The integrity self-assessment method - China

China-Europe Public Administration Project II (CEPA II)
中国 – 欧盟公共管理二期项目
Asie/2009/221-725
Technical Assistance of China-Europe
Public Administration Project II
Structured mechanism on “integrity management”
(guideline) for a public service organization
(AWP 2013, TA 3.3
)
Mr. John HECK
Draft 15 May 2013
Financing Agreement N o
DCI-ASIE/2008/019646
Service Contract N o
DCI-ASIE/2009/221-725
1
Table of contents
2
3
Structured mechanism on “integrity management”
(guideline) for a public service organization
A manual to a preventive self-assessment of vulnerabilities within public organizations
4
About the manual
Summary
From the point of view of integrity all (public) organizations are vulnerable. This manual offers a method to enhance the resistance capability of an organization against integrity violations. It is first of all a preventive instrument which enables the mapping of the most vulnerable activities, processes and positions in the organization.
The Manual is based on ethics management good practices in the European Union and has been used in public administrations in many EU member states. Its applicability was reviewed for usability in
China in 2013 within the framework of the China-Europe Public Administration Project (CEPA II).
The Manual pays attention to the identification and assessment of vulnerable activities related to the performance of a job and organization-wide vulnerabilities which supersede job related vulnerabilities. But before the actual kick-off of the identification and assessment, the Manual addresses the preparatory measures which need to be taken. It is designed in such a way that the user can perform the integrity research independently. This practical instruments, background information and examples are added.
This Manual is composed of three parts. Part I explains why public organizations need to pay attention to integrity seriously. This Part is of a more general nature, primarily intended for the (top) management. The focus is on the concept of integrity and the resistance capability against integrity violations. Starting point is that an integrity violation will always harm the reputation of the organization, as integrity has everything to do with confidence and reliability. Therefore, the prevention of integrity violations by an organization or an individual is of utmost importance.
Part II is intended for the implementation of the integrity assessment. The implementation takes place in a three-step procedure. This Part refers many times to Part III which contains the background information, checklists and examples.
Starting points
This Manual leads step by step through an integrity self-assessment which identifies the potential vulnerabilities in the organization. The assessment is based on the following essential starting points.
Firstly, it concerns a preventive assessment or diagnosis. It is not aimed at the detection, accusation
of possible not integer persons in the organization. The focus is to optimize the resistance capability
(existing regulations, measures, procedures) of the organization against integrity violations. This will prevent integrity breaches .
Secondly, it is a self-assessment, implemented by the organization itself, using knowledge and experience of its own employees. This all based on the experience that they are in the best position to assess possible vulnerabilities, risks and quality of measures in their own Department.
5
Thirdly, the assessment is aimed at possible improvements in the organizational structure. This concerns rules, procedures and systems.
The method in brief
The assessment method takes place in three consecutive phases. In each phase reference is made to practical hints, checklists and examples of which are listed in Part III of this Manual.
The first phase contains preparatory activities or the activities needed before the actual start of the assessment. This concerns issues as the composition of the project group for the implementation of the assessment, the information to the organization to be assessed. Then follow three phases that constitute the core of the assessment.
In Phase A the vulnerabilities are mapped. There is a first look at the vulnerable job related activities, e.g. activities related to money or sensitive information. The organizational vulnerabilities concern activities related to e.g. the recruitment of (unreliable) staff or the performance of a secondary job
(not in line with your work as an official). The (top) management identifies the (potential) vulnerabilities by itself.
To assess whether the vulnerabilities mapped in Phase A are really factual vulnerabilities, Phase B maps the existing resistance capabilities against possible integrity violations by indicating which rules, regulations, instructions are already available and whether there is a need for improvements.
This is done by interviews with employees holding vulnerable positions.
Based on the results of Phase B, recommendations are drafted (Phase C).
However, more is necessary. Depending on the kind of organization the integrity policy should be supplemented and perfected. To this end Part III offers some suggestions, such as a Format for the drafting of an integrity policy or examples on the purpose of a Code of Conduct.
6
Schedule methodology integrity self-assessment
Phase A
Identification of vulnerable activities
Introductory meeting integrity project group
Pre-meeting project group with (top) management
(Top) management gives overview vulnerable activities + organizational vulnerabilities
Project group interviews members
(top) management
Approved report of
Stage A
Phase B
Assessment of existing resistance capability
-Project group examines existing protection of vulnerabilities:
-Presence of regulations, policy matters;
-Quality of these regulations;
-Awareness, application of regulations
Establishing factual risks
Approved report
Stage B
Stage C
Recommendations to (top) management
Project group makes recommendations to
(top)management on factual integrity risks
-Incorporation of results in approved implementation plan;
-Arrangements to ensure continuous awareness;
-Follow-up
Final meeting for all relevant parties and approved final report
7
Part 1: Integrity
Integrity and integrity policy
It is of utmost importance that those responsible for the organization and functioning of the public service realize that integrity and ethics management are increasingly becoming a standard by which both personal performance and the performance of the organization as a whole are judged.
Confidence in the civil service is directly related to its integrity. An organization may easily be discredited once its integrity has been violated. In general, the ensuing damage to its reputation is substantial, while the effort to win back betrayed confidence are in no proportion to the preventive efforts to reduce the risk of a loss of integrity. This has also everything to do with the credibility of the civil servants/public officials.
Unfortunately, however, a preventive integrity policy cannot completely secure an organization against integrity violations. It can reduce the risk, however. A visible preventive policy may also influence the judgment of an integrity incident by outsiders. After all, a violation will be judged differently when the management of the organization has demonstrably tried to reduce the risk of such incidents. The responsible management should be able to show the existence of ethics/integrity relevant rules, procedures and mechanisms for supervision and control. This Manual may help in this respect.
The term “integrity” originates from Latin; its literal meaning is ‘not touch’ (in tangere). So it refers to something that or someone who “has not been touched” in the sense of being unaffected, untarnished, unblemished or intact.
Organization and the individual
A complete and effective integrity policy is focused on both the structure and culture of an
organization and on the integrity of the individual employees. It should cover both to the compliance with rules and the stimulation of responsibility and awareness.
It is necessary, on the one hand, to develop and observe clear rules, guidelines and codes within an organization in in order to arm the organization against integrity violations. In the personal sphere the selection of personnel and sanctioning play an important role. Both interrelated aspects are relevant to the compliance-related side of the integrity policy. On the other hand, it is impossible to cover every type of appropriate behavior by rules, guidelines and codes. After all, new or very complex situations that have not (yet) been covered by rules always crop up. In these situations the employees should have the proper moral competences on the basis of which they can independently
– but in line with the organization – take well considered and sensible decisions.
Moral competence is a quality that can be enhanced and stimulated by means of, for example, dilemma or moral judgment training. The provision of information about integrity questions also increases awareness. An open-minded culture in which people feel no inhibitions to make mistakes
and to discuss (private) problems is also very important.
8
Finally it is recommended in this Manual to appoint an integrity coordinator or integrity Confidential
Counselor who co-ordinates the various activities and who can tell the employees how and where to report suspected integrity violations, if this may happen (see Part III, section 4.3).
Aspects of integrity policy
Organisation oriented integrity
Person oriented integrity
Compliance
Morally defensible organisational structure
Selection/recruitment of personnel and personnel policy
Stimulation
Sense of responsibility
Moral competence
The particular importance of integrity to public service
Integrity is not only a major requirement in the public service; it is also a valued quality in the private sector and in social interactions between citizens. But where the public sector is concerned, integrity has an extra dimension.
The fact is that citizens are largely dependent on government actions. Government institutions have many specific powers that may directly influence the life of citizens. And in that capacity the civil service often has a monopoly position. Government organizations issue licenses, collect taxes, grant allowances, supervise the compliance with regulations, impose punishments if necessary, etc. These actions are meant to ensure safety, to facilitate life for the citizens and to protect them against inappropriate actions by others.
For this reason high demands are made to the quality of public administration and the quality of those who are working under its responsibility. Corruption and other forms of unethical behaviour in public sector also have a negative effect on the spontaneous preparedness of citizens to comply with obligatory and prohibitory provisions. In that sense the integrity of the public service is a precondition for the acceptance of government authority and for the compliance with laws and regulations.
It is because of this influence, the monopoly position and the fact that government actions are financed by tax money that the public service has to meet special requirements. Integrity is an essential part of these requirements.
Why does integrity demands more attention?
Over the past few decades much has changed within the public sector and within society as a whole.
Various developments have led to new procedures within the civil service and have changed the relations between the political domain, the civil service and society. These developments have added
9
to the increasing importance of integrity within public administrations all over the world. They can be sketched as follows:
The civil service is acting increasingly like a normal “market party”, doing “business” with the private sector. On the market (private sector), however, other standards and values apply than within the public sector. Civil servants who are acting on or close to the market may be exposed to the temptations of the world of copious business dinners, study trips to far-off countries and other services that are required in return;
Over the past few years, a large number of government organizations have been more or less disconnected from the public service to be (partly) privatized. This has caused a fragmentation of the central values and standards of the civil service, which have become subject to the individual preferences of managers. In addition, a business oriented government organization has an enterprise character, which sometimes implies that certain risks (with tax money) are taken;
The media have become much more critical of the performance of the civil service. This means that they follow the behaviour of civil servants and their managers much more closely than before;
Globalization has prompted national government services to operate increasingly within complex and not very transparent international co-operation groups.
