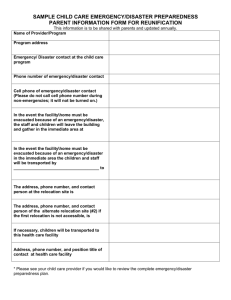
Determine the risk to network data and provide
advertisement

Determine the risk to network data and provide data recovery services according to organisational procedures 1 2004 Preview Network Administrators need to determine the security requirements of an organisation, identify the risks to security, and make use of a disaster recovery plan (DRP) in the event of a minor or major disaster situation. Before an organisation can develop a DRP it needs to undertake a risk analysis to gauge the impact of loss and threats to the network. Contributing to the risk analysis is part of the role of a Network Administrators. You will not be expected to undertake a full risk analysis, but rather contribute to it, especially by providing technical issues and recovery options. Learning outcomes After completing this topic you will be able to: Review security requirements for users and data to be stored on the network. Determine any risks to which data is exposed and provide appropriate prevention and recovery processes. Document the disaster recovery process. Implement systems to provide backup and be able to restore services in the event of a disaster. Before you start You should be familiar with the features of a network operating system, using network administration tools, and backup procedures. Check your understanding Do you think you already have the knowledge covered in this topic? Answer the following questions to check your understanding. Answer true or false. 2 2004 The place to start a review of risk and recovery procedures is to look at the security in place to stop access to the office building. Feedback Correct, this is false. The place to start is with the organisation’s policies and any Service Level Agreement (SLA) requirements. Try again. Standards for how quick the organisation should be able to recover from a disaster will be found in: The backup documentation The SLA The latest audit report The Standards Australia handbook Feedback Correct. This information is found in the SLA. Try again. What types of systems are ‘mission critical’? Feedback Financial, customer-related, cash flow-related, etc, are all systems that can be critical to the core business of an organisation or business. What are the steps to follow when carrying out a risk analysis on the network? Feedback To carry out a risk analysis on the network: Identify threats to the network operations/services. Consider the probability of each of the threats occurring. Estimate the cost of resulting losses. Consider the safeguards that could be put into place. Undertake a cost benefit analysis of implementing the safeguards. Implement safeguards as appropriate. List five threats to a network that should be considered in a risk analysis. 3 2004 Feedback Threats to a network that should be considered in a risk analysis include: ‘eavesdropping’ denial of service viruses unauthorised access cable faults server problems power disruptions. List precautions an organisation can take to prevent or minimise the impact of disastrous events. Feedback Precautions include having the following safeguards in place: fault-tolerant systems uninterruptible power supplies (UPS) encryption virus checkers RAID systems. List the options an organisation can use to recover from a disaster. Feedback Options to help an organisation to recover from a disaster are: backup routines hot or cold sites standby equipment. Once the risks to a system have been identified: All risks should be safeguarded in some way The backup system is modified to eliminate all risks Safeguards that are cost effective are considered Risks that relate to the finance system need to be addressed first Feedback 4 2004 Correct. Safeguards that are cost effective are considered. Try again. Answer true or false. Management may decide to ignore a risk. Feedback Correct, this is true. The cost of prevention may be so high that management will decide to live with the risk. Try again. A disaster recover plan (DRP): Should be created as part of a risk assessment process Is only used when there is a fire in the building Only covers the backup procedures Is a secret document known only to very senior management Feedback Correct. A disaster recovery plan should be created as part of a risk assessment process. Try again. 5 2004 Reading Inside this resource The readings here will help you develop your knowledge and skills for determining the risk to network data and providing data recovery services according to organisational procedures. This will involve an understanding of: Reviewing security requirements Risk analysis Documenting the disaster recovery process Implementing backup systems and restoring services. Icon to print reading Get reading (.doc 183 KB) 6 2004 Practice Activity 1: Summarise the impact of policies Review the policy and procedures document for the company Call Centres R US. Write a report that summarises the impact that these policies will have on risk analysis and disaster recovery. Feedback Your report should have covered the following points: Disaster and recovery planning is a part of the policy standards. Risk analysis needs to be undertaken regularly. Measures to be employed must be cost effective. Major changes need a further risk assessment. Backup procedures are documented. Backup procedures can only be completed after the risk assessment is completed. A backup log is specified. Systems are critical if they impact external clients. Support staff are able to work on all hardware except for monitors. Activity 2: Identify built-in facilities Imagine that a risk analysis determined that customer files are commercially confidential and need to be protected from unauthorised access. 7 2004 Using any operating system that you have access to (ideally a networking operating system) identify the built-in facilities that will help stop unauthorised access to data files. Feedback Your response will depend upon the operating system you use, but as an example, with Windows Server you could have identified: the use of encryption using public keys the use of cryptography to protect data transmission the use of an audit to track file accesses the restricted use of shared folder permissions the use of NTFS permissions. Note that the solutions themselves can then create other risks. For example, if data is encrypted and the person that knows the password leaves, or is not available, then the data may be irrecoverable. Activity 3: Identify support for a UPS One important disaster recovery option is to make use of uninterruptible power supplies (UPS) to allow servers to shut down properly. Review your network operating system and identify any support it may have for a UPS. Feedback For example, with Windows 2000 server: You should check that the UPS is listed on the Hardware Compatibility List (HCL). You can connect the UPS with a serial cable so the UPS can notify the server that power had been lost. You can specify the conditions that will trigger a shut down on the server. You can set the time internal for sending messages after power failure. Note that certain UPS vendors may provide their own software to provide additional services that work with their product and various operating systems. 8 2004 Research A network person is often expected to know or learn about every new piece of network equipment that comes into the workplace. It is important that you build a list of resources that relate to your network operating system. Many of these resources can be found on the Internet or in textbooks. You should always check that you have access to the original documentation that came with the system you are using, as it can provide some very useful information. Most hardware and operating system vendors have their own website which provides a ‘Support’ section. Searching their websites with key terms such as the name of your operating system followed by the word ‘tutorial’ or ‘support’ or ‘help’ will provide many useful links. Websites The following websites contain information on risk analysis, disaster recovery planning and/or links to other similar websites: http://www.disasterplan.com/ http://www.drj.com/ http://www.mhhe.com http://www.dir.state.tx.us http://www.securityauditor.net/ 9 2004 Terms DRP disaster recovery plan, describing recovery processes to get the business or organisation back in operation as soon as possible in the event of a particular disaster; it usually assumes the worst possible scenario and identifies how the organisation could get up and running in the least possible time RAID systems redundant array of inexpensive disks systems, sometimes also referred to as mirrored disks; a prevention option to allow access to data to continue even if a disk fails SLA service level agreement, between the network group and the user community; also contain essential information about the availability and recovery operations of the network that needed to develop restoration services UPS uninterruptible power supplies, a prevention option to minimise the impact of power loss or spikes and surges 10 2004