Configure PIX Easy VPN Server using CLI
advertisement

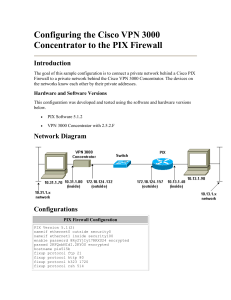
ITSY 2301 Firewalls and Network Security Fall 2009 Lab 16 Remote Access Virtual Private Network Purpose: Create a secure VPN between Boston’s External Host and the PIX Firewall. Topology: See the ITSY2301 standard PIX configuration diagram. Confirm the cabling of the PIX, router and switch. Directions: The PIX device has 3 Ethernet interfaces and no Serial interface. When the router is added to the topology, the PIX and the router will be connected by a crossover Ethernet cable to by-pass the need for a switch. Load the Boston router with the Basic Boston router configuration. Check the IP address of the External Host. Be sure that it can ping all the router interfaces. It will not be able to ping the PIX at this point. On the Boston Router: confirm the default route is a Default Gateway. ip route 0.0.0.0 0.0.0.0 e0 If you have erased the Basic configuration from lab 14, reload the PIX with that configuration data. Preparation: Download the Cisco VPN Client v4.6 or higher from Cisco.com to the External Host. The VPN tunnel will be created between the PIX and the External Host. The traffic that brings up the tunnel will be any packets that are generated by 13.0.13.0/24. Therefore, all traffic between the External Host and the PIX firewall will be encrypted when it originates from the External Host. ******* Before starting on the exercise, be sure that the External Host can ping the Inside Host. The traffic from 11.0.13.2 will not be encrypted before or after the VPN is set up. Step1. Create local accounts on the PIX for remote client login username Tony password Romo privilege 4 username Jerry password Jones privilege 15 Step 2. Configure the ISAKMP part of the VPN on the PIX a. Enable IKE on the outside interface: isakmp enable outside b. Set an identity for IKE isakmp identity address c. Create an ISAKMP policy with a pre-shared key. The policy will use many of the IKE defaults. isakmp policy 10 authentication pre-share d. Verify the isakmp policy show run isakmp Copy the results here. Answer Reflection Question 1. Step 3. Set up a pool of IP addresses for the VPN clients to receive dynamically through the PIX IKE mode configuration: ip local pool VPN-POOL 13.0.13.2-13.0.13.254 This “DHCP” step is necessary so that the secure VPN knows the client’s VPN IP address. Step 4. Configure an access-list to allow the External Host client(s) access to the Inside Host: access-list INBOUND extended permit ip 13.0.13.0 255.255.255.0 host 10.0.1.10 Step 5. Create and configure a tunnel-group and set its type to remote access: tunnel-group cowboys type IPSec_RA tunnel-group cowboys general-attributes address-pool VPN-POOL What happened to the prompt? Step 6. Configure the tunnel-group ipsec-attributes tunnel-group cowboys ipsec-attributes pre-shared-key training What happened to the prompt? You will now need an access list that permits traffic from the inside network to hosts using addresses from VPN pool: This is a numbered extended ACL to be used with NAT. access-list 101 permit ip 10.0.1.0 255.255.255.0 13.0.13.0 255.255.255.0 Step 7. The traffic from the VPN connection does not need to be translated. Instead we will allow it un-translated access. nat (inside) 0 access-list 101 Step 8. Now configure the transform set to be used for the VPN clients: crypto ipsec transform-set PIXEN esp-3des esp-sha-hmac **** this step may need to be modified ---- 3des? Step 9. Configure a new type of crypto map. This is a dynamic map that allows the VPN clients to connect to the PIX firewall. crypto dynamic-map MYMAP 10 set transform-set REMOTE Answer Reflection Question 2. Step 10. Now create the familiar crypto map and “marry” the dynamic crypto map to it: crypto map RA-PEER 20 ipsec-isakmp dynamic MYMAP Step 11. Lastly, apply the crypto map to the PIX outside interface: crypto map RA-PEER interface outside Step 12. Time to verify your configuration a. Check the IP local pool: show run ip local pool b. Check the NAT configuration: show run nat There should be two lines of information. c. Check your crypto map: show run crypto map There should be two lines of information. d. Check the transform set: show run crypto ipsec e. Verify the IKE policy: show run isakmp Multiple lines of information f. Verify the tunnel-group configuration: show running-config tunnel-group tunnel-group training type IPSec_RA tunnel-group training general-attributes address-pool MYPOOL tunnel-group training ipsec-attributes pre-shared-key * Step 4 Configure the Cisco VPN Client If needed, complete the following steps to configure the Cisco VPN Client. a. Choose Start>Programs>Cisco Systems VPN Client>VPN Client. The Cisco Systems VPN Client window opens. b. Click New. The New Connection Entry window opens. c. Enter PixP as the name in the Connection Entry field. Enter the IP address of the PIX Security Appliance public interface, 192.168.P.2, as the IP address of the Host. d. In the Authentication tab, verify that the Group Authentication radio button is selected and enter the following group information. Enter a group name: training Enter and Confirm a group password: training e. In the Transport tab, verify that Enable Transparent Tunneling is checked. f. Click the Save button to save the connection entry. Step 5 Launch the VPN Client on the Student PC Complete the following steps to launch the VPN Client on the student PC: a. Choose Start>Programs>Cisco Systems VPN Client>VPN Client. b. Verify that the Connection Entry is PixP. c. Verify that the IP address of the remote server is set to the public interface IP address of the PIX Security Appliance, 192.168.P.2. d. Click Connect. Several messages flash by quickly. Complete the following sub-steps to establish the VPN tunnel: i. When prompted for a username, enter admin. ii. When prompted to enter a password, enter admin123. e. The window closes and a VPN (lock) icon appears in the system tray. This indicates the VPN tunnel has been successfully created. Step 6 Verify the VPN Connection Complete the following steps to verify the IPSec connection: a. Open a web browser on the VPN Client PC. b. Use the web browser to access the inside web server by entering http://10.0.P.10 c. The home page of the inside server should display. d. Right-click the VPN Dialer icon in the system tray, then left click on Statistics and observe the IP address that was assigned to the student PC. Keep this window open. Note the number of encrypted packets. e. On the PIX Security Appliance console, view the IKE SAs. show crypto isakmp sa f. View the IPSec SAs. g. Verify the running configuration with the ending configuration. h. On the Student PC, Disconnect the remote VPN session. Reflection Questions 1. Which default settings are different from those of the router VPN and why? (refer to Cisco.com --- Remote Access VPNs – for help) 2. What do you expect a dynamic crypto mapping to do for the VPN?