Malleability of Cryptosystems
advertisement

Malleability of
Cryptosystems
KEVIN ALLISON
Definitions
𝑀𝑎𝑙𝑙𝑒𝑎𝑏𝑖𝑙𝑡𝑦: The ability to manipulate a given ciphertext α into a
ciphertext β that, when decrypted, produces a related plaintext.
𝑁𝑜𝑛 − 𝑚𝑎𝑙𝑙𝑒𝑎𝑏𝑖𝑙𝑖𝑡𝑦: Not being able to compute a different related
ciphertext β from a given ciphertext α
What Does Non-malleablity
Provide?
Improved security by knowing the encrypted message has not been
tampered
Ideologically equivalent to existentially unforgeable signatures
Secrecy does not imply independence
◦ Non-malleable cryptosystems prove this
Simple Example
Professor Kaminsky enjoys encrypting his grades and giving each
student their own symmetric key for decryption. Unfortunately you
forgot how to add and did not do so well on the first test. With a
malleable cryptosystem, this can be fixed!
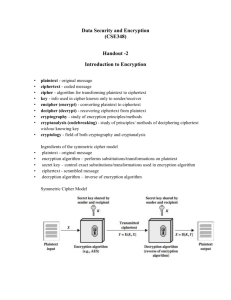
D
Start Grade
Encrypt
α
Various
Operations
β
Relation
Check
If R(α,
β) == 1
Decrypt
A
Done!
End Grade
(The previous assumes Professor Kaminsky uses a malleable encryption scheme. This is unlikely).
Security
Given a relation R and the ciphertext α
Malleable if 𝛽: 𝑅 𝛼, 𝛽 = 1
◦ B is able to create a related ciphertext β from ciphertext α
Non-malleable if ∀𝐴 𝑚𝑜𝑢𝑛𝑡𝑖𝑛𝑔 𝐺 ∃𝐴′ : 𝑅 𝛼, 𝛾 = 1
◦ For every attacker A launching an attack G there is an A’ that produces a
ciphertext γ without access to ciphertext α and with a similar probability as A
Two types:
◦ Semantic Security
◦ Non-malleable Security
α – Message
β – Rel. Msg
G – Attack
A - Attacker
A’ - Simulator
R - Relation
𝛾 – Rel. Msg.
Semantic Security
Definition 2.1:
A scheme S for public-key cryptosystems is semantically secure with
respect to relations under chosen plaintext attack if for every
probabilistic polynomial time adversary A as above there exists a
probabilistic polynomial time adversary simulator A’ such that for every
relation 𝑅(𝑚, 𝛽) and function ℎ𝑖𝑠𝑡 𝑚 computable in probabilistic
polynomial time 𝜋 𝐴, 𝑅 − 𝜋′(𝐴′ , 𝑅) is subpolynomial.
𝜋(𝐴, 𝑅) – Probability A Succeeds
𝜋′(𝐴′, 𝑅) – Probability A’ Succeeds
ℎ𝑖𝑠𝑡(𝑚) – Function ret. info on m
Types of Attacks
Chosen Plaintext
◦ Attacker can encrypt any plaintext to get the ciphertext
◦ Least Powerful
Chosen Ciphertext – Pre Processing
◦ Access a decryption oracle < xp times, then remove oracle
Chosen Ciphertext – Post Processing
◦ Gets challenge ciphertext before oracle is removed
◦ Can decrypt any ciphertext excluding the challenge via the oracle
◦ Most Powerful
Incorrect Implementations
(Dolav et al.)
Appending encryption to a zero-knowledge proof
◦ Proof could be malleable, therefore possible to generate new encryption and
new proof
Sending encryption plus signature
◦ Possible to generate new encrypted message E(m+1) and new signature
based-off that
Signature inside Ciphertext
◦ Same as above
Public Key Overview
Scheme S (Dolev et al.)
◦ Create public signature verification key/private signing key
◦ Encrypt message using several keys derived from public signature verification
key
◦ Zero-knowledge proof used to show value encrypted is the same
◦ Encryptions and proof are signed from using the key from step 1
Public Key Generation (Dolev
et al.)
GP – Key Generator
U – Random String
H – Family of Functions: ∀𝑥 𝑦 ≠ 𝑥: ℎ 𝑦 = ℎ 𝑥 𝑖𝑠 ℎ𝑎𝑟𝑑
Public Key Encryption (Dolev
et al.)
GS – Signature Key Generator
h – One Way Hash Function
Public Key Encryption (Dolev
et al.)
i≤𝑘
𝑣
𝑣
𝐹, 𝑠, 𝑐1 , 𝑝1 , 𝑐2 , 𝑝2 … 𝑐𝑘 , 𝑝𝑘
𝑣
Run 𝑍𝐾𝑃 on 𝑐𝑖 = 𝑒1 1 𝑒2 2 … 𝑒𝑛𝑛
with witness 𝑟𝑖1 𝑟𝑖2 … 𝑟𝑖𝑛 𝑎𝑛𝑑 𝑈
𝑗 ≤𝑛
𝑟𝑖𝑗 ∈𝑅 {0,1}𝑝(𝑛)
𝑐𝑖𝑗 = 𝐸 𝑣𝑗 𝑏𝑖 , 𝑟𝑖𝑗
𝑒𝑗
ZKP – Zero Knowledge Proof
k – Length of input
n –size of the generator
Non-malleable Security
Run the Public Key Generation on Related Scheme (S’):
◦
◦
◦
◦
Only run GN(n) n times. Not 2n.
Public Key: 𝑒1 , … , 𝑒𝑛
Private Key: 𝑑1 , … , 𝑑𝑛
Message ---encrypt---> 𝑐1 , … , 𝑐𝑛
If S is broken for malleability, then S’ is broken for semantic security
◦ Thus if S’ is semantically secure, then S is non-malleable
Critical Components
Security of the one-way hash function
◦ If it is possible to reverse the hash function, then the Scheme is invalid
◦ Does the hash function produce collisions?
◦ Another failure case
Is the Zero Knowledge Authentication system correct?
◦ Otherwise verification of information is jeopardized.
Modern Implications
What if the Key is malleable?
◦ Is it possible to modify the key in such a way that it will produce a related
plaintext that will decryption with correct public key.
◦ Then the proposed encryption scheme does not work. It is vulnerable to
that attack
To combat this, we need to make the relation take the public key into
account!
◦ Redefine a relation to be contain 𝑝𝑘 and 𝑝𝑘 ∗ in addtion to 𝛼 and 𝛽
References
Dorlev et al. Non-Malleable Cryptography.
http://www.cs.rit.edu/~kra2178/crypto/files/10.1.1.49.4643.pdf
Fisclin, Marc. Completely Non-malleable Schemes.
http://www.cs.rit.edu/~kra2178/crypto/files/completely_non_malleabl
e_schemes.pdf
Ventre, Carmine. Completely Non-Malleabe Encryption Revisited.
http://www.iacr.org/archive/pkc2008/49390068/49390068.pdf
Boldyreva et al. Foundations of Non-malleable Hash and One-Way
Functions.
http://www.cs.rit.edu/~kra2178/crypto/files/found_non_malleable.pdf
Questions?