cloud computing.
advertisement

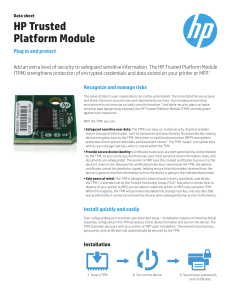
TUTORIAL PROPOSAL CyberSec2012 SECURITY, TRUST AND PRIVACY IN EMBEDDED SYSTEMS AND CLOUD COMPUTING. Research Group Members: Dr. Jamalul-lail Ab Manan (Project Leader) Mohd Anuar Mat Isa Mohd Faizal Mubarak Hadi Khorasanizadeh Hamed Khiabani Farag Elhagari Usama Tharwat Farag Elhagari 1. TITLE Security, Trust and Privacy in Embedded Systems and Cloud Computing. 2. SUMMARY Our research group will present tutorials and booths that cover latest research trends in security, trust and privacy. This research group is joint ventures between researchers in university and industry such as MIMOS, UITM, UPM, UTM, CSM and etc. The aim of research group is to promote security technology in defense the national sovereignty. 3. TOPICS A) Future Challenges in Information Security (Dr Jamal) Dr Jamalul-lail will present the Future Challenges in Information Security and in particular issues related to security, trust and privacy in emerging technologies. He will give an example of the importance of Security, Trust and Privacy (STP) in two sectors of the country’s economy, i.e. Healthcare and Education. STP will make its way in all emerging technologies. B) Fundamental of Trusted Computing (Usama) Actually, exposure of data on systems, system compromise due to software attack, lack of user identity assurance for authorization (identity theft), and physical theft of laptops and computing devices are some examples of the concerns of information and communication technology (ICT) users and organizations. The Trusted Computing Group (TCG), which is a not-for-profit organization, came into existence to respond to this need. The TCG has therefore chosen the approach of having a physically secure trusted component, Trusted Platform Module (TPM), in order to design a Trusted Platform (TP). The TPM works as a root, building block, of trust in TP. In this talk, we will discuss the concepts of TC, the main features of TP and the TPM security services. C) Remote Attestation (Faizal) Today’s computer access techniques can provide security to computer system if it designed to take into account various threats. In recent years computer threats are also becoming more dangerous and can easily cause damages to computer system. Usually, authentication is a very common computer access technique between remote systems (clients) to the server. Unfortunately, most of the authentication methods are without system integrity verification and hence poses system security threat because unverified applications running inside host platform which can be compromised either by any malicious codes or man in the middle attack. In order to strengthen the system security of current authentication system between client and server, integrity verification (attestation) module should be implemented to create trust between them. The embedded trusted platform module (TPM) inside the client host and server will enable system integrity measurements and verifications. D) Multi Tenancy of Cloud Computing (Hamed & Hadi) Cloud computing in essence does not provide the required assurance for many applications. This is the impeding factor holding many players keeping them away from migrating to a cloud based system. “Trusted Multi-Tenant Infrastructure Work Group” was formed in 2010 to develop the standards for implementing Shared infrastructures, Multi-provider infrastructures, Reference models and implementation guidance and to identify and address gaps in existing standards. The recently established workgroup is intended to extent the currently developed specifications from Trusted Network Connect, Trusted Platform Module and Virtualization workgroups. The objectives of Trusted Multi-tenant infrastructure is to assist in trust assessment of the cloud service providers at all times. In this section the necessity for this standard will be explained. Also trust requirement for utilizing the cloud based infrastructure will be elaborated. E) Technical Overviews & Programming for Trusted Platform Module (TPM) version 1.2 (Anuar) Trusted Computing Group (TCG) defines some key elements to evaluate trustworthiness of the hardware and software using root of trust in the security architecture. The TCG’s Trusted Platform Modules (TPM) specifications are an industry attempt to build a series of “roots of trust” in a computing platform. To interface with the TPM chip, the TCG prescribe a standard interface to communicate with the TPM. With all these specifications coming from the TCG group, the developer community lacks the understanding of how trusted platform can be implemented in a system. The main question coming from the community is “How can we be assured device(s) and system(s) are trusted if we use trusted computing platform (e.g. TPM) as root of trust?”