sender algorithm
advertisement

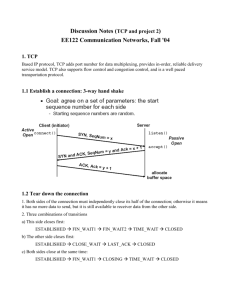
CISC 856: TCP/IP and Upper Layer Protocols Document: Homework – The Eifel Detection Algorithm Presented by: Maitreya Natu (natu@cis.udel.edu) Due Date: Nov 18th, 2004 Q1. Describe, by adding to the timing diagram below, the sender behavior in each of the following scenarios: a) TCP without Eifel b) TCP with Eifel You have to submit 2 timing diagrams. For each scenario indicate the following: 1. PDUs sent by the sender at points A, B and C. 2. Sender’s cwnd and ssthresh values just after the timeout, and after receiving each ACK (A2, A3, A4). 3. In your annotated timing diagram for b, indicate the timestamp values sent with the PDUs. (sender and receiver timestamp values at various points are shown in the following figure in italics. Assume that prior to sending D1, the sender had received a timestamp of 150 from the receiver) Sender Receiver ssthresh=16 cwnd=8 200 D1 D8 . . . A2 A3 Time out 500 A 505 B 510 C 515 A4 300 300 300 D1 600 Q2. Describe, by adding to the timing diagram below, the sender behavior in each of the following scenarios: a) TCP with Eifel b) TCP with DSACK based spurious retransmission detection For each scenario, indicate the following: 1. PDUs sent by the sender at point A, B, C and D. (Assume the sender always has new data available to send. Use names D5, D6,…, for new data) 2. Sender’s cwnd and ssthresh values after timeout and after receiving each ACK. (Assume sender remains in slow start when cwnd = ssthresh) 3. In your annotated timing diagram for a, indicate the timestamp values sent with the PDUs. 4. In your annotated timing diagram for b, indicate the D-SACKs (if any) sent with the ACKs. 5. Show when a spurious retransmission is detected in both a and b. Comment on which detection policy is better in the given scenario. Sender 200 D1 D2 D3 D4 ssthresh=16 cwnd=4 Receiver A2 A3 A4 Time out A5 500 A 505 B 510 C 515 D 520 300 300 300 D1 600 200 Extra Credit: The specification of TCP round-trip time measurement requires that the echoed timestamp should correspond to the most recent data segment that advanced the window. Thus at point B in the timing diagram below, the receiver echoes back the sender timestamp 100 instead of timestamp 400, because 1st PDU with data D1 and sender timestamp 100, was the most recent PDU that advanced the window. How will the Eifel algorithm behave in the following scenario? What will the sender do at points A and C? Can you see a problem with Eifel algorithm? How will the Eifel algorithm recover? Sender ssthresh=8 cwnd=4 100 Receiver D1, 100, 50 D2, 100, 50 D3, 100, 50 D4, 100, 50 A2, 200, 100 200 Time out 400 A D1, 400, 50 600 A2, 600, 100 B C Reference: RFC 1323, TCP Extensions for High Performance RFC 2883, An Extension to the Selective Acknowledgement (SACK) Option for TCP RFC 3708, Using TCP Duplicate Selective Acknowledgement (DSACKs) and Stream Control Transmission Protocol (SCTP) Duplicate Transmission Sequence Numbers (TSNs) to Detect Spurious Retransmissions Pasi Sarolahti , Markku Kojo , Kimmo Raatikainen, F-RTO: an enhanced recovery algorithm for TCP retransmission timeouts, ACM SIGCOMM Computer Communication Review, v.33 n.2, April 2003