Attacks - No diagrams
advertisement

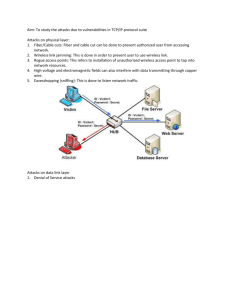
Aim: To study the attacks due to vulnerabilities in TCP/IP protocol suite Theory: Overview of TCP/IP Protocol suite The Internet protocol suite is the networking model and a set of communications protocols used for the Internet and similar networks. It is commonly known as TCP/IP, because its most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) were the first networking protocols defined in this standard. TCP/IP provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination. This functionality has been organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link), the internet layer, connecting independent networks, thus establishing internetworking, the transport layer handling host-tohost communication, and the application layer, which contains all protocols for specific data communications services on a process-to-process level. Attacks on physical layer 1. Fiber/Cable cuts: Fiber and cable cut can be done to prevent authorized user from accessing network. 2. Wireless link jamming: This is done in order to prevent user to use wireless link. 3. Rogue access points: This refers to installation of unauthorized wireless access point to tap into network resources. 4. High voltage and electromagnetic fields can also interfere with data transmitting through copper wire. 5. Eavesdropping (sniffing): This can be used for listening network traffic. Attacks on data link layer 1. Denial of Service attacks A Denial of Service attack is a type of attack that exploits weaknesses in protocols and services by exhausting resources, causing service disruption or Quality of Service (QoS) degradation. Its main goal is to affect availability of the targeted service. If an attacker can launch a DoS attack that affects L2 networking devices, a single residential user might cause havoc to all others using services on the same network. The effect of such an attack could encompass many users, depending on the architecture and layout of the network. 2. CAM table overflow attack A switch's CAM table contains network information such as MAC addresses available on physical switch ports and associated VLAN parameters. CAM Table Overflows occur when an influx of MAC addresses are flooded into the table and the CAM table threshold is reached. This causes the switch to act like a hub, flooding the network with traffic out all ports. The flooding caused by a CAM Table Overflow is limited to the source VLAN, thus does not affect other VLANs on the network. 3. MAC address spoofing MAC address spoofing is another major threat to data link layer. Through MAC address spoofing an attacker can change his MAC address to the MAC address of a different machine in the network. Due to which the switch will start sending frames to the attackers machine. Mac address spoofing can also be used to bypass several security measures, taken by ISP's to block users. In Linux Mac address spoofing can be done very easily through command line. Mac address spoofing can also be done in windows. 4. DHCP related attacks Another vulnerable protocol which can be compromised using Data Link layer is DHCP. DHCP is mainly used to automatically obtain the network configuration details, for a host. The details are like IP address, Gateway, DNS server details etc. Normally the IP address provided by the DHCP server, is on a lease basis, which will expire after a certain period of time, during this period the DHCP server will not allocate the same address to any other clients. DHCP server's maintain a list of IP's that are already allocated, and the IP's that are not allocated. So this poses a denial of service attack risk, if an attacker sends large number of DHCP request with spoofed MAC address to the DHCP server to consume all the available IP addresses. Such kind of a denial of service attack against DHCP server is called IP pool starvation attack. At this point of time, the DHCP server cannot allocate any IP address to the new hosts in the network (Because all the IP pool addresses are consumed by the attacker's spoofed DHCP requests). So the attacker will change himself to a DHCP server, and will allot IP's and gateway as per his wish, to monitor the entire network traffic. DHCP IP pool starvation attack can be prevented by using switch's port security features. 5. ARP Attacks Similar to the switch's CAM table, each and every machine contains an ARP table. ARP stands for Address Resolution Protocol. This table consists of IP to MAC address mapping. Whenever you try to reach a computer on your network, the first thing that your computer does is to look its ARP table to find, the destination MAC address corresponding to the destination IP address. An attacker can send broadcasts with spoofed MAC and IP addresses, so that the machine's in the network will update their ARP table entry with the attacker's spoofed address and MAC. Network layer attacks 1. Ping of death attack A ping of death (abbreviated "PoD") is a type of attack on a computer that involves sending a malformed or otherwise malicious ping to a computer. A ping is normally 56 bytes in size (or 84 bytes when the Internet Protocol header is considered); historically, many computer systems could not handle a ping packet larger than the maximum IPv4 packet size, which is 65,535 bytes. Sending a ping of this size could crash the target computer. In early implementations of TCP/IP, this bug was easy to exploit. This exploit has affected a wide variety of systems, including Unix, Linux, Mac, Windows, printers, and routers. However, most systems since 1997–1998 have been fixed, so this bug is mostly historical. Generally, sending a 65,536-byte ping packet would violate the Internet Protocol as written in RFC 791, but a packet of such a size can be sent if it is fragmented; when the target computer reassembles the packet, a buffer overflow can occur, which often causes a system crash. In recent years a different kind of ping attack has become widespread—ping flooding simply floods the victim with so much ping traffic that normal traffic fails to reach the system 2. ICMP flood attack A smurf attack is one particular variant of a flooding DoS attack on the public Internet. It relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the broadcast address of the network, rather than a specific machine. The network then serves as a smurf amplifier. In such an attack, the perpetrators will send large numbers of IP packets with the source address faked to appear to be the address of the victim. The network's bandwidth is quickly used up, preventing legitimate packets from getting through to their destination. To combat denial of service attacks on the Internet, services like the Smurf Amplifier Registry have given network service providers the ability to identify misconfigured networks and to take appropriate action such as filtering. 