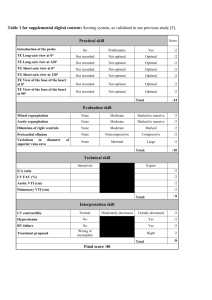
FrontPage Server Extensions
advertisement

MICROSOFT FRONTPAGE 2000 SERVER EXTENSIONS SECURITY WHITE PAPER TODD M FEINMAN DAVID J. GOLDMAN Table of Contents TABLE OF CONTENTS .............................................................................................................................................i INTRODUCTION ..................................................................................................................................................... iii ABSTRACT ............................................................................................................................................................... iii ABOUT PRICEWATERHOUSECOOPERS LLP ...............................................................................................................iv DISCLAIMER ..............................................................................................................................................................v Limitation of Testing ............................................................................................................................................ v EXECUTIVE SUMMARY .........................................................................................................................................1 OVERVIEW ................................................................................................................................................................3 BACKGROUND ..........................................................................................................................................................4 What are the FrontPage Server Extensions? .......................................................................................................4 What can I do with FrontPage Server Extensions?..............................................................................................4 What is a FrontPage Extended Web? ..................................................................................................................5 What are root webs and subwebs? .......................................................................................................................5 TEST CASE APPROACH ..........................................................................................................................................7 Windows NT .........................................................................................................................................................7 UNIX ....................................................................................................................................................................7 Test Environment Topology .................................................................................................................................8 APPROACH ............................................................................................................................................................... 10 Installation Tests ................................................................................................................................................ 10 Configuration Tests ............................................................................................................................................ 10 Penetration Tests................................................................................................................................................ 10 Data Capture Tests ............................................................................................................................................ 10 SUMMARY OF FINDINGS .......................................................................................................................................... 11 Installation Tests ................................................................................................................................................ 11 Configuration Tests ............................................................................................................................................ 11 Penetration Tests................................................................................................................................................ 13 Data Capture Tests ............................................................................................................................................ 14 CONCLUSION ........................................................................................................................................................... 15 WINDOWS NT TEST CASE RESULTS ................................................................................................................ 16 UNIX TEST CASE RESULTS ................................................................................................................................. 24 BASELINE SECURITY CONFIGURATION ........................................................................................................ 31 WINDOWS NT .......................................................................................................................................................... 31 2/12/16 Page i User Setup .......................................................................................................................................................... 31 Directory Permissions........................................................................................................................................ 32 Configuration Files ............................................................................................................................................ 34 Event Log ........................................................................................................................................................... 39 UNIX ...................................................................................................................................................................... 40 User Setup .......................................................................................................................................................... 40 System Settings and Services .............................................................................................................................. 40 Directory Permissions........................................................................................................................................ 41 Configuration Files ............................................................................................................................................ 42 FRONTPAGE SERVER EXTENSIONS .......................................................................................................................... 43 OTHER CONSIDERATIONS ........................................................................................................................................ 49 Networking ......................................................................................................................................................... 49 Miscellaneous..................................................................................................................................................... 49 APPENDIX A – WINDOWS NT .............................................................................................................................. 50 OBJECTIVE - CONFIGURATION ................................................................................................................................. 50 Scenario – Acknowledgement of Subwebs.......................................................................................................... 50 Scenario – Use of Rights .................................................................................................................................... 51 Scenario – Subweb Information Gathering ........................................................................................................ 57 Scenario – User Information Gathering ............................................................................................................ 68 Scenario – File Execution .................................................................................................................................. 70 OBJECTIVE - PENETRATION ..................................................................................................................................... 72 Scenario – Port Discovery ................................................................................................................................. 72 Scenario – Account Lockout............................................................................................................................... 72 OBJECTIVE - DATA CAPTURING ............................................................................................................................... 76 Scenario – Password Gathering ........................................................................................................................ 76 Scenario – Confidential Information Gathering ................................................................................................ 80 APPENDIX B – UNIX ............................................................................................................................................... 85 OBJECTIVE - CONFIGURATION ................................................................................................................................. 85 Scenario – Acknowledgement of Subwebs.......................................................................................................... 85 Scenario – Use of Rights .................................................................................................................................... 86 Scenario – Subweb Information Gathering ........................................................................................................ 93 Scenario – File Execution ................................................................................................................................ 111 OBJECTIVE - PENETRATION ................................................................................................................................... 116 Scenario – Port Discovery ............................................................................................................................... 116 OBJECTIVE - DATA CAPTURING ............................................................................................................................. 117 Scenario – Password Gathering ...................................................................................................................... 117 Scenario – Confidential Information Gathering .............................................................................................. 120 ABOUT THE AUTHORS AND EVALUATION TEAM .................................................................................... 125 2/12/16 Page ii Introduction Abstract This document presents the results of tests designed to evaluate the security controls for Microsoft FrontPage 2000 Server Extensions. The approach used to evaluate Microsoft FrontPage 2000 Server Extensions is discussed, and definitions of multiple test cases covering installation, configuration, penetration and data capturing are provided. The configuration of the testing laboratory and its equipment used to evaluate this product is described, and a security checklist and baseline security configuration are presented. 2/12/16 Page iii About PricewaterhouseCoopers LLP PricewaterhouseCoopers LLP (PricewaterhouseCoopers) is one of the world's leading professional services firms providing audit, tax, management consulting, financial advisory and human resource advisory services to clients in a broad range of industries on a globally integrated basis in 140 countries. In the United States, the firm has been serving clients since 1898 and today has 17,000 partners and staff working in over 100 offices. Organized along industry lines, the firm seeks to create value for its clients and to bring a competitive advantage to their activities. Its clients include a variety of large and small, publicly and privately held companies, many numbered among the Fortune 500. PricewaterhouseCoopers has recognized the risks and threats to information since the early stages of information technology development. Their original approach to auditing computer based systems included the study and evaluation of controls over the security of information. The firm has since established the Technology Risk Services (TRS) national practice dedicated to serving their clients’ needs in addressing security over one of their most important resourcestechnology generated and resident information. The TRS professionals are recognized leaders in the fields of information technology, telecommunications, logical and physical security, and auditing. They are knowledgeable in the latest security tools and methods, and in evaluating, analyzing, developing and implementing security and control solutions. 2/12/16 Page iv Disclaimer This document (the “Evaluation”) presents certain discussions and recommendations concerning Microsoft FrontPage 2000 Server Extensions security. The Evaluation is based on Microsoft FrontPage 2000 Server Extensions Release Candidate (Build 2528) running on Windows NT Server Version 4.0 RTM (Build 1381), Windows NT Server Version 5.0 (beta 2), Solaris 2.6 and to a large extent upon technical documentation and other information developed and supplied by Microsoft. PricewaterhouseCoopers LLP (“PricewaterhouseCoopers”) did not review source code for dormant flaws, and cannot ensure that every potential weakness that might arise in the future has been identified. The Evaluation is based upon a collection of methodologies and tests interacting at a single point in time with an Internet environment that is continually changing and becoming ever more complex. Internet security is continuously being assaulted by hackers and other criminals who are increasingly sophisticated and resourceful. Just as software virus protection programs are hard put to remain more than a small step ahead of the virus perpetrators, security analyses and recommendations may unexpectedly become out-dated. PricewaterhouseCoopers and the individual authors of this report (collectively, the “Authors”) have used methodologies and software they believe to be reliable in evaluating the security issues presented, but the Authors make no representations or warranties concerning either those methodologies and software or the results obtained from their use. While the Authors believe that the material in this Evaluation presents a fair and reasonable picture of Microsoft FrontPage 2000 Server Extensions security controls, nothing herein can substitute for each reader’s own professional and business judgment, independent investigations, and research into the subjects covered. All information presented herein is of a general nature and may not be applicable to any particular situation. Nothing herein constitutes an endorsement of any product by the Authors. Limitation of Testing It is important to note that not all types of penetration tools and techniques were utilized or attempted for the Evaluation. The tests executed in the Evaluation utilized penetration testing tools and techniques common to the security industry. Many penetration attempts rely on long periods of time to analyze and understand targets, utilize intermediary nodes and networks, and employ automated techniques that may run unattended for extended periods of time. Such long term testing was beyond the scope of the Evaluation. In addition, penetration tests provide 2/12/16 Page v information regarding only very specific security vulnerabilities and should not be viewed as conclusive of Microsoft FrontPage 2000 Server Extensions’ overall security posture. The results of the Evaluation cannot disclose every weakness that may exist in prior or future versions. The Evaluation focused on technical security controls. There are additional non-technical techniques, such as social engineering, that have proven to be very effective in circumventing security controls, but were not addressed in this Evaluation. 1999 PricewaterhouseCoopers LLP 2/12/16 Page vi Executive Summary The Microsoft FrontPage Server Extensions are provided as a means to facilitate the rapid and easy development and administration of a potentially complex web site. In the increasingly popular arena of Electronic Business and the Internet, this process is progressively more important. When connecting to the Internet, in any capacity, organizations and individuals assume significant security risk. When the focus of this connection is to conduct business, the risk is even greater. This white paper has been written to assist in enhancing the security controls surrounding the FrontPage Server Extensions and to help mitigate many of the common security issues that are introduced by engaging in remote administration of a web site on the Internet. This document represents an attempt to accomplish the following: Provide an evaluation of the Microsoft FrontPage Server Extensions; Provide information regarding the nature of risks and threats; Uncover specific potential vulnerabilities within the product; And, recommended countermeasures for mitigating the risk of any exposure. This white paper should be used in conjunction with vendor literature, such as the Server Extensions Resource Kit (SERK), and your own critical assessment, to determine its effectiveness and appropriateness for your business environment. This white paper is one of several sources that can be referenced when attempting to configure and assess a web server enabled with FrontPage Server Extensions. It is critical to note that there is no one right answer to the question of what constitutes enough security. The answer is often a custom solution that depends on your business needs for control and flexibility. Adopting a business practical approach when addressing the level of security an organization requires should be fundamental to all security decisions. In our assessment of the Microsoft FrontPage Server Extensions, we completed a four-phase evaluation program: Installation, Configuration, Penetration Testing, and Data Capture. The rationale for designing this four-phase approach was to emulate, as closely as possible, the life cycle of product deployment in a commercial environment. The approach was designed to 2/12/16 Page 1 reveal security vulnerabilities that would have a major impact on the overall security of a web server and how to configure a web server so that security exposures are mitigated. A number of tests were performed and re-performed and followed by careful and detailed analysis of the results. Upon review of all relevant data, it was determined that, when properly configured, the Microsoft FrontPage Server Extensions can provide a safe and secure conduit for developing and administering web sites. In addition, the FrontPage Server Extensions did not expose a web server to any common exploitable vulnerabilities that would place the web server at significant risk when communicating via the Internet. In summary, it appears that the Microsoft FrontPage Server Extensions, when properly installed, configured, maintained, and monitored, can provide a reasonable and practical level of security for developing and maintaining an electronic Internet presence. 2/12/16 Page 2 Overview To help understand the purpose of this white paper and the eight sections contained within, the following summary is presented. Background: This section provides an overview of the product. It gives a brief introduction of to the product feature set and explains some of the terminology used throughout the remainder of the document Test Case Approach: This section describes the nature of the tests performed and the test environment. It outlines the types of tests that were executed and the types of hardware and software that they were performed on. Windows NT Test Case Results: This section lays out the issues to consider when running the FrontPage Server Extensions on Windows NT with Internet Information Server. It describes what to be aware of and how to address these issues. UNIX Test Case Results: This section lays out the issues to consider when running the FrontPage Server Extensions on UNIX with the Apache Web Server. It describes what to be aware of and how to address these issues. Baseline Security Configuration: This section provides the technical details to configure the FrontPage Server Extensions in a secure fashion as described in the previous two sections. It contains settings, permissions, and configuration options specific to the FrontPage Server Extensions, the web server, and the underlying operating system. Appendix A – Detailed Windows NT Test Results: This appendix shows, in every detail, the tests and their results as they we executed in the Windows NT test environment. It provides a way to duplicate any test performed or to learn more technical information about an issue that was described previously in the document. Appendix B – Detailed UNIX Test Results: This appendix shows, in every detail, the tests and their results as they we executed in the UNIX test environment. It provides a way to duplicate any test performed or to learn more technical information about an issue that was described previously in the document. 2/12/16 Page 3 Background What are the FrontPage Server Extensions? The Microsoft FrontPage 2000 Server Extensions are a set of programs on a Web server that support administering, authoring, and browsing a FrontPage-extended Web site. The FrontPage Server Extensions work with many popular Web servers, both commercial and freeware. To support the many server types, the FrontPage Server Extensions execute via the Common Gateway Interface (CGI) or the Internet Server Application Programming Interface (ISAPI). Communication between a client computer and a Web server containing the Server Extensions uses the same protocol, HTTP, that Web browsers on a client computer use to interact with a Web server. No file-sharing access on the Web server machine is needed, and neither FTP nor telnet access is required. No proprietary file system sharing calls are necessary to use the FrontPage Server Extensions. When the FrontPage Server Extensions are installed on a Web server, FrontPage-extended web authoring and administering functionality are available from any computer that has the FrontPage client, whether the computer is on the Internet or on an intranet. The browse-time functionality of the Server Extensions is available from any Web browser. What can I do with FrontPage Server Extensions? With FrontPage Server Extensions it is possible to administer and author a FrontPage-extended web, as well as add other functionality to it. Administering FrontPage-extended webs includes setting permissions for authors, administrators, and Web site visitors. Authoring a FrontPageextended web includes automatically maintaining hyperlinks, generating and maintaining navigation bars across all pages, and automatically formatting pages to give them a consistent appearance. Added functionality includes interactive discussion groups, hit counters, and search forms. 