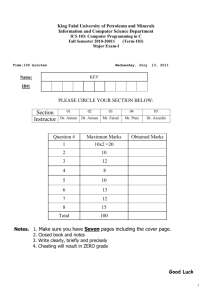
Tool
advertisement

LE VIGNAN UNIVERSITY::VADLAMUDI
DEPARTMENT OF CSE
LAB MANUAL
INFORMATION SECURITY LAB (COURSE CODE: CS417)
FACULTY NAME: Jyostna devi Bodapati
Lab.
S.no
Topic
no
Page
No.
1. Write program for Ceaser cipher encryption and decryption
1
2
3
Lab-1
2. Write program for Mono alphabetic cipher encryption and
decryption
LAB-2
1. Implementation of Play Fair cipher
2.Implementation of Vigenere cipher (Polyalphabetic substitution)
LAB-3
1. Implementation of Hill cipher
2. Implementation of Rail Fence cipher
1. Implementation of S-DES algorithm for data encryption
4
LAB-4
2. Implement RSA asymmetric (public key and private key)Encryption.
1. Generate digital signature using Hash code
5
LAB-5
2. Generate digital signature using MAC code
1. Implement the hash code using MD5
6
7
8
9
LAB-6
2. Implement the hash code using SHA-1
LAB-7
Ethereal Tool ( Wire Shark )
LAB-8
NMAP Tool
LAB-9
PGP- Thunder Bird
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
1
LAB-1: Session1
AIM: Write a program for Ceaser cipher encryption and decryption using files
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++/Java
Procedure:
Algorithm Encryption:
1. Open a file which contains the plain text in read mode
2. Create a new file to which the cipher to be written.
3. Read one by one character of file-1 and call encrypt function write the cipher character in
file2.
4. Close the files.
Algorithm Decryption:
1. Open a file which contains the cipher text in read mode
2. Read one by one character of file and call decrypt function
3. Close the file.
Note: Use an integer digit from 1-26 key. The same key is used for Encryption and Decryption.
Encrypt function:
Read the key
if character is between A to Z .
code = character + key;
cipher_character = to_char(code);
Decryption function:
if character is between A to Z .
code= character – key;
code=code+26;
original_character = to_char(code);
Example:
Key = 3
Replace ABCDEFGHI………………………………..WXYZ with
CDEFGHI………………………………..WXYZAB respectively.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
2
In Encryption replace A with C , B with D and so on.
If we consider plain text : Vignan
The cipher is
:Ykiqcq
Implementation:
//Ceaser Cipher
#include<stdio.h>
#include<conio.h>
FILE *source,*dest;
void encrypt();
void decrypt();
void main()
{
int choice;
int k;
printf("Enter Key from 1-26");
scanf("%d",&k);
do
{
clrscr();
printf("\n\n\t\tCeaser Cipher\n\nEnter your chice:\n");
printf("1.Encryption\n2.Decryption\n3.Exit.\n\nYour Choice:");
scanf("%d",&choice);
switch(choice)
{
case 1:encrypt(k);
break;
case 2:decrypt(k);
break;
default:exit(0);
}
getch();
}while(choice);
}
void encrypt(int k)
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
3
{
char fname[15],ch;
int n;
printf("\n\nEnter the name of file to be encrypted:\n");
flushall();
gets(fname);
flushall();
source = fopen(fname,"r");
dest = fopen("Dest.txt","w");
while ((ch=getc(source))!=EOF)
{
n=((toupper(ch)-65)+k)% 26;
ch=(char)(n+65);
putc(ch,dest);
}
fclose(dest);
fclose(source);
printf("\n\nThe file has been encrypted...\n\nThe contents are:\n");
dest=fopen("Dest.txt","r");
while((ch=getc(dest))!=EOF)
printf("%c",ch);
}
void decrypt(int k)
{
char fname[15],ch;
int i,n;
printf("\n\nEnter the name of file to be decrypted:\n");
flushall();
gets(fname);
flushall();
dest = fopen(fname,"r");
printf("\nDecrypted contents are : ");
while ((ch=getc(dest))!=EOF)
{
n=(toupper(ch)-65)-k;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
4
if(n<0)
{
n=n+26;
}
n=n%26;
ch=(char)(n+65);
putchar(ch);
}
fclose(source);
}
Sample Output:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
5
LAB-1:Session2
AIM: Write program for Mono alphabetic cipher encryption and decryption using files
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
Algorithm Encryption:
1. Open a file which contains the plain text in read mode
2. Create a new file to which the cipher to be written.
3. Read one by one character of file-1 and call encrypt function write the cipher character in
file2.
4. Close the files.
Algorithm Decryption:
1. Open a file which contains the cipher text in read mode
2. Read one by one character of file and call decrypt function
3. Close the file.
Note: Use a 26 letter key. The same key is used for Encryption and Decryption
Encrypt function:
Read the key
if character is between A to Z .
code = Ascii(character) + key; /* key = value between 1 to 25.
if code>ascii(Z)
code=code-26;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
6
cipher_character = to_char(code);
Decryption function:
if character is between A to Z .
code= Ascii(character) – key;
if code<ascii(A)
code=code+26;
original_character = to_char(code);
Example:
In this case we will use the character string as Key instead of integer value
Key = {'z','y','x','w','v','u','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t'};
Replace ABCDEFGHI………………………………..WXYZ with
'z','y','x','w','v','u','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t'
In Encryption replace A with Z , B with Y and so on.
