ValidationQuestionnaire
advertisement

Input Validation
Questionnaire
Author: Eric Sheridan
eric.sheridan@owasp.org
Revision: First Draft
OWASP Papers Program
Table of Contents
A1 Introduction .............................................................................................................................................................................. 1
A1.1 Overview ...................................................................................................................................................................... 1
A2 Understand the Vectors of Attack ........................................................................................................................................... 2
2.1.1
2.1.2
2.1.3
2.1.4
2.1.5
Purpose .................................................................................................................................... 2
Input Source: {NAME}............................................................................................................... 2
Input Source: {NAME}............................................................................................................... 2
Input Source: {NAME}............................................................................................................... 3
Input Source: {NAME}............................................................................................................... 3
A3 The Likelihood of Abuse .......................................................................................................................................................... 4
A3.1 Purpose ........................................................................................................................................................................ 4
3.1.1
3.1.2
A3.2
Source: {NAME} ........................................................................................................................................................... 4
3.2.1
3.2.2
A3.3
Likelihood ................................................................................................................................. 5
Explanation ............................................................................................................................... 5
Source: {NAME} ........................................................................................................................................................... 5
3.4.1
3.4.2
A3.5
Likelihood ................................................................................................................................. 4
Explanation ............................................................................................................................... 4
Source: {NAME} ........................................................................................................................................................... 5
3.3.1
3.3.2
A3.4
Likelihood Scale (1-5): 1 – Lowest, 5 – Highest ............................................................................ 4
Factors to Consider .................................................................................................................... 4
Likelihood ................................................................................................................................. 5
Explanation ............................................................................................................................... 5
Source: {NAME} ........................................................................................................................................................... 5
3.5.1
3.5.2
Likelihood ................................................................................................................................. 5
Explanation ............................................................................................................................... 5
A4 The Impact of Exploitation ....................................................................................................................................................... 6
4.1.1
4.1.2
A4.2
Source: {NAME} ........................................................................................................................................................... 6
4.2.1
4.2.2
A4.3
Impact ..................................................................................................................................... 7
Explanation ............................................................................................................................... 7
Source: {NAME} ........................................................................................................................................................... 7
4.4.1
4.4.2
A4.5
Impact ..................................................................................................................................... 6
Explanation ............................................................................................................................... 6
Source: {NAME} ........................................................................................................................................................... 7
4.3.1
4.3.2
A4.4
Impact Scale (1-5): 1 – Lowest, 5 – Highest ................................................................................ 6
Factors to Consider .................................................................................................................... 6
Impact ..................................................................................................................................... 7
Explanation ............................................................................................................................... 7
Source: {NAME} ........................................................................................................................................................... 7
4.5.1
4.5.2
Impact ..................................................................................................................................... 7
Explanation ............................................................................................................................... 7
A5 Severity and the Mitigation Response .................................................................................................................................... 8
5.1.1
5.1.2
5.1.3
A5.2
Source: {NAME} ........................................................................................................................................................... 9
5.2.1
5.2.2
A5.3
Severity .................................................................................................................................... 9
Mitigation Implementation and Reasoning.................................................................................... 9
Source: {NAME} ........................................................................................................................................................... 9
5.3.1
5.3.2
A5.4
Likelihood Scale (1-5): 1 – Lowest, 5 – Highest ............................................................................ 8
Severity Calculation ................................................................................................................... 8
Factors to Consider .................................................................................................................... 8
Severity .................................................................................................................................... 9
Mitigation Implementation and Reasoning.................................................................................... 9
Source: {NAME} ......................................................................................................................................................... 10
OWASP Papers Program
5.4.1
5.4.2
A5.5
Severity .................................................................................................................................. 10
Mitigation Implementation and Reasoning.................................................................................. 10
Source: {NAME} ......................................................................................................................................................... 10
5.5.1
5.5.2
Severity .................................................................................................................................. 10
Mitigation Implementation and Reasoning.................................................................................. 10
A6 References ............................................................................................................................................................................. 11
OWASP Papers Program
A1 Introduction
A1.1 Overview
The purpose of this document is to assist in the design and implementation of our input validation architecture. With an
understanding of the potential security risks concerning input validation, we can produce more secure and reliable code.