2/12/16 Page 4 What is a FrontPage Extended Web? FrontPage works with World Wide Web content by managing FrontPage-extended webs. A FrontPage-extended web contains all the Web pages, graphics, and other files and documents that make up a Web site. Authors create, delete, open, and close FrontPage-extended webs by using FrontPage on a client computer. A FrontPage-extended web can be stored on a remote or local Web server. Using FrontPage, FrontPage-extended webs can be copied from one Web server to another. What are root webs and subwebs? A root web is a FrontPage-extended web that is the top-level content directory of a Web server or, in a multihosting environment, of a virtual Web server. It can have many levels of subdirectories containing its content. There can be only one root web per Web server or virtual Web server. A subweb is a complete FrontPage-extended web that is a subdirectory of the root web or of another subweb. Subwebs are the FrontPage mechanism for breaking up a Web site so that different areas can be owned and maintained by different people or groups. Each subweb can have many levels of subdirectories. A public subweb is a subweb whose content can be viewed by any individual that can connect to the website. An individual using an anonymous account will be able to read the content of this subweb. A private subweb is a subweb with restricted access. To view the content of a private subweb, a user must supply a username and password and be authenticated by the web server. This means that a individual browsing under an anonymous account will not be able to view the content. By using subwebs, finer security granularity is automatic because each subweb maintains separate security settings. An additional benefit of using subwebs is potentially better performance, because the time required to recalculate hyperlinks is directly proportional to the number and size of the documents stored in a single web. 2/12/16 Page 5 In earlier versions of FrontPage, subwebs could only be created directly below the root web. In FrontPage 2000, subwebs can be created at any level of your content structure, including below another subweb. In large organizations, webs are usually divided into areas that are owned and maintained by different groups in the organization allowing Webmasters to set up their Web sites in a logical way that matches the structure of the organization. Even though subwebs appear below other webs in the Web server's file system and URL space, the content of a subweb is not included in its parent web. An author of a FrontPage-extended web does not automatically have permission to edit any of its subwebs. This separation of content is done by the FrontPage Server Extensions. 2/12/16 Page 6 Test Case Approach PricewaterhouseCoopers evaluated Microsoft FrontPage Server Extensions by creating a “Test Case Approach”. This approach involved developing a test environment, setting objectives, creating test case scenarios to meet those objectives, executing the procedures outlined by each scenario, and interpreting the results. This approach was duplicated and performed on four sample technical environments split into two major sections: Windows NT 1. Microsoft Windows NT 4.0 Server with Service Pack 3 running Internet Information Server 4.0 2. Microsoft Windows NT Server 5.0 beta 2 running Internet Information Server 5.0 (This product will be released as Windows 2000) UNIX 3. Solaris 2.6 running Apache 1.3.1 4. Solaris 2.6 running Apache 1.3.1 with the FrontPage Apache Patch Note: All tests were performed on Microsoft FrontPage 2000 Server Extensions Release Candidate (Build 2528). The most significant component of the approach is the test case scenarios, which focus on four objectives; Installation, Configuration, Penetration, and Data Capture. Each scenario contains procedures and findings designed to satisfy the test scenario objectives. This section describes the test environment topology and test scenario objectives. Procedures and findings are detailed in the Appendices. 2/12/16 Page 7 Test Environment Topology The following network diagram PricewaterhouseCoopers approach. depicts the lab infrastructure used in the Differences in infrastructure could produce dissimilar results. Note that this is not a secure or ideal way for your organization to set up their production network topology; it is only for testing purposes. IP: 223.1.1.4 IP: 223.1.1.6 Windows NT Server 4.0 Internet Infomration Server 4.0 FrontPage Server Extensions Windows NT Server 5.0 beta 2 Internet Infomration Server 5.0 FrontPage Server Extensions IP: 223.1.1.2 IP: 223.1.1.3 Solaris 2.6 Apache 1.3.1 FrontPage Server Extensions Solaris 2.6 Apache 1.3.1 / FrontPage Patch FrontPage Server Extensions Hub IP: 223.1.1.5 IP: 223.1.1.10 NT Server 4.0 Sniffer Windows NT Server 4.0 FrontPage Client 2/12/16 Page 8 The following web topology diagram depicts the web site configuration used in the PricewaterhouseCoopers approach. Differences in web site configurations could produce dissimilar results. FP Extended Web Root Administrators: Administrator,RootAdmin Author: Rootauth Browsers: Everyone http://223.1.1.4 Public Site Private Site http://223.1.1.4/Publicsite http://223.1.1.4/Privatesite Permissions Inherited Permissions Not Inherited Administrators: RootAdmin, PrivateAdmin Authors: Rootauth, Privateauth Browser: PrivateBrowse Public Site Subweb http://223.1.1.4/Publicsub Permissions Inherited Private Site Subweb Private Site Subweb2 http://223.1.1.4/Privatesub http://223.1.1.4/Privatesub2 Permissions Inherited 2/12/16 Permissions Not Inherited Administrators: RootAdmin, PrivateSub2Admin Authors: Rootauth, PrivateSub2auth Browser: PrivateBrowse Page 9 Approach PricewaterhouseCoopers completed a four-phase evaluation program: Installation, Configuration, Penetration Testing, and Data Capture. The approach was designed to reveal if there are security vulnerabilities and how to configure a web server so that security exposures are mitigated. Installation Tests The objective of the installation test is to identify any security related installation options, and evaluate the security implications of the installation options and overall installation procedure. Configuration Tests The objective of the configuration tests are to identify any security related configuration options, and to evaluate security when Microsoft FrontPage Server Extensions are configured with default, and custom security settings. Penetration Tests The objective of the penetration tests are to evaluate Microsoft FrontPage Server Extensions’ external vulnerabilities. The penetration tests were designed to use a combination of standard Internet tools, used for determining vulnerabilities of common Internet connected Servers, in addition to special PricewaterhouseCoopers methods and tools designed to exploit specific Internet vulnerabilities and Microsoft FrontPage Server Extensions specific vulnerabilities (based on our understanding of how it was designed). Data Capture Tests The objective of the data capture tests are to determine if Microsoft FrontPage Server Extensions transmit or receive data in a manner that can be compromised using readily available tools. 2/12/16 Page 10 Summary of Findings The following tables give an overview of all the tests performed on the FrontPage Server Extensions. For more detailed information on the specific test, refer to the appropriate Appendix. For more detailed information on the Issues and Resolutions, refer to the appropriate Test Case Results section. The tables are organized by the areas of evaluation defined above. Installation Tests Test Objective Test Method Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution Identify potential security vulnerabilities with default installation options. Install the FrontPage Server Extensions and evaluate all configuration options and results. Undesired administrative privileges could be granted; Numerous undesired Windows NT groups could be created; The web could be configured to execute in an insecure fashion. Careful installation procedures can mitigate all of these risks. Identify potential security vulnerabilities with activation of the remote administration forms. Activate the remote administration forms and evaluate configuration options and results. The obscurity of the administration website could be reduced. Careful installation procedures can mitigate all of these risks. Configuration Tests Test Objective Test Method Observation/Issue Resolution Test Objective Test Method To determine if individuals have the ability to acknowledge the existence of FrontPage extended webs to which they have not been granted permission. Use a web browser to attempt to remotely discover subwebs. Individuals are able to confirm the existence of any subweb off the root and any subweb directly below an anonymously browseable subweb. Special considerations must be made before configuring the website. To determine if an individual can browse, author, or administer a FrontPage extended web if that individual is not granted explicit permission. Use a web browser to attempt to directly access private content; Use the FrontPage client to attempt to open private subwebs; Use the FrontPage client to attempt to publish to private subwebs; Use a web browser to attempt to access the remote administration forms; Use the FrontPage client to attempt to administer FrontPage security; Use the remote command line utilities to attempt to perform FrontPage administration. 2/12/16 Page 11 Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution Under certain circumstances, anonymous users will have access to portions of the website which were configured securely. Ensure that security is applied as each subweb is created, and not after the fact. To determine what information an intruder can obtain about a website if it is running FrontPage Server Extensions. Use a web browser, the FrontPage client, and the command line to attempt to remotely access all FrontPage related files; Use directory navigation shortcuts to attempt to access files outside of the specified virtual directory; Use a custom form to execute FrontPage RPC methods against the Server Extensions. Information such as file locations, server type, and operating system type can be retrieved by any individual with access to the website. A hierarchical segregation of duties can be created, but a strict one cannot. These issues have no mitigating factors. To determine if FrontPage Administrators possess the capability to enumerate a list of system users. Use the configuration features to grant users FrontPage functions. By default, FrontPage Administrators can enumerate all users from the Windows NT user account database. Make specific modifications to the Windows NT registry and follow guidelines for creating new FrontPage users and groups. To determine if an Author can use scripts and other executable files to gather information from or gain access to the system. Use the FrontPage client to attempt to upload scripts and executable programs; Use a web browser to attempt to remotely execute scripts and programs on the server. Although not by default, changes can be made to system configuration files that would allow Authors to upload files (such as a Trojan horse) into an executable directory. Ensure that Authors do not have the ability to upload into executable directories by setting specific parameters in the appropriate configuration files. 2/12/16 Page 12 Penetration Tests Test Objective Test Method Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution To determine what ports are opened or listening on a FrontPage extended website. Run port scanning software against the server while idle; Run port scanning software against the server while during browsing activity; Run port scanning software against the server during authoring activity; Run port scanning software against the server during administration activity. The FrontPage Server Extensions do not necessitate the opening of any ports other than those necessary for HTTP (80) and the administration forms (User defined). None Needed. To determine if a denial of service can be perpetrated by locking out browsing, authoring, and administrative accounts. Attempt repeated incorrect logons for a user with Browse only rights to a subweb from a web browser, the FrontPage client, and the remote command line utilities; Attempt repeated incorrect logons for a user with Author rights to a subweb from a web browser, the FrontPage client, and the remote command line utilities; Attempt repeated incorrect logons for a user with Administrator rights to a subweb from a web browser, the FrontPage client, and the remote command line utilities; Attempt repeated incorrect logons for a the IUSR_MachineName account from a web browser, the FrontPage client, and the remote command line utilities. On Windows NT, users will be locked out in accordance with the system account lockout policy. Enforce an account lockout and ensure proper monitoring exists to reduce the risk of a denial of service attack. 2/12/16 Page 13 Data Capture Tests Test Objective Test Method Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution Test Objective Test Method Observation/Issue Resolution To Determine if passwords are passed in clear text during the authentication process. Use a sniffing tool to capture all network data during the authentication process from a web browser to the FrontPage Server Extensions; Use a sniffing tool to capture all network data during the authentication process from the FrontPage client to the FrontPage Server Extensions; Use a sniffing tool to capture all network data during the authentication process from the remote command line utilities to the FrontPage Server Extensions. Under certain authentication schemes, passwords will be transmitted in easily decoded form. Ensure that the appropriate method of authentication is used. To determine if confidential information is passed in clear text during administration. Use a sniffing tool to capture all network data during remote administration from a web browser to FrontPage extended web In addition to user and website information, FrontPage specific configuration information may be passed in clear text during authoring. Ensure that SSL is used wherever possible. To determine if confidential information is passed in clear text during authoring. User a sniffing tool to capture all network data while performing authoring actions from the FrontPage client. In addition to the contents of web pages, FrontPage specific configuration information may be passed in clear text during authoring. Ensure that SSL is used wherever possible. 2/12/16 Page 14 Conclusion A total of twenty-four test cases were executed on Windows NT and sixteen on UNIX, in the four areas described above, during the testing of the Microsoft FrontPage Server Extensions. In summary, the results of the following test cases show that the Microsoft FrontPage Server Extensions, when properly installed, configured, maintained, and monitored, can provide a reasonable and practical level of security for developing and maintaining an electronic Internet presence. 2/12/16 Page 15 Windows NT Test Case Results Issue There are several options to consider during the installation process which affect the security of the Server Extensions. Depending on the choice of a web site administrator, undesired administrative capabilities of the Windows NT server could be granted. The installation may create unnecessary local groups. Description It is not necessary for the administrator of the web site to be a member of the local Administrators group. By allowing the installation to create groups, there may be groups created that are not needed. If it is understood that these groups are not needed, they may not be audited and thus an individual may be inadvertently added to the group. Additionally, for large implementation such as ISPs with thousands of individually administered subwebs, an unnecessarily large user account database could be created. This could potentially consume memory and disk space as well as processor cycles and bandwidth during replication between domain controllers. How To Address This Issue A group should be created before installation, named “ComputerName Admins”, to which the administrator of the web site will be added. During installation, this group should be designated the group to administer the web site. After creation of the local groups, any group to which members are not added for the purposes of browsing, authoring, or administering the web site, should be deleted. Issue Literally following the documentation in the Server Extensions Resource Kit (SERK) concerning the activation of the remote administration forms may reduce the obscurity of the HTML administration forms website. This could give an intruder necessary information for launching an attack against your web site. 2/12/16 Page 16 Description The documentation in the SERK suggests using a nonstandard port for the forms, such as 8234. How To Address This Issue During installation of the HTML Remote Administration Forms port 8234 should not be selected, rather an obscure non-standard port should be chosen. Additionally, as evidenced in later tests, SSL should be used to ensure the confidentiality and integrity of all transmitted data. Issue Individuals are able to confirm the existence of any subweb off the root and any subweb directly below an anonymously browseable subweb. The name of a directory could potentially provide a starting point of attack for an intruder. Description By enumerating all directories directly below the root, an intruder could attempt to access (read, write, or publish to) these directories. If any directories are inadequately secured, modifications to the web site could occur or sensitive information could be obtained. How To Address This Issue The FrontPage Server Extensions allow web sites to be configured in a manner that will limit the availability of directory names. If all sensitive data is created in a structure below a private subweb, directory names cannot be revealed without proper authentication. Issue Under certain circumstances, the IUSR_computername account may have read permissions to subwebs that “Use same permissions as parent web” and where “only registered users have browse access” to the parent web. Description In this instance, the content of the subweb will be available to anyone who connects anonymously when the full path to a web page is entered. Because this subweb inherited permissions from a restricted subweb, its content should also be restricted. This event will occur 2/12/16 Page 17 when the sub-subweb is created before all proper restrictions have been emplaced on the parent web. How To Address This Issue When creating private subwebs which are to have restricted access, ensure that appropriate settings are configured (i.e., “allow anonymous access” is disabled, the Everyone group is not granted explicit access, and that the IUSR_computername account is not granted explicit access) before creating any subsequent subwebs. Additionally, review NTFS permissions on all directories in the web to ensure that no undesired permissions have been set. Issue The functionality of the FrontPage Server extensions is such that each FrontPage Administrator can administer, author and browse; each Author can author and browse; and each Browser can only browse. However, it may be undesirable for Administrators to edit the content of the web site. Description With a proper segregation of duties, a web site Administrator would perform only administration functions while an Author would perform only authoring functions. Under the permissions scheme inherently implemented by the FrontPage Server Extensions, Administrators will be able to alter the content of the web site. How To Address This Issue If it is undesirable to allow Administrators of a web to author content for that web, it is necessary to have proper policies and controls in place. Audit logs should be generated and routinely reviewed to ensure that users access is commensurate with their responsibility. Issue If anonymous access is allowed to a web site configured with the FrontPage Server Extensions, an intruder can use a variety of methods to gain information about the system. This information could potentially provide a starting point for an attack. 2/12/16 Page 18 Description Individuals can determine information such as the following: The type of operating system (due to vti_inf.html); Location of the files that handle Remote Procedure Calls (RPC), Authoring, and Administration (due to vti_inf.html); The version of FrontPage Server Extensions running (due to RPC methods); HTTPD version (due to RPC methods); Web Server type (due to RPC methods); The names of all subwebs directly under any anonymously browseable subweb (due to RPC methods); If the site has a search bot (due to RPC methods); Valid file extensions (due to RPC methods); How To Address This Issue Because the _vti_inf.html file is located in the root of the web site and must be readable by all, there is no way to restrict the information that it supplies. Also, because the Server Version and List Services RPC methods require only browse access, any individual with browse access can execute them. Therefore, any root web that is anonymously accessible will yield this information. To minimize the risk of the misuse of any of this information, several steps should be taken. Appropriate security updates and patches to the web server should be regression tested and applied to prevent known vulnerabilities from being exploited. When Microsoft releases such updates, they are detailed and available for download at www.microsoft.com/security. The web site should be configured with subwebs in a secure manner as described herein. Issue By default, FrontPage Administrators can enumerate all users from the Windows NT user account database. User names can potentially be used as a starting point for an attack on a system. 2/12/16 Page 19 Description By obtaining a user name, a FrontPage Administrator can begin a brute force guessing attack on those accounts’ passwords with the intent to gain unauthorized system access. Since a FrontPage Administrator is granted only those rights necessary for his/her responsibilities, he/she should be prevented from accessing the system as another user. How To Address This Issue This is not a major security risk because it will be very difficult to gain unauthorized system access given only a list of usernames. In addition, there are several other ways to enumerate users that are not caused by the installation of FrontPage Server Extensions. However, if business requirements dictate this necessity, the FrontPage Server Extensions provide a way to limit the enumeration of usernames. To restrict this list, the RestrictIISUsersAndGroups registry key needs to be modified as per the instructions in the Recommendations Section. Issue By default, Authors cannot upload files into executable directories. But, changes can be made to the registry that would allow them to. If an Author uploaded files (such as a Trojan horse) into an executable directory and then used the browser to run the program on the server, they could potentially gain full control of the system. Description As evidenced in the test in the Appendix, Authors could potentially upload programs that would allow them to gain access to the system or change system settings. How To Address This Issue Ensure that Authors do not have the ability to upload into executable directories by setting the NoExecutableCgiUpload registry value and key permissions as per the Baseline Security Configuration section. 