DES Encryption
advertisement

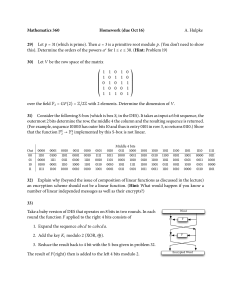
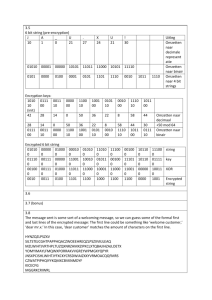
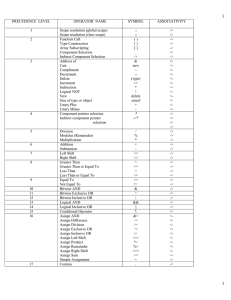
CSCI 440 – Computer Security – DES Algorithm Encrypt a message of your choice up to 16 bits in length (2 characters as ASCII) using 2 rounds of a simplified DES. You will first create a 16 bit key (2 characters as ASCII) for the encryption/decryption process. Once encrypted trade your key and ciphertexts and decrypt the characters. 𝑀𝑒𝑠𝑠𝑎𝑔𝑒 (𝐴𝑆𝐶𝐼𝐼) = 𝑀𝑒𝑠𝑠𝑎𝑔𝑒 (𝐵𝑖𝑛𝑎𝑟𝑦) = Step 1. Create subkeys from the 16 bit key, 𝐾 using the following tables for permutations and shift schedule. Eliminate the bits using the same method as DES. 𝐾 (𝐴𝑆𝐶𝐼𝐼) = 𝐾 (𝐵𝑖𝑛𝑎𝑟𝑦) = 𝑃𝐶1 12 10 15 11 5 14 1 2 6 9 4 13 7 3 𝑃𝐶1(𝐾) = Split 𝑃𝐶1(𝐾) into 2 halves and left rotation on schedule. 𝑆ℎ𝑖𝑓𝑡 𝑆𝑐ℎ𝑒𝑑𝑢𝑙𝑒 Round 1 1 Round 2 3 𝑅𝑜𝑢𝑛𝑑 1 𝐿𝑒𝑓𝑡 = 𝑅𝑜𝑢𝑛𝑑 1 𝑅𝑖𝑔ℎ𝑡 = 𝑅𝑜𝑢𝑛𝑑 2 𝐿𝑒𝑓𝑡 = 𝑅𝑜𝑢𝑛𝑑 2 𝑅𝑖𝑔ℎ𝑡 = Concatenate Round 1 Left and Right and permute using 𝑃𝐶2 to create 𝑆𝑢𝑏𝑘𝑒𝑦1 . Do the same for 𝑆𝑢𝑏𝑘𝑒𝑦2 using Round 2 Left and Right. 𝑃𝐶2 6 11 13 3 1 10 𝑆𝑢𝑏𝑘𝑒𝑦1 4 8 12 5 2 9 = 𝑆𝑢𝑏𝑘𝑒𝑦2 = Step 2. Permute message using Initial Permutation, 𝐼𝑃. 𝐼𝑃 2 12 5 11 14 8 13 1 6 16 3 15 10 4 9 7 𝐼𝑃 𝑅𝑒𝑠𝑢𝑙𝑡 = Split IP Result into left and right halves. 𝐿𝑒𝑓𝑡 = 𝑅𝑖𝑔ℎ𝑡 = Round 1 Step 3. Expansion and process 𝑆𝑢𝑏𝑘𝑒𝑦1 Expansion: Expand 𝑅𝑖𝑔ℎ𝑡 using Expansion table, 𝐸 below 𝐸 8 1 2 3 4 5 4 5 6 7 8 1 𝐸𝑥𝑝𝑎𝑛𝑠𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 = XOR with 𝑆𝑢𝑏𝑘𝑒𝑦1 𝑅1 ⊕ 𝑆𝑢𝑏𝑘𝑒𝑦1 = Substitution: Apply Substitution with S-boxes on each 6 bit Left and Right halves of 12-bit XORed result. 