CSE - 702 - NIT Arunachal Pradesh
advertisement

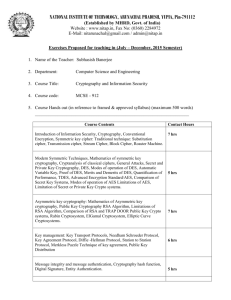
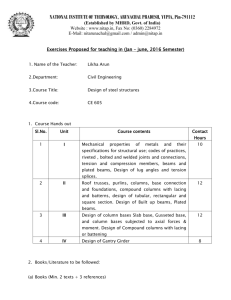
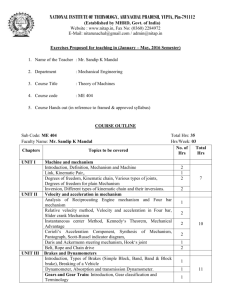
NATIONAL INSTITUTE OF TECHNOLOGY, ARUNACHAL PRADESH, YUPIA, Pin-791112 (Established by MHRD, Govt. of India) Website : www.nitap.in, Fax No: (0360) 2284972 E-Mail: nitarunachal@gmail.com / admin@nitap.in Exercises Proposed for teaching in (July – December, 2015 Semester) 1. Name of the Teacher: Subhasish Banerjee 2. Department: Computer Science and Engineering 3. Course Title: Information Security 4. Course code: CSE - 702 5. Course Hands out (in reference to framed & approved syllabus) (maximum 500 words) ____________________________________________________________________ Unit I: Information Technology in 21st Century :Introduction, Recent Progress of Computer Technologies, Newer technologies, Molecular Electronics, Bio/Chemical Computers, Autonomic Computing, Quantum Computing, Current and Future Communication Technologies , Personal Communication , Cellular Communication/Cordless , telephone/DCS etc , Wireless data/ LAN/Wireless Ethernet, Protocols, Standards, etc, Paging/VSAT , Mobile Satellite Service , Wireless ATM, Internet , Local Loop Transport Technology , Fiber Free Optical Communication/Network , DSL Technologies, ADSL.VDSL, xDSL/ Comparison with Modem/ISDN, Multimedia Communication and Standards , UTN Personal Communication , 2G to 3G , Beyond 3G , e-business etc , Knowledge age etc. Unit II: Advanced Error Control Techniques in Network : Introduction, Basic BEC Techniques, Different Modified Techniques, Sastry’s and Morris Modifications Other Modifications, Two Level Coding, Parity Selection in Two Level Coding, Packet Combining Scheme, Modified Packet Combining Scheme, ARQs for Variable Error Rate Channels/ YAO Technique, Chakraborty’s Technique, New Schemes, ARQ Schemes Under Practical Situations, GBN and SRQ under different schemes, Issues of sending different signal waveforms for repeated retransmitted copies, Application of multilevel coding scheme in variable error rate channel, Majority Technique, Analysis of the majority scheme for SW ARQ. Unit III: Data /Network Security Techniques and Approaches :Introduction, Cryptography, Conventional Encryption, Classical Cipher, Substitution Codes, Transposition codes, Cryptanalysis of classical ciphers, General Attacks, Secret and Private Key Cryptography, Stream Cipher, Block Cipher, DES, Modes of operation of DES, Automatic Variable Key, Proof of DES, Merits and Demerits of DES,Quantification of Performance, TDES, IDEA, Advanced Encryption Standard/AES, Comparison ofSecret Key Systems, Modes of operation of AES Limitations of AES, Limitation of Secret or Private Key Crypto systems , Key Transport Protocols, Needham – Schroeder Protocol, Key Agreement Protocol, Diffie-Hellman Protocol, Station to Station Protocol, Merkles’s Puzzle Technique of key agreement, Quantum Security, Public Key Cryptography RSA Algorithm, Hoe Secured is RSA Algorithm , Limitations of RSA Algorithm, Trapdoor Knapsack Problem , McEliece’s Public Key ; Comparison of RSA and TRAP DOOR Public Key Crypto systems; PUBLICKEY CRYPTOGRAPHIC NATIONAL INSTITUTE OF TECHNOLOGY, ARUNACHAL PRADESH, YUPIA, Pin-791112 (Established by MHRD, Govt. of India) Website : www.nitap.in, Fax No: (0360) 2284972 E-Mail: nitarunachal@gmail.com / admin@nitap.in MECHANISMS , Digital Signature ,Digital Signature under RSA algorithm ; CHECK FUNCTIONS for authenticity, integrity and norepudiation of the message content, Non repudiation by digital signature of RSA, Strength of Mechanism ; PGP (Pretty Good Privacy) Modern Crypto Systems ,Integrated Solution of Security and Error Control; Internet Security . Unit IV: IT and Looking into FUTURE IT : Information and Knowledge, Proof Of Tom Stonier’s Theorem; Tom Stonier’s Theorem With Shannon’s Theorem , Proposing Laws Of Information , Mass Energy Equivalency; Present Imbalance In It Era, Digital Divide, Dd Between The Developed And The Developing, Dd Trend In Future, Dd Between India And China Dd Within A Country, Dd In Language Zone; Looking Differently, Looking into Future IT 6. Books/Literature to be followed: (a) Books (Min. 2 texts + 3 references) (i) Title Author Publisher Edition Information Technology Network and Internet C. T. Bhunia New Age Publication ----------- (ii) Title Author Publisher Edition Cryptography and Network Security B. A. Forouzan, D. Mukhopadhyay Tata McGraw Hill Second Edition (iii) Title Author Publisher Edition Cryptography and Network Security W. Stallings Pearson Fifth Edition (iv) Title Author Publisher Edition Cryptography Theory and Practice D. R. Stinson Chapman & Hall/CRC Third edition (v) Title Author Publisher Edition Cryptography and Network Security Atul Kahate Tata McGraw-Hill Second Edition NATIONAL INSTITUTE OF TECHNOLOGY, ARUNACHAL PRADESH, YUPIA, Pin-791112 (Established by MHRD, Govt. of India) Website : www.nitap.in, Fax No: (0360) 2284972 E-Mail: nitarunachal@gmail.com / admin@nitap.in (b) Magazines/Journals (Minimum 5) (i) Information Security - SC Magazine, Haymarket Media Inc., United State (ii) InfoSec Magazines, United Kingdom (iii)Journal of Computer Security, IOS press, Netherland (iv) International Journal of Information Security - Springer, United State (v) Journal of Information Security and Applications - Elsevier, Netherland 7. Mode of Teaching: J.C Bose/S. N. Bose (please tick). J. C. Bose 7. If the course is of practices, list the experiments to be offered. (i). (ii). (iii). (iv). (v). (vi). Automatic Repeat Request (ARQ) Asymmetric Cipher: RSA, Advance Error Control Implementation Digital Signatures: RSA digital signature scheme, Elgamal digital signature, etc. Entity Authentication: Challenge response, Zero knowledge, etc Key management: Diffie- Hellman, etc. Are the manuals ready for the experiments to be conducted? Yes Remarks/ Endorsement by the HoD With his /her signature with date Name of the Teacher: Subhasish Banerjee Designation: Assistant Professor Signature with Date: