A Comparative Study OF Routing Protocols IN Mobile Ad
advertisement

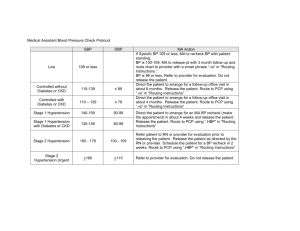
A Comparative Study OF Routing Protocols IN Mobile Ad-hoc Network Neha Pharswan1, Prof. Dr. (Mrs.) Rama Sushil2 1 Department of Computer Science and Engineering, DIT University, Dehradun, Uttarakhand nehapharswan.86@gmail.com 2 Professor, Department of Computer Science & Application, DIT University, Dehradun, Uttarakhand ramasushil@yahoo.co.in Abstract: Mobile Ad hoc Networks (MANET) are a kind of temporary networks in which nodes are moving without any fixed infrastructure or centralized administration. Due to the diverse applications it is an interesting current research area. There are different current research area in MANET are routing, synchronization, power consumption etc. This paper concentrates on routing protocols which is the most challenging issue due to the dynamic topology of ad hoc networks. There are different strategies proposed for efficient routing which claimed to provide improved performance. It is a kind of challenge and quite difficult to determine which protocol is best suitable protocol for different network conditions. This paper provides an overview of different routing protocols proposed in literature. I. Multi-hop radio relaying- When a source node and destination node for a message is out of the radio range, the MANETs are capable of multi-hop routing. Distributed nature of operation for security, routing and host configuration. A centralized firewall is absent here. The nodes can join or leave the network anytime, making the network topology dynamic in nature. Mobile nodes are characterized with less memory, power and light weight features. The reliability, efficiency, stability and capacity of wireless links are often inferior when compared with wired links. This shows the fluctuating link bandwidth of wireless links. Introduction A mobile ad hoc network (MANET) is a self-configuring infrastructure less network of mobile devices connected by wireless. Each device in a MANET is free to move independently in any direction, and will therefore change its links to other devices frequently. Each must forward traffic unrelated to its own use, and therefore be a router. The primary challenge in building a MANET is equipping each device to continuously maintain the information required to properly route traffic. Such networks may operate by themselves or may be connected to the larger Internet. MANETs are a kind of Wireless ad hoc network that usually has a routable networking environment on top of a Link Layer ad hoc network. In recent years MANET has gained popularity and lots of research is being done on different aspects of MANET. It is an infrastructure less network having no fixed base stations MANET is characterized by dynamic topology low bandwidth and low power consumption. All the nodes in the network are moving i.e. topology of the network is dynamic so the nodes can act both as host as well as router to route information unnecessary for its use. II. Characteristics of MANET In MANET, each node acts as both host and router. That is it is autonomous in behavior. III. Routing Protocols Routing protocols define a set of rules which governs the journey of message packets from source to destination in a network. In MANET, there are different types of routing protocols each of them is applied according to the network circumstances. Basic classification of routing protocols is: 1. Reactive Routing Protocol: Reactive routing protocol is also known as on demand routing protocol. In this protocol route is discovered whenever it is needed Nodes initiate 0route discovery on demand basis. Source node sees its route cache for the available route from source to destination if the route is not available then it initiates route discovery process. The on- demand routing protocols have two major components. Route discovery: In this phase source node initiates route discovery on demand basis. Source nodes consults its route cache for the available route from source to destination otherwise if the route is not present it initiates route discovery. The source node, in the packet, includes the destination address of the node as well address of the intermediate nodes to the destination. Route maintenance: Due to dynamic topology of the network cases of the route failure between the nodes arises due to link breakage etc, so route maintenance is done. Reactive protocols have acknowledgement mechanism due to which route maintenance is possible Reactive protocols add latency to the network due to the route discovery mechanism. Each intermediate node