{PUT ORGANIZATIONAL SPIN HERE}
1
OWASP Papers Program
A2 Understand the Vectors of Attack
2.1.1
Purpose
In order to build the necessary validation components for our application, we must understand and document every source of
input. Each additional source of input into our web application carries multitudes of new input validation attack vectors.
2.1.2
Input Source: {NAME}
Description:
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
Access Requirements (check all that apply):
[ ]
External Access
[ ]
Internal Access
[ ]
VPN Access
[ ]
Thick Client
[ ]
Valid IP Address
[ ]
Proxy Access
[ ]
Secure Certificate
[ ]
_______________
[ ]
_______________
2.1.3
Input Source: {NAME}
Description:
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
Access Requirements (check all that apply):
[ ]
External Access
[ ]
Internal Access
[ ]
VPN Access
[ ]
Thick Client
[ ]
Valid IP Address
[ ]
Proxy Access
[ ]
Secure Certificate
[ ]
_______________
[ ]
_______________
2
OWASP Papers Program
2.1.4
Input Source: {NAME}
Description:
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
Access Requirements (check all that apply):
[ ]
External Access
[ ]
Internal Access
[ ]
VPN Access
[ ]
Thick Client
[ ]
Valid IP Address
[ ]
Proxy Access
[ ]
Secure Certificate
[ ]
_______________
[ ]
_______________
2.1.5
Input Source: {NAME}
Description:
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
Access Requirements (check all that apply):
[ ]
External Access
[ ]
Internal Access
[ ]
VPN Access
[ ]
Thick Client
[ ]
Valid IP Address
[ ]
Proxy Access
[ ]
Secure Certificate
[ ]
_______________
[ ]
_______________
3
OWASP Papers Program
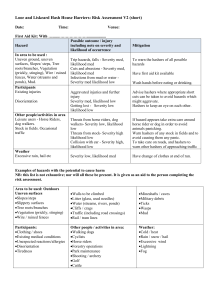
A3 The Likelihood of Abuse
A3.1 Purpose
In order to allocate our engineering resources to properly address the validation concerns, we must understand two important
factors: the likelihood of an attack and the impact of an attack. In this section, we analyze each of our defined sources of input
in an attempt to rate the likelihood of attack for a particular source.
3.1.1
Likelihood Scale (1-5): 1 – Lowest, 5 – Highest
Key:
1 – Highly Unlikely
3.1.2
2 – Unlikely
3 – Probably
4 – Likely
5 – Highly Likely
Factors to Consider
How might the access requirements affect the likelihood of an attack?
Can you trust your “trusted” users? Even the disgruntled ones?
How does the user registration process work? Can anonymous users register?
Are we sharing this source with another application? Will the other application pass an attack to us?
Has all the data coming from the source been validated before it entered the source?
How difficult would it be to discover the flaw? What is the skill level required?
A3.2 Source: {NAME}
3.2.1
Likelihood
Our analysis efforts conclude that the likelihood of an attack coming from {source name} is ___.
3.2.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
4
OWASP Papers Program
A3.3 Source: {NAME}
3.3.1
Likelihood
Our analysis efforts conclude that the likelihood of an attack coming from {source name} is ___.
3.3.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
A3.4 Source: {NAME}
3.4.1
Likelihood
Our analysis efforts conclude that the likelihood of an attack coming from {source name} is ___.
3.4.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
A3.5 Source: {NAME}
3.5.1
Likelihood
Our analysis efforts conclude that the likelihood of an attack coming from {source name} is ___.