If we consider plain text : Vignan
The cipher is
:pcahzh
Implementation:
//Monalphabetic Cipher
#include<stdio.h>
#include<conio.h>
FILE *source,*dest;
void encrypt();
void decrypt();
void main()
{
int choice;
char k[26]={'z','y','x','w','v','u','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t'};
do
{
clrscr();
printf("\n\n\t\tMonoalphabetic Cipher\n\nEnter your chice:\n");
printf("1.Encryption\n2.Decryption\n3.Exit.\n\nYour Choice:");
scanf("%d",&choice);
switch(choice)
{
case 1:encrypt(k);
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
7
break;
case 2:decrypt(k);
break;
default:exit(0);
}
getch();
}while(choice);
}
void encrypt(char k[26])
{
char fname[15],ch;
int i,n;
printf("\n\nEnter the name of file to be encrypted:\n");
flushall();
gets(fname);
flushall();
source = fopen(fname,"r");
dest = fopen("Dest.txt","w");
i=0;
while ((ch=getc(source))!=EOF)
{
n=(int)ch-97;
putc(k[n],dest);
}
fclose(dest);
fclose(source);
printf("\n\nThe file has been encrypted...\n\nThe contents are:\n");
dest=fopen("Dest.txt","r");
while((ch=getc(dest))!=EOF)
printf("%c",ch);
}
void decrypt(char k[26])
{
char fname[15],ch;
int i,n;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
8
printf("\n\nEnter the name of file to be decrypted:\n");
flushall();
gets(fname);
flushall();
dest = fopen(fname,"r");
printf("\nDecrypted contents are : ");
while ((ch=getc(dest))!=EOF)
{
for (i=0;ch!=k[i];i++);
putchar(97+i);
}
fclose(source);
}
Sample Output:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
9
LAB-2 Session1
AIM: Implementation of Play Fair Cipher Encryption
Objective: To provide confidentiality to the message and protect the message against attacks
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
10
Packages: Turbo/Borland/GNU - C/C++
Analyzing the Problem:
By analyzing the problem it is found that two basic steps are required for implementing the data
encryption using Play Fair cipher
1) Generate Key matrix
2) Encrypt the data using encryption rule and key matrix
Step1: Generating Key matrix
To Generate the key matrix take any random key of any length and form a 5X5 matrix.
Go on filling the rows of the matrix with the key characters (if repeating character occurs then
ignore it). Fill the remaining matrix with alphabets from A to Z (except those already occurred in
the key). For example for the key “monarchy” we have the matrix as follow
M
O
N
A
R
C
H
Y
B
D
E
F
G
I/J
K
L
P
Q
S
T
U
V
W
Y
Z
Step 2: Encrypt the data using encryption rule and key matrix
To Encrypt the data take two characters at time from plain text file and encrypt it using one of
the following rules.
Encryption rules
1) Repeating plain text letters that would fall in the same pair are separated with filler letter, such
as x.( i.e. Balloon becomes Ba, lx, lo, on)
2) If both the characters are in the same raw then replace each with the character to its right, with
the last character followed by the first, in the matrix.
3) If both the characters are in the same column then replace each with the character below it,
with the bottom character followed by the top, in the matrix.
4) Otherwise each plain text letter is replaced by the letter that lies in its own row and the column
occupied by the other plain text letter
Example: Using key as “monarchy” we have
- Encryption of AR as RM
- Encryption of MU as CM
- Encryption of BP as IM
Designing the Solution:
For this solution we have to implement the following functions given below.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
11
1) Input function for key & Plain Text.
2) Matrix generation.
3) Encryption function for generating Cipher Text.
4) Print function for printing Cipher Text Output.
Implementation:
/*PLAY FAIR CIPHER*/
#include <stdio.h>
#define siz 5
void playfair(char ch1,char ch2, char mat[siz][siz])
{
int j,m,n,p,q,c,k;
for(j=0,c=0;(c<2)||(j<siz);j++)
for(k=0;k<siz;k++)
if(mat[j][k] == ch1)
m=j,n=k,c++;
else if(mat[j][k] == ch2)
p=j,q=k,c++;
if(m==p)
{
n++; q++;
if(n==siz)
n=0;
if(q==siz)
q=0;
printf("%c%c",mat[m][n],mat[p][q]);
}
else if(n==q)
{
m++; p++;
if(m==siz)
m=0;
if(q==siz)
p=0;
printf("%c%c",mat[m][n],mat[p][q]);
}
else
{
printf("%c%c",mat[m][q],mat[p][n]);
}
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
12
}
void main()
{
char mat[siz][siz],key[20],str[25]={0};
int m,n,i,j;
char temp;
printf("Enter Key String:");
gets(key);
printf("Enter Plain text");
gets(str);
m=n=0;
for(i=0;key[i]!='\0';i++)
{
for(j=0;j<i;j++)
if(key[j] == key[i]) break;
if(key[i]=='j') key[i]='i';
if(j>=i)
{
mat[m][n++] = key[i];
if(n==siz)
n=0,m++;
}
}
for(i=97;i<=122;i++)
{
for(j=0;key[j]!='\0';j++)
if(key[j] == i)
break;
else if(i=='j')
break;
if(key[j]=='\0')
{
mat[m][n++] = i;
if(n==siz) n=0,m++;
}
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
13
}
printf("\n\nMatrix :\n");
for(i=0;i<siz;i++)
{
for(j=0;j<siz;j++)
printf("%c\t",mat[i][j]);
printf("\n");
}
printf("\n\nEntered text :%s\nCipher Text :",str);
for(i=0;str[i]!='\0';i++)
{
temp = str[i++];
if(temp == 'j') temp='i';
if(str[i]=='\0')
playfair(temp,'x',mat);
else
{
if(str[i]=='j') str[i]='i';
if(temp == str[i])
{
playfair(temp,'x',mat);
i--;
}
else
playfair(temp,str[i],mat);
}
}
}
Sample Output:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
14
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
15
LAB-2:Session2
AIM: Implementation of Vigenere cipher (Polyalphabetic substitution)
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
Algorithm Encryption:
1. Open a file which contains the plain text in read mode
2. Create a new file to which the cipher to be written.
3. Read one by one character of file-1 and call encrypt function write the cipher character in
file2.
4. Close the files.
Algorithm Decryption:
1. Open a file which contains the cipher text in read mode
2. Read one by one character of file and call decrypt function
3. Close the file.
Note: Use a string as a key. The same key is used for Encryption and Decryption
Encrypt function:
Read the key
J=0
code = Ascii(character) + key[j]; /* key[j] is the jth char of the key.
Code=code%26
cipher_character = to_char(code);
j=(j+1)%key_len;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
16
Decryption function:
Read the key
J=0
code = Ascii(character) - key[j]; /* key[j] is the jth char of the key.
Code=code%26
cipher_character = to_char(code);
j=(j+1)%key_len;
Example:
In this case we will use the character string as Key instead of integer value
Key = cse
If we consider plain text : VIGNAN
The cipher is
: XAKPSR
You can use the following table for reference
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
17
Implementation:
#include <stdio.h>
#include <ctype.h>
#include <string.h>
#include<stdlib.h>
void encrypt(char key[]);
void decrypt(char key[]);
FILE *source, *dest;
void main()
{
int choice;
char key[26];
printf("Enter Encryption Key [Max. 32 Characters/ only aphabets]: ");
gets(key);
while(1)
{
printf("\n1. Encrypt Text\n");
printf("2. Decrypt Text\n");
printf("3. Exit\n");
printf("Enter Your Choice : ");
scanf("%d",&choice);
fflush(stdin);
if(choice == 3)
exit(0);
else if(choice == 1)
encrypt(key);
else if(choice == 2)
decrypt(key);
else
printf("Please Enter Valid Option.");
}
}
void encrypt(char key[26])
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
18
{
char fname[15],ch;
int n,j;
printf("\n\nEnter the name of file to be encrypted:\n");
flushall();
gets(fname);
flushall();
source = fopen(fname,"r");
dest = fopen("Dest.txt","w");
j=0;
while ((ch=fgetc(source))!=EOF)
{
ch=(char)(65+(((toupper(ch)-65)+(toupper(key[j])-65))%26));
putc(ch,dest);
j++;
j=j%strlen(key);
}
fclose(dest);
fclose(source);
printf("\n\nThe file has been encrypted...\n\nThe contents are:\n");
dest=fopen("Dest.txt","r");
while((ch=getc(dest))!=EOF)
printf("%c",ch);
}
void decrypt(char key[26])
{
char fname[15],ch;
int i,j,n,value;
printf("\n\nEnter the name of file to be decrypted:\n");
flushall();
gets(fname);
flushall();
dest = fopen(fname,"r");
printf("\nDecrypted contents are : ");
j=0;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
19
while ((ch=getc(dest))!=EOF)
{
value = (toupper(ch)-64)-(toupper(key[j])-64);
if( value < 0)
{
value = 26 + value;
}
printf("%c",65 + (value % 26));
j++;
j=j%strlen(key);
}
fclose(source);
}
Sample Experimental results:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
20
LAB-3:Session1
AIM: Implementation of encryption and decryption using Hill cipher
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
21
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
Algorithm Encryption:
1. Read plain text
2. Read the key 2*2 matrix
3. Divide the plain text into pairs
4. Replace each letter by the number corresponding to its position in the alphabet i.e. A=1, B=2,
C=3…Z=0. See Table A below for quick reference.
5. Multiply pair of letters with key
6. Repeat steps 3,4 till the end of the string
Algorithm Decryption:
1. Take cipher text as input
2. Read the key 2*2 matrix
3. Find the Inverse of the key
4. Divide the cipher text into pairs
5. Replace each letter by the number corresponding to its position in the alphabet i.e. A=1, B=2,
C=3…Z=0. See Table A below for quick reference.
6. Multiply the pair of letters, key inverse
7. Repeat steps 3,4 till the end of the string
Note: Use a 2*2 matrix as a key. The same key is used for Encryption and Decryption
Example:
1. In this example, we will encipher the message friday.
2. Key is
7 8
9 3
3. Group the plaintext into pairs. If you have an odd number of letters, repeat the last letter.
FR
ID
AY
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
22
4. Replace each letter by the number corresponding to its position in the alphabet i.e. A=1, B=2,
C=3…Z=0. See Table A below for quick reference.
Now the pair of letters are:
4 17
83
0 23
5. Cipher text : pqcfkv
Implementation:
#include<stdio.h>
#include<conio.h>
#include<string.h>
void main()
{
char aa[26]="abcdefghijklmnopqrstuvwxyz";
char pt[10];
int m,d,q=0,i,j,k[2][2],p[4],pp[4],t[5];
int k1[2][2],k2[2][2],det;
clrscr();
printf("enter the plaintext:" );
scanf("%s",&pt);
m=strlen(pt);
puts(pt);
/*printf("enter the numbers:");
for(i=0;i<2;i++)
{
for(j=0;j<2;j++)
{
scanf("%d",&k[i][j]);
}
} */
k[0][0]=7;
k[0][1]=8;
k[1][0]=19;
k[1][1]=3;
for(i=0;i<m;i++)
{
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
23
for(j=0;j<26;j++)
{
if(pt[i]==aa[j])
{
t[q]=j;
printf("%d\t",t[q]);
q++;
break;
}
}
}
p[0]=((k[0][0]*t[0])+(k[0][1]*t[1]))%26;
p[1]=((k[1][0]*t[0])+(k[1][1]*t[1]))%26;
p[2]=((k[0][0]*t[2])+(k[0][1]*t[3]))%26;
p[3]=((k[1][0]*t[2])+(k[1][1]*t[3]))%26;
k1[0][0]=k[1][1];
k1[0][1]=-(k[0][1]);
k1[1][0]=-(k[1][0]);
k1[1][1]=k[0][0];
printf("\nThe encrypted text :");
for(i=0;i<m;i++)
{
printf("%c\t",aa[p[i]]);
}
det=(abs((k1[0][0]*k1[1][1])-(k1[0][1]*k1[1][0])))%26;
for(i=0;i<26;i++)
{
if((det*i)%26==1)
{
d=i;
break;
}
}
printf("\n%d",d);
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
24
for(i=0;i<2;i++)
{
for(j=0;j<2;j++)
{
k2[i][j]=((d*k1[i][j]));
printf("%d\t",k2[i][j]);
}
printf("\n");
}
printf("Inverse Key is\n")
for(i=0;i<2;i++)
{
for(j=0;j<2;j++)
{
if(k2[i][j]<0)
k2[i][j]+=26;
printf("%d\t",k2[i][j]);
}
printf("\n");
}
pp[0]=abs(((k2[0][0]*p[0])+(k2[0][1]*p[1])))%26;
pp[1]=abs(((k2[1][0]*p[0])+(k2[1][1]*p[1])))%26;
pp[2]=abs(((k2[0][0]*p[2])+(k2[0][1]*p[3])))%26;
pp[3]=abs(((k2[1][0]*p[2])+(k2[1][1]*p[3])))%26;
for(i=0;i<m;i++)
{
printf("\nThe decrypted plain text :%c",aa[pp[i]]);
}
getch();
}
Sample Outputs:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
25
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
26
LAB-3:Session2
AIM: Implementation of encryption and decryption using railfence cipher
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
Rail Fence cipher is a Transposition cipher. Encryption is the result by changing the position of
the message. In this particular scheme the message is written in two rows. That is the first
character is written in the first row, second character is written in the second row and so on. To
get the cipher read the message off, row by row, first row followed by second row.