involved in the route discovery process adds latency. These protocols decrease the routing overhead but at the cost of increased latency in the network. Hence these protocols are suitable in the situations where low routing overhead is required. There are various well known reactive routing protocols present in MANET for example DSR, AODV and DYMO. Dynamic source routing (DSR) is based on source routing where the source specifies the complete path to the destination in the packet header. All intermediary nodes along the path simply forwards the packet to the next node as specified in the packet header. This means that intermediate nodes only need to keep track of their neighboring nodes to forward data packets. The source on the other hand, needs to know the complete hop sequence to the destination. This eliminates the need for maintaining latest routing information by the intermediate nodes as in DSDV. In DSR, all nodes in a network cache the latest routing information. When more than one route to the destination is found, the nodes cache all the route information so that in case of a route failure, the source node can look up their cache for other possible routes to the destination. If an alternative route is found, the source node uses that route; else the source node will initiate route discovery operations to determine possible routes to the destination. During route discovery operation, the source node floods the network with query packets. Only the destination or a node which already knows the route to destination can reply to it, hence avoiding the further propagation of query packets from it. If a broken link is detected by a node, it sends route error messages to the source node. The source node on receiving error messages will initiate route discovery operations. Unlike DSDV, there are no periodically triggered route updates. Ad Hoc On-Demand Distance Vector (AODV) routing protocol shares DSR’s on demand characteristics in that it also discovers routes on an “as needed’’ basis via a similar route discovery process. However, AODV adopts different mechanism to maintain routing information. It uses traditional DSDV routing tables, with one entry per destination. AODV uses sequence numbers maintained at each destination to determine whether the routing information is latest and up to date and to prevent looping of packets across routes. Just like DSDV, during route discovery AODV floods broadcast route request packets to its neighboring nodes. Each route request contains the source node id, the destination node id, the sequence numbers of the source and the destination, the hop count and the broadcast id. Every time a route discovery operation is initiated, the source sequence number is incremented. AODV depends on sequence numbers to avoid count to infinity problem. Like DSR, a response message is generated once the request packet reaches the destination or a node which knows the route to the destination. This response message contains the latest route information from the source to the destination. AODV also has a feature called "precursor list" maintained by every node. It contains the list of neighbor nodes that are most likely to use the current node for routing packets. Routing table entry of every node contains a list of predecessor nodes that most likely to use that entry to route data packets. This becomes essential when a broken link is encountered. On encountering such broken links, all the predecessor nodes will be notified with route error messages. DYMO(Dynamic MANET On Demand) routing protocol has been proposed by Perkins & Chakeres as advancement to the existing AODV protocol. It is also defined to as successor of AODV and keeps on updating till date. DYMO operates similar to its predecessor i.e. AODV and does not add any extra modifications to the existing functionality but operation is moreover quite simpler. DYMO is a purely reactive protocol in which routes are computed on demand i.e. as and when required. Unlike AODV, DYMO does not support unnecessary HELLO messages and operations purely based on sequence numbers assigned to all the packets. It is a reactive routing protocol that computes unicast routes on demand or when required. It employs sequence numbers to ensure loop freedom. It enables on demand, multi-hop unicast routing among the nodes in a mobile ad hoc network. The basic operations are route discovery and maintenance. Route discovery is performed at source node to a destination for which it does not have a valid path. And route maintenance is performed to avoid the existing obliterated routes from the routing table and also to reduce the packet dropping in case of any route break or node failure. Basic DYMO protocol shows in a figure. 