Information Security Classification and Handling Guideline
advertisement
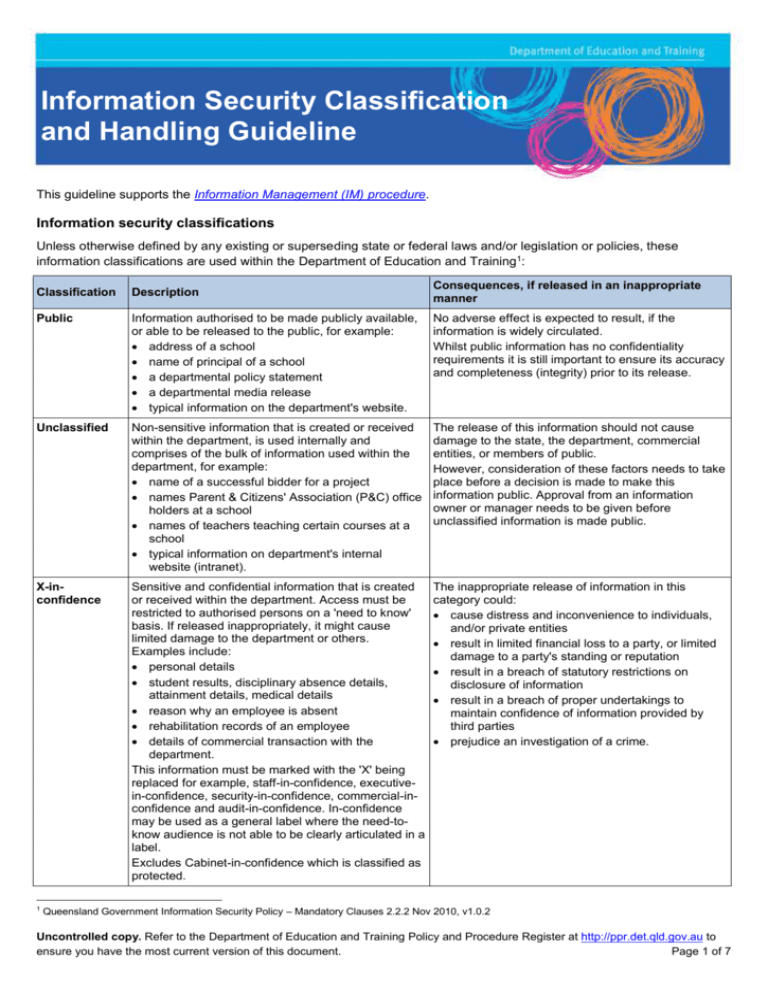
Information Security Classification and Handling Guideline This guideline supports the Information Management (IM) procedure. Information security classifications Unless otherwise defined by any existing or superseding state or federal laws and/or legislation or policies, these information classifications are used within the Department of Education and Training1: Consequences, if released in an inappropriate manner Classification Description Public Information authorised to be made publicly available, or able to be released to the public, for example: address of a school name of principal of a school a departmental policy statement a departmental media release typical information on the department's website. No adverse effect is expected to result, if the information is widely circulated. Whilst public information has no confidentiality requirements it is still important to ensure its accuracy and completeness (integrity) prior to its release. Unclassified Non-sensitive information that is created or received within the department, is used internally and comprises of the bulk of information used within the department, for example: name of a successful bidder for a project names Parent & Citizens' Association (P&C) office holders at a school names of teachers teaching certain courses at a school typical information on department's internal website (intranet). The release of this information should not cause damage to the state, the department, commercial entities, or members of public. However, consideration of these factors needs to take place before a decision is made to make this information public. Approval from an information owner or manager needs to be given before unclassified information is made public. X-inconfidence Sensitive and confidential information that is created or received within the department. Access must be restricted to authorised persons on a 'need to know' basis. If released inappropriately, it might cause limited damage to the department or others. Examples include: personal details student results, disciplinary absence details, attainment details, medical details reason why an employee is absent rehabilitation records of an employee details of commercial transaction with the department. This information must be marked with the 'X' being replaced for example, staff-in-confidence, executivein-confidence, security-in-confidence, commercial-inconfidence and audit-in-confidence. In-confidence may be used as a general label where the need-toknow audience is not able to be clearly articulated in a label. Excludes Cabinet-in-confidence which is classified as protected. The inappropriate release of information in this category could: cause distress and inconvenience to individuals, and/or private entities result in limited financial loss to a party, or limited damage to a party's standing or reputation result in a breach of statutory restrictions on disclosure of information result in a breach of proper undertakings to maintain confidence of information provided by third parties prejudice an investigation of a crime. 1 Queensland Government Information Security Policy – Mandatory Clauses 2.2.2 Nov 2010, v1.0.2 Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 1 of 7 Classification Description Consequences, if released in an inappropriate manner Protected (includes Cabinet-inconfidence) Very sensitive and confidential information that, in the event of unauthorised and/or premature disclosure, might cause damage to one or more parties for example: release of a security code for access to employee's personal information release of details of rates charged for work quoted in a tender to another competing tenderer after the tender has closed release of information about an employee's performance appraisal. Cabinet-in-confidence is to be applied to information, policies, bills and other types of submissions to the Queensland Cabinet. The inappropriate release of information in this category could: endanger an individual and/or private entity result in release of personal or commercially sensitive information to third parties cause financial loss to any party cause damage to any party's standing or reputation cause distress to any party threaten government agencies' systems, or agencies' capacity to conduct their business facilitate commission of a serious crime or hinder its detection impede an investigation of a crime. Highly protected Information that requires a substantial degree of protection as compromise of the information could cause serious damage to the state, the government, commercial