Algorithm Encryption:
1. Read plain text
2. Consider CT as a temporary string to which cipher is copied
3. Copy all the even indexed letters of the plain text to CT
4. Copy all the odd indexed letters of the plain text to CT
5. CT contains the cipher
Algorithm Decryption:
1. Read cipher text, CT
2. Consider PT as a temporary string to which plain text is copied
3. k=strlen(CT)/2
4. i=0,j=0;
5. PT[i]=CT[i]
6. PT[i+1]=CT[k]
7. i++,j++,k++
8. Repeat steps 5,6,7 till the end of the char is reached in CT
9. PT contains the plain text derived based on cipher
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
27
Example:
If we consider plain text : VIGNANUNIVERSITY
Intermediate text representation is:
VGAUIEST
INNNVRIY
The cipher is
:VGAUIESTINNNVRIY
The plain text
: VIGNANUNIVERSITY
Implementation:
#include<stdio.h>
#include<conio.h>
#include<string.h>
void main()
{
int i,j,k,l;
char a[20],c[20],d[20];
clrscr();
printf("\nEnter the input string : ");
scanf("%s",&a);
l=strlen(a);
for(i=0,j=0;i<l;i++)
{
if(i%2==0)
{
c[j]=a[i];
printf("%c ",c[j]);
j++;
}
}
printf("\n");
for(i=0;i<l;i++)
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
28
{
if(i%2==1)
{
c[j]=a[i];
printf("%c ",c[j]);
j++;
}
}
c[j]='\0';
printf("\nCipher text after applying rail fence :");
printf("\n%s",c);
/*Deciphering*/
if(l%2==0)
k=l/2;
else
k=(l/2)+1;
for(i=0,j=0;i<k;i++)
{
d[j]=c[i];
j=j+2;
}
for(i=k,j=1;i<l;i++)
{
d[j]=c[i];
j=j+2;
}
d[l]='\0';
printf("\nText after decryption : ");
printf("%s",d);
getch();
}
Sample Outputs:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
29
LAB-4: Session1
AIM: Implementation of encryption and decryption using S-DES algorithm.
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks. S-DES is a Symmetric key encryption algorithm.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
30
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
S-DES is a simplified version of DES. S-DES algorithm is used for the academic purpose. SDES uses bit wise operation on message letters to encrypt the data so it is more powerful against
the cryptanalysis attacks. This algorithm takes 8-bit of the message as input, also takes 10 bit key
and produces 8 bit cipher text. This algorithm has two rounds. It generates 2, 8-bit keys that are
to be used in each round. Following figure shows the functional details of S-DES.
Design:
Algorithm to generate key:
As there are two rounds we have to generate two keys from the given 10-bit key
1: Apply permutation function P10 on 10 bit key
2: Divide the result into two parts each containing 5-bit, call them L0 and L1
3: Apply one bit Circular Left Shift on both L0 and L1
4: L0 and L1 together will form out 10-bit number
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
31
5: Apply permutation function P8 on result to select 8 out of 10 bits for key K1 (for the
first round)
6: Again apply two bit Circular Left Shift to L0 and L1
7: Combine the result, which will form out 10-bit number
8: Apply permutation function P8 on result to select 8 out of 10 bits for key K2 (for the
second round)
Algorithm for Encryption:
1: Get 8 bit message text (M) apply Initial permutation function (IP)
2: Divide IP(M) into nibbles L0 and R0
3: Apply function Fk on L0
4: XOR the result with R0 ( That is R0 (+) Fk(L0))
5: Swap the result with RO
6: Repeat the step 1 to 5 for the second round
7:Apply (IP-1) on the result to get the encrypted data
Algorithm for function Fk:
1: Give the 4-bit input to EP (Expansion function) the result will be a 8-bit expanded data
2: XOR the 8-bit expanded data with 8-bit key (K1 for the first round and K2 for the
second round)
2: Divide result into upper (P1) and lower (P2) nibble
3: Apply compression function S0 to P0 and S1 to P1, which will compress the 4-bit input
to 2-bit output
4: Combine 2-bit output from S0 and S1 to form a 4-bit digit
5: Apply permutation function P4 to 4-bit result
Functions used in S-DES:
P10 = 3 5 2 7 4 10 1 9 8 6
P8 = 6 3 7 4 8 5 10 9
P4 = 2 4 3 1
IP = 2 6 3 1 4 8 5 7
IP-1 = 4 1 3 5 7 2 8 6
EP = 4 1 2 3 2 3 4 1
S0:
1032
3210
0213
3132
S1:
0123
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
32
2013
3010
2103
Example:
Plain text: 10001011
Key: 0000011011
Key1:11100100
Key2:01011100
Cipher Text: 11110001
Plain Text: 10001011
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
