )2 = 80h4 .
P
Lemma 4.3. Let h ≥ n ≥ 1, b ≥ 210 h4 , and G ∈ P (n, h). Then
√
deg G ≤ 0 =⇒ |G(a, b)| < b,
√
deg G > 0 =⇒ |G(a, b)| > 2 b.
√
Proof. If deg G ≤ 0, then G ∈ Q and |G| ≤ h < b. Suppose deg G = d > 0
with d ≤ n. So G = f (y)+g(y)x
with f, g ∈ Z[Y ],
c
kf k, kgk ≤ h,
max(deg f, 1 + deg g) = d,
c ∈ Z, 0 < c ≤ h.
Put F := f (y) + g(y)x and write
f = rd Y d + · · · + r0 ∈ Z[Y ],
g = sd−1 Y
d−1
r0 , . . . , rd ∈ Z,
+ · · · + s0 ∈ Z[Y ],
s0 , . . . , sd−1 ∈ Z.
Then we have, with the notations in the proof of Lemma 4.2,
F (a, b) =
d
X
ci bi ,
ci := ri + si−1
i=0
a
for i = 0, . . . , d,
b
where s−1 = 0. Hence
|
d−1
X
i=0
while |cd bd | >
d
b
6h ,
ci bi | ≤ 3h
d−1
X
bi ≤ 3nhbd−1 ,
i=0
and thus
bd /6h − 3nhbd−1
|F (a, b)|
|G(a, b)| ≥
≥
h
h
√
1
3n d
> 2 b.
=b
−
6h2
b
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
14
·
L. van den Dries and Y. N. Moschovakis
Put A(n, h) := Z ∩ {F (a, b) : F ∈ P (n, h)}. It is easy to check that
(i) A(n, h) + A(n, h) ⊆ A(n, 2h2 ),
(ii) A(n, h) · A(n, h) ⊆ A(2n, (4n + 1)h2 ).
Lemma 4.4. Let n ≥ 1, h ≥ 4n + 1, b ≥ (2h)50n , and s, t ∈ A(n, h). Then
iq(s, t), rem(s, t) ∈ A 3n − 1, (2h)11n .
Proof. Write s =
f (b)+g(b)a
c
kf k, kgk, kkk, klk ≤ h,
and t =
k(b)+l(b)a
d
with f, g, k, l ∈ Z[Y ],
deg f, deg k ≤ n,
deg g, deg l ≤ n − 1,
and c, d ∈ Z, 0 < c, d ≤ h. The conclusion of the lemma holds trivially if t = 0, so
we shall assume below that t 6= 0.
We first treat the simple case deg(k(y) + l(y)x) = 0. Then l = 0 and k ∈ Z, so
|t| ≤ h, hence |rem(s, t)| < h, and thus
f (b) − rem(s, t)c + g(b)a
s − rem(s, t)
iq(s, t) =
=
,
t
ct
from which we get
iq(s, t) ∈ A(n, h + h2 ) ⊆ A 3n − 1, (2h)11n ,
rem(s, t) ∈ A(0, h) ⊆ A 3n − 1, (2h)11n .
For the rest of the proof we assume that deg(k(y) + l(y)x) > 0. Multiplying s
and t by k(b) − l(b)a yields
d[f (b)k(b) − g(b)l(b)(2b2 + 1) + g(b)k(b) − f (b)l(b) a]
s
=
.
t
c[k(b)2 − l(b)2 (2b2 + 1)]
So with N := 2n and H := (4n + 1)h3 , we have
θ(b) 6= 0, and
s
t
=
φ(b)+ψ(b)a
θ(b)
where φ, ψ, θ ∈ Z[Y ],
deg φ ≤ N, deg ψ ≤ N − 1, 0 < deg θ = 2 deg(k(y) + l(y)x) ≤ N,
kφk ≤ H, kψk ≤ H, kθk ≤ H.
We can also assume that the leading coefficient ` of θ is positive.
If deg(φ(y) + ψ(y)x) < deg θ, then |φ(b) + ψ(b)a| < θ(b) by Lemma 4.2, so either
iq(s, t) = 0 and rem(s, t) = s, or iq(s, t) = −1 and rem(s, t) = s + t, and in either
case we have the desired result. For the rest of the proof we can therefore assume
that
N ≥ max{deg φ, 1 + deg ψ} ≥ deg θ > 0.
Pseudo-division of φ and ψ by θ—see Chapter 6 in [von zur Gathen and Gerhard
1999]—gives
`N φ = q1 θ + r1 ,
`N ψ = q2 θ + r2
where qi , ri ∈ Z[Y ], deg ri < deg θ for i = 1, 2, and
kq1 k ≤ 2N −1 H N ,
kr1 k ≤ 2N H N +1 ,
kq2 k ≤ 2N −2 H N ,
kr2 k ≤ 2N −1 H N +1 .
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
15
(Details: if deg φ < deg θ, put q1 = 0 and r1 = `N φ; if deg φ ≥ deg θ, then
0 ≤ deg φ − deg θ ≤ N − 1, and we can use the bounds of Exercise 6.44 on p. 193
of [von zur Gathen and Gerhard 1999]; if deg ψ < deg θ, put q2 = 0 and r2 = `N ψ;
if deg ψ ≥ deg θ, then 0 ≤ deg ψ − deg θ ≤ N − 2, and we can use again the bounds
of that same exercise.) Hence
r1 (b) + r2 (b)a
`N s
= q1 (b) + q2 (b)a +
.
t
θ(b)
Let c2 be the coefficient of Y (deg θ)−1 in r2 . Then
√
√
|c2 2| < 2N −1 H N +1 2 < 2N H N +1 ` = leading coefficient of 2N H N +1 θ.
Thus by Lemma 4.3 and the way Q[x, y] is ordered, we have
|r1 (b) + r2 (b)a| < 2N H N +1 θ(b),
provided b ≥ 80 2N H N +2 )4 . This last inequality on b follows from our assumption
b ≥ (2h)50n because (2h)50n ≥ 80 2N H N +2 )4 . (To derive this last inequality, note
that it is equivalent to
250n h50n ≥ 80 · 28n (4n + 1)8n+8 h24n+24 ,
that is, to 242n h26n−24 ≥ 80 · (4n + 1)8n+8 . In view of h ≥ 4n + 1, it is enough that
242n (4n + 1)18n−32 ≥ 80, and this is easily verified for n = 1, and is obvious for
n > 1.) From |r1 (b) + r2 (b)a| < 2N H N +1 θ(b) we get
|
r1 (b) + r2 (b)a
| < 2N H N +1 .
θ(b)
2 (b)a
Therefore, with ρ := b r1 (b)+r
c:
θ(b)
iq(`N s, t) = (q1 (b) + ρ) + q2 (b)a,
Now iq(s, t) =
iq(`N s,t)−i
`N
|ρ| ≤ 2N H N +1 .
with i ∈ {0, . . . , `N − 1}, and `N ≤ H N , so
(q1 (b) + ρ − i) + q2 (b)a
,
`N
kq1 + ρ − ik ≤ 2N −1 H N + 2N H N +1 + H N .
iq(s, t) =
Next, for the remainder we have
rem(s, t) = s − iq(s, t)t
f (b) + g(b)a [(q1 (b) + ρ − i) + q2 (b)a][k(b) + l(b)a]
−
c
d`N
N
N
d` f (b) + d` g(b)a (q1 (b) + ρ − i)k(b) + q2 (b)l(b)(2b2 + 1)
=
−
cd`N
d`N
[(q1 (b) + ρ − i)l(b) + q2 (b)k(b)]a
−
d`N
N
d` f (b) − c q1 (b) + ρ − i k(b) − cq2 (b)l(b)(2b2 + 1)
=
cd`N
N
[d` g(b) − c q1 (b) + ρ − i l(b) − cq2 (b)k(b)]a
+
.
cd`N
=
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
16
·
L. van den Dries and Y. N. Moschovakis
Straightforward estimates using the last expression and earlier bounds yield
rem(s, t) ∈ A(3n − 1, (n + 1)2N +1 h2 H N +1 ).
Thus rem(s, t) ∈ A(3n − 1, (2h)11n ), provided (n + 1)2N +1 h2 H N +1 ≤ (2h)11n . This
last inequality is equivalent to
(n + 1)22n+1 (4n + 1)2n+1 h6n+5 ≤ 211n h11n ,
that is, to (n + 1)(4n + 1)2n+1 ≤ 29n−1 h5n−5 , which in view of h ≥ 4n + 1 holds if
n + 1 ≤ 29n−1 (4n + 1)3n−6 : this last inequality is easily verified for n = 1, and is
obvious for n > 1.
Corollary 4.5. Suppose that b ≥ 22
10m2
. Then
m 2
G×
m (a + 1, b) ⊆ A(3 , 2
4m2 +4
),
Also, gcd(a + 1, b) ∈
/ G×
m (a + 1, b) for m > 0.
Proof. The inclusion clearly holds for m = 0. Next, we have
4(m+1)2 +4
4m2 +4 11·3m
22
> 2 · 22
10(m+1)2
4m2 +4 50·3m
22
> 2 · 22
,
inequalities that are best checked for m = 0 by inspection, and are easily proved
for m > 0. With these inequalities, the inclusion follows by induction on m using
the previous lemma.
In view of the inequality right after the proof of Lemma 3.2, the claim about
4m2 +4
gcd(a + 1, b) follows from Lemma 4.3 (with n := 3m , h := 22
, m > 0). Thus
gcd(a + 1, b) ∈
/ A(n, h).
Proof of Theorem 4.1. The non-membership result about gcd(a+1, b) in this
10m2
corollary means that g× (a+1, b) > m whenever b ≥ 22
, m > 0, that is, whenever
√
√
10
b ≥ 22 and 0 < m ≤ √110 log log b. It follows that g× (a + 1, b) > √110 log log b
10
10
if b ≥ 22 , which yields the theorem for b ≥ 22 ; the result holds trivially for
10
2 ≤ b < 22 .
PART 2. LOWER BOUNDS FOR (NON-UNIFORM) TERM COMPLEXITY
The basic idea in Part 1 was that the computation of gcd(α, β) cannot take fewer
steps than those needed to construct the value gcd(α, β) from α and β using the
primitives, cf. the remarks at the end of the introduction to Part 1. In order to
derive lower bounds for arithmetic decision problems which take values in {0, 1},
we require more precise notions about algorithms. We introduce these in Section 5 for simple algorithms given by explicit terms with conditionals and equality
tests, and we derive lower bounds for these algorithms over initial segments of N
in Sections 6 – 10. In Part 3 we derive corresponding uniform lower bounds for
algorithms expressed by recursive programs. The idea in both of these parts is to
establish lower bounds on complexity using embeddings, roughly as automorphisms
are used to establish non-definability in a first order language.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
17
In connection with the non-uniform term algorithms of this Part, it is worth
noting that, because of the “lookup” algorithm, we cannot expect better than
logarithmic lower bounds, from any but the most trivial primitives. Lemma 5.2
states a precise version of this well-known fact.
5.
COMPUTATION IN PARTIAL ALGEBRAS AND TERM-COMPLEXITY
An adequate notion of computation demands that the function computed by an
algorithm may be partial as opposed to total . Moreover, certain basic functions
like “division by 2 on Z” are partial by nature. We write f : X * Y to indicate that
f is a partial function from X to Y , that is, f is a function with domain D(f ) ⊆ X
and codomain Y . This includes of course (total) functions f : X → Y . We write
f (x) ↓ (read “f (x) converges”) to indicate that x ∈ D(f ). In some places, we will
also appeal to the natural partial ordering of partial functions,
f v g ⇐⇒ (∀x ∈ X)[f (x)↓ =⇒ f (x) = f (y)]
(f, g : X * Y ).
Partial algebras
Let Φ be a signature, that is, a set of function symbols, each equipped with an arity
in N, and let
A = A, 0A , 1A , (φA )φ∈Φ ,
a Φ-algebra with 0, 1; thus 0A and 1A are distinguished elements of the set A with
0A 6= 1A , and φA : An * A is a partial n-ary function on A for φ ∈ Φ of arity n.
In this setting we deal with relations on A via their (total) characteristic functions: the characteristic function χR : An → {0, 1} ⊆ A of an n-ary relation R ⊆ An
is given by χR (a) = 1 if a ∈ R and χR (a) = 0 otherwise.
We often omit the superscript A in 0A , 1A and φA when no confusion with the
corresponding symbols 0, 1 and φ (for φ ∈ Φ) is likely. The distinction between
these symbols and their interpretations in A, whether or not shown on paper,
should of course be kept in mind.
Examples
The two algebras with 0, 1 encountered so far are
Z(1) := Z, 0, 1, +, −, iq, rem, <
and
Z(2) := Z, 0, 1, +, −, ·, iq, rem, < .
(4)
In referring to these structures as algebras we mean that < designates here the
characteristic function of the usual (strict) ordering on Z.
For each integer d > 0, let iq(−, d) denote the function x 7→ iq(x, d) : Z → Z. In
the next section we consider for each integer D > 1 the following algebra with 0, 1:
Z(divD ) := Z, 0, 1, +, −, iq(−, 1), iq(−, 2), . . . , iq(−, D), < .
