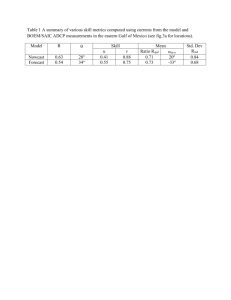
SSH

CS265 Term Paper Spring 2003
SSH: The Secure Shell
CS265 Term Paper
Rachana Maheswari
April 14 2003
Submitted to Dr. Mark Stamp as fulfillment of the Term Paper Requirement for CS265, Spring 2003
SSH: The Secure Shell 1 Rachana Maheswari
CS265 Term Paper Spring 2003
Abstract
Most widely used utilities to login through a network in Unix environment are telnet and rlogin.
In both of the above cases user's login name and password are transmitted as clear text. In addition, data transmission after login is also in clear text. An intruder can easily see such data by using freeware programs. Secure shell provides a secure channel for data transmission.
SSH, the Secure Shell is a popular, powerful, software-based approach to network security.
This paper explains what are secure shell (SSH), brief history, its features and its security mechanisms. For the most part, this paper assumes SSH is implemented on Unix platform.
Secure shell is a protocol as well as a product. The protocol is indicated as SSH-1 for version 1 and SSH-2 for version 2.Finally, the differences of SSH-1 and SSH-2 features are covered.
Brief history of SSH
Tatu Ylonen developed SSH (secure shell) in 1995 while he was working as a researcher at the
Helsinki University of Technology, Finland. The product SSH was developed as an answer to a network attack on the university computer. In the same year SSH was released as free software for public use. Later in the year, Ylonen published the protocol SSH-1 as an IETF (Internet
Engineering Task Force) draft. Term SSH is widely used to refer to the protocol as well as the software.
To commercialize and further popularize the use of SSH, Ylonen founded SSH communications security Ltd., in late 1995 (http://www.ssh.com). SSH-2 protocol was released in 1996, which in essence fixed the bugs in SSH-1.But SSH-2 did not have backward compatibility with SSH-1.
The product SSH2 was released in 1998. Unlike original version, SSH-2 was more for paid commercial use. Even after the release of SSH-2, people continue to use SSH (or known as
SSH1) because of its useful features. A freeware version of SSH known as openssh
(http://www.openssh.com, mainly developed under openBSD project), is available. Now SSH is ported freely on Linux and is available in major flavors of Unix.
What is SSH?
SSH is a powerful, convenient approach to protecting communications on a computer network.
Through secure encryption technologies and authentication, SSH supports secure remote logins, secure remote command execution, secure file transfers, and other secure network services.
Secure shell provides a secure channel for data transmission. To some extent the same secure shell is a misnomer; it is not a shell like born shell or korn shell. SSH is not a command interpreter. SSH does not give the user a prompt to execute commands like born shell or korn shell. It is only a secure pipe to open up a command interpreter. SSH encrypts any data sent through this pipe. SSH automatically decrypts incoming encrypted data. SSH uses modern,
SSH: The Secure Shell 2 Rachana Maheswari
CS265 Term Paper Spring 2003 secure encryption algorithms and is effective enough to be found within mission critical applications.
SSH has a client server architecture. An SSH server program, typically installed by a system administrator accepts or rejects incoming connections to its host computer. In most Unix SSH implementations, the server is sshd . Users then run SSH client programs to make requests to the
SSH server. In SSH1, SSH2 and OpenSSH, the major clients are ssh and scp .
Features of SSH
The major features of the Secure Shell protocol are Privacy, Integrity, Authentication,
Authorization, and Forwarding.
Privacy: of data is obtained via strong end-to-end encryption that is based on random keys which are securely negotiated for that session, and then destroyed when the session is over. SSH supports encryption algorithms such as DES, IDEA, Blowfish, ARC-
FOUR, and triple-DES. The next section goes into the details of the security mechanism.
Integrity: .SSH1 uses a weak method which is a 32 bit Cyclic Redundancy Check
(CRC-32) on the unencrypted data in each packet.SSH2 uses keyed hash algorithms based on MD5 and SHA1.
Authentication: involves server authentication which is done using the servers host key, and client authentication is usually done by password authentication or public key authentication.
Authorization: occurs after authentication, and is controlled at a server wide level or per account basis.
SSH supports Forwarding , means encapsulating another TCP based service such as
Telnet within an SSH session. For example, by forwarding telnet through SSH, all data are automatically encrypted, integrity checked, and authenticated using SSH credentials.
SSH Security Mechanism
This section gives an overall picture of how the features mentioned in the above section are implemented in Secure Shell to guarantee security of a network connection. Four keys are used in SSH to establish a secure connection. They are the user key, session key, host key and server key. Of these, the session key is private and all the other three keys are public keys.
Establishing the Secure Connection
Typically, the client initiates the connection by sending a request to the TCP port of the SSH server. At this point all communication is un-encrypted. Server reveals it's SSH protocol version to the client. If the client and server decide their versions are compatible, the connection process continues; other wise either party may decide to terminate the connection. After protocol version is accepted, client and server switch to a packet-based protocol.
SSH: The Secure Shell 3 Rachana Maheswari
CS265 Term Paper Spring 2003
SSH server then sends the following to the client - its host key which is used to identify itself, the server key which helps to establish the secure connection, a list of supported encryption, compression and authentication methods, and a sequence of eight random bytes. Client checks identity of server by using the host key, and checking it in the known-hosts database. If Client rejects host key, connection ends. Client then, has to prove its identity by including the eight random bytes called check bytes in its next response. This is a built-in mechanism to prevent IP spoofing.
In the next step, the client generates a session key, which is a private key used to encrypt and decrypt the real data. The SSH client generates the session key and encrypts it with the public host key it received from the server. Generated output is again encrypted with the server key the client received from the server. This double encrypted session key is then sent to the server along with the check bytes and acceptable algorithm. Server then decrypts the session key it received.
It then sends to the client a confirmation (acknowledgement) which is encrypted with this session key. Once the client gets the confirmation from the proper server (which accepted and deciphered the session key encrypted with the host key verified earlier), the server authentication is also confirmed , and the real encrypted SSH communication starts. Session key is encrypted twice for added security. Server key changes periodically, so even if unauthorized client has the old key, for a new session such unauthorized client cannot create a valid session key. Entire process of establishing a secure connection is shown in Figure 1.
SSH: The Secure Shell
Figure 1
4 Rachana Maheswari
CS265 Term Paper Spring 2003
Client authentication
After the secure connection is established, the client attempts to authenticate itself. There are many methods of authentication. Here, we discuss two widely used ones which are password authentication and public-key authentication.
Password authentication is simple. User on the client machine types in the password, which is sent through the encrypted channel. Server uses the password authentication mechanism of server operating system to check the validity. User is granted login connection on successful validation against the password database. This authentication mechanism does not need any additional configuration on the server side.
In public key authentication, client sends the server a part of authorization private key. Server receives it and checks for the corresponding public key in ~/. ssh/authorized_keys (where ~ stands for user's home directory). If the server finds the corresponding public part, connection proceeds otherwise connection is ended. If it proceeds, server checks for authorization restrictions and proceed accordingly. After successful authorization, server generates random
256-bit challenge string, encrypts it with clients public key and send to client. Client decrypts it with private key, then generates a hash value with a session identifier and sends hash value to server. Server generates hash value of the challenge, if those match; session is authenticated, otherwise not. The public key method is the most secure authentication method for SSH.
Additional features of SSH2
SSH-2 is a new protocol, an improvement over SSH-1. Recently, SSH communications security
Ltd., introduced SSH-3. SSH-2, unlike SSH-1 is a combination of three separate protocols. These three modular protocols are SSH-Transport layer protocol, SSH-Authentication protocol and
SSH-Connection protocol. SSH-1 has a single host table for server and client authentication.
SSH-2 keeps 2 different tables, one each for server authentication and client authentication.
Servers running SSH-2 can also run SSH-1 to take care of clients running SSH-1. Unlike SSH-1, host based authentication is independent of client machines network used. Thus, a client machine can be behind a proxy server or even can use NAT (Network address translation). SSH-2 allows more than one form of user authentication per session. The need for server key (which is an integral part of SSH-1) is removed in SSH2. SSH2 allows any number of sessions per connection. (SSH-1 only allows one session per connection). Unlike SSH-1, SSH-2 uses
Message Authentication Code (MAC) algorithm for integrity checking.
Conclusion
Secure shell is widely used software based secure channel of communication between machines on a TCP/IP network. Secure shell is a product as well as protocol. Original protocol is SSH-
1.Improved version is SSH-2. Latest in the series is SSH-3. Secure shell provides a secure channel for data transmission. SSH supplements the security of a network working in conjunction with other mechanisms like firewall.
SSH: The Secure Shell 5 Rachana Maheswari
CS265 Term Paper Spring 2003
References
[1] DJ Barrett and RE Silverman, “SSH The secure shell: The definitive guide”, O’Reilly 2001
[2] http://www.ssh.fi/
[3] http://www-h.eng.cam.ac.uk/help/jpmg/ssh/ssh-detail.html
[4] http://www.ietf.org/internet-drafts/draft-ietf-secsh-architecture-13.txt
[5] Secure Shell (SSH): Introduction and Implementation, http://biss.beckman.uiuc.edu/security/workshops/2000-02/
SSH: The Secure Shell 6 Rachana Maheswari