Those developments make it difficult to maintain the integrity of public administrations. One or few of these developments do not necessarily lead to violations of the integrity of the public sector.
Nevertheless, a climate seems to have arisen in which the public sector has to meet more and more wide-ranging and sometimes contradictory values and standards. This has made the civil service more vulnerable to integrity-related risks.
10
Part II: The integrity self-assessment method
Summary
Part I has addressed various aspects of the concept of integrity. In addition, this Part is also meant for those who have to decide upon starting the integrity self-assessment in the organization, to inform about its contents and starting points.
Part II is meant for those who play an important role of the implementation of the self-assessment.
In this part of the manual the focus is on the methodology of the assessment. This methodology consists of three consecutive phases that an organization must go through step by step. Before these stages in detail, it is first paid attention to some important activities carried out in the preparation of the actual self-assessment.
The method presented here is constructed in such a way that the members of the project group are supported with practical material at each stage in the implementation of the integrity assessment. In
Part III are sample material, background information and practical advices included.
Preparatory activities
Prior to the description of the actual assessment, Part II pays attention to the start and the management of the integrity self-assessment. Some issues should be put on the right track, whether there is adequate framework to promote the success of the assessment. Think of the availability of sufficient number of staff and (financial) resources, the acquisition of support and commitment to the project within the organization.
Phase A
Per Department two kinds of vulnerabilities are mapped. Firstly, it is observed whether vulnerable activities (VA) are being implemented. This concerns job related activities related to e.g. money or sensitive information. Secondly, the focus is on the (aspects of) organizational vulnerabilities. This concerns certain situations, processes potentially prone to integrity violations. Think of recruitment of (unreliable) employees, or the performance of (unwanted) secondary jobs by employees.
At the identification of both types of vulnerabilities, consultation takes place with the (top) management. The results of the assessment in Phase A give an overview on the vulnerable activities
(VA) and the organizational activities (OA). Together they form the potential risks to which the organization is exposed.
11
Phase B
To assess whether the potential risks are really factual risks, in Phase B the existing resistance capability (rules, instructions, etc.) against integrity violations is mapped. The focus then is then on the adequacy of (qualitatively) good rules, instructions, procedures to deal with the vulnerable
activities. In addition, it is also assessed whether the employees are really able to apply these rules.
By comparing the observed vulnerability with the resistance found, Phase B can provide an overview on the factual integrity risks within the organization.
Phase C
In this Phase, and based on the results of the previous phases, it is assessed whether if and how the resistance against integrity violations can be optimized. Recommendations are made to minimize the factual risks and how to embed follow-up activities in the organization.
12
1 Preparatory activities
Introduction
With the help of the Manual the public organization can enhance the resistance capability against integrity violations. This will bring about an important improvement of the quality of the organization. Preceded by the actual integrity self-assessment, it is necessary to pay a number of preparatory activities.
In this Manual we work with red and green instruments. These refer to the place where you can find this instrument in part III. The use of the red instruments is necessary. The green instruments can be construed as recommendations.
Role (top) management
What should the (top) management do in this preparatory phase?
Take a decision on the start of the project (integrity self-assessment);
Inform other stakeholders about the project (other Directors, etc.);
Ask enough people and resources available during the implementation phases A and B;
Nominate a project supervisor
Project group
After the decision to start the integrity self-assessment, the (top) management has to nominate a project supervisor . He/she will be charged by the task to establish a project group, to draft a plan of activities, to be submitted to the (top) management for approval.
The project supervisor is responsible for the establishment, process, time planning and daily implementation of the self-assessment and for the composition of the project group.
In consultation with the (top) management the project supervisor selects the members of the project group .
These come from the organization itself and should have sufficient knowledge and insight into the functioning of the organization. It is recommended that representatives from different parts of the organization and with different functions take a seat in the project group.
Communication
It is useful to organize a kick-off meeting for all staff involved in the integrity self-assessment.
For the kick-off meeting Part III of the Manual provides an example presentation by the management and a presentation by the project supervisor .
The participants to the kick-off meeting need the following information:
13
Decision by the (top) management on the start of the project;
The importance of integrity for the organization;
Objectives, process and content of the project;
Something about one intends to do with the results
A clear “statement” that the project is not motivated by mistrust of the employees.
In addition to the kick-off meeting, depending of the size of the organization, stakeholders can be informed by a letter or an article in a staff magazine. Part III of the Manual shows an example letter to the employees or article in the staff magazine .
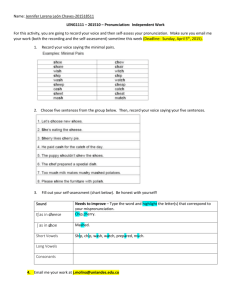
Part III provides also a List of Concepts to be used in the Manual. To check whether all steps have been taken, Part III contains a Checklist preparatory activities.
2 The methodology
Schedule Phase A
Mapping the vulnerabilities (indicated by managers)
PROJECT GROUP
Kick-off meeting for all participants
Pre-meeting with (top) management
Explanation content vulnerable activities (VA) and organizational activities (OV)
Submission overviews (+ Manual).
(Top)management and support
To map/identify the VA;
To map/identify the OV, according to the overviews (in Part III, 2.1, 2.2).
Project group
Processes results
14
REPORT PHASE A
Discussion report with (top) management/commissioning authority
Approval (or after amendments)
Dissemination report to parties concerned
Start PHASE B
2.1 Phase A. Mapping the vulnerabilities indicated by (top) management
General
Within any organization certain activities are to designate that are potentially vulnerable to integrity violations. In Phase A of the integrity self-assessment these vulnerabilities are mapped. There are two types of vulnerabilities:
Vulnerable activities (VA)
First of all, this concerns vulnerabilities related to a job or position which can create a possible integrity risk for the organization. Think of working with sensitive information, money, and the management of goods of the organization.
The kind of vulnerable activities in this Manual relate to the most common activities. Nevertheless, there could also other vulnerable activities in the organization. The organization itself can fill out the list at its own discretion.
Organizational vulnerabilities (OV)
These vulnerabilities supersede the individual, job related vulnerabilities. These concern the organization-wide aspects of vulnerability. This Manual (Part III, section 2.2) distinguishes ten organizational vulnerabilities.
To map the vulnerabilities the project group could have interviews with all employees, but that is not feasible and is too time consuming. To assess who to interview an organogram can be useful.
In Phase A it is important the (top) management indicates the vulnerable activities, by using the overview in Part III (2.1 and 2.2) and raising at least the following questions to the management;
Which vulnerable activities are being implemented?
15
Which functions, jobs are involved?
Which vulnerable activities can cause the largest consequential damage for the organization?
Think of: o Financial loss; o Abuse of resources o Reputational damage o Negative influence on working climate o Disadvantage citizens o Legal status-consequences for employees o Political implications
Which aspects of organizational vulnerabilities are considered very important related to integrity?
Phase A in four steps
The collection of information in Phase A should take place in the following four steps:
Conduct of pre-meeting with (top) management;
Mapping the vulnerabilities;
Conduct of interviews with (top) management
Presentation of results in a report
The report should give insight in:
Which vulnerable activities are implemented within the Department of the interviewed manager;
Which job/positions are involved;
Which job related vulnerabilities can cause large(st) consequential damage;
Which organizational vulnerabilities are considered most important.
16
Schedule Phase B
Mapping the existing resistance (indicated by employees)
PROJECT GROUP
Identifying/assessing the existing resistance capability (= official rules, procedures, instructions and other measures which contribute to the integer functioning of the organization)
1.
Do rules, regulations, procedures, etc. exist for dealing with vulnerable activities?
2.
Do the existing rules, regulations, procedures, etc. cover the vulnerable activities sufficiently?
3.
Do employees know the existing rules, regulations, procedures, etc. and are these applied?
4.
Have measures and policies formulated on the organizational vulnerabilities?
5.
Do these cover the organizational vulnerabilities sufficiently?
6.
Do employees the formulated policies and measures taken and do they act accordingly?
Project group processes the results
1 and 4: project group
2 and 5: administrative department
3 and 6: interviews with employees
REPORT PHASE B
Discussion report with commissioning authority
Approval (or after amendments)
Dissemination report to managers concerned
Start Phase C
17
2.2 Phase B. Mapping and assessing the existing resistance
General
The report of Phase A gives insight into the vulnerable activities in the different parts of the organization. Phase A only maps the potential vulnerabilities, as indicated by the (top) management.
To map the factual risks (integrity risks) the existing resistance of the organization against integrity violations will be identified.
What is resistance?
Resistance is defined as the total of (official) rules, procedures, working-instructions, provisions and policy which contribute to the integer functioning of the organization.
Assessment resistance capability by the project group
The assessment of the resistance capability related to the vulnerabilities mapped in Phase A, is a task of the project group. The project group assesses the provisions, measures, policy and interviews the employees about knowledge and application of the rules, working-instructions, and procedures.
Assessment criteria
To assess the resistance it will be reviewed whether:
A: the vulnerabilities are covered by measures, rules, provisions;
B: the quality of these is sufficient;
C: the employees actually are familiar with these and whether these are applied.
Any lack of provisions, rules is considered a risk aggravating factor.
Part III, section 3.2., provides a Checklist resistance integrity measures and policy Phase B
Regarding the qualitative assessment of the resistance, the following criteria can apply:
Up to date (from which date they are applied, frequent update?)
Understandable (easy to read, understand?)
