View session overview, activities and output
advertisement

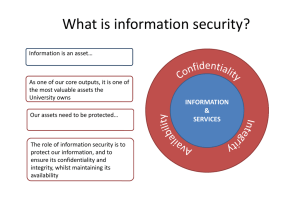
It’s the Data Stupid Overview o Cybersecurity is often focused on the tools and techniques of cyber defense. While appropriate, the purpose of these protections is to protect data that is the key assets of the enterprise. Such data may be intellectual property, such as inventions or trade secrets, or customer related data. Activities o Discuss the ability to identify key data assets/crown jewels and to appropriately protect them from various classes of adversaries What are your crown jewels and who makes that determination? How do they identify important data assets? What factors are considered? What are the threats to these assets that you protect against? Insiders leaking/exfiltrating data? External actors breaching protections to collect data? Failure of storage devices? Ransomware? How are you kept aware of changes in threat related to important data? Where do you keep your data? Your data center? A government data center? A commercial data center? Do you know where your key data assets are stored? What other organizations access your key data assets? What trust relationships exist with these other organizations? How do you manage these organizations’ access? How do you respond to a breach to minimize impact? How do you measure the impact of a breach? Do you insure against cyber loss? o Identify tools and techniques that can be used to assess, manage and protect key enterprise data assets. For the threats identified above, how do you mitigate risk associated with these threats? What tools do you use today? Do you feel your tools adequately protect your data against known threats? Do you have plans for additional tools in the future? What does “data-centric protection” mean to you? Does your organizations use it? What role do data loss prevention techniques play in your data security solution? How do you know your data is protected? What measures do you use to gauge risk/exposure? Do you share information about data breach incidents or operational impact on mission/business? If so, with whom? If not, why not? What analysis/information would you want back as a result of sharing? Would you be willing to share information to enable cyber insurance? Output o Prioritized list of desired capabilities to protect and defend key enterprise data assets. What are the three most important capabilities you have today to protect data assets? What are the three capabilities you lack today that you most want to protect data assets? Are there data protection capabilities you use today that you feel are unnecessary/ineffective? Moderator o Don Faatz (MITRE) o Tom Finan (DHS) o Travis Rosiek (FireEye)