33
Implementation:
#include <stdio.h>
int l[4],r[4],keys[2][8],ct[8];
void sbox(int sip[],int p[],int sbno,int i)
{
int sbox[2][4][4]={1,0,3,2,3,2,1,0,0,2,1,3,3,1,3,2,0,1,2,3,2,0,1,3,3,0,1,0,2,1,0,3};
int rw,c,sop;
rw = sip[3]+sip[0]*2;
c = sip[2]+sip[1]*2;
sop = sbox[sbno][rw][c]; //sop gives decimal value of S-Box Output
for(;sop!=0;sop/=2)
p[i--]=sop%2;
}
void cmp_fun(int round)
{
int EP[]={4,1,2,3,2,3,4,1},i,epd[8];
int slip[4],srip[4];
int p[4]={0},p4[]={2,4,3,1},np[4];
for(i=0;i<8;i++) // E/P Permutation
epd[i]=r[EP[i]-1];
for(i=0;i<8;i++)//Performing XOR with Key
if(i<4)
slip[i] = epd[i]^keys[round][i]; // Using Key _ 1=>0
else
srip[i-4] = epd[i]^keys[round][i];
sbox(slip,p,0,1);//Calling SBox 1, 0->SBOX 1
sbox(srip,p,1,3);//Calling SBox 1, 1->SBOX 2
for(i=0;i<4;i++) //P4 permutation
np[i]=p[p4[i]-1];
for(i=0;i<4;i++)
l[i] = l[i]^np[i];
}
void left_shift(int keyip[],int nob)
{
int t1,t2,i;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
34
while(nob>0)
{
t1=keyip[0],t2=keyip[5];
for(i=0;i<9;i++)
if(i<4)
keyip[i] =keyip[i+1];
else if(i>4)
keyip[i] = keyip[i+1];
keyip[4]=t1,keyip[9]=t2;
nob--;
}
}
void gen_keys()
{
int key[10],i,keyip[10];
int p10[]={3,5,2,7,4,10,1,9,8,6},p8[]={6,3,7,4,8,5,10,9};
printf("Enter Key :");
for(i=0;i<10;i++)
scanf("%d", &key[i]);
for(i=0;i<10;i++) // Permutation P10
keyip[i] = key[p10[i]-1];
left_shift(keyip,1);
// Left Shifting (Array,No of bts)
printf("\nKey1 :");
for(i=0;i<8;i++){
//Permuting P8 on key1
keys[0][i] = keyip[p8[i]-1];// Key1 Generated!!
printf("%d",keys[0][i]);
}
left_shift(keyip,2);// Generating Key2 . .
printf("\nKey2 :");
for(i=0;i<8;i++){
keys[1][i] = keyip[p8[i]-1];// Key2 Generated!!
printf("%d",keys[1][i]);
}
}
void En_De(int pt[],int c)
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
35
{
int ip[]={2,6,3,1,4,8,5,7},ipi[]={4,1,3,5,7,2,8,6},t[8],i;
for(i=0;i<8;i++)// Performing Permutation on input bits!!
if(i<4)
l[i]=pt[ip[i]-1];
else
r[i-4] = pt[ip[i]-1];
cmp_fun(c);//Round 0+1 using key 0+1
for(i=0;i<4;i++) //Swapping left & right
r[i]=l[i]+r[i],l[i]=r[i]-l[i],r[i]=r[i]-l[i];
printf("\n\n");
cmp_fun(!c); // Round 1+1 wid key1+1 wid swapped bits
for(i=0;i<8;i++)
if(i<4) t[i]=l[i];
else
t[i]=r[i-4];
for(i=0;i<8;i++)
ct[i] = t[ipi[i]-1];
}
void main()
{
int pt[8]={0},i;
printf("Enter plain text binary bits:");
for(i=0;i<8;i++)
scanf("%d",&pt[i]);
gen_keys(); // Generating Keys key1 & key2
En_De(pt,0);
printf("\nCipher Text :");
for(i=0;i<8;i++)
printf("%d",ct[i]);
En_De(ct,1);
printf("\nPlain Text (After Decrypting):");
for(i=0;i<8;i++)
printf("%d",ct[i]);
}
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
36
Sample outputs:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
37
LAB-4: Session2
AIM: Implement RSA asymmetric (public key and private key)-Encryption.
Objective: To provide confidentiality to the message and to protect the message against Release
of message contents attacks. RSA is a public key encryption algorithm.
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
It was developed by Rivest, Shamir and Adleman. This algorithm makes use of
an expression with exponentials. Plaintext is encrypted in blocks. With each block
having a binary value less than some number n. For some plaintext block M and
ciphertext block C:
e
Encryption : C = M mod n
Decryption : M = Cd mod n
Public key of KU = {e, n} and a private key of KR = {d, n}.
Algorithm:
Key generation:
Step1: Select two prime numbers, p ,q.
Step2: Calculate n = p*q
Step3: Calculate Ф(n) = (p-1)(q-1)
Step4: Select e such that e is relatively prime to Ф(n), gcd(e, Ф(n))=1 and less thanФ(n);
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
38
Step5: Determine d such that d =e -1 mod Ф(n)
Encryption:
Step1: Read Plain Text, M
Step 2: Find C= M*M mod n
Step 3: Repeat Step 2 for e times
Step 4: C contains cipher
Decryption:
Step1: Read Cipher Text, C
Step 2: Find M= C*C mod n
Step 3: Repeat Step 2 for d times
Step 4: M contains plain text
Example:
Select two prime numbers, p = 17 and q = 11.
Calculate n = p*q = 17*11 = 187
Calculate Ф(n) = (p-1)(q-1) = 16*10 = 160.
Select e such that e is relatively prime to Ф(n) = 160 and less than Ф(n); choose e = 7.
Determine d such that ed ≡ 1 mod Ф(n) and d<160. the correct value is d = 23, because 23*7 =
161 = 1 mod 160.