(5)
The algebras Z(1), Z(2) and Z(divD ) are infinite and total, but their finite subalgebras (defined later in this section) are genuinely partial, and play a key role in the
rest of the paper.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
18
·
L. van den Dries and Y. N. Moschovakis
Objectifying the undefined
For each set A, choose an object ↑ ∈
/ A to represent “the undefined”, and let
A ↑ := A ∪ { ↑ }. Each partial function f : An * A extends naturally to a (total)
function
f ↑ : (A ↑ )n → A ↑
by setting f ↑ (a) = ↑ for each a ∈ An↑ \ D(f ). We call f ↑ the up-arrow extension
of f . Notice that for a ∈ An , f (a)↓ ⇐⇒ f ↑ (a) ∈ A.
Logical symbols
We introduce two symbols Eq and Co. The equality symbol Eq is interpreted in A
by the function
EqA : A2↑ → {0, 1, ↑ } ⊆ A ↑
given by EqA (a, b) = 1 if a, b ∈ A and a = b, EqA (a, b) = 0 if a, b ∈ A and a 6= b,
and EqA (a, b) = ↑ if a = ↑ or b = ↑ . The conditional symbol Co is thought of
as “if . . . , then . . . , else . . . ” and it is interpreted in A by the ternary function
CoA : A3↑ → A ↑ given by
CoA (a, b, c) = b if a = 1,
CoA (a, b, c) = c if a ∈ A, a 6= 1,
CoA (a, b, c) = ↑ if a = ↑ .
Again, we often omit the superscript A in EqA and CoA when no confusion with
the symbols Eq and Co is likely.
Notice that EqA is the up-arrow extension of the characteristic function of the
equality relation on A, but CoA is not the up-arrow extension of any partial function
on A, because it takes values in A on some inputs which include the object ↑ , e.g.,
Co(1, 0, ↑ ) = 0. (In computer science terminology, Co is a non-strict function
on A ↑ .) We consider 0, 1, Eq, Co as four distinct (logical) symbols, not among
the symbols in Φ and independent of A. In constructing Φ-terms (see below) we
consider 0, 1 as constant (nullary) function symbols, Eq as a binary function symbol,
and Co as a ternary function symbol.
In addition we fix once and for all infinitely many variables: symbols of arity 0,
not in the set {0, 1, Eq, Co} ∪ Φ.
Terms with equality tests and conditionals
A Φ-term with equality tests and conditionals is a word on the alphabet
{variables} ∪ {0, 1, Eq, Co} ∪ Φ
formed according to the usual syntactic rules that take into account the arity of
the symbols.
For brevity we write “Φ-term” instead of “Φ-term with equality tests and conditionals”. The length of a Φ-term is its length as a word. So the Φ-terms of length
one are 0, 1 and the words x and φ where x is a variable and φ ∈ Φ has arity 0; the
Φ-terms of length > 1 are exactly the words φt1 . . . tn where φ ∈ {Eq, Co} ∪ Φ has
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
19
arity n > 0 and t1 , . . . , tn are Φ-terms. For better readability we often write such
a Φ-term φt1 . . . tn as φ(t1 , . . . , tn ).
Term evaluation
Below x, y denote distinct variables, ~x denotes a tuple (x1 , . . . , xm ) of distinct variables, and so does ~y = (y1 , . . . , yn ). In referring to a Φ-term t(~x) we mean a Φ-term
t together with a tuple ~x = (x1 , . . . , xm ) such that all variables occurring in t are
among x1 , . . . , xm . Such a Φ-term t(~x) defines a function
~a 7→ t(~a) : Am
↑ → A↑,
~a = (a1 , . . . , am )
as follows: if t is xi , then t(~a) := ai ; if t is 0, 1, then t(~a) := 0, 1, respectively; if t is Eq(t1 , t2 ), then t(~a) := Eq(t1 (~a), t2 (~a)); if t = Co(t1 , t2 , t3 ), then
t(~a) := Co(t1 (~a), t2 (~a), t3 (~a)); if t = φ(t1 , . . . , tn ) with n-ary φ ∈ Φ, then t(~a) :=
φ ↑ (t1 (~a), . . . , tn (~a)).
We only care about the value of t(~a) when all components ai lie in A, but have
to allow ai = ↑ because of the inductive nature of the definition. If it is necessary
to indicate the Φ-algebra A in which t(~a) is computed, we write tA (~a) instead of
t(~a).
Given a Φ-algebra A, we also refer to a Φ-term t(~x) as an A-term.
Boolean operations
We can express boolean operations by Φ-terms as follows. Let ¬(x), ∨(x, y) and
∧(x, y) be the Φ-terms defined by
¬(x) := Co(x, 0, 1), ∨(x, y) := Co(x, 1, y), ∧(x, y) := Co(x, y, 0).
Then we have, with 0, 1 ∈ A:
¬(0) = 1, ¬(1) = 0,
∨(0, 0) = 0, ∨(0, 1) = ∨(1, 0) = ∨(1, 1) = 1,
∧(0, 0) = ∧(0, 1) = ∧(1, 0) = 0, ∧(1, 1) = 1.
Terms as algorithms
Let t(~x) be an A-term, g : Am
↑ → A ↑ a function on the up-arrow extension of A,
m
and S ⊆ A ↑ . We say that t(~x) computes g on S if t(~a) = g(~a) for all ~a ∈ S.
We are primarily interested in the case when S ⊆ Am and g = f ↑ is the up-arrow
extension of a partial function f : Am * A, in which case we will say simply that
“t(~x) computes f on S”. (But it is useful to have the more general notion.) If
S ⊆ Am and f is the characteristic function of an m-ary relation R ⊆ Am , we also
say that “t(~x) decides” (rather than “computes”) R on S.
We think of terms as expressing algorithms of a particularly explicit nature. In
Part 3 we will consider McCarthy programs which express more general (recursive)
algorithms; by Proposition 11.4 terms define exactly the recursive algorithms of
bounded complexity.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
20
·
L. van den Dries and Y. N. Moschovakis
Depth and arithmetic depth
The depth of a Φ-term t is the natural number defined inductively as follows:
depth(t) := 0 if t is 0, 1 or a variable,
depth(t) := 1 + max{depth(t1 ), . . . , depth(tn )} if t = φ(t1 , . . . , tn )
where φ ∈ {Eq, Co} ∪ Φ has arity n.
Here and below we set max ∅ := 0, so depth(t) = 1 if t is a constant symbol in Φ.
We modify this depth to arithmetic depth by taking into account only function
symbols in Φ. The arithmetic depth of a Φ-term t is the natural number defined
inductively as follows:
deptha (t) := 0 if t is a variable or 0 or 1,
deptha (t) := max{deptha (t1 ), . . . , deptha (tn )}
if t = φ(t1 , . . . , tn ) where φ ∈ {Eq, Co} has arity n,
deptha (t) := 1 + max{deptha (t1 ), . . . , deptha (tn )}
if t = φ(t1 , . . . , tn ) where φ ∈ Φ has arity n.
In particular, deptha (t) = 1 if t is a constant symbol in Φ.
Embeddings
Let B = (B, 0, 1, . . . ) be a second Φ-algebra.
A map ı : A → B is said to be an embedding of A into B if ı(0) = 0, ı(1)
= 1 and
for each φ ∈ Φ of arityn and ~a ∈ D(φA ) we have ı(~a) := ı(a1 ), . . . , ı(an ) ∈ D(φB )
and ı φ(~a) = φ ı(~a) . We write ı : A B to indicate that ı is an embedding
of A into B. One easily verifies that for such an embedding ı, a Φ-term t(~x), and
~a ∈ Am , we have
tA (~a)↓ =⇒ ı tA (~a) = tB ı(~a) .
In case A ⊆ B and the inclusion map A ,→ B is an embedding A B we call A
a subalgebra of B. For each set U ⊆ A with 0, 1 ∈ U we obtain a subalgebra A U
of A by taking U as its underlying set, and requiring D(φA U ) = {~a ∈ U n : ~a ∈
D(φA ), φA (~a) ∈ U } for each φ ∈ Φ of arity n. (Notice that φAU may not be a
total function, even if φA is total.)
All proofs of lower bounds in later sections use embeddings of algebras A U into
A which are not given by the inclusion U ,→ A.
Composition of terms
We compose terms as follows: given a Φ-term t(~x) and Φ-terms τ1 (~y ), . . . , τm (~y ),
we let t(τ1 (~y ), . . . , τm (~y )) be the Φ-term t∗ (~y ) obtained from t by replacing each
occurrence of a variable xi in t by τi . One verifies easily by induction on depth(t)
that then
t∗ (~b) = t(τ1 (~b), . . . , τm (~b)) for ~b ∈ An↑
depth(t(τ1 (~y ), . . . , τm (~y )) ≤ depth(t) + max{depth(τ1 ), . . . , depth(τm )}
deptha (t(τ1 (~y ), . . . , τm (~y )) ≤ deptha (t) + max{deptha (τ1 ), . . . , deptha (τm )}
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
21
Arithmetic depth and generation
For X ⊆ A and k ∈ N we define the set GA
k (X) ⊆ A generated by X in k steps in
the obvious way:
GA
0 (X) :={0, 1} ∪ X
A
A
n
~
~
GA
k+1 (X) :=Gk (X) ∪ {φ(b) : φ ∈ Φ has arity n, b ∈ D(φ) ∩ Gk (X) }.
A
A
A
A
A
Note that GA
0 (X) ⊆ G1 (X) ⊆ G2 (X) ⊆ . . . , and Gk (G` (X)) = Gk+` (X).
m
A
A
Let ~a = (a1 , . . . , am ) ∈ A and put Gk (~a) := Gk ({a1 , . . . , am }). An easy
induction on k yields
Lemma 5.1. GA
a) = A ∩ {t(~a) : t(~x) is a A-term with deptha (t) ≤ k}. If
k (~
⊆ U ⊆ A, then for each Φ-term t(~x) with deptha (t) ≤ k we have tA U (~a) =
t (~a).
GA
a)
k (~
A
The second part of this lemma states a useful absoluteness property. Note that
with the notations from Sections 3 and 4 we have
Z(1)
Gk
(a, b) = Gk (a, b),
Z(2)
Gk
(a, b) = G×
k (a, b),
a, b ∈ Z.
Examples
(i) Let A = (N, 0, 1, +) and a ∈ N>0 . We claim that there is an A-term t(x) such
that t(a) = a2 and deptha (t) ≤ 2 log a.
To see this, write a = 2e(0) + · · · + 2e(k) with integers 0 ≤ e(0) < · · · < e(k),
so k ≤ e(k) ≤ log a < e(k) + 1. Iterated doubling yields 2e a ∈ GA
e (a) for all
e ∈ N, in particular, 2e(0) a, . . . , 2e(k) a ∈ GA
(a).
Adding
these
numbers
yields
e(k)
2
A
a ∈ Ge(k)+k (a). Now use that e(k) + k ≤ 2 log a.
This upper bound is matched by a similar lower bound: deptha (t) ≥ log a for
each A-term t(x) such that t(a) = a2 . (To see this, note that by induction on
e
e ∈ N we have max GA
e (a) = 2 a.) This lower bound remains valid for A =
(Z, 0, 1, +, −, iq, rem, gcd, <) and a ∈ N>0 because addition and subtraction are the
only primitives of A that can output numbers larger in absolute value than the
inputs.
(ii) In connection with A = Z(1), we can reformulate Theorem 3.1 as saying
that whenever a, b are integers > 2 such that a2 − 2b2 = 1, then any Z(1)-term
t(x, y) such that t(a + 1, b) = gcd(a + 1, b) must have arithmetic depth greater than
1
6 log log a. Theorem 4.1 can be reformulated in a similar way with lower bounds
on the arithmetic depth of Z(2)-terms computing the gcd of certain integers.
Lower bound√
arguments as in Example (i) are too crude to deal with arithmetic
functions like b nc. More refined results on growth functions as in Example (ii)
still cannot handle decision problems where 0 and 1 are the only values to be
determined. For such problems we need a more subtle approach.
Term-complexity
We define two non-uniform measures of complexity, one based on depth, the other
on arithmetic depth.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
22
·
L. van den Dries and Y. N. Moschovakis
Let f : Am * A be a partial function and S ⊆ Am . (In applications S will be
finite.) If there is an A-term t(~x) that computes f on S, then we let cA (f, S) be
the minimal depth of such a term, and call it the term-complexity of computing f
on S in A. If there is no such term we put cA (f, S) = ∞. If f is the characteristic
function of an m-ary relation R ⊆ Am , we also write cA (R, S) for cA (f, S) and call
it the term-complexity of deciding R on S.
When in this definition we replace “depth” by “arithmetic depth”, then termcomplexity turns into arithmetic term-complexity, and the notations cA (f, S) and
A
A
A
cA (R, S) must be replaced by cA
a (f, S) and ca (R, S). Note that ca (f, S) ≤ c (f, S).
A
A
Usually we have N ⊆ A and 0 and 1 are the elements 0 and 1 of N. In that
case we write cA (f, N ) instead of cA (f, S) for S = {1, . . . , N }m , N ∈ N>0 , and we
A
use cA (R, N ), cA
a (f, N ) and ca (R, N ) in a similar way.
