DSKPP and PSKC, IETF standard protocol and payload for
advertisement

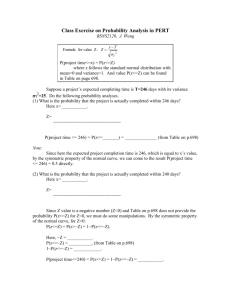
DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning Philip Hoyer Senior Architect – Office of CTO ActivIdentity (UK) 117 Waterloo Road, London SE1 8UL phoyer@actividentity.com Abstract This paper will describe the work currently being completed by the IETF ‘keyprov’ working group to create a standard online protocol and payload to provision symmetric keys. Dynamic Symmetric Key Provisioning Protocol - DSKPP provides an open and interoperable mechanism for initializing and configuring symmetric keys to cryptographic modules that are accessible over the Internet. The portable Symmetric Key Container - PSKC specifies a symmetric key XML format for transport and provisioning of symmetric keys (for example One Time Password (OTP) shared secrets or symmetric cryptographic keys) to different types of devices. The paper will outline the mechanisms of DSKPP and its main application use cases. It will also describe the PSKC payload format and its applicability for use within the DSKPP protocol or as a standalone format for off-line key provisioning and transport. 2 DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 1 Introduction Securing modern application and technology infrastructure components is mainly based on cryptography using keys. Even though advances have been made in implementation by adding asymmetric (PKI) and symmetric key based security and cryptographic mechanisms, one main area that keeps an overall system secure is the availability of fresh uncompromised keys. To achieve this effective key management and provisioning is essential. When a symmetric key is used in application it is usually used with a specific algorithm. Some algorithms require additional parameters or values (key meta-data) that are used as input in the computation of the algorithm (for example a counter for a one time password algorithm). Additionally it might be desirable to restrict and govern the usage of the key in terms of time period when the key can be used or number of times a key should be used (key policy). It is hence highly desirable during key provisioning to be able to provision the additional key meta data and policy to the application using the key. The state of affair when the ‘keyprov’ working group was founded was that mostly provisioning of symmetric keys was performed using proprietary and hence non-interoperable protocols and transport formats. This meant that in the majority of cases, applications requiring keys would not be able to interoperate with key provisioning infrastructure from other providers. This meant that more often than not key provisioning was either completely lacking or suboptimal from a security perspective. Fig 1: Historical state of affair, no interoperability between proprietary symmetric key provisioning The need for provisioning protocols in PKI architectures has been recognized for some time. Although the existence and architecture of these protocols provide a feasibility proof for the work in the IETF ‘keyprov’ working group, assumptions built into these protocols mean that it was not possible to apply them to symmetric key architectures without substantial modification. DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning In particular the ability to provision symmetric keys and associated key meta-data (attributes) dynamically to already issued devices such as cell phones and USB drives was highly desirable. The IETF working group was hence set-up to develop the necessary protocols and data formats required to support provisioning and management of symmetric keys and related meta-data, both proprietary and standards based. The following highlight two major use cases of the ones that have been considered: 1. Online symmetric key provisioning – this is when an application has network connectivity and requires symmetric keys for application functionality. In this case the application would connect over the network using the symmetric key provisioning protocol to retrieve one or more symmetric keys and related meta-data. One example could be an application on a mobile phone capable of generating One-Time-Passwords using an algorithm that utilizes symmetric keys and a counter. 2. Offline bulk key provisioning - this use case is when applications or devices that harbor symmetric keys, injected at manufacturing, need to be imported into an infrastructure for usage. The knowledge of the keys and their related meta-data need to be securely imported from the manufacturing to the infrastructure components. One example would be One-Time-Password tokens that come with related keys and counters (seed data) and are imported into a validation server possibly for securing remote access VPNs. 1.1 History of the ‘keyprov’ working group The state of affair when the IETF ‘keyprov’ working group was founded in early 2007 was of an ecosystem of vendor-specific solutions for provisioning of symmetric keys (and meta-data) but no standardized solution was available. The main key provisioning scenarios required included over the wire (an application with network TCP/IP connectivity) over the air (an application on a mobile phone) or offline (bulk, multiple keys securely transported for example on a CD-ROM) Not only was there no standardised online protocol but there was no standardized container for keys and