Solution, Information Security and Cyber Laws CT II

JRE SCHOOL OF Engineering
CLASS TEST-2 EXAMINATIONS OCTOBER 14
Subject Name Information Security and Cyber Laws
Roll No. of Student
Date 13 October 2014
For B.Tech. (IT) Branch
Subject Code EIT-505
Max Marks 30 Marks
Max Duration 1 Hr.
Time 9:20 am to 10:20 am
SECTION – A (
3 marks * 5 Questions = 15 Marks)
NOTE: ATTEMPT ALL QUESTIONS
Q.1
What do you mean by Digital Signature System (DSS) ? How is DSS related to public key cryptography ?
Ans: A digital signature (not to be confused with a digital certificate) is an electronic signature that can be used to authenticate the identity of the sender of a message or the signer of a document, and possibly to ensure that the original content of the message or document that has been sent is unchanged. Digital signatures are easily transportable, cannot be imitated by someone else, and can be automatically time-stamped. The ability to ensure that the original signed message arrived means that the sender cannot easily repudiate it later.
A digital signature can be used with any kind of message, whether it is encrypted or not, simply so that the receiver can be sure of the sender's identity and that the message arrived intact. A digital certificate contains the digital signature of the certificate-issuing authority so that anyone can verify that the certificate is real.
In DSS we perform opposite of public key cryptography i.e. we sign using private key and verify using public key
Q.2
What is Penetration Testing ? Why do you think it plays an important role in modern day software such as mobile software ?
Ans: A penetration test, or the short form pentest, is an attack on a computer system with the intention of finding security weaknesses, potentially gaining access to it, its functionality and data
The process involves identifying the target systems and the goal, then reviewing the information available and undertaking available means to attain the goal. A penetration test target may be a white box (where all background and system information is provided) or black box (where only basic or no information is provided except the company name). A penetration test will advise if a system is vulnerable to attack, if the defenses were sufficient and which defenses (if any) were defeated in the penetration test.
Q.3
Briefly write about hashing ? What do you mean by collision in context of hashing.
Ans: Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string. Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.
Collision or clash is a situation that occurs when two distinct pieces of data have the same hash value
Cryptographic hash functions have many information security applications, notably in digital signatures, message authentication codes (MACs), and other forms of authentication. They can also be used as ordinary hash functions, to index data in hash tables, for fingerprinting, to detect duplicate data or uniquely identify files, and as checksums to detect accidental data corruption.
Indeed, in information security contexts, cryptographic hash values are sometimes called (digital) fingerprints, checksums, or just hash values, even though all these terms stand for more general functions with rather different properties and purposes.
Q.4
Briefly explain the following terms:
(a) Authentication
(b) Authorization
(c) Non-repudiation
Authentication is the process of determining whether someone or something is, in fact, who or what it is declared to be. In private and public computer networks (including the Internet), authentication is commonly done through the use of logon passwords.
Authorization is the process of giving someone permission to do or have something. In multi-user computer systems, a system administrator defines for the system which users are allowed access to the system and what privileges of use (such as access to which file directories, hours of access, amount of allocated storage space, and so forth).
Nonrepudiation is the assurance that someone cannot deny something. Typically, nonrepudiation refers to the ability to ensure that a party to a contract or a communication cannot deny the authenticity of their signature on a document or the sending of a message that they originated.
Q.5
Write a short note on VPN. List down the main components needed to create VPN connections.
VPN is a network that is constructed by using public wires — usually the Internet — to connect to a private network, such as a company's internal network. There are a number of systems that enable you to create networks using the Internet as the medium for transporting data. These systems use encryption and other security mechanisms to ensure that only authorized users can access the network and that the data cannot be intercepted.
Components of virtual private networks
A VPN connection includes the following components:
VPN server
A computer that accepts VPN connections from VPN clients.
VPN client
A computer that initiates a VPN connection to a VPN server. A VPN client can be an individual computer or a router.
Tunnel
The portion of the connection in which your data is encapsulated.
VPN connection
The portion of the connection in which your data is encrypted. For typical secure VPN connections, the data is encrypted and encapsulated along the same portion of the connection.
SECTION – B (
5 marks * 1 Questions = 5 Marks)
Q.6 What do you understand by the terms Cryptanalysis ? Explain various types of cryptanalytic attacks ?
Cryptanalysis refers to the study of ciphers, ciphertext, or cryptosystems (that is, to secret code systems) with a view to finding weaknesses in them that will permit retrieval of the plaintext from the ciphertext, without necessarily knowing the key or the algorithm. This is known as breaking the cipher, ciphertext, or cryptosystem.
1) Known-plaintext analysis: With this procedure, the cryptanalyst has knowledge of a portion of the plaintext from the ciphertext. Using this information, the cryptanalyst attempts to deduce the key used to produce the ciphertext.
2) Chosen-plaintext analysis (also known as differential cryptanalysis): The cryptanalyst is able to have any plaintext encrypted with a key and obtain the resulting ciphertext, but the key itself cannot be analyzed. The cryptanalyst attempts to deduce the key by comparing the entire ciphertext with the original plaintext. The Rivest-Shamir-Adleman encryption technique has been shown to be somewhat vulnerable to this type of analysis.