. In order to answer this question, we need to refer to its definition, architecture, design and implementation of trusted platform as mentioned by the TCG. Acquiring full knowledge of Trusted Computing is a critical success factor to successfully develop or modify existing application that including design, coding and testing the TPM based application. This tutorial presents a bridging between the concepts and practices of the TPM and its related services. Therefore, this tutorial will clarify the concept of establishing trust and its implementation (including programming) for a secure platform. The topic for presentation is Technical Overviews & Programming for Trusted Platform Module (TPM) version 1.2. The material for presentations and demos are: Technical demos for concept and practice of the TPM. How to setup a computer system and enabling TPM on the machine. Downloading and installing tools for TPM’s Programming. Go through TPM Based Services (TBS) API in Windows 7. Writing sample C codes through TBS API in Windows 7. Compiles and runs TPM Emulator for machine without TPM in Windows 7. Compiles and runs Trousers (Trusted Software Stack (TSS)) in Windows 7. Writing sample C codes through TSS’s API in Windows 7. Hacking the Windows TBS. * All materials are provided by author. If participant interested to have a copy, they are required to bring a USB disk around 5 GB for the materials. To do lab programming, the machine must have TCG’s TPM 1.2 compliant chip and Windows 7. However, participant may use TPM emulator if their machine did not have a physical TPM chip. F) Potential Security Trust and Privacy (STP) Projects (Dr. Jamal) Dr Jamalul-lail will present areas of focus in STP Research. Among the areas that will be highlighted will cover areas in Education and Healthcare. G) Booth for Demo the Existing Research Works. (We need 4 tables with 4 Power Extensions) a) Remote Attestation for network communication. b) Trusted Integrity Verification Architecture (IVA) for Windows Operating Systems. c) Active Management Technology (AMT) for defense against cyber-terrorism attacks. d) Trusted Wireless Sensor Node for preventing node cloning attack in wireless sensor network. 4. Format and duration (May do adjustment based on organizer schedules) Title Introduction to Security, Trust and Privacy Fundamental of Trusted Computing Remote Attestation Break Multi Tenancy of Cloud Computing Technical Overviews & Programming for Trusted Platform Module (TPM) version 1.2 Future Works Booth for Demo the Existing Research Works Format Time Duration Presentation 9.00-9.15 AM 15 minutes Presentation Presentation Presentation Presentation / Demo 9.15-9.45 AM 9.45-10.15 AM 10.15-10.30 AM 10.30-11.15 AM 11.15-11.45 AM 30 minutes 30 minutes 15 minutes 45 minutes 30 minutes Presentation Booth 11.45-12.00 PM 12.00-12.30 PM 15 minutes 30 minutes 5. Organizer CV Dr Jamalul-lail Ab Manan graduated from University of Sheffield, UK with a Bachelor in Electrical Engineering (B. Eng). He pursued his Master of Science (MSc) in Microprocessor Engineering from University of Bradford, UK and PhD in Communications Engineering from University of Strathclyde, Glasgow, UK. He has been the Senior Director at Advanced Information Security Cluster, MIMOS Berhad. He has 17.5 years of experience in teaching Electrical and Electronics, Microprocessor Engineering and Network Security. He has many years of industrial experience as Network Engineer, Senior Manager and Senior Vice President in ICT based government linked companies in Malaysia. In MIMOS Berhad, his current research focus is Information Security, particularly in Encryption, Trusted Computing, Privacy Enhancing Technologies. He is currently the Principal Researcher for Privacy Enhancing Technology research in MIMOS. Mohd Anuar Mat Isa is a former researcher in the MIMOS