[#FS-5839] Support multiple SSL/TLS protocols on
advertisement
![[#FS-5839] Support multiple SSL/TLS protocols on](http://s3.studylib.net/store/data/007626067_2-4befaef812d1d215235159e390ba65b0-768x994.png)
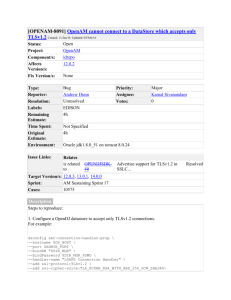
[FS-5839] Support multiple SSL/TLS protocols on the same profile automagically Created: 02/Oct/13 Updated: 24/Feb/14 Resolved: 06/Feb/14 Status: Project: Component/s: Affects Version/s: Fix Version/s: Security Level: Closed FreeSWITCH mod_sofia None Type: Reporter: Resolution: Labels: Remaining Estimate: Time Spent: Original Estimate: Environment: Improvement Kristian Kielhofner Fixed None Not Specified Issue Links: Related relates to FS-5719 TLS negotiation failing with Elliptic... CPU Architecture: Kernel: Userland: Compiler: FreeSWITCH GIT Revision: GIT Master Revision hash:: None public Priority: Assignee: Votes: Minor Travis Cross 0 Not Specified Not Specified All Closed x86 Linux GNU/Linux gcc All Yes Description Assuming underlying OpenSSL support, FreeSWITCH should support at least the following SSL/TLS protocols on the same profile and socket automagically (like Apache): SSL v2.3 (shame on you!) TLS v1 TLS v1.1 TLS v1.2 Comments Comment by Brian West [ 02/Oct/13 ] Tested with setting the method to sslv23 on the profile does indeed support them all. <16>:java -jar TestSSLServer.jar 192.168.1.112 5066 Supported versions: SSLv3 TLSv1.0 TLSv1.1 TLSv1.2 Deflate compression: no Supported cipher suites (ORDER IS NOT SIGNIFICANT): SSLv3 TLS_ECDH_ECDSA_WITH_RC4_128_SHA TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA (TLSv1.0: idem) (TLSv1.1: idem) TLSv1.2 TLS_ECDH_ECDSA_WITH_RC4_128_SHA TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384 ---------------------Server certificate(s): 48dec9e21d1036bc201f0b9c709fbc349616aac0: O=bkw.org, CN=pbx.bkw.org ---------------------Minimal encryption strength: strong encryption (96-bit or more) Achievable encryption strength: strong encryption (96-bit or more) BEAST status: vulnerable CRIME status: protected Comment by Brian West [ 02/Oct/13 ] Extend it. To specify protocols and possibly ciphers. Comment by Kristian Kielhofner [ 02/Oct/13 ] Awesome. What about only supporting > version and up automatically. Config=tlsv1: tlsv1 supported tlsv1.1 supported tlsv1.2 supported ssl v2.3 NOT supported ssl v3 NOT supported Comment by Travis Cross [ 05/Feb/14 ] Talked with Brian. The current state is clearly a bit awkward. The way forward is likely to be listing the versions you want to support individually. We're looking into this. Comment by Travis Cross [ 06/Feb/14 ] This is now in tree; please test. You can specify one or more protocols to support, e.g. <param name="tls-version" value="tlsv1,tlsv1.2"/> Generated at Tue Feb 09 17:29:48 EST 2016 using JIRA 6.4.10#64025sha1:5b8b74079161cd76a20ab66dda52747ee6701bd6.






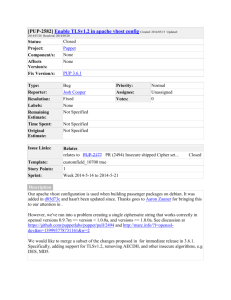
![[#PUP-4445] Add support to TLS 1.2 connections to Puppet Forge](http://s3.studylib.net/store/data/008513485_1-bfcc379eccefaa4db4acb7c13d3685f0-300x300.png)