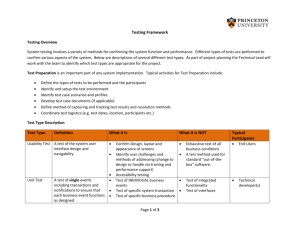
Architecture Methods, Elements and Standards required to achieve
Boundaryless Information Flow™
Terence J. Blevins VP and CIO
The Open Group
44 Montgomery Street
Suite 960
San Francisco, CA 94104 USA
t.blevins@opengroup.org
ABSTRACT: AbstractBoundaryless Information Flow is an expression used to suggest an end state where
the information is made available to the right people at the right time and in the right format to take action in
extended enterprises. To achieve Boundaryless Information Flow requires attention to specific architecture
methods, the implementation of specific architecture elements, and specific use of standards in the creation of
boundaryless infrastructure. To develop a boundaryless infrastructure an open enterprise architecture method
is required.
1 INTRODUCTION
1.1 Preface
The Boundaryless Information Flow [1] problem
space is shared by many organizations. It is a problem space that can no longer be ignored. You can see
the criticality of this problem space in other initiatives like Real-time where getting information to the
right people at the right time is of paramount importance to operations of the mission and/or business.
The Open Group [2] has accepted the challenge of
doing its part to address this problem space. From a
technical perspective we have developed a high-level
reference model that depicts the major components
to address this problem. This paper provides a description of the Boundaryless Information Flow Reference Model developed using TOGAF’s Architecture Development method that responds to the
Boundaryless Information Flow problem. The model
is documented as it stands today and is to be used as
a vehicle for discussion so that the model can be refined as necessary.
1.2 Summary
The Interoperable Enterprise Business Scenario [3]
describes the needs driving our customers’ deployment of their own information infrastructure capability. The follow-up analysis of this work has resulted
in the development of a Boundaryless Information
Flow Reference Model aimed to address the Boundaryless Information Flow problem space.
This paper describes the Boundaryless Information
Flow Reference Model. The goal is to inform others
of the intended meaning behind the graphic to engage in further discussion. Ultimately we will end up
with a high level model that could be communicated
widely and persist throughout the next few years as
progress is made toward the Boundaryless Information Flow space.
The Boundaryless Information Flow Reference
Model provides insights related to customer needs
for information infrastructure in enterprise environments. The Boundaryless Information Flow Reference Model also points to rules and standards to assist in leveraging solutions and products within the
value chain. The following sections provide a brief
discussion of the Boundaryless Information Flow
Reference Model along with a description of the architecture method used to develop the model.
2 BOUNDARYLESS INFORMATION FLOW
REFERENCE MODEL
The reference model is a model of the major component categories for developing, managing, and operating an information infrastructure. It is a model of
a set of applications that sit on top of an application
platform. This reference model is now a subset of
the TOGAF [4] TRM and it uses a different orienta-
tion than the TRM. Consider Fig. 1 below where two
views of the TOGAF TRM are presented. The side
view is the typical view of the TOGAF TRM; where
we are looking at the model as if we were looking at
a house from the side revealing the contents of the
floors. The top down view depicts what one might
see if looking at a house from the roof down.
Fig. 2: Focus of Boundaryless Information Flow
Model
The resulting Boundaryless Information Flow Reference Model is depicted in Fig. 3. It is fundamentally a reference model of application and application
services software essential for an information infrastructure; it assumes the underlying existence of a
computing and network platform, so they are not depicted in the model.
Fig. 3 - Boundaryless Information Flow Model
Fig. 1: TOGAF TRM Orientation Views
The subset of the TRM that comprises the Boundaryless Information Flow Reference Model is depicted in Fig. 2 below. Here you see that we focus on the
application, application platform, and qualities subset of the TOGAF TRM.
The Boundaryless Information Flow Reference
Model has the following core components:
An application platform of services such as location and directory services, work flow services,
data management services, data interchange services, etc… which provide the abilities to locate,
access, and move information within the environment
Information consumer applications which provide
delivery of content to the user of the system, and
the services to request access to information in
the system
Brokering applications which manage the requests
from any number of clients to and across any
number of service providers
Information provider applications which provide
response to client requests and provide rudimentary access to data managed by a particular server
Development tools which provide all the necessary modeling, design, and construction tools to
develop and deploy applications that require access to the integrated information in a manner
consistent with the standards of the environment
Management utilities which provide all the necessary utilities to understand, operate, tune, and
manage the runtime system in order to meet the
demands of an ever changing business in a manner consistent with the standards of the environment
Interfaces that are used between the components.
Interfaces include formats and protocols, application programming interfaces, switches, data values, etc.
Following the TOGAF TRM, the applications are
divided into two main categories: Business Applications and Infrastructure Applications. Information
consumer, information provider, and brokering applications are all Business Applications. Development tools and Management utilities are all Infrastructure Applications. (There are more Business
Applications and Infrastructure Applications than
these, but the above are the subsets relevant to
Boundaryless Information Flow.)
The applications and application platform must
adhere to the policies and requirements depicted by
the qualities back plane.
The following sections describe each of the
runtime, development, and management elements of
the reference model in further detail.
ensure effective and consistent transfer of data between process activities, reducing manual re-entry
errors and improving efficiency. Key to supporting
applications are the services in the application platform that allow those applications to be focused on
understanding and processing the information, in
contrast to understanding the form, format, and/or
location of the information required.
Broker applications are now being built to serve
up single requests that require access to multiple information sources. The brokerage applications break
down the request, distribute the request to multiple
information sources, collect the responses, and send
a single response back to the requesting client.
The following sections describe the application
components of the Boundaryless Information Flow
Reference Model.
3.1.1 Information Provider Applications
Recognizing that information is today held hostage
as depicted in the following figure, information provider applications are those applications that liberate
data from their silos.
3 RUN-TIME ELEMENTS
3.1 Applications
Information consumer, information provider, and
brokering applications provide information brokerage, information access, and information update synchronization. These applications create an environment that provides a rich set of user services that
transparently access heterogeneous systems, databases, and file systems.
Applications are built on top of the services in the
application platform provided in this model. The
Boundaryless Information Flow Reference Model
supports traditional applications as well as applications called Information Brokers, Information Consumers, and Information Providers. The services of
application platform enable the maximum leverage
of a single operational environment that provides
transparency, to the extent possible, for fast and efficient development and deployment of the applications. The services of the application platform also
Fig. 4: Need to Liberate Data
Information provider applications address this by
providing an open interface to a potentially proprietary silo interface. The following Fig. 5 depicts this
where the interfaces on the left of the IPA are open
interfaces and the interfaces between the IPA and silo data are proprietary interfaces.
mation consumer applications with the security services depicted in the brick pattern.
Fig. 5: Liberating the Data
3.1.2 Brokerage Applications
Broker applications serve up single requests that
require access to multiple information sources. The
brokerage applications break down the request, distributes the request to multiple information sources,
collect the responses, and send a single response
back to the requesting client. Brokerage applications
access information providers using the open standard
interface provide by information providers and integrate information from multiple information providers and pass the information using open interfaces to
information consumers. Brokerage applications also
enable access to information within the enterprise by
strategic partners.
Fig. 6: Integrating data
3.1.3 Information Consumer Applications
Information consumer applications provide information to the end user in a form they need it, when
they need it, and in a secured manner. This includes
providing the information in text, video, audio, English, German, …
Information consumer applications communicate
with information brokers or information providers
using the available open interfaces of the brokerage
applications or the information provider applications. Security is provided through the firewalls and
or security services. Fig. 7 below depicts the infor-
Fig. 7: Delivering Data
3.2 Application Platform
Different types of application described above are
built on top of the services provided by the Application Platform.
The Application Platform component of the
Boundaryless Information Flow Reference Model
comprises a subset of all the services defined in the
TOGAF Technical Reference Model, the subset that
pertains to the services required to deliver Boundaryless Information Flow. Specifically, it comprises all
those services in the TRM application platform that
allow applications to focus on understanding and
processing the information required, rather than understanding the form, format, and/or location of the
information.
The services of the Application Platform component can be used to support conventional applications as well as Brokerage, Information Consumer,
and Information Provider applications. When used as
part of an overall Applications Architecture in this
way, such an approach enables maximum leverage
of a single operational environment that is designed
to ensure effective and consistent transfer of data between processes, and to support fast and efficient
development, deployment and management of applications.
The Application Platform component comprises
the following categories of service.
Software Engineering include:
Languages
Libraries and
Registries
Security services include:
AAAC
SSO
Digital Signature
Firewall
Encryption
Intrusion detection
Identity
Key Management
Location and Directory services provide access facilities for name, location, description and relationship of data. Directory services are required to deploy a directory and to ensure that it is made
available throughout the enterprise. The data in the
directory is made available to all other components
in the reference model.