Consider plaintext: VIGNAN
V=22
e
ENCRYPTION : C = M mod n
C= 227 mod 187 = 14
Decryption : M = Cd mod n
M=1423 mod 187 = 22
REMAINING LETTERS ARE LEFT TO THE STUDENTS AS AN EXCERCISE
Implementation:
/* C program for the Implementation Of RSA Algorithm */
#include<stdio.h>
#include<conio.h>
int phi,M,n,e,d,C,FLAG;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
39
gcd(int a,int b)
{
int temp = 0;
while(b != 0)
{
temp = a;
a = b;
b = temp % b;
}
return a;
}
int isprime(int n)
{
int i,count=1;
for(i=2;i<n;i++)
{
if(n%i==0)
count=0;
break;
}
return count;
}
int check()
{
int i;
if((e<=1)||(e>=phi))
{
FLAG = 1;
return;
}
if(gcd(e,phi)!=1)
{
FLAG = 1;
return;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
40
}
if(isprime(e)==0)
{
FLAG = 1;
return;
}
FLAG = 0;
return;
}
void encrypt()
{
int i;
C = 1;
for(i=0;i< e;i++)
C=C*M%n;
C = C%n;
printf("\n\tEncrypted keyword : %d",C);
}
void decrypt()
{
int i;
M = 1;
for(i=0;i< d;i++)
M=M*C%n;
M = M%n;
printf("\n\tDecrypted keyword : %d",M);
}
void main()
{
int i,p,q,s;
clrscr();
printf("Enter Two Relatively Prime Numbers\t: ");
scanf("%d%d",&p,&q);
n = p*q;
phi=(p-1)*(q-1);
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
41
printf("\n\tF(n)\t= %d",phi);
do
{
printf("\n\nEnter e value\t: ");
scanf("%d",&e);
check();
}while(FLAG==1);
printf("GCD",gcd(e,phi));
d = 1;
for(i=1;i<phi;i++)
{
if((e*i)%phi==1)
{
d=i;
break;
}
}
printf("\n\tPublic Key\t: {%d,%d}",e,n);
printf("\n\tPrivate Key\t: {%d,%d}",d,n);
printf("\n\nEnter The Plain Text\t: ");
scanf("%d",&M);
encrypt();
//printf("\n\nEnter the Cipher text\t: ");
//scanf("%d",&C);
decrypt();
getch();
}
Sample outputs:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
42
LAB-5: Session1
AIM: Generate digital signature using Hash code
Objective: To provide authenticate to the message and to assure that the message is not altered
during transmission.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
43
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
Hash function is a public function that maps a message of any length into a fixed length hash
value, which serves as the authenticator.
Hash function provides digital signature. Digital
signature is the mechanism used to provide both authentication and confidentiality of the
message. Hash function is used to generate the Hash Code of the message which provides the
authentication and this Hash code is encrypted using the public key of receiver to provide
confidentiality, and at the receiver side received Hash code is decrypted and compared against
the Hash code generated from the received message.
The simple Hash function is used to generate the hash code of the message. In the simple
Hash functions if we want to generate the m byte Hash code then we divide the message in to
sub group each containing m byte and then XOR all the sub part to generate Hash code.
Algorithm:
Step 1: The message M which is divided into n sub part (M1, M2, M3, -….Mn ) each containing
m byte
Step 2: Hi = Mi; for i=0;
Step 3: Hi= Mi XOR Hi-1;
Step 4: Repeat Step3 process for n times.
Example:
Message is
111111111111111111111111111000000000000000000000000000000000000000000101010100
101010100101000101010010101010011111111111111111111111111111111111000000000000
000000000000000000000000000000101010100101010100101000101010010101010011111111
111111111111111111111111111000000000000000000000000000000000000000000101010100
101010100101000101010010101010011111111111111111111111111111111110000000000000
00000000000000000000000000000101010100101010100101000101010010101010011111111
Dividing into 64-bit blocks :
Block1 : 1111111111111111111111111110000000000000000000000000000000000000
Block2 : 0000010101010010101010010100010101001010101001111111111111111111
Block3 : 1111111111111111000000000000000000000000000000000000000000101010
Block4 : 1001010101001010001010100101010100111111111111111111111111111111
Block5 : 1111100000000000000000000000000000000000000000010101010010101010
Block6 : 0101000101010010101010011111111111111111111111111111111110000000
Block7 : 0000000000000000000000000000000000010101010010101010010100010101
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
44
Block8 : 0010101010011111111
After padding 0s to the last block to make it 64 bit block
Block8 : 0010101010011111111000000000000000000000000000000000000000000000
Intialize hash code to all 0s
Hash:
00000000000000000000000000000000000000000000000000000000000000000
Xor hash with each block to get the final hash code
Final hash code is: 00010011110101010110100001111100111111101100000001110000101001
Implementation:
//Hash code generation
#include<stdio.h>
#include<conio.h>
FILE *source,*dest;
void xor(int h1[64],int b1[64])
{
int i;
for(i=0;i<64;i++)
{
h1[i]=h1[i]^b1[i];
// printf("%d",h1[i]);
}
}
void main()
{
int choice,len,i,b1[64],h[64],k;
char fname[15],ch;
clrscr();
for(i=0;i<64;i++)
{
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
45
h[i]=0;
}
printf("\n\nEnter file name on which hash code to be generated:\n");
gets(fname);
source = fopen(fname,"r");
i=0;
k=1;
printf("\nblock1 :");
while ((ch=getc(source))!=EOF)
{
if(i==64)
{
xor(h,b1);
i=0;
k++;
printf("\nblock%d :",k);
}
b1[i]=(int)(ch-48);
printf("%d",b1[i]);
i++;
}
for(;i<64;i++)
{
b1[i]=0;
printf("%d",b1[i]);
}
xor(h,b1);
fclose(source);
printf("\n\nHASH CODE:");
for(i=0;i<64;i++)
{
printf("%d",h[i]);
}
}
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
46
Sample Output:
LAB-5: Session2
AIM: Generate digital signature using MAC code
Objective: To provide authenticate to the message and to assure that the message is not altered
during transmission.
