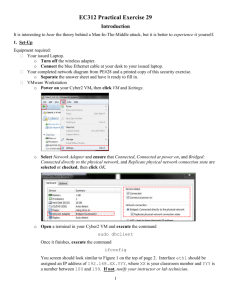
SI202: Week 1
advertisement

EC312 Lesson 29: The Man-In-The-Middle Attack Objectives: (a) Describe the Man-In-The-Middle (MITM) attack and list what advantages it provides the attacker. (b) Construct a routing table based on a network diagram and manipulate a routing table to exploit a specific target. (c) Describe the steps that should be taken to prevent false route injection and identify who is responsible for performing these preventative actions and how they can be applied. I. Trust 1. A Quick Review Where are we at in our understanding of how networks interconnect? We’ve talked about routing algorithms and how these weird things called routing tables are constructed; we’ve talked about the layers and protocols involved in networking; we’ve also talked about addressing schemes and specifically how MAC addresses and IP addresses are used; but, what is the point of all this? Much like the host section in the first six weeks of EC312, we need to understand how networks work before we can manipulate their operation and violate the principles of security. Much like a locksmith, once we understand how a lock operates, we know that a key is not the only thing that can open a door. If we are thinking like a locksmith about networks from a security perspective, what is the underlying assumption between routers in the routing algorithms they use to construct their routing tables? The assumption is that each router can trust the information that other routers are sending it. That is, Router A assumes by default that Router B is telling the truth about the state of its links or the distance between it and other routers. But what happens when that is not the case? Would a machine ever lie to another machine? Are there evil machines out there that want to do bad, mean, horrible things to people? Gasp, what if it was true! Have you ever seen Terminator 2: Judgment Day!? Sadly, most of your classmates were not born when this movie released, but I highly recommend it for your Netflix queue. You will not be able to call yourself a hacker until you watch it. 1 Example 1 Consider the network below. How would the routing table evolve using distance vector routing? RB 4 2 RA RD RC 5 2 Solution: B C D RA 4 (B) 5 (C) ∞ RB 4 (A) ∞ 2 (D) A C D A B D RC 5 (A) ∞ 2 (D) A B C RD ∞ 2 (B) 2 (C) Everyone shares table with neighbors. But what if Router C was evil and began to falsify information about its link to Router A; how would the routing table change? RB 4 2 RA RD RC 1 B C D RA 4 (B) 5 (C) ∞ A C D RB 4 (A) ∞ 2 (D) A B D Everyone shares table with neighbors. 2 2 RC 1 (A) ∞ 2 (D) A B C RD ∞ 2 (B) 2 (C) What does this mean for all of Router D’s traffic destined for Router A? More importantly, why would Router D’s traffic go through Router C instead? Fortunately, machines cannot lie to one another, but the humans that operate the machines do lie (or make mistakes) and can force the machines to do the same. In the previous example, we saw how a simple lie about the distance between two routers could change the direction of traffic flow within the network, but why is this of concern? Even with this manipulation, if Router D wanted to send packets to Router A won’t the information be delivered just as before? No. Now that Router C is in the middle of Router D and Router A, it can: 1. Observe the traffic moving between these devices. 2. Change the information moving between these devices. 3. Stop the traffic from moving between these devices. Hi, remember me? I’m Ciana. Why is this an issue? Recall from SI110, there are five pillars of information assurance we want to preserve when offering services through routers and other information systems.1 1. Confidentiality – protection of information from disclosure to unauthorized individuals, systems, or entities. 2. Integrity – protection of information, systems, and services from unauthorized modification or destruction. 3. Availability – timely, reliable access to data and information services by authorized users. 4. Non-repudiation – the ability to correlate, with high certainty, a recorded action with its originating individual or entity. 5. Authentication – the ability to verify the identity of an individual or entity. Grr…Don’t remember me, huh? You’d better for the test! Example 2 What primary pillar of information assurance is violated in each thing Router C can do once it is in the middle of Router D and Router A? (a) The ability to observe traffic violates: (b) The ability to change traffic violates: (c) The ability to stop traffic violates: 2. The Man-In-The-Middle (MITM) Attack 1 See http://www.usna.edu/CS/si110/lec/l00/lec.html to review these topics and definitions. 3 This type of problem is called the Man-In-The-Middle attack. We have seen this once already during Practical Exercise 27 in Lesson 27. Specifically, the technique used to conduct the MITM attack in Practical Exercise 27 was called ARP-Spoofing because to redirect another computer’s traffic on a single network required your computer to tell a specific lie about the association between its MAC address and IP address Much like a nasty rumor in the Brigade, that lie had to spread around for it to be effective. Similarly, you included your own MAC address with the target’s IP address through multiple unsolicited ARP-Replies to convince everyone on your local network that your machine was the target host. Finally, everyone on your local network had to believe your lie for you to begin receiving packets destined for the target machine. Do you think it is possible for something like this to happen on a bigger scale? That is, instead of a Man-InThe-Middle attack on one network as with ARP-spoofing, can this happen between multiple networks? Yes it could happen, and things similar to this have already happened, but to understand how requires a bit more understanding of the how networks interconnect. However, just as before with ARP-Spoofing, there are four critical steps that must occur for an attacker to make this possible. 