Clear (not ambiguous?);
Enforceability (they comply and enforceable?);
Practicability (actually to be performed?)
Completeness (is the scope sufficient and detailed enough?)
Consistency (are they contradictory?)
Interviews employees
The project group makes itself a choice of the entire workforce. It is very important to interview experienced and new employees.
Part III, section 3.1, provides the Questionnaire employees Phase B .
18
Analysis and reporting Phase B
The report of Phase B should at least contain the following aspects:
1.
Have rules, provisions been formulated for all vulnerable activities?
2.
Is the quality of these sufficient?
3.
Do the employees know the provisions?
4.
Have rules, provisions been formulated for the organizational vulnerabilities?
5.
Is the quality of these sufficient?
6.
The employees know the purpose of the measures, policy?
The actual assessment of the resistance is up to the organization itself.
Schedule Phase C
Recommendations to (top) management
Project group
Recommendations to (top) management
1 Arising from the results of the self-assessment
Securing identified integrity leaks.
Improving the quality of provisions, measures, policy.
Improving the awareness and application of the measures, regulations, etc.
2 To organize permanent attention to integrity issues
Ensuring the implementation of the recommendations
Nominate a employee in charge of dealing with integrity issues (see Part III, section 4.3
Confidential Counselor)
3 To update the integrity policy (see Part III, section 4.1 Format Integrity policy)
Drafting planning for regular integrity self-assessment.
Project group processes the results
Record recommendations in a report
Report Phase C
Discussion report with commissioning authority
19
Approval (or after amendments)
Concluding meeting
2.3 Phase C. Recommendations to (top) management
Recommendations
It is not possible to predict which specific integrity risks will occur in a particular organization.
Recommendations can be related to;
1.
The lack of provisions, measures, regulations. It is advisable to use the Checklist resistance capability integrity measures and integrity policy , Part III, section 3.2.
2.
Insufficient quality of the measures, regulations. See phase B above, the qualitative assessment criteria.
3.
Employees not familiar with the measures, regulations, procedures. Recommendations on this can be linked to training on integrity (see Part III, section 4.4).
To organize permanent attention to integrity issues.
1.
Direct implementation of report Phase 3 by the (top) management
2.
Integrity self-assessment part of integrity policy planning (see part III, annex Format integrity plan)
20
Part III: Background information, examples, annexes
Summary
Part III of this Manual provides a tool kit for the implementation of an integrity self-assessment. It contains various instruments, such as checklists and questionnaires, background information and examples. This material has been developed on the basis of experience with an integrity self- assessment implemented in a Chinese organization.
The instruments support the implementation of the self-assessment. As this Manual has a general lay-out (after all, the Manual should be applicable to all kinds of public organizations), each organization may adjust the instruments tailored to its own specific situation. This is of great importance. The project group needs to consider whether all vulnerabilities have been taken into account exhaustively, or that specific areas in the organization should be added.
The presentation of the various instruments follows the sequence of Part 1 and II of this Manual. In the text there is a reference to red and green instruments.
The use of the red instruments is essential for the implementation of the integrity self-assessment.
The use of the green instruments is optional; they are not so much necessary, but handy.
21
List of Core Concepts
Conflict of interest
The phenomenon that employees are putting other interests (mainly private interests) above the obligations of public service.
Dilemma
A practical situation where integrity plays an important role, giving somebody a difficult choice. This concerns a situation where it is not immediately clear whether you should do or say something.
Dilemma’s concern issues in the course of which a choice has to be made out of more alternatives.
These alternatives cannot be chosen at the same time and for each alternative one may have good reasons.
Job rotation
A policy in the organization that employees at (very) vulnerable positions periodically change position, based on pre-structured intervals.
Division of tasks
A policy in the organization to avoid the accumulation of various (very) vulnerable activities with one employee, by assigning various parts of these activities to various employees.
Consequential damage
Subjective assessment of the seriousness and size of the consequences of the possible damage to the organization where not-integer activities are being implemented.
Integrity
All the issues relating to the desirable behaviour of one who holds public/or other (e.g. business) office , indicating the level of honesty and the extent to which a person or organization complies with the integrity values and norms.
Integrity policy
All policy measures taken by the organization aimed at the improvement of the resistance capability of the organization against possible integrity violations.
Integrity risks
The sum of the vulnerability minus the existing resistance capability.
22
Vulnerable activities (VA)
Job/position related tasks and activities which could possibly harm the integrity of the organization.
These tasks and activities need additional rules, measures and a policy to enhance the resistance capability of the organization.
Organizational structure
The total complex of rules, procedures and regulations to promote integrity.
Organizational culture
The underlying (informal) values and norms affecting the way of working within the organization.
Culture influences the behaviour and the relations between employees of the organization
(internally) and the contacts with the outside world (externally).
Organizational vulnerabilities (OV)
Situations or processes which supersedes the tasks of an individual and which are more focused at the organization-wide aspects of vulnerability involving integrity risks.
Optimal resistance
The presence of necessary regulations, instructions, measures and policy, implemented to avoid possible integrity violations.
Resistance capability
The extent to which an organization is “armed” against integrity violations. Resistance is defined from a structural approach. It consists of the total of (formal) rules, procedures, work instructions, policy and other measures, which contribute to the proper and integer functioning of the organization.
23
1.
Tools to prepare the integrity self-assessment
24
1.1 Checklist preparatory activities
The overview below concerns activities to prepare the self-assessment. The activities are partly aimed at informing, deciding and setting the conditions for the implementation of the selfassessment. x x x x x x x x x x x x x x x x x x x x x x
Inform top management about the self-assessment and obtain support for the starting-up x Map the financial, personnel and organizational consequences of the selfassessment
Indicate willingness to take measures to enhance the resistance capability after the self-assessment (if any)
Management of the organization is commissioning the self-assessment and sets an example
Decision-making on the start of the self-assessment
Draft Terms of Reference for the tasks and authorities of the project group
Draft and approval of the self-assessment project budget
Organize support from managers and staff to the project
Nominate a project supervisor (see tool Job profile project supervisor )
Inform other relevant Departments about the start of the self-assessment x Provide information/communication in the organization
Establish project group (see tool Job profile member project group ) x Take note of the Manual and ensure that the objectives of the selfassessment are clear for all concerned.
Organize office support (office space, manuals, secretarial support, etc.
Allocate tasks, authorities, responsibilities in the project (roles, information, feedback moments0
Draft a time table
1 Responsible for the assignment of the self-assessment
25
1.2 Example of letter from manager to employees
Dear Colleagues,To all employees,
(Name of the organization) has to function according to the officially formulated values and norms and in compliance with the requirements for the functioning of a good civil servant. In this way we are a reliable partner for citizens and other organizations. The making of clear working arrangements and taking responsibility are important conditions.
It is not only the integrity of the organization as a whole what counts, but also the personal integrity is important. All employees do have the ability to make objective and fair decisions, in a way that our name will not be discredited and our ‘clients’ have complete faith in our functioning.
Integrity requires permanent attention. Therefore, we have decided to start a project in all
(departments, sectors, units) of our organization. This project is an integrity self-assessment where we look by ourselves which activities related to our job could cause a possible risk for the integrity of the organization. In addition we will assess whether the organization itself carries certain risks which can be reduced.
The self-assessment will start on (date) . For the implementation of the self-assessment project we have established a project group. The project group is composed of representative s of our own organization. These are: (names of the project supervisor and project group members).
The ultimate aim is to investigate whether measures should be taken and arrangements should be made to enhance the resistance capability of (name of the organization) and our employees . It is the intention that the project will be concluded on (date) .
The management underlines that the self-assessment is in no way aimed at testing the personal integrity of the employees of the organization, which are not in question. The project is only aimed at identifying and assessing the existing relevant rules and regulations, in order to exclude (future) integrity risks for the organization as a whole.
To work on integrity is a continuous process. Integrity requires constant openness, honesty and involvement of every employee.
In cooperation with the project group you will be informed regularly about the progress of the project.
Signed by…. on behalf of….Director
26
1.3 Example text internal staff magazine/website
Start self-assessment
On (date) an integrity self-assessment project will start with the title (title project) .
The aim is to avoid the violation of integrity as much as possible. The project will be implemented by employees of our own organization. It is expected that the project will be accomplished on (date) .
Interest in integrity.
The subject of integrity and measures to reduce the risks of corruption is more and more in the spotlight. Completely right. The citizen has to rely on the public service. While asking citizens to comply with the rule of law and regulations, we should lead by example. Respect for citizens, honesty, and integrity are core values and norms of our Government. Monitoring of integer behaviour is high on the agenda. An integer reputation is not obvious, but has to be deserved every day. Its conservation requires permanent attention.
What does it mean integrity?
Integrity of the organization has to do with an open and clear mode of operation. It is linked to reliability, objectivity, neutrality and professionalism, care in relationships among employees themselves and in contacts with citizens. There should be room for critics, openness and working arrangements must be kept. Responsibilities have to be taken and authorities must be known.
Personal integrity is the ability to make fair and responsible decisions.
The integrity self-assessment is aimed at the reduction of integrity risks in our organization. This involves identifying risks, caused by e.g. conflicts of interest, contacts with third parties, access to confidential and financial information and flow of funds. Besides the attention to vulnerable activities related to a job, the self-assessment will also focus on the organizational vulnerabilities which supersede the tasks of an individual and which are more focused on the organization-wide aspects of vulnerability involving integrity risks, e.g. the lack of a Code of Conduct for the organization as a whole.
