Unit 1 - Summative Assignment (Encryption)
advertisement

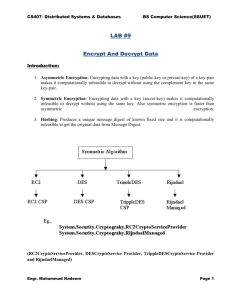
ICS4U1 – Unit 1 Java Review Name: _______________ Unit 1 - Summative Assignment (Encryption) Due Date: Tuesday Feb. 17th, 2015 Description: In this assignment, you will create a piece of encryption software that will encrypt or decrypt a given file’s text based on a primitive encryption scheme. Part of this assignment will rely on your ability to research and use the Java API. You should find the following resources useful: Java String API (for manipulating Strings): http://docs.oracle.com/javase/7/docs/api/java/lang/String.html You will be given an opportunity to approach this from a variety of difficulty levels. In other words, everyone will be able to produce some sort of encryption software. Background: Encryption is formally defined as converting data into code. Decryption is the reverse action – turning code back into data. Every time you log into a secure website (your email, online banking, etc.), data is encrypted (encoded) before being sent over the Internet. Once it’s received by the recipient, the data is decrypted (decoded) back into the original message. The secret behind encryption is the cipher – the method used to convert the message into code. If someone knows your cipher, they can then decipher your message by performing the inverse (reverse) operation. Today’s encryption is incredibly difficult to decipher thanks to modern day mathematics. For this assignment, you’ll be using the Caesar cipher. This is a substitution cipher where each letter is shifted by some fixed quantity. For instance, a Caesar shift of 3 replaces every letter with the character of the alphabet that is 3 positions to its left: In the above case, the letters A, B and C are mapped to X, Y and Z respectively. One can view this cipher as follows: Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ Cipher: XYZABCDEFGHIJKLMNOPQRSTUVW Therefore, the message “MATH” would be encoded as “JXQK”. ICS4U1 – Unit 1 Java Review Name: _______________ Decryption is done in reverse – all given characters are mapped to the alphabet member 3 units to the right (wrapping around, if necessary, to the start of the alphabet). Specification: You will produce a class called SecretSafe. Your class must contain the following methods. public SecretSafe() - creates a new SecretSafe object with a Caesar cipher shift of 3 to the left public SecretSafe(int s) - creates a new SecretSafe object that will encrypt using a Caesar cipher shift specified by the parameter s public String Encrypt (String message) - returns an encrypted version of the given string m public String Decrypt (String code) - returns a decrypted version of the given string code Marking Scheme: The following general guidelines hold in addition to good programming practices (appropriate documentation and variable naming): Level 1: Your class encrypts and decrypts messages consisting of letters A-Z using a fixed cipher shift of 3 (i.e. you created the default constructor for SecretSafe). Your class maps spaces to spaces. Level 2: Your class meets all Level 1 expectations. Additionally, your class also encrypts all forms of whitespace to whitespace and letters a-z. Level 3: Your class meets all Level 2 expectations. Additionally, your class also encrypts using an arbitrary cipher shift (i.e. you correctly implemented the parameterized constructor for SecretSafe). Level 4: Your class meets all Level 3 expectations. Additionally, your class encrypts using a new encryption scheme other than the basic Caesar shift. Be creative! BONUS: Feel like working with file input/output? Try to implement the following methods: public void Encrypt(String inFile, String outFile) - reads the contents of the file with name specified by inFile, encrypts it, and outputs the encrypted text into the file specified by outFile public void Decrypt (String inFile, String outFile) - reads the contents of the file with the name specified by inFile, decrypts it, and outputs the decrypted text into the file specified by outFile