Biometric ID
Technical overview
Overview
The Microsoft Tamper-Resistant Biometric ID Card system (MS Biometric ID) provides a
cryptographically secure ID card that can be easily deployed at a low cost. This system requires only
simple, low-cost, off-the-shelf hardware to generate and validate ID cards. It can create secure cards
using only standard paper, or business card stock. It can also be integrated into a system using smart
cards, if desired.
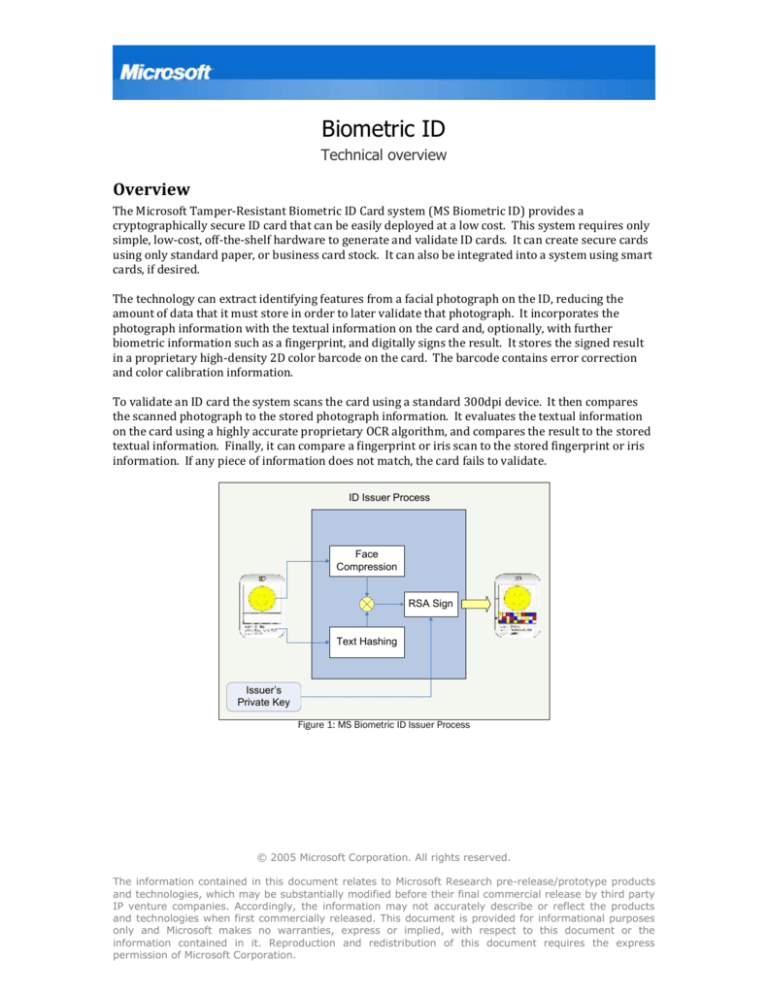
The technology can extract identifying features from a facial photograph on the ID, reducing the
amount of data that it must store in order to later validate that photograph. It incorporates the
photograph information with the textual information on the card and, optionally, with further
biometric information such as a fingerprint, and digitally signs the result. It stores the signed result
in a proprietary high-density 2D color barcode on the card. The barcode contains error correction
and color calibration information.
To validate an ID card the system scans the card using a standard 300dpi device. It then compares
the scanned photograph to the stored photograph information. It evaluates the textual information
on the card using a highly accurate proprietary OCR algorithm, and compares the result to the stored
textual information. Finally, it can compare a fingerprint or iris scan to the stored fingerprint or iris
information. If any piece of information does not match, the card fails to validate.
ID Issuer Process
Face
Compression
RSA Sign
Text Hashing
Issuer’s
Private Key
Figure 1: MS Biometric ID Issuer Process
© 2005 Microsoft Corporation. All rights reserved.
The information contained in this document relates to Microsoft Research pre-release/prototype products
and technologies, which may be substantially modified before their final commercial release by third party
IP venture companies. Accordingly, the information may not accurately describe or reflect the products
and technologies when first commercially released. This document is provided for informational purposes
only and Microsoft makes no warranties, express or implied, with respect to this document or the
information contained in it. Reproduction and redistribution of this document requires the express
permission of Microsoft Corporation.
ID Verifier Process
Authentic /
Invalid
Compare
Scan
Face
Compression
?