2. Proactive Routing Protocol: Proactive routing protocols are also called as table driven routing protocols. In this every node maintain routing table which contains information about the network topology even without requiring it. This feature although useful for datagram traffic, incurs substantial signaling traffic and power consumption. The routing tables are updated periodically whenever the network topology changes. Proactive protocols are not suitable for large networks as they need to maintain node entries for each and every node in the routing table of every node. These protocols maintain different number of routing tables varying from protocol to protocol. There are various well known reactive routing protocols present in MANET for example DSDV and OLSR. Destination sequenced distance vector (DSDV) routing protocol is table driven protocol based on the Distributed Bellman Ford Algorithm. In DSDV, each node maintains a routing table which contains an entry for destination node in the network. The routing table contains entries such as the next hop address, metric or the number of hop counts, and the sequence number. Sequence numbers are assigned by destination node for identification of the routes. DSDV tags each route with a sequence number and considers a route X more favorable than Y if X has a greater sequence number, or if the two routes have equal sequence numbers but X has a lower metric. This was done so that the routing tables have the latest updated path. The sequence number for a route is updated every time a new route discovery is initiated. When a broken link is encountered, the sequence number is set to infinity and it is broadcasted to all the nodes so that the routing tables of the node containing the broken link can be updated to infinity and the link is discarded. The sequence number of every route is assigned by the destination and it is incremented for every route discovery operation. Thus in case of mobile ad-hoc networks, the sequence numbers enable DSDV to maintain up to date routing information at the nodes ensuring the consistency of routing data across all routing tables. Both periodic and triggered route updates are initiated by DSDV to maintain consistency of routing information. In case of periodic updates, fresh route discovery operations are initiated after the elapse of fixed interval of time. Triggered route updates are initiated whenever a node encounters a broken link which can be a result of sudden network topology change or communication link failure. Optimized Link State Routing Protocol (OLSR) is an IP routing protocol optimized for mobile ad hoc networks, which can also be used on other wireless ad hoc networks. OLSR is a proactive link- state routing protocol, which uses hello and topology control (TC) messages to discover and then disseminate link state information throughout the mobile ad hoc network. Individual nodes use this topology information to compute next hop destinations for all nodes in the network using shortest hop forwarding paths. Link-state routing protocols such as Open Shortest Path First (OSPF) and ISIS elect a designated router on every link to perform flooding of topology information. In wireless ad hoc networks, there is different notion of a link, packets can and do go out the same interface; hence, a different approach is needed in order to optimize the flooding process. Using Hello messages the OLSR protocol at each node discovers 2-hop neighbor information and performs a distributed election of a set of multipoint relays (MPRs). Nodes select MPRs such that there exists a path to each of its 2-hop neighbors via a node selected as an MPR. These MPR nodes then source and forward TC messages that contain the MPR selectors. This functioning of MPRs makes OLSR unique from other link state routing protocols in a few different ways: The forwarding path for TC messages is not shared among all nodes but varies depending on the source, only a subset of nodes source link state information, not all links of a node are advertised but only those that represent MPR selections. Since link-state routing requires the topology database to be synchronized across the network, OSPF and IS-IS perform topology flooding using a reliable algorithm. Such an algorithm is very difficult to design for ad hoc wireless networks, so OLSR doesn't bother with reliability; it simply floods topology data often enough to make sure that the database does not remain unsynchronized for extended periods of time. Proactive