Presentation Three
advertisement

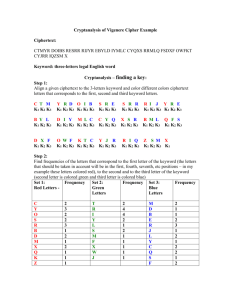
Vigenére Cipher Kimberly Chiffens & Maria Jannelli Progress Report •Implementation of Vigenere encryption and decryption •Applet design •Website design •Implementation of Friedman attack which one way to find the key length in cryptanalysis Future Plans •December: Finish introduction of the paper, Finish Kasiski implementation •January: Start to implement the Cryptanalysis and finish draft of the paper •February: Implement cryptanalysis •March: Implement cryptanalysis •April: Finish final project and paper Cryptanalysis •Given only the Ciphertext, we must find the Plaintext and the key •The first step in doing this is finding the KEY LENGTH •Two ways to find this key length is: •Friedman Attack implementation •Kasiski Attack implementation Friedman Attack • The goal is to find the key length • Uses frequencies to count the amount of each letter in the ciphertext • We multiply the count of each letter by count minus 1 and then add up the sum. • It computes the sum of the frequencies as follows: • for(int k = 0; k < 26; k++) • sum = sum + Fcount[k]*(Fcount[k]-1); • } Friedman Attack • We then find the index of coincidence • To find this we divide the entire sum of the frequencies with the length of the cipher times the length minus 1. • index= sum/(lc*(lc-1)); , where lc is the length • Then we must calculate the key length. To do so we use this equation: • keyword2= ((0.0265*lc)/((0.065index)+(lc*(index-0.0385)))); Friedman Example Ciphertext: OAKKADKMFCRBCKBOMTTITMIF Frequencies: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z 2 2 2 1 0 2 0 0 2 0 4 0 3 0 2 0 0 1 0 3 0 0 0 0 0 0 Length = 24 letters Sum of frequencies = Σ letterCount*(letterCount-1) Key: Cat Plaintext: mariakimmariakimmariakim Program Demonstration Ciphertext: KSEUOBHCSABMBSGBCLHCSATYLSLXHNJGRNRMWGMVSMCVCADJJQCOCPRTGCKC ASUQSPNWRRGLXHWXIKRUFCRGBZGTSWXIPWCQNOJXHGVOERBCRTWXIPYFCLW MDGLXGCFSPNGYWRURQFNRGWPCCKCNBWXIPCCCBHFJHAUSYAZWFCSUR8WCRK SYCFCJHDXFWXIBKSDXFANRRXGKNZJHCSATCNHWXIPWCQNKMDZBKSYBCSAQCXTB