Issuer’s Public
Key
Scan
Scan &
OCR
RSA
Verify
Text
Hashing
Figure 2: MS Biometric ID Verifier’s Process
Components
MS Biometric ID incorporates three state-of-the-art technologies:
1. Face compression: Storing a standard JPEG face image from an ID card (approximately 2cm
x 2cm) in a barcode could require a barcode larger than the ID card itself. After compression
the face image data can fit into a small barcode in one corner of the card. However, the
system can use this compressed data to robustly determine if the original image has been
tampered with or replaced.
2. OCR: Standard OCR algorithms are not accurate enough to use in ID card validation, due to
the problems caused by false negatives. For this technology Microsoft Research has
developed a neural-network based OCR algorithm that remains accurate even when faced
with standard wear and tear that can slightly alter characteristics of characters.
3. 2D color barcode: To further reduce the space requirements of the biometric information
on an ID card, the system uses a very high density color barcode. By using eight colors this
barcode achieves approximately twice the density of existing barcodes, while still
incorporating error correction information.
Core Scenarios
The Microsoft Biometric ID system can incorporate any combination of textual, facial biometric, other
biometric, or other information on an ID card. It can be used in any situation that calls for creating an
inexpensive artifact for secure identification of a person or entity. For instance:
Company ID cards for employees: Many large companies require employees to carry
corporate IDs with facial photographs. Security personnel then visually examine ID photos
to validate that an ID holder is an employee. This system would allow security personnel to
quickly validate that an ID is not a fake, or alteration of a valid ID.
© 2005 Microsoft Corporation. All rights reserved.
2
The information contained in this document relates to Microsoft Research pre-release/prototype products
and technologies, which may be substantially modified before their final commercial release by third party
IP venture companies. Accordingly, the information may not accurately describe or reflect the products
and technologies when first commercially released. This document is provided for informational purposes
only and Microsoft makes no warranties, express or implied, with respect to this document or the
information contained in it. Reproduction and redistribution of this document requires the express
permission of Microsoft Corporation.
Driver’s licenses: The driver’s license has become the de facto means for proving identity,
age, and residency in the United States. As such it is a common target for faking or
alteration. This system would allow an organization that accepts a driver’s license as ID to
quickly check the license for validity.
Event tickets: This system would allow event promoters to cheaply produce and validate
tickets for events. While the tickets may not need to be tied to a particular person, they
could contain textual information as well as a unique identifier for the ticket in the barcode.
PIN alternative: IDs such as ATM cards that require automated validation have associated
PINs or passwords, which have significant security drawbacks. This system can create cards
that have biometric data such as a fingerprint, which a validating reader can scan and check
against the data in the card.
Documentation
For more information on the MS Biometric ID technology please visit
http://www.microsoft.com/products/msbit/default.mspx.
Related Work
Differentiating Features
Cryptographically tamper-resistant: Information on the ID card is digitally signed using
RSA public-private key encryption and stored in a barcode. During verification, the
information on the ID badge is verified against the barcode.
Cost effective to issue: ID cards can be printed on common physical media such as paper or
plastic with no special features. The digitally signed barcode is used to detect tampering
with the physical ID.
Cost effective to validate: The integrity of the information on the ID card is validated using
PC software and a business card scanner. All that is then required is a person to confirm that
the face on the card matches the face of the presenter. For a mobile solution, the software
can be embedded in a smart scanner with only a red/green LED display to determine
authenticity.
Does not compromise the privacy of the individual: The Microsoft Tamper-Resistant
Biometric ID Card system does not require the remote creation, access or storage of any
personally identifiable information. All the information required to check the validity of the
card is on the card itself. Furthermore, the information on the card cannot be changed by the
issuer without issuing a new card, meaning that the cardholder is always aware of any
changes to the information on the card.
Can be combined with any biometric data.
Demo/Prototype
Development Status
The system can now produce and validate ID cards. The prototype uses a standard PC, webcam,
color inkjet printer, fingerprint scanner, and business card scanner. The state of the code is that of a
mature prototype.
© 2005 Microsoft Corporation. All rights reserved.
3
The information contained in this document relates to Microsoft Research pre-release/prototype products
and technologies, which may be substantially modified before their final commercial release by third party
IP venture companies. Accordingly, the information may not accurately describe or reflect the products
and technologies when first commercially released. This document is provided for informational purposes
only and Microsoft makes no warranties, express or implied, with respect to this document or the
information contained in it. Reproduction and redistribution of this document requires the express
permission of Microsoft Corporation.






