Lesson 10 Exam Review Performance Tasks Computer Concepts
advertisement
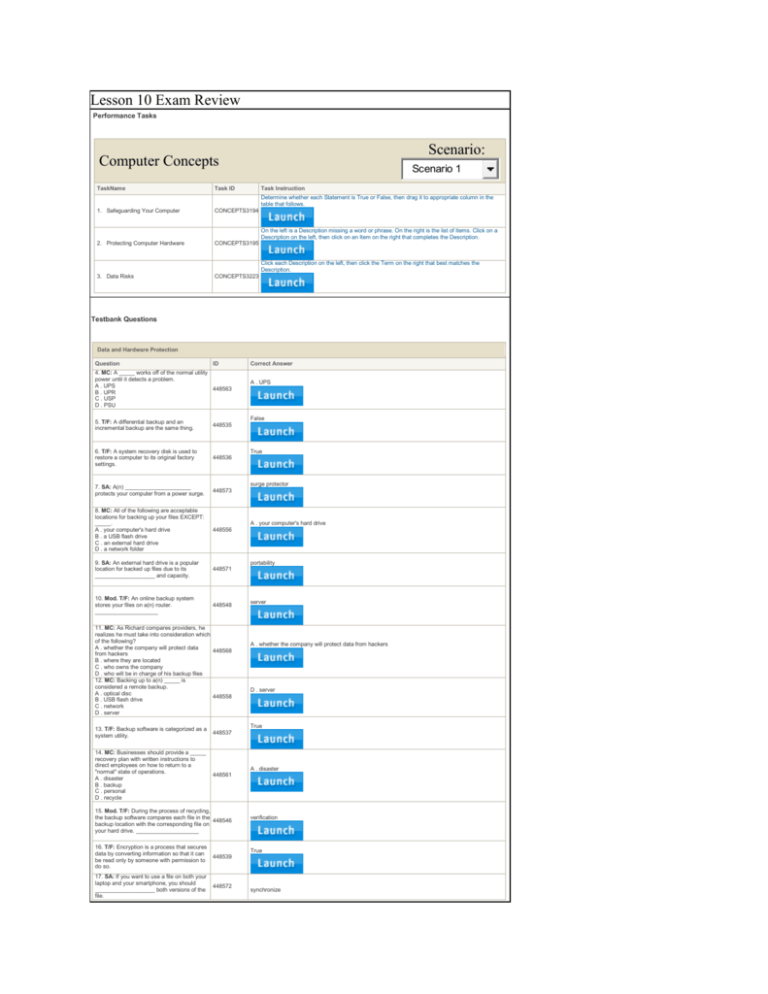
Lesson 10 Exam Review Performance Tasks Scenario: Computer Concepts Scenario 1 TaskName Task ID Task Instruction 1. Safeguarding Your Computer CONCEPTS3194 2. Protecting Computer Hardware CONCEPTS3195 3. Data Risks CONCEPTS3223 Determine whether each Statement is True or False, then drag it to appropriate column in the table that follows. On the left is a Description missing a word or phrase. On the right is the list of Items. Click on a Description on the left, then click on an Item on the right that completes the Description. Click each Description on the left, then click the Term on the right that best matches the Description. Testbank Questions Data and Hardware Protection Question ID 4. MC: A _____ works off of the normal utility power until it detects a problem. A . UPS 448563 B . UPR C . USP D . PSU Correct Answer A . UPS False 5. T/F: A differential backup and an incremental backup are the same thing. 448535 6. T/F: A system recovery disk is used to restore a computer to its original factory settings. 448536 7. SA: A(n) _____________________ protects your computer from a power surge. 448573 8. MC: All of the following are acceptable locations for backing up your files EXCEPT: _____. A . your computer's hard drive B . a USB flash drive C . an external hard drive D . a network folder 448556 9. SA: An external hard drive is a popular location for backed up files due to its ___________________ and capacity. 448571 10. Mod. T/F: An online backup system stores your files on a(n) router. ____________________ 448548 True surge protector A . your computer's hard drive portability 11. MC: As Richard compares providers, he realizes he must take into consideration which of the following? A . whether the company will protect data 448568 from hackers B . where they are located C . who owns the company D . who will be in charge of his backup files 12. MC: Backing up to a(n) _____ is considered a remote backup. A . optical disc 448558 B . USB flash drive C . network D . server server A . whether the company will protect data from hackers D . server True 13. T/F: Backup software is categorized as a system utility. 448537 14. MC: Businesses should provide a _____ recovery plan with written instructions to direct employees on how to return to a "normal" state of operations. A . disaster B . backup C . personal D . recycle 448561 A . disaster 15. Mod. T/F: During the process of recycling, the backup software compares each file in the 448546 backup location with the corresponding file on your hard drive. ____________________ 16. T/F: Encryption is a process that secures data by converting information so that it can be read only by someone with permission to do so. 448539 17. SA: If you want to use a file on both your laptop and your smartphone, you should ___________________ both versions of the file. 448572 verification True synchronize 18. MC: In a(n) _____ backup, copies of the files that have changed since the last full system backup are recorded. A . selective B . differential C . status D . incremental 19. MC: In a(n) _____ backup, copies of the files that have changed since the last full system backup or the last incremental backup are recorded. A . selective B . differential C . status D . incremental 20. MC: In a(n) _____ backup, only the files you choose are backed up. A . selective B . differential C . status D . incremental 21. MC: In some cases, when a backup file becomes too large, you can select the _____ feature to use more than one drive to store the file. A . encryption B . verification C . media spanning D . overflow B . differential 448550 D . incremental 448551 A . selective 448552 C . media spanning 448555 22. Mod. T/F: In