1. Take control of a machine on the network and manipulate its operation. 2. Force the machine to tell the “right” kind of lie. 3. Force the machine to spread the lie around. 4. Force other machines to believe the lie. 3. Wait a Minute… “Boring! Okay, so I may not remember much from SI110, but the one thing I do remember is that encryption solves all of our problems. If someone is snooping around and reading my packets, then I will just encrypt them and ruin their ability to influence my communication. Done, may I go now?” 4 As Mr. Eric Snowden recently revealed, that is exactly what the National Security Agency (NSA) and others would want you to think.2 While it is true that encryption may make eavesdropping harder for the man in the middle, it is not insurmountable. In reality, as the New York Times explains, some of the core encryption protocols of the Internet are already broken. For those that are not, the NSA allegedly spends upwards of $250 million a year on US and foreign industries to covertly influence commercial product designs to make them exploitable. To leverage this advantage, the NSA pays a significant amount of money to become the man in the middle so they can read any Internet traffic, encrypted or not. One example from WIRED magazine talks about a $652 million NSA project to help take control of routers and networks to monitor foreign communications.3 Hopefully, it is clear that understanding how a MITM attack can take place across multiple networks is very important to Cyber Warfare as a whole. Yes, sir! Please give me more details so that I can understand this critically important material. II. A Closer Look at How Networks Interconnect 1. An Important Example Let’s say there is an important website that all midshipmen need to access to in order to prepare for EC312 each day. That website is located at IP address 4.4.5.155 on the network 4.4.5.0/24. The midshipmen who need access to it are located on network 192.168.65.0/24, and have one of the 253 available host IP addresses assigned to their laptops. See “SSL has Fallen” for more details (http://www.nytimes.com/2013/09/06/us/nsa-foils-much-internetencryption.html?pagewanted=1&_r=2&). 3 See “NSA Hacks Routers, not User PCs” for more details (http://www.wired.com/threatlevel/2013/09/nsa-router-hacking/) 2 5 Example 3 Construct the routing table for Router A using address aggregation where appropriate. Now, let’s pretend there is an evil instructor (because aren’t all instructors evil?) located on the 5.5.5.0/25 network that wants to prevent students from reaching the EC312 website at 4.4.5.155. What would that instructor need to do in order to make the student’s traffic go to some place they did not intend? 6 a) First, the instructor will need to: take control of a machine on the network and manipulate its operation. Being an instructor, ITSD has graciously allowed him (or her) privileged access to his office computer for ‘academic research’, but nowhere else. ITSD has restricted the instructor’s privileged access in order to prevent him from making any changes that could affect other computers on the network. Therefore, the instructor will need to manipulate his computer in such a way where it can alter the flow of traffic across the networks and deny midshipmen access to the course website. To accomplish this, he decides to turn his computer into a router using a special software tool called Loki.4 This tool ‘speaks’ the Open Shortest Path First (OSPF) protocol, which will enable the injection of false routing information into the networks. 4 Loki is a Python based framework implementing many packet generation and attack modules for Layer 3 protocols. It was developed by ERNW, an IT security service provider, in 2010. See https://www.ernw.de/research/loki.html for more details. 7 b) Second, the instructor will need to: force his router to tell the “right” kind of lie. But what is the “right” kind of lie to tell? Well, that depends on the effect the instructor wants to have on the networks. For example, if the instructor wanted to cause a panic across the entire Brigade, he or she might say that “buffalo chicken sandwiches will no longer be offered in King Hall.” However, if he only wanted to terrorize the students in his EC312 section, the instructor could say “you will have a quiz tomorrow over Lessons 1 through 15 worth 99.2003% of your final grade.” The instructor’s goal is to stop the students’ traffic from reaching the EC312 web server located at 4.4.5.155. To do this the instructor would like to direct the students’ traffic to a different location where their web requests will go unanswered. Knowing that routers transmit information to the destination that matches the longest network prefix in their routing table, the instructor decides to create a false network from his router with a more specific network ID that will direct the student’s traffic away. Example 4 What is the first and last IP address of the 4.4.5.0/24 network where the webserver is located? (a) First Address: (b) Last Address: Looking at Router A’s table, what network ID and mask should the evil instructor choose? Other options? What is the first and last address of the false network the evil instructor will advertise? (a) First Address: (b) Last Address: Does the IP address of the webserver fall within the IP address block that the evil instructor will advertise? c) Third, the instructor will need to: force his router to spread the lie around. Recall from Lesson 28, under the Internet’s Open Shortest Path First (OSPF) protocol, routers communicate with one another using Link State Packets (LSP). These packets are distributed to all routers through “controlled flooding” to allow each router to build a full and complete picture of the topology of the entire network. However, before routers swap LSP with each other, they must become neighbors first and agree on