Features of the integrity-self assessment.
Step-by-step the project group will map the job related vulnerable activities and organizational vulnerabilities. The project group will also look at ways on how to reduce the vulnerabilities. Are there clear instructions and regulations in place for the implementation of your work? Is there enough control? Is sufficient attention being paid to integrity during the selection and recruitment of new staff?
The self-assessment will provide a view on the risky activities and vulnerabilities in general. In the end it will appear whether it will be necessary to take measures to enhance the resistance capability of our organization and individuals (e.g. by training) against integrity violations.
27
What can you do?
We are asking you to cooperate with the integrity self-assessment. For further questions please contact a member of the project group (name, telephone number, email address members project group + project supervisor) .
28
1.4 Example presentation by (top) management at the start of the integrity self-assessment
Integrity self-assessment
The importance of integrity
Government, citizens, media places high demands on an integer civil service
Public service works with tax money
Legitimacy of the public service is at stake
The public service should lead by example
The importance for the organization
Integrity violations leads to loss of reputation
Integrity is like effectiveness, efficiency and customer a quality aspect
Integrity is a pre-condition for the citizens’ trust in the public administration
29
Invest in integrity
Organisations must invest in integrity
Attention to integrity is a permanent task
Over the past few decades much has changed in the public administration and within society as a whole
Various developments have led to new procedures within the civil service and have changed the relations between the political domain, the civil service and society
These developments have added to the increasing importance of integrity within public administrations all over the world
READY?
No
One can never exclude future integrity violations, but risks scan be reduced
Permanent attention is necessary
Besides the structure, we also need to pay attention to our organizational culture and awareness
30
Preventive self-assessment organizational structure
Aimed at
vulnerable activities
-Processes linked to money, permits, confidential information, procurement
Organizational vulnerabilities, e.g.
-Selection and recruitment, job descriptions, gifts, dealing with integrity violations
1.5 Example presentation by the project supervisor at the kick-off meeting
Project integrity self-assessment
…(name of the organisation)
Design presentation
Manual self-assessment
Project and process
The phases of the self-assessment
Results of each phase and end result
Need for permanent attention
Manual integrity assessment
Starting points:
-preventive
-self-assessment
-primary aimed at organisational
structure
31
Project and process
Management of the organisation responsible
Implemented by internal project group
(members)
Reporting to management
Duration of the project
Phases of the project
Part II of the Manual
-Preparatory activities
-Phase A mapping the vulnerabilities
-Phase B mapping the resistance
-Phase C recommendations integrity risks
Results Phase A
-Insight into vulnerable activities (VA)
-Insight into organizational vulnerabilities (OV)
Based on interviews managers
32
Results Phase B
-Insight into presence of rules, policy, measures: project group
-Insight into quality rules, policy, measures: project group
-Insight into knowing and application of rules, policy, measures: interview employees
A-B = Integrity risk
Results Phase C
Recommendations improvements resistance on
-vulnerable activities
-organisational activities
Focus on structure, but also attention to awareness on integrity, code of conduct, dilemma’s, confidential counselor, etc.
33
1.6 Profile of a Project Group supervisor
Profile and expertise required
As indicated below, the following conditions, qualifications and abilities could be taken in consideration while searching and recruiting a Project supervisor. He/she should be released from other tasks which could hamper the implementation of this position.
Indicate Skills/abilities/experiences
Hold a Master degree or equivalent in public policy and management or related field
Project management experience in design, costing, implementation, monitoring and evaluation of projects
Wide knowledge of the functioning of public institutions in China, the legal framework in which they operate and Chinese policies in the area of anti-corruption and integrity
Ability to deal with sensitive information
Ability to deal with resistance in the organization
Excellent report writing, good communication and network skills, adaptability ad social awareness.
Excellent command of spoken and written Chinese language
Authoritative and ability to work at senior level
1.7 Profile of project group member
Profile and expertise required
The conditions, qualifications and abilities which should be represented in a Project group are shown below.
Starting point is that a Project group should be composed of 5 to 7 members, in a balanced way, thus representing management and staff from various Departments to ensure the complete overview on the activities in the organization subject to the self-assessment. The members should be released from other tasks which could hamper the implementation of their tasks. It is recommended, after the establishment of the Project group, to nominate a secretary. The secretary will be assigned with the management of the relevant information/documents and monitoring of the reporting.
Indicate Skills/abilities/experiences
Hold a College degree or equivalent in public policy and management or related field
Experience with personnel and organization, finance, administrative organization or related fields
Good communication and network skills, adaptability ad social awareness
Ability to deal with sensitive information
Excellent report writing,
Ability to work in a team
Project management experience
Experience with working in the public sector
34
2.
Tools Phase A
35
2.1 Overview vulnerable activities related to a job (VA)
In the table below job related vulnerable areas, activities and sub- activities are listed (see List of Core Concepts). This list is not limitative and can differ from organization to organization. Information about the vulnerable activities should come from the (top) managers (phase A).
In the first column of the table below the vulnerable activities are filled in. The second, a general description. The third indicates examples of sub-activities.
An area of the activities of a state or municipal institution shall be considered to be particularly prone to integrity violations if it meets one or several of the following criteria:
The activities are related to payments, collection of money
The activities are related to the issue of granting permits, concessions, awards
There is access to the information classified as a state or professional secret
Its principle functions are control, oversight
Etc., etc.
Managers, if desired assisted by employees, fill in the overview on vulnerable activities. This task is elaborated in section 2.3.
Vulnerable activities Description
Names of positions or job titles
Number of employees
E.g.
Supervisor
Finance
Dep.
2
E.g.
Cashier
1 1
36
Sub-activities
Money
Budget, declarations Declarations, allowances
Activities related to payments
Money
Collection
Activities related to collection of taxes, contributions
Money
Payments Activities related to payments of subsidies, allowances, sponsoring, benefits, etc.
Allocation of budgets
Control of budgets
Allocation allowances
Others:
Control of information received from tax payer
Application assessment criteria
Determining the amount due
Collecting the amount due
Decision on payments
Payments allocated amounts
Others:
Checking information of the applicant
Application assessment criteria
Determining the amount to be paid
X
37
X
Commissioning the execution of primary tasks
Goods and Services for internal organization
Activities related to assignments, orders, procurement
Decision on payment
Payment of awarded amount
Others:
Determining available budget
Determining specifications, qualifications
To make a choice on public or restricted procurement
Assessing applications
Controlling implementation
Deciding on purchase Activities related to purchase, management of goods
(office equipment, company cars, etc.), services (advice, cleaning, services, catering, etc.).
Setting quality conditions
Organizing procurement
Negotiating with suppliers
38
Confidential information
Activities related to the handling of confidential information, knowledge about others, handling of confidential documents, data bases.
Selecting suppliers
Bearing (prior) knowledge
Distributing confidential information
Receiving confidential documents
Drafting, copying confidential documents
Processing confidential information
Controlling applicants Permits, identity cards Activities related to the issuing of permits, identity cards, passports, authorizations, etc.
Applying assessment criteria
Issuing identity cards
Controlling application
39
Enforcement
Vulnerable = X
Very vulnerable = red shading
Activities related to monitoring, control, tracing, law enforcement, etc. permits
Prioritizing checks
Registration integrity violations, offences
Applying disciplinary sanctions
40
2.2 Examples of vulnerable activities related to a job
As a result of the mapping in Phase A, the project group is able to list the vulnerable activities, position by position. The table below shows an example related to the vulnerable position Officer Subsidy applications.
If selected, the project group can start with Phase B and decide to interview the Officer.
Vulnerable activities, indicated by (top) management
Money
Description
•
•
•
Providing information to clients on subsidies and financing;
Phase A
Screening subsidy applications whether in compliance with internal guidelines, policy;
Recommendation approval or refusal of application.
Vulnerable
(sub-)activity
• Activities on finance applications;
• Dealing with confidential information.
Vulnerable position/job title
Officer
Subsidy applications
Phase B
To map the factual risks
(integrity risks)
The existing resistance of the organization against integrity violations will be identified.
Interviews employees
Phase C
Recommended measures
•
•
•
Keep record on client database, external contacts;
Always discuss external contacts in internal (team) working meetings;
Obliged recording of external conversations on applications.
As indicated in the above Overview vulnerable activities , money in and of itself is to a general understanding. In setting the vulnerable activities, more precision is necessary. Does it concern the granting (of subsidies), or collection of money?
In phase A it is important to identify all steps with regard to the vulnerable activity with money. By mapping the process step-by-step, it will very often appear that more employees of various departments/units are involved in that vulnerable activity.
41
2.3 Overview organizational vulnerabilities (OV)
Below a list of ten frequent vulnerabilities are shown. This concerns particular situations or processes which are potentially vulnerable form an integrity point of view. The (top) management has to indicate whether these vulnerabilities could harm the integrity of his Department/Unit . If so, special attention to these vulnerabilities should be given.
During the pre-meeting with the (top) management and in the Guide for (top) managers Phase A,
(2.4 below) these vulnerabilities are explained.
Organizational vulnerabilities
1
2
The process of selection and recruitment new employees
Introduction new employees
Division of tasks, authority, responsibilities employees 3
4
5
6
7
8
Implementation of various sub-activities of a vulnerable activity by one and the same person
Close relations between employees and clients, suppliers or interest groups
Acceptance of gifts by employees
Secondary jobs of employees
Communication about integrity within the organization
9 Advice and facilities for reporting on integrity issues
10 Processing of integrity violations
Very important point of attention
42
2.4 Guide for (top) managers for the identification of vulnerable activities
This Guide has two objectives.