We have an easy logarithmic upper bound when addition is a primitive:
Lemma 5.2 The lookup term algorithm. Given any relation R ⊆ Nm and
any integer N > 0 we have cA
a (R, N ) ≤ 2 log N , where A = (N, 0, 1, +).
Proof. For the simplest case m = 1, argue as in Example (i) above: For n ≥ 1
we have n = 2e(0) + · · · + 2e(k) , with e(0) < e(1) < · · · < e(k) and e(k) + k ≤ 2 log n,
so n is the value in A of a closed term of arithmetic depth ≤ 2 log n, and hence the
unary relation x = n on N is decided by a term tn (x) of arithmetic depth ≤ 2 log n.
It follows that R is decided on {1, . . . , N } by the “disjunction” of the terms tn (x)
for which 1 ≤ n ≤ N and R(n) holds. The case m > 1 is handled in the same
way.
In the next two sections we deal with the following situation: We are given an
m-ary relation R ⊆ Am and a finite set S ⊆ Am , and are interested in a lower
A
bound on cA
a (R, S) or c (R, S). In this connection the following is relevant.
Lemma 5.3. Let ~a ∈ S be such that R(~a) holds. Suppose GA
a) ⊆ U ⊆ A
k (~
(k ∈ N), and ı : A U A is an embedding such that ı(~a) ∈ S and ¬R(ı(~a)).
Then cA
a (R, S) > k.
Proof. Let t(~x) be an A-term such that tA (~a) = 1 and deptha (t) ≤ k. Then
t
(~a) = 1 by the absoluteness property of Lemma 5.1, hence tA (ı(~a)) = 1. But
¬R(ı(~a)), so t cannot decide R on S.
AU
This suggests how to go about obtaining lower bounds: construct an embedding
ı as above with k as high as possible.
Robustness of term-complexity
Let B = B, 0B , 1B , (ψ B )ψ∈Ψ be a second partial algebra with 0, 1 such that
A = B, 0A = 0B , 1A = 1B . Then A is said to be term-reducible to B if each
n
n-ary φA
↑ with φ ∈ Φ is computable by a B-term on A ↑ . Note that the relation of
term-reducibility is reflexive and transitive. The corresponding equivalence relation
is called term-equivalence, that is, A and B are term-equivalent if and only if A
is term-reducible to B and B is term-reducible to A. In that case A and B are
essentially equivalent from the term-complexity viewpoint. More precisely, we have
the following robustness or invariance feature of term-complexity.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
23
Lemma 5.4. Suppose Φ is finite and A is term-reducible to B. Then there are
positive integers c(A, B), ca (A, B) such that for all f : An * A and S ⊆ An we
have
A
cB (f, S) ≤ c(A, B) · cA (f, S) and cB
a (f, S) ≤ ca (A, B) · ca (f, S).
Proof. For each m-ary φ ∈ Φ, let tφ (~x) be a B-term that computes φ on Am
↑.
Take positive integers c(A, B) and ca (A, B) such that c(A, B) ≥ depth(tφ ) and
ca (A, B) ≥ deptha (tφ ) for all φ ∈ Φ.
We define inductively for each A-term t(~y ) a B-term B t(~y ) as follows: if t(~y ) is the
B
variable yj , then B
t(~y ) is 0, 1, respectively; if t(~y) =
t(~y ) is yj ; if t(~y ) is 0, 1, then B
φ t1 (~y ), . . . , tk (~y ) with k-ary
φ
∈
{Eq,
Co},
then
t(~y ) := φ B t1 (~y ), . . . , B tk (~y ) ; if
t(~y ) = φ t1 (~y ), . . . , tm (~y ) with m-ary φ ∈ Φ, then B t(~y ) := tφ B t1 (~y ), . . . , B tm (~y ) .
An obvious induction using the facts on composition of terms then yields t(~a) =
B
t(~a) for all ~a ∈ An↑ and
depth(B t) ≤ c(A, B) · depth(t) and deptha (B t) ≤ ca (A, B) · deptha (t).
The lemma now follows easily.
Circuits
One could also introduce circuits, directed acyclic graphs whose nodes are labeled
by either a variable (input gate), or a logical symbol (logic gate), or an element of
Φ (arithmetic gate). Circuits do the same job as terms, but can be much smaller in
size as measured by the number of edges of a circuit versus the length of a term; see
[Poizat 1995]. So far our methods only yield lower bounds on computational depth,
and circuits perform no better than terms when depth is the relevant parameter.
Therefore we do not consider circuits in this paper.
6.
LOWER BOUNDS WITH LINEAR OPERATIONS AS PRIMITIVES
Throughout this section and the rest of Part 2 we let a, b, c, d, e, sometimes with
subscripts, denote integers, while κ, λ, p, N range over positive integers.
Presburger functions
Presburger arithmetic refers to the first order theory of the structure (Z, 0, 1, +, −, <),
the ordered group of integers with 1 as distinguished element. A classical result
due to Presburger (and Skolem, see [Smoryński 1991]) is that this structure has
elimination of quantifiers when we admit as extra primitives the unary relations
2Z, 3Z, 4Z, 5Z, . . . .
This means the following. A basic Presburger set in Zn is by definition an intersection of finitely many sets of the form
{~a ∈ Zn : q(~a) = 0}, {~a ∈ Zn : q(~a) > 0}, and {~a ∈ Zn : q(~a) ∈ dZ},
where q(X1 , . . . , Xn ) ∈ Z[X1 , . . . , Xn ] is a polynomial of degree at most 1, and
d > 0. A Presburger set in Zn is by definition a finite union of basic Presburger
sets in Zn .
Then a subset of Zn is (first-order) definable in (Z, 0, 1, +, −, <) iff it is a Presburger set in Zn . Also, a partial function f : Zn * Z is definable in (Z, 0, 1, +, −, <)
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
24
·
L. van den Dries and Y. N. Moschovakis
iff its domain D(f ) is a disjoint union of of basic Presburger sets B1 , . . . , Bk in Zn
and there are polynomials q1 (X), . . . , qk (X) ∈ Q[X], X = (X1 , . . . , Xn ), of degree
at most 1 such that f (~a) = qj (~a) for all ~a ∈ Bj , j = 1, . . . , k.
Let Lin denote the collection of all partial functions Zn * Z (for all n) that
are definable in (Z, 0, 1, +, −, <). (We choose this notation to reflect the piecewise
linear nature of these functions.)
Let Φ be a finite subset of Lin, and let A := Z, 0, 1, (φ)φ∈Φ be the corresponding partial algebra with 0, 1.
Theorem 6.1. Let R ⊆ Z be a unary relation, and let F : N>0 → N>0 be such
that for all λ and p:
(i) R(p) =⇒ ¬R(κp) with κ = 1 + λF (λ),
(ii) F (λ) ≤ dλe , with d, e > 0 independent of λ.
Then there is a p0 ∈ N and a real constant r > 0 such that if p > p0 and R(p)
holds, and N := dpe+2 , then
cA
a (R, N ) > r log N.
(6)
In particular, if R(p) holds for infinitely many p, then (6) holds for infinitely
many N .
The proof will show that p0 and r can be chosen to depend only on A and on
(A, d, e), respectively, and not on R.
Corollary 6.2. The relations Ri ⊆ Z and functions Fi , i = 1, . . . , 4, defined
below satisfy the hypothesis of the theorem, and so its conclusion:
R1 (x) :⇐⇒ x > 0 and x is prime,
R2 (x) :⇐⇒ x > 0 and x is a power of 2,
R3 (x) :⇐⇒ x > 0 and x is a perfect square,
R4 (x) :⇐⇒ x > 0 and x is square-free,
F1 (λ) = 1
F2 (λ) = 2
F3 (λ) = λ
F4 (λ) = 2 + λ.
Note that (Z, 0, 1, (φ)φ∈Φ ) is term-reducible to Z(divD ) as defined in (5), where
D is an integer > 1 depending on Φ. Thus by Lemma 5.4, it suffices to prove the
Theorem for A = Z(divD ), and this is what we do below.
Lower bounds for Z(divD )
Let D be an integer > 1, E := D!, and A := Z(divD ). Let ~a = (a1 , . . . , an ), and,
for k ∈ N, put
o
nc + c a + · · · + c a
0
1 1
n n
: |c0 |, . . . , |cn | ≤ (2E)k .
Bk (~a) := Z ∩
k
E
Lemma 6.3. We have the following inclusions for k ∈ N:
(i) Bk (~a) ⊆ Bk+1 (~a);
(ii) Bk (~a) + Bk (~a) ⊆ Bk+1 (~a), Bk (~a) − Bk (~a) ⊆ Bk+1 (~a);
(iii) iq Bk (~a), d ⊆ Bk+1 (~a) for 1 ≤ d ≤ D;
(iv) GA
a) ⊆ Bk (~a).
k (~
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
25
Proof. The last inclusion follows from the earlier ones by induction and from
GA
a) = {0, 1, a1 , . . . , an } ⊆ B0 (~a).
0 (~
Let b ∈ Bk (~a), and write
b=
c0 + c1 a1 + · · · + cn an
,
Ek
|c0 |, . . . , |cn | ≤ (2E)k .
Then
Ec0 + Ec1 a1 + · · · + Ecn an
,
|Ec0 |, . . . , |Ecn | ≤ (2E)k+1 ,
E k+1
so b ∈ Bk+1 (~a). Let 1 ≤ d ≤ D and iq(b, d) = (b − i)/d, 0 ≤ i < d. Then
b=
(E/d)(c0 − iE k ) + (E/d)c1 a1 + · · · + (E/d)cn an
E k+1
k
with |(E/d)(c0 − iE )|, |E/d)c1 |, . . . , |(E/d)cn | ≤ (2E)k+1 ,
iq(b, d) =
so iq(b, d) ∈ Bk+1 (~a).
Let b, b0 ∈ Bk (~a), write b as above and
b0 =
c00 + c01 a1 + · · · + c0n an
,
Ek
|c00 |, . . . , |c0n | ≤ (2E)k .
Then
E(c0 + c00 ) + E(c1 + c01 )a1 + · · · + E(cn + c0n )an
,
E k+1
with |E(c0 + c00 )|, . . . , |E(cn + c0n )| ≤ (2E)k+1 ,
b + b0 =
so b + b0 ∈ Bk+1 (~a), and similarly with b − b0 .
Lemma 6.4. Suppose |c0 |, |c1 | < a. Then
(i) c0 + c1 a = 0 ⇐⇒ c0 = c1 = 0;
(ii) c0 + c1 a > 0 ⇐⇒ either c1 > 0, or (c1 = 0 and c0 > 0).
Suppose |c0 |, |c1 |, |d0 |, |d1 | < a2 . Then
(iii) c0 + c1 a = d0 + d1 a ⇐⇒ c0 = d0 and c1 = d1 ;
(iv) c0 + c1 a < d0 + d1 a ⇐⇒ either c1 < d1 , or (c1 = d1 and c0 < d0 ).
We leave (i) and (ii) as an easy exercise; note that (iii) and (iv) follow.
Lemma 6.5. Let a > (D + 1)(2E)m , κ ≡ 1 mod E m , and U := Bm (a). Then
we have an embedding ı : A U A given by
c + c a c + c κa
0
1
0
1
ı
=
, |c0 |, |c1 | ≤ (2E)m .
(7)
Em
Em
Proof. By Lemma 6.4, (7) defines a mapping ı, and it is quite easy to prove that
it is an embedding ı : A U A, using Lemma 6.4. We verify here only one item
to explain why the factor D + 1 is included in the inequality on a. Let c ∈ U ∩ dZ
and 1 ≤ d ≤ D be such that c/d ∈ U ; we need to check that then ı(c/d) = ı(c)/d.
Write c = (c0 + c1 a)/E m and c/d = (d0 + d1 a)/E m with |ci |, |di | ≤ (2E)m for
i = 0, 1. Then (c0 − d0 d) + (c1 − d1 d)a = 0, so c0 = d0 d and c1 = d1 d by the
inequality on a and part (i) of Lemma 6.4. Hence ı(c/d) = ı(c)/d.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
26
·
L. van den Dries and Y. N. Moschovakis
The following result is a more precise version of Theorem 6.1 for the algebra
A = Z(divD ).
Theorem 6.6. Suppose R ⊆ Z is a unary relation, F : N>0 → N>0 is a function
and d, e > 0 are such that for all λ and p:
(i) R(p) =⇒ ¬R(κp) with κ = 1 + λF (λ),
(ii) F (λ) ≤ dλe .
Then for all p > D + 1, if R(p) holds and N := dpe+2 , then
cA
a (R, N ) > r log N, where r =
1
.
(2e + 4 + log d) log 2E
(8)
In particular, if R(p) is true for infinitely many p, then (8) holds for infinitely
many N .
The specific value of r is of no consequence, of course, but it witnesses the fact
that r is independent of the specific relation R and it exhibits the form of its
dependence on D, e and d.
Proof. Suppose p > D + 1 and R(p). Take m such that
(D + 1)(2E)m < p ≤ (D + 1)(2E)m+1 .