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Procedure:
MAC stands for Message authentication code (MAC). Essentially, the MAC is
a small fixed-size block of data that is generated based on a message M of variable
length using secret key K as follows. It is also called cryptographic checksum. MAC = C
(K, M)
A simple MAC algorithm is:
Step1: Let M=(X1||X2||….Xm) be a message Where each Xi Consisting of 64 bits.
Step2: Define ∆M = X1 ^X2^ ….Xm
Step3: C(K,M)=E(K, ∆M)
Example:
Message is
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
47
111111111111111111111111111000000000000000000000000000000000000000000101010100
101010100101000101010010101010011111111111111111111111111111111111000000000000
000000000000000000000000000000101010100101010100101000101010010101010011111111
111111111111111111111111111000000000000000000000000000000000000000000101010100
101010100101000101010010101010011111111111111111111111111111111110000000000000
00000000000000000000000000000101010100101010100101000101010010101010011111111
Dividing into 64-bit blocks :
Block1 : 1111111111111111111111111110000000000000000000000000000000000000
Block2 : 0000010101010010101010010100010101001010101001111111111111111111
Block3 : 1111111111111111000000000000000000000000000000000000000000101010
Block4 : 1001010101001010001010100101010100111111111111111111111111111111
Block5 : 1111100000000000000000000000000000000000000000010101010010101010
Block6 : 0101000101010010101010011111111111111111111111111111111110000000
Block7 : 0000000000000000000000000000000000010101010010101010010100010101
Block8 : 0010101010011111111
After padding 0s to the last block to make it 64 bit block
Block8 : 0010101010011111111000000000000000000000000000000000000000000000
∆M : 00010011110101010110100001111100111111101100000001110000101001
To perform Step 3 - C(K,M)=E(K, ∆M) S-DES algorithm is used
∆M is divided into 8, 8-bit blocks and S-DES is used to produce 8-bit cipher.
If key is- 1100101011
Then C(K, ∆M) =
000000000000000000000010011010100001111110011111111110101111000101
Implementation:
//MAC code generation
#include<stdio.h>
#include<conio.h>
#include "sdes_mac.h"
FILE *source,*dest;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
48
void xor(int h1[64],int b1[64])
{
int i;
for(i=0;i<64;i++)
{
h1[i]=h1[i]^b1[i];
}
}
void main()
{
int choice,len,i,b1[64],h[64],s,k[10],j,t[8];
char fname[15],ch;
clrscr();
for(i=0;i<64;i++)
{
h[i]=0;
}
printf("\n\nEnter file name on which hash code to be generated:\n");
gets(fname);
// printf("\nEnter key of size 10 bit:\n");
// for(i=0;i<10;i++)
//scanf("%d",&k[i]);
source = fopen(fname,"r");
i=0;
s=1;
printf("\nblock1 :");
while ((ch=getc(source))!=EOF)
{
if(i==64)
{
xor(h,b1);
i=0;
s++;
printf("\nblock%d :",s);
}
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
49
b1[i]=(int)(ch-48);
printf("%d",b1[i]);
i++;
}
for(;i<64;i++)
{
b1[i]=0;
printf("%d",b1[i]);
}
xor(h,b1);
fclose(source);
gen_keys();
for(i=0;i<8;i++)
{
for(j=0;j<8;j++)
t[j]=h[i];
En_De(t,0);
for(j=0;j<8;j++)
h[i*1+j]=t[j];
}
printf("\n\nHASH CODE:");
for(i=0;i<64;i++)
{
printf("%d",h[i]);
}
}
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
50
Sample output:
LAB-6: Session1
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
51
AIM: Implement the hash code using MD5
Objective: To provide authentication to the message and to assure that the message is not altered
during transmission.
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Hash generator tool
Procedure:
Hashing is a process of generating a string (or number) with limited width from a data stream of
arbitrary length. Produced hash identifies that particular data stream while not exceeding a
certain length.
MD5 (Message Digest 5) – very popular algorithm well-known for its quality. Hash takes 16
bytes (128 bits) but is often converted to 32-character long string (simply a hexadecimal
representation of raw hash) containing Latin characters (case-insensitive) and digits.
About the tool:
Generates hashes from file upload, text or URL using various algorithms. This online tool
generates hashes using various algorithms (MD5, MD5-24, SHA1, CRC32 and more) for
either uploaded files or directly entered data.
Source for the tool:
This hash code generator tool is available online at the URL : http://i-tools.org/hash
Sample Screen shot of the hash generator:
LAB-6: Session2
AIM: Implement the hash code using SHA-1
Objective: To provide authenticate to the message and to assure that the message is not altered
during transmission.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
52
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
SHA1 (Secure Hash Algorithm 1) – a 40-character long string which strength can be compared
to that of MD5.
Procedure:
Step1: Append padding bits
Step2: Append length
Step3: Initialize MD buffer
Step4: Process message in 512-bit(16word)blocks
Step5: Output
About the tool:
Generates hashes from file upload, text or URL using various algorithms. This online tool
generates hashes using various algorithms (MD5, MD5-24, SHA1, CRC32 and more) for
either uploaded files or directly entered data.
Source for the tool:
This hash code generator tool is available online at the URL : http://i-tools.org/hash
Sample Screen shot of the hash generator:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
53
LAB-7
AIM: Working with Ethereal Tool ( Wire Shark ) for network communication
Objective: Understanding how to capture live network traffic and analyse the captured data.
Tools / Apparatus: Ethereal Tool ( Wire Shark )
Tool Download:
Download and install the Wireshark software at the following URL:
http://www.wireshark.org/download.html
About the tool:
Wireshark is a network protocol analyzer. It is first released in 1998 by Gerald Combs as
Ethereal. It is a Open source and free software and a graphical alternative to tcpdump. It is a
Powerful tool for network troubleshooting, Sniffs and captures live traffic, Filters data for ease of
analysis, Statistics and graphs available.
Wireshark GUI Main Window:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
54
Capturing Live Network Data using WireShark:
To capture:
Go to Capture menu and select Interfaces...Start capturing on interface that has IP
address.