1.
To provide general background information about the nature and setting of the integrity selfassessment;
2.
To provide information about the activities to be implemented by the manager, concerning
Phase A of the self-assessment.
Brief note on the integrity self-assessment
General objective of the self-assessment is to map the vulnerabilities of the organization concerning integrity. It is the task of the manager to map in your Department/unit for which you are responsible, the vulnerabilities. Each manager will receive two overviews indicating the most frequent vulnerabilities.
Attention!
In this phase there is no need to pay attention to the existing resistance capability against integrity violations, such as rules, regulations, procedures, instructions or integrity measures already taken. All matters which can reduce the vulnerability.
Methodology of the integrity self-assessment
Preparatory activities All activities related to the starting-up of the integrity self-assessment.
To organize staff and resources; participants project group; take note of the methodology.
Phase A Identification of vulnerabilities within the Department/Unit for which you are responsible. This results in an impression of potential integrity risks.
Phase B
Phase C
Assessment of potential vulnerabilities and risks in case the resistance capability would be insufficient.
Drafting of recommendations to take measures to enhance the resistance capability of the organization against integrity violations.
Factual risks can be reduces.
The need for structural attention to integrity violations will be stressed.
Attention!
The integrity self-assessment is not aimed at finding fraud, corruption or not-integer employees. The assessment will only map the risky situations, which can be discussed and to make them manageable.
43
The role of the manager in the integrity self-assessment.
A manager knows which activities and processes are being implemented in his/her organization
(Directorate, Unit, sector, etc.). Therefore, he/she is able to portray the vulnerabilities. Please fill up both overviews (VA: Vulnerable Activities and OA: Organizational Activities). It is recommended to be assisted by some of the well-informed employees.
After the accomplishment of the self-assessment the manager has still an important role to play, as integrity is supposed to be integrated in the day-to-day activities of the organization. Permanent attention to integrity results in quality improvements of the organization.
Integrity of the employees very much depends on the integrity of the management.
The filling-in of the overview Vulnerable Activities (VA)
The definition of “vulnerable activities” within the context of the self-assessment:
Function/Position related tasks and activities which could possibly harm the integrity of the organization.
The integrity self-assessment pays particular attention to very vulnerable activities which can cause big consequential damage for the organization. Examples;
Financial loss
Wasting of tax money
Negative image of the organization: citizens, companies will lose confidence
Negative influence on atmosphere at work, stress, declining standards
Harming of citizens, clients, relations
Negative consequences for legal position employees
Political implications
In the overview VA most frequent vulnerable activities are shown. In the first column: a general description of the vulnerable activity, linked to money, tasking, goods and services, (sensitive) information, issuing and enforcement.
The second column: a general description of the kind of vulnerable activity.
The second column: examples of (sub-) activities.
In the overview the manager indicates which of these activities are implemented through which positions/functions and how many employees are involved. Moreover, the manager marks whether the activity is vulnerable of very vulnerable.
Attention!
The overview in this Manual is not limitative. Only examples of vulnerable activities are shown, which could be applied to every public organization.
44
This means that, in cooperation with the Project group, the manager needs to find out whether areas, activities are missing, which are not part of the overview. Possible additional activities should then also be taken into account in Phase B of the self-assessment.
Filling-in the overview on organizational vulnerabilities (OV)
The manager fills up the overview on organizational vulnerabilities. This concerns particular situations or processes which are vulnerable from the point of view of integrity interests. These are not linked to a particular function or position, but to the level of the Department or Unit.
In this Manual ten frequent vulnerabilities are distinguished, linked to:
Recruitment and introduction new employees
Communication/information on integrity
Allocation of tasks and responsibilities
External relations of employees
Proceedings of integrity violations
A brief explanation of the ten vulnerabilities is shown below;
1.
The process of recruitment of new employees
It is of utmost importance to avoid recruitment of incorruptible employees. It is important to select reliable persons. Incorruptible persons could also have a spill-over effect on the behaviour of other employees. One person could seriously threat the whole organization.
2.
The introduction of new employees in the organization
New employees are not yet familiar with rules, procedures, norms and values of the organization.
They do not know how to deal with integrity issues. The introduction period can be considered vulnerable to integrity violations.
3.
Division of tasks, authorities, responsibilities
New employees need to know their tasks, way of implementation, their authority and responsibilities. Vagueness in this respect can result in the implementation of not-sharply defined activities without clear limitations/boundaries.
4.
Implementation of various sub-activities of a vulnerable activity (VA) by one and the same person.
Within an organization there are processes not fit for implementation by one and the same person.
Activities which are part of that kind of processes are vulnerable in the hands of one person.
5.
Close connections between employees and clients, customers, interest groups.
Employees who carry out vulnerable activities for a long period run the risk of undesirable, informal relations with clients, suppliers and interest groups.
6.
Acceptance of gifts by employees
45
The acceptance of gifts can result in vulnerable situations. Gifts can influence the employee in his/her decision-making. Objectivity, neutrality can be at stake. Bribing, corruption is an integrity violation and closely related to this vulnerability.
7.
Secondary jobs and private interests.
Objectivity, neutrality of the decision-making process can be harmed by secondary jobs, as a result of intertwined interests. Interests of family, friends can put private interests above the obligations of the public service.
8.
Communication on integrity in the organization
Insufficient communication/information about integrity could result in risks. Employees might get the impression that the organization is not so much interested in the integer functioning of the employees. This can also lead to unclearness about expectations on what to do or not to do. The lack of clearness in this respect can result in integrity violations.
9.
Advice and reporting on integrity violations by employees
In case employees do not have the possibility to ask for advice on integrity issues, they run the risk of making wrong decisions. This can be particularly relevant where it suspicious cases concerns and no internal channels are available for reporting. In a worst case the information is leaked to nonauthorized institutions, such as the media, and/or before the organization has been able to investigate the suspicious case.
10.
Way of dealing with integrity violations
In case the organization does not have clear procedures on how to deal with integrity violations, the consequences can be that a) the organization does not know how to deal with an integrity violation at all and b) the impression may rise that the organization does not pay attention to the subject of integrity and that integrity violations are more or less allowed.
Return delivery overview, conducting interviews and reporting
After ( number of days/weeks) the filled in overviews should be returned. Upon receipt the project group reviews the overviews on completeness. Thereafter a member of the project group will conduct an interview with the manager to discuss the replies and for an explanation on the choices made. The results will be processed in a report on Phase A (insight into potential risks).
In phase B: the factual risks will be identified (vulnerability versus resistance0.
Perhaps unnecessarily
This is only about the mapping of vulnerabilities. Phase a leaves aside the way one deals with the vulnerabilities. It is not looked at the person who carries out the activities or that the vulnerability is covered by a measure or rule, instruction, etc.
It only goes to estimate of the size of the consequential damages in case no rule or measure would exist and the question what then would be the risk.
46
2.4 Example vulnerable activity
Example: the vulnerable activities related to dealing with money
As indicated in the Overview vulnerable activities , money in and of itself is to a general understanding. In setting the vulnerable activities, more precision is necessary. Does it concern the granting (of subsidies), or collection (taxes) of money?
In phase A it is important to identify all steps with regard to the vulnerable activity with money. So, of the person who prepares a tax assessment to the person who collects the tax. By mapping the process step-by-step, it will very often appear that more employees of various departments/units are involved in that vulnerable activity.
This example is applicable to all vulnerable activities in the overview.
This always concerns:
Mapping and identification of the current vulnerable activities;
Indicating the functions of which the activities are performed;
Indicating vulnerable activities could have the largest consequential damages
47
3 Tools Phase B
48
3.1 Questionnaire interviews employees
The current situation in the public organization shall be analyzed by means of a Questionnaire.
Replies to the given questions will help to identify vulnerable activity areas of the organization and describe them according to the selected criteria for determining the probability of integrity violations, e.g. money, confidential information, activities related to granting or restricting permits, concessions.
The questionnaire contains 6 questions about vulnerable activities and 11 about (aspects of) organizational vulnerabilities.
The replies will also give an insight in the knowledge and application of the identified rules, regulations and measures.
49
Part 1 Identification of the knowledge and application of rules, measures on vulnerable activities (VA)
1 Vulnerable activities: money
(Example: budgets, collection, payments)
1A Are you responsible for budgets or the collection or payment of money?
1B
1C
1D
(if not, proceed to question 2)
Requirements in your organization have been formulated?
Yes/no
(if not or unknown, proceed to question 2) Yes/no/ do not know
If yes, are you familiar with the purpose of these requirements? Yes/if no, why not?
Are these rules applied in practice? Yes/if no, why not?
2 Vulnerable activities: Procurement
2C
2D
(Example: organizing public procurement, awarding of contracts)
2A Are you involved in procurement processes?
2B
(if not, proceed to question 3) Yes/no
Requirements/rules/instructions in your organization have been formulated?
Yes/no/ do not know
(if not or unknown, proceed to question 3)
If yes, are you familiar with the purpose of these requirements?
Are these rules applied in practice?
Yes/if no, why not?
Yes/if no, why not?
3 Vulnerable activities: goods and services internal organization
(Example: purchases, monitoring, hiring)
3A Are you involved in purchase/hiring or monitoring of goods and service Yes/no?