Put κ := 1 + E m F (E m ), so ¬R(κp). By Lemma 6.5 we have an embedding ı :
A Bm (p) A such that ı(p) = κp. Also
κp = (1 + E m F (E m ))p ≤ (1 + dE m(e+1) )p ≤ dpe+2 = N,
where the last inequality uses (2E)m < p. Hence cA
a (R, N ) ≥ m + 1 by Lemma 5.3,
and it is enough to show that m + 1 > r log N with the r above.
Using the assumed hypotheses and setting δ = log d:
N = dpe+2 ≤ d(D + 1)e+2 (2E)(e+2)(m+1)
≤ d(2E)(e+2)(m+2)
< (2E)(e+2)(m+2)+δ
≤ (2E)(e+2)(m+1)+(e+2)+δ
≤ (2E)(m+1)(e+2+
e+2+δ
m+1 )
≤ (2E)(m+1)(2e+4+δ) .
The desired inequality follows from this by taking the logarithms of both sides.
Remark
The proof shows that the logarithmic lower bound is forced by just two inputs: if
p > D + 1 and R(p), then there is a number κ such that κp ≤ N = dpe+2 and any
A-term t(x) that decides R on {p, κp} has arithmetic depth > r log N .
7.
OPTIMALITY OF THE BINARY GCD-ALGORITHM
A careful look at the binary algorithm shows that for A = Z(div2 ) and a, b >
0 we have gcd(a, b) ∈ GA
m (a, b) with m ≤ 2(log a + log b). A little more work
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
27
yields for each positive integer N an A-term t(x, y) of arithmetic depth ≤ 4 log N
that computes gcd on {1, . . . , N }2 . (One obtains t(x, y) by imitating what the
binary algorithm does on inputs in {1, . . . , N }2 .) Hence there is also for each
positive integer N an A-term t⊥ (x, y) of arithmetic depth ≤ 4 log N that decides
the coprimeness relation ⊥ on {1, . . . , N }2 .
Theorem 7.1 below shows that the binary algorithm is in a sense optimal for algorithms deciding ⊥ using just linear operations, since the upper bound is matched
by a proportional lower bound. (More precisely, Theorem 7.1 is the non-uniform
version; the uniform version is Theorem 12.2.)
Theorem 7.1. If A := Z(divD ) with D > 1, then there is a real constant r > 0
depending only on D such that for all a > (D + 1)2 ,
3
cA
a (⊥, N ) > r log N with N = a .
The lemmas and proofs involved are very similar to those in the previous section.
Lemma 7.2. Suppose |c0 |, |c1 |, |c2 | < a and b > a2 . Then
(i) c0 + c1 κa + c2 κb = 0 ⇐⇒ c0 = c1 = c2 = 0;
(ii) c0 + c1 κa + c2 κb > 0 ⇐⇒ either c2 > 0, or (c2 = 0 and c1 > 0),
or (c2 = c1 = 0 and c0 > 0).
Suppose |c0 |, |c1 |, |d0 |, |d1 | < a/2 and b > a2 . Then
(iii) c0 + c1 κa + c2 κb = d0 + d1 κa + d2 κb ⇐⇒ c0 = d0 , c1 = d1 , c2 = d2 ;
(iv) c0 + c1 κa + c2 κb < d0 + d1 κa + d2 κb ⇐⇒ either c2 < d2 , or
(c2 = d2 and c1 < d1 ), or
(c2 = d2 , c1 = d1 , c0 < d0 ).
Proof. Note that |c0 + c1 κa| ≤ a − 1 + κ(a2 − a) < κa2 < κb, so Lemma 6.4 with
b in the role of a yields (i) and (ii). Items (iii) and (iv) are obvious consequences
of (i) and (ii).
The proof of the next lemma is like that of Lemma 6.5.
Lemma 7.3. Suppose D > 1, E = D!, a > (D+1)(2E)m , U := Bm (a, b), b > a2 ,
and κ ≡ 1 mod E m . Then there exists an embedding ı : A U A given by
c + c a + c b c + c κa + c κb
0
1
2
0
1
2
ı
, |c0 |, |c1 |, |c2 | ≤ (2E)m .
=
Em
Em
Proof of Theorem of 7.1. Suppose a > (D + 1)2 > (D + 1), and choose m
such that
(D + 1)(2E)m < a ≤ (D + 1)(2E)m+1 .
Put b := a2 + 1 and κ := 1 + E m , so a ⊥ b, but κa 6⊥ κb. By Lemma 7.3
we have an embedding ı : A Bm (a, b) A such that ı(a, b) = (κa, κb). Also
κb = (1 + E m )(a2 + 1) < a3 = N . Hence cA
a (⊥, N ) ≥ m + 1 by Lemma 5.3.
From (D + 1)(2E)m+1 ≥ a we obtain m + 1 ≥ log a − log(D + 1) / log 2E. Using
log N = 3 log a this yields
cA
a (⊥, N ) ≥
1
(log N − 3 log(D + 1)).
3 log 2E
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
28
·
L. van den Dries and Y. N. Moschovakis
Now the hypothesis a > (D +1)2 together with log N = 3 log a implies that log N >
6 log(D + 1), so that log N − 3 log(D + 1) > 12 log N , and when we insert this in the
inequality just derived we obtain the desired
cA
a (⊥, N ) ≥
1
log N.
6 log 2E
Notice that if only division by 2 is assumed, then E = 2! = 2 and so the con1
—compared to 4 in the upper bound for the binary
stant in the lower bound is 12
algorithm which only uses division by 2.
Remark
As in the previous section, the lower bound is forced by just two inputs: if a >
(D + 1)2 then there is κ > 1 such that κ(a2 + 1) < N := a3 and any A-term that
decides ⊥ on the two inputs (a, a2 + 1) and (κa, κ(a2 + 1)) has arithmetic depth
> (log N )/6 log 2E.
8.
LOWER BOUNDS FOR UNARY RELATIONS FROM +, −, ÷
For each finite Φ ⊆ Lin the partial algebra (Z, 0, 1, +, −, (φ)φ∈Φ , <) is term-reducible
to Z(1) = (Z, 0, 1, +, −, iq, rem, <). But iq and rem do not belong to Lin, so Z(1) is
not term-reducible to (Z, 0, 1, +, −, (φ)φ∈Φ , <) for any finite Φ ⊆ Lin. In contrast
to the single logarithmic bounds of Sections 6 and 7, the lower bounds we will derive
relative to Z(1) in this section are double logarithmic, and we will establish them
for term complexity rather than the (smaller) arithmetic term complexity.
For unary relations we have an analogue of Theorem 6.1, but for term-complexity.
Theorem 8.1. Suppose R ⊆ Z is a unary relation, F : N>0 → N>0 is a function, and d, e > 0 are such that for all λ and p:
(i) R(p) =⇒ ¬R(κp) with κ = 1 + λF (λ),
(ii) F (λ) ≤ dλe .
Then for all sufficiently large p such that R(p), if N := p(e+1)b
cZ(1) (R, N ) >
log p
5 c
, then
1
log log N.
7
(9)
In particular, if R(p) is true for infinitely many p, then (9) holds for infinitely
many N .
As with Theorem 6.1 this result applies to the unary relations of being prime,
being a power of 2, being a perfect square, and being square-free. We do not
know if a double logarithmic bound as in this theorem holds for the arithmetic
Z(1)
term-complexity ca .
p
Lemma 8.2. Suppose a > 0, |ci |, |di | < a2 for i = 0, 1, 2 and c2 , d2 6= 0. Then
(i)
(ii)
c0 +c1 a
c2
c0 +c1 a
c2
=
<
d0 +d1 a
d2
d0 +d1 a
d2
⇐⇒
⇐⇒
c0
c2
d0
c1
d2 and c2
either cc12 < dd12 ,
=
d1
d2 ;
or ( cc21
=
=
d1
d2
and
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
c0
c2
<
d0
d2 ).
Arithmetic Complexity
·
29
This follows easily from Lemma 6.4 by clearing denominators.
Let h be an integer > 1 and put
nc + c a
o
0
1
A(a, h) := Z ∩
: c2 6= 0, |ci | ≤ h for i = 0, 1, 2 .
c2
Lemma 8.3. Let a > 2h4 , and c, d ∈ A(a, h). Then c + d, c − d, iq(c, d), and
rem(c, d) lie in A(a, 2h4 ).
Proof. Write
c=
c0 + c1 a
,
c2
d=
d0 + d1 a
d2
with c2 , d2 6= 0 and |ci |, |di | ≤ h for i = 0, 1, 2. Then
c+d=
(c0 d2 + c2 d0 ) + (c1 d2 + c2 d1 )a
,
c2 d2
hence c + d ∈ A(a, 2h2 ) ⊆ A(a, 2h4 ), and similarly for c − d. To deal with iq(c, d)
and rem(c, d) we first consider the case d1 6= 0. Solving for a in d = (d0 + d1 a)/d2
and substituting in the expression for c, we get
c d − c d c0 d1 − c1 d0
c1 d2
0 1
1 0
d+
, with c=
≤ 2h2 .
c2 d1
c2 d1
c2 d1
The assumption a > 2h4 easily yields |d| > 2h2 , so
c
c1 d2
=
+ , with || < 1.
d
c2 d1
Hence |iq(c, d)| ≤ h2 + 2, in particular iq(c, d) ∈ A(a, 2h4 ), and
c0 + c1 a iq(c, d)d0 + iq(c, d)d1 a
−
c2
d2
(c0 d2 − iq(c, d)c2 d0 ) + (c1 d2 − iq(c, d)c2 d1 )a
=
.
c2 d2
rem(c, d) = c − iq(c, d)d =
Hence rem(c, d) ∈ A(a, h2 + (h2 + 2)h2 ) ⊆ A(a, 2h4 ).
Next, suppose d1 = 0. We can assume d 6= 0, so
|rem(c, d)| < |d| ≤ |d0 | ≤ h,
in particular rem(c, d) ∈ A(a, 2h4 ), and
iq(c, d) =
c0 d0 − rem(c, d)c2 d2 + c1 d0 a
c − rem(c, d)
=
,
d
c2 d0
which yields iq(c, d) ∈ A(a, 2h3 ) ⊆ A(a, 2h4 ).
Suppose that a > 2h2 and u ∈ A(a, h). Then by part (i) of Lemma 8.2 there is a
unique triple (c0 , c1 , c2 ) such that |ci | ≤ h for i = 0, 1, 2, c2 > 0, gcd(c0 , c1 , c2 ) = 1,
1a
and u = c0 +c
. Denote the component c2 of this unique triple by c2 (u). With
c2
these notations we have:
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
30
·
L. van den Dries and Y. N. Moschovakis
Lemma 8.4. Suppose a > 2h4 , 0, 1 ∈ U ⊆ A(a, h), and κ ≡ 1 mod c2 (u) for
each u ∈ U . Then we have an embedding ı : Z(1) U Z(1) such that
c + c a c + c κa
0
1
0
1
ı
=
c2
c2
whenever |ci | ≤ h for i = 0, 1, 2, c2 6= 0 and
c0 +c1 a
c2
∈ U.
This follows easily from Lemma 8.2, and from Lemma 8.3 and its proof.
m
k
Lemma 8.5. Suppose a > 25 , and put Ak (a) := A(a, 25 ) for 0 ≤ k ≤ m. We
have the following inclusions for k < m:
(i) Ak (a) ⊆ Ak+1 (a);
(ii) Ak (a) + Ak (a), Ak (a) − Ak (a), iq(Ak (a), Ak (a)) and rem(Ak (a), Ak (a)) are
subsets of Ak+1 (a);
Z(1)
(iii) Gk
Z(1)
(a) ⊆ Ak (a) and Gm (a) ⊆ Am (a).
Proof. The last inclusion follows from (ii) by induction and from GA
0 (a) =
{0, 1, a} ⊆ A(a, 2) = A0 (a). The inclusions (ii) follow from 8.3 using the fact that
k+1
k 4
25
≥ 2 25 .
m
If we were to proceed now as in the proof of Theorem 6.6, we would take λ := 25 !
(for suitable m depending on p), put κ := 1 + λF (λ), and obtain an embedding
of a certain algebra Z(1) U into Z(1) that sends p to κp. Unfortunately, κ as a
Z(1)
function of m grows so fast that it would result in a lower bound on ca (R, N )
(for R as in Theorem 8.1) that is triple logarithmic in N . To achieve a double
logarithmic lower bound we shall work with ordinary term-complexity instead of
arithmetic term-complexity, and introduce the notion of computation space.
Computation space
This subsection is of a general nature, and A is any Φ-algebra. Given
a Φ-term
t(~x) and ~a ∈ Am such that t(~a) ↓ , the computation space S t(~x), ~a is the finite
subset of A defined inductively as follows:
(S1) if t(~x) is 0, 1, xi , respectively, then S t(~x), ~a = {0}, {1}, {ai }, respectively;
(S2) if t(~x) is Eq t1 (~x), t2 (~x) , then S t(~x), ~a = S t1 (~x), ~a ∪ S t2 (~x), ~a ;
and if t(~x) is Co t1 (~x), t2 (~x), t3 (~x) , then
S t1 (~x), ~a ∪ S t2 (~x), ~a if t1 (~a) = 1,
S t(~x), ~a =
S t1 (~x), ~a ∪ S t3 (~x), ~a otherwise;
(S3) if t(~x) is
φ t1 (~x), . . . , tk (~x) where φ ∈ Φ has arity k, then S t(~x), ~a =
S t1 (~x), ~a ∪ · · · ∪ S tk (~x), ~a ∪ {t(~a)}.
