ICISC 2010 program - +=+ International Conference on
advertisement
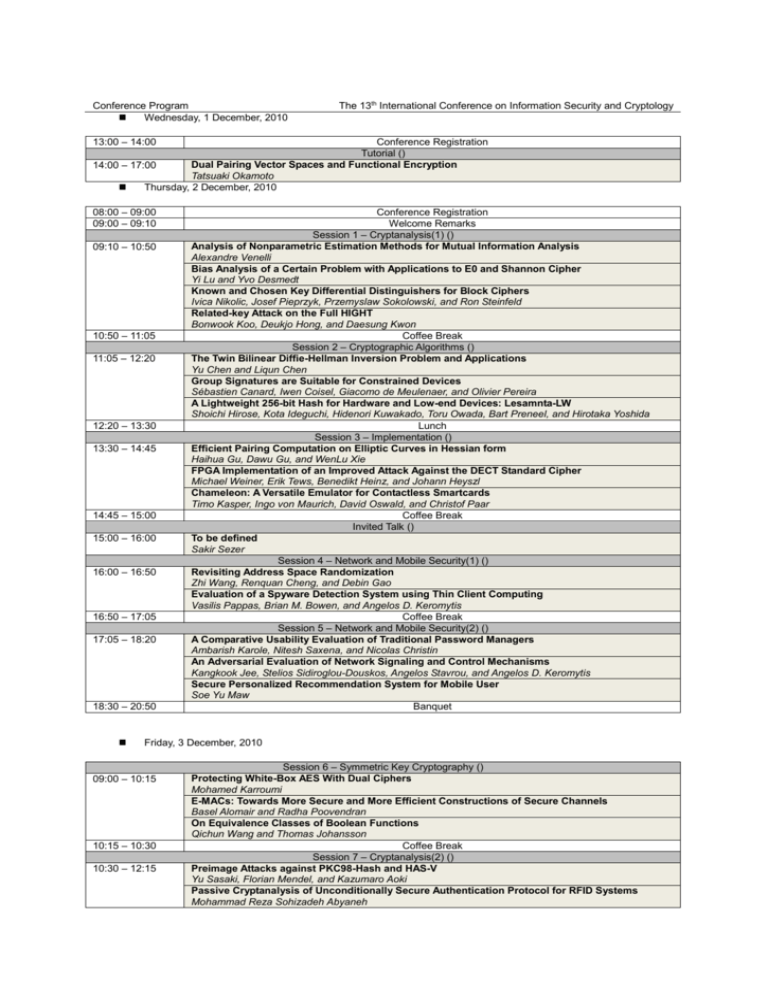
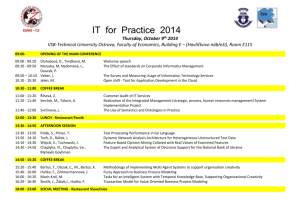
Conference Program Wednesday, 1 December, 2010 The 13th International Conference on Information Security and Cryptology 13:00 – 14:00 Conference Registration Tutorial () Dual Pairing Vector Spaces and Functional Encryption 14:00 – 17:00 Tatsuaki Okamoto Thursday, 2 December, 2010 08:00 – 09:00 09:00 – 09:10 09:10 – 10:50 10:50 – 11:05 11:05 – 12:20 12:20 – 13:30 13:30 – 14:45 14:45 – 15:00 15:00 – 16:00 16:00 – 16:50 16:50 – 17:05 17:05 – 18:20 18:30 – 20:50 Conference Registration Welcome Remarks Session 1 – Cryptanalysis(1) () Analysis of Nonparametric Estimation Methods for Mutual Information Analysis Alexandre Venelli Bias Analysis of a Certain Problem with Applications to E0 and Shannon Cipher Yi Lu and Yvo Desmedt Known and Chosen Key Differential Distinguishers for Block Ciphers Ivica Nikolic, Josef Pieprzyk, Przemyslaw Sokolowski, and Ron Steinfeld Related-key Attack on the Full HIGHT Bonwook Koo, Deukjo Hong, and Daesung Kwon Coffee Break Session 2 – Cryptographic Algorithms () The Twin Bilinear Diffie-Hellman Inversion Problem and Applications Yu Chen and Liqun Chen Group Signatures are Suitable for Constrained Devices Sébastien Canard, Iwen Coisel, Giacomo de Meulenaer, and Olivier Pereira A Lightweight 256-bit Hash for Hardware and Low-end Devices: Lesamnta-LW Shoichi Hirose, Kota Ideguchi, Hidenori Kuwakado, Toru Owada, Bart Preneel, and Hirotaka Yoshida Lunch Session 3 – Implementation () Efficient Pairing Computation on Elliptic Curves in Hessian form Haihua Gu, Dawu Gu, and WenLu Xie FPGA Implementation of an Improved Attack Against the DECT Standard Cipher Michael Weiner, Erik Tews, Benedikt Heinz, and Johann Heyszl Chameleon: A Versatile Emulator for Contactless Smartcards Timo Kasper, Ingo von Maurich, David Oswald, and Christof Paar Coffee Break Invited Talk () To be defined Sakir Sezer Session 4 – Network and Mobile Security(1) () Revisiting Address Space Randomization Zhi Wang, Renquan Cheng, and Debin Gao Evaluation of a Spyware Detection System using Thin Client Computing Vasilis Pappas, Brian M. Bowen, and Angelos