3B
(if not, proceed to question 4)
Requirements in your organization have been formulated?
(if not or unknown, proceed to question 4)
Yes/no
Yes/no/ do not know
3C If yes, are you familiar with the purpose of these requirements? Yes/if no, why not?
50
3D Are these rules applied in practice?
4 Vulnerable activities: Confidential information
(Example: dealing, producing confidential documents)
4A Do you come into contact with confidential information?
4B
4C
4D
(if not, proceed to question 5)
Requirements in your organization have been formulated?
(if not or unknown, proceed to question 5)
If yes, are you familiar with the purpose of these requirements?
Are these rules applied in practice?
Yes/if no, why not?
Yes/no
Yes/no/ do not know
Yes/if no, why not?
Yes/if no, why not?
5 Vulnerable activities: Granting or restricting permissions,
concessions, allowances
5D
5E
5F
5G
(Example: licenses, permits, certificates)
5A Are you involved in the granting, issuing or awarding of personal
5B
5C documents?
(If not, proceed to question 6)
Are the principles (regulations, criteria) for granting/restricting particular rights defined/regulated? Are such criteria exhaustive?
Are these principles applied in practice?
Yes/no
Yes/no/do not know
Yes/if no, why not?
If yes, are you familiar with the purpose of these requirements?
Are the specific rights granted limited/unlimited (limited/ unlimited number of rights)? Who and how defines the number of rights?
Is any preventive (forecasting and eliminating problems), comparative
(monitoring and regulating the process), feedback (monitoring results
Yes/if no, why not?
Yes/no/do not know and learning from mistakes) control undertaken?
Have any disclosure reports been made regarding the implementation
Yes/no/do not know process of control and/or supervision by external audit findings? Yes/no/do not know
51
6 Vulnerable activities: Enforcement
6B
6C
6D
(Example: supervision, monitoring, control)
6A Do you perform enforcement, controlling, supervisory tasks?
(If not, proceed to question 7)
Requirements in your organization have been formulated?
(if not or unknown, proceed to question 7)
If yes, are you familiar with the purpose of these requirements?
Are these rules applied in practice?
Yes/no
Yes/no/ do not know
Yes/if no, why not?
Yes/if no, why not?
Part II Research on the awareness and application of measures related to
(aspects of) organizational vulnerabilities (OV)
7E
7F
7G
7A
7B
7C
7D
7 Attention to integrity in selection and recruitment
Did you have to submit a resume?
Did you have credentials which information could be obtained about
Yes/no your functioning in a previous function?
If yes, are those references actually checked?
One has to original diploma’s requested?
Yes/no
Yes/no/ do not know
Yes/no
Yes/no Did you have to submit a certificate of good behaviour?
Are you at interview explicitly pointed to any integrity aspects of your (new) work?
Having seen the previous questions, did you follow the official application procedure?
Yes/no
Yes/no
8 Introduction period and attention to integrity
8A
8B
8C
8D
Did you swear an oath or promise by appointment?
(if no, proceed with question 8 D)
Yes/no
If yes, is there a connection with the subject of integrity? Yes/no
After your appointment, did you follow an introduction programme? Yes/no
Did the programme pay explicitly attention to integrity and
52
problems which may occur in this connection?
9 Job descriptions
Yes/no
9A
9B
9C
9D
Are the functions of your job defined?
(if no, proceed with question 10)
Yes/no
Are you in possession of your job description? Yes/no
Are all functions of your current job and authorities clearly defined? Yes/no
Do you perform duties which are not described in your job description? Yes/no
10 Provisions on division of responsibilities and tasks
10A Do you perform duties in vulnerable processes prone to a conflict of interest? Yes/no
10B Requirements in your organization have been formulated? Yes/no/do not know
(if not, or unknown, proceed to question 11)
10C If yes, do you know the purpose of these measures/requirements? Yes/no
10D Are those applied in practice? Yes/if not, why not?
11 Provisions on job rotation
11A Are you involved in vulnerable processes, where you are in contact with the same clients or interest groups over a long period of time? Yes/no
11B Does job rotation exists within your organization?
(if not, or unknown, proceed to question 12)
11C If yes, do you know the purpose of job rotation?
11D Is this applied in practice?
Yes/no/do not know
Yes/if not, why not?
Yes/if not, why not?
12 Provisions on gifts
12A You are offered something sometimes?
12B Are their provisions on acceptance of gifts in your organization?
(if not, proceed with question 13)
12C If yes, do you know the purpose of these provisions?
Yes/no
Yes/no/do not know
Yes/if not, why not?
53
12D Are those applied in practice?
13 Provisions on secondary jobs
13A Do you perform or your closest colleague secondary jobs?
13B Are their provisions on performing secondary jobs?
(if not, proceed with question 14)
13C If yes, do you know the purpose of those provisions?
13D Are those applied in practice?
14 Communication
Yes/if not, why not?
Yes/no
Yes/no/do not know
Yes/if not, why not?
Yes/if not, why not?
14A Is integrity discussed in staff meetings?
14B Is integrity regularly raised on various occasions and through
Different communication channels? (website, speeches management, staff magazine, etc.)
Yes/no
Often/sometimes/never, why not?
15 Integrity Confidential counselor
15A Is it clear for you how to deal with integrity violations (to whom to report, etc.), in case you have observed an integrity violation within the organization by other employees?
15B Do you know where to go to for advice on integrity issues?
Yes/no
Yes/no
15C Has a confidential Counselor been appointed in your organization? Yes/no/do not know
(if not, proceed to question 16)
15D Do you know who this person is and for what problems you can contact with this person?
15E Is this person easy to approach?
Yes/no
Yes/if not, why not?
16 Procedure processing integrity violations?
16A Have you ever heard about integrity violations in your organization? Yes/no
(abuse of resources, discrimination of women, theft, corruption, etc.)
16B Are there provisions, procedures on how to deal with such cases?
16C Is it clear how to deal in case of having observed an integrity violation
Yes/no/do not know
54
by other employees?
16D Do you have the impression that actions are always taken seriously
Yes/if not, why not? and in compliance with the regulations in case of integrity violations? Yes/if not, why not?
The answers to all these questions need to be processed. In the next table an example of processing the answers to question 5:
Vulnerable activities: Granting or restricting permissions,
concessions, allowances (hereinafter-the granting/restrictions of particular rights) is shown.
Basically, the criteria (Activities, Activity control, Employees, Decisions) can be applied to all selected vulnerable areas/activities. In the first column the criteria are linked to the questions (Ref. means reference). The second column shows indicators of process, while the last column refers to the performance indicators in section 3.3.
3.2 Example processing replies of the interviews employees (process indicators)
Criteria Indicators of process Performance indicator reference
(Section 3.3)
A. Activities Please shade the degree and scale of existence and implementation
1 2 3
A.1
Regulation of activities
Ref.:
Question
5/5B
Principles
(regulation criteria) for granting are defined/regulated non-exhaustively
Principles
(regulation criteria) for granting are not defined/regulated
Activities involving the granting are not defined
A.2 Activity specifics
Ref: Question
5/5E
Unlimited specific rights are granted
(unlimited number of rights)
Limited specific rights are granted
A limited number of specific rights is granted as determined by the institution
B. Activity control
B.1 Preventive control
Preventive control
Ref.:
Question
5/5F.
B.2 Control by external entities
Ref.:
Question
5/5G. is undertaken, but is not defined/regulated
There are disclosure reports regarding the process of granting: adequate actions taken
Performance of preventive control is not defined/regulated
There are disclosure reports regarding the process of granting: necessary actions partly taken
Such control is not defined/regulated and is not undertaken
There are disclosure reports regarding the process of granting: no actions taken
C. Employees.
4
4
8, 11
11
55
C.1
Regulations of employee activities
Ref.:
Question
9/9C
C.2 Control of employee activities
Ref.:
Question 16,
16A,B
Activities of the employees granting specific rights are narrower than defined
There are disclosure reports regarding actions, activities, etc. of the employees granting specific rights: adequate actions taken
Activities of the employees granting specific rights are broader than defined
There are disclosure reports regarding actions, activities, etc. of the employees granting specific rights: necessary actions partly taken
Activities of the employees granting specific rights are not defined
There are disclosure reports regarding actions, activities, etc. of the employees granting specific rights: no actions taken
3
10
D. Decisions
D.1 Attempt to influence decisions
Ref.:
Question
12/12A.
There are disclosure reports regarding attempt to influence decisions: adequate actions taken
There are disclosure reports regarding attempt to influence decisions: necessary actions partly taken
There are disclosure reports regarding attempt to influence decisions: no actions taken
6, 7
Note: These process indicators show whether the various elements of integrity management have been implemented in full or not (yet). If an element has not yet been implemented in full, this need not automatically lead to an adverse assessment. A public organization might think a particular element is of secondary importance or is adequately covered by compensatory measures. The information should also lead to information on which elements could be given priority for further improvement. They do not pretend to give a full overview of all conceivable elements. It should also be noted that the information illustrates the implementation of certain elements of integrity management, not the public organization’s actual integrity. The actions needed to implement a particular element differ from case to case and depend in part on, for example, the organization’s size. This cannot be seen directly from the eleven aspects above.
56
3.3 Performance indicators (resistance capability) integrity measures and integrity policy
Through this list of performance indicators it is to determine the extent of the necessary aspects of a particular desired integrity measure or policy are actual and sufficiently present, or to assess progress.