entities or members of the public, for example: release of information about a tender price before the tender is closed, which could lead to substantial loss if it allowed a competitor to place a lower bid release of a student's location, when that student is under a child protection order release of details about a criminal investigation into a sexual abuse complaint at a school. The inappropriate release of information in this category could: cause a serious risk to any party's personal safety, including death result in release of personal, political or commercially sensitive data to third parties cause substantial financial loss to any party result in substantial distress being caused to any party create a significant threat to government agencies' systems or agencies' capacity to conduct their business assist in commissioning of a serious crime or hinder its detection. Detailed application and handing of the information security classifications is available within the Queensland Government Information Security Classification Framework (QGISCF) and the section below. Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 2 of 7 Handling of information according to its information security classification Information security classification Item Action Public Unclassified In-confidence (excludes Protected Highly protected Stored in a locked drawer or filing cabinet. Label document or folder with classification, or affix label to magnetic media, if possible. Stored in a locker or secure container. Label document or folder with classification, or affix label to magnetic media, if possible. cabinet-in-confidence) Removable storage media including: paper documents files backup tapes removable hard drives CDs DVDs USB flash drives flash memory cards memory sticks. Storage Stored on departmental premises. No specific security requirements. No specific security requirements. Stored in a locked drawer or filing cabinet. Label document or folder with classification, or affix label to magnetic media, if possible. Stored outside of departmental premises. No specific security requirements. No specific security requirements. Stored securely e.g. locked Media must not be sent outside drawer or locked filing cabinet of departmental premises or in secure storage area. without the permission of the 'information owner'. Stored in a locker or container approved by permission of the 'information owner'. No specific security requirements. No specific security requirements. Send in a sealed envelope Send in a sealed envelope with with instructions for the item to instructions for the item to only only be opened by the be opened by the addressee. addressee. Must be hand delivered in a sealed envelope directly to the addressee. Sent outside of No specific departmental security premises (e.g. requirements. posted via Australia Post, courier, or hand delivery). No specific security requirements. Send in a sealed opaque Send in a sealed opaque envelope, padded bag or box. envelope, padded bag or box, with instructions for the item to be opened by the addressee only. Send in a sealed opaque envelope, padded bag or box by registered mail or courier, with instructions for the item to be opened by the addressee only. Carried outside of departmental premises. No specific security requirements. Must be carried securely e.g. in locked brief case or bag. Must be carried in a sealed envelope in a locked brief case or bag with the contents of any electronic media encrypted using approved encryption method. Transmission Sent within departmental premises. No specific security requirements. Must be carried in a sealed envelope in a locked brief case or bag, unless the contents of the media are encrypted using approved encryption method. Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 3 of 7 Information security classification Item Action Public Unclassified In-confidence (excludes Protected Highly protected cabinet-in-confidence) Disposal Mobile information processing devices including: laptop computers PDAs notebook computers tablets mobile phones with text capability and other high level devices. Also applies to personally owned devices e.g. laptops, PDAs, notebooks, tablets, PCs Paper-based items. No specific security requirements. Recycle paper where a scheme exists. No specific security Items should be pulped or requirements. shredded. Recycle paper where a scheme exists. Items should be shredded with a crosscut shredder. Items should be shredded with a crosscut shredder. Optical media, including CD's, DVD's. Render disk unreadable by scratching surface or other means. Render disk Disks should be physically unreadable by destroyed or shredded. scratching