meta-data available either. Resulting in a state of no interoperability between client and servers for provisioning symmetric keys. Hence in February 2007 the IETF ‘keyprov’ working group was founded with input from VeriSign (DSKPP), RSA (CT-KIP), and OATH (PSKC) with the following main deliverables: 1. An online XML based protocol to allow online provisioning of symmetric keys – The Dynamic Symmetric Key Provisioning Protocol [DSKPP] 2. An XML based symmetric key payload (transport) format – Portable Symmetric Key Container [PSKC] 3. An ASN.1 based symmetric key payload (transport) format – Symmetric Key Package Content Type [SKPC] 3 4 DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 2 The Dynamic Symmetric Key Provisioning Protocol (DSKPP) DSKPP [DSKPP] is a XML based client-server protocol for initialization (and configuration) of symmetric keys to cryptographic modules or applications requiring symmetric keys. It is intended for use within computer and communications systems employing symmetric cryptographic modules that are locally (over-the-wire) or remotely (over-the-air) accessible. The protocol can be run with or without private-key capabilities in the cryptographic modules, and with or without an established public key infrastructure. 2.1 DSKPP Protocol variants DSKPP protocol variants support multiple usage scenarios: Four-pass variant enables mutual key generation by the provisioning server and cryptographic module in near real-time; provisioned keys are not transferred over-thewire or over-the-air. Two-pass variant enables generation and transport of symmetric keys to a cryptographic module in environments where near real-time communication is not possible. Two-pass variant also enables transport of pre-generated (e.g., legacy) keys to a cryptographic module. Fig 2: DSKPP: 2 pass and 4 pass protocol variant comparison DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 2.2 Cryptographic properties DSKPP allows for: Key confirmation of the provisioned keys (proof that the key reached the destination) In both 2 pass and 4 pass protocol variants via a MAC on the exchanged data Replay protection (protection against another rogue client asking for the same key) In both 2 pass and 4 pass variants through inclusion of client-provided data in MAC Server authentication (making sure that the client is communicating with the correct key provisioning server instead of a rogue key server impersonation) In both 2 pass and 4 pass variants through MAC in ServerFinished message when replacing existing key Protection against Man-In-The-Middle (MITM) In both 2 pass and 4 pass variants through use of shared keys, client certificates, or server public key usage User authentication (make sure that the right user is operating the receiving application / cryptographic module) In both 2 pass and 4 pass variants using a user entered authentication code Device authentication (make sure that the keys reach the correct device) In both 2 pass and 4 pass variants if based on shared secret key or if device sends a client certificate 2.3 DSKPP bindings Security Binding Transport level encryption (e.g., TLS) is not required for key transport, the protocol protects the keys in transit with in-built key protection mechanisms TLS/SSL is required if other parameters/attributes must be protected in transit HTTP Binding It is recommended to use the Special Content-Type header defined in [DSKPP] Examples are provided in the specification [DSKPP] 5 6 DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 3 Portable Symmetric Key Container (PSKC) Portable Symmetric Key Container (PSKC) [PSKC] is a standardized XML-based document for transporting symmetric keys and key related meta data. PSKC specifies the information elements (meta-data) that may be required when the symmetric key is utilized for specific purposes, such as the algorithm type or the initial counter in the HOTP [HOTP] algorithm. It also allows transmission of a PIN that will protect the usage of the key and related PIN policies such as maximum and minimum length of PIN. PSKC also allows transmission of key policies and key utilization purpose aligned with NIST SP800-57 “Recommendation for Key Management” [NISTSP800-57]. This allows the transfer of the purpose of utilization of the key, for example ‘authentication’. It became clear that for keys that are intended for a specific purpose and use a specific algorithm the transported key and meta-data would conform to a set of mandatory meta data elements that have been defined as a PSKC profile. This means that a receiver of a PSKC transport document for a specific purpose will know exactly which of the meta-data elements are present. To define a centralised open reference of such profiles the PSKC specification requested to IANA the creation of a IANA maintained registry for PSKC algorithm profiles: Such a profile contains a common name, pointer to a stable reference, URN for reference to the profile, information about PSKC XML elements and attributes being used, and examples. PSKC spec defines two PSKC algorithm profiles: HOTP and KEYPROV-PIN Further algorithm profiles are described in [PSKC-PROFILES] A symmetric key container using an ASN.1 based encoding instead of XML, bust completely aligned with the definition and specification of PSKC is available with [SKPC]. DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 3.1 PSKC Data Model Fig 3: PSKC Data Model The portable key container is based on an XML schema definition and contains the following main conceptual entities: 1. KeyContainer entity - representing the container that carries a number of KeyPackages. A valid container MUST carry at least 1 KeyPackage. 