esMD HL7 Digital Signatures Ballot Reconciliation Community
advertisement

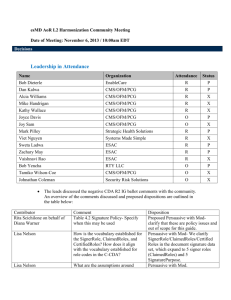
esMD HL7 Digital Signatures Ballot Reconciliation Community Meeting Date of Meeting: November 20, 2013 / 10:00am EDT Decisions Leadership in Attendance Name Organization Attendance Status Bob Dieterle EnableCare R P Dan Kalwa CMS/OFM/PCG R P Alcia Williams CMS/OFM/PCG R X Mike Handrigan CMS/OFM/PCG R X Kathy Wallace CMS/OFM/PCG R X Joyce Davis CMS/OFM/PCG O X Joy Sam CMS/OFM/PCG O X Mark Pilley Strategic Health Solutions R P Viet Nguyen Systems Made Simple R X Sweta Ladwa ESAC R P Zachary May ESAC R P Vaishnavi Rao ESAC R P Bob Yencha RTY LLC O X Tamiko Wilson-Coe CMS/OFM/PCG O X Johnathan Coleman Security Risk Solutions O X Announcements: o All esMD community meetings are cancelled for the week of 11/25-11/29 due to the Thanksgiving Holiday. o The edited and updated version of the C-CDA R2 IG will be posted to the esMD wiki for community review during the week of 11/25. The leads will discuss any concerns or comments regarding IG resolutions during the community meeting on 12/4. Bob D. presented the HL7 Digital Signatures ballot reconciliation comments spreadsheet and the comments and dispositions discussed are outlined in the table below: Contributor John Moerke Comment Section 3.4.1- Verify that the signature date is appropriate. Disposition Persuasive with Mod- Change wording to inspect for consistence with signature and timestamp policy from verify for the date validation. Persuasive with Mod. John Moerke Security considerations: you must identify that there is a risk of datestamp fabrication and this risk is not managed by this specification and needs to be operationally managed through good policy. John Moerke Section 3.3.1- esMD-9:sdtc:signatureText DoR SHOULD contain one [XAdES-X-L] validation signature- How does one know if they have this? Position sensitive approach is fragile. Persuasive with Mod- Added xml tags to the various components of the digital signature contained in the signature text to identify each element. John Moerke Section 3.2.6- This section outlines ONE solution to the revocation of delegation. It should be cast as ONE solution. I would rather see this removed from the specification as being too situation specific. Section 3.4.1- you have identified many optional values in the signature block. What processing of these optional values is needed? Persuasive with Mod- We are allowing for multiple revocation solutions by adding <dortype> which will also allow for the selection of other validation/revocation processes. Persuasive with Mod- use of optional fields should be agreed upon by trading partners and is outside the scope of this document. Persuasive with Mod- add general introduction and move all CMS/esMD specific language to an example. John Moerke John Moerke John Moerke John Moerke John Moerke Lisa Nelson Section 1.0- The introduction should be purely about what the specification is about. There could be a background that identifies the CMS and esMD as motivating and precedent setting examples. Section 1.0- Alternatives to this method of digital signature should be mentioned. No need for details, but it should be mentioned that XMLSignature contains 2 other methods of signatures that are appropriate for policy situations. The delegation of rights model outlined is not the only model for delegation. I am concerned that the specification is locking in without room for other methods. Section 2.0- The use-cases should be made more general purpose without losing the technical needs. The examples from CMS and esMD can be used as examples but should not be outlined as the demanding use-cases. Section 3.0- The rationale for “excluding the legalAuthenticator and authenticator from the calculation of the digest” needs further explanation. Not Persuasive with Mod- This guide focuses only on embedded digital signatures and other guides focus on external processes and there may be any number of these. Persuasive with Mod- Add <dortype> to allow for more than one approach to DoR. Persuasive with Mod- Eliminate all CMS/esMD specific language from the use case descriptions. Persuasive with Mod- add additional explanation- we are not eliminating legal Authenticator and authenticator from the CDA, just from the information that is digitally signed by each of the signers. Lisa Nelson Section 3.3- How do co-signatures and counter signatures play into this? Persuasive with Mod- Expand descriptions for co-signer and counter signer in the notes section in 3.3. Zach will follow up with Bob Dolin regarding the HL7 C-CDA IG to verify that no detail is given within the signature text and ensure that signature text contents are not specified in any examples that may be incorrect. Zach will add an example in the appendix of the C-CDA R2 IG to show how to incorporate signatureText in any CDA R2 and verify that all language allows for use in any CDA R2. The leads specified that any documents that have been previously digitally signed must not be altered in terms of sections of the CDA signed. Action Items Name Subject Zach C-CDA R2 IG Zach C-CDA R2 IG Task Add an example in the appendix of the C-CDA R2 IG to show how to incorporate signatureText in any CDA R2 and verify that all language allows for use in any CDA R2. Follow- up with Bob Dolin regarding the CCDA to verify that no detail is given within the signature text and ensure that signature text contents are not specified in any examples that may be incorrect. Due Date 11/22 11/22