The following depicts the juxtaposition of location
and directory services to the other components.
Fig. 8: Registering the Location of Data
Browser services
Meta indices
Portal and personalization services
Data Interchange include:
Information Format
eForm services
Instant messaging services
Application messaging
Application to application communications services
Enterprise application integration
Information access services provide the ability for
an application to access an integrated view of data,
regardless of whether the data exists in a mainframe
system or in a distributed system. The information
access services ensure that data integrity is maintained among multiple databases and also provide
on-line data cleansing (which means that data is
checked against data rules for each access.)
Data Access Services provide open interfaces to
legacy data, provide new applications standard database access services to vast amounts of existing data,
and provide standard access services to new data
types.
Information and data access
Transformation Mapping
Query distribution
Aggregation
Search
File services
Additional services demand attention to enable the
flow of information as depicted in the following figure.
Location and directory services include services
to:
Access the directory
Register
Publish/Subscribe
Discover
Name
Reference/Dereference
Human Interaction Services provide the means to
consistently present data to the end user in the appropriate format. The human interaction component
of the Boundaryless Information Flow Reference
Model provides services that assist in the formulation of customer data requests and enable visualization and presentation of the data accessed.
Presentation
Transformation
Fig. 9: Workflow Services Enable Information Flow
Workflow services enable process automation by
facilitating user interactions and execution of appli-
cations according to a process map. Workflow services supports the Boundaryless Information Flow
Reference Model through enterprise integration of
applications resulting in applications of extended
value. Workflow services provide essential support
for newer workflow processing, but also addresses
the needs of managing an environment where legacy
systems are prevalent. Specifically, Workflow services can become key enabling software for cleaning
up data due to redundant data re-entry. Workflow
services also provide a means to encapsulate existing
applications thereby supporting the customer’s need
for leverage of existing assets.
4.2 Business Modeling Tools
3.3 Qualities
A rich tool set is provided to design, define and
document the most pertinent information technology
elements of the business based upon the business
and business process rules. Examples of elements to
be designed include, connections between people,
organizations, workflows and computers; data and
object models; physical data translation and translation rules; and constraints.
Qualities are supported by quality of service services including the various services required to
maintain the quality of the system as specified in
service level agreements. Included in this are the
services to post conditions and react to requests from
the Quality of Service Manager.
Additionally qualities are provided through tools
and utilities. For example the following tools and
utilities provide greater manageability and programmability.
4 DEVELOPMENT ELEMENTS
4.1 Development Tools
The Development Tools component provides tools
and a repository for the rules that govern the information needed for point of contact decisions, information required between process steps to reduce
manual re-entry, integrity constraints between customer databases to reduce new dirty data, and to flag
existing dirty data.
The Development Tools provides tools for modeling, designing and construction. Specifically, tools
are provided for business, process, and data modeling, as well as the traditional application construction tool set. The goal of this component is to transform the business model into software that
automates the business processes revolving around
information. Note that each set of tools will be logically connected through the Directory, allowing one
tool to be driven by data from another. The following sections describe the requirements for components of Development Tools.
Tools are provided for the modeling of business
rules and business process rules. Business modeling
describes and documents the business into a comprehensive knowledge base. It establishes a consensus among general management of the business direction, organization, processes, information
requirements, and the current environment of the
business. Perhaps most importantly, this understanding is documented in a common, business-oriented
format to be utilized for subsequent enhancement.
4.3 Design Modeling Tools
4.4 Implementation and Construction Tools
Implementation tools are required to enable timely
development of reusable processes, applications and
applications services. Such tools include intelligent
browsers, data manipulation language compilers and
optimizers, distributed application compilers and
debuggers, heterogeneous client and server development tools, policy definition tools, and work flow
script generation tools.
4.5 Deployment Tools
Deployment tools are necessary to move implemented software from the development environment
into the operational environment.
4.6 Libraries
The Development Toolkit would not be complete
without re-usable libraries of software that utilized
the standards within the operational environment.
5 MANAGEMENT ELEMENTS
5.1 Management Utilities
These utilities are for operations, administration
and systems management, as well as utilities for the
management of data based upon availability and cost
requirements. The utilities provided by this domain
execute in an attended or an unattended environment.
