Data Communication & Networking Assignment
advertisement

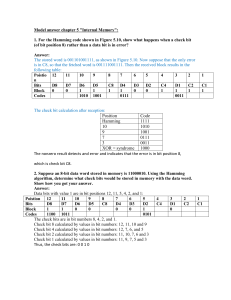
WebCT Assignment 1 1. The Medium is the physical path over which a message travels. 2. In Full-duplex transmission, the channel capacity is equally shared by both sending and receiving devices at all times on a circuit. 3. A Point to point connection provides a dedicated link between two devices. 4. The information to be communicated in a data communication system is the Message. 5. Frequency of failure and network recovery time after a failure is measures of the Reliability of a network. 6. The Internet, five-layer model provides guidelines for the development of universally compatible networking protocols. 7. The data link layer is responsible for delivering data units from one station to the next without errors. 8. The transport layers DO NOT directly support the physical layers. 9. The process-to-process delivery of the entire message is the responsibility of the Transport layer. 10. The Physical layer is closest to the transmission medium. 11. Mail services are available to network users through the Application layer. 12. The main difference(s) between the Internet and OSI models is/are: 1. The Internet model was designed by the Department of Defense (DoD) and the OSI model was designed by the International Organization for Standardization (ISO) 2. The Internet model is a five layer model and the OSI model is a seven layer model 3. The Internet model probably best describes WANs and the OSI model probably best describes LANs. 13. The number of bits sent each second within a network or between networks is known as the Data Rate. 14. The physical layer defines the: 1. Characteristics of the interface between the devices and the transmission media. 2. Type of transmission medium. 3. Acceptance of encoded electrical or optical signals 15. According to the Internet model, the Transport layer lies between the network layer and the application layer. 16. The Physical layer changes streams of bits into electromagnetic signals. 17. Regarding the Internet model, when data are transmitted from computing device A to computing device B. The header from A's layer 4 is read by B's Data Link Layer. 18. On the incoming side of the internetwork, as the data packet moves from the lower to the upper layers, headers are subtracted. 19. Protocols are: 1. The rules that govern data transmissions within and between networks. 2. Required for successful network to network transmission. 3. Designed so network devices and software can inter operate with other network devices and their software. 20. Interface Between Layers: 1. Defines what information and services a layer must provide for the layer above it. 21. Internet Model : 1. 5 layer protocol stack that provides guidelines for the development of universally compatible network protocols 22. Header: 1. Control information added to the beginning of the data packet by the corresponding layer. 23. Flow Control : 1. Mechanism employed in communications to prevent overwhelming the receiver. 24. Routing: 1. The process of selecting a path from origin to destiny for a given packet. WebCT Assignment 2 1. Binary data is represented as a series of bits (1s and 0s). 2. If the bandwidth of a signal is 5 kHz and the lowest frequency is 52kHz, what is the highest frequency of the bandwidth while the signal is in transit along the media? 1. 57 kHz 3. These can impair a signal on a network 1. Attenuation 2. Distortion 3. Noise 4. Distortion is a type of transmission impairment in which the signal loses strength due to the different propagation speeds of each frequency that makes up the signal. 5. Noise is a type of transmission impairment in which an outside source such as crosstalk corrupts a signal. 6. A signal has been received that only has values in measures of -1, 0, and 1. This is an example of: 1. Discrete Signal 2. Digital Signal 7. A signal is periodic if it consists of a continuously repeating pattern. One example would be an analog signal in the form of a sine wave 8. A time-domain graph plots each sine waves peak amplitude against its frequency 9. The Shannon capacity is NOT a formula used to determine the theoretical data rate for a noiseless channel. 10. Attenuation is the loss of a signal's strength due to the resistance of the medium. Extending a signal past a recommended maximum cable segment length can cause attenuation. 11. As frequency increases, the period decreases. 12. Data transmission can be encoded as either analog or digital signals, depending on the respective network media's available bandwidth. 