Eleven aspects
1 Recruitment policy.
It is up to the project group to map whether recruitment measures are in place where the risk on recruitment of non-integer employees is reduced.
There is excellent resistance if the recruitment policy at least contains the following elements:
The querying of a comprehensive resume;
The querying and control of references;
The control of original diploma’s and certificates;
The request for a declaration on good behaviour;
Information to applicants on (possible) integrity aspects of their duties;
The consistently following of a set application procedure.
2 Introduction policy which attention is paid to integrity
There is excellent resistance when the following issues are taken into consideration;
The taking of an oath or promise related to integrity;
The explanation and issuing of a Code of Conduct;
The introduction of a Confidential Counselor.
Background information on oath of office, the promise, or Code of Conduct is shown in Section 4.2 below.
Background information about the Confidential Counselor is shown in Section 4.3 below.
3 The presence of job descriptions
There is excellent resistance on job descriptions when
Job descriptions are defined for all employees;
Each employee has a personal copy of his/her job description;
Job descriptions indicate the current status of the existing working conditions;
The job descriptions indicate all the duties to be performed.
4 Policy on division of functions
57
There is excellent resistance regarding division of functions, if:
The organization has a clear view on vulnerable activities and functions;
The various vulnerable sub-activities are performed by different employees;
Vulnerable activities which cannot be sub-divided and cannot be implemented separately, are performed in a team.
5 Policy on job rotation
There is excellent resistance regarding job rotation, if:
The organization has a clear view on vulnerable activities and functions;
Employees, performing vulnerable duties, rotate jobs regularly;
Employees to serve other clients in case it is not possible to rotate.
6 Policy on gifts
There is excellent resistance regarding gifts, if there is clarity about
The maximum value;
How to deal with dinner invitations, study trips, etc.;
Whether it is allowed to accept gifts at home;
Which gifts may be kept or hand over to the Department;
What to do with gifts which are in conflict with the above mentioned rules.
7 Policy on secondary jobs and private interests
There is excellent resistance regarding gifts, if there is clarity about
Which secondary jobs should be notified;
Which kind of secondary jobs are not allowed;
In which cases the employee has to report that he/she comes into contact with private interests;
How to deal with (possible) private interests.
8 The degree and mode of communication about integrity in the organization
Regarding communication there is excellent resistance, if
The organization pays regularly attention to the subject of integrity;
There is communication in different ways and several channels about integrity;
Integrity is discussed during performance assessment and staff meetings;
Information material is available about integrity (brochures, code of conduct, etc.)
Integrity is part of staff trainings.
9 Advice and reporting possibilities for employees on integrity issues
There is excellent resistance, if:
The organization has appointed a Confidential Counselor (see Section 4.3 below)
58
The Confidential Counselor (CC), on request, gives advice to employees on integrity issues;
The CC is available for consultation in case of integrity violations;
The CC is easy to approach.
10 The way of dealing with integrity violations
The way of dealing with integrity violations contributes to an excellent resistance if
The organization has clearly defined/documented how to deal with integrity violations;
There is consistent ruling on such violations and this happens in all openness (but anonymously).
11 Enforcement
There is excellent resistance , if:
The organization controls the activities prone to integrity violations;
The enforcement of the rules and regulations is monitored;
The enforcement is controlled by independent (external) auditors/
If any of these desired integrity measures do not exist, please take action.
4 Tools Phase C
This chapter provides background information which can be helpful in increasing the resistance capability of the organization.
59
4.1 Example format Integrity policy
Integrity policy plan
Author:
Version:
Approved by:
Date:
Validity (duration):
1. Vision
-Objectives
-Vision on integrity
-Starting points
-Commitment (top) management
2. Values and norms
-Core values organization
-Code of conduct
-List of relevant regulations, administrative orders, etc.
3. Structure, culture and measures
-Internal organization related to integrity
-Administrative organization
-Information on integrity measures taken, to be taken, e.g. number of trainings
4. Integrity violations
-Records
-Procedures
-Integrity coordinator
5. Monitoring, evaluation, reporting
-who, how, to whom, frequency?
60
4.2 Examples Codes of Conduct
UNITED KINGDOM
CIVIL SERVICE CODE
Presented to Parliament pursuant to section 5 (5) of the Constitutional Reform and Governance Act 2010
Civil Service values
1.
The statutory basis for the management of the Civil Service is set out in Part 1 of the Constitutional Reform and Governance Act 2010.
2.
The Civil Service is an integral and key part of the government of the United
Kingdom 2 . It supports the Government of the day in developing and implementing its policies, and in delivering public services. Civil servants are accountable to Ministers 3 , who in turn are accountable to Parliament 4 .
3. As a civil servant, you are appointed on merit on the basis of fair and open competition and are expected to carry out your role with dedication and a commitment to the Civil Service and its core values: integrity, honesty, objectivity and impartiality. In this Code:
‘integrity’ is putting the obligations of public service above your own personal interests;
‘honesty’ is being truthful and open;
‘objectivity’ is basing your advice and decisions on rigorous analysis of the evidence; and
2 Civil servants working for the Scottish Executive and the Welsh Assembly Government, and their Agencies, have their own versions of the Code. Similar Codes apply to the Northern Ireland Civil Service and the
Diplomatic Service. Civil servants working in Non Ministerial Departments in England, Scotland and Wales are covered by this Code.
3 Some civil servants are accountable to the office holder in charge of their organisation. This is made clear in terms and conditions of employment.
4 Civil servants advising Ministers should be aware of the constitutional significance of Parliament, and of the conventions governing the relationship between Parliament and the Government.
61
‘impartiality’ is acting solely according to the merits of the case and serving equally well
Governments of different political persuasions.
4. These core values support good government and ensure the achievement of the highest possible standards in all that the Civil Service does. This in turn helps the Civil Service to gain and retain the respect of Ministers, Parliament, the public and its customers.
5.
This Code 5 sets out the standards of behaviour expected of you and other civil servants. These are based on the core values which are set out in legislation. Individual departments may also have their own separate mission and values statements based on the core values, including the standards of behaviour expected of you when you deal with your colleagues
.
Standards of behaviour
Integrity
6.
You must:
fulfill your duties and obligations responsibly;
always act in a way that is professional 6 and that deserves and retains the confidence of all those with whom you have dealings 7 ;
carry out your fiduciary obligations responsibly (that is make sure public money and other resources are used properly and efficiently);
deal with the public and their affairs fairly, efficiently, promptly, effectively and sensitively, to the best of your ability;
keep accurate official records and handle information as openly as possible within the legal framework; and
comply with the law and uphold the administration of justice.
7. You must not:
misuse your official position, for example by using information acquired in the course of your official duties to further your private interests or those of others;
5 The respective responsibilities placed on Ministers and special advisers in relation to the Civil Service are set out in their Codes of Conduct: www.cabinetoffice.gov.uk/propriety_and_ethics. Special advisers are also covered by this Civil Service Code except, in recognition of their specific role, the requirements for objectivity and impartiality (paras 10-15 below).
6 Including taking account of ethical standards governing particular professions.
7 Including a particular recognition of the importance of cooperation and mutual respect between civil servants working for the UK Government and the devolved administrations and vice-versa.
62
accept gifts or hospitality or receive other benefits from anyone which might reasonably be seen to compromise your personal judgment or integrity; or
disclose official information without authority. This duty continues to apply after you leave the Civil Service.
Honesty
8. You must:
set out the facts and relevant issues truthfully, and correct any errors as soon as possible; and
use resources only for the authorized public purposes for which they are provided.
9. You must not:
deceive or knowingly mislead Ministers, Parliament or others; or
be influenced by improper pressures from others or the prospect of personal gain.
Objectivity
10. You must:
provide information and advice, including advice to Ministers, on the basis of the evidence, and accurately present the options and facts;
take decisions on the merits of the case; and
take due account of expert and professional advice.
11. You must not:
ignore inconvenient facts or relevant considerations when providing advice or making decisions; or
frustrate the implementation of policies once decisions are taken by declining to take, or abstaining from, action which flows from those decisions.
Impartiality
12. You must:
carry out your responsibilities in a way that is fair, just and equitable and reflects the Civil
Service commitment to equality and diversity.
13. You must not:
63
act in a way that unjustifiably favours or discriminates against particular individuals or interests.
Political Impartiality
14. You must:
serve the Government 8 , whatever its political persuasion, to the best of your ability in a way which maintains political impartiality and is in line with the requirements of this
Code, no matter what your own political beliefs are;
act in a way which deserves and retains the confidence of Ministers, while at the same time ensuring that you will be able to establish the same relationship with those whom you may be required to serve in some future Government; and
comply with any restrictions that have been laid down on your political activities.
15. You must not:
act in a way that is determined by party political considerations, or use official resources for party political purposes; or
allow your personal political views to determine any advice you give or your actions.
Rights and responsibilities
16. Your department or agency has a duty to make you aware of this Code and its values. If you believe that you are being required to act in a way which conflicts with this Code, your department or agency must consider your concern, and make sure that you are not penalised for raising it.
17. If you have a concern, you should start by talking to your line manager or someone else in your line management chain. If for any reason you would find this difficult, you should raise the matter with your department’s nominated officers who have been appointed to advise staff on the Code.
18. If you become aware of actions by others which you believe conflict with this Code you should report this to your line manager or someone else in your line management chain; alternatively you may wish to seek advice from your nominated officer. You should report evidence of criminal or unlawful activity to the police or other appropriate regulatory authorities. This Code does not cover HR management issues.
