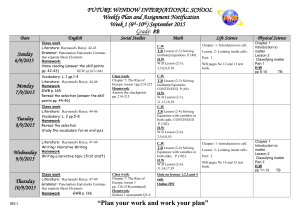
Instructor`s notes

Class notes for Raymond Chang’s presentation on 03/30
Shudong Jin
Let us start. The title of this talk is “SEAD: Secure Efficient Distance Vector Routing for
Mobile Wireless Ad Hoc Network”.
(1)
Raymond states SEAD’s properties, and says SEAD doesn’t protect against Tunneling and Vertex Cut attacks (indeed, no secure protocols exist to handle these attacks).
Shudong: raises a question on whether this is true today and gets an affirmative answer from Raymond.
(2)
Raymond explains that SEAD is a periodic protocol.
Shudong asks if a node broadcasts routing information on fixed intervals. Raymond explains it further.
Siva asks if a node broadcasts even when there is no update, and received an affirmative answer.
(3)
On a question whether this protocol is efficient/inefficient, Zhihua says it depends on the mobility level. More dynamic topology causes frequent broadcasts. Shudong says it also depends on the load.
(4)
While talking about DSDV-SQ, Sanjaya raises a question on whether the sequence number always increases (or whether it has a limit). Raymond agrees it could be a problem (indeed this should be a non-issue as the number may wrap around).
Hongbo follows with a question on whether there is a sequence number for each node and receives an affirmative.
(5)
On the one-way function, Raymond shows this picture
Easy h i-1 h i
Difficult
There are more discussions on the relative computational complexity in two directions.
(6) At this point, Shudong lost one discussion between Hongbo and Raymond.
(7) Hongbo asks what if the attacker uses a large sequence number. Raymond explains it is handled by SEAD.
(8) Siva asks what is MAC? Raymond answers it is the key shared between (among) nodes. It is a hard question
(9) Shudong asks why SEAD waits average weighted settling time. Raymond answers
SEAD doesn’t use it. Shudong acknowledges a misunderstanding.
(10)While discussing the “Protect metric and sequence number”, Hongbo asks how to obtain the original authenticate elements. Raymond answers they are pre-distributed(?)
(11) Raymond draws a picture show the hash chains for groups. h
1 h n-2m h n-m h n k=n/m
…
k=2 k=1
(12) When Raymond talks about the Tunneling attacks (not protected by SEAD), he shows the compromised route length is 2 only (see slides). Shudong asks why it is not 3.
This needs further understanding.
(13) On the simulation, Shudong asks if there are attackers in the simulation. A negative answer is provided by Raymond.
(14) Shudong has two questions on the simulation results. First, why there is a drop of packet delivery ratio as a function of pause time. No answer is given. Second, why the delay for SEAD is much higher? Zhihua provides an explanation(?)