3) Ciphertext-only analysis: The cryptanalyst has no knowledge of the plaintext and must work only from the ciphertext. This requires accurate guesswork as to how a message could be worded.
It helps to have some knowledge of the literary style of the ciphertext writer and/or the general subject matter.
4) Man-in-the-middle attack: This differs from the above in that it involves tricking individuals into surrendering their keys. The cryptanalyst/attacker places him or herself in the communication channel between two parties who wish to exchange their keys for secure communication (via asymmetric or public key infrastructure cryptography). The cryptanalyst/attacker then performs a key exchange with each party, with the original parties believing they are exchanging keys with each other. The two parties then end up using keys that are known to the cryptanalyst/attacker.
This type of attack can be defeated by the use of a hash function.
5) Timing/differential power analysis: This is a new technique made public in June 1998, particularly useful against the smart card, that measures differences in electrical consumption over a period of time when a microchip performs a function to secure information. This technique can be used to gain information about key computations used in the encryption algorithm and other functions pertaining to security. The technique can be rendered less effective by introducing random noise into the computations, or altering the sequence of the executables to make it harder to monitor the power fluctuations. This type of analysis was first developed by Paul Kocher of
Cryptography Research, though Bull Systems claims it knew about this type of attack over four years before.
A ciphertext-only attack is one in which the cryptanalyst obtains a sample of ciphertext, without the plaintext associated with it. This data is relatively easy to obtain in many scenarios, but a successful ciphertext-only attack is generally difficult, and requires a very large ciphertext sample. A known-plaintext attack is one in which the cryptanalyst obtains a sample of ciphertext and the corresponding plaintext as well.
A chosen-plaintext attack is one in which the cryptanalyst is able to choose a quantity of plaintext and then obtain the corresponding encrypted ciphertext.
An adaptive-chosen-plaintext attack is a special case of chosen-plaintext attack in which the cryptanalyst is able to choose plaintext samples dynamically, and alter his or her choices based on the results of previous encryptions.
A chosen-ciphertext attack is one in which cryptanalyst may choose a piece of ciphertext and attempt to obtain the corresponding decrypted plaintext. This type of attack is generally most applicable to public-key cryptosystems.
An adaptive-chosen-ciphertext is the adaptive version of the above attack. A cryptanalyst can mount an attack of this type in a scenario in which he has free use of a piece of decryption hardware, but is unable to extract the decryption key from it.
SECTION – C (
10 marks * 1 Questions = 10 marks)
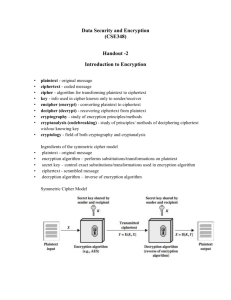
Q.7 Using block diagrams, explain symmetric and asymmetric cryptography. What are the pros and cons of each of the two ? symmetric cryptography (or symmetric-key encryption), the same key is used for both encryption and decryption as shown in Figure 1.
Figure 1. Symmetric key encryption
Symmetric key ciphers are valuable because:
It is relatively inexpensive to produce a strong key for these ciphers.
The keys tend to be much smaller for the level of protection they afford.
The algorithms are relatively inexpensive to process.
Therefore, implementing symmetric cryptography (particularly with hardware) can be highly effective because you do not experience any significant time delay as a result of the encryption and decryption. Symmetric cryptography also provides a degree of authentication because data encrypted with one symmetric key cannot be decrypted with any other symmetric key. Therefore, as long as the symmetric key is kept secret by the two parties using it to encrypt communications, each party can be sure that it is communicating with the other as long as the decrypted messages continue to make sense.
Typically, with a symmetric key, you can exchange the key with another trusted participant; usually you produce a unique key for each pair of participants. You can be assured that any messages that you exchange, which are encrypted in a specific key, between the participants can only be deciphered by the other participant that has that key. In this way, the key must be kept secret to each participant. Consequently, these keys are also referred to as secret-key ciphers. If anyone else finds the key, it affects both confidentiality and authentication. A person with an unauthorized symmetric key not only can decrypt messages sent with that key, but can encrypt new messages and send them as if they came from one of the two parties who were originally using the key.
The major drawback to secret-key ciphers is in exchanging the secret key because any exchange must retain the privacy of the key. This usually means that the secret key must be encrypted in a different key, and the recipient must already have the key that will be needed to decrypt the encrypted secret-key. This can lead to a never-ending dependency on another key.
Asymmetric cryptography or public-key cryptography is cryptography in which a pair of keys is used to encrypt and decrypt a message so that it arrives securely. Public key cryptography
involves a pair of keys known as a public key and a private key (a public key pair), which are associated with an entity that needs to authenticate its identity electronically or to sign or encrypt data. Each public key is published and the corresponding private key is kept secret. Data that is encrypted with the public key can be decrypted only with the corresponding private key.
RSA public key pairs can be any size. Typical sizes today are 1024 and 2048 bits.
Public key cryptography enables the following:
Encryption and decryption, which allow two communicating parties to disguise data that they send to each other. The sender encrypts, or scrambles, the data before sending it. The receiver decrypts, or unscrambles, the data after receiving it. While in transit, the encrypted data is not understood by an intruder.
Figure 1. Public-key encryption
************************