a basic set of operating parameters. Therefore, in order for the evil instructor to spread his lie about the fake 8 network he must become neighbors first with a router on his network. Then he can send his malicious LSP advertising the false network he is connected to. d) Fourth, the instructor will need to: force the other routers to believe the lie. Fortunately in OSPF this is relatively easy because controlled flooding is already built into the protocol. As previously mentioned, LSP are forwarded to all routers through controlled flooding to ensure all routers have a complete picture of the network’s topology. Thus, once Router B learns about the new false network from the evil instructor, Router B will turn around and tell Routers A and C. Example 5 What will Router A’s routing table look like, once it hears the lie about the fake network from Router B? 9 Thus, whenever a student sends a packet destined for the webserver at 4.4.5.155, where will Router A forward their packet? Will the EC312 students ever be able to reach the course web page? Do you think it is possible that something like this could ever happen on the Internet? Unlike the previous example, the Internet consists of hundreds of thousands of networks stretched across the entire globe. Could it be possible for someone to change the way traffic flows across such a big and complex distributed system? Yes it could happen, and similar things like this have already happened, but to understand how requires a bit more understanding of the Internet. 2. Protection Against False Route Injection How can we stop such malicious behavior? Recall that by default routers trust the information other routers are sending, but this does not have to be the case. The Open Shortest Path First protocol has two authentication mechanism built in to protect against false route injection. The first is a simple plaintext-password added to all LSPs so each router can authenticate the information it is receiving. If a router sends a LSP without the appropriate password, then the LSP is rejected. The second method is an MD5-hash of the OSPF packet and a shared secret key. Recall from SI110, that hashing is a ‘one-way’ encryption technique that produces the same message digest (i.e., encrypted output) given the same input string. Additionally, while it is easy to hash the input string, it is very hard to identify the input string given only the message digest (remember the Rubik’s cube?). In OSPF, routers can send the hash of the OSPF packet and a shared secret key along with their LSP to authenticate themselves with other routers. Of course, all routers must know the shared secret key in advance. This may seem trivial at first, but consider the number of routers at a place like Google or Amazon Web Services where there are literally thousands of routers. Lastly, separate from these two authentication mechanisms, most implementations of OSPF allow for creation of passive interfaces. Just like when your roommate starts getting on your nerves and you tune him or her out by putting your headphones on, routers can do the same thing. Once a network administrator sets up a passive interface on a router, the router will ignore all routing information being sent over that interface. However, this requires network administrators to make smart decisions when setting up the topology of their networks and configuring their routers. Example 6 Briefly describe two technical solutions to protect against false route injection and identify who is responsible for implementing them. Solution #1: Solution #2: OPTIONAL: Interestingly, of the three actions an attacker can take during a MITM attack, what do you think an attacker would most likely want to do? Observe, change, or stop your traffic? It seems frightening to have our traffic 10 stopped by someone else or changed as it is moving to its destination, but recent cyber activity has indicated it is more likely an attacker would want to observe your traffic in the end. Consider the following excerpt from Kevin Mandiant’s report on Advanced Persistent Threat 1 (APT1), a Chinese cyber warfare unit: Our evidence indicates that APT1 has been stealing hundreds of terabytes of data from at least 141 organizations across a diverse set of industries beginning as early as 2006. Remarkably, we have witnessed APT1 target dozens of organizations simultaneously. Once the group establishes access to a victim’s network, they continue to access it periodically over several months or years to steal large volumes of valuable intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, emails and contact lists from victim organizations’ leadership. We believe that the extensive activity we have directly observed represents only a small fraction of the cyber espionage that APT1 has committed. Once APT1 has compromised a network, they repeatedly monitor and steal proprietary data and communications from the victim for months or even years. For [141] organizations... we found that APT1 maintained access to the victim’s network for an average of 356 days. The longest time period APT1 maintained access to a victim’s network was at least 1,764 days, or four years and ten months. APT1 was not continuously active on a daily basis during this time period; however, in the vast majority of cases we observed, APT1 continued to commit data theft as long as they had access to the network.5 Notice the chosen behavior of this Chinese cyber warfare unit. Rather than shut down the networks of the various companies they invaded or change the information located there, they simply observed the traffic and stole copies for themselves. It would seem their primary desire was not to do damage but to gain information. Maj. Agur Adams, USMC Help us improve these notes! Send comments, corrections and clarifications to aadams@usna.edu 5 See http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf for the full report on APT1 originally published in 2013. 11