SEC-2015-0577-TR-0012_JOSE_RFC_References - FTP
advertisement

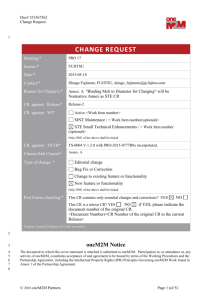
Doc# 533559969 1 2 3 I NPUT C ONTRIB UTION Meeting ID* SEC#18 Title:* TR-0012 JOSE RFC References Source:* Phil Hawkes, Qualcomm, phawkes@qti.qualcomm.com Wolfgang Granzow, Qualcomm, wgranzow@qti.qualcomm.com Josef Blanz, Qualcomm, jblanz@qti.qualcomm.com Uploaded Date:* 2015-07-23 Document(s) WI-0016 Impacted* TR-0012-V-0.5.1 End-to-End Security and Group Authentication Intended purpose of Decision document:* Discussion Information Other <specify> Decision requested or recommendation:* Agree to the proposed changes Template Version:23 February 2015 (Dot not modify) 4 5 oneM2M Notice 6 7 8 9 The document to which this cover statement is attached is submitted to oneM2M. Participation in, or attendance at, any activity of oneM2M, constitutes acceptance of and agreement to be bound by terms of the Working Procedures and the Partnership Agreement, including the Intellectual Property Rights (IPR) Principles Governing oneM2M Work found in Annex 1 of the Partnership Agreement. 10 11 © 2015 oneM2M Partners Page 1 (of 2) Doc# 533559969 12 Motivation 13 14 15 At SEC#17, Qualcomm introduced text with references to some IETF draft documents being produced by the IETF Javascript Object Signing and Encryption JOSE) working group. Since that time, the IETF drafts have been published as RFCs. This contribution updates the references in TR-0016, as well as text referring to those documents. 16 Proposed Changes 17 ---- Start of change 1 ---- 18 8.1.1.5.1 19 20 The IETF JSON Object Signing and Encryption (JOSE) working group [JOSE] has been chartered to develop a secure object format based on JSON. The JOSE working group has published the following documents: 21 22 JOSE use cases and requirements. [i.19]. The use cases include security tokens, OAuth, OpenID Connect, XMPP, emergency alerting, constrained devices (including object security for CoAP). 23 24 JSON Web Algorithms (JWA) [i.6] registers cryptographic algorithms and identifiers to be used with JOSE specifications. 25 26 [i.8] JSON Web Key (JWK) defines JSON-based data structures that represent a cryptographic key (JWK) and a set of JWKs (JWK set).” 27 28 [i.7] JSON Web Encryption (JWE) represents encrypted content using JSON based data structures. The JWE cryptographic mechanisms encrypt and provide integrity protection for an arbitrary sequence of octets. 29 30 31 [i.9] JSON Web Signature (JWS) represents content secured with digital signatures or Message Authentication Codes (MACs) using JSON-based data structures. The JWS cryptographic mechanisms provide integrity protection for an arbitrary sequence of octets.” High Level Description of JSON Security 32 The JOSE cookbook [i.5] provides a representative set of examples of protecting content using JOSE. 33 34 35 The secured objects produced using JOSE specifications can use either a JSON serialization or a compact, URL-safe text serialization (intended for space constrained environments such as HTTP Authorization headers and URI query parameters). 36 ---- End of change 1 ---- 37 38 ---- Start of changes to informative References ---- 39 40 [i.5] IETF RFC 7520: “Examples of Protecting Content using JavaScript Object Signing and Encryption (JOSE)”, 2015 41 [i.6] IETF RFC 7518: “JSON Web Algorithms (JWA)”, 2015 42 [i.7] IETF RFC 7526: “JSON Web Encryption (JWE)”, 2015 43 [i.8] IETF RFC 7527: “JSON Web Key (JWK)”, 2015 44 [i.9] IETF RFC 7525: “JSON Web Signature (JWS)”, 2015 45 ---- End of changes to informative References ---- 46 © 2015 oneM2M Partners Page 1 (of 2)