13. Each sine wave can be characterized by its amplitude, frequency and phase. 14. What is the bandwidth of a signal that ranges from 40kHz to 4MHz? 1. 3.96 MHz 15. Bit rate and bit interval are NOT used to describe analog signals. 16. Frequency is the rate of change with respect to time. This means that: 1. Change in a short span of time means high frequency 2. Change in a long span of time means low frequncy 3. Period is the inverse of frequency 17. In essence, a digital signal: 1. Is a complete signal 2. Has an infinite bandwidth 18. The Nyquist rate is NOT a formula used to determine the theoretical maximum data rate for a noisy channel. 19. A periodic signal completes one cycle in 0.0001s. What is the frequency? 1. 10 Khz 20. A signal is measured at two different points. The power of P1 at the first point and P2 at the second point. The dB is 0. This means P2 equals P1. 21. A signal power is measured at two different points of a communication channel, input P1 and output P2. If the value of P2 is 50% of the value of P1. This means that the channel Attenuates the signal in -3dB. 22. When propagation speed is multiplied by propagation time, we get the distance a signal or bit has traveled. 23. A sine wave in the time domain can be represented by one single spike in the frequency domain. 24. The bandwidth-delay product defines the number of bits that can fill the link. 25. What is the maximum data rate of a channel with a bandwidth of 200KHz if we use four levels of digital signaling? 1. 800Kbps 26. In certain channels, it takes 20 microseconds to transmit 10 bits, then the data rate is 500 Kbps. 27. A channel with 4 Khz bandwidth is used to send data at 100 Kbps, what is the minium SNRdb? 1. 75.257 28. What is the transmission time of a packet sent by a station if the length of the packet is 1 million bytes and the bandwidth of the channel is 200Kbps? 1. 40s 29. A file contains 2 million bytes. How long does it take to download this file using a 56Kbps channel? 1. 285.714 30. How many bits can fit on a link with a 2 ms delay if a bandwidth of the link is 10 Mbps? 1. 20,000 bits WebCT Assignment 3 1. In a fiber-optic cable, the signal is propagated along the inner core by reflection. 2. Infrared waves are used for short-range communications such as those between a PC and a peripheral device. 3. Which of the following primarily uses guided media? 1. Local telephone system 4. What is the major factor that makes coaxial cable less susceptible to noise than twisted-pair cable? 1. Outer Conductor 5. When a beam of light travels through media of two different densities, if the angle of incidence is greater than the critical angle, reflection occurs. 6. A parabolic dish antenna is a(n) unidirectional antenna. 7. Coaxial cable can carry signals of higher frequency ranges than twisted-pair cable. 8. The DSSS technique expands the bandwidth of a signal by replacing each data bit with n bits. 9. In an optical fiber, the inner core is less dense than the cladding. 10. Radio waves are omni directional. 11. Data can essentially be transmitted in two primary ways within and between computing device(s). These two essential modes of transmission are parallel and serial. 12. In asynchronous transmissions, we send one start bit at the beginning and one or more stop bits at the end of each byte. 13. In serial transmission, bits: 1. Travel with one bit following another in a stream or a single line. 2. Only one communication channel is needed. 3. Represented most closely with communication between devices. 14. Serial transmissions are timed by the amount of bits that are sent with each tick of the internal system clock of the computing device on the network. These can be sent: 1. Synchronously as in simultaneous transmissions 2. Asynchronously as in request / respond transmissions 15. Since synchronous transmission sends bits one after another without start/stop bits or gaps, we can conclude that: 1. Timing is essential between the sender and receiver. 2. It is the responsibility of the receiving device to organize the bytes for decoding 3. A dedicated circuit (either physical or virtual) is established between the sender and the receiver. 16. Synchronization of data transmissions between sending and receiving computing devices is based on the explicit timing between sender and receiver. 17. The reason why we call it asynchronous transmission is because: 1. Data can be sent, stored in buffers, and forwarded on the destination for optimal transmission. 2. The sending device makes a request for access or data and the receiving device responds to that request. 