Intuitively, S t(~x), ~a is the part of A used in computing t(~a) via t(~x). The next
lemma follows by an easy induction on depth(t).
Lemma 8.6. Let t(~x) be a Φ-term and ~a ∈ Am with t(~a) ∈ A. Suppose that
depth(t) ≤ k ∈ N and each symbol in Φ has arity ≤ ` where 1 ≤ ` ∈ N. Then
(i) t(~a) ∈ S t(~x), ~a ⊆ GA
a);
k (~
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
31
(ii) |S t(~x), ~a | ≤ (` + 1)k .
The advantage of S t(~x), ~a over GA
a) is that |S t(~x), ~a | grows at most exk (~
ponentially in k (by part (2) of the above lemma), while |GA
a)| can grow doubly
k (~
exponentially in k.
The next absoluteness lemma also follows by an easy induction on t.
Lemma 8.7. Let t(~x) be a Φ-term,~a ∈ Am and t(~a) ∈ A. Let U ⊆ A be such
that 0, 1, a1 , . . . , am ∈ U and S t(~x), ~a ⊆ U . Then tA U (~a) = tA (~a).
Proof of Theorem 8.1. Suppose p ≥ 225(e+1) , p > d, and R(p) holds. Take
m+1
m
m maximal such that p ≥ 25
, so m ≥ 1, and notice that with M := 25 , we
have
p ≥ M 5 > 2M 4 .
Suppose t(x) is a Z(1)-term of depth ≤ m such that t(p) = 1.
Claim. There exists λ such that for κ = 1 + λF (λ) we have t(κp) = 1 and
log p
κp ≤ N := p(e+1)b 5 c .
To prove this claim, set U := S(t(x), p) ∪ {0, 1, p}, and note that by part (i) of
Lemma 8.6 and part (iii) of Lemma 8.5 we have
U ⊆ GZ(1)
m (p) ⊆ Am (p).
By part (ii) of Lemma 8.6 we have |U \ {0, 1}| ≤ K := 3m + 1. We set
Y
λ :=
c2 (u),
u∈U \{0,1}
with c2 (u) as defined just before Lemma 8.4, with p and M in the role of a and h.
Note that λ ≡ 0 mod c2 (u) for all u ∈ U . Put κ := 1 + λF (λ), so κ ≡ 1 mod c2 (u)
for all u ∈ U . Hence by Lemma 8.4 we have an embedding ı : Z(1) U Z(1) such
that ı(p) = κp, and thus t(κp) = 1 by part (1) of Lemma 8.6, using also Lemma
8.7. To finish the proof of the claim it remains to show that κp ≤ N . Using the
assumption p > d, we have
κ ≤ 1 + dλe+1 ≤ 1 + dM (e+1)K ≤ pM (e+1)K ,
hence κp ≤ p2 M (e+1)K ≤ p(e+1)K , where the last inequality uses the assumption
1
M ≤ p 5 and K ≥ 3. Finally
K = 3m + 1 < 5m =
5m+1
log p
≤
,
5
5
log p
and hence K ≤ b log5 p c, so that p(e+1)K ≤ p(e+1)b 5 c = N .
Because t(x) was an arbitrary Z(1)-term of depth ≤ m with t(p) = 1, it follows
from the claim that
cZ(1) (R, N ) ≥ m + 1,
and so to complete the proof, it suffices to show that log log N < 7(m + 1). Using
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
32
·
L. van den Dries and Y. N. Moschovakis
the definition of N , we compute:
log p
c log p
5
(log p)2
≤ (e + 1)
5
2
(log p)3
(by the hypothesis 25 (e+1) ≤ p),
≤
3
5
and so log log N ≤ 3 log log p − 3 log 5. On the other hand, by the choice of m we
m+2
have p < 25
, which yields log log p < (log 5)(m + 2); thus
log N = (e + 1)b
log log N < (3 log 5)(m + 2) − 3 log 5 = (3 log 5)(m + 1)
which yields the required 7(m + 1) > (3 log 5)(m + 1) > log log N .
9.
A LOWER BOUND FOR COPRIMENESS FROM +, −, ÷
Here we derive a log log lower bound for deciding coprimeness in
Z(1) = (Z, 0, 1, +, −, iq, rem, <),
the analog for Z(1) of Theorem 7.1.
Theorem 9.1. For infinitely many positive integers N ,
1
log log N.
(10)
7
√
In fact, for all coprime positive a, b such that | ab − 2| < 1b and a ≥ 2128 , if m is
3m+4
7(m+1)
largest with a ≥ 22
, then (10) holds with N := 22
.
cZ(1) (⊥, N ) ≥
The proof is very much like that of Theorem 7.1, with almost all the required
estimates already derived
in Sections 3 and 7. In the next two lemmas a and b are
√
positive with | ab − 2| < 1b . (These lemmas do not assume coprimeness of a and b.)
Z(1)
Note that then Gm (a, b) = Gm (a, b), with Gm (a, b) as defined in the beginning
of Part 1. We also use the sets A(h) defined just before lemma 3.5 in terms of a, b
and an integer h ≥ 2.
√
3m
Lemma 9.2. Let m ≥ 1, h := 22 , a ≥ h16 , b > 0, | ab − 2| < 1b . Then
Gm (a, b) ⊆ A(h), and for each u ∈ A(h) there is a unique tuple (c0 , c1 , c2 , c3 ) such
that
|ci | ≤ h for i = 0, 1, 2, 3,
c3 > 0,
c0 + c1 a + c2 b
u=
,
gcd(c0 , c1 , c2 , c3 ) = 1.
c3
√
Proof. From h ≥ 28 , a ≥ h16 and | ab − 2| < 1b we obtain the following lower
bounds on b, to be used in this proof and in the proof of the next lemma:
1
1
a ≥ h16 > 400h4 > 10h.
2
2
Then Lemma 3.5 yields Gm (a, b) ⊆ A(h). Note that each u ∈ A(h) has the required
form. The uniqueness of the representation follows from Lemma 3.3, which for
b>
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
33
its application to the equality of two numbers of the required form assumes that
2h2 ≥ 2 and 10(2h2 )2 = 40h4 ≤ b; these bounds follow from the above.
Let c3 (u) denote the component c3 of the unique tuple (c0 , c1 , c2 , c3 ) that the
lemma above associates to an element u ∈ A(h).
Lemma 9.3. With the same assumptions as the previous lemma, let 0, 1 ∈ U ⊆
A(h) and κ ≡ 1 mod c3 (u)|v| for all u, v ∈ U with 0 < |v| ≤ h. Then we have an
embedding ı : Z(1) U Z(1) such that
ı
c0 + c1 a + c2 b c0 + c1 κa + c2 κb
=
c3
c3
whenever |ci | ≤ h for i = 0, 1, 2, 3, c3 6= 0 and
c0 +c1 a+c2 b
c3
∈ U.
Proof. The previous lemma yields a function ı : U → Z satisfying the indicated
identity. We have to show that ı is an embedding Z(1) U Z(1). Consider
elements f, g, u ∈ U ,
f=
c0 + c1 a + c2 b
,
c3
g=
d0 + d1 a + d2 b
,
d3
u=
e0 + e1 a + e2 b
,
e3
with |ci |, |di |, |ei | ≤ h for i = 0, 1, 2, 3, and c3 , d3 , e3 > 0. Among the things to check
is that if f < g, then ı(f ) < ı(g). We have
C0 + C1 a + C2 b
, where C0 := c0 d3 − c3 d0 ,
C3
C1 := c1 d3 − c3 d1 , C2 := c2 d3 − c3 d2 , C3 := c3 d3 , and
C0 + C1 κa + C2 κb
.
ι(f ) − ι(g) =
C3
f −g =
2 2
Now |Ci | ≤ 2h2 for i = 0, 1, 2 and b ≥
√ 10(2h ) , so by Lemma 3.3, if f < g and
C1 and C2 are not both zero, then C1 2 + C2 < 0, and thus ı(f ) < ı(g), again by
Lemma 3.3. If f < g and C1 and C2 are both zero, then f − g = ı(f ) − ı(g), so
ı(f ) < ı(g) as well.
Next assume that f − g = u; we have to check that then ı(f ) − ı(g) = ı(u). The
equality f − g = u yields
(C0 e3 − C3 e0 ) + (C1 e3 − C3 e1 )a + (C2 e3 − C3 e2 )b = 0.
Since |Ci e3 − C3 ei | ≤ 4h3 for i = 0, 1, 2, and b ≥ 10(4h3 )2 , Lemma 3.3 yields
Ci e3 − C3 ei = 0 for i = 0, 1, 2, which gives ı(f ) − ı(g) = ı(u). Likewise it follows
that if f + g = u, then ı(f ) + ı(g) = ı(u).
It remains to show that if iq(f, g) = u, then iq(ı(f ), ı(g)) = ı(u), and that
if rem(f, g) = u, then rem(ı(f ), ı(g)) = ı(u). If g = 0, then these implications
are trivially valid. In the rest of the proof we assume g > 0; the case g < 0
can be treated in the same way. First assume that also d1 = d2 = 0. Then
0 ≤ rem(f, g) < g ≤ h.
Suppose that rem(f, g) = u; then f ≡ u mod g. Without loss we have c3 (f ) =
c3 , so κ ≡ 1 mod c3 g and thus ı(f ) ≡ u mod g. In view of ı(g) = g and ı(u) = u,
this yields the desired rem(ı(f ), ı(g)) = ı(u).
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
·
34
L. van den Dries and Y. N. Moschovakis
Next, suppose that iq(f, g) = u. Put r := rem(f, g). From the identity f − gu −
r = 0 we obtain by substitution for f and u:
(c0 e3 − c3 e0 g − rc3 e3 ) + (c1 e3 − c3 e1 g)a + (c2 e3 − c3 e2 g)b = 0.
Since b ≥ 10(3h3 )2 , this yields by Lemma 3.3:
c0 e3 − c3 e0 g − rc3 e3 = c1 e3 − c3 e1 g = c2 e3 − c3 e2 g = 0,
which in turn yields ı(f ) − gı(u) − r = 0; in view of ı(g) = g and 0 ≤ r < g, this
gives iq(ı(f ), ı(g)) = ı(u), as required.
For the rest of the proof we assume that d1 and d2 are not both zero. From the
proof of Lemma 3.5 we recall that
X + Y a + Zb
< g, with
C3
Y = c1 d3 − iq(f, g)c3 d1 , Z = c2 d3 − iq(f, g)c3 d2 ,
0 ≤ rem(f, g) = f − iq(f, g)g =
X = c0 d3 − iq(f, g)c3 d0 ,
κa+Zκb
. Note also that by the proof of Lemma 3.5
Likewise, ı(f )−iq(f, g)ı(g) = X+Y C
3
3
we have |iq(f, g)| ≤ 7h .
Suppose iq(f, g) = u; we have to show iq(ı(f ), ı(g)) = ı(u). The√proof of
Lemma 3.6 with u instead of f shows that if e1 6= 0 or e2 6= 0, then |u| > 2 b > 7h3 ,
which contradicts |u| = |iq(f, g)| ≤ 7h3 . So e1 = e2 = 0, hence |u| ≤ h, and thus
ı(u) = u and |X|, |Y |, |Z| ≤ h2 + h3 . Also
rem(f, g) =
d0 + d1 a + d2 b
X + Y a + Zb
<g=
,
C3
d3
so
(X − C3 d0 ) + (Y − C3 d1 )a + (Z − C3 d2 )b < 0.
7
Since b ≥ h ≥ 10(h2 + h3 + h3 )2 , Lemma 3.3 yields
√
(Y − C3 d1 ) 2 + (Z − C3 d2 ) < 0
if Y − C3 d1 and Z − C3 d2 are not both zero. Again by Lemma 3.3, and trivially so
when Y − C3 d1 = Z − C3 d2 = 0, this yields
(X − C3 d0 ) + (Y − C3 d1 )κa + (Z − C3 d2 )κb < 0, so
X + Y κa + Zκb
< ı(g).
ı(f ) − u · ı(g) =
C3
From
X+Y a+Zb
C3
≥ 0 we obtain likewise that
X+Y κa+Zκb
C3
rem(ı(f ), ı(g)) = ı(f ) − u · ı(g) =
≥ 0. Hence
X + Y κa + Zκb
,
C3
in particular, iq(ı(f ), ı(g)) = u = ı(u).
Finally, let rem(f, g) = u; to derive rem(ı(f ), ı(g)) = ı(u), note that
rem(f, g) =
X + Y a + Zb
e0 + e1 a + e2 b
=
= u,
C3
e3
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
35
from which we obtain
(e0 C3 − e3 X) + (e1 C3 − e3 Y )a + (e2 C3 − e3 Z)b = 0.