Once the capturing starts,until the data is exchanged on Network Interface Card
(NIC),main window will be blank.
When packets exchanged on NIC, the packets will be dumped to main window
Capturing can be stopped by clicking on “Stop the running capture” button on the main
toolbar
STEP1: Go to Capture menu and select Interfaces...Start capturing on interface that has IP
address.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
55
STEP2: Once the capturing starts,until the data is exchanged on Network Interface Card
(NIC),main window will be blank.
STEP3: When packets exchanged on NIC, the packets will be dumped to main window
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
56
Step 4: Capturing can be stopped by clicking on “Stop the running capture” button on the main
toolbar
Filtering while capturing network Data using WireShark:
Filter by entering the “protocol name or field name” (Ex: http) and click the apply button in the
filter menu. Detailed filters can be applied by creating expressions
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
57
Protocol Analysis with Wireshark :
Using Wireshark tool Packets/protocols can be analyzed after capturing. Individual fields
in protocols can be easily seen. Graphs and flow diagrams can be helpful in analysis. Analysis is
performed manually. Example shows TCP segment with SYNand ACKfields set to 0.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
58
LAB-8
AIM: Working with NMAP Tool for network scanning
Objective: Understanding how to capture live network traffic and analyse the captured data.
Tools / Apparatus: NMAP Tool ( Zenmap)
Tool Download:
Download and install the Wireshark software at the following URL:
http://nmap.org/download.html
About the tool:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
59
Nmap (Network Mapper) is a security scanner used to discover hosts and services on a
computer network, thus creating a "map" of the network. To accomplish its goal, Nmap sends
specially crafted packets to the target host and then analyzes the responses. Unlike many simple
port scanners that just send packets at some predefined constant rate, Nmap accounts for the
network conditions (latency fluctuations, network congestion, the target interference with the
scan) during the run. Zenmap is the official Nmap Security Scanner GUI.
Zenmap GUI main window :
Begin Zenmap by typing zenmap in a terminal or by clicking the Zenmap icon in the desktop
environment. The main window, is as shown below.
Scanning:
Running a scan is as simple as typing the target in the “Target” field, selecting the
“Intense scan” profile, and clicking the “Scan” button. While a scan is running (and after it
completes), the output of the Nmap command is shown on the screen. Any number of targets,
separated by spaces, may be entered in the target field.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
60
Profiles:
The “Intense scan” is just one of several scan profiles that come with Zenmap. Choose a
profile by selecting it from the “Profile” combo box. Some profiles are: quick scan, common
scan, intense scan, regular scan, ping scan etc;
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
61
Scan Aggregation:
Zenmap has the ability to combine the results of many Nmap scans into one view, a
feature known as scan aggregation. When one scan is finished, you may start another in the
same window. When the second scan is finished, its results are merged with those from the first.
The collection of scans that make up an aggregated view is called a network inventory. An
example of aggregation will make the concept clearer. Let's run a quick scan against
172.168.8.14
Now do the same for www.google.com
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
62
Interpreting Scan Results:
Nmap's output is displayed during and after a scan. Zenmap's interface interpret and
aggregate the terminal output in a way that makes scan results easier to understand and use.
Each scan window contains five tabs which each display different aspects of the scan results.
They are: “Nmap Output”, “Ports / Hosts”, “Topology”, “Host Details”, and “Scans”.
The “Nmap Output” tab: The “Nmap Output” tab is displayed by default when a scan is run. The
display highlights parts of the output according to their meaning; for example, open and closed
ports are displayed in different colors.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
63
The “Ports / Hosts” tab
The “Ports / Hosts” tab's display differs depending on whether a host or a service is currently
selected. When a host is selected, it shows all the interesting ports on that host, along with
version information when available.
When a service is selected, the “Ports / Hosts” tab shows all the hosts which have that port open
or filtered.
The “Topology” tab: The “Topology” tab is an interactive view of the connections between hosts
in a network. Hosts are arranged in concentric rings. Each ring represents an additional network
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
64
hop from the center node. Clicking on a node brings it to the center. Because it shows a
representation of the network paths between hosts, the “Topology” tab benefits from the use of
the --traceroute option.
The “Host Details” tab: The “Host Details” tab breaks all the information about a single host into
a hierarchical display. Shown are the host's names and addresses, its state (up or down), and the
number and status of scanned ports. The host's uptime, operating system, OS icon and other
associated details are shown when available.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
65
The “Scans” tab
The “Scans” tab shows all the scans that are aggregated to make up the network inventory. From
this tab you can add scans (from a file or directory) and remove scans.
While a scan is executing and not yet complete, its status is “Running”. You may cancel a
running scan by clicking the “Cancel Scan” button.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
66
Sorting by Host
On the left side of Zenmap's main window is a column headed by two buttons labeled “Hosts”
and “Services”. Clicking the “Hosts” button will bring up a list of all hosts that were scanned.
Commonly this contains just a single host, but it can contain thousands in a large scan.
Host selection
The host list can be sorted by OS or host name/IP address by clicking the headers at the top of
the list. Selecting a host will cause the “Ports / Hosts” tab to display the interesting ports on that
host.
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
67
Sorting by Service:
Above the same list that contains all the scanned hosts is a button labeled “Services”. Clicking
that will change the list into a list of all ports that are open, filtered, or open|filtered on any of the
targets. (Ports that were not listed explicitly in Nmap output are not included.) The ports are
identified by service name (http, ftp, etc.). The list can be sorted by clicking the header of the list.
Service selection
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
68
LAB-9
AIM: PGP- Thunder Bird
Objective:
Tools / Apparatus: O.S.: Microsoft Windows (any) / Linux / DOS
Packages: Turbo/Borland/GNU - C/C++
Source for the tool:
http://www.mozilla.org/en-US/thunderbird/download/?product=thunderbird17.0.4&os=win&lang=en-US
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
69
Screenshot of the Main Screen of the tool:
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
70
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
71
Vignan University - Computer Science & Engineering Dept–
IV- BTECH-IISEM-Information Security LAB MANUAL
72