3. Asynchronous transmission can be more efficient if information needs are not immediate 18. What is the maximum data rate of a channel with a bandwidth 200 Khz if we use four levels of digital signaling? 1. 800 Kbps 19. Which multiplexing technique transmits analog signals? 1. FDM 2. WDM 20. In synchronous TDM, for n signal sources of the same data rate, each frame contains n slots. 21. In Synchronous TDM, the transmission rate of the multiplexed path is usually equal to the sum of the transmission rates of the signal sources. 22. Which multiplexing technique involves signals composed of light beams? 1. WDM 23. The word channel refers to a portion of a link that carries a transmission. 24. Suppose that a communication channel between two stations use synchronous communication. The clock in the receiver is slower than the clock in the transmitter by 1%. The speed used is 10 Kbps. If the first bit arrived in the receiver is correctly sampled, in the middle of the bit, what would be the maximum number of bits that could be transmitted before loosing synchronization? 1. 50 25. In statistical TDM, slots are dynamically allocated to improve bandwidth efficiency. 26. In spread spectrum, we combine signals from different sources to fit into a larger bandwidth. 27. Spread spectrum is designed to be used in wireless applications in which stations must be able to share the medium without interception by an eavesdropper and without being subject to jamming from a malicious intruder. 28. The FHSS technique uses M different carrier frequencies that are modulated by the source signal. At one moment, the sign modulates one carrier frequency; at the next moment, the signal modulates another carrier frequency. WebCT Assignment 4 1. Adding 1 and 1 in modulo-2 arithmetic results in 0. 2. We add r redundant bits to each block to make the length n = m + r. The resulting n-bit blocks are called codewords. 3. A burst error means that two or more bits in the data unit have changed. 4. An extra bit (parity bit) is added to the data unit in the parity check method. 5. By rearranging the order of bit transmission of the data units, the Hamming code can correct burst errors. 6. Errors can be categorized as a single-bit error or burst error. 7. If the data unit is 111101, the divisor 1101, what is the dividend at the transmitter? a. 111101000 8. In block coding, we divide our message into blocks, each of k bits, called datawords. 9. In forward error correction, the receiver corrects errors without requesting retransmission. 10. In Error correction by retransmission a receiver can have the sender retransmit the entire data unit when an error is discovered. 11. The Hamming distance between equal codewords is 0. 12. In Forward error correction a receiver can use an error-correcting code that automatically corrects certain errors. 13. In cyclic redundancy checking, the divisor is one bit more than the CRC check bits. 14. In two-dimensional parity check, a redundant data unit follows n data units. 15. Redundancy is the concept of sending extra bits for use in error detection. 16. The Hamming is an error correction method using redundant bits. 17. The parity check can detect odd number of errors and not an even number of errors. 18. Three common redundancy methods are: a. parity check b. cyclic redundancy check c. check-sum 19. Which error detection method consists of a parity bit for each data unit as well as an entire data unit of parity bits? a. Two-dimensional parity check 20. Which error detection method consists of just 1 redundant bit per data unit? a. Single parity 21. Suppose that we have a code with 5 symbols: X1 = 000000, X2 = 111111, X3 = 111000, X4 = 000111, X5 = 011000, X6 = 001100. How many errors can be detected if we use the code? a. 0 i. There are two symbols with a Hamming Distance of 1. X3 XOR X4 = 100000. Therefore if an error occurs in the first position the error is not detected. 22. The Hamming distance between 100 and 001 is 2. 23. Which error detection method involves polynomials? a. CRC 24. Which error detection method uses one's complement arithmetic? a. Checksum 25. Which of the following best describes a single-bit error? a. A single bit is inverted per data unit 26. While it's a good thing for networks to be able to detect errors, it is better to be able to have in place the capacity of/for: a. Error correction 27. If in certain transmission the message is 111011101 and the received message is 111010111 then the polynomial that represents E(X), the error, will be X3 + X. 28. What is the maximum effect of a 2ms burst of noise on data transmitted at 100 Kbps? a. 200 bits 29. Cyclic codes are special linear block codes with one extra property. If a codeword is rotated, the result is another codeword. 