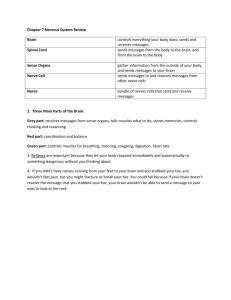
CS170: Fundamentals of Computer Science I
advertisement

CS430-001: Project Fall 2012 (201230) Due Date and Time: Monday, December 3, 2012 at 4:00 PM The Project will require the modeling and verification of a multiphase protocol using PROMELA and SPIN. The Verification Model The verification model is shown pictorially in Figure 1. In Figure 1, we show two stations, called M and N, connected by a communication channel, called the physical layer. M consists of a network layer containing one process (i.e., M3, to be discussed later) and a data link layer containing two processes: the primary station of the Unbalanced Link Initialization Protocol (i.e., M1) [Baratz and Segall, 1988] and the sending station of the Positive Acknowledgement/Retransmission Protocol (i.e., M2) [Tanenbaum, 1989]. Similarly, N consists of a network layer containing one process (i.e., N3, to be discussed later) and a data link layer containing two processes: the secondary station of the Unbalanced Link Initialization Protocol (i.e., N1) and the receiving station of the Positive Acknowledgement/Retransmission Protocol (i.e., N2). The objective of the Project is to construct and verify the multiphase protocol (M, N), where M and N are the protocols created by combining processes M1 and M2, respectively, and processes N1 and N2, respectively. Figure 1: The verification model The multiphase protocol (M, N) works, as follows. M3 in the network layer of M instructs M1 to set up a connection with N. M1 sets up a connection by exchanging a series of messages with N1. When M1 has determined that a high-quality connection has been established, it notifies M3. Concurrently, N1 notifies N3 in the network layer of N that a connection has been established. After receiving the notification from M1, M3 instructs M2 to begin sending data to N2. Concurrently, after receiving the notification from N1, N3 instructs N2 to expect to receive data from M2. The protocol must enforce the following conditions. First, since the physical layer can corrupt and lose messages, M and N must be capable of re-synchronizing, when necessary. Second, M1 and M2, and N1 and N2, can communicate concurrently with M3 and N3 in the network layer of M and N, respectively. Third, only one of the processes in the data link layers of M and N should be active at any given time (i.e., sending (receiving) messages to (from) the physical layer). Fourth, if M1 attempts to set up a connection with N2, M1 and N2 must be able to handle the resulting collisions. And last, if M2 sends data to N1, M2 and N1 must be able to handle the resulting collisions. The Unbalanced Link Initialization Protocol Let M1 and N1 be the primary and secondary stations, respectively, of the Unbalanced Link Initialization Protocol shown in Figures 2 and 3, respectively. The Unbalanced Link Initialization Protocol is a reliable data link layer technique for opening a connection between two stations and ensuring synchronization prior to transferring data. The protocol is called unbalanced because the stations have different statuses (i.e., the primary station is the leader and the secondary station is the follower). The primary station is responsible for making all decisions regarding the quality and status of the connection between the two stations. Figure 2: The primary station of the Unbalanced Link Initialization Protocol Figure 3: The secondary station of the Unbalanced Link Initialization Protocol The initial state of both M1 and N1 is state 1. The protocol works as follows when the link connecting the two stations is of high quality. Following some period of time, M1 times out in state 1 and moves to state 2. From state 2, M1 sends a disconnect message to N1 and moves back to state 1. From state 1, N1 receives the disconnect message sent from M1 and moves to state 2, where it immediately sends a dack (i.e., disconnect acknowledgement) message to M1 and moves back to state 1. From state 1, M1 receives the dack message sent from N1 and moves to state 3, where it immediately sends a clear message to N1 and moves to state 4. From state 1, N1 receives the clear message sent from M1 and moves to state 2, where it immediately sends a cack (i.e., clear acknowledgement) message to M1 and moves back to state 1. From state 4, M1 receives the cack message from N1 and moves to state 5, where it immediately sends a test message to N1 and moves to state 6. From state 1, N1 receives the test message sent from M1 and moves to state 4, where it immediately sends a tack (i.e., test acknowledgement) message to M1 and moves back to state 1. From state 6, M1 receives the tack message sent from N1 and moves to state 7, where it immediately sends a success message to N1 and moves to state 8. From state 1, N1 receives the success message sent from M1 and moves to state 5. At this point in the protocol, with M1 at state 8 and N1 at state 5, the stations are considered connected and in the connected state. When the link connecting two stations is unreliable (i.e., messages may be lost or corrupted), M1 is able to detect situations where messages need to be retransmitted. This can occur at state 4 when the receipt of a cack message exceeds the timeout period. When this occurs, M1 moves to state 3, resends the clear message, and moves back to state 4. It can also occur at state 6 when the receipt of a tack message exceeds the timeout period. When this occurs, M1 moves to state 2 and immediately sends a disconnect message to N1. This course of action results in the protocol being restarted at state 1 in both M1 and N1. The protocol can also be restarted from the connected state by M1 sending a disconnect message from state 8 which is received by N1 at state 