Since |X|, |Y |, |Z| ≤ h2 + 7h3 h2 ≤ 8h5 , the coefficients of 1, a, b in the above expression are all of absolute value ≤ h7 . Since b ≥ 10(h7 )2 , Lemma 3.3 yields
e0 C3 − e3 X = e1 C3 − e3 Y = e2 C3 − e3 Z = 0,
so
e0 + e1 κa + e2 κb
X + Y κa + Zκb
=
,
C3
e3
that is, ı(f ) − iq(f, g)ı(g) = ı(u), and thus rem(ı(f ), ı(g)) = ı(u).
Proof of Theorem 9.1. Let a, b be positive and coprime, such that
1
a √
| − 2| < , a ≥ 2128 .
b
b
3m+4
3m
Take m be maximal with a ≥ 22
, so m ≥ 1, and put h := 22 and N :=
1
27(m+1)
16
2
. Then h ≤ a ≤ N and 7 log log N = m + 1; assume towards a contradiction that t(x, y) is a Z(1)-term of depth ≤ m deciding coprimeness for all pairs c, d
with 1 ≤ c, d ≤ N , in particular, t(a, b) = 1. Let U := S(t(x, y), a, b) ∪ {0, 1, a, b}
(the computation space for t at input (a, b) augmented with 0, 1, a, b). Then
U ⊆ Gm (a, b) ⊆ A(h) by Lemmas 8.6 and 9.2. Put
Y
Y
κ = 1 +
c3 (u) ·
|u|.
u∈U
u∈U, 0<|u|≤h
Then κ ≡ 1 mod c3 (u)|v| for all u, v ∈ U with 0 < |v| ≤ h. Let
ı : Z(1) U Z(1)
be the embedding of Lemma 9.3. Since ι(a) = κa and ι(b) = κb and t(a, b) = 1
we have t(κa, κb) = 1. Thus to reach a contradiction, it is enough to show that
κa ≤ N , since κa and κb are not coprime and hence cannot be within the interval
[1, N ] in which t(x, y) is assumed to decide coprimeness. Recall that |U | ≤ 3m + 4
by Lemma 8.6, and note that if u ∈ U, 0 < |u| ≤ h, then c3 (u) = 1. Hence
3m 3m +4
3m
m
m
m
m
6m
κ ≤ 1 + 22
= 1 + 22 (3 +4) = 1 + 2(24) +4.8 < 2(64) = 22 ,
and then, by the selection of m,
κa < 22
6m
22
3(m+1)+4
= 22
6m
(1+27−3m )
≤ 22
6m
(1+24 )
< 22
7(m+1)
= N,
which is the desired contradiction.
10.
LOWER BOUNDS FOR UNARY RELATIONS FROM +, −, ÷, ×
We now include multiplication among the primitives by considering
Z(2) = Z, 0, 1, +, −, ·, iq, rem, < .
We
√ have the following analogue of Theorem 8.1. Instead of a log log bound we get
a log log bound.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
36
·
L. van den Dries and Y. N. Moschovakis
Theorem 10.1. Let R ⊆ Z be a unary relation, F : N>0 → N>0 a function, and
d, e > 0 such that for all λ and p:
(i) R(p) =⇒ ¬R(κp) with κ = 1 + λF (λ),
(ii) F (λ) ≤ dλe .
Then for all sufficiently large p, if R(p) and N := pe+3 , then
1p
cZ(2) (R, N ) >
log log N .
(11)
2
In particular, if R(p) is true for infinitely many p, then (11) holds for infinitely
many N .
As with Theorem 8.1 this result applies to the unary relations of being prime,
being a power of 2, being a perfect square, and being square-free.
Let h ∈ N, h > 0, let X be an indeterminate, and put
F
: F ∈ Z[X], deg F ≤ n, kF k∞ ≤ h, 0 < c ≤ h}
c
c0 + c1 X + · · · + cn X n
={
: |c0 |, . . . , |cn | ≤ h, 0 < c ≤ h}.
c
We make Q[X] into an ordered ring by setting, for non-zero f (X) ∈ Q[X]: f > 0
iff the leading coefficient of f is > 0.
Q[X; n, h] : = {
Lemma 10.2. If a > h and f ∈ Q[X; n, h], f > 0, then f (a) > 0. If a > 2h2 ,
then the evaluation map
f 7→ f (a) : Q[X; n, h] → Q
is injective, and preserves order: f, g ∈ Q[X; n, h], f < g =⇒ f (a) < g(a).
The proof is a routine exercise left to the reader.
The set of integer values of polynomials in Q[X; n, h] at a is given by
Z[a; n, h] := Z ∩ {f (a) : f (T ) ∈ Q[X; n, h]}.
Notice that
(i) Z[a; n, h] + Z[a; n, h] ⊆ Z[a; n, 2h2 ],
(ii) Z[a; n, h] · Z[a; n, h] ⊆ Z[a; 2n, (n + 1)h2 ].
Lemma 10.3. Suppose a > 2n+1 hn+2 , and s, t ∈ Z[a; n, h]. Then
iq(s, t), rem(s, t) ∈ Z[a; n, 2n+1 hn+2 ].
Proof. By symmetry we can assume t > 0. Write s = f (a) and t = g(a) with
f, g ∈ Z[X; n, h] and g 6= 0. If deg f < deg g, then |s| < t, so either iq(s, t) = 0 and
rem(s, t) = s, or iq(s, t) = −1 and rem(s, t) = s + t, and in either case the desired
result clearly holds. If deg g = 0, then t ≤ h, so |rem(s, t)| ≤ h, and hence
f (a) − rem(s, t)
∈ Z[a; n, h2 + h] ⊆ Z[a; n, 2n+1 h2n+3 ].
t
as desired. Therefore we can assume n ≥ deg f ≥ deg g > 0 in the rest of the
proof. Take 0 < c, d ≤ h such that F := cf and G := dg belong to Z[X] and
iq(s, t) =
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
37
kF k∞ , kGk∞ ≤ h. Let e > 0 be the leading coefficient of G. Then pseudo-division of
F by G (cf. [von zur Gathen and Gerhard 1999]) yields, with k = deg f −deg g < n:
ek+1 F = QG + R,
Q, R ∈ Z[X],
n−1 n
deg R < deg G = deg g
n n+1
with kQk∞ ≤ 2
h and kRk∞ ≤ 2 h
, for example by Exercise 6.44 in [von zur
Gathen and Gerhard 1999]. Put b := ek+1 c, so 0 < |b| ≤ hn+1 . Division by b and
substitution of a for X in the equality above yields
R(a)
dQ(a)
and r =
.
b
b
From deg R < deg G, the inequality assumed about a, and the first part of Lemma
10.2 it follows easily that |r| < t. Writing dQ(a) = q 0 b + r0 where q 0 , r0 ∈ Z and
0 ≤ |r0 | < |b|, we have
s = qt + r, with q =
q0 b + r0
r0
t + r = q 0 t + ( t + r),
b
b
We now distinguish four cases.
r0
| t + r| < 2t.
b
s=
Case 1. 0 ≤
0
q =
dQ(a)−r
b
0
r0
bt
+ r < t. Then iq(s, t) = q 0 and rem(s, t) =
r0
bt
+ r. We have
, hence by the bounds on kQk∞ , kRk∞ :
iq(s, t) ∈ Z[a; n, 2n−1 hn+1 + hn+1 ] ⊆ Z[a; n, 2n+1 hn+2 ],
r0 G(a) R(a)
r0 G(a) + dR(a)
r0
t+r =
+
=
b
bd
b
bd
∈ Z[a; n, hn+2 + 2n hn+2 ] ⊆ Z[a; n, 2n+1 hn+2 ].
rem(s, t) =
Case 2. −t ≤
r0
b t+r
0
0
r 0 +b
b t+r
dQ(a)−r 0 −b
, so
b
< 0. Then s = (q 0 − 1)t + r b+b t + r with 0 ≤
so iq(s, t) = q − 1 and rem(s, t) =
r 0 +b
b t
0
+ r. Now q − 1 =
< t,
iq(s, t) ∈ Z[a; n, 2n−1 hn+1 + 2hn+1 ] ⊆ Z[a; n, 2n+1 hn+2 ],
(r0 + b)G(a) + dR(a)
r0 + b
t+r =
b
bd
∈ Z[a; n, 2hn+2 + 2n hn+2 ] ⊆ Z[a; n, 2n+1 hn+2 ].
rem(s, t) =
0
Case 3. t ≤ rb t + r < 2t. Then
0
q + 1) we are back in case 1.
0
r0
b
Case 4. −2t < rb t + r < −t. Then
by q 0 − 1) we are back in case 2.
> 0; after replacing r0 by r0 − b (and q 0 by
r0
b
< 0; after replacing r0 by r0 + b (and q 0
Suppose that a > 2h2 and u ∈ Z[a; n, h]. Then by Lemma 10.2 there is a unique
tuple (c, c0 , . . . , cn ) such that
0 < c ≤ h, |ci | ≤ h for i = 0, . . . , n, gcd(c, c0 , . . . , cn ) =
n
na
1, and u = c0 +c1 a+···+c
.
Denote
the component c of this unique tuple by c(u).
c
With these notations we have
Lemma 10.4. Let a > 2n+1 hn+2 , let 0, 1 ∈ U ⊆ Z[a; n, h], and suppose κ ≡ 1
mod c(u) for each u ∈ U . Then we have an embedding ı : Z(2) U Z(2) such
that
c + c a + · · · + c an c + c κa + · · · + c κn an
0
1
n
0
1
n
ı
=
c
c
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
38
·
L. van den Dries and Y. N. Moschovakis
whenever 0 < |c| ≤ h, |ci | ≤ h for i = 0, 1, . . . , n and
c0 +c1 a+···+cn an
c
∈ U.
This follows by closely inspecting the proofs of Lemma 10.3 and of items (i) and
(ii) listed just ahead of that lemma.
Lemma 10.5. Suppose a > 22
3m2
, and put
Ck (a) := Z[a; 2k , 22
3k2
],
0 ≤ k ≤ m.
We have the following inclusions for 0 ≤ k < m:
(i) Ck (a) ⊆ Ck+1 (a);
(ii) Ck (a) + Ck (a), Ck (a) − Ck (a), iq(Ck (a), Ck (a)), rem(Ck (a), Ck (a)) and Ck (a) ·
Ck (a) are subsets of Ck+1 (a);
Z(2)
(iii) Gk
Z(2)
(a) ⊆ Ck (a) and Gm (a) ⊆ Cm (a).
Z(2)
Proof. Inclusions (iii) follow from (ii) by induction and G0
Z[a; 1, 2] = C0 (a). Inclusions (ii) follow from Lemma 10.3.
(a) = {0, 1, a} ⊆
12
Proof of Theorem 10.1. Let p ≥ 22 , p > d, such that R(p) holds. Take m
3(m+1)2
maximal such that p ≥ 22
, so m ≥ 1. Put M := 22
Z(2)-term of depth ≤ m such that t(p) = 1.
3m2
. Suppose t(x) is a
Claim. There exists λ such that for κ = 1 + λF (λ) we have t(κp) = 1 and
κp ≤ N := pe+3 .
To prove this claim we set U := S(t(x), p) ∪ {0, 1, p}, and we note that by part
(i) of Lemma 8.6 and part (iii) of Lemma 10.5 we have
U ⊆ GZ(2)
m (p) ⊆ Cm (p).
By part (ii) of Lemma 8.6 we have |U | ≤ K := 3m + 3. Put
Y
λ :=
c(u)
u∈U
where we use the notations of Lemma 10.4 with p, 2m and M in the role of a, n and
h. Then λ ≡ 0 mod c(u) for all u ∈ U . Put κ := 1 + λF (λ), so κ ≡ 1 mod c(u) for
all u ∈ U . Hence by Lemma 10.4 we have an embedding ı : Z(2) U Z(2) such
that ı(p) = κp, and thus t(κp) = 1 by part (i) of Lemma 8.6, using also Lemma
8.7. To finish the proof of the claim it remains to show that κp ≤ N . We have
κ ≤ 1 + dλe+1 ≤ 1 + dM (e+1)K ≤ pM (e+1)K ≤ pe+2 , since
pe+1 = 2(e+1)2
3(m+1)2
≥ M (e+1)K = 2(e+1)(3
m
+3)23m
2
.
Hence κp ≤ pe+3 = N , which establishes the claim.
Because t(x) was an arbitrary Z(2)-term of depth ≤ m with t(p) = 1, it follows
from the claim that cZ(2) (R, N ) ≥ m + 1. In view of
log log N = log(e + 3) + 3(m + 1)2
√
it follows that cZ(2) (R, N ) > 21 log log N provided p > P0 where the constant
P0 > 0 depends only on e.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
39
12
The arguments above show that for P = max{d, 22 , P0 } we have
p > P and R(p)
=⇒
cZ(2) (R, N ) >
1p
log log N .
2
Decision-tree complexity
√
With essentially the same primitives, [Mansour et al. 1991b] has a log log lower
bound for “being a perfect square”, and [Meidânis 1991] has such a bound for
primality. As usual in computer science these bounds are expressed as functions
√ of
the length of the binary representation of the input, and therefore show up as log
bounds. A more substantial difference is that the lower bounds in [Mansour et al.
1991a], [Mansour et al. 1991b] and [Meidânis 1991] are for a sequential model of
computation, namely decision-trees, in contrast to our term-complexity.