D. Keromytis Coffee Break Session 5 – Network and Mobile Security(2) () A Comparative Usability Evaluation of Traditional Password Managers Ambarish Karole, Nitesh Saxena, and Nicolas Christin An Adversarial Evaluation of Network Signaling and Control Mechanisms Kangkook Jee, Stelios Sidiroglou-Douskos, Angelos Stavrou, and Angelos D. Keromytis Secure Personalized Recommendation System for Mobile User Soe Yu Maw Banquet Friday, 3 December, 2010 09:00 – 10:15 10:15 – 10:30 10:30 – 12:15 Session 6 – Symmetric Key Cryptography () Protecting White-Box AES With Dual Ciphers Mohamed Karroumi E-MACs: Towards More Secure and More Efficient Constructions of Secure Channels Basel Alomair and Radha Poovendran On Equivalence Classes of Boolean Functions Qichun Wang and Thomas Johansson Coffee Break Session 7 – Cryptanalysis(2) () Preimage Attacks against PKC98-Hash and HAS-V Yu Sasaki, Florian Mendel, and Kazumaro Aoki Passive Cryptanalysis of Unconditionally Secure Authentication Protocol for RFID Systems Mohammad Reza Sohizadeh Abyaneh 12:35 – 13:50 13:50 – 15:30 15:30 – 15:45 15:45 – 16:45 16:45 – 17:00 17:00 – 18:15 18:15 – Cryptanalysis of RSA with Small Prime Combination Xianmeng Meng Lunch Session 8 – Cryptographic Protocols () Public Discussion Must be Back and Forth in Secure Message Transmission Takeshi Koshiba and Shinya Sawada Scalar Product-based Distributed Oblivious Transfer Chris L. F. Corniaux and Hossein Ghodosi Unconditionally Secure Rational Secret Sharing in Standard Communication Networks Zhifang Zhang and Mulan Liu Oblivious Transfer with Complex Attribute-Based Access Control Lingling Xu and Fangguo Zhang Coffee Break Invited Talk () To be defined Giuseppe Ateniese Coffee Break Session 9 – Side Channel Attack () Fault Attacks on the Montgomery Powering Ladder Joern-Marc Schmidt and Marcel Medwed First Principal Components Analysis: A New Side Channel Distinguisher Youssef Souissi, Maxime Nassar, Sylvain Guilley, Jean-Luc Danger, and Florent Flament Fault Analysis on Stream Cipher MUGI Junko Takahashi, Toshinori Fukunaga, and Kazuo Sakiyama Adjourn


![저기요[jeo-gi-yo] - WordPress.com](http://s2.studylib.net/store/data/005572742_1-676dcc06fe6d6aaa8f3ba5da35df9fe7-300x300.png)