2. KeyPackage entity - representing the package of at most one key and its related provisioning endpoint or current usage endpoint, such as a physical or virtual device and a specific CryptoModule 3. DeviceInfo entity - representing the information about the device and criteria to uniquely identify the device 4. CryptoModuleInfo entity - representing the information about the CryptoModule where the keys reside or are provisioned to 5. Key entity - representing the key transported or provisioned 6. Data entity - representing a list of meta-data related to the key, where the element name is the name of the meta-data and its associated value is either in encrypted form (for example for Data element <Secret>) or plaintext (for example the Data element <Counter>) 7 8 DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 3.2 PSKC Example <KeyContainer Version="1.0“ xmlns="urn:ietf:params:xml:ns:keyprov:pskc“ … > <EncryptionKey><ds:KeyName>Pre-shared-key</ds:KeyName></EncryptionKey> <KeyPackage> <DeviceInfo><Manufacturer>Manufacturer</Manufacturer><SerialNo>987654321</SerialNo> </DeviceInfo> <CryptoModuleInfo><Id>CM_ID_001</Id></CryptoModuleInfo> <Key Id="12345678" Algorithm="urn:ietf:params:xml:ns:keyprov:pskc:hotp"> <Issuer>Issuer</Issuer> <AlgorithmParameters><ResponseFormat Length="8" Encoding="DECIMAL"/></AlgorithmParameters> <Data> <Secret> <EncryptedValue> <xenc:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/> <xenc:CipherData><xenc:CipherValue>pgznhXdDh…. </xenc:CipherValue></xenc:CipherData> <EncryptedValue> <ValueMAC>ooo0Swn6s/myD4o05FCfBHN0560=</ValueMAC> </Secret> <Counter><PlainValue>0</PlainValue></Counter> </Data> <Policy><KeyUsage>OTP</KeyUsage></Policy> </Key> </KeyPackage> </KeyContainer> 3.3 PSKC Key protection methods PSKC allows for various options to protect symmetric keys in transit: Protection by underlying transport protocol (for example TLS) Protection based on pre-shared symmetric keys o For those cases where the encryption algorithm does not provide integrity protection an additional MAC key and MAC algorithm Protection based on Password Based Encryption (PBE) o Key derived from password based on PKCS#5. o XML Encryption 1.1 element structure is used. Protection based on Asymmetric Keys (PKI) o Information about the used certificate must be included in the Key Container Encryption of secret within the PSKC document is performed by leveraging XML Encryption. Digital signature can be applied to the entire <KeyContainer>. DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning 3.4 PSKC additional features PSKC can be used for offline Bulk provisioning of keys o Multiple Key Packages referencing different provisioning endpoints (devices) within a single Key Container document. PSKC has the ability to carry a key policy determining usage of the key in the application or the device. o Start & Expire Date of a key o Restriction on the number of key usages o PIN protection policy Registry for key usage, such as “OTP”, “CR”, “Encrypt” (based on NIST SP800-57 “Recommendation for Key Management” [NISTSP800-57]). 4 Conclusion The work of the IETF ‘keyprov’ working group has delivered three main building blocks to allow standardised interoperable key provisioning for symmetric keys, their meta-data and related key policies. These specifications are open and royalty free to implement: 1. An online XML based protocol to allow online provisioning of symmetric keys – The Dynamic Symmetric Key Provisioning Protocol [DSKPP] 2. An XML based symmetric key payload (transport) format – Portable Symmetric Key Container [PSKC] 3. An ASN.1 based symmetric key payload (transport) format – Symmetric Key Package Content Type [SKPC] Implementations from different vendors will be interoperable allowing for the first time to decouple securely symmetric key clients (applications/crypto modules) and provisioning servers. Fig 4: Interoperable symmetric key provisioning using IETF DSKPP & PSKC Interoperable Symmetric Key Provisioning is possible using IETF ‘keyprov’ standards, spread the word and implement! 9 10 DSKPP and PSKC, IETF standard protocol and payload for symmetric key provisioning References [OATH] The Initiative for Open Authentication, In: www.openauthentication.org. [DSKPP] IETF: Dynamic Symmetric Key Provisioning Protocol, https://datatracker.ietf.org/doc/draft-ietf-keyprov-dskpp/ ,2010. In: [PSKC] IETF: Portable Symmetric Key Container, https://datatracker.ietf.org/doc/draft-ietf-keyprov-pskc/ ,2010. In: [SKPC] IETF: Symmetric Key Package Content Type, In: https://datatracker.ietf.org/doc/draft-ietf-keyprov-symmetrickeyformat/ 2010. [HOTP] IETF: HOTP: An HMAC-Based One-Time Password Algorithm, In: http://www.ietf.org/rfc/rfc4226.txt , 2005. [NISTSP800-57] NIST: Recommendations for Key Management, http://csrc.nist.gov/publications/nistpubs/800-57/sp800-57-Part1revised2_Mar08-2007.pdf , 2007 In: [PSKC-PROFILES] IETF: Additional Portable Symmetric Key Container (PSKC) Algorithm Profiles, In: http://tools.ietf.org/html/draft-hoyer-keyprov-pskc-algorithm-profiles-01 , 2010. Keywords Protocols, Symmetric Keys, Key Provisioning, Security Interoperability, Standards