𝑆-𝐵𝑜𝑥1 (Left) 0𝑦𝑦𝑦𝑦0 0𝑦𝑦𝑦𝑦1 1𝑦𝑦𝑦𝑦0 1𝑦𝑦𝑦𝑦1 𝑥0000𝑥 0100 1101 0001 0110 𝑥0001𝑥 1011 0000 0100 1011 𝑥0010𝑥 𝑥0011𝑥 0010 1110 1011 0111 1011 1101 1101 1000 𝑥0100𝑥 1111 0100 1100 0001 𝑥0101𝑥 0000 1001 0011 0100 𝑥0110𝑥 𝑥0111𝑥 1000 1101 0001 1010 0111 1110 1010 0111 0𝑦𝑦𝑦𝑦0 0𝑦𝑦𝑦𝑦1 1𝑦𝑦𝑦𝑦0 1𝑦𝑦𝑦𝑦1 𝑥1000𝑥 0011 1110 1010 1001 𝑥1001𝑥 1100 0011 1111 0101 𝑥1010𝑥 1001 0101 0110 0000 𝑥1011𝑥 0111 1100 1000 1111 𝑥1100𝑥 0101 0010 0000 1110 𝑥1101𝑥 1010 1111 0101 0010 𝑥1110𝑥 0110 1000 1001 0011 0𝑦𝑦𝑦𝑦0 0𝑦𝑦𝑦𝑦1 1𝑦𝑦𝑦𝑦0 1𝑦𝑦𝑦𝑦1 𝑥0000𝑥 1101 0001 0111 0010 𝑥0001𝑥 0010 1111 1011 0001 𝑥0010𝑥 𝑥0011𝑥 1000 0100 1101 1000 0100 0001 1110 0111 𝑥0100𝑥 0110 1010 1001 0100 𝑥0101𝑥 1111 0011 1100 1010 𝑥0110𝑥 𝑥0111𝑥 1011 0001 0111 0100 1110 0010 1000 1101 0𝑦𝑦𝑦𝑦0 0𝑦𝑦𝑦𝑦1 1𝑦𝑦𝑦𝑦0 1𝑦𝑦𝑦𝑦1 𝑥1000𝑥 1010 1100 0000 1111 𝑥1001𝑥 1001 0101 0110 1100 𝑥1010𝑥 0011 0110 1010 1001 𝑥1100𝑥 0101 0000 1111 0011 𝑥1101𝑥 0000 1110 0011 0101 𝑥1110𝑥 1100 1001 0101 0110 𝑥1111𝑥 0001 0110 0010 1100 𝑆-𝐵𝑜𝑥2 (Right) 𝑥1011𝑥 1110 1011 1101 0000 𝑆𝑢𝑏𝑠𝑡𝑖𝑡𝑢𝑡𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 (8-𝑏𝑖𝑡𝑠) = Permutation: Permute of the 𝑆𝑢𝑏𝑠𝑡𝑖𝑡𝑢𝑡𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 using 𝑃-𝑏𝑜𝑥 𝑃-𝐵𝑜𝑥 6 4 7 3 5 1 8 2 𝑅𝑒𝑠𝑢𝑙𝑡 = XOR 𝑅𝑒𝑠𝑢𝑙𝑡 with 𝐿𝑒𝑓𝑡 𝐶𝑖𝑝ℎ𝑒𝑟𝑡𝑒𝑥𝑡 = 𝑥1111𝑥 0111 0010 1000 1011 Round 2 Swap 𝐶𝑖𝑝ℎ𝑒𝑟𝑡𝑒𝑥𝑡 and 𝑅𝑖𝑔ℎ𝑡. That is 𝐶𝑖𝑝ℎ𝑒𝑟𝑡𝑒𝑥𝑡 becomes the new Right Side and 𝑅𝑖𝑔ℎ𝑡 becomes the new 𝐿𝑒𝑓𝑡 𝐿𝑒𝑓𝑡 = 𝑅𝑖𝑔ℎ𝑡 = Repeat Expansion, Substitution and Permutation steps on 𝑅𝑖𝑔ℎ𝑡 using 𝑆𝑢𝑏𝑘𝑒𝑦2 . 𝐸𝑥𝑝𝑎𝑛𝑠𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 = 𝑅1 ⊕ 𝑆𝑢𝑏𝑘𝑒𝑦2 = 𝑆𝑢𝑏𝑠𝑡𝑖𝑡𝑢𝑡𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 = 𝑃𝑒𝑟𝑚𝑢𝑡𝑎𝑡𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 = XOR 𝑃𝑒𝑟𝑚𝑢𝑡𝑎𝑡𝑖𝑜𝑛 𝑅𝑒𝑠𝑢𝑙𝑡 and 𝐿𝑒𝑓𝑡 𝐶𝑖𝑝ℎ𝑒𝑟𝑡𝑒𝑥𝑡 = Concatenate 𝐶𝑖𝑝ℎ𝑒𝑟𝑡𝑒𝑥𝑡 and 𝑅𝑖𝑔ℎ𝑡 𝑅𝑒𝑠𝑢𝑙𝑡 = Step 4. Permute the ciphertext 𝑅𝑒𝑠𝑢𝑙𝑡 with 𝐼𝑃−1 𝐼𝑃−1 14 9 12 10 1 3 4 2 11 16 13 15 8 6 5 7 𝑬𝒏𝒄𝒓𝒚𝒑𝒕𝒆𝒅 𝑴𝒆𝒔𝒔𝒂𝒈𝒆 = Trade your encrypted message and your secret key with someone in class and decrypt their message using their key. What does their message say?