2/12/16 Page 20 Issue The ports that are open and listening on a web server provide a network entry point to the machine. External commands can be sent to these ports and potentially elicit a response or perform an action. Description When the remote administration forms are installed and activated, they require a port to be opened. However, this port must be specified by the user and at no point, are any other ports opened, that are not already open on IIS, such as those necessary for HTTP (port 80) and SSL (possibly 443). No changes will be necessary to firewall or proxy server rules for the FrontPage Server Extensions to function properly. How To Address This Issue Ensure that all ports that are not necessary for the web server to function are closed. (See Baseline Security Configuration) Issue Accounts will be locked out in accordance with the Windows NT account policy. A denial of service for the entire web site could be perpetrated if the IUSR_ComputerName account was locked out. Additionally, denials of service could occur for Author and Administrator accounts. Description While account lockout is enabled, if an intruder attempts excessive failed logins to a web server via the IUSR_ComputerName, Browser, Author, or Administrator account, they would become locked out and no one could anonymously connect, browse, author, or administer the web site until those accounts are unlocked. How To Address This Issue If the IUSR_computername account is used for anonymous connections, or user account lockout status is not monitored, then account lockout should not be used because a denial of service could occur. If account lockout is used due to a specific business requirement, then audit logs and account status for all FrontPage related accounts should be monitored regularly. It should be 2/12/16 Page 21 noted that the FrontPage Server Extensions do not cause any of this behavior; this is part of the Windows NT functionality. Issue When using the Basic Authentication scheme, passwords are passed in uuencoded text. Description If an individual on the Internet captures a password and uudecodes it, he/she will obtain the actual password to the FrontPage Server Extensions and may be able to compromise the server. How To Address This Issue If you will not be accessing the FrontPage Server Extensions through a firewall or proxy server, use Windows NT Challenge/Response authentication as described in the Baseline Security Configuration section, under the heading FrontPage Server Extensions Configuration. When Basic Authentication is necessary, FrontPage supports the use of Secure Sockets Layer (SSL). SSL is a protocol that provides communications privacy, authentication, and message integrity for a TCP/IP connection. SSL transmits passwords in an encrypted form that is unreadable by normal means. By using this protocol, clients and servers can communicate in a way that prevents eavesdropping, tampering, or message forgery. Require SSL for the HTML administration forms. Additionally, it is recommended to require SSL for all authoring actions and for browse access to any private and sensitive portions of the web site. Issue Confidential information contained within web pages that are to be published to restricted portions of a web site are passed in clear text from the client to the server. Additionally, information that the FrontPage client uses for communication with the FrontPage Server Extensions is passed in clear text. A third party sniffing the web traffic could capture information passed in clear text from the client to the server. Description Information that is to reside in password protected directories and FrontPage proprietary directories, is considered confidential. As this data is passed in clear text across the network, a third party could potentially run a network data capture (sniffer) program and capture this data. 2/12/16 Page 22 How To Address This Issue To ensure that no unauthorized individuals can intercept and interpret confidential information, and for maximum security use the Secure Sockets Layer (SSL) protocol for all authoring and remote administration. 2/12/16 Page 23 UNIX Test Case Results Issue During initial installation, a group must be chosen as the context under which the FrontPage Server Extensions will execute. Description Without proper consideration, a group may be chosen which allows excessive access rights to users of the web. How To Address This Issue During installation, configure the FrontPage Server Extensions to execute under the same user and group contexts as your web server. Issue Literally following the documentation in the Server Extensions Resource Kit (SERK) concerning the activation of the remote administration forms may reduce the obscurity of the HTML administration forms website. This could give an intruder necessary information for launching an attack against your web site. Description The documentation in the SERK suggests using a nonstandard port for the forms, such as 8234. How To Address This Issue During installation of the HTML Remote Administration Forms port 8234 should not be selected, rather an obscure non-standard port should be chosen. Additionally, as evidenced in later tests, SSL should be used to ensure the confidentiality and integrity of all transmitted data. Issue Users may be able to read from and/or write to content in webs which they do not own. 2/12/16 Page 24 Description Because the Web server runs under a UNIX account, any process it runs and any files that it accesses must be available under the permissions of the same UNIX account. This can cause a security problem in a multihosted environment, because one user's CGI script could read files in another user's content area on the server. This problem is compounded if write access is supported, as it is with the FrontPage client. How To Address This Issue Use the Fpsrvadm utility, to change the execute permissions of the server extensions executable files to SUID/SGID (Set User ID/Set Group ID). This forces the server extensions to be executed with the file-system permissions of the owner of shtml.exe, author.exe, and admin.exe. When suitable permissions for each customer's content area are applied, the FrontPage Server Extensions (and any other CGI scripts) for one customer are prevented from writing to the content areas of other users. By default, a 022 umask is used when the server extensions are installed or chowned. To set a custom umask, you must edit and recompile the FrontPage Server Extensions stub executable file, /usr/local/frontpage/version4.0/srcs/fp.suid.c. Issue Users of the FrontPage client may not be able to create new subwebs, and users with telnet and/or ftp access to the web server could modify content in a web they do not own. Description The FrontPage Server Extensions need to modify the Web server's configuration file to mark directories containing the server extensions as executable. Therefore, there must be stub executable files in each subweb. Additionally, the web server must be able to read from and write to each subweb. How To Address This Issue FrontPage supplies an optional patch to overcome this limitation. With this patch, copies of the FrontPage Server Extensions executable files are stored in one centralized location. This makes it unnecessary to mark directories in each web as executable, and makes it possible for the FrontPage client to create new FrontPage-extended webs without modifying server configuration files. The patch to the Apache Web server intercepts each call that the FrontPage client makes to 2/12/16 Page 25 the server extensions executable files. It then performs security checks, sets user ID to the owner of the Web site (thus requiring SUID/SGID operation of the server extensions and the web content), and invokes a centralized copy of the server extensions executable files. Because of the nature of the patch, Microsoft makes the source code of the FrontPage Apache module and the fpexe stub program available for review. It is therefore possible to modify the source of the patch and recompile it to suit individual needs. Issue Individuals are able to confirm the existence of any subweb off the root and any subweb directly below an anonymously browseable subweb. The name of a directory could potentially provide a starting point of attack for an intruder. Description By enumerating all directories directly below the root, an intruder could attempt to access (read, write, or publish to) these directories. If any directories are inadequately secured, modifications to the web site could occur or sensitive information could be obtained. How To Address This Issue The FrontPage Server Extensions allow web sites to be configured in a manner that will limit the availability of directory names. If all sensitive data is created in a structure below a Private subweb (a subweb with restricted [no anonymous] access), directory names cannot be revealed without proper authentication. Issue The functionality of the FrontPage Server extensions is such that each FrontPage Administrator can administer, author and browse; each Author can author and browse; and each Browser can only browse. However, it may be undesirable for Administrators to edit the content of the web site. Description With a proper segregation of duties, a web site Administrator would perform only administration functions while an Author would perform only authoring functions. Under the permissions 2/12/16 Page 26 scheme inherently implemented by the FrontPage Server Extensions, Administrators will be able to alter the content of the web site. How To Address This Issue If it is undesirable to allow Administrators of a web to author content for that web, it is necessary to have proper policies and controls in place. Audit logs should be generated and routinely reviewed to ensure that users access is commensurate with their responsibility. Issue If anonymous access is allowed to a web site configured with the FrontPage Server Extensions, an intruder can use a variety of methods to gain information about the system. This information could potentially provide a starting point for an attack. Description Individuals can determine information such as the following: The type of operating system (due to vti_inf.html); Location of the files that handle Remote Procedure Calls (RPC), Authoring, and Administration (due to vti_inf.html); The version of FrontPage Server Extensions running (due to RPC methods); HTTPD version (due to RPC methods); Web Server type (due to RPC methods); The names of all directories directly under the root (due to RPC methods); If the site has a search bot (due to RPC methods); Valid file extensions (due to RPC methods); How To Address This Issue Because the _vti_inf.html file is located in the root of the web site and must be readable by all, there is no way to restrict the information that it supplies. Also, because the Server Version and List Services RPC methods require only browse access, any individual with browse access can execute them. Therefore, any root web that is anonymously accessible will yield this information. To minimize the risk of the misuse of any of this information, several steps should be taken. Appropriate security updates and patches to the web server should be regression tested and applied to prevent known vulnerabilities from being exploited. 2/12/16 Page 27 The web site should be configured with subwebs in a secure manner as described herein. Issue By default, Authors cannot upload files into executable directories. But, changes can be made to the frontpage.cnf configuration file that would allow them to. If an Author uploaded files into an executable directory and then used the browser to run the program on the server, they could potentially gain full control of the system. Description As evidenced in the test in the Appendix, Authors could potentially upload programs which would allow them to gain access to the system or change system settings. How To Address This Issue Ensure that Authors do not have the ability to upload into executable directories. Further ensure that the frontpage.cnf configuration file is properly secured so that Authors cannot clear the value of the variable NoExecutableCgiUpload. Refer to the Baseline Security Configuration section for appropriate configuration file and File System permissions. Issue The ports that are open and listening on a web server provide a network entry point to the machine. External commands can be sent to these ports and potentially elicit a response or perform an action. Description When the remote administration forms are installed and activated, they require a port to be opened. However, this port must be specified by the user and at no point, are any other ports opened, that are not already open on Apache, such as those necessary for HTTP (port 80) and SSL (possibly 443). No changes will be necessary to firewall or proxy server rules for the FrontPage Server Extensions to function properly. How To Address This Issue Ensure that all ports which are not necessary for the function of the web server are closed. (See Baseline Security Configuration) 2/12/16 Page 28 Issue If an intruder compromises a FrontPage Server Extensions password, or password file, it maybe possible for that person to gain access to confidential data or compromise the system. Description Because there is no account lockout feature inherent to the Apache Web Server or FrontPage Server Extensions Accounts, it is necessary to ensure that strong passwords are used. How To Address This Issue Set the entry ComplexPasswords in the frontpage.cnf file to a non-zero value. This configures the FrontPage Server Extensions to require complex passwords for FrontPage Administrator and Authoring accounts. When set, the following rules apply to passwords: 1. The user name cannot be embedded in the password. 2. The password must contain at least one alphabetic character. 3. The password must have more than 8 characters. Issue When using the Basic Authentication scheme, passwords are passed in uuencoded text. Description If an individual on the Internet captures a password and uudecodes it, he/she will obtain the actual password to the FrontPage Server Extensions and may be able to compromise the server. How To Address This Issue FrontPage supports the use of Secure Sockets Layer (SSL). SSL is a protocol that provides communications privacy, authentication, and message integrity for a TCP/IP connection. SSL transmits passwords in an encrypted form that is unreadable by normal means. By using this protocol, clients and servers can communicate in a way that prevents eavesdropping, tampering, or message forgery. Require SSL for the HTML administration forms. Additionally, it is recommended to require SSL for all authoring actions and for browse access to any private and sensitive portions of the web site. 2/12/16 Page 29 Issue Confidential information contained within web pages that are to be published to restricted portions of a web site are passed in clear text from the client to the server. Additionally, information that the FrontPage client uses for communication with the FrontPage Server Extensions is passed in clear text. A third party sniffing the web traffic could capture information passed in clear text from the client to the server. Description Information that is to reside in password protected directories and FrontPage proprietary directories, is considered confidential. As this data is passed in clear text across the network, a third party could potentially run a data capturing (sniffer) program and capture this data. How To Address This Issue Use the Secure Sockets Layer (SSL) protocol for all authoring and remote administration so that no unauthorized individuals can intercept and interpret confidential information, . 2/12/16 Page 30 Baseline Security Configuration PricewaterhouseCoopers recognizes the hectic and fast-paced life of the information technologist and security administrator. We understand that sometimes it is hard to sift through all the material in a white paper. Therefore, we have combined some important Windows NT and UNIX security control features, FrontPage Server Extensions’ features, and our recommended settings into the following matrix to be used as a baseline security configuration and as a quick reference. Security administrators should use this section as a guide when building their Windows NT security environment. Windows NT The following section only applies to Windows NT 4.0 with Service Pack 3. User Setup Ensure that all accounts have passwords or are disabled. The built-in user accounts, Administrator and Guest, should be renamed to obscure values for maximum security. The Guest account should be disabled and never used. Account Policies should be set so that complex passwords must be used and changed periodically, however account lockout should be used with caution as it could potentially create a denial of service to users. This is because the IUSR_computername account is used for anonymous authentication but could be locked out if incorrect passwords are guessed too many times. If IUSR_computername is locked out, this would prevent anonymous browsing. However, not using an account lockout allows an attacker to rapidly brute force guess passwords. If an administrator’s password is compromised, the system will be as well. It is a double-edged sword and careful consideration should be taken when determining your account lockout policy. The best answer is to ensure complex and strong passwords are always used. 2/12/16 Page 31 Directory Permissions Windows NT System Directories Directory \ (Root on an NTFS volume) \WINNT\ \WINNT\SYSTEM32 \WINNT\SYSTEM32\CONFIG \WINNT\SYSTEM32\DRIVERS \WINNT\SYSTEM32\SPOOL \WINNT\SYSTEM32\REPL \WINNT\SYSTEM32\REPL\IMPORT \WINNT\SYSTEM32\REPL\EXPORT \WINNT\REPAIR Recommended Permissions Administrators Server Operators Everyone CREATOR OWNER SYSTEM Administrators Server Operators Everyone CREATOR OWNER SYSTEM Administrators Server Operators Everyone CREATOR OWNER SYSTEM Administrators Everyone CREATOR OWNER SYSTEM Administrators Server Operators Everyone CREATOR OWNER SYSTEM Administrators Server Operators Print Operators Everyone CREATOR OWNER SYSTEM Administrators Server Operators Everyone CREATOR OWNER SYSTEM Administrators Server Operators Everyone CREATOR OWNER Replicator NETWORK SYSTEM Administrators Server Operators Everyone CREATOR OWNER Replicator SYSTEM Administrators 2/12/16 Full Control Change Read Full Control Full Control Full Control Change Read Full Control Full Control Full Control Change Read Full Control Full Control Full Control List Full Control Full Control Full Control Change Read Full Control Full Control Full Control Change Full Control Read Full Control Full Control Full Control Change Read Full Control Full Control Full Control Change Read Full Control Change No Access Full Control Full Control Change Read Full Control Read Full Control Full Control Page 32 FrontPage Directories Directory \Program Files\Common Files\Microsoft Shared\Web Server Extensions\ (and subdirectories) \Program Files\Common Files\Microsoft Shared\Web Server Extensions\40\Admisapi (and subdirectories) Recommended Permissions Administrators SYSTEM Everyone Administrators SYSTEM Computername Admins Full Control Full Control Read Full Control Read Read Web site Directories From the configuration of a fictional web site below, the permissions for any desired situation should be easily extrapolated. The machine name is FP_Server Group Name FP_Server Admins FP_Server Authors FP_Server Browsers Privatesite Admins Privatesite Authors Privatesite Browsers Function Administer the Root Web and public subwebs Author content of Root Web and public subwebs Browse public portions of the web site Administer the Private portions of the web site Author the Private portions of the web site Browse the private portions of the web site Members RootAdmin RootAuthor IUSR_FP_Server PrivateAdmin PrivateAuthor PrivateBrowser Note permissions are as follows: Read, Write, Execute, Delete, Change Permissions, Take Ownership (R,W,X,D,P,O) Directory Root Description Root Web, Anonymously Accessible PublicSite Subweb of Root, Inherit Permissions from parent, Anonymously Accessible Subweb of Root, Uses Unique Permissions, Browsing requires authentication PrivateSite PrivateSub Subweb of PrivateSite, Inherit Permissions from parent, Browsing requires authentication 2/12/16 Recommended Permissions Administrators Full Control SYSTEM Full Control FP_Server Admins RWXDP FP_Server Authors RWXD FP_Server Browsers RX Same as above Administrators SYSTEM PrivateSite Admins PrivateSite Authors PrivateSite Browsers Same as above Full Control Full Control RWXDP RWXD RX Page 33 Configuration Files Registry Permissions Ensure that the permissions on the following registry keys are set as indicated: Other Registry Keys Recommended Permissions HKLM\System\CurrentControlSet\Control\ SecurePipeServers\winreg Add this key to prevent remote registry editing Administrators Full Control HKLM\SOFTWARE\Microsoft\Windows\ CurrentVersion\Run And all files listed in the Run key should have the Everyone: Read permission. HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce Administrator Full Control System Full Control Everyone Read Administrator Full Control System Full Control Everyone Read Administrator Full Control System Full Control Everyone Read Administrator Full Control System Full Control Everyone Read Administrator Full Control System Full Control Everyone Read This key must be owned by FP_Server Admins hkey_local_machine\SOFTWARE\Microsoft\Shared Server Extensions Tools\Web hkey_local_machine\SOFTWARE\Microsoft\Shared Server Extensions\All Ports Tools\Web hkey_local_machine\SOFTWARE\Microsoft\Shared Server Extensions\Ports Tools\Web hkey_local_machine\SOFTWARE\Microsoft\Shared Tools\Web Server Extensions\Ports\Port /LM/W3SVC/InstanceNumber Administrator System FP_Server Admins Everyone Other Registry Keys HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT \RPC (and all subkeys) \WindowsNT\CurrentVersion\ \WindowsNT\CurrentVersion\AeDebug \WindowsNT\CurrentVersion\Compatibility \WindowsNT\CurrentVersion\Drivers \WindowsNT\CurrentVersion\Embedding \WindowsNT\CurrentVersion\Fonts \WindowsNT\CurrentVersion\FontSubstitutes \WindowsNT\CurrentVersion\GRE_Initialize \WindowsNT\CurrentVersion\MCI \WindowsNT\CurrentVersion\MCI Extensions \WindowsNT\CurrentVersion\Port (and all subkeys) \WindowsNT\CurrentVersion\ProfileList \WindowsNT\CurrentVersion\ Windows3.1MigrationStatus \WindowsNT\CurrentVersion\WOW (and all subkeys) HKEY_CLASSES_ROOT (and all subkeys) 2/12/16 Full Control Full Control Full Control Read Recommended Permissions Administrator Full Control System Full Control Everyone Read Administrator System Everyone Full Control Full Control Read Page 34 Registry Values specific to Windows NT HKLM\SOFTWARE\Microsoft\WindowsNT\ CurrentVersion\Winlogon\ 0 Shut Down Without Logging On ShutdownWithoutLogon 1 Disable Floppy Drive AllocateFloppies 1 Disable CD-ROM AllocateCDROMS 0 Automatic Logon AutoAdminLogon 1 Do Not Display Last User to Log In DontDisplayLastUserName “Legal Notice” “Warning” or acceptable heading Legal Notice Caption LegalNoticeCaption or other A message approved by your legal department Legal Notice LegalNoticeText HKLM\SYSTEM\CurrentControlSet\Control\LSA\ 0 (unless necessary organizational requirements) Enable auditing of rights FullPrivilegeAuditing for 0 Schedule Service SubmitControl HKLM\SYSTEM\CurrentControlSet\Services\ 0 Disable Autorun CDROM\Autorun 2/12/16 Page 35 Registry Values specific to FrontPage Server Extensions Ensure that the following registry value names are present and set with the corresponding values. Hkey_local_machine\SOFTWARE\Microsoft\Shared Tools\Web Server Extensions\All Ports AccessControl 1 (Default) AllowExecutableScripts 0 (Default) ClientVerCuttoff vti_clientvercutoff:SX|4.0.2.0000:This web can only be edited using FrontPage 2000. Logging 1 NoExecutableCgiUpload 1 (Default) NoMarkScriptable 1 NoSaveResultsPipeTo 1 (Default) NoSaveResultsToAbsoluteFile 1 (Default) PrivateBrowsable 0 (Default) RestrictIISUsersAndGroups Value Entry: 1 Note: In User Manager, add the group below: FP_[InstanceNumber][_Directories][_Subweb] RequireSSL Then, add all the users which should be available to the FrontPage administrator, to this group. enabled (Only set this value if SSL is employed, recommended) 2/12/16 Page 36 Services Service Name Alerter Computer Browser Event Log FTP Publishing Service Messenger Network DDE Network DDE DSDM NT LM Security Support Provider Remote Procedure (RPC) Locator Call Remote Procedure (RPC) Service Call Schedule Server Spooler UPS Workstation World Wide Publishing Service Web Description Notifies users and computers of the administrative alerts that occur. Maintains an up-to-date list of computers and provides this list to applications when requested. Records system. Security, and application events to be viewed in Event Viewer. Provides File Transfer Protocol functionality Sends and receives messages sent by the administrator or the alerter service Provides a network transport as well as security for DDE conversations Manages the DDE conversations. Provides Windows NT security to RPC applications that use transports other than named pipes. Allows distributed applications to use the Microsoft RPC service and manages the RPC Name Service database. The RPC subsystem for Windows NT. It includes the endpoint mapper and other related services. Must be running if tasks are scheduled with the AT command. Provides RPC support, file and print, and named piping sharing by using SMB services. Provides print spooling services. Manages an uninterruptible power supply. Provides network connections and communications. Provides services to publish web site content on the machine through IIS. 2/12/16 Recommended Setting Running if sending alerts Running Running Stopped Running if Alerter service is running Stopped Stopped Running Stopped Running Running if using scheduler. Use Scheduler account. Stopped Running Running if using UPS Running Running Page 37 User Rights Standard User Rights User Right Access this computer from network Add workstations and member servers to domain Back up files and directories Change the system time Force shutdown from a remote system Log on locally Manage auditing and security log Restore files and directories Shut down the system Take ownership of files or other objects Recommended Group Assignments No one No one Backup Operators Administrators No one Administrators, IUSR_machinename, IWAM_machinename Auditors (must be created) Backup Operators Administrators Administrators Advanced User Rights User Right Act as part of the operating system Bypass traverse checking Create a pagefile Create a token object Create permanent shared objects Debug programs Generate security audits Increase quotas Increase scheduling priority Load and unload device drivers Lock pages in memory Log on as a batch job Log on as a service Modify firmware environment variables Profile single process Profile system performance Replace a process level token Recommended Group Assignments No one Everyone Administrators No one No one Administrators No one Administrators Administrators Administrators No one No one No one Administrators Administrators Administrators No one 2/12/16 Page 38 Event Log On Windows NT servers, Event Log entries are generated when an individual tries to directly access SHTML.DLL through a browser. Due to this, the settings and actions of the Event Log need to be considered. The Event Log should be configured as follows: Overwrite Policy Setting Maximum Log Size Security Log Overwrite events older than 14 days 4096 K Application Log Overwrite events necessary 2048 K 2/12/16 as System Log Overwrite events than 14 days 2048 K older Page 39 UNIX The following section only applies to the FrontPage Server Extensions configuration on Solaris 2.6. User Setup Ensure that all accounts have passwords or are locked out by reviewing the /etc/shadow file. If a user is to be locked out, replace the encrypted password with an asterisk (*). System Settings and Services Review the /etc/hosts.equiv file. Verify that there are no entries in this file. Search for any rhosts files on the system and remove them. Review the /etc/inetd.conf file. Comment out all unnecessary services: i.e. telnet, chargen, rlogin, rsh, rcp, tftp, finger and ftp. Install a replacement such as SSH for telnet and ftp which will provide encrypted login sessions where no data will pass in clear-text. Review what network daemons are running on the system. Document those that are unknown and shut down all that are unneeded. If it is necessary to enable the FTP service, make sure only authorized users can FTP to the server. All users that are not authorized, such as root, bin, uucp, smtp and sys should be added to the /etc/ftpusers file. Disallow remote logins directly to the root account by ensuring that the CONSOLE=/dev/console line has been uncommented from the /etc/default/login file. Ensure that all system activities are being logged through syslog, preferably to a secure logging host with the command *.emerg;*.alert;*.crit;*.err;*.warning;*.notice;*.info;*debug /var/adm/sysmessages 2/12/16 Page 40 Directory Permissions System Files and Directories File or Directory / /bin/ /etc/ /etc/default/ /etc/inet/ /etc/inet/hosts /etc/inet/inetd.conf /etc/inet/services /etc/passwd /etc/shadow /etc/syslog.conf /sbin/ /usr/bin/ /usr/bin/login /usr/bin/passwd /usr/bin/su /var/adm/ Recommended Permissions drwxr-xr-x drwxrwxr-x drwxr-xr-x drwxrwxr-x drwxr-xr-x -r--r--r--r--r-----r--r--r--rw-r--r--r--------r-------drwxrwxr-x drwxrwxr-x -r-sr-xr-x ---x--x--x -r-sr-xr-x drwxrwxr-x Owner root root root root root root root root root root root root root root root root root Recommended Permissions drwxrwxr-x dr-xr-xr-x dr-xr-xr-x Owner Bin Bin Bin Recommended Permissions drwxr-xr-x drwxr-xr-x drwxr-xr-x drwxr-xr-x drwxr-xr-x drwxr-xr-x drwxr-xr-x drwxr-xr-x Owner Nobody Nobody Nobody Nobody Nobody Nobody Nobody Nobody FrontPage Directories Directory /usr/local/frontpage/version4.0/ /usr/local/frontpage/version4.0/admin/ /usr/local/frontpage/version4.0/admin/scripts/ Web site Directories Directory /usr/local/apache/share/htdocs/ /usr/local/apache/share/htdocs/images/ /usr/local/apache/share/htdocs/_vti_txt/ /usr/local/apache/share/htdocs/_vti_log/ /usr/local/apache/share/htdocs/_private/ /usr/local/apache/share/htdocs/_vti_bin/ /usr/local/apache/share/htdocs/_vti_cnf/ /usr/local/apache/share/htdocs/_vti_pvt/ 2/12/16 Page 41 Configuration Files frontpage.cnf Ensure that the following entries are present and set with the corresponding values. /usr/local/frontpage/version4.0/frontpage.cnf AccessControl 1 (Default) ClientVerCuttoff vti_clientvercutoff:SX|4.0.2.0000:This web can only be edited using FrontPage 2000. ComplexPasswords 1 Logging 1 NoExecutableCgiUpload 1 (Default) NoSaveResultsPipeTo 1 (Default) NoSaveResultsToAbsoluteFile 1 (Default) RequireSSL enabled (Only set this value if SSL is employed, recommended) service.grp From the configuration of a fictional web site below, the permissions for any desired situation should be easily extrapolated. These are settings for the _vti_pvt/service.grp file referenced by the .htaccess file in each subweb. User Name Administrator RootAuthor Anonymous PrivateAdmin PrivateAuthor PrivateBrowser Function Administer the Root Web and public subwebs Author content of Root Web and public subwebs Browse public portions of the web site Administer the Private portions of the web site Author the Private portions of the web site Browse the private portions of the web site Directory Root Description Root Web, Anonymously Accessible PublicSite Subweb of Root, Inherit Permissions from parent, Anonymously Accessible Subweb of Root, Uses Unique Permissions, Browsing requires authentication PrivateSite PrivateSub Subweb of PrivateSite, Inherit Permissions from parent, Browsing requires authentication PublicSub Subweb of PublicSite Inherit Permissions from parent, Anonymously Accessible 2/12/16 Recommended Permissions Administrators Administrator Authors RootAuthor Browsers None Administrators None Authors None Browsers None Administrators Administrator PrivateAdmin Authors PrivateAuthor Browsers None Administrators Administrator PrivateSubAdmin Authors PrivateSubAuthor Browsers None Administrators None Authors None Browsers None Page 42 FrontPage Server Extensions Feature Auditablility - The ability to gather information about the use of the Microsoft FrontPage Server Extensions is important to overall system security as the knowledge of what users are accessing and what information is being moved over the network helps identify problems. Without such detection controls, the network administrator knows nothing about the activity of the FrontPage Server Extensions . Weak or nonexistent monitoring controls increase the risk associated with detecting attacks on your network or FrontPage servers. In addition to the logging provided by Internet Information Server or Apache, the Microsoft FrontPage Server Extensions enable administrators to activate activity and security logging functionality. Recommendation Logging – There are two levels of logging available. The first records visits and can be set per sub-web. The second covers authoring actions; the system records the time an author's action was performed, the author's user name, the web name, the remote host, and per-operation data, and stores this information in a log file named _vti_log/Author.log, in the root web. Both forms of logging should be enabled and the log files generated should be regularly reviewed. Feature Authentication - The Microsoft FrontPage Server Extensions offers three kinds of user level authentication which can be set on a per-subweb basis. Basic Authentication With Basic Authentication enabled, a username and password are passed between client and server in the uuencoded format. Uuencoding means that the text is scrambled, but normal ASCII characters are visible, so the username Murray might come out as Nvttbz. To the casual viewer this may seem unusable; however, encoded text can be unscrambled by certain programs. Additionally, any account authentication using Basic Authentication must have the Windows NT user right Log On Locally. 2/12/16 Page 43 Windows NT Challenge/Response Authentication Windows NT Challenge/Response authentication is the next level of Windows NT security. Challenge/Response is typically run in a networked environment which includes Windows NT Servers and Workstations and may include Windows 95 workstations. Digest Access Authentication Digest Access Authentication, which requires the use of Internet Explorer 5.0 on the client machine, is based on a simple challenge-response method. The Digest scheme generate a unique challenges for each request. A valid response contains several pieces of information to ensure that the password is never sent as easily decoded text. Recommendation Windows NT Windows NT Challenge/Response Authentication should be used whenever possible. In some cases, Basic Authentication will be necessary and should be used in conjunction with SSL. UNIX Basic Authentication is the only scheme supported on UNIX and therefore must be employed. To ensure security, SSL should be employed. Feature Patch – Microsoft supplies a patch to the Apache Web server which intercepts each call that the FrontPage client makes to the server extensions executable files. It then performs security checks, sets user ID to the owner of the Web site (thus requiring SUID/SGID operation of the server extensions and the web content), and invokes a centralized copy of the server extensions executable files. With the patch installed, a number of security checks are performed before executing the fpexe stub program. Checks are performed to validate the following: Proper ownership and permissions are set for the fpexe stub program and its directory. Proper ownership and permissions are set for the server extensions executable files and their directories. The web content area being authored has a valid user ID. The web content area being authored has a valid group ID. 2/12/16 Page 44 Only the FrontPage Server Extensions CGI executable files are being executed, not other CGI scripts on the system. The environment variables (including the path) are cleaned and passed only if the variable is on a pre-selected, approved list. FrontPage Server Extensions executable files are being invoked only by the Web server. A 128-byte key value that is dynamically generated when the Web server process is initialized is passed to the fpexe program and validated, ensuring that only the Web server is able to run fpexe. Recommendation Windows NT This feature does not apply to Windows NT. UNIX Review and install the Apache Patch for all installations of The FrontPage Server Extensions. As part of the server's maintenance, change the contents of the custom key file regularly when restarting the server. This will protect the key value. Feature IP Address Restriction – The FrontPage Server Extensions provide a means to restrict, by IP address, the machines which may access a subweb. Recommendation This provides an added level of protection, and should be implemented. Most commonly this feature would be employed to restrict Administration or Authoring to single machine or a group of machines. To further ensure that only authorized individuals are connecting to the FrontPage web, the FrontPage client version should be set to the major version number corresponding to that of the Server Extensions on the web server. This can be accomplished through the ClientVerCutoff registry key as described in the Baseline Security Configuration Section. Feature Password Policy – The FrontPage Server Extensions provide the means to ensure that simple passwords are not used and therefore reduce the likelihood of password being compromised. 2/12/16 Page 45 Recommendation Windows NT Set the Windows NT account policy as follows: Feature Maximum Password Age Minimum Password Age Minimum Password Length Password Uniqueness Account Lockout Recommendation Expires in 60 days Allow changes in 7 days At least 6 characters Remember 6 passwords Lockout after 5 bad logon attempts Reset count after 1440 minutes Lockout Duration Forever (until admin unlocks) In addition, employ the use of a password filter such as passfilt.dll. Passfilt.dll requires that passwords be at least 6 characters long, that they do not include the username, and that they contain characters from at least three of the following classes: English uppercase letters, English lowercase letters, westernized arabic numerals, and nonalphanumeric characters. Note: Under this configuration, it will become possible for the IUSR_machinename account to become locked out. If this occurs, no individual attempting to authenticate under the anonymous context will be successful. UNIX Set the entry ComplexPasswords in the frontpage.cnf file to a non-zero value. This configures the FrontPage Server Extensions to require complex passwords for FrontPage Administrator and Authoring accounts. When set, the following rules apply to passwords: 1. The user name cannot be embedded in the password . 2. The password must contain at least one alphabetic character. 3. The password must have more than 8 characters. Feature Subwebs – In many environments, it is undesirable to allow Authors to access all content on the web site. While one employee may be responsible for graphic design or content layout, another employee may be responsible for human resource information. When it is desirable that these employees cannot access the others data, a segregation of duties exists. To facilitate this control, the FrontPage Server Extensions allow the creation of separate subwebs. These subwebs appear to the user (accessing the web site through a web browser) as normal subdirectories, but can have completely separate Administrators and Authors. 2/12/16 Page 46 Recommendation Separate subwebs should be created and maintained for all distinct areas of content. Feature Directory Browsing – Directory browsing allows the display of all contents of the specified directory when no default HTML document exists there. Directory Browsing is, by default, disabled for all directories. Recommendation This feature allows content to remain obscure and should only be enabled when specifically warranted. Feature Content Indexing – Content indexing allows one of several applications to index content on the site. This feature provides the means for “Table of Contents” pages or site search engines. Once indexed, the content may be available to anonymous users even though this may not be desirable. Recommendation Windows NT Although a useful feature when properly employed, content indexing should only be enabled after careful consideration of the files in the subweb. The FrontPage Server Extensions support the use of both the built-in WAIS search engine, and the Microsoft’s Index Server. This feature can be enabled on a per subweb basis. UNIX Although a useful feature when properly employed, content indexing should only be enabled after careful consideration of the files in the subweb. The FrontPage Server Extensions support only the built-in WAIS search engine and therefore all content of the specified subweb will be indexed. 2/12/16 Page 47 Feature Support for the Secure Sockets Layer (SSL) protocol – SSL provides communications privacy, authentication, and message integrity for a TCP/IP connection. SSL transmits passwords in an encrypted form that is unreadable by normal means. By using this protocol, clients and servers can communicate in a way that prevents eavesdropping, tampering, or message forgery. Recommendation The FrontPage Server Extensions should be used with the Secure Sockets Layer (SSL) protocol to ensure that all information passed from a FrontPage client or through the HTML administration forms is transmitted in a secure manner. Feature Version Control - If multiple individuals are editing content on a web site, it is often desirable to invoke version control. The FrontPage Server Extensions allows the use of built-in source control on both the Windows NT and UNIX platforms. Additionally, on Windows NT, the FrontPage Server Extensions support the use of Microsoft Visual SourceSafe. The following table, taken from the Server Extensions Resource Kit, highlights some of the actions that the built-in source control software takes: When an The FrontPage Server Extensions… Unless… author… Edits and saves a Check the page out, update it, and check it N/A page that has not back into the web and the VSS project (if VSS been checked out control is enabled). Moves a file Move the file in the web and the VSS project (if VSS control is enabled). Then the Server Extensions check out every page in the web that contains a hyperlink to the moved file, update all hyperlinks to it, and check every page back in. A page with a hyperlink to the moved file is checked out. In this case, FrontPage will not let the author move the file. Renames a file Rename the file in the web and the VSS project (if VSS control is enabled). Then the Server Extensions prompt the author to check out every page in the web that contains a hyperlink to the moved file, update all hyperlinks to it, and check every page back in. A page with a hyperlink to the renamed file is already checked out. In this case, FrontPage will not let an author rename the file. Recommendation 2/12/16 Page 48 Source control should be enabled for all subwebs. This ensures that new files are not overwritten with older ones and that individuals are notified when files are in use. Other Considerations Networking A firewall should be placed between the Web server running FrontPage server extensions and the public (most likely the Internet) so that only HTTP (port 80) is allowed inbound and outbound. This will prevent against known denial of service attacks and other types of malicious and unauthorized activity. Miscellaneous In the previous versions of the Microsoft FrontPage Server Extensions, the runtime portion of the page hit-counter, fpcount.exe, was susceptible to certain specific buffer overflows which would crash the FrontPage Server Extensions. In this version, those problems have been corrected. 2/12/16 Page 49 Appendix A – Windows NT Objective - Configuration Determine if the possibility exists for users to access resources for which they have not been granted authorization. Scenario – Acknowledgement of Subwebs To determine if individuals have the ability to acknowledge the existence of FrontPage extended webs to which they have not been granted permission. Procedure Using a web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.4/ 2. Enter the full URL of each subweb off the root web 3. Enter the full URL of a subweb off the root web that does not exist 4. Enter the full URL of all subwebs off the PrivateSite subweb 5. Enter the full URL of a subweb off the PrivateSite subweb that does not exist Findings 1. The default web page was displayed. 2. Subwebs off the root produced the following results: When http://223.1.1.4/PublicSite/ was entered, the default document in that directory was displayed. When http://223.1.1.4/PrivateSite/ was entered, the NTLM authentication prompt was displayed. 3. When http://223.1.1.4/NonExistentDir/ was entered, the browser returned a 404 Not Found message. 4. When http://223.1.1.4/PrivateSite/PrivateSub/ was entered, the NTLM authentication prompt was displayed. 5. When http://223.1.1.4/PrivateSite/NonExistentDir/ was entered, the NTLM authentication prompt was displayed. 2/12/16 Page 50 Scenario – Use of Rights To determine if an individual can browse, author, or administer a FrontPage extended web if that individual is not granted explicit permission. Procedure BROWSE Using the web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.4/PrivateSite/ 2. When the NTLM authentication prompt appears, do not authenticate AUTHOR Using the FrontPage client from workstation 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Enter http://223.1.1.4/PublicSite/ 3. When the NTLM authentication prompt appears, do not authenticate 4. Enter http://223.1.1.4/PrivateSite/ 5. When the NTLM authentication prompt appears, authenticate as a Browser 6. Enter http://223.1.1.4/PrivateSite/ 7. When the NTLM authentication prompt appears, authenticate as the Author of PublicSite 8. Enter http://223.1.1.4/PrivateSite/ 9. When the NTLM authentication prompt appears, authenticate as the Author of PrivateSub2 10. Enter http://223.1.1.4/PrivateSite/ 11. When the NTLM authentication prompt appears, authenticate as the Author of Root 12. Create an HTML file named configcase.htm 13. Choose File | Publish Web… 14. Enter http://223.1.1.4/PublicSite/ 15. When the NTLM authentication prompt appears, do not authenticate 16. Enter http://223.1.1.4/PrivateSite/ 17. When the NTLM authentication prompt appears, authenticate as a Browser of PrivateSite 18. Enter http://223.1.1.4/PrivateSite/ 2/12/16 Page 51 19. When the NTLM authentication prompt appears, authenticate as the Author of PublicSite 20. Enter http://223.1.1.4/PrivateSite/ 21. When the NTLM authentication prompt appears, authenticate as the Author of PrivateSub2 ADMINISTER Using the web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.4:8234/fpadmin.htm 2. When the NTLM authentication prompt appears, do not authenticate; 3. When the NTLM authentication prompt appears, authenticate as a Browser of PrivateSite; 4. When the NTLM authentication prompt appears, authenticate as an Author of Root. 5. When the NTLM authentication prompt appears, authenticate as an Administrator of Root. Using the FrontPage client from workstation 223.1.1.5, perform the following: 6. Choose File | Open Web… 7. Enter http://223.1.1.4/PublicSite/ 8. When the NTLM authentication prompt appears, do not authenticate 9. Choose Tools | Security 10. Enter http://223.1.1.4/PrivateSite/ 11. When the NTLM authentication prompt appears, authenticate as a Browser 12. Choose Tools | Security 13. Enter http://223.1.1.4/PrivateSite/ 14. When the NTLM authentication prompt appears, authenticate as an Author 15. Choose Tools | Security 16. Enter http://223.1.1.4/PrivateSite/ 17. When the NTLM authentication prompt appears, authenticate as the Administrator of PublicSite 18. Choose Tools | Security 19. Enter http://223.1.1.4/PrivateSite/ 20. When the NTLM authentication prompt appears, authenticate as the Administrator of Root 21. Choose Tools | Security 22. Enter http://223.1.1.4/PrivateSite/ 2/12/16 Page 52 23. When the NTLM authentication prompt appears, authenticate as the Administrator of PrivateSub2 24. Choose Tools | Security Using the Command Line from workstation 223.1.1.5, perform the following: 25. From the Command Line enter “fpremadm.exe –targetserver http://223.1.1.4:8234/scripts/fpadmdll.dll -o enable –p 80” 26. When the NTLM authentication prompt appears, do not authenticate 27. When the NTLM authentication prompt appears, authenticate as a Browser of PrivateSite 28. When the NTLM authentication prompt appears, authenticate as an Author of Root 29. When the NTLM authentication prompt appears, authenticate as the Administrator of PrivateSite 30. When the NTLM authentication prompt appears, authenticate as the Administrator of Root Findings BROWSE 1. The NTLM authentication prompt appeared. 2. After Cancel was clicked, a “401.2 – Unauthorized: Logon failed due to server configuration” HTML page appeared. AUTHOR 1. The Open Web dialog box was displayed. 2. The NTLM authentication prompt appeared. 3. After Cancel was clicked, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” If YES is clicked, the client is displayed, but the web is not opened. If NO is clicked, the Open Web dialog box is re-displayed. 4. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/PrivateSite 5. After attempting to authenticate as a browser unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 6. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/PrivateSite 2/12/16 Page 53 7. After attempting to authenticate as a browser unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 8. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/PrivateSite 9. After attempting to authenticate as a browser unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 10. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/PrivateSite 11. After attempting to authenticate as the Author of Root, a “Microsoft FrontPage” dialog box appeared: “The folder ‘HTTP://223.1.1.4/PrivateSite’ isn’t accessible. The folder may be located on an unavailable volume or protected with a password.” After clicking OK, the “Open Web” dialog box is displayed. After clicking OPEN, the web is opened at the Root Level. (Security cannot be administered) 12. File configcase.htm was created with the FrontPage client. 13. The Publish Web dialog box was displayed 14. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 15. After clicking cancel, the publish web dialog box is displayed. 16. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 17. After attempting to authenticate as a browser, prompt reappears until cancel is clicked. After clicking cancel, the publish web dialog box is displayed. 18. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 19. After attempting to authenticate as the Author of PublicSite, prompt reappears until cancel is clicked. After clicking cancel, the publish web dialog box is displayed. 20. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 21. After attempting to authenticate as the Author of PrivateSub2, prompt reappears until cancel is clicked. After clicking cancel, the publish web dialog box is displayed. 2/12/16 Page 54 ADMINISTER 1. The NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 2. After Cancel was clicked, a “401.3 – Unauthorized: Unauthorized due to ACL on resource” HTML page was displayed. 3. After attempting to authenticate as a browser, prompt reappears three times. Then “401.3 – Unauthorized: Unauthorized due to ACL on resource” HTML page was displayed. 4. After attempting to authenticate as an author, prompt reappears three times. Then “401.3 – Unauthorized: Unauthorized due to ACL on resource” HTML page was displayed. 5. The HTML administration forms frameset was displayed. 6. The Open Web dialog box appeared. 7. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Publicsite 8. After Cancel was clicked, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 9. The option for Security is grayed out (as there is no connection to a remote machine) 10. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 11. After attempting to authenticate as a browser unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 12. The option for Security is grayed out (as there is no connection to a remote machine) 13. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 14. After attempting to authenticate as Privateauth unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 15. The option for Security is grayed out (as there is no connection to a remote machine) 16. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 17. After attempting to authenticate as Publicadmin unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 2/12/16 Page 55 18. The option for Security is grayed out (as there is no connection to a remote machine) 19. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 20. After authenticating as the Administrator of Root, the web was opened at the root level. 21. The option for Security is grayed out (as there is no connection to a remote machine) 22. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 23. After attempting to authenticate as the Administrator of PrivateSub2 unsuccessfully three times, a “Microsoft FrontPage” dialog box appeared: “You do not have permission to make changes to this document. Do you want to open a read-only copy?” 24. The option for Security is grayed out (as there is no connection to a remote machine) 25. The GUI NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 26. After Cancel is clicked, “Access denied: invalid password” is displayed at the command prompt 27. After attempting to authenticate as a browser, “a 401.3 Unauthorized” HTML source is displayed at the command prompt 28. After attempting to authenticate as a browser, “a 401.3 Unauthorized” HTML source is displayed at the command prompt 29. After attempting to authenticate as a browser, “a 401.3 Unauthorized” HTML source is displayed at the command prompt 30. The command prompt returned with: Starting enable, port: 80, web: “root web” Version: 4.0.0.2121 Created: 11 Dec 1998 19:13:10 –0000 Port 80: Authoring enabled 2/12/16 Page 56 Scenario – Subweb Information Gathering To determine what information an intruder can obtain about a website if it is running FrontPage Server Extensions. Procedure ABSOLUTE REFERENCES Using a web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.4/_vti_inf.html 2. Enter http://223.1.1.4/_private/ 3. Enter http://223.1.1.4/_vti_cnf/ 4. Enter http://223.1.1.4/_vti_log/ 5. Enter http://223.1.1.4/_vti_pvt/ 6. Enter http://223.1.1.4/_vti_pvt/access.cnf 7. Enter http://223.1.1.4/_vti_pvt/botinfs.cnf 8. Enter http://223.1.1.4/_vti_pvt/bots.cnf 9. Enter http://223.1.1.4/_vti_pvt/category.idx 10. Enter http://223.1.1.4/_vti_pvt/deptodoc.btr 11. Enter http://223.1.1.4/_vti_pvt/doctodep.btr 12. Enter http://223.1.1.4/_vti_pvt/frontpg.lck 13. Enter http://223.1.1.4/_vti_pvt/linkinfo.cnf 14. Enter http://223.1.1.4/_vti_pvt/service.cnf 15. Enter http://223.1.1.4/_vti_pvt/service.lck 16. Enter http://223.1.1.4/_vti_pvt/svcacl.cnf 17. Enter http://223.1.1.4/_vti_pvt/uniqperm.cnf 18. Enter http://223.1.1.4/_vti_pvt/writeto.cnf 19. Enter http://223.1.1.4/_vti_txt/ 20. Enter http://223.1.1.4/images/ 21. Enter http://223.1.1.4/_vti_bin/ 22. Enter http://223.1.1.4/_vti_bin/fpcount.exe 23. Enter http://223.1.1.4/_vti_bin/shtml.dll 24. Enter http://223.1.1.4/_vti_bin/_vti_adm/ 25. Enter http://223.1.1.4/_vti_bin/_vti_adm/admin.dll 26. Enter http://223.1.1.4/_vti_bin/_vti_aut/ 2/12/16 Page 57 27. Enter http://223.1.1.4/_vti_bin/_vti_aut/author.dll 28. Enter http://223.1.1.4/_vti_bin/_vti_aut/dvwssr.dll 29. Enter http://223.1.1.4/Publicsite/_vti_bin/fpcount.exe 30. Enter http://223.1.1.4/Publicsite/_vti_bin/shtml.dll 31. Enter http://223.1.1.4/Publicsite/_vti_bin/_vti_aut/dvwssr.dll 32. Enter http://223.1.1.4/Publicsite/images 33. Enter http://223.1.1.4/Publicsite/_vti_pvt/service.lck 34. Enter http://223.1.1.4/Publicsite/Publicsub/images 35. Enter http://223.1.1.4/Publicsite/Publicsub/_vti_bin/fpcount.exe 36. Enter http://223.1.1.4/Publicsite/Publicsub/_vti_pvt/service.lck 37. Enter http://223.1.1.4/Publicsite/Publicsub/_vti_bin/_vti_aut/dvwssr.dll 38. Enter http://223.1.1.4/Privatesite/_vti_bin/fpcount.exe 39. Enter http://223.1.1.4/Privatesite/_vti_bin/shtml.dll 40. Enter http://223.1.1.4/Privatesite/_vti_bin/_vti_aut/dvwssr.dll 41. Enter http://223.1.1.4/Privatesite/images 42. Enter http://223.1.1.4/Privatesite/_vit_pvt/service.lck 43. Enter http://223.1.1.4/Privatesite/Privatesub/_vti_bin/fpcount.exe 44. Enter http://223.1.1.4/Privatesite/Privatesub/_vit_pvt/service.lck 45. Enter http://223.1.1.4/Privatesite/Privatesub/_vti_bin/_vti_aut/dvwssr.dll 46. Enter http://223.1.1.4/Privatesite/Privatesub/images DIRECTORY NAVIGATION Using a web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.4/PrivateSite/PrivateSub/.. RPC METHODS 1. Create an HTML form to send RPC methods to 223.1.1.4 Execute the following RPC Server Methods: 2. server version 9. remove service 3. restart server 10. list url-directories 4. list interpreters 11. create url-directory 5. list libraries 12. create url-directories 6. list services 13. remove url-directory 7. open service 14. mark url-directory executable 8. create service 15. list documents 2/12/16 Page 58 16. get document 50. list access 17. get documents 51. update access 18. get bot 52. list special access 19. put document 53. update special access 20. put documents 54. change mnemonic 21. remove documents 55. verify user 22. move document 56. list domains 23. rename url 57. get service access control 24. list themes 58. set service access control 25. put theme 59. TextSource enumerate 26. get theme 60. TextSource createTextSource 27. apply theme 61. TextSource dropTextSource 28. apply border 62. TextSource enumerateTables 29. apply stylesheet 63. TextSource enumerateFields 30. set service meta-info 64. TextSource createTable 31. set document meta-info 65. TextSource dropTable 32. add document to source control 66. TextSource stopIndexing 33. checkout document 67. TextSource startIndexing 34. checkin document 68. TextSource reIndex 35. uncheckout document 69. TextSource addToIndex 36. remove links 70. TextSource removeFromFutureIndexes 37. recalc control 71. TextSource executeQuery 38. browser recalc 72. html-table add row 39. set source control 73. html-table change row 40. rename service 74. html-table remove row 41. getDocsMetaInfo 75. get web struct 42. setDocsMetaInfo 76. get web struct by url 43. query access setup 77. put web struct 44. modify access setup 78. put nav text overlays 45. list users 79. replace web struct 46. update user list 80. recalc pages 47. list groups 81. list data sources 48. update group list 82. get database schema 49. update group 83. list record sources 2/12/16 Page 59 84. get record source schema 86. list drivers 85. get query schema 87. url to web url Findings ABSOLUTE REFERENCES The web server responded by displaying: 1. The HTML file _vti_inf.html 2. A “403.2 Forbidden” HTML message page 3. A “403.2 Forbidden” HTML message page 4. A “403.2 Forbidden” HTML message page 5. A “403.2 Forbidden” HTML message page 6. A “403.2 Forbidden” HTML message page 7. A “403.2 Forbidden” HTML message page 8. A “403.2 Forbidden” HTML message page 9. A “403.2 Forbidden” HTML message page 10. A “403.2 Forbidden” HTML message page 11. A “403.2 Forbidden” HTML message page 12. A “403.2 Forbidden” HTML message page 13. A “403.2 Forbidden” HTML message page 14. A “403.2 Forbidden” HTML message page 15. A “403.2 Forbidden” HTML message page 16. A “403.2 Forbidden” HTML message page 17. A “403.2 Forbidden” HTML message page 18. A “403.2 Forbidden” HTML message page 19. A “403.2 Forbidden” HTML message page 20. A “403 Forbidden” HTML message page 21. A “403 Forbidden” HTML message page 22. A “CGI Error” HTML message page 23. A “FrontPage Error” HTML message page as follows: User: please report details to this site's webmaster. Webmaster: please see the server's application event log for more details. The associated EventLog message was: Error #60003 Message: Trying to run the SmartHTML Interpreter on this non-HTML page "" 24. A “403 Forbidden” HTML message page 2/12/16 Page 60 25. The Username/Password/Domain NTLM Authentication Prompt 26. A “403 Forbidden” HTML message page 27. The Username/Password/Domain NTLM Authentication Prompt 28. A “The page cannot be displayed” HTML message page 29. A “CGI Error” HTML message page 30. A “FrontPage Error” HTML message page as above. 31. A “Invalid or Unrecognized response” HTML message page 32. A “403 Forbidden” HTML message page 33. A “403.2 Forbidden” HTML message page 34. A “403 Forbidden” HTML message page 35. The Username/Password/Domain NTLM Authentication Prompt 36. A “403.2 Forbidden” HTML message page 37. A “The page cannot be displayed” HTML message page 38. The Username/Password/Domain NTLM Authentication Prompt 39. The Username/Password/Domain NTLM Authentication Prompt 40. The Username/Password/Domain NTLM Authentication Prompt 41. The Username/Password/Domain NTLM Authentication Prompt 42. The Username/Password/Domain NTLM Authentication Prompt 43. The Username/Password/Domain NTLM Authentication Prompt 44. The Username/Password/Domain NTLM Authentication Prompt 45. The Username/Password/Domain NTLM Authentication Prompt 46. The Username/Password/Domain NTLM Authentication Prompt DIRECTORY NAVIGATION 1. The NTLM authentication prompt for site 223.1.1.4 was displayed. RPC METHODS All attempted commands returned the following unless otherwise noted by their complete responses. method=MethodName:4.0.2.2000 status= - status=917505 - osstatus=0 - msg=The user 'IUSR_SERVER4' is not authorized to execute the ‘MethodName’ method. - osmsg= 1. Created formpost.html with the following source: <html> <head><title>POST TEST</title> 2/12/16 Page 61 <body> <form method="POST" action="http://223.1.1.4/Privatesite/_vti_bin/shtml.dll/_vti_rpc" enctype="application/x-www-form-urlencoded"> Enter a method: <input name="method" type="text"><p> <input name="OK" type="submit"> </form> </body> </html> Executing the listed commands results in the following output: 2. method=server version:4.0.0.2121 server version= * major ver=4 * minor ver=0 * phase ver=0 * ver incr=2121 3. method=restart server:4.0.0.2121 status= * status=917507 * osstatus=0 * msg=The method 'restart server' is not supported. * osmsg= 4. method=list interpreters:4.0.0.2121 status= * status=917507 * osstatus=0 * msg=The method 'list interpreters' is not supported. * osmsg= 5. method=list libraries:4.0.0.2121 status= * status=917507 * osstatus=0 * msg=The method 'list libraries' is not supported. * osmsg= 6. method=list services:4.0.0.2121 services_list= * service_name= * meta_info= * vti_casesensitiveurls * IX|0 * vti_textextensions * SX|.txt.txt. * vti_featurelist 2/12/16 Page 62 * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * VX|vti_ACCreateNewUsers vti_ACChangePassword vti_ACNoUserGroup vti_ACCreateNewGroups vti_ACModifyGroups vti_ServiceMarkUrlDirExec vti_ServerEmailTransport vti_dependenciesood IR|0 vti_httpdversion SX|Microsoft-IIS/4.0 vti_navbuttonuplabel SR|Up vti_webservertype SR|msiis vti_categories VR|Travel Expense\ Report Business Competition Goals/Objectives Ideas Miscellaneous Waiting VIP In\ Process Planning Schedule vti_textindexood IR|0 vti_navbuttonnextlabel SR|Next vti_approvallevels VR|Content\ Review Legal\ Review Code\ Review Manager\ Review vti_timecreated TR|15 Oct 1996 14:04:28 -0000 vti_extenderversion SR|4.0.0.2121 vti_navbuttonprevlabel SR|Back vti_longfilenames IX|1 vti_welcomenames VX|Default.htm Default.asp vti_insecureserverurl SR|http://223.1.1.4 vti_disableautoimgsizeexts SX|.asp vti_oldestcompatibleversion SR|2.0.0.0 vti_restartmanual IX|0 vti_defaultcharset SR|none vti_defaultlanguage SR|en vti_hassearchbot BR|false vti_autorecalc IX|1 vti_htmlextensions SX|.htm.html.stm.html.htm.shtml.shtm.htx.asp.alx.asa. vti_createpostinfo BX|false 2/12/16 Page 63 * * * * vti_navbuttonhomelabel * SR|Home service_name=/Privatesite service_name=/Publicsite meta_info= * vti_casesensitiveurls * IX|0 * vti_textextensions * SX|.txt.txt. * vti_featurelist * VX|vti_ACCreateNewUsers vti_ACChangePassword vti_ACNoUserGroup vti_ACCreateNewGroups vti_ACModifyGroups vti_ServiceMarkUrlDirExec vti_ServerEmailTransport * vti_httpdversion * SX|Microsoft-IIS/4.0 * vti_ignorekeyboard * IR|0 * vti_navbuttonuplabel * SR|Up * vti_dependenciesood * IR|0 * vti_webservertype * SR|msiis * vti_categories * VR|Travel Expense\ Report Business Competition Goals/Objectives Ideas Miscellaneous Waiting VIP In\ Process Planning Schedule * vti_navbuttonnextlabel * SR|Next * vti_textindexood * IR|0 * vti_approvallevels * VR|Content\ Review Legal\ Review Code\ Review Manager\ Review * vti_timecreated * TR|15 Oct 1996 14:06:24 -0000 * vti_extenderversion * SR|4.0.0.2121 * vti_navbuttonprevlabel * SR|Back * vti_longfilenames * IX|1 * vti_welcomenames * VX|Default.htm Default.asp * vti_insecureserverurl * SR|http://223.1.1.4 * vti_disableautoimgsizeexts * SX|.asp * vti_oldestcompatibleversion * SR|2.0.0.0 * vti_restartmanual * IX|0 2/12/16 Page 64 * * * * * * * * * * * * * * vti_title SW|Publicsite vti_defaultcharset SR|iso-8859-1 vti_defaultlanguage SR|en vti_hassearchbot BR|false vti_autorecalc IX|1 vti_htmlextensions SX|.htm.html.stm.html.htm.shtml.shtm.htx.asp.alx.asa. vti_navbuttonhomelabel SR|Home 7. open service 8. create service 9. remove service 10. list url-directories 11. create url-directory 12. create url-directories 13. remove url-directory 14. mark url-directory executable 15. list documents 16. get document 17. get documents 18. get bot 19. put document 20. put documents 21. remove documents 22. move document 23. rename url 24. list themes 25. put theme 26. get theme 27. apply theme 28. apply border 29. apply stylesheet 30. set service meta-info 31. set document meta-info 32. add document to source control 33. checkout document 34. checkin document 35. uncheckout document 36. remove links 37. recalc control 38. method=browser recalc:4.0.0.2121 status= * status=589852 2/12/16 Page 65 * osstatus=0 * msg=Unable to recalculate links for "". * osmsg= 39. set source control 40. rename service 41. getDocsMetaInfo 42. setDocsMetaInfo 43. query access setup 44. modify access setup 45. list users 46. update user list 47. list groups 48. update group list 49. update group 50. list access 51. update access 52. list special access 53. update special access 54. change mnemonic 55. verify user 56. list domains 57. get service access control 58. set service access control 59. TextSource enumerate 60. method=TextSource create TextSource :4.0.0.2121 status= * status=917506 * osstatus=0 * msg=The method 'TextSource create TextSource ' is not recognized. * osmsg= 61. TextSource dropTextSource Not Authorized 62. TextSource enumerateTables 63. TextSource enumerateFields 64. TextSource createTable 65. TextSource dropTable 66. TextSource stopIndexing 67. TextSource startIndexing 68. TextSource reIndex 69. TextSource addToIndex 70. TextSource removeFromFutureIndexes 71. TextSource executeQuery 72. html-table add row 73. html-table change row 74. html-table remove row 75. get web struct 76. get web struct by url 77. put web struct 2/12/16 Page 66 78. put nav text overlays 79. replace web struct 80. recalc pages 81. list data sources 82. get database schema 83. list record sources 84. get record source schema 85. get query schema 86. list drivers 87. method=url to web url:4.0.0.2121 status= * status=262145 * osstatus=0 * msg=Missing parameter 'url' for function 'url to web url' * osmsg= 2/12/16 Page 67 Scenario – User Information Gathering To determine if FrontPage Administrators possess the capability to enumerate users from the Windows NT user account database. Procedure PRE-REGISTRY MODIFICATION Using the FrontPage client on workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.4/ 2. When the NTLM authentication prompt appears, authenticate as the Administrator of the Root web 3. Choose Tools | Security 4. Select the Users tab 5. Click the Add button POST-REGISTRY MODIFICATION Make the following modificiations: In the registry, at: HKLM\Software\Microsoft\Shared Tools\Web Server Extensions\All Ports\ Add the Value Name: RestrictIISUsersAndGroups With the Value Entry: 1 In User Manager, add the group below: FP_[VirtualServer][_Directories][_Subweb] So, in this case: FP_223.1.1.4:80 Using the FrontPage client on workstation 223.1.1.5, perform the following: 6. Enter http://223.1.1.4/ 7. When the NTLM authentication prompt appears, authenticate as the Administrator of the Root web 8. Choose Tools | Security 9. Select the Users tab 10. Click the Add button 2/12/16 Page 68 Findings PRE-REGISTRY MODIFICATION 1. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 2. After authenticating as the Administrator of the Root web, the web was opened at the root level. 3. The “Permissions <Root Web>” dialog box was displayed. 4. The Users pane was displayed 5. The complete list of Windows NT system users except for the IUSR_ComputerName account was displayed. POST-REGISTRY MODIFICATION 6. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 7. After authenticating as the Administrator of the Root web, the web was opened at the root level. 8. The “Permissions <Root Web>” dialog box was displayed. 9. The Users pane was displayed 10. A restricted list of Windows NT system users as created in User Manager on 223.1.1.4 was displayed. 2/12/16 Page 69 Scenario – File Execution To determine if an Author can use scripts and other executable files to gather information from or gain access to the system. Procedure UPLOADING FILES Pre-Registry Modification Using the FrontPage client from workstation 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Select a local web 3. Choose File | Import… 4. Click Add File… 5. Select regdmp.exe, Click Open, Click OK 6. Choose File | Publish Web… 7. Enter http://223.1.1.4/PublicSite/exedir and Click Publish Note: /exedir is a directory marked as executable. 8. When the NTLM authentication prompt appears, authenticate as the Author of PublicSite 9. Click OK Post-Registry Modification Make the following modification: In the registry, at: HKLM\Software\Microsoft\Shared Tools\Web Server Extensions\All Ports\ Locate the Value Name: NoExecutableCgiUpload With the Value Entry: Change the Value Entry to: 1 0 Using the FrontPage client from workstation 223.1.1.5, perform the following: 10. Choose File | Publish Web… 11. Enter http://223.1.1.4/PublicSite/exedir and click Publish 12. When the NTLM authentication prompt appears, authenticate as the Author of PublicSite 13. Click OK Restore the Registry Key to the previous value as above. 2/12/16 Page 70 EXECUTING FILES Using the web browser from 223.1.1.5, perform the following: 1. Enter http://223.1.1.4/PublicSite/exedir/regdmp.exe Findings UPLOADING FILES 1. The Open Web dialog box was displayed. 2. The web "C:\WINNT\Profiles\administrator\My Webs" was selected. 3. The Import dialog box was displayed. 4. The Add File to Import List file section box was displayed. 5. regdmp.exe was added as a file to the web. 6. The Publish Web dialog box was displayed. 7. http://223.1.1.4/Publicsite/exedir was entered in the "specify the location" box. 8. The NTLM authentication prompt appeared requesting administrator permission for 223.1.1.4:80, and the Author of PublicSite was used to authenticate. 9. A “Microsoft FrontPage” dialog box was displayed. “/PublicSite/exedir” is marked executable. “Server Error: The folder You are not allowed to put files into an executable folder on this server. 10. The Publish Web dialog box was displayed. 11. http://223.1.1.4/Publicsite/exedir was typed into the "specify the location" box. 12. The NTLM authentication prompt appeared requesting author permission for 223.1.1.4:80, and the Author of PublicSite was used to authenticate. 13. The file was published successfully. EXECUTING FILES 1. The results of the registry of server 223.1.1.4 were displayed on the web browser of 233.1.1.5. 2/12/16 Page 71 Objective - Penetration Determine what vulnerabilities exist after FrontPage Server Extensions are installed on a website. Scenario – Port Discovery To determine what ports are opened or listening on a FrontPage extended website. Procedure 1. Run a port scanner from 223.1.1.5 Findings 1. The following ports were open: Port 80 – For communicating via HTTP Port 137 - NETBIOS Name Service Port 139 - NETBIOS Session Service Port 8234 – The port configured for remote administration Scenario – Account Lockout To determine if accounts will be locked out after a specific number of bad logon attempts. Procedure WEB BROWSER ACCESS Using the web browser from 223.1.1.5, perform the following: 1. Enter http://223.1.1.4:8234/fpadmin.htm 2. When the NTLM authentication prompt appears, enter the username RootAdmin with an incorrect password; 3. Ensure the Windows NT account policy is set to lockout accounts after five bad logon attempts, and repeat the prior step six times. 4. Attempt to authenticate once more and enter the username RootAdmin with the correct password 5. Enter http://223.1.1.4/PrivateSite/ 6. When the NTLM authentication prompt appears, enter the username RootAdmin with an incorrect password; 2/12/16 Page 72 7. Ensure the Windows NT account policy is set to lockout accounts after five bad logon attempts, and repeat the prior step six times. 8. Attempt to authenticate once more and enter the username RootAdmin with the correct password FRONTPAGE CLIENT ACCESS Using the FrontPage client from 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Enter http://223.1.1.4/ 3. When the NTLM authentication prompt appears, enter the username RootAdmin with an incorrect password 4. Ensure the Windows NT account policy is set to lockout accounts after five bad logon attempts, and repeat the prior step six times. 5. Attempt to authenticate once more and enter the username RootAdmin with the correct password 6. Create an HTML file named penetcase.htm 7. Choose File | Publish Web… 8. Enter http://223.1.1.4/ 9. When the NTLM authentication prompt appears, enter the username RootAdmin with an incorrect password 10. Ensure the Windows NT account policy is set to lockout accounts after five bad logon attempts, and repeat the prior step six times. 11. Attempt to authenticate once more and enter the username RootAdmin with the correct password COMMAND LINE ACCESS Using the Command Line from 223.1.1.5, perform the following: 1. From the Command Line enter “fpremadm.exe –targetserver http://223.1.1.4:8234/scripts/fpadmdll.dll -o enable –p 8234” 2. When the NTLM authentication prompt appears, enter the username RootAdmin with an incorrect password 3. Ensure the Windows NT account policy is set to lockout accounts after five bad logon attempts, and repeat the prior step six times. 4. Attempt to authenticate once more and enter the username RootAdmin with the correct password 2/12/16 Page 73 Findings WEB BROWSER ACCESS 1. The NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 2. After an unsuccessful logon attempt, the authentication prompt was re-displayed. 3. After two more unsuccessful logon attempts, a “401.1 Unauthorized Logon Failure” HTML page was displayed. After a refresh, and three more failed attempts, the page was displayed again. 4. The account was locked out, according to the Windows NT account policy and, even with the correct password, the user could not authenticate. 