30. A simple parity-check code can detect an odd-number of errors. 31. Checksums use one's complement arithmetic. 32. If the Hamming distance between a dataword and the corresponding codeword is four, then there are 4 bits in error. 33. If the Hamming distance between a dataword and the corresponding codeword is three, there are 3 bits in error. 34. In block coding, if k =2 and n =3, we have 4 invalid codewords. 35. In cyclic redundancy checking, what is the CRC? a. The remainder 36. Suppose that we intend to send ASCII-E characters of 8 bits. For that purpose we use a code that can correct one single error. How many bits of redundancy are required? a. 4 bits 37. The Hamming distance between two words is the number of differences between corresponding bits. 38. The checksum (sent) of 1111 and 1111 is 0000. 39. The divisor in a cyclic code is normally called the generator. 40. To guarantee the detection of up to 5 errors in all cases, the minimum Hamming distance in a block code must be 6. WebCT Assignment 5 1. Flow control is the regulation of the sender's data rate so that the receiver buffer does not become overwhelmed. 2. The bandwidth-delay product is a measure of the number of bits a system can have in transit at any given time. 3. An example of piggybacking is when acknowledgment packet is sent with a data frame. 4. In Stop and Wait ARQ, the sender sends a frame and waits for an acknowledgment from the receiver before sending the next frame. 5. Flow control mechanisms with sliding windows have control variables at Sender and Receiver sides. 6. HDLC handles data transparency by adding a 0 whenever there are five consecutive 1's. This is called bit stuffing. 7. For a sliding window of size n-1 (n sequence numbers), there can be a maximum of n-1 frames sent but unacknowledged. 8. A Go-Back-N ARQ uses a window size of 15. How many bits are needed to define the sequence number? 1. 4 9. A Selective Repeat ARQ is using 7 bits to represent the sequence numbers. What is the size of the window? 1. 64 10. Bit-stuff the following data: 0001111110111110011110011111001 1. 0001111101011111000111100111110001 11. A Go-Back-N ARQ uses a window size of 15. How many data buffers are needed in the transmiter side to keep copies of unacknowleded frames? 1. 15 12. A Selective-Repeat ARQ uses 4 bits to mange the windows. How many data buffers are needed in the transmiter side? 1. 8 13. If an Stop-and-Wait ARQ is used in a line with 1 Mbps bandwidth, 10 msec of total propagation time (to make a round trip) and data frames are 1000 bits, what is the utilization (aproximate) percentage of the link? 1. 10% 14. If the link of the last problem uses Go-Back-N ARQ with 3, bits what is the maximum (aproximate) utilization of the link?. 1. 70% 15. Bandwith-delay product: 1. A measure of the number of bits that a system can have in transit 16. Piggybacking 1. Couples an acknowledgement with a data frame 17. Pipelining 1. Sending several frames before news (acknowledgements) are received 18. Data Transparency 1. The ability to send any bit pattern as data without it being mistaken for control bits. 19. Frame Check Sequence (FCS) 1. The HDLC error-detection containing either a 2 or 4 bytes Cyclic redundancy Check (CRC) 20. A transfer of data in HDLC is represented in the following figure. What would be the values for N(S) and N(R) for frame X? 1. N ( S ) = 2 ; N ( r ) = 2 21. According to the PPP transition state diagram exchange of user control and data packets occurs in Networking state. 22. According tot he PPP transition state diagram, options are negotiated in Establishing state. 23. The following data fragment occurs in the middle of a dta stram for which the byte-stuffing algorithm is used: A B ESC C ESC FLAG FLAG D. What is the output after stuffing? 1. A B ESC ESC C ESC ESC ESC FLAG ESC FLAG D 24. A sender sends a series of packets to the same destination using 5-bits sequence numbers. If the sequence number starts with 0, what is the sequence number after 150 packets? 1. 22 25. The previous figure shows part of the GO-BACK-N sender algorithm. What action(s) is(are) carried out in the segment delimited by the brackets with the letter A? 1. Moving the lower edge of the windows and clearing the buffers occupied by acknowledged frames. 26. The previous figure shows part of the GO-BACK-N sender algorithm. What action(s) is(are) carried out in the segment delimited by the brackets with the letter B? 1. Sending all pending frames.