5. The Positive Acknowledgement/Retransmission Protocol Let M2 and N2 be the sending and receiving stations, respectively, of the Positive Acknowledgement/Retransmission Protocol [Tanenbaum, 1989] shown in Figures 4 and 5, respectively. The Positive Acknowledgement/Retransmission Protocol is a reliable data link layer alternating-bit technique that allows data to be transmitted in one direction over a channel that may corrupt and lose messages. It is called an alternating-bit protocol because sequence numbers in messages are one bit in length and are set to either a 0 or a 1. The sender and receiver work together to ensure that messages are received in the correct order according to the alternating bit. The sender remembers the sequence number of the next message to send and the receiver remembers the sequence number of the next message to receive. Figure 4: The sending station of the Positive Acknowledgement/Retransmission Protocol Figure 5: The receiving station of the Positive Acknowledgement/Retransmission Protocol The initial states of M2 and N2 are states 9 and 6, respectively. The protocol works as follows when the link connecting the two stations is of high quality. From state 9, M2 sends a data-0 (where 0 represents the value of the alternating bit) message to N2 and moves to state 10. From state 6, N2 receives the data-0 message received from M2 and moves to state 7, where it immediately sends an ack-0 (zero acknowledgement) message to M2 and moves to state 8. From state 10, M2 receives the ack-0 message sent from N2 and moves to state 11, where it immediately sends a data-1 message to N2 and moves to state 12. From state 8, N2 receives the data-1 message sent from M2 and moves to state 10, where it immediately sends an ack-1 (one acknowledgement) message to M2 and moves to state 6. From state 12, M2 receives the ack-1 message sent from N2 and moves to state 9. The protocol has now completed one full cycle where two messages have been sent and received, and the alternating bit has been set to 0 and 1 for the first and second messages, respectively. The protocol is now ready to begin another cycle. When the link connecting the two stations is unreliable (i.e., messages may be lost or corrupted), M2 is able to detect situations where messages need to be retransmitted. This can occur at state 10 when the receipt of an ack-0 message exceeds the timeout period. When this occurs M2 moves to state 9, resends the data-0 message, and moves back to state 10. It can also occur at state 12 when the receipt of an ack-0 message exceeds the timeout period. When this occurs, M2 moves to state 11, resends the data-1 message and moves back to state 12. There are states in N2 that correspond to the resending of message from states 10 and 12 in M2. If M2 times out and resends a data-0 message from state 8, N2 receives the data-0 message sent from M2 and moves to state 9, where it immediately sends an ack-0 message to M2 and moves back to state 8. If M2 times out and resends a data-1 message from state 6, N2 receives the data-1 message sent from M2 and moves to state 11, where it immediately sends an ack-1 message to M2 and moves back to state 6. The Multiphase Protocol The multiphase protocol (M, N) obtained by joining states 8 and 9 of M1 and M2, respectively, and states 5 and 6 of N1 and N2, respectively, is shown in Figures 6 and 7, respectively. Nothing has changed in the leading and trailing phases of the component protocols from which the multiphase protocol is constructed, other than the combining of states. Figure 6: The primary/sending station M Figure 7: The secondary/receiving station N Your Responsibilities for the Project Develop a PROMELA model for the multiphase protocol (M, N) described above. Simulate and verify it using SPIN and PAN. One technique that could be used to construct (M, N) is to develop a PROMELA model where the CFSM for M includes all of the features of the component protocols M1 and M2, and another PROMELA model where the CFSM for N includes all of the features of the component protocols N1 and N2. However, you are NOT to model (M, N) in this way. You are required to take a modular approach. That is, you are to develop a PROMELA model for M1 and M2, where M1 and M2 are separate processes, and one for N1 and N2, where N1 and N2 are separate processes. In Figure 1, the primary/sending station M and the secondary/receiving station N each have one sending (receiving) connection to (from) the physical layer, as represented by the pair of arrows going to and from the physical layer. This is intended to signify that only one of the component protocols at each end of the channel is actively sending or receiving messages at any one time. For example, if M1 (N1) is actively sending or receiving messages, then M2 (N2) must be idle. For the protocol to work correctly, if M1 (M2) is the active component in M, then N1 (N2) should be the active component in N. The simulated network layer at each end of the channel is responsible for generating simulated data to send via the data link layer and consuming simulated data received via the data link layer. Submit your PROMELA source code and an annotated script (or scripts) containing evidence generated by PAN that the multiphase protocol is correct. That is, when the protocol terminates, you need to demonstrate that all processes are in a valid end state, that there are no non-progress cycles, and that the finite progress assumption has been satisfied. References [Baratz and Segall, 1988] Baratz, A.E. and Segall, A., “Reliable Link Initialization Procedures,” IEEE Transactions on Communications, Vol. 36, No. 2, pp. 144-152. [Tanenbaum, 1989] Tanenbaum, A.S., Computer Networks, 2nd Edition, Prentice Hall, 1989.