5. The NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 6. After an unsuccessful logon attempt, the authentication prompt was re-displayed. 7. After two more unsuccessful logon attempts, a “401.1 Unauthorized Logon Failure” HTML page was displayed. After a refresh, and three more failed attempts, the page was displayed again. 8. The account was locked out, according to the Windows NT account policy and, even with the correct password, the user could not authenticate. FRONTPAGE CLIENT ACCESS 1. The Open Web dialog box was displayed. 2. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 3. After an unsuccessful logon attempt, the authentication prompt was re-displayed. 4. After six more unsuccessful logon attempts, the authentication prompt was still displayed. 5. The account was locked out, according to the Windows NT account policy and, even with the correct password, the user could not authenticate. 6. File penetcase.htm was created with the FrontPage client. 7. The Publish Web dialog box was displayed 8. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 9. After an unsuccessful logon attempt, the authentication prompt was re-displayed. 10. After six more unsuccessful logon attempts, the authentication prompt was still displayed. 2/12/16 Page 74 11. The account was locked out, according to the Windows NT account policy and, even with the correct password, the user could not authenticate. COMMAND LINE ACCESS 1. The GUI NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 2. After an unsuccessful logon attempt, the “401.3 Unauthorized” HTML source was displayed at the command prompt 3. After each successive failed logon attempt, the “401.3 Unauthorized” HTML source was displayed at the command prompt 4. The account was locked out, according to the Windows NT account policy and, even with the correct password, the user could not authenticate. 2/12/16 Page 75 Objective - Data Capturing Determine if the possibility exists to capture information as it is passed to the FrontPage Server Extensions. Scenario – Password Gathering To Determine if passwords are passed in clear text during the authentication process. Procedure WEB BROWSER ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 2. Enter http://223.1.1.4:8234/fpadmin.htm 1. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password; Using the network sniffer from 223.1.1.10, perform the following: 2. Disable data capture 3. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 4. Enter http:// 223.1.1.4/PrivateSite/ 5. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password; Using the network sniffer from 223.1.1.10, perform the following: 6. Disable data capture FRONTPAGE CLIENT ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 2. Choose File | Open Web… 3. Enter http://223.1.1.4/ 4. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password Using the network sniffer from 223.1.1.10, perform the following: 2/12/16 Page 76 5. Disable data capture 6. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 7. Create an HTML file named sniffcase.htm 8. Choose File | Publish Web… 9. Enter http://223.1.1.4/ 7. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password Using the network sniffer from 223.1.1.10, perform the following: 8. Disable data capture COMMAND LINE ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the Command Line from 223.1.1.5, perform the following: 2. From the Command Line enter “fpremadm.exe –targetserver http://223.1.1.4:8234/scripts/fpadmdll.dll -o enable –p 80 ” 3. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password Using the network sniffer from 223.1.1.10, perform the following: 4. Disable data capture Using the network sniffer from 223.1.1.10, perform the following: 5. Enable the network sniffer to start capturing data Using the Command Line from 223.1.1.5, perform the following: 6. From the Command Line enter “fpremadm.exe –adminusername RootAdmin – adminpassword rootadmin –targetserver http://223.1.1.4:8234/scripts/fpadmdll.dll -o enable –p 80” Using the network sniffer from 223.1.1.10, perform the following: 7. Disable data capture Findings WEB BROWSER ACCESS 1. Network Monitor Capture | Start was executed 2. The NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 2/12/16 Page 77 3. The HTML Administration forms frameset was displayed 4. Network Monitor Capture | Stop was executed 5. Network Monitor Capture | Start was executed 6. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 7. The default page for Privatesite was displayed 8. Network Monitor Capture | Stop was executed FrontPage Client Access 1. Network Monitor Capture | Start was executed 2. The Open Web Dialog Box was displayed 3. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/ 4. The web was opened at the Root level 5. Network Monitor Capture | Stop was executed 6. Network Monitor Capture | Start was executed 7. An HTML file was created with the FrontPage Client 8. The Publish Web dialog box was displayed 9. The NTLM authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.4:80” 10. The web was opened at the root level 11. Network Monitor Capture | Stop was executed COMMAND LINE ACCESS 1. Network Monitor Capture | Start was executed 2. The GUI NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 3. The command prompt returned with: Starting enable, port: 80, web: “root web” Version: 4.0.0.2121 Created: 11 Dec 1998 19:13:10 –0000 Port 80: Authoring enabled 4. Network Monitor Capture | Stop was executed 5. Network Monitor Capture | Start was executed 6. The command prompt returned with: Starting enable, port: 80, web: “root web” 2/12/16 Page 78 Version: 4.0.0.2121 Created: 11 Dec 1998 19:13:10 –0000 Port 80: Authoring enabled 7. Network Monitor Capture | Stop was executed 2/12/16 Page 79 Scenario – Confidential Information Gathering To determine if confidential information is passed in clear text during administration and authoring. Procedure WEB BROWSER ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 2. Enter http://223.1.1.4:8234/fpadmin.htm 1. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password; Perform the following functions 2. Renaming a Subweb a. b. c. d. In the contents listing, click Rename Subweb. In the Virtual Host Name field, type 223.1.1.4 In the Port Number field, type 80. In the Subweb Name field, type TestSub This should be the path to the subweb's top-level directory, from the server’s toplevel directory. e. In the New Subweb Name field, type NewSubName f. Click Rename Subweb. 3. Setting Permissions for a User a. b. c. d. In the contents listing, click User Permissions. In the Virtual Host Name field, type 223.1.1.4 In the Port Number field, type 80 In the Web Name field, type / This should be the path to the web's top-level directory, from the server's toplevel directory. To specify the root web, type a forward slash (/). e. In the Username field, type TestGuy f. Select the level of access for the user: Browse, Author, and Administrate Access. g. Click Change Permissions. 4. Setting Permissions for IP Addresses a. In the contents listing, click IP Address Permissions. b. In the Virtual Host Name field, type 223.1.1.4 c. In the Port Number field, type 80 2/12/16 Page 80 d. In the Web Name field, type / This should be the path to the web's top-level directory, from the server's toplevel directory. To specify the root web, type a forward slash (/). e. In the IP Address field, enter the IP address of the computer or set of computers whose permissions you are adding, removing, or changing. Enter 223.1.1.3 f. Select the level of access for the computer or group of computers: Browse, Author, and Administrate Access. g. Click Change Permissions. 5. Specifying That a Folder Can Contain Programs a. b. c. d. In the contents listing, click Set Directory Executable. In the Virtual Host Name field, type 223.1.1.4 In the Port Number field, type 80 In the Web Name field, type / This should be the path to the web's top-level directory, from the server's toplevel directory. To specify the root web, type a forward slash (/). e. In the Directory URL field, type a URL relative to the top-level directory of the FrontPage-extended web. Enter NewSubName f. Click Set Directory Executable. 6. Deleting a SubWeb a. b. c. d. e. In the contents listing, click Delete Subweb. In the Virtual Host Name field, type 223.1.1.4 In the Port Number field, type 80 In the Subweb Name field, type /NewSubName. This should be the path to the subweb's top-level directory, from the server's toplevel directory. f. e. Click Delete Subweb. Using the network sniffer from 223.1.1.10, perform the following: 7. Disable data capture 8. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 9. Enter http:// 223.1.1.4/PrivateSite/ 10. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password; Using the network sniffer from 223.1.1.10, perform the following: 11. Disable data capture 2/12/16 Page 81 FRONTPAGE CLIENT ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 2. Choose File | Open Web… 3. Enter http://223.1.1.4/PrivateSite/ 4. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password 5. Double-click on publcase.htm 6. Modify the contents 7. Save the file Using the network sniffer from 223.1.1.10, perform the following: 8. Disable data capture 9. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 10. Create an HTML file named publ2case.htm 11. Choose File | Publish Web… 12. Enter http://223.1.1.4/PrivateSite/ 1. When the NTLM authentication prompt appears, enter the username RootAdmin with the correct password Using the network sniffer from 223.1.1.10, perform the following: 15. Disable data capture 16. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 17. Choose File | Import… 18. Select the Import Web Wizard and click OK 19. On the “Choose Source” Screen, a. Select the “From a World Wide Web site” radio button b. Enter 223.1.1.4 in the Location field and click Next 20. On the “Choose Download Amount” Screen, Click Next 21. On the “Finish” Screen, Click Finish Using the network sniffer from 223.1.1.10, perform the following: 22. Disable data capture 2/12/16 Page 82 Findings WEB BROWSER ACCESS 1. Network Monitor Capture | Start was executed 2. The NTLM authentication prompt “Enter Network Password” appeared for site http://223.1.1.4/ 3. The HTML Administration forms frameset was displayed 4. The Form Submission results page displayed the following: Starting rename, port: 80, web: "TestSub" Version: 4.0.0.2121 Created: 11 Dec 1998 19:37:09 -0000 Port 80: Renamed web "TestSub" to "NewSubName" 5. The Form Submission results page displayed the following: Starting security, port: 80, web: "/" Version: 4.0.0.2121 Created: 11 Dec 1998 19:37:09 -0000 Port 80: User "TestGuy" and IP address "" added to administrators for web "/" 6. The Form Submission results page displayed the following: Starting security, port: 80, web: "/" Version: 4.0.0.2121 Created: 11 Dec 1998 19:37:09 -0000 No user will be added. Port 80: IP address "223.1.1.3" added to administrators for web "/" 7. The Form Submission results page displayed the following: Starting setdirexec, port: 80, web: "/NewSubName" Version: 4.0.0.2121 Created: 11 Dec 1998 19:37:09 -0000 Port 80: Set folder "" executable in web "/NewSubName" 8. The Form Submission results page displayed the following: Starting delete, port: 80, web: "/NewSubName" Version:4.0.0.2121 Created: 11 Dec 1998 19:37:09 -0000 2/12/16 Page 83 Port 80: Deleted web "/NewSubName" 9. Network Monitor Capture | Stop was executed 10. Network Monitor Capture | Start was executed 11. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/Privatesite 12. The default page for Privatesite was displayed 13. Network Monitor Capture | Stop was executed FRONTPAGE CLIENT ACCESS 1. Network Monitor Capture | Start was executed 2. The Open Web dialog box was displayed 3. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/PrivateSite 4. The web was opened at the PrivateSite level 5. The contents of publcase.htm were displayed in the document window 6. The contents were modified to include the phrase: “contents now modified” 7. The file was successfully saved 8. Network Monitor Capture | Stop was executed 9. Network Monitor Capture | Start was executed 10. An HTML file named publ2case.htm was created with the FrontPage client 11. The Publish Web dialog box was displayed 12. The NTLM authentication prompt “Enter Network Password” appeared for resource http://223.1.1.4/PrivateSite 13. The file was successfully published as indicated by the dialog box. 14. Network Monitor Capture | Stop was executed 15. Network Monitor Capture | Start was executed 16. The “New” web site dialog box was displayed 17. The “Import Web Wizard – Choose Source” dialog box was displayed 18. The “Import Web Wizard – Choose Download Amount” dialog box was displayed 19. The “Import Web Wizard – Finish” dialog box was displayed 20. The Web was imported and displayed (Root and PublicSite only) 21. Network Monitor Capture | Stop was executed 2/12/16 Page 84 Appendix B – UNIX Objective - Configuration Determine if the possibility exists for users to access resources for which they have not been granted authorization. Scenario – Acknowledgement of Subwebs To determine if individuals have the ability to acknowledge the existence of FrontPage extended webs to which they have not been granted permission. Procedure Using a web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.2/ 2. Enter the full URL of each subweb off the root web 3. Enter the full URL of a subweb off the root web that does not exist 4. Enter the full URL of all subwebs off the PrivateSite subweb 5. Enter the full URL of a subweb off the PrivateSite subweb that does not exist Findings 1. The default web page was displayed. 2. Subwebs off the root produced the following results: When http://223.1.1.2/PublicSite/ was entered, the default document in that directory was displayed. When http://223.1.1.2/PrivateSite/ was entered, the authentication prompt was displayed. 3. When http://223.1.1.2/NonExistentDir/ was entered, the browser returned a 404 Not Found message. 4. When http://223.1.1.2/PrivateSite/PrivateSub/ was entered, the authentication prompt was displayed. 5. When http://223.1.1.2/PrivateSite/PrivateSub/NonExistentDir/ was entered, the authentication prompt was displayed. 2/12/16 Page 85 Scenario – Use of Rights To determine if an individual can browse, author, or administer a FrontPage extended web if that individual is not granted explicit permission. Procedure BROWSE Using the web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.2/PrivateSite/ 2. When the .htaccess authentication prompt appears, do not authenticate AUTHOR Using the FrontPage client from workstation 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Enter http://223.1.1.2/PublicSite/ 3. When the .htaccess authentication prompt appears, do not authenticate 4. Enter http://223.1.1.2/PrivateSite/ 5. When the .htaccess authentication prompt appears, authenticate as a Browser 6. Enter http://223.1.1.2/PrivateSite/ 7. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 8. Enter http://223.1.1.2/PrivateSite/ 9. When the .htaccess authentication prompt appears, authenticate as the Author of PrivateSub2 10. Enter http://223.1.1.2/PrivateSite/ 11. When the .htaccess authentication prompt appears, authenticate as the Author of Root 12. Create an HTML file named configcase.htm 13. Choose File | Publish Web… 14. Enter http://223.1.1.2/PublicSite/ 15. When the .htaccess authentication prompt appears, do not authenticate 16. Enter http://223.1.1.2/PrivateSite/ 17. When the .htaccess authentication prompt appears, authenticate as a Browser 18. Enter http://223.1.1.2/PrivateSite/ 19. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 20. Enter http://223.1.1.2/PrivateSite/ 21. When the .htaccess authentication prompt appears, authenticate as the Author of PrivateSub2 2/12/16 Page 86 ADMINISTER Using the web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.2:8234/fpadmin.htm 2. When the .htaccess authentication prompt appears, do not authenticate; 3. When the .htaccess authentication prompt appears, authenticate as a Browser; 4. When the .htaccess authentication prompt appears, authenticate as an Author. Using the FrontPage client from workstation 223.1.1.5, perform the following: 5. Choose File | Open Web… 6. Enter http://223.1.1.2/PublicSite/ 7. When the .htaccess authentication prompt appears, do not authenticate 8. Choose Tools | Security 9. Enter http://223.1.1.2/PrivateSite/ 10. When the .htaccess authentication prompt appears, authenticate as a Browser 11. Choose Tools | Security 12. Enter http://223.1.1.2/PrivateSite/ 13. When the .htaccess authentication prompt appears, authenticate as an Author 14. Choose Tools | Security 15. Enter http://223.1.1.2/PrivateSite/ 16. When the .htaccess authentication prompt appears, authenticate as the Administrator of PublicSite 17. Choose Tools | Security 18. Enter http://223.1.1.2/PrivateSite/ 19. When the .htaccess authentication prompt appears, authenticate as the Administrator of Root 20. Choose Tools | Security 21. Enter http://223.1.1.2/PrivateSite/ 22. When the .htaccess authentication prompt appears, authenticate as the Administrator of PrivateSub2 23. Choose Tools | Security Using the Command Line from workstation 223.1.1.5, perform the following: 24. From the Command Line enter “fpremadm.exe –targetserver http://223.1.1.2:8234/scripts/fpadmcgi.exe -o enable –p 80” 25. When the .htaccess authentication prompt appears, do not authenticate 26. When the .htaccess authentication prompt appears, authenticate as a Browser 27. When the .htaccess authentication prompt appears, authenticate as an Author 2/12/16 Page 87 28. When the .htaccess authentication prompt appears, authenticate as the Administrator of PublicSite 29. When the .htaccess authentication prompt appears, authenticate as the Administrator of PrivateSub2 Findings BROWSE 1. The authentication prompt appeared. 2. After Cancel was clicked, the following appeared: “Authorization Required” This server could not verify that you are authorized to access the document you requested. Either you supplied the wrong credentials (e.g., bad password), or your browser doesn’t understand how to supply the credentials required. AUTHOR 1. The Open Web dialog box was displayed. 2. The authentication prompt appeared. 3. After Cancel was clicked, a “Name and Password Required” dialog box appeared prompting for Name and Password with the following message: “This operation requires author permission for 223.1.1.2:80. Name and password are case sensitive.” Clicking Cancel again results in a “Microsoft FrontPage” dialog box appearing with the following message: “The server could not complete your request. Contact your Internet service provider or web server administrator to make sure that the server has the FrontPage Server Extensions installed. For more specific information, click Details. 4. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 5. After attempting to authenticate as a browser unsuccessfully three times, a new “Name and Password Required” authentication prompt appeared for permission to 223.1.1.2:80. An unlimited amount of failed attempts can be tried. 6. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 7. After attempting to authenticate as the Author of PublicSite unsuccessfully three times, a new “Name and Password Required” authentication prompt appeared for permission to 223.1.1.2:80. An unlimited amount of failed attempts can be tried. 2/12/16 Page 88 8. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 9. After attempting to authenticate as the Author of PrivateSub2 unsuccessfully three times, a new “Name and Password Required” authentication prompt appeared for permission to 223.1.1.2. An unlimited amount of failed attempts can be tried. 10. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 11. Attempting to authenticate as Author of Root results in successful login. 12. Created configcase.htm with the FrontPage client. 13. The Publish Web dialog box was displayed. 14. The authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.2:80” 15. After clicking cancel, the publish web dialog box is displayed. 16. The authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.2:80” 17. After attempting to authenticate as a browser, prompt reappears until cancel is clicked. After clicking cancel, the publish web dialog box is displayed. 18. The authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.2:80” 19. After attempting to authenticate as the Author of PublicSite, prompt reappears until cancel is clicked. After clicking cancel, the publish web dialog box is displayed. 20. The authentication prompt “Name and Password Required” appeared “This operation requires author permission for 223.1.1.2:80” 21. After attempting to authenticate as the Author of PrivateSub2, prompt reappears until cancel is clicked. After clicking cancel, the publish web dialog box is displayed. ADMINISTER 1. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/ 2. After Cancel was clicked, a “401 Authorization Required” HTML page was displayed. 3. After attempting to authenticate as a browser, prompt reappears three times. Then a “401 Authorization Required” HTML page was displayed. 4. After attempting to authenticate as an author, prompt reappears three times. Then a “401 Authorization Required” HTML page was displayed. 5. The Open Web dialog box appeared. 2/12/16 Page 89 6. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PublicSite 7. After Cancel was clicked, a “Name and Password Required” dialog box appeared prompting for Name and Password with the following message: “This operation requires author permission for 223.1.1.2:80. Name and password are case sensitive.” Clicking Cancel again results in a “Microsoft FrontPage” dialog box appearing with the following message: “The server could not complete your request. Contact your Internet service provider or web server administrator to make sure that the server has the FrontPage Server Extensions installed. For more specific information, click Details. 8. The option for Security is grayed out (as there is no connection to a remote machine) 9. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 10. After three unsuccessful attempts to authenticate as a Browser, a “Name and Password Required” dialog box appeared prompting for Name and Password with the following message: “This operation requires author permission for 223.1.1.2:80. Name and password are case sensitive.” Attempting to authenticate as a Browser here results in the reappearance of the “Name and Password Required” dialog box. Clicking on cancel results in a “Microsoft FrontPage” dialog box appearing with the following message: “The server could not complete your request. Contact your Internet service provider or web server administrator to make sure that the server has the FrontPage Server Extensions installed. For more specific information, click Details. 11. The option for Security is grayed out (as there is no connection to a remote machine) 12. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2PrivateSite 13. Authenticating as Author results in successful login. 14. A “Name and Password Required” dialog box was displayed with the following message: “This operation requires administrator permission for 223.1.1.2:80. Name and password are case sensitive.” 15. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 16. After three unsuccessful attempts to authenticate as the Administrator of PublicSite, a “Name and Password Required” dialog box appeared prompting for Name and Password with the following message: “This operation requires author permission for 223.1.1.2:80. Name and password are case sensitive.” Attempting to authenticate as PublicSite Administrator here 2/12/16 Page 90 results in the repeated reappearance of the “Name and Password Required” dialog box. Clicking on cancel results in a “Microsoft FrontPage” dialog box appearing with the following message: “The server could not complete your request. Contact your Internet service provider or web server administrator to make sure that the server has the FrontPage Server Extensions installed. For more specific information, click Details. 17. The option for Security is grayed out (as there is no connection to a remote machine) 18. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 19. After authenticating as Administrator of Root, the web was opened successfully at the PrivateSite level. 