5.1.1 Operations, Administration and Management
Utilities
The OA&M component covers traditional systems
management and administration utilities that manage
business rules and information objects. Examples include utilities for installation, copyright and license
management, and miscellaneous administration, configuration and registration functions. Additional utilities are required for the control of service billing,
service triggering and account management.
5.1.2 Quality of Service Manager Utilities
Including Health Monitoring and Management
Utilities.
ards are needed in some of the key areas depicted by
the reference model. This is an incomplete list and
should be used to stimulate further research. Please
note that the search is for standard interfaces to services, not standard services.
6.1 Standards based Workflow
The following are recommended areas where
standards are required for Workflow services.
Workflow service standard interfaces to access
transactional workflows
Workflow service standards for encoding workflow applications
Workflow service standards for encoding and executing rule and constraint based workflows
6.2 Standards-based Information Access Services
5.1.3 Copy Management Utilities
The copy management utilities within the Boundaryless Information Flow Reference Model ensure the
maximum leverage of operational systems data by
deploying tools that manage data movement from
any given operational system to necessary distribution points in the enterprise. The distribution points
support decisions at distribution points as needed.
Also, the copy management utilities provide tools
that detect and flag poor quality data.
5.1.4 Storage Management Utility
A set of utilities is required to provide least-cost
data storage management. Storage management utilities support the wide variety of storage mechanisms
and are to be connected to file, object and database
systems.
Information access services are a part of the
Boundaryless Information Flow Reference Model.
Information access services require standardization
the in following areas:
Statistical information standards to support distributed query optimization
Metadata exchange standards to support on-line
dirty data detection and cleansing
Data dictionary and repository access standards
Heterogeneous database referential integrity encoding standards
Encoding standards for “push” services
Encoding standards for “pull” services
Standard universal interface for information access to heterogeneous sets of information
Standard interface to tag information for universal
access
6.3 Standards-based Management
6 STANDARDS REQUIRED
To address the Boundaryless Information Flow
problem long-term open standards are required for
the interfaces. Without open standard interfaces new
silos will be created. Interfaces include invocation,
formats, and protocols.
Invocation standards include standard mechanisms
to invoke a given service, e.g. programming interface, switches, shared memory, semaphores, …
Formats standards include message formats,
metadata, encodings, …
Protocol standards include the known rules of processing that must be adhered to, for example TCP is
a protocol specification.
The following sections describe where open stand-
The following are suggested areas where standards
are needed, but the specific interfaces are not identified. These areas relate to information centric management tools for the economic management of the
infrastructure. The standards should enable:
A Boundaryless Information Flow Management
Utility for enterprise processes, people, applications, objects, data and information in heterogeneous environment. Included are integration of
legacy management capabilities and specific database backup, restore and recovery utilities.
A set of Boundaryless Information Flow information copy management utilities that provide
rules based information and data movement for
heterogeneous environments. This utility ensures
that data and information are available throughout
the enterprise based upon the business rules driving the need for the access. Included is database
replication management that provides performance, consistency and availability. Specific
standards for data synchronization area required
here.
A Boundaryless Information Flow storage management utility that manages data and information
storage based upon lowest cost per use.
6.4 Standards-based Development Environment
A Standards-based Development Environment that
complements the run-time also requires examination
for standards. Development environment standards
should enable:
Enterprise-wide application reuse, management
and control tools
Common active directory and repository used for
ADE and runtime, reusable objects,...
Legacy application encapsulation and re-use tools
Enterprise planning tools (strategies to technologies)
Enterprise process management development
tools
Application mining tools to "discover" knowledge
of existing applications
Standards include:
Enterprise modeling data interchange standards
Directory standards for applications and libraries
Standards for universal dynamic link libraries
Binary application standards
6.5 Standards based Enterprise Visualization and
Access
An examination of the standards require to get information delivered to the “edge” is also required.
The following lists likely areas to look for standardization of interfaces.
Standard interfaces to support voice recognition
services
Standard interfaces to support text to speech and
speech to text services
Standard interfaces to support an interactive query
interface environment
Standard interfaces to support presentation (including 3D and 4D visualization) tools
Standards for meta indices/meta data
Standards for personalization preference encodings
Naming services
Discovery services
Registration Services
6.7 Data Interchange Services
Standards need to be selected for the following to
support the ability for applications to communicate
with other applications in a boundaryless environment:
Application to application invocation interface
Application to application information exchange
formats and protocols
6.8 Security Services
Standards need to be selected for the following to
support the ability to secure the flow of information
in a boundaryless environment:
Identification and authentication services
System entry control services
Audit services
Access control services
Non-repudiation services
Encryption services
Digital signature services
Key management services
6.9 International Operation Services
Standards need to be selected for the following to
support the ability to provide cost effective support
of the international flavor in the boundaryless environment:
Character sets and data representation services
Cultural convention services
Local language support services
6.10 Quality of Service
To maintain quality of service in an extended enterprise standard interfaces are paramount. The following are likely areas to look for standardization of
interfaces.