19. If you have raised a matter covered in paragraphs 16 to 18, in accordance with the relevant procedures
9
, and do not receive what you consider to be a reasonable response,
8 Some civil servants are accountable to the office holder in charge of their organisation. This is made clear in terms and conditions of employment.
9 The whistleblowing legislation (the Public Interest Disclosure Act 1998) may also apply in some circumstances. The Directory of Civil Service Guidance and the Civil Service Management Code give more information: www.cabinetoffice.gov.uk/conduct-ethics/civil-service.aspx.
64
you may report the matter to the Civil Service Commission
10
. The Commission will also consider taking a complaint direct. Its address is:
3rd Floor, 35 Great Smith Street, London SW1P 3BQ.
Tel: 020 7276 2613
email: info@civilservicecommission.org.uk
If the matter cannot be resolved using the procedures set out above, and you feel you cannot carry out the instructions you have been given, you will have to resign from the
Civil Service.
20. This Code is part of the contractual relationship between you and your employer. It sets out the high standards of behaviour expected of you which follow from your position in public and national life as a civil servant. You can take pride in living up to these values.
November 2010
10 The Civil Service Commission’s Guide to Bringing a Complaint gives more information, available on the
Commission’s website: www.civilservicecommission.org.uk.
65
COUNCIL OF EUROPE
International Code of Conduct for Public Officials
I. General principles
1. A public office, as defined by national law, is a position of trust, implying a duty to act in the public interest. Therefore, the ultimate loyalty of public officials shall be to the public interests of their country as expressed through the democratic institutions of government.
2. Public officials shall ensure that they perform their duties and functions efficiently, effectively and with integrity, in accordance with laws or administrative policies. They shall at all times seek to ensure that public resources for which they are responsible are administered in the most effective and efficient manner.
3. Public officials shall be attentive, fair and impartial in the performance of their functions and, in particular, in their relations with the public. They shall at no time afford any undue preferential treatment to any group or individual or improperly discriminate against any group or individual, or otherwise abuse the power and authority vested in them.
II. Conflict of interest and disqualification
4. Public officials shall not use their official authority for the improper advancement of their own or their family’s personal or financial interest. They shall not engage in any transaction, acquire any position or function or have any financial, commercial or other comparable interest that is incompatible with their office, functions and duties or the discharge thereof.
5. Public officials, to the extent required by their position, shall, in accordance with laws or administrative policies, declare business, commercial and financial interests or activities undertaken for financial gain that may raise a possible conflict of interest. In situations of possible or perceived conflict of interest between the duties and private interests of public officials, they shall comply with the measures established to reduce or eliminate such conflict of interest.
Public officials shall at no time improperly use public moneys, property, services or information that is acquired in the performance of, or as a result of, their official duties for activities not related to their official work.
7. Public officials shall comply with measures established by law or by administrative policies in order that after leaving their official positions they will not take improper advantage of their previous office.
III. Disclosure of assets
66
8. Public officials shall, in accord with their position and as permitted or required by law and administrative policies, comply with requirements to declare or to disclose personal assets and liabilities, as well as, if possible, those of their spouses and/or dependents.
IV. Acceptance of gifts or other favours
9. Public officials shall not solicit or receive directly or indirectly any gift or other favour that may influence the exercise of their functions, the performance of their duties or their judgment.
V. Confidential information
10. Matters of a confidential nature in the possession of public officials shall be kept confidential unless national legislation, the performance of duty or the needs of justice strictly require otherwise. Such restrictions shall also apply after separation from service.
VI. Political activity
11. The political or other activity of public officials outside the scope of their office shall, in accordance with laws and administrative policies, not be such as to impair public confidence in the impartial performance of their functions and duties .
67
4.3 Information Confidential Integrity Counselor
This information is used in The Netherlands for working with Confidential Integrity Counselors(CIC).
Confidential counselors exist in many EU public administrations.
Integrity
Integrity is considered very important at all levels of government in the Netherlands. A host of initiatives are being implemented at both central and local level to promote integrity. The appointment of a Confidential Integrity Counselor (CIC) is one of these initiatives.
Broad outline of duties
Fleshing out the role of the CIC is a task which confronts many government organizations, particularly following the introduction of the ‘Order establishing the procedure to be followed in dealing with a suspected abuse’.
1
This provides outline guidance on the creation of a CIC provision.
The CIC generally fulfills two roles. On the one hand, the CIC plays a sounding board role, whereby government employees can obtain advice on integrity issues. This involves advising on how to deal with particular ethical or integrity-related issues which the government employee encounters. On the other hand, the CIC plays a reporting desk role where government employees can report (their suspicions of) breaches of integrity perpetrated within their own organization if they do not wish to report it to their superior. The CIC then advises the government employee on the right path to follow, or passes the allegation on - on the employee's behalf and with their approval - to the appropriate authorities. However, the precise duties, powers and position of the CIC are largely left undefined and are implemented differently from organization to organization.
Job profile
Skills & personality
To fulfill the role effectively, a CIC needs to have certain specific skills and qualities. Alongside a number of professional qualities, the person's nature - i.e. their character - is at last equally important. Hence the CIC needs to be a sociable, approachable, sincere and authoritative figure that enjoys the confidence of staff but can simultaneously also gets on well with the management of the organization. The CIC must also be able to put things in perspective and soothe the fears and emotions of the complainants.
Experience & network
It is a good idea to appoint a CIC who already has the necessary experience within the organization concerned and has thus built up an internal network. Familiarity with integrity is naturally a must. An example of a job profile is given below.
3
This covers the main skills, qualities and knowledge required.
Skills
• The confidential counselor has strong communication skills, both verbal and written (can communicate adequately with staff from various levels and specialisms within the organization).
68
• The confidential counselor has an insight into their own actions (demonstrates awareness of how their own behaviour can appear to others).
• The confidential counselor is able to give advice (is able to identify a problem on the basis of a conversation and to provide clear and understandable advice on that basis).
• The confidential counselor is able to participate in dialogue (able to actively listen and help a conversation to develop constructively).
Qualities
• Has experience of life and integrity.
• Has a balanced personality.
• Can reflect on their own behaviour and that of others.
• Can handle confidential information.
• Can cope with resistance.
• Is able to adopt an independent position.
• Has an insight into the context within which, and the way in which, unwanted forms of interaction and other improper behaviour occur within an organization.
• Is approachable / accessible to staff within the organization.
• The confidential counselor is able to maintain a professional detachment from the subject under discussion and the person with whom they are speaking, yet at the same time still remains involved.
• The confidential counselor is open to peer supervision and periodic discussions with colleagues.
Most important duties
The CIC has a number of duties. The most important are briefly described below:
4
• Informing: the CIC informs the organization about their role and duties and how they work.
• Listening: the CIC is a point of contact and is responsible for the initial contact with employees who have queries relating to integrity issues.
• Advising: the CIC advises employees on ethical or integrity issues. This particularly relates to practical dos and don'ts, as well as explaining the applicable law and regulations and any relevant code of conduct in this area. In the case of breaches by others, the CIC advises on the options for communicating the information to the competent authorities. The confidential counselor can give managers solicited and unsolicited advice about implementing policy within the organization.
• Assisting: the CIC assists and supports the complainant in flagging up suspicions of improper conduct to the competent authorities.
69
• Recording and reporting: all queries and allegations received by confidential counselors are recorded in a consistent manner. Every year an anonymised report about the nature, seriousness and scope of the allegations will be submitted in a standardised form to the integrity policy coordinator, who submits a combined report to the Minister. In addition, each confidential counselor submits an annual anonymised report to the competent authorities in the unit to which the issue / allegation applies.
• Monitoring and providing aftercare: the confidential counselor provides the complainant with aftercare. The confidential counselor checks whether the complainant has suffered deleterious consequences in their job as a result of the allegation. The confidential counselor also monitors how satisfied the complainant in question is with the resolution of the highlighted problem, both by the confidential counselor themselves and possibly by others in the organization. The CIC must thereby also inform the complainant about progress and any resolution.
• Preventing: if the CIC receives a large number of queries about particular integrity issues, or if it is found as a result of an allegation that a breach of integrity has occurred, it must be possible for people across the organization to learn from this, and the (integrity) policy will need to be amended accordingly. Anonymised case histories can be used to inform the organization of what breaches of integrity have taken place, and what steps have been taken against it.
70
4.4 Example Basic training course integrity and integrity self-assessment
Basic Course: Integrity and integrity self-assessment
Target group: (top) managers
Duration: 1 day (+ self-study)
The Basis training course enables government organisations to establish where there integrity policies could be enhanced
Learning objectives:
Understands the concept of integrity
Knows how to distinct various phases in an integrity self-assessment
Insight in the core elements of an integrity audit
Able to play a leading role in the organisation in connection with other Directorates and
Departments to start an integrity audit on his own
Knows how to direct a self-assessment team towards the desired results
Learns how to organise the related tasks and responsibilities efficiently and effectively
Ability to direct subordinates to towards desired results
This course has to be successfully passed before starting a specialised course: How to implement an integrity self-assessment for designated staff members.
This course generates a view on which working processes of the organisation are most vulnerable and prone to specific integrity risks. Attention is also paid to cultural aspects of the organisation such as awareness of integrity and the role of management.
Duration 2 days, including a pilot self-assessment.
This course is also aimed at the training of a self-assessment project supervisor and members of the project group.
71