solution

Name:
TEST 1
CSCE 522 – Fall 2003
October 1, 2003
Name:
Major
SSN (last 4 digits):
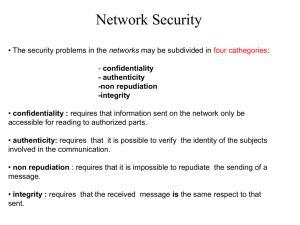
Answer the following questions. Be brief and precise!
Undergraduate students need to answer questions for a total of 85 points . Please indicate clearly which are the questions you’re not answering . If you attempt to answer questions for more than 85 points, your test will be graded as a graduate student’s test.
Graduate students need to answer all questions.
Bonus question is open for all students for extra credit.
You have 50 minutes to finish the exam.
1.
10 points
Briefly explain how policies and procedures contribute to information systems’ security. (7 points)
Policy: what to protect
Policies and procedures support enforcement of security in addition to hardware and software enforcement
Not enough by themselves
E.g., change of password, installing new software, usage of computer systems, etc.
Controls – physicals, ethical, legal
Community standards and expectations
Needs training and administration
No formal standards yet
What does effectiveness of control mean in the context of security? (3 points)
How well the control performs what it is supposed to do
Proper usage of the control: human factor (want to use it, know how to use it), system factor (backdoors)
Likelihood of usage
Overlapping controls – layered defense
Review
2.
10 points
What is the key distribution problem of secret-key encryption? (7 points)
Establish key before communication – need secure channel
Need n(n-1)/2 keys with n different parties – too many keys to maintain
1
Name:
How does Diffie-Hellman solve this problem? (3 points)
Do not give algorithm.
Allows two parties to agree on a shared secret key via insecure channel. Now previous communication is needed. Requires reliable channel to prevent man-in-the-middle attack.
3.
15 points
What are DES and AES? (2 points)
Secret key encryption systems.
What are the fundamental encryption techniques they use? (3 points)
Substitution
Permutation
Shifting (AES)
Compare the levels of security provided by DES and AES. (5 points)
AES:
New – little experimental results
Cryptanalysis results
Few theoretical weakness
No real problem
No relation to government agency
9 rounds
11 rounds
13 rounds
Has sound mathematical foundation
Key size: 128, 192, or 256 bits
no allegations of tampering with code
Block size: 128
Processed as 4 groups of 4 bytes (state)
Operates on the entire block in every round
Number of rounds depending on key size:
Key=128
Key=192
Key=256
DES:
Breakable by exhaustive search on 56-bit key size for known plaintext, chosen plaintext and chosen ciphertext attacks
Security: computational complexity of computing the key under the above scenarios (22 hours)
56 bit key size
64 bit block size for plaintext and cipher text
16 iterations
2
Name:
Briefly explain the four basic steps of Rijndael algorithm. (5 points)
1.
Byte Substitution: Non-linear function for confusion
• S-box used on every byte (table look-up)
2.
Shift Rows: Linear mixing function for diffusion
• Permutes bytes between columns
• Different for different block sizes (128, 192 same, 256 different)
3.
Mix columns: Transformation
• Shifting left and XOR bits
• Effect: matrix multiplication
4.
Add Round Key: incorporates key and creates confusion
• XOR state with unique key
4.
15 points
With a public-key encryption, suppose John wants to send an encrypted and signed message to
Paul.
What are the keys for Paul and John. (2 points)
Public key John: KE-J, Private key John: KD-J
Public key Paul: KE-P, Private key Paul: KD-P
Show what steps and the keys used by John to create a message so that only Paul can decrypt the message but a third party can verify that the message came from John. Let M be the plain text message, show what is the signed message, what is the encrypted and signed message (8 points).
3
Signature and Encryption
Name:
John
Plaintext
D
Signed
Plaintext
E
Encrypted
Signed
Plaintext
D
Signed
Plaintext
E
Paul
Plaintext
P’s public key J’s public key
J’s private key
P’s private key
Show what steps Paul needs to perform to decrypt the message? (5 points)
5.
10 points
How does double-DES work? What is the effective key size? (7 points)
P E
K1
(P)
Intermediate
Ciphertext
Plaintext
Encryption Encryption
E
K2
[E
K1
(P)]
Ciphertext
K1
Known-plaintext: meet-in-the-middle attack
Effective key size: 57 bit
What is the meet-in-the-middle attack? (3 points)
Attacker have pairs of (P1,C1), …, (Pn,Cn)
Try all keys on P1, …, Pn
store result in table
Try all keys on C1, …, Cn
store result in table
Look for match in the two tables.
K2
4
Name:
6.
10 points
Assume that Mary wants to send a large file F to Pete. The message does not have to be confidential, but it is necessary that Pete will be able to verify that F didn’t get corrupted during the transmission. Show how hash functions can be used to allow Pete to check the integrity of the received message.
Mary:
create h(M)=h concatenate M and h
send M||h to Pete
Pete:
detach h from M
create h(M)=h’ from received M
if h’=h then M has not been modified during transmission
5
Name:
5 points
Briefly explain the three security objectives? (3 points)
Confidentiality: prevent/detect/deter improper disclosure of information
Integrity: prevent/detect/deter improper modification of information
Availability: prevent/detect/deter improper denial of access to services
Give a medical example of each. (2 points)
Confidentiality: patients’ record should be disclosed by authorized users only
Integrity: patients’ medical record should be correct
Availability: emergency medical data should be available when needed
7.
15 points
Define : (5 points)
Threat: potential occurrence that can have an undesired effect on the system
Vulnerability: characteristics of the system that makes is possible for a threat to potentially occur
Attack: action of malicious intruder that exploits vulnerabilities of the system to cause a threat to occur
Risk: measure of the possibility of security breaches and severity of the damage
What is an interception threat? (4 points)
Interception – unauthorized party gains access to an asset (confidentiality)
What is the principle of easiest penetration? (3 points)
Attackers use the easiest way to penetrate the system. Security of the system is as good as its weakest component .
What does assurance mean in the context of information security? (3 points)
How well the security components perform what they are supposed to do. Defines how much the security can be trusted
-----------------------------------------------------------------------------------------------------------
(BONUS QUESTION)
5 points
Show a way to provide message authenticity to a third party using only secret key encryption.
Use a trusted third party to send messages. Each message goes to TTH, who validates the origin of the message (e.g., shared secret key between the TTH and the sender). TTH transmits the message to the recipient (e.g., using shared secret key between TTH and recipient.) TTH will be able to verify to any other party later the origin of the message.
6