Year 7 Computer Science - University Academy of Engineering
advertisement

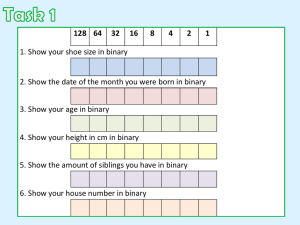
Year 7 Module 2 Big Picture Learning Area: Computer Science University Academy Engineering Southbank Module 2: F1 Data Week # Week 1 Week 2 Week 3 Week 4 Week 5 Context Computers use binary numbers to represent the data that is input into. This is because computers are like massive fields of light bulbs. Each pattern of lightbulb represents a different message. We can convert decimal numbers into binary numbers to show how numbers are stored in a computer. We can also convert binary numbers into decimal numbers. F1 teams use computers to store lots of data about their cars, we can imagine how the F1 championship table would look in binary. We can also speak about the size of data using prefixes in front of bits and bytes. Computers can perform basic mathematical calculations very quickly. They can only add. However, depending on the number of bytes available, a computer will have a limit to how much it can add up to. We can simulate how a computer add and subtracts two numbers. If a computer does have enough bytes, an error will occur. This error is called overflow and simply means that a computer does not have enough space to complete the calculation. F1 teams use computers to add up data, we can imagine how the table we created in binary would look after a few races. Computers can also store text, but they store them in binary as well. We can show how a letter is stored in binary using ASCII and we can even write a short sentence in binary as well. We can also convert binary into words and short sentences. F1 teams can send messages to each other using email, but what would the message look like in binary? Computers can also store images, but can you guess how they store them? We can show how images are stored in computers and create simple bit map images. We can start with simple 1 bit images and then try 2 bit images; we can go as far as 24 bits. Depending on the number of bits we should be able to tell how many colours are available. We can make better pictures by having smaller dots Computers can store numbers, text and images but they store them as binary. The same binary data can be used to represent either numbers, text or images. Week 6 The safe use of computers is important and also our responsibility. We need to be aware of what to do when we encounter inappropriate behaviour Week 7 We can be exposed when using the internet and there are ways to protect our identity and access to our online data Skills Defining the key terms data, binary, decimal, bit and byte; showing how computers store data that is input into a computer; converting binary numbers into decimal and decimal numbers into binary Defining the key term overflow; showing how computers perform addition; solving a series of binary additions; Analysing the impact of overflow when performing binary addition and suggesting ways to reduce the impact. Defining the key terms ASCII and text; showing how letters, words and sentences are stored in computers; converting letters, words, and sentences into binary and vice versa; Analysing the impact of sending secret messages using ASCII and suggesting alternatives. Defining the key terms bit map, pixel, and image; Showing how images are stored in computers; Drawing 1 bit and 2 bit images following simple instructions; analysing the impact of more bits and smaller pixels when representing images Showing how numbers, text and images are stored in computers; converting binary numbers into decimal numbers, text or images depending upon need and vice versa; analysing the impact of space when storing binary data on computers Explaining what to do when we encounter inappropriate behaviour when using computers; suggest a number of responses to inappropriate behaviour when using computers, analyse the impact of responses to inappropriate behaviour Defining the key term online identity; explaining how to protect your online identity; suggesting a number of ways to protect your online identity; analysing the impact of online identity protection methods; evaluating identify protection methods and justifying their use in our school.