20. Clicking Tools | Security results in the display of a “Permissions – PrivateSite” dialog box. 21. Authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 22. After three unsuccessful attempts to authenticate as the Administrator of PrivateSub2, a “Name and Password Required” dialog box appeared prompting for Name and Password with the following message: “This operation requires author permission for 223.1.1.2:80. Name and password are case sensitive.” Attempting to authenticate as PrivateSub2 Administrator here results in the repeated reappearance of the “Name and Password Required” dialog box. Clicking on cancel results in a “Microsoft FrontPage” dialog box appearing with the following message: “The server could not complete your request. Contact your Internet service provider or web server administrator to make sure that the server has the FrontPage Server Extensions installed. For more specific information, click Details. 23. The option for Security is grayed out (as there is no connection to a remote machine) 24. “fpremadm.exe –targetserver http://223.1.1.2:8234/scripts/fpadmcgi.exe –o enable –p 80” was entered into the Command Line 25. Access denied: Invalid password 26. 401 Authorization Required. This server could not verify that you are authorized to access the document you requested. Either you supplied the wrong credentials, or your browser doesn’t understand how to supply the credentials required. 27. 401 Authorization Required. This server could not verify that you are authorized to access the document you requested. Either you supplied the wrong credentials, or your browser doesn’t understand how to supply the credentials required. 2/12/16 Page 91 28. 401 Authorization Required. This server could not verify that you are authorized to access the document you requested. Either you supplied the wrong credentials, or your browser doesn’t understand how to supply the credentials required. 29. 401 Authorization Required. This server could not verify that you are authorized to access the document you requested. Either you supplied the wrong credentials, or your browser doesn’t understand how to supply the credentials required. 2/12/16 Page 92 Scenario – Subweb Information Gathering To determine what information an intruder can obtain about a web site if it is running FrontPage Server Extensions. Procedure ABSOLUTE REFERENCES Using a web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.2/_vti_inf.html 2. Enter http://223.1.1.2/_private/ 3. Enter http://223.1.1.2/_vti_cnf/ 4. Enter http://223.1.1.2/_vti_log/ 5. Enter http://223.1.1.2/_vti_pvt/ 6. Enter http://223.1.1.2/_vti_pvt/access.cnf 7. Enter http://223.1.1.2/_vti_pvt/botinfs.cnf 8. Enter http://223.1.1.2/_vti_pvt/bots.cnf 9. Enter http://223.1.1.2/_vti_pvt/deptodoc.btr 10. Enter http://223.1.1.2/_vti_pvt/doctodep.btr 11. Enter http://223.1.1.2/_vti_pvt/frontpg.lck 12. Enter http://223.1.1.2/_vti_pvt/linkinfo.cnf 13. Enter http://223.1.1.2/_vti_pvt/service.cnf 14. Enter http://223.1.1.2/_vti_pvt/service.lck 15. Enter http://223.1.1.2/_vti_pvt/svcacl.cnf 16. Enter http://223.1.1.2/_vti_pvt/writeto.cnf 17. Enter http://223.1.1.2/_vti_pvt/services.cnf 18. Enter http://223.1.1.2/_vti_pvt/.htaccess 19. Enter http://223.1.1.2/_vti_pvt/structure.cnf 20. Enter http://223.1.1.2/_vti_pvt/service.grp 21. Enter http://223.1.1.2/_vti_pvt/service.pwd 22. Enter http://223.1.1.2/_vti_txt/ 23. Enter http://223.1.1.2/images/ 24. Enter http://223.1.1.2/_vti_bin/ 25. Enter http://223.1.1.2/_vti_bin/fpcount.exe 26. Enter http://223.1.1.2/_vti_bin/shtml.exe 2/12/16 Page 93 27. Enter http://223.1.1.2/_vti_bin/_vti_adm/ 28. Enter http://223.1.1.2/_vti_bin/_vti_adm/admin.exe 29. Enter http://223.1.1.2/_vti_bin/_vti_adm/.htaccess 30. Enter http://223.1.1.2/_vti_bin/_vti_aut/ 31. Enter http://223.1.1.2/_vti_bin/_vti_aut/author.exe 32. Enter http://223.1.1.2/_vti_bin/_vti_aut/.htaccess 33. Enter http://223.1.1.2/Publicsite/_vti_bin/fpcount.exe 34. Enter http://223.1.1.2/Publicsite/_vti_bin/shtml.exe 35. Enter http://223.1.1.2/Publicsite/_vti_bin/.htaccess 36. Enter http://223.1.1.2/Publicsite/_vti_bin/_vti_aut/ 37. Enter http://223.1.1.2/Publicsite/_vti_bin/_vti_aut/.htaccess 38. Enter http://223.1.1.2/Publicsite/_vti_bin/_vti_aut/author.exe 39. Enter http://223.1.1.2/Publicsite/images 40. Enter http://223.1.1.2/Publicsite/_vti_pvt/service.lck 41. Enter http://223.1.1.2/Publicsite/_vti_pvt/.htaccess 42. Enter http://223.1.1.2/Publicsite/_vti_pvt/svacl.cnf 43. Enter http://223.1.1.2/Publicsite/_vti_pvt/access.cnf 44. Enter http://223.1.1.2/Publicsite/_vti_pvt/services.cnf 45. Enter http://223.1.1.2/Publicsite/_vti_pvt/service.cnf 46. Enter http://223.1.1.2/Publicsite/_vti_pvt/linkinfo.cnf 47. Enter http://223.1.1.2/Publicsite/_vti_pvt/doctodep.btr 48. Enter http://223.1.1.2/Publicsite/_vti_pvt/deptodoc.btr 49. Enter http://223.1.1.2/Publicsite/_vti_pvt/service.grp 50. Enter http://223.1.1.2/Publicsite/_vti_pvt/service.pwd 51. Enter http://223.1.1.2/Publicsite/Publicsub/images 52. Enter http://223.1.1.2/Publicsite/Publicsub/.htaccess 53. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/fpcount.exe 54. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/shtml.exe 55. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/.htaccess 56. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/_vti_adm 57. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/_vti_adm/admin.exe 58. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/_vti_adm/.htaccess 59. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/_vti_aut 60. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/_vti_aut/author.exe 2/12/16 Page 94 61. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_bin/_vti_aut/.htaccess 62. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/service.lck 63. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/.htaccess 64. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/access.cnf 65. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/services.cnf 66. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/service.cnf 67. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/linkinfo.cnf 68. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/doctodep.btr 69. Enter http://223.1.1.2/Publicsite/Publicsub/_vti_pvt/deptodoc.btr 70. Enter http://223.1.1.2/Privatesite/_vti_bin/fpcount.exe 71. Enter http://223.1.1.2/Privatesite/_vti_bin/shtml.exe 72. Enter http://223.1.1.2/Privatesite/_vti_bin/.htaccess 73. Enter http://223.1.1.2/Privatesite/_vti_bin/_vti_aut/author.exe 74. Enter http://223.1.1.2/Privatesite/_vti_bin/_vti_aut/.htaccess 75. Enter http://223.1.1.2/Privatesite/images 76. Enter http://223.1.1.2/Privatesite/_vti_pvt/service.lck 77. Enter http://223.1.1.2/Privatesite/_vti_pvt/services.cnf 78. Enter http://223.1.1.2/Privatesite/_vti_pvt/service.cnf 79. Enter http://223.1.1.2/Privatesite/_vti_pvt/linkinfo.cnf 80. Enter http://223.1.1.2/Privatesite/_vti_pvt/doctodep.btr 81. Enter http://223.1.1.2/Privatesite/_vti_pvt/deptodoc.btr 82. Enter http://223.1.1.2/Privatesite/_vti_pvt/.htaccess 83. Enter http://223.1.1.2/Privatesite/_vti_pvt/access.cnf 84. Enter http://223.1.1.2/Privatesite/_vti_pvt/svcacl.cnf 85. Enter http://223.1.1.2/Privatesite/_vti_pvt/service.grp 86. Enter http://223.1.1.2/Privatesite/_vti_pvt/service.pwd 87. Enter http://223.1.1.2/Privatesite/Privatesub/_vti_bin/fpcount.exe 88. Enter http://223.1.1.2/Privatesite/Privatesub/_vti_bin/shtml.exe 89. Enter http://223.1.1.2/Privatesite/Privatesub/_vti_bin/.htaccess 90. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/service.lck 91. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/.htaccess 92. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/access.cnf 93. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/services.cnf 94. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/service.cnf 2/12/16 Page 95 95. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/linkinfo.cnf 96. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/doctodep.btr 97. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/deptodoc.btr 98. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/service.grp 99. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/service.pwd 100. Enter http://223.1.1.2/Privatesite/Privatesub/_vit_pvt/svcacl.cnf 101. Enter http://223.1.1.2/Privatesite/Privatesub/_vti_bin/_vti_aut/author.exe 102. Enter http://223.1.1.2/Privatesite/Privatesub/_vti_bin/_vti_aut/.htaccess 103. Enter http://223.1.1.2/Privatesite/Privatesub/images DIRECTORY NAVIGATION Using a web browser from workstation 223.1.1.5, perform the following: 1. Enter http://223.1.1.2/PrivateSite/.. RPC METHODS 1. Create an HTML form to send RPC methods to 223.1.1.2 Execute the following RPC Server Methods: 2. server version 20. put documents 3. restart server 21. remove documents 4. list interpreters 22. move document 5. list libraries 23. rename url 6. list services 24. list themes 7. open service 25. put theme 8. create service 26. get theme 9. remove service 27. apply theme 10. list url-directories 28. apply border 11. create url-directory 29. apply stylesheet 12. create url-directories 30. set service meta-info 13. remove url-directory 31. set document meta-info 14. mark url-directory executable 32. add document to source control 15. list documents 33. checkout document 16. get document 34. checkin document 17. get documents 35. uncheckout document 18. get bot 36. remove links 19. put document 37. recalc control 2/12/16 Page 96 38. browser recalc 63. TextSource enumerateFields 39. set source control 64. TextSource createTable 40. rename service 65. TextSource dropTable 41. getDocsMetaInfo 66. TextSource stopIndexing 42. setDocsMetaInfo 67. TextSource startIndexing 43. query access setup 68. TextSource reIndex 44. modify access setup 69. TextSource addToIndex 45. list users 70. TextSource removeFromFutureIndexes 46. update user list 71. TextSource executeQuery 47. list groups 72. html-table add row 48. update group list 73. html-table change row 49. update group 74. html-table remove row 50. list access 75. get web struct 51. update access 76. get web struct by url 52. list special access 77. put web struct 53. update special access 78. put nav text overlays 54. change mnemonic 79. replace web struct 55. verify user 80. recalc pages 56. list domains 81. list data sources 57. get service access control 82. get database schema 58. set service access control 83. list record sources 59. TextSource enumerate 84. get record source schema 60. TextSource createTextSource 85. get query schema 61. TextSource dropTextSource 86. list drivers 62. TextSource enumerateTables 87. url to web url Findings ABSOLUTE REFERENCES 1. The HTML file _vti_inf.html 2. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 3. A “403 Forbidden” HTML message page. 4. A “403 Forbidden” HTML message page. 2/12/16 Page 97 5. A “403 Forbidden” HTML message page. 6. A “403 Forbidden” HTML message page. 7. A “403 Forbidden” HTML message page. 8. A “403 Forbidden” HTML message page. 9. A “403 Forbidden” HTML message page. 10. A “403 Forbidden” HTML message page. 11. A “403 Forbidden” HTML message page. 12. A “403 Forbidden” HTML message page. 13. A “403 Forbidden” HTML message page. 14. A “403 Forbidden” HTML message page. 15. A “403 Forbidden” HTML message page. 16. A “403 Forbidden” HTML message page. 17. A “403 Forbidden” HTML message page. 18. A “403 Forbidden” HTML message page. 19. A “403 Forbidden” HTML message page. 20. A “403 Forbidden” HTML message page. 21. A “403 Forbidden” HTML message page. 22. A “403 Forbidden” HTML message page. 23. “Index of /images” is displayed 24. A “403 Forbidden” HTML message page. 25. A “403 Forbidden” HTML message page. 26. Page displayed with following message: “Cannot run the FrontPage Server Extensions’ Smart HTML interpreter on this non-HTML page” 27. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 28. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in: ““FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page.” Three unsuccessful logins result in “401 Authorization Required” HTML message page. 29. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 2/12/16 Page 98 30. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 31. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in: ““FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page.” Three unsuccessful logins result in “401 Authorization Required” HTML message page. 32. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 33. A “500 Internal server error” HTML message page: “The page cannot be found” 34. Page displayed with following message: “Cannot run the FrontPage Server Extensions’ Smart HTML interpreter on this non-HTML page” 35. A “403 Forbidden” HTML message page. 36. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 37. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 38. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in: “FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page.” Three unsuccessful logins result in “401 Authorization Required” HTML message page. 39. “Index of /PublicSite/images” is displayed 40. A “403 Forbidden” HTML message page. 41. A “403 Forbidden” HTML message page. 42. A “403 Forbidden” HTML message page. 43. A “403 Forbidden” HTML message page. 44. A “403 Forbidden” HTML message page. 45. A “403 Forbidden” HTML message page. 46. A “403 Forbidden” HTML message page. 2/12/16 Page 99 47. A “403 Forbidden” HTML message page. 48. A “403 Forbidden” HTML message page. 49. A “403 Forbidden” HTML message page. 50. A “403 Forbidden” HTML message page. 51. “Index of /PublicSite/images” is displayed 52. Displays the .htaccess file 53. A “500 Internal server error” HTML message page: “The page cannot be found” 54. Page displayed with following message: “Cannot run the FrontPage Server Extensions’ Smart HTML interpreter on this non-HTML page” 55. A “403 Forbidden” HTML message page. 56. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 57. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in:” “FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 58. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 59. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 60. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in: “FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 61. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 62. A “403 Forbidden” HTML message page. 63. A “403 Forbidden” HTML message page. 2/12/16 Page 100 64. A “403 Forbidden” HTML message page. 65. A “403 Forbidden” HTML message page. 66. A “403 Forbidden” HTML message page. 67. A “403 Forbidden” HTML message page. 68. A “403 Forbidden” HTML message page. 69. A “403 Forbidden” HTML message page. 70. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “500 Internal server error” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 71. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in page displayed with following message: “Cannot run the FrontPage Server Extensions’ Smart HTML interpreter on this nonHTML page” Three unsuccessful logins result in “401 Authorization Required” HTML message page. 72. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 73. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in: “FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 74. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 75. “Index of /PrivateSite/images” is displayed after successful login. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 76. A “403 Forbidden” HTML message page. 77. A “403 Forbidden” HTML message page. 78. A “403 Forbidden” HTML message page. 79. A “403 Forbidden” HTML message page. 80. A “403 Forbidden” HTML message page. 81. A “403 Forbidden” HTML message page. 2/12/16 Page 101 82. A “403 Forbidden” HTML message page. 83. A “403 Forbidden” HTML message page. 84. A “403 Forbidden” HTML message page. 85. A “403 Forbidden” HTML message page. 86. A “403 Forbidden” HTML message page. 87. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “500 Internal server error” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 88. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/ Successful login results in page displayed with following message: “Cannot run the FrontPage Server Extensions’ Smart HTML interpreter on this nonHTML page” Three unsuccessful logins result in “401 Authorization Required” HTML message page. 89. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 90. A “403 Forbidden” HTML message page. 91. A “403 Forbidden” HTML message page. 92. A “403 Forbidden” HTML message page. 93. A “403 Forbidden” HTML message page. 94. A “403 Forbidden” HTML message page. 95. A “403 Forbidden” HTML message page. 96. A “403 Forbidden” HTML message page. 97. A “403 Forbidden” HTML message page. 98. A “403 Forbidden” HTML message page. 99. A “403 Forbidden” HTML message page. 100. A “403 Forbidden” HTML message page. 101. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in: “FrontPage Error. User: please report details to this site’s webmaster. Webmaster: please see the server’s system log for more details.” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 2/12/16 Page 102 102. The authentication prompt “Enter Network Password” appeared for the site http://223.1.1.2/. Successful login results in “403 Forbidden” HTML message page. Three unsuccessful logins result in “401 Authorization Required” HTML message page. 103. “Index of /PrivateSite/PrivateSub/images” is displayed after successful login. Three unsuccessful logins result in “401 Authorization Required” HTML message page. DIRECTORY NAVIGATION 1. http://223.1.1.2/index.html gets displayed. RPC METHODS All attempted commands returned the following unless otherwise noted by their complete responses. method=MethodName:4.0.2.2000 status= - status=917505 - osstatus=0 - msg=The user 'IUSR_SERVER4' is not authorized to execute the ‘MethodName’ method. - osmsg= 1. Created formpost.html with the following source: <html> <head><title>POST TEST</title> <body> <form name="rpc" method="POST" action="http://223.1.1.2/_vti_bin/shtml.exe/_vti_rpc" enctype="application/x-www-form-urlencoded" user-agent="MSFrontPage/4.0"> RPC<p> Enter a method <input name="method" type="text"><p> <input name="OK" type="submit"> </form> </body> </html> Executing the listed commands results in the following output: 2. method=server version server version= * major ver=4 * minor ver=0 * phase ver=1 * ver incr=2418 3. method=restart server:4.0.1.2418 status= 2/12/16 Page 103 * * * * status=917507 osstatus=0 msg=The method 'restart server' is not supported. osmsg= 4. method=list interpreters:4.0.1.2418 status= * status=917507 * osstatus=0 * msg=The method 'list interpreters' is not supported. * osmsg= 5. method=list libraries:4.0.1.2418 status= * status=917507 * osstatus=0 * msg=The method 'list libraries' is not supported. * osmsg= 6. method=list services:4.0.1.2418 services_list= * service_name= * meta_info= * vti_casesensitiveurls * IX|1 * vti_textextensions * SX|.txt. * vti_featurelist * VX|vti_ACGroups vti_ServiceMarkUrlDirBrowse vti_ServiceMarkUrlDirScript vti_ServiceMarkUrlDirExec vti_ServiceMarkUrlDirExec vti_ServerEmailTransport vti_ServerIndexServer vti_ServerODBC vti_ServerASP * vti_dependenciesood * IR|0 * vti_httpdversion * SX|Apache/1.3.1 (Unix) * vti_navbuttonuplabel * SR|Up * vti_webservertype * SR|apache * vti_categories * VR|Travel Expense\ Report Business Competition Goals/Objectives Ideas Miscellaneous Waiting VIP In\ Process Planning Schedule * vti_textindexood * IR|0 * vti_navbuttonnextlabel * SR|Next * vti_approvallevels * VR|Content\ Review Legal\ Review Code\ Review Manager\ Review * vti_timecreated 2/12/16 Page 104 * * * TR|28 Dec 1998 22:10:50 -0000 * vti_extenderversion * SR|4.0.1.2418 * vti_navbuttonprevlabel * SR|Back * vti_longfilenames * IX|1 * vti_welcomenames * VX|index.html * vti_insecureserverurl * SR|http://223.1.1.2 * vti_disableautoimgsizeexts * SX|.asp * vti_oldestcompatibleversion * SR|2.0.0.0 * vti_restartmanual * IX|0 * vti_defaultcharset * SR|windows-1252 * vti_defaultlanguage * SR|en * vti_publishmetainfokeys * VR|vti_assignedto vti_approvallevel vti_categories vti_description * vti_hassearchbot * BR|false * vti_autorecalc * IX|1 * vti_htmlextensions * SX|.htm.html.shtml.shtm.stm.htt.htx.asp.alx.asa. * vti_createpostinfo * BX|false * vti_navbuttonhomelabel * SR|Home service_name=/PrivateSite meta_info= * vti_casesensitiveurls * IX|1 * vti_textextensions * SX|.txt. * vti_featurelist * VX|vti_ACGroups vti_ServiceMarkUrlDirBrowse vti_ServiceMarkUrlDirScript vti_ServiceMarkUrlDirExec vti_ServiceMarkUrlDirExec vti_ServerEmailTransport vti_ServerIndexServer vti_ServerODBC vti_ServerASP * vti_httpdversion * SX|Apache/1.3.1 (Unix) * vti_ignorekeyboard * IR|0 * vti_navbuttonuplabel * SR|Up 2/12/16 Page 105 * * * * * * * * vti_dependenciesood IR|0 vti_webservertype SR|apache vti_categories VR|Travel Expense\ Report Business Competition Goals/Objectives Ideas Miscellaneous Waiting VIP In\ Process Planning Schedule * vti_navbuttonnextlabel * SR|Next * vti_approvallevels * VR|Content\ Review Legal\ Review Code\ Review Manager\ Review * vti_timecreated * TR|28 Dec 1998 22:33:30 -0000 * vti_extenderversion * SR|4.0.1.2418 * vti_navbuttonprevlabel * SR|Back * vti_longfilenames * IX|1 * vti_welcomenames * VX|index.html * vti_insecureserverurl * SR|http://223.1.1.2 * vti_disableautoimgsizeexts * SX|.asp * vti_oldestcompatibleversion * SR|2.0.0.0 * vti_restartmanual * IX|0 * vti_defaultcharset * SR|iso-8859-1 * vti_defaultlanguage * SR|en * vti_publishmetainfokeys * VR|vti_assignedto vti_approvallevel vti_categories vti_description * vti_htmlextensions * SX|.htm.html.shtml.shtm.stm.htt.htx.asp.alx.asa. * vti_navbuttonhomelabel * SR|Home service_name=/PublicSite meta_info= * vti_casesensitiveurls * IX|1 * vti_textextensions * SX|.txt. * vti_featurelist * VX|vti_ACGroups vti_ServiceMarkUrlDirBrowse vti_ServiceMarkUrlDirScript vti_ServiceMarkUrlDirExec vti_ServiceMarkUrlDirExec vti_ServerEmailTransport vti_ServerIndexServer vti_ServerODBC vti_ServerASP 2/12/16 Page 106 * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * * vti_httpdversion SX|Apache/1.3.1 (Unix) vti_ignorekeyboard IR|0 vti_navbuttonuplabel SR|Up vti_dependenciesood IR|0 vti_webservertype SR|apache vti_categories VR|Travel Expense\ Report Business Competition Goals/Objectives Ideas Miscellaneous Waiting VIP In\ Process Planning Schedule vti_navbuttonnextlabel SR|Next vti_approvallevels VR|Content\ Review Legal\ Review Code\ Review Manager\ Review vti_timecreated TR|28 Dec 1998 22:35:13 -0000 vti_extenderversion SR|4.0.1.2418 vti_navbuttonprevlabel SR|Back vti_longfilenames IX|1 vti_welcomenames VX|index.html vti_insecureserverurl SR|http://223.1.1.2 vti_disableautoimgsizeexts SX|.asp vti_oldestcompatibleversion SR|2.0.0.0 vti_restartmanual IX|0 vti_defaultcharset SR|iso-8859-1 vti_defaultlanguage SR|en vti_publishmetainfokeys VR|vti_assignedto vti_approvallevel vti_categories vti_description vti_htmlextensions SX|.htm.html.shtml.shtm.stm.htt.htx.asp.alx.asa. vti_navbuttonhomelabel SR|Home 7. open service 8. method=create service:4.0.1.2418 status= * status=917506 2/12/16 Page 107 * osstatus=0 * msg=The method 'create service' is not recognized. * osmsg= 9. remove service 10. list url-directories 11. create url-directory 12. create url-directories 13. remove url-directory 14. mark url-directory executable 15. list documents 16. get document 17. HTTP 500 - Internal server error Internet Explorer 18. get bot 19. put document 20. put documents 21. remove documents 22. move document 23. rename url 24. list themes 25. put theme 26. HTTP 500 Internal server error Page cannot be found 27. apply theme 28. apply border 29. apply stylesheet 30. set service meta-info 31. set document meta-info 32. add document to source control 33. checkout document 34. checkin document 35. uncheckout document 36. remove links 37. recalc control 38. method=browser recalc:4.0.1.2418 status= * status=589852 * osstatus=0 * msg=Unable to recalculate links for "". * osmsg= 39. set source control 40. rename service 41. getDocsMetaInfo 2/12/16 Page 108 42. setDocsMetaInfo 43. query access setup 44. modify access setup 45. list users 46. update user list 47. list groups 48. update group list 49. update group 50. list access 51. update access 52. list special access 53. update special access 54. change mnemonic 55. verify user 56. list domains 57. get service access control 58. set service access control 59. TextSource enumerate 60. method= TextSource createTextSource:4.0.1.2418 status= * status=917506 * osstatus=0 * msg=The method ' TextSource createTextSource' is not recognized. * osmsg= 61. TextSource dropTextSource 62. TextSource enumerateTables 63. TextSource enumerateFields 64. TextSource createTable 65. TextSource dropTable 66. TextSource stopIndexing 67. TextSource startIndexing 68. TextSource reIndex 69. TextSource addToIndex 70. TextSource removeFromFutureIndexes 71. TextSource executeQuery 72. html-table add row 73. html-table change row 74. html-table remove row 75. get web struct 76. get web struct by url 77. put web struct 78. put nav text overlays 79. replace web struct 80. recalc pages 81. list data sources 82. get database schema 83. list record sources 84. get record source schema 2/12/16 Page 109 85. get query schema 86. list drivers 87. method=url to web url:4.0.1.2418 status= * status=262145 * osstatus=0 * msg=Missing parameter 'url' for function 'url to web url' * osmsg= 2/12/16 Page 110 Scenario – File Execution To determine if an Author can use scripts and other executable files to gather information from or gain access to the system. Procedure UPLOADING FILES Pre-Configuration Modification Using the FrontPage client from workstation 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Select a local web 3. Choose File | Import… 4. Click Add File… 5. Select [ps - a unix executable file], Click Open, Click OK 6. Choose File | Publish Web… 7. Enter http://223.1.1.2/PublicSite 8. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 9. Click Publish 10. Choose File | Import… 11. Click Add File… 12. Select ShellTest.sh, Click Open, Click OK 13. Choose File | Publish Web… 14. Enter http://223.1.1.2/PublicSite 15. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 16. Click Publish 17. Rename [ ps ] to [ ps.aut ] in the local web 18. Choose File | Publish Web… 19. Enter http://223.1.1.2/PublicSite 20. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 21. Click Publish 22. Rename testasp.asp to testasp.aut in the local web 23. Choose File | Publish Web… 24. Enter http://223.1.1.2/PublicSite 25. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 2/12/16 Page 111 26. Click Publish Post-Configuration Modification Make the following modification: In file /usr/local/frontpage/version4.0/frontpage.cnf. Ensure that the entry NoExecutableCgiUpload is present with a value of 0 Using the FrontPage client from workstation 223.1.1.5, perform the following: 27. Choose File | Open Web… 28. Select a local web 29. Choose File | Import… 30. Click Add File… 31. Select [ Unix executable file ], Click Open, Click OK 32. Choose File | Publish Web… 33. Enter http://223.1.1.2/PublicSite 34. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 35. Click Publish 36. Choose File | Import… 37. Click Add File… 38. Select ShellTest.sh, Click Open, Click OK 39. Choose File | Publish Web… 40. Enter http://223.1.1.2/PublicSite 41. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 42. Click Publish Restore the < config file > to the previous state as above. RENAMING UPLOADED FILES Using the FrontPage client from workstation 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Enter http://223.1.1.2/PublicSite 3. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 4. Rename someting.aut to [ Unix executable file ] 5. Rename ShellTest.aut to ShellTest.sh EXECUTING FILES Using the FrontPage client from workstation 223.1.1.5, perform the following: 1. Choose File | Open Web… 2. Enter http://223.1.1.2/PublicSite 2/12/16 Page 112 3. When the .htaccess authentication prompt appears, authenticate as the Author of PublicSite 4. Move [ Unix executable file ] into directory exedir (marked executable) Using the web browser from 223.1.1.5, perform the following: 5. Enter http://223.1.1.2/PublicSite/exedir/[ Unix executable file ] 6. Enter http://223.1.1.2/PublicSite/ShellTest.sh Findings UPLOADING FILES 1. The Open Web dialog box was displayed 2. The web “C:\WINNT\Profiles/administrator\My Webs” was selected. 3. The Import dialog box was displayed 4. The Add File to Import List file section box was displayed 5. “ps” was added as a file to the web 6. The Publish Web dialog box was displayed 7. http://223.1.1.2/PublicSite was entered in the “Specify the location” field of the Publish Web dialog box 8. The authentication prompt appeared requesting author permission for 223.1.1.2:80, and the Author of PublicSite was used to authenticate 9. Did not click Publish being that it published automatically after authenticating 10. The Import dialog box was displayed 11. The Add File to Import List file section box was displayed 12. “ShellTest.sh” was added as a file to the web 13. The Publish Web dialog box was displayed 14. http://223.1.1.2/PublicSite was entered in the “Specify the location” field of the Publish Web dialog box 15. The .htaccess authentication prompt did not appear being that authentication was already done before (step #8) 16. Did not click Publish being that it published automatically 17. Renamed “ps” to “something.aut” 18. The Publish Web dialog box was displayed 19. http://223.1.1.2/PublicSite was entered in the “Specify the location” field of the Publish Web dialog box 20. The .htaccess authentication prompt did not appear being that authentication was already done before (step #8) 2/12/16 Page 113 21. Did not click Publish being that it attempted to publish automatically and had the following dialog box as a result: Do you want to remove this file? The file ‘ps’ exists on the destination server but does not exist in the current Web. Would you like FrontPage to remove it from ‘/PublicSite’? 22. Renamed “ShellTest.sh” to “ShellTest.aut” 23. The Publish Web dialog box was displayed 24. http://223.1.1.2/PublicSite was entered in the “Specify the location” field of the Publish Web dialog box 25. The .htaccess authentication prompt did not appear being that authentication was already done before (step #8) 26. Did not click Publish being that it attempted to publish automatically and had the following dialog box as a result: Do you want to remove this file? The file ‘ShellTest.sh’ exists on the destination server but does not exist in the current Web. Would you like FrontPage to remove it from ‘/PublicSite’? 27. The Open Web dialog box was displayed 28. The web “C:\WINNT\Profiles/administrator\My Webs” was selected. 29. The Import dialog box was displayed 30. The Add File to Import List file section box was displayed 31. “ps” was added as a file to the web 32. The Publish Web dialog box was displayed 33. http://223.1.1.2/PublicSite was entered in the “Specify the location” field of the Publish Web dialog box 34. The authentication prompt appeared requesting author permission for 223.1.1.2:80, and the Author of PublicSite was used to authenticate 35. Did not click Publish being that it published automatically after authenticating 36. The Import dialog box was displayed 37. The Add File to Import List file section box was displayed 38. “ShellTest.sh” was added as a file to the web 39. The Publish Web dialog box was displayed 40. http://223.1.1.2/PublicSite was entered in the “Specify the location” field of the Publish Web dialog box 41. The .htaccess authentication prompt did not appear being that authentication was already done before (step #34) 42. Did not click Publish being that it published automatically after authenticating 2/12/16 Page 114 RENAMING UPLOADED FILES 1. The Open Web dialog box was displayed 2. http://223.1.1.2/PublicSite was entered in the “Folder name” field of the Open Web dialog box 3. The authentication prompt appeared requesting authentication information for resource: 223.1.1.2:80, and the Author of PublicSite was used to authenticate 4. Renamed “ps.aut” to “ps” 5. Renamed “ShellTest.aut” to “ShellTest.sh” EXECUTING FILES 1. The Open Web dialog box was displayed 2. http://223.1.1.2/PublicSite was entered in the “Folder name” field of the Open Web dialog box 3. The authentication prompt appeared requesting authentication information for resource: 223.1.1.2:80, and the Author of PublicSite was used to authenticate 4. Unable to move Unix executable “ps” into directory exedir (marked executable) 5. HTTP 404 – File not found 6. File Download dialog box gets displayed 2/12/16 Page 115 Objective - Penetration Determine what vulnerabilities exist after FrontPage Server Extensions are installed on a website. Scenario – Port Discovery To determine what ports are opened or listening on a FrontPage web. Procedure 1. Run a port scanner from 223.1.1.5 Findings 1. The following ports were open: Port 80 – For communicating via HTTP Port 8234 – The port configured for remote administration 2/12/16 Page 116 Objective - Data Capturing Determine if the possibility exists to capture information as it is passed to the FrontPage Server Extensions. Scenario – Password Gathering To determine if passwords are passed in clear text during the authentication process. Procedure WEB BROWSER ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 2. Enter http://223.1.1.2:8234/fpadmin.htm 3. When the .htaccess authentication prompt appears, enter the username Administrator with the correct password; Using the network sniffer from 223.1.1.10, perform the following: 4. Disable data capture 5. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 6. Enter http:// 223.1.1.2/PrivateSite/ 7. When the .htaccess authentication prompt appears, enter the username Administrator with the correct password; Using the network sniffer from 223.1.1.10, perform the following: 8. Disable data capture FRONTPAGE CLIENT ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 2. Choose File | Open Web… 3. Enter http://223.1.1.2/ 4. When the .htaccess authentication prompt appears, enter the username Administrator with the correct password Using the network sniffer from 223.1.1.10, perform the following: 2/12/16 Page 117 5. Disable data capture 6. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 7. Create an HTML file named sniffcase.htm 8. Choose File | Publish Web… 9. Enter http://223.1.1.2/ 10. When the .HTACCESS authentication prompt appears, enter the username Administrator with the correct password Using the network sniffer from 223.1.1.10, perform the following: 11. Disable data capture COMMAND LINE ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the Command Line from 223.1.1.5, perform the following: 2. From the Command Line enter “fpremadm.exe –targetserver http://223.1.1.2:8234/scripts/fpadmdll.dll -o enable –p 80 ” 3. When the .htaccess authentication prompt appears, enter the username Administrator with the correct password Using the network sniffer from 223.1.1.10, perform the following: 4. Disable data capture Using the network sniffer from 223.1.1.10, perform the following: 5. Enable the network sniffer to start capturing data Using the Command Line from 223.1.1.5, perform the following: 6. From the Command Line enter “fpremadm.exe –adminusername Administrator – adminpassword Administrator –targetserver http://223.1.1.2:8234/scripts/fpadmdll.dll -o enable –p 80” Using the network sniffer from 223.1.1.10, perform the following: 7. Disable data capture Findings WEB BROWSER ACCESS 1. Network Monitor Capture | Start was executed 2. An “Enter Network Password” dialog box is displayed prompting for username and password for site 223.1.1.2 2/12/16 Page 118 3. Authenticating with the correct password for Administrator grants access to the site. 4. Network Monitor Capture | Stop was executed 5. Network Monitor Capture | Start was executed 6. An “Enter Network Password” dialog box is displayed prompting for username and password for site 223.1.1.2 7. Authenticating with the correct password for PrivateSiteAdmin grants access to the site. 8. Network Monitor Capture | Stop was executed FRONTPAGE CLIENT ACCESS 1. Network Monitor Capture | Start was executed 2. The “Open Web” dialog box appears 3. http://223.1.1.2 was entered in the “Folder name” field of the Open Web dialog box 4. Attempting to authenticate with the correct password for Administrator grants access. 5. Network Monitor Capture | Stop was executed 6. Network Monitor Capture | Start was executed 7. Created sniffcase.htm 8. The “Publish Web” dialog box is displayed 9. http://223.1.1.2 was entered in the “Specify the location” field of the Publish Web dialog box 10. Attempting to authenticate with the correct password for Administrator grants access. 11. Network Monitor Capture | Stop was executed COMMAND LINE ACCESS 1. Network Monitor Capture | Start was executed 2. “fpremadm.exe –targetserver http://223.1.1.2:8234/scripts/fpadmdll.dll -o enable –p 80 ” was entered into the Command Line 3. Authenticating as Administrator with the correct password results in “Authoring enabled.” 4. Network Monitor Capture | Stop was executed 5. Network Monitor Capture | Start was executed 6. Port 80: Authoring enabled. 7. Network Monitor Capture | Stop was executed 2/12/16 Page 119 Scenario – Confidential Information Gathering To determine if confidential information is passed in clear text during administration and authoring. Procedure WEB BROWSER ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 2. Enter http://223.1.1.2:8234/fpadmin.htm 3. When the .htaccess authentication prompt appears, enter the username Administrator with the correct password; Perform the following functions 4. Renaming a Subweb a. b. c. d. In the contents listing, click Rename Subweb. In the Virtual Host Name field, type 223.1.1.2 In the Port Number field, type 80. In the Subweb Name field, type TestSub This should be the path to the subweb's top-level directory, from the server’s toplevel directory. e. In the New Subweb Name field, type NewSubName f. Click Rename Subweb. 5. Setting Permissions for a User a. b. c. d. In the contents listing, click User Permissions. In the Virtual Host Name field, type 223.1.1.2 In the Port Number field, type 80 In the Web Name field, type / This should be the path to the web's top-level directory, from the server's toplevel directory. To specify the root web, type a forward slash (/). e. In the Username field, type TestGuy f. Select the level of access for the user: Browse, Author, and Administrate Access. g. Click Change Permissions. 6. Setting Permissions for IP Addresses a. In the contents listing, click IP Address Permissions. b. In the Virtual Host Name field, type 223.1.1.2 c. In the Port Number field, type 80 2/12/16 Page 120 d. In the Web Name field, type / This should be the path to the web's top-level directory, from the server's toplevel directory. To specify the root web, type a forward slash (/). e. In the IP Address field, enter the IP address of the computer or set of computers whose permissions you are adding, removing, or changing. Enter 223.1.1.3 f. Select the level of access for the computer or group of computers: Browse, Author, and Administrate Access. g. Click Change Permissions. 7. Specifying That a Folder Can Contain Programs a. b. c. d. In the contents listing, click Set Directory Executable. In the Virtual Host Name field, type 223.1.1.2 In the Port Number field, type 80 In the Web Name field, type / This should be the path to the web's top-level directory, from the server's toplevel directory. To specify the root web, type a forward slash (/). e. In the Directory URL field, type a URL relative to the top-level directory of the FrontPage-extended web. Enter NewSubName f. Click Set Directory Executable. 8. Removing the FrontPage Server Extensions from a Virtual Server a. b. c. d. In the contents listing, click . In the Virtual Host Name field, type 223.1.1.2 In the Port Number field, type 80 In the Full Uninstall list, click Yes to uninstall the FrontPage Server Extensions without leaving any FrontPage meta-information in the web. Click No to leave some FrontPage meta-information in the web. If you select Yes and then reinstall the FrontPage Server Extensions on the virtual server, FrontPage subwebs will not be automatically recreated. If you select No, any subwebs on the server will be recreated when the FrontPage Server Extensions are reinstalled. Click No. e. Click Uninstall. Using the network sniffer from 223.1.1.10, perform the following: 9. Disable data capture 10. Enable the network sniffer to start capturing data Using the web browser from 223.1.1.5, perform the following: 11. Enter http:// 223.1.1.2/PrivateSite/ 12. When the .htaccess authentication prompt appears, enter the username PrivateSiteAdmin with the correct password; Using the network sniffer from 223.1.1.10, perform the following: 13. Disable data capture 2/12/16 Page 121 FRONTPAGE CLIENT ACCESS Using the network sniffer from 223.1.1.10, perform the following: 1. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 2. Choose File | Open Web… 3. Enter http://223.1.1.2/PrivateSite/ 4. When the .HTACCESS authentication prompt appears, enter the username PrivateSiteAdmin with the correct password 5. Double-click on publcase.htm 6. Modify the contents 7. Save the file Using the network sniffer from 223.1.1.10, perform the following: 8. Disable data capture 9. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 10. Create an HTML file named publ2case.htm 11. Choose File | Publish Web… 12. Enter http://223.1.1.2/PrivateSite/ 13. When the .HTACCESS authentication prompt appears, enter the username PrivateSiteAdmin with the correct password Using the network sniffer from 223.1.1.10, perform the following: 14. Disable data capture 15. Enable the network sniffer to start capturing data Using the FrontPage client from 223.1.1.5, perform the following: 16. Choose File | Import… 17. Select the Import Web Wizard and click OK 18. On the “Choose Source” Screen, a. Select the “From a World Wide Web site” radio button b. Enter 223.1.1.2 in the Location field and click Next 19. On the “Choose Download Amount” Screen, Click Next 20. On the “Finish” Screen, Click Finish Using the network sniffer from 223.1.1.10, perform the following: 21. Disable data capture 2/12/16 Page 122 Findings WEB BROWSER ACCESS 1. Network Monitor Capture | Start was executed 2. The authentication prompt “Enter Network Password” appeared for site http://223.1.1.2 3. Administrator with correct password logged in successfully 4. The Form Submission results page displayed the following: Starting rename, port: 80, web: "TestSub" Created: 05 Jan 1999 22:08:54 -0000 Version: 4.0.1.2418 5. The Form Submission results page displayed the following: Starting security, port: 80, web: "/" Created: 05 Jan 1999 22:08:54 -0000 Version: 4.0.1.2418 Port 80: User "TestGuy" and IP address "" added to administrators for web "/" 6. The Form Submission results page displayed the following: Starting security, port: 80, web: "/" Created: 05 Jan 1999 22:08:54 -0000 Version: 4.0.1.2418 No user will be added. Port 80: IP address "223.1.1.3" added to users for web "/" 7. The Form Submission results page displayed the following: Starting setdirexec, port: 80, web: "/" Created: 05 Jan 1999 22:08:54 -0000 Version: 4.0.1.2418 8. The Form Submission results page displayed the following: Starting fulluninstall, port: 80, web: “root web” Created: 05 Jan 1999 22:08:54 –0000 Version: 4.0.1.2418 9. Network Monitor Capture | Stop was executed 10. Network Monitor Capture | Start was executed 11. The “Enter Network Password” dialog box was displayed for site 223.1.1.2 12. Authenticating with the correct password for PrivateSiteAdmin successfully opens the page. 13. Network Monitor Capture | Stop was executed FRONTPAGE CLIENT ACCESS 1. Network Monitor Capture | Start was executed 2. The “Open Web” dialog box gets displayed 3. The authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 2/12/16 Page 123 4. Authentication is successful as PrivateSiteAdmin with the correct password and the web was opened at the PrivateSite level 5. The contents of publcase.htm were displayed in the document window 6. The contents were modified to include the phrase: “contents now modified” 7. The file was successfully saved. 8. Network Monitor Capture | Stop was executed 9. Network Monitor Capture | Stop was executed 10. An HTML file named publ2case.htm was created with the FrontPage client 11. The Publish Web dialog box was displayed 12. The authentication prompt “Enter Network Password” appeared for resource http://223.1.1.2/PrivateSite 13. The file was successfully published as indicated by the dialog box. 14. Network Monitor Capture | Stop was executed 15. Network Monitor Capture | Start was executed 16. The “New” web site dialog box was displayed 17. The “Import Web Wizard – Choose Source” dialog box was displayed 18. The “Import Web Wizard – Choose Download Amount” dialog box was displayed 19. The “Import Web Wizard – Finish” dialog box was displayed 20. The Web was imported and displayed 21. Network Monitor Capture | Stop was executed 2/12/16 Page 124 About the Authors and Evaluation Team Eric Budke Eric is a Technical Specialist and focuses on a variety of UNIX platforms (SunOS, Solaris, AIX, HP-UX, Linux, BSD, IRIX), Firewalls (Gauntlet, Raptor, Firewall-1), Internet Security (topologies and protection strategies), Internet Services (web, BIND/DNS, DHCP, Certificate Servers),TCP/IP Networking, Penetration Testing (internal and external) and system security assessments. In this capacity he has reviewed and implemented a variety of UNIX platforms, firewalls and network topologies and assessed and implemented appropriate security controls. He has also participated on numerous Attack and Penetration "Tiger" teams. Neil Cooper, CISSP Neil is a Senior Technical Manager and has over 18 years experience in data processing. Neil has primary responsibility for leading the Windows NT security service line for PricewaterhouseCoopers and is part of the technical team for UNIX, Windows NT, Netware, and Internet Security Services. Neil's technical capabilities include knowledge of Windows NT, UNIX, TCP/IP, X-Windows, as well as mid-range systems. He co-authored Microsoft Windows NT 4.0: Security, Audit, and Control. Todd M Feinman Todd is a Senior Technical Specialist and is focusing on Windows NT, Internet and Electronic Commerce security including network privacy, cryptography, firewalls, and protection strategies. In this capacity, he has reviewed system configurations, network topologies, and assessed the appropriateness of the related security controls. Todd is a co-author of the book Microsoft Windows NT 4.0: Security and Audit and Control, published by Microsoft Press and a principal author of Electronic Commerce: Security, Risk Management, and Control, published by Irwin/McGraw Hill, 1999. He has also co-authored various papers on topics in information security including a paper entitled Security Basics and a professional practices booklet entitled Electronic Commerce and the Internet. 2/12/16 Page 125 David J. Goldman David Goldman is a Technical Specialist focusing on Windows NT and UNIX operating systems as well as the Internet and other networking environments. In this capacity he has reviewed system configurations, security architectures, and assessed the appropriateness of the related security controls. He also has experience in web-development and electronic business application design. Christopher O'Hara, CISSP Chris is a Technical Manager and focuses on a variety of UNIX variants (SunOS, Solaris, IBM AIX, Linux, HP-UX), Internet security (firewalls, topologies, protection strategies), TCP/IP networking, remote access connectivity, and DEC VAX/VMS data security assessments. In this capacity he has reviewed system configurations, network topologies, network access points, and assessed the appropriateness of the related security controls. Amy Shum Amy Shum is a Technical Specialist and focuses on the UNIX operating system and other networking environments. In this capacity she has reviewed system configurations, network architectures, and assessed the appropriateness of the related security controls. Andrew Toner Andrew is a nationally recognized leader in the field of information security with over fourteen years of experience developing solutions for the security challenges of major corporations such as Prudential Insurance Company, NationsBank, Chase, Bankers Trust and ConAgra. During this period, he developed many practices and methodologies that helped shape the field of information security consulting. He is a partner in the PricewaterhouseCoopers' Resource Protection Consulting Practice with responsibility for the New York/Metro region. Andrew has written articles for the InfoSecurity Products News and has been quoted in several major journals, such as Information Week, American Banker and Crains New York Business. 2/12/16 Page 126 Danny Wen Danny is a support technician and focuses on the UNIX operating system and other networking environments. Danny is earning a Bachelors of Science in Computer Science from Cornell University. Christopher Yap Christopher Yap is a Technical Specialist and focuses on the UNIX operating system and other networking environments. In this capacity he has reviewed system configurations, network architectures, and assessed the appropriateness of the related security controls. 2/12/16 Page 127