the Exclude Folders window, you can select files you do not want included 448547 in the backup process. ____________________ 23. MC: In Windows, _____ can be used to restore any version of a file that File History has saved. A . Access 448557 B . Preferences C . File Explorer D . Control Panel 24. MC: Mac OS X computers provide backup software called _____ to make incremental backups of files that have changed. A . Reports 448554 B . Time Machine C . Pages D . Encryption 25. Mod. T/F: Mobile devices that support iOS can be backed up to iTunes. ____________________ 448545 26. T/F: Most online backup services are free. 448540 C . File Explorer B . Time Machine True False 27. SA: Once backup software is installed, 448570 the next step is to _____________________. 28. MC: Once Nate chooses a backup method, he then needs to ______. A . decide who can access the data B . decide how many folders he needs to create C . choose a password D . choose a location for the backup 448565 29. T/F: Once you make a backup copy of a file, it cannot be reused. 448534 30. T/F: One advantage to using an optical disc as a backup medium is its access and storage speed. 448538 set a schedule D . choose a location for the backup False False 31. MC: One of the first things Nate needs to decide before backing up his data is ______. A . the type of backup to create B . how much time the backup will take 448566 C . how much space is available on his hard drive D . what he should name his backup file A . the type of backup to create True 32. T/F: Redundancy means that you have more than one copy of a backup. 448542 33. MC: Richard knows that the online backup service he selects must have _____ so the data can be recovered at any time. A . mobility B . validation C . shareware D . imaging 448567 34. T/F: Synchronizing your files is the same thing as backing up your files. 448541 B . validation False 35. SA: The system ____________________ disk restores the computer to its factory 448569 settings. 36. Mod. T/F: To back up only files that have changed since the last full system backup, 448544 choose the selective backup option. ____________________ 37. MC: Using a _____, you can reinstall all the files needed to restart your computer when there is a problem. A . security recovery disk B . system image True recovery incrementaldifferential D . system repair disk 448553 C . system recovery disk D . system repair disk 38. MC: When deciding to back up your files, you should consider all of the following EXCEPT: ______. A . what to name the folder storing your files 448549 B . which backup method to use C . the type of backup to create D . where to store the files 39. T/F: When tracking software is installed on your computer, you have a better chance of locating it if it is stolen. 40. MC: When tracking software is installed on your phone, it can do all of the following EXCEPT: ______. A . Play an urgent sound to help you locate it. B . Lock the device and erase your data. C . Beep and display a phone number. D . Call you automatically. 41. MC: Which of the following backup services provides a certain amount of space on a secure server where you can keep files, but backups are not automatic? A . optical B . online C . cloud D . flash 42. MC: Which of the following factors does NOT affect the safekeeping of your hardware? A . temperature B . lighting C . humidity D . liquids 43. MC: Which of the following is NOT true about online backup services? A . No username or password is needed to access your data. B . They usually require a subscription fee. C . You can schedule the type of backup you want to perform. D . Backed up data is usually encrypted. A . what to name the folder storing your files True 448543 D . Call you automatically. 448564 C . cloud 448560 B . lighting 448562 448559