3. Overlapping fragment attack The IP fragment overlapped exploit occurs when two fragments contained within the same IP datagram have offsets that indicate that they overlap each other in positioning within the datagram. This could mean that either fragment A is being completely overwritten by fragment B, or that fragment A is partially being overwritten by fragment B. Some operating systems do not properly handle fragments that overlap in this manner and may throw exceptions or behave in other undesirable ways upon receipt of overlapping fragments. This is the basis for the teardrop Denial of service attacks. Transport layer attacks 1. Port scan attack A port scanner is a software application designed to probe a server or host for open ports. This is often used by administrators to verify security policies of their networks and by attackers to identify running services on a host with the view to compromise it. A port scan or portscan can be defined as an attack that sends client requests to a range of server port addresses on a host, with the goal of finding an active port and exploiting a known vulnerability of that service, although the majority of uses of a port scan are not attacks and are simple probes to determine services available on a remote machine. To portsweep is to scan multiple hosts for a specific listening port. The latter is typically used in searching for a specific service, for example, an SQL-based computer worm may portsweep looking for hosts listening on TCP port 1433. 2. SYN flood attack A SYN flood occurs when a host sends a flood of TCP/SYN packets, often with a forged sender address. Each of these packets is handled like a connection request, causing the server to spawn a half-open connection, by sending back a TCP/SYN-ACK packet (Acknowledge), and waiting for a packet in response from the sender address (response to the ACK Packet). However, because the sender address is forged, the response never comes. These half-open connections saturate the number of available connections the server is able to make, keeping it from responding to legitimate requests until after the attack ends. 3. UDP flood attack A UDP flood attack is a denial-of-service (DoS) attack using the User Datagram Protocol (UDP), a session less/connectionless computer networking protocol. Using UDP for denialof-service attacks is not as straightforward as with the Transmission Control Protocol (TCP). However, a UDP flood attack can be initiated by sending a large number of UDP packets to random ports on a remote host. As a result, the distant host will: a. Check for the application listening at that port; b. See that no application listens at that port; c. Reply with an ICMP Destination Unreachable packet. Thus, for a large number of UDP packets, the victimized system will be forced into sending many ICMP packets, eventually leading it to be unreachable by other clients. The attacker(s) may also spoof the IP address of the UDP packets, ensuring that the excessive ICMP return packets do not reach them, and anonymizing their network location(s). Most operating systems mitigate this part of the attack by limiting the rate at which ICMP responses are sent. Application layer attacks 1. Session Hijacking Session hijacking, sometimes also known as cookie hijacking is the exploitation of a valid computer session—sometimes also called a session key—to gain unauthorized access to information or services in a computer system. In particular, it is used to refer to the theft of a magic cookie used to authenticate a user to a remote server. It has particular relevance to web developers, as the HTTP cookies used to maintain a session on many web sites can be easily stolen by an attacker using an intermediary computer or with access to the saved cookies on the victim's computer. A popular method is using source-routed IP packets. This allows a hacker at point A on the network to participate in a conversation between B and C by encouraging the IP packets to pass through its machine. If source-routing is turned off, the hacker can use "blind" hijacking, whereby it guesses the responses of the two machines. Thus, the hacker can send a command, but can never see the response. However, a common command would be to set a password allowing access from somewhere else on the net. A hacker can also be "inline" between B and C using a sniffing program to watch the conversation. This is known as a "man-in-the-middle attack". 2. SQL Injection attacks SQL injection is a code injection technique, used to attack data driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database. 3. Cross Site scripting Cross-site scripting (XSS) is a type of computer security vulnerability typically found in Web applications. XSS enables attackers to inject client-side script into Web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec as of 2007. Their effect may range from a petty nuisance to a significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner. 4. Root traversal attacks on web server Directory traversal attacks are used to attempt to access files not intended to be accessed, i.e., files that are not under the root directory, explained below, on a server. Directory traversal attacks are also known as ../ (dot dot slash) attacks, directory climbing, and backtracking. A Web site uses a server to store and give access to the files that contain web content. These publicly accessible files are stored in what is typically called the "web document root" or simply "root" directory. A directory is another word for what shows up as a folder in the Microsoft Windows operating system. Directories allow hierarchical organization of files and other directories. By exploiting a directory traversal vulnerability, an attacker can access files in directories other than the root directory. This can be harmful, since access to restricted files containing passwords or other private information may compromise the web server. Conclusion: Thus we have studied the attacks due to vulnerabilities in TCP/IP protocol suite