protocols also has various advantages and disadvantages, being table driven protocols they increase the control messages in the network due which message overhead in the network increases .But at the same time due to routing information already present latency is reduced in the network. Proactive approaches also suffer from either out of date states or flooding of periodic updates. IV. Parametric comparison Parameters Routing philosophy Routing scheme Routing overhead Latency Scalability level Availability of routing information Periodic updates Storage capacity Mobility support Reactive Protocol Flat On demand Low High due to flooding Not suitable for large network Available when required Proactive Protocol Flat/Hierarchical Table driven High Low due to routing tables Low Not needed as route available On demand Low generally Depends upon the number of routes Route maintenance Yes. Whenever the topology of the network changes High ,due to the routing tables Always available stored in tables Periodical updates V. Conclusion Wireless mobile ad-hoc network has very enterprising applications in today’s world. With fast growing technology mobile laptop computers and wireless hardware costs are becoming very affordable. There is increasing use of wireless devises. The field of mobile ad-hoc networks is very vast and there are various challenges that need to be met, so these networks are going to have widespread use in the future. Reactive and Proactive protocols are active research area in the field of ad-hoc mobile network. There are still lots of simulations to be done in this promising field. VI. Future Work: In future, we intend to design an optimized protocol, for a specific area of application e.g. for battlefield a protocol could be designed with basic MANET needs, and Maximum life time data gathering approach, customized for AODV routing or OLSR routing. References: [1] Robinpreet Kaur & Mritunjay Kumar Rai. “A Novel Review on Routing Protocols in MANETs”. Undergraduate Academic Research Journal (UARJ), ISSN: 227 –1129, Volume-1, Issue-1,2012. [2] Charles E.Perkins and Elizabeth M. Royer, “Ad hoc on demand distance vector (AODV) routing (Internet-Draft)”,Aug-1998. [3] Tarek Sheltami and Hussein Mouftah “Comparative study of on demand and Cluster Based Routing protocols in MANETs”, IEEE conference, pp. 291-295, 2003. [4] Krishna Gorantala , “Routing Protocols in Mobile Ad-hoc Networks”, A Master’ thesis in computer science, pp-1-36, 2006. [5] Anuj K. Gupta, Harsh Sadawarti and Anil K.Verma. “IMPLEMENTATION OF DYMO ROUTING PROTOCOL”. International Journal of Information Technology, Modeling and Computing (IJITMC) Vol.1, No.2, May 2013 [6] Anuj K. Gupta, Harsh Sadawarti, Anil K. Verma, “Review of various Routing Protocols forMANETs”, International Journal of Information & Electronics Engineering (IJIEE), ISSN: 1109- 2742, Article No. 40, 1(3): 251-259, November 2011. [7] Williams Su, Sung-Ju Lee and Mario Gerla, “Mobility prediction and routing in ad hoc wireless networks”, International journal of network management, 2001; 11:3-30 [8] Padmini Misra, “Routing Protocols for ad hoc mobile wireless Networks”, http://www.cse.ohio-state.edu /~jain/cis78899/ftp/adhoc_routing/#TDRP, Nov-1999. [9] Gurpreet Singh Saini, Priyanka Dubey, Md Tanzilur Rahman. Review Study For InterOperability Of ManetProtocols In Wireless Sensor Networks. International Journal of Computer Trends and Technology (IJCTT) – volume 4 Issue 6–May 2013 ISSN: 2231 [10] Elizabeth M. Royer “A Review of Current Routing Protocols for Ad Hoc Mobile Wireless Networks” University of California, Santa Barbara Chai-Keong Toh, Georgia Institute of Technology, IEEE Personal Communications, pp. 46-55, April 1999. [11] Abdellah Jameli, Najib Naja and Driss ElOuadgiri “Comparative Analysis of Ad Hoc Networks Routing Protocols For Multimedia Streaming”, IEEE, 1999. [12] T.G.Basavaraju and Subir Kumar Sarkar, “Ad-hoc Mobile Wireless Networks: Principles,Protocols and Applications ”, Auerbach Publications, 2008. [13] Anuj K. Gupta, Harsh Sadawarti, Anil K. Verma, “Performance Analysis of MANET Routing Protocols in Different Mobility Models”, International Journal of Information Technology and Computer Science (IJITCS), ISSN: 2074-9015, 5(6): 73-82, May 2013. [14] A. Boukerche, B. Turgut, N. Aydin, M. Z. Ahmad, L. Bölöni, and D.Turgut, “Routing protocols in ad hoc networks: A survey,” “Elsevier Computer Networks”, 55 (2011) 3032 - 3080. [15] Shailender Gupta, Chirag Kumar, Seema Rani and Bharat Bhushan, “Performance comparison of routing protocols using different mobility models”, IJMECS, vol. 4, no. 8, pp. 54-61, 2012.