PART 3. LOWER BOUNDS FOR RECURSIVE PROGRAMS
There is no single term t(x, y) which computes gcd(x, y) for all x, y ∈ N>0 , in any
of the algebras we have considered, and similarly for coprimeness and the other
examples we have studied. Thus the lower bounds of Part 2 apply to (non-uniform)
term-algorithms, which compute the relevant function for inputs ≤ N using some
term tN (~x). In this Part we will derive lower bounds for uniform algorithms which
apply to all inputs and are expressed by recursive programs. These uniform results
have an especially simple, “pointwise” form which identifies directly the inputs that
account for the lower bounds. Moreover, their precise formulation sheds some light
on the expected “lower efficiency” of uniform (relative to non-uniform) algorithms,
and we will discuss this phenomenon briefly after the statements of Theorems 12.1
and 12.2.
Weaker versions of some of the results in this part have already appeared in [van den
Dries and Moschovakis 2004], whose last Section 6 also explains how to extend them
to classes of algorithms much wider than those expressed by recursive programs.
11.
RECURSIVE (MCCARTHY) PROGRAMS
We follow here the notation and conventions of Section 5, and we let k and K range
over N.
Program syntax
An n-ary recursive or McCarthy Φ-program is a (K + 1)-tuple
α = (α0 (~v , f~), α1 (~v , f~), . . . , αK (~v , f~))
of terms (with equality tests and conditionals), in the expanded signature
(Φ, f~) = Φ ∪ {f1 , . . . , fK },
where, as usual, ~v = (v1 , . . . , vn ), is a sequence of (distinct) variables which includes
all the variables that occur free in the terms αi . Here f1 , . . . , fK are fresh, n-ary
function symbols, the recursion variables of α. The body of α is the K-tuple of
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
40
·
L. van den Dries and Y. N. Moschovakis
terms αi (~v , f~), which encodes the system of identities
f1 (~v ) = α1 (~v , f~)
..
.
fK (~v ) = αK (~v , f~)
(12)
The first term α0 (~v , f~) is the head of α.
We allow K = 0, in which case f~ is the empty sequence and α is identified with
its head—so that each Φ-term can be viewed as a program.
Fixed point semantics
Terms in the signature (Φ, f~) of a recursive program α are naturally interpreted in
expansions
(A, p1 , . . . , pK ) = (A, 0, 1, {φA }φ∈Φ , p1 , . . . , pK )
of a (partial) Φ-algebra A. To interpret α on A, we view the recursion variables
f1 , . . . , fK as the unknowns in the system of identities determined by the body of
α. It is well known that each such system has a v-least tuple of partial functions
f 1 , . . . , f K : An * A
which satisfies it, essentially because the operations on partial functions defined by
terms are monotone and continuous; in fact
S (s)
(0)
(1)
f i = s f i , where f i v f i v · · · (i = 1, . . . , K),
(s)
so that the iterates f i provide approximations to the tuple (f 1 , . . . , f K ) of mutual
fixed points of the body of α, e.g., see Section 1 of [van den Dries and Moschovakis
2004]. This tuple of partial functions is the first semantic value of α on A, and it
determines the associated expansion
(A, α) = (A, f 1 , . . . , f K ) = (A, 0, 1, {φA }φ∈Φ , f 1 , . . . , f K ).
It depends only on the body of α. The second is the n-ary partial function α :
An * A computed by α,
α(~a) := α0 (~a, f 1 , . . . , f K ).
If K = 0, then (A, α) = A and α is just the partial function explicitly defined by
the head α0 (~v ). Given a relation R ⊆ An and a set S ⊆ An we say that α decides
R on the set S ⊆ An if for all ~a ∈ S,
(
1 if ~a ∈ R,
α(~a) =
0 otherwise.
Notation
We have exhibited the recursion variables f1 , . . . , fK in the parts of a recursive program, to emphasize that they can be used to define operations on partial functions.
It will also be convenient to do this in the sequel sometimes, i.e., name (Φ, f~)-terms
by expressions like t(~x, f~). Most of the times, however, when it is not needed, we
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
41
will denote (Φ, f~)-terms as usual, s(~x), u1 (~x), . . ., and for each Φ-algebra A we will
interpret them in the associated expansion (A, α). Thus each (Φ, f~)-term s(~x) defines on each Φ-algebra a partial function ~a 7→ t(~a) by the standard definitions of
Section 5. If none of the recursion variables fi occurs in t(~x), then (obviously) t(~a)
has the same value in A and in (A, α).
Examples
(1) Let A = N, 0, 1, S, Pd where S is the successor function and Pd the predecessor
(with Pd(0) = 0). Then a partial function f : Nn * N is A-computable exactly
when it is computable by a Turing machine. This is the main result of [McCarthy
1963], where these programs were introduced.
(2) Recursive algorithms are sometimes most naturally defined by a single recursive equation. For example, the euclidean algorithm,
(
y,
if rem(x, y) = 0,
gcd(x, y) =
gcd(y, rem(x, y)), otherwise
computes the greatest common divisor of two positive integers. To agree with the
definition of programs given here, we add a trivial head which just “calls” the single
function defined, leading in this case to the program
ε0 (x, y) = gcd(x, y),
gcd(x, y) = Co(Eq(rem(x, y), 0), y, gcd(y, rem(x, y))
in the algebra (Z, 0, 1, rem). Formally, this is the pair of terms
ε = gcd(x, y), Co(Eq(rem(x, y), 0), y, gcd(y, rem(x, y)) .
Complexity functions
For a Φ-algebra A and a recursive program α of signature (Φ, f~), let Σ = ΣA
α be
the set of convergent (Φ, f~)-terms with parameters, i.e., the set of all pairs t(~x), ~a
such that t(~x) = t(~x, f~) is a (Φ, f~)-term, ~a ∈ Am , and t(~a)↓ .
Proposition 11.1. There are two functions
C = CαA : Σ → N,
D = DαA : Σ → N
which satisfy the following conditions.
(C0) C(xi , ~a) = C(0, ~a) = C(1, ~a) = 0
D(xi , ~a) = D(0, ~a) = D(1, ~a) = 0
(C1) C(Eq(t1 (~x), t1 (~x)), ~a) = max{C(t1 (~x), ~a), C(t2 (~x), ~a)}
D(Eq(t1 (~x), t1 (~x)), ~a) = max{D(t1 (~x), ~a), D(t2 (~x), ~a)} + 1
max{C(t1 (~x), ~a), C(t2 (~x), ~a)},
if t1 (~a) = 1,
(C2) C(Co(t1 (~x), t2 (~x), t3 (~x)), ~a) =
max{C(t
x), ~a), C(t3 (~x), ~a)},
1 (~
if t1 (~a) 6= 1
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
42
·
L. van den Dries and Y. N. Moschovakis
max{D(t1 (~x), ~a), D(t2 (~x), ~a)} + 1,
if t1 (~a) = 1,
D(Co(t1 (~x), t2 (~x), t3 (~x)), ~a) =
max{D(t1 (~x), ~a), D(t3 (~x), ~a)} + 1,
if t1 (~a) 6= 1
(C3) C(φ(t1 (~x), . . . , tk (~x)), ~a) = max{C(t1 (~x), ~a), . . . , C(tk (~x), ~a)} + 1,
D(φ(t1 (~x), . . . , tk (~x)), ~a) = max{D(t1 (~x), ~a), . . . , D(tk (~x), ~a)} + 1,
if φ ∈ Φ
(C4) C(fi (t1 (~x), . . . , tm (~x)), ~a) = max{C(t1 (~x), ~a), . . . , C(tm (~x), ~a)}
+ C(αi (~x), t1 (~a), . . . , tm (~a))
D(fi (t1 (~x), . . . , tm (~x)), ~a)
= max{D(t1 (~x), ~a), . . . , D(tm (~x), ~a), D(αi (~x), t1 (~a), . . . , tm (~a))} + 1
Proof. This follows by an application of the same Fixed Point Lemma in Section 1 of [van den Dries and Moschovakis 2004] which justifies the definitions of f i
and α above.
For (t(~x), ~a) ∈ Σ, the tree-depth complexity D(t(~x), ~a) is the depth of a computation tree which is naturally associated with the computation of t(~a) using the
system of recursive equations (12). It is a natural (semantic) extension to programs
of depth(t). We will not have much to say about it, but it provides a useful method
of proving inductively properties of convergent, recursive terms.
The (strict) complexity C(t(~x), ~a) measures (roughly) the maximal depth of nested
calls to the primitives in the computation of t(~a). It is a natural extension of
deptha (t) to recursive programs, and it is the main object of our study here.
Lemma 11.2. Let A be a Φ-algebra and t(~x) a Φ-term. For each ~a such that
t(~a)↓ ,
C(t(~x), ~a) ≤ deptha (t(~x)).
This is proved by a straightforward induction on depth(t). The Lemma is not
true with equality (rather than ≤) because of the conditional, where the syntactic
measure deptha (t(~x)) counts the formal (putative) calls to the primitives in both
branches, while the semantic measure C(t(~x), ~a) has access to the parameters ~a and
disregards the branch which is not used.
The complexity function of a program α is the complexity of its head term,
Cα (~a) = CαA (~a) = C(α0 (~x), ~a).
It is defined when α(~a)↓ .
The next proposition is the key tool for the lower bound results in Section 12. It
is the version of Lemmas 5.1 and 5.3 appropriate for recursive programs.
Proposition 11.3. Let A be a Φ-algebra and α an n-ary Φ-program with recursion variables f~, and let t(~x) be a (Φ, f~)-term, ~x = (x1 , . . . , xm ).
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
43
(i) If ı : A B is an embedding of A into a Φ-algebra B, then for every ~a ∈ Am
such that tA (~a)↓ ,
ı(tA (~a)) = tB (ı(~a)) and C A (t(~x), ~a) = C B (t(~x), ι(~a)).
(ii) If ~a ∈ Am , tA (~a)↓ and C A (t(~x), ~a) ≤ k, then
A
tA (~a) ∈ GA
a) and tA (~a) = tAGk (~a) (~a).
k (~
(iii) If ~a ∈ An and k are such that α(~a) = 1 and α(ı(~a)) 6= 1 for some embedding
ı : A GA
a) A, then Cα (~a) > k.
k (~
Proof. (i) and (ii) are proved by routine inductions on D(t(~x), ~a), and (iii)
follows directly.
One easy corollary of it is the identification of explicit definability with recursive
definability with bounded complexity:
Proposition 11.4. Let A be a Φ-algebra. Given f : An * A and S ⊆ D(f ),
the following are equivalent:
(i) there is a Φ-term τ (~x) that computes f on S;
(ii) there is an n-ary Φ-program α that computes f on S such that the set {Cα (~a) :
~a ∈ S} is bounded.
Proof (Outline). (i) =⇒ (ii) by Lemma 11.2. For the converse, it is convenient first to add one more equation
f0 (~x) = α0 (~x, f1 , . . . , fK )
to the given program, so that α(~x) = f 0 (~x) and we can treat the head of α as
(s)
part of its body. We first check that each of the iterates f i of α in a Φ-algebra
A is defined by an explicit (Φ, ↑ )-term ts,i (~x, ↑ ) which does not depend on A,
where ↑ is a new symbol denoting the undefined, nullary function; this is done by
a simple (if somewhat messy) argument that relies on replacement properties for
partial function variables in (Φ, f~, ↑ )-terms. It follows that for each m, there is
some s = s(m) such that
f i (~a) = tA
a, ↑ )
s,i (~
(i = 0, . . . , K)
for every finite algebra A of size ≤ m, because of the monotonicity of the iterates;
and then by (ii) of Proposition 11.3, if Cα (~a) ≤ k for all ~a ∈ S, m is an upper
a) (which depends only on the arities of the symbols in
bound on the size of GA
k (~
Φ, the arity n of α and k) and s = s(m), then
AGA
k
f i (~a) = ts,i
(~a, ↑ )
(~a ∈ S).
We finish the proof by setting τ (~x) = ts,0 (~x, 0), which (easily) has the same value
AGA
k
as ts,0 (~x, ↑ ) on S because we have assumed that f 0 (~a) = ts,0
~a ∈ S.
(~a, ↑ ) ↓ when
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
44
·
L. van den Dries and Y. N. Moschovakis
Simulating Turing Machines with Lin-programs
We end this section with a simple simulation result which helps relate some of the
lower bounds in the next section to classical complexity estimates.
Proposition 11.5. If a function f : N → N is computable by a Turing machine
M in time T (log n) for n > 0, then there is a natural number k and a Lin-program
α which computes f with cα (n) ≤ kT (log n) for n > 0.
In particular, if f is computable in polynomial time, then it is computable by a
Lin-program α with cα (n) ≤ k logd n, for some natural numbers k, d and all n > 1.
We are assuming here that the input n is entered on a tape of M in binary
notation (which is why we express the complexity as a function of log n), but other
than that, the result holds in full generality: M may or may not have separate
input and output tapes, it may have one or many, semi-infinite or infinite work
tapes, etc. An analogous result holds also for functions of several variables.