surface or other means. Disks should be physically destroyed or shredded. Disks should be physically destroyed or shredded. Cartridge tapes. Degauss tape. Degauss tape. Degaussed prior to re-use. Tapes should be physically destroyed. Tapes should be physically destroyed. Removable hard drives, USB and other flash drives, memory sticks etc. Delete information prior to re-use. Delete information prior to re-use. If possible, information must be removed before return, using an Australian Signals Directorate recommended wiping program/procedure. If possible, information must be removed before return, using an Australian Signals Directorate recommended wiping program/procedure. If possible, information must be removed before return, using an Australian Signals Directorate recommended wiping program/procedure. Used on departmental premises. No specific security requirements. No specific security requirements. Access to device, file or record must be password protected. Device to be password protected and file or record to be encrypted using encryption functions and protocols approved by the Manager, Operational Security. Device to be password protected and file or record to be encrypted using encryption functions and protocols approved by the Manager, Operational Security. Used outside of departmental premises. No specific security requirements. No specific security requirements. Access to device, file or record must be password protected. Device to be password protected and files or records are to be encrypted using an approved encryption method. Device to be password protected and files or records are to be encrypted using an approved encryption method. Storage Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 4 of 7 Information security classification Item Action Public Unclassified In-confidence (excludes Protected Highly protected Device to be password protected and files or records are to be encrypted using an approved encryption method. Device to be password protected and files or records are to be encrypted using an approved encryption method. cabinet-in-confidence) Transmission Carried outside of departmental premises. No specific security requirements. No specific security requirements. Access to device, file or record must be password protected. No specific security requirements. No specific security requirements. Information must be removed Information must be removed using an approved program or using an approved program or process. process. Information must be removed using an approved program or process. Used on departmental premises. No specific security requirements. No specific security requirements. Access to the device, file or record must be password protected. Access to the device and file or record must be password protected. Used outside of departmental premises. No specific security requirements. No specific security requirements. Device and file or record to be Information must be removed password protected. using an approved program or process. Information must be removed using an approved program or process. Undertaken on departmental premises. No specific security requirements. No specific security requirements. Employee repairing the item is to sign a non-disclosure agreement, and be made aware of the need to keep the information secure. Employee repairing the item is to sign a non-disclosure agreement, and be made aware of the need to keep the information secure. Employee repairing the item is to sign a non-disclosure agreement, and be made aware of the need to keep the information secure. Undertaken outside of departmental premises. No specific security requirements. No specific security requirements. Employee repairing the item is to sign a non-disclosure agreement, and be made aware of the need to keep the information secure. Employee repairing the item is to sign a non-disclosure agreement, and be made aware of the need to keep the information secure. Only use a repairer with secure data recovery and repair processes. Employee repairing the item is to sign a non-disclosure agreement, and be made aware of the need to keep the information secure. Only use a repairer with secure data recovery and repair processes. Disposal Removable media or mobile devices. Non mobile devices and non-removable storage media including: desktop computers PCs. It is not recommended that official or 'business' records, or sensitive information, be stored on internal hard drives of these machines e.g. on 'C' drive. Storage Access to the device and file or record must be password protected. Repair Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 5 of 7 Information security classification Item Action Public Unclassified