Berhad. Currently, he is doing a full time research as PhD student. Mohd Anuar has wide experience conducting research and development in Trusted Computing. His security experience is rooted in Windows Operating Systems, virtualization and embedded systems. He also a visiting lecturer and research officer in Faculty Electical Engineering at the UiTM Shah Alam. Mohd Faizal Bin Mubarak is currently working at MIMOS as a Staff Researcher and has been working for almost 15 years and has vast experiences in telecoms and telecommunications systems. Involve in various types of research especially in information security. His research interests are on RFID, sensors, security and privacy, trusted computing, networking, operating system and secured programming. He has received professional certificates from EC-Council for Certified Ethical Hacker on 2009 and Certified Secure Programmer on 2008. He also is currently doing part-time PhD at UITM, Shah Alam. Hadi KhorasaniZadeh started working as network administrator and programmer on various project at the age of 12. Studied bachelor degree in Telecommunication Engineering (Electrical Engineering) at Amirkabir University of Tehran. Continued studying in the UK, at Aston Internet Technology where MSc with distinction in internet technology was obtained. Soon After, started working as a network security/ Firewall engineer in Emco Iran consulting engineers for a year before starting his Ph.D. in Malaysia. His other professional certifications include CISSP, GCIH, CEH, ISO 27001 Implementation, CCNA and CCNA Security. Hamed Khiabani is an Information Security expert with over 17 years hands on experience in IT industry. He received his B.Eng. degree in computer engineering-hardware from Iran University of Science and Technology in 1995 and his M. Eng. degree in computer architecture from Azad University-Science & Research Branch in 1998. He is currently pursuing his Ph.D. degree in Computer Science (information Security) in University Technology Malaysia while attached to MIMOS Berhad under a research collaboration program. Hamed holds CISSP, GPEN, GCIH, GCFA, GSEC, CEH, CHFI and ISO27001 Lead Auditor certifications and is a Juniper & Fortinet certified engineer. He is member of GIAC Advisory Board and graduate student member of IEEE. Usama Tharwat Elhagari is a researcher in The Egyptian Nuclear Research Centre. He graduated from Elmenufia University, Egypt; with a Bachelor in Electronic Engineering (Computer Science and Engineering). He got his Master of Computer Science in Information Security from the Center for Advanced Software Engineering (CASE),Universiti Teknologi Malaysia (UTM). He has been a lecturer in Kingdom of Saudi Arabia at different universities. He has been the system administrator of the physical protection systems of the second Egyptian research reactor (ETRR-R). He represented his country, Egypt, in many meetings to discuss the convention revision of nuclear material physical protection, held at the International Atomic Energy Agency (IAEA), Vienna, Austria. Currently, he is a PhD candidate in Universiti Teknologi Malaysia (UTM) and he is attached to the Malaysian Security Evaluation Facility (MySEF) Laboratory, Cyber Security Malaysia (CSM). His major research interests include computer security, security analysis, formal methods, physical security systems, RFID, trusted computing and security testing. 6. Expected Participants 15~30 participants from university. 15~30 participants from industry. 7. Significance in relation to the topics of the conference This research workgroup will focus the presentation and booth regarding these security issues: i) Trusted Computing for PCs, Embedded Systems and Cloud Computing. ii) Anonymity (Privacy) for Online Services. iii) Critical infrastructure protection from electronic warfare and cyber-terrorism. iv) Authentication and access control systems based on Trusted Computing’s Remote Attestation. v) Security policies, trust and identity management for client-server architecture. 8. Details of any previous workshops i) ii) iii) Trusted Computing & Privacy - Advance Informatics School (AIS), UTM Campus KL, March 2011. Trusted Computing – Faculty of Electrical Engineering, UITM Shah Alam, Nov 2009. 2nd Asia Pacific Trusted Infrastructure Summer School 2008 (APTISS’08), KL, August 2008.