Proof (Outline). Consider the simplest case, where M has a two-way infinite
tape and only one symbol in its alphabet, 1. We use 0 to denote the blank symbol,
so that the “full configuration” of a machine at a stage in a computation is a triple
(q, τ, i), where q is a state, τ : Z → {0, 1}, τ (j) = 0 for all but finitely many j’s,
and i ∈ Z is the location of the scanned cell. If we write τ as a pair of sequences
emanating from the scanned cell y0
· · · x3 x2 x1 x0 y0 y1 y2 y3 · · ·
↑
one “growing” to the left and the other to the right, we can then code (τ, i) by the
pair of numbers
P
P
(x, y) = ( j xj 2j , j yj 2j ).
Notice that y0 = rem(y, 2) and x0 = rem(x, 2), so that the scanned symbol and the
symbol immediately to its left are computed from x and y by Lin-operations. The
input configuration for the number z is coded by the triple (q0 , 0, z), with q0 the
starting state, and all machine operations correspond to simple Lin-functions on
these codes. For example:
move to the right : x 7→ 2x + y0 ,
move to the left : x 7→ iq(x, 2),
y 7→ iq(y, 2),
y 7→ 2y + x0 .
It is now not difficult to write a Lin-program using these functions which simulates
M.
If M has K > 1 symbols, we can either give essentially the same proof starting
with a coding of tapes using numbers in K-adic expansions, or appeal to some of
the standard reductions of K-symbol Turing machines to 1-symbol machines. The
codings are somewhat messier when M has semi-infinite tapes.
12.
LOWER BOUNDS IN THE UNIFORM SETTING
In this section we obtain lower bounds on Cα for programs that decide relations
like those considered earlier in the non-uniform setting of term-complexity. In fact,
things are a bit simpler than before, and results take on a rather attractive form.
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
45
We collect in two theorems the uniform versions of Theorems 6.6, 8.1, 10.1, 7.1 and
9.1. Throughout this section we let a, b, p and λ denote positive integers.
Theorem 12.1. Suppose R ⊆ Z is a unary relation such that for all p, λ and
some function F : N>0 → N>0 ,
R(p) =⇒ ¬R(1 + λF (λ)).
(i) Let A := Z(divD ) where D > 1 is an integer. Then for each unary A-program
α that decides R on N>0 ,
p > (D + 1)2 and R(p) =⇒ Cα (p) >
log p
2 log 2E
(E := D!).
(ii) Let A := Z(1). Then for each unary A-program α that decides R on N>0 ,
p > 225 and R(p) =⇒ Cα (p) >
log log p
.
2
(iii) Let A := Z(2). Then there is a constant P > 0 (independent of the relation
R), such that for each unary A-program α that decides R on N>0 ,
√
log log p
.
p > P and R(p) =⇒ Cα (p) >
2
Note that the hypothesis on F is weaker than in Theorems 6.1, 8.1 and 10.1,
since no polynomial growth is assumed.
Proof. All the real work for these results has been done in Sections 6, 8, 10 in
constructing certain embeddings A U A. We only show (iii), since the other
proofs are similar.
Let A = Z(2) and let α be a unary A-program that decides R on N>0 . As in
12
the proof of Theorem 10.1, let p ≥ 22 be such that R(p) holds; take m maximal
3(m+1)2
3(m+2)2
such
that p ≥ 22
, so m ≥ 1 and p < 22
, so log log p < 3(m + 2)2 , hence
√
12
log
log
p
1
1
√
< m+2. Since 2 < √3 , this gives a natural number P ≥ 22 (independent
3
√
GA
of the relation R) such that log2log p < m + 1 if p > P . Also, Q
m (p) ⊆ Cm (p),
A
using notations from Section 10. Put U := Gm (p), and take λ := u∈U c(u), using
the notations of Lemma 10.4. That lemma provides an embedding ı : A U A
such that ı(p) = κp
where κ = 1 + λF (λ), so by (iii) of Proposition 11.3, we have
√
log log p
Cα (p) ≥ m + 1 >
if p > P .
2
Theorem 12.2. (i) If α is a binary program which decides coprimeness on
(N>0 )2 in Z(divD ) (with D > 1), then
p > (D + 1)2 =⇒ Cα (p, p2 + 1) >
log p
2 log 2E
(E := D!).
(ii) If α is a binary program √
which decides coprimeness on (N>0 )2 in Z(1) and
a
a, b are coprime such that | b − 2| < 1b , then
a ≥ 22
16
=⇒ Cα (a, b) >
log log a
.
4
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
46
·
L. van den Dries and Y. N. Moschovakis
Proof. We only show (ii), since the proof of (i) is similar. Assume the hypothe16
3m+4
ses in (ii) on α, a and b, with a ≥ 22 , and take m maximal with a ≥ 22
, so
3(m+1)+4
m ≥ 1 and a < 22
, hence log log a < 3(m + 1) + 4, and thus
m+1>
log log a 4
log log a
− ≥
.
3
3
4
m
Setting h := 22 and κ := 1 + (h2 )!, Lemmas 9.2 and 9.3 yield an embedding
ı : Z(1) Gm (a, b) Z(1) such that ı(a) = κa and ı(b) = κb. Then (iii) of
a
, as promised.
Proposition 11.3 gives Cα (a, b) ≥ m + 1 > log log
4
Uniform vs. non-uniform lower bounds
It is plausible that uniform algorithms are in general less efficient on inputs ≤ N
than some non-uniform term algorithm tN (~x), so we would generally expect higher
(better) lower bounds for uniform algorithms. In the case of Z(divD ), however, with
Presburger primitives, we derived in Theorems 12.1 (i) and 12.2 (i) logarithmic lower
bounds for recursive programs which are the same as the non-uniform lower bounds
of Theorems 6.6 and 7.1, up to a multiplicative constant. For Z(1) and Z(2), we also
derived lower bounds of the same form as in Part 2, but for the complexity function
Cα (~x), which corresponds to arithmetic complexity for terms and is generally lower
than the corresponding uniform version of term complexity—for which better lower
bounds may well be derivable. The cost in increased complexity for uniformity is an
important problem, but this indication of its form (and what causes it) is about the
best we can do now, in the absence of proofs of optimality for the known uniform
algorithms, like the euclidean.
A refinement
We are now going to extend part (ii) of Theorem 12.2 in two directions. First,
the embedding lemma 9.3 on which it depends does not assume that a and b are
coprime, and we shall take advantage of that. Secondly, we increase
√ the set of
inputs for which the lower bound holds by considering a > b with | 2 − ab | < b1ρ
where ρ is a real parameter, 0 < ρ ≤ 1. The price to pay is that we have to restrict
to inputs with b > b(ρ) where b(ρ) → ∞ as ρ → 0. Here is a precise statement.
Theorem 12.3.
Let 0 < ρ ≤ 1. Then there exists b(ρ) > 0 such that if a >
√
b > b(ρ) and | 2 − ab | < b1ρ , then for some λ and every binary Z(1)-program α, if
a
α(a, b) = 1 and α (nλ+1)a, (nλ+1)b 6= 1 for some n > 0, then cα (a, b) > log log
.
4
Proof. In connection with Theorem 3.9 it was already mentioned that the lemmas of Section 3 have ρ-versions. This leads to ρ-versions of Lemmas 9.2 and 9.3: in
the first of these lemmas the inequality a ≥ h16 should be replaced by aρ ≥ h16 , and
the statement of the second lemma can be kept, with “previous lemma” referring
now to its ρ-version. The proofs are the same, mutatis mutandis.
The rest of the proof follows that of part (ii) of Theorem 12.2 but is included
here to show how b(ρ) depends on ρ and λ on ρ, a. Assume that a > b and
√
16
3m+4
, so m ≥ 1
| 2 − ab | < b1ρ , with aρ ≥ 22 , and take m maximal with aρ ≥ 22
3(m+1)+4
and aρ < 22
, hence
log ρ + log log a < 3(m + 1) + 4,
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
Arithmetic Complexity
·
47
and thus
log log a log ρ 4
log log a
+
− ≥
3
3
3
4
where the last inequality holds provided b (and hence a) is large enough, say b >
m
b(ρ), which we assume in the rest of the proof. Set h := 22 and λ := (h2 )!.
Let α be a binary Z(1)-program
and let n > 0 be such that α(a, b) = 1 and
α (nλ + 1)a, (nλ + 1)b 6= 1. With κ := nλ + 1, the ρ-versions of Lemmas 9.2 and
9.3 yield an embedding
m+1>
ı : Z(1) Gm (a, b) Z(1)
such that ı(a) = κa and ı(b) = κb. Then (iii) of Proposition 11.3 gives Cα (a, b) ≥
a
m + 1 > log log
, as promised.
4
Corollary 12.4. Let 0 < ρ ≤ 1, and let ` : N>1 → R>1 be a function such that
`(n) = o(n) as n → ∞. Then there exists a b(ρ) > 0 (independent of `) such that
for each binary Z(1)-program α that decides the binary relation
{(x, y) ∈ Z2 : x > 0, y > 0 and gcd(x, y) < `(x + y)}
√
on (N>0 )2 and all a, b, if a > b > b(ρ), | 2 − ab | < b1ρ , and gcd(a, b) < `(a + b),
a
then cα (a, b) > log log
.
4
Proof. Take b(ρ) as in Theorem 12.3, let α be a√binary Z(1)-program α that
decides the relation indicated, and let a > b > b(ρ), | 2 − ab | < b1ρ , and gcd(a, b) <
`(a + b). Note that then α(a, b) = 1. Take λ with the property of Theorem 12.3.
The assumption on ` allows us to take an n so large that nλ+1 ≥ ` (nλ+1)(a+b) .
Then
gcd (nλ + 1)a, (nλ + 1)b ≥ ` (nλ + 1)a + (nλ + 1)b ,
a
so α (nλ + 1)a, (nλ + 1)b 6= 1, and thus cα (a, b) > log log
.
4
Theorem 12.2(ii)
√ is the case where ρ = 1 and `(n) = 2 for all n > 1, but we can
also take `(n) := n, giving rise to the relation
√
x > 0, y > 0 and gcd(x, y) < x + y,
and `(n) := n/ log n, with corresponding relation
x > 0, y > 0 and gcd(x, y) < (x + y)/ log(x + y).
Upper bounds
Theorem 12.1 yields lower bounds for programs deciding primeness, being a power
of 2, being a perfect square, and being square-free. Our knowledge on upper bounds
for such programs is as follows.
Primeness is decidable in polynomial time by [Agrawal et al. 2004], and so by
Proposition 11.5, it is decided by a Lin-program α with Cα (n) ≤ C(log n)d for
some positive constants C and d and all n > 1. The lower bound of Theorem 12.1
comes within a power of this upper bound, and we do not know of a better lower
bound in the literature.
There is an obvious Z(div2 )-program α that decides “being a power of 2” with
Cα (n) ≤ C log n for some positive constant C and all n > 0, so for this unary
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.
48
·
L. van den Dries and Y. N. Moschovakis
relation, the lower bound of Theorem 12.1 is matched by a proportional upper
bound.
From [Mansour et al. 1991b] one can extract a Z(2)-program α that decides
“being a perfect square” with Cα (n) ≤ C log log n for
√ some positive constant C and
all sufficiently large n, while Theorem 12.1 gives a log log lower bound.
It seems to be open whether “being square-free” is even decidable in polynomial
time.
For coprimeness, the lower bound in (i) of Theorem 12.2 is matched by a proportional upper bound for the binary gcd algorithm. For Z(1), we do not know of
any work which gets closer to the euclidean log upper bound than the log log lower
bound in (ii) of Theorem 12.2.
REFERENCES
Agrawal, M., Kayal, N., and Saxena, N. 2004. Primes is in P. Annals of Mathematics, Second
Series 160, 781–793.
van den Dries, L. 2003. Generating the greatest common divisor, and limitations of primitive
recursive algorithms. Foundations of computational mathematics 3, 297–324.
van den Dries, L. and Moschovakis, Y. N. 2004. Is the Euclidean algorithm optimal among
its peers? Bulletin of Symbolic Logic 10, 390–418.
Knuth, D. E. 1973. The Art of Computer Programming. Fundamental Algorithms, Second ed.
Addison-Wesley.
Mansour, Y., Schieber, B., and Tiwari, P. 1991a. A lower bound for integer greatest common
divisor computations. Journal of the Association for Computing Machinery 38, 453–471.
Mansour, Y., Schieber, B., and Tiwari, P. 1991b. Lower bounds for computations with the
floor operation. SIAM Journal on Computing 20, 315–327.
McCarthy, J. 1963. A basis for a mathematical theory of computation. In Computer programming and formal systems, P. Braffort and D. Herschberg, Eds. North-Holland, 33–70.
Meidânis, J. 1991. Lower bounds for arithmetic problems. Information Processing Letters 38,
83–87.
Moschovakis, Y. N. 2003. On primitive recursive algorithms and the greatest common divisor
function. Theoretical Computer Science 301, 1–30.
Poizat, B. 1995. Les Petits Cailloux. Nur al-Mantiq wal-Ma’rifah.
Rose, H. 1994. A Course in Number Theory, second ed. Clarendon Press.
Smoryński, C. 1991. Logical Number Theory I. Springer.
von zur Gathen, J. and Gerhard, J. 1999. Modern Computer Algebra. Cambridge University
Press.
Received August 2006; revised March 2007; accepted March 2007
ACM Transactions on Computational Logic, Vol. V, No. N, May 2007.