Standard interfaces to report information about
state, e.g. health, performance, etc
Standard interfaces to communicate operational
command requests
Standard model to depict end-to-end quality of
service
6.6 Location and Directory Services
Standards need to be selected for the following to
support the ability to locate and access resources in a
boundaryless environment:
Directory access services
7 USING TOGAF ADM
TOGAF is a “detailed method and a set of supporting tools - for developing an enterprise architec-
ture” [4]. The TOGAF Architecture Development
Method (ADM – described in Appendix-TOGAF
ADM) was used to develop the Boundaryless Information Flow reference model. The first deliverable
of the method produced the Interoperable Enterprise
Business Scenario [3] that set the context for the enterprise and established the imperative. Without taking this view, a lesser picture would have been produced. The second deliverable produced was the
Boundaryless Information Flow Reference Model
described in this document. This reference model
paints a very large picture of what is needed to address the Boundaryless Information Flow problem.
Using the method further will be more difficult in
that we are talking about an industry changing, not
an organization.
Architecture views which enable the architect to
ensure that a complex set of requirements are adequately addressed
Linkages to practical case studies
Guidelines on tools for architecture development
9.1 What is Enterprise Architecture
Architecture is “the structure of components, their
interrelationships, and the principles and guidelines
governing their design and evolution over time.”
Enterprise architecture is an extension of the
above definition; the extension is based on further
describing the components. In a technology architecture the components are typically components such
as servers, networks, applications, however in an enterprise architecture the components are broader,
they include organizations, processes, humans, data,
applications, technology, and more.
8 CONCLUSION
Addressing the Boundaryless Information Flow
problem is not an easy one. But applying the methods and techniques in the relevant parts of TOGAF
has provided a realistic view of the scope of the
problem and the further work that is necessary. Following the advise of TOGAF what comes next is to
determine what standard interfaces exist for all of
the areas covered and populate the architecture with
those standards. If standards don’t exist a plan must
be established to determine how to fill in those gaps.
Taking an enterprise view helps move forward
with our eyes wide open.
9 APPENDIX-TOGAF ADM
TOGAF is a “detailed method and a set of supporting tools - for developing an enterprise architecture.” [4] The TOGAF Architecture Development
Method (ADM) explains how to derive an organization-specific enterprise architecture that addresses
business requirements. The ADM provides a reliable, proven way of developing the architecture; architecture views which enable the architect to ensure
that a complex set of requirements are adequately
addressed; linkages to practical case studies; and
guidelines on tools for architecture development.
The TOGAF Architecture Development Method
(ADM) explains how to derive an organizationspecific enterprise architecture that addresses business requirements. The ADM provides:
A reliable, proven way of developing the architecture
10 COPYRIGHT
Copyright © 2004 by The Open Group, San
Francisco, California, U.S.A. All rights reserved.
11 TRADEMARK
Boundaryless Information Flow is a trademark of
The Open Group.
12 ACKNOWLEDGMENT
This paper is the result of work done by the many
members of The Open Group.
13 REFERENCES
[1] The Open Group, Boundaryless Information
Flow Vision [Online]. Available:
http://www.opengroup.org/overview/index.htm
[2] The Open Group, The Open Group Making
Standards Work [Online]. Available:
http://www.opengroup.org/
[3] J. Spencer, T. Blevins (2002), Interoperable Enterprise Business Scenario [Online]. Available:
http://www.opengroup.org/cio/iop/index.htm
[4] J. Spencer, et al (2004). TOGAF “Enterprise
Edition” Version 8.1 [Online]. Available:
http://www.opengroup.org/architecture/togaf8doc/arch/
[5] J. Spencer , Architecture Forum [Online]. Available:
http://www.opengroup.org/architecture/
[6] J. F. Sowa, J. A. Zachman (1992). Extending and
formalizing the framework for information systems architecture, IBM System Journal, Vol 31,
No 3, 1992