In-confidence (excludes Protected Highly protected cabinet-in-confidence) Warranty replacement of storage media or devices containing storage media. No specific security requirements. No specific security requirements. If possible, information must be removed before return, using an Australian Signals Directorate wiping program/procedure. Only use a repairer with secure data recovery and repair processes. If possible, information must be removed before return, using an Australian Signals Directorate wiping program/procedure. If information cannot be removed appropriately the storage media should be destroyed. If possible, information must be removed before return, using an Australian Signals Directorate wiping program/procedure. If information cannot be removed appropriately the storage media should be destroyed. Information must be removed before disposal. Re-format hard drive/s. Information must be removed before disposal. Re-format hard drive/s. If possible, information must be removed before return, using an approved wiping program. If information cannot be removed appropriately the storage media should be destroyed. The media or equipment is to be physically destroyed by cutting, breaking, bashing or burning and disposed of as classified waste. The media or equipment is to be physically destroyed by cutting, breaking, bashing or burning and disposed of as classified waste. No specific security requirements. No specific security requirements. Access to the file or record Information must be encrypted must be restricted by using an approved encryption password protection or access method. control. Information must be encrypted using an approved encryption method. Approval of the 'information owner' is required before the information is placed on the internet. Application subject to security audit, prior to implementation. Information must be encrypted Information not to be made using encryption functions and available via the internet. protocols approved by the Manager, Operational Security. Information not to be made available via the internet. Disposal Disposal of media / information equipment. Electronic Transmission transmission including: Within departmental emails instant messaging text messages facsimile documents. Remember that emails, text messages and faxes may be departmental documents, and suitable records need to be kept. WAN or school LAN. Outside departmental No specific WAN or school LAN. security requirements. Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 6 of 7 Information security classification Item Action Public Unclassified In-confidence (excludes Protected Highly protected cabinet-in-confidence) Refer to the Information Management (IM) Procedure recordkeeping section. Extranets. No specific security requirements. Approval of 'information owner' required before information is placed on extranets. Extranet will be subject to security audit, prior to implementation. Information must be encrypted Information not to be made using an approved encryption available via extranet. method. Information not to be made available via extranet. Wireless. No specific security requirements. Wireless network to be secured in accord with the Mobile Telecommunications Facilities procedure. Wireless network to be secured in accord with the Mobile Telecommunications Facilities procedure. Information not to be made available via wireless network. Information not to be made available via wireless network. Faxes. No specific security requirements. May be transmitted in May be transmitted in the the clear (i.e. unclear (i.e. un-encrypted) on encrypted). internal networks only. Faxes should not be used for protected information. Faxes should not be used for highly protected information. Mobile phones. No specific security requirements. May be transmitted in Mobile phones should not be the clear (i.e. unused to discuss classified encrypted) information. Mobile phones should not be used to discuss classified information. Mobile phones should not be used to discuss classified information. Security and licence This document has an information security classification of public. © The State of Queensland (Department of Education and Training) 2013 Unless otherwise noted below, materials included in this paper are licensed under a Creative Commons Attribution 3.0 Australia licence. To view a copy of this licence, visit http://creativecommons.org/licenses/by/3.0/au/ Last review date: 7 April 2014 Final TRIM Ref: 14/32951 Uncontrolled copy. Refer to the Department of Education and Training Policy and Procedure Register at http://ppr.det.qld.gov.au to ensure you have the most current version of this document. Page 7 of 7