3.5.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
5
OWASP Papers Program
A4 The Impact of Exploitation
In order to allocate our engineering resources to properly address the validation concerns, we must understand two important
factors: the likelihood of an attack and the impact of an attack. In this section, we analyze each of our defined sources of input
in an attempt to rate the impact of exploitation for a particular source.
4.1.1
Impact Scale (1-5): 1 – Lowest, 5 – Highest
Key:
1 – Trivial
4.1.2
2 – Insignificant
3 – Moderate
4 – Dangerous
5 – Severe
Factors to Consider
Does exploitation affect some or all of the users of the application?
Does exploitation affect the integrity of sensitive data?
Does exploitation affect the availability of the system?
Will exploitation of this application’s source affect another resource?
A4.2 Source: {NAME}
4.2.1
Impact
Our analysis efforts conclude that the impact of an exploitation of {source name} is ___.
4.2.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
6
OWASP Papers Program
A4.3 Source: {NAME}
4.3.1
Impact
Our analysis efforts conclude that the impact of an exploitation of {source name} is ___.
4.3.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
A4.4 Source: {NAME}
4.4.1
Impact
Our analysis efforts conclude that the impact of an exploitation of {source name} is ___.
4.4.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
A4.5 Source: {NAME}
4.5.1
Impact
Our analysis efforts conclude that the impact of an exploitation of {source name} is ___.
4.5.2
Explanation
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
7
OWASP Papers Program
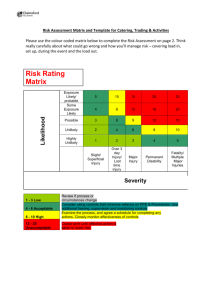
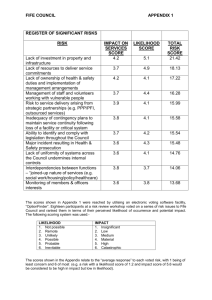
A5 Severity and the Mitigation Response
Given the assessment of the both the likelihood and impact, we can now calculate the overall severity of utilizing each input
source in our application. Refer to 5.1.2 for the severity calculation algorithm. Once you’ve calculated the severity, describe
the implementation efforts necessary to mitigate the input validation issues for each source.
5.1.1
Likelihood Scale (1-5): 1 – Lowest, 5 – Highest
Key:
1 – Trivial
5.1.2
2 – Insignificant
3 – Moderate
4 – Dangerous
5 – Severe
Severity Calculation
(LIKELIHOOD + IMPACT) / 2 = SEVERITY
5.1.3
Factors to Consider
Are you implementing a positive validation model? Are you defining what is acceptable rather than what is
not?
Is your input validation mechanism centralized? Can it be bypassed?
Are your validation rules/routines as strict as possible?
Are there exceptions to your validation mechanisms? What are they?
Does the every-day developer need to utilize validation API? Is it simplistic?
Does the validation mechanism respond appropriately to all validation violations? If not, does the application
logic handle violations appropriately?
Does it make sense to utilize an existing open-source implementation? Struts? Stinger?
What is the amount of time required to implement the mitigating control? Does it make sense considering
the severity?
Can the validation mechanism be reused in future applications?
8
OWASP Papers Program
A5.2 Source: {NAME}
5.2.1
Severity
Our analysis efforts conclude that the overall severity of {source name} is ___.
5.2.2
Mitigation Implementation and Reasoning
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
A5.3 Source: {NAME}
5.3.1
Severity
Our analysis efforts conclude that the overall severity of {source name} is ___.
5.3.2
Mitigation Implementation and Reasoning
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
9
OWASP Papers Program
A5.4 Source: {NAME}
5.4.1
Severity
Our analysis efforts conclude that the overall severity of {source name} is ___.
5.4.2
Mitigation Implementation and Reasoning
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
A5.5 Source: {NAME}
5.5.1
Severity
Our analysis efforts conclude that the overall severity of {source name} is ___.
5.5.2
Mitigation Implementation and Reasoning
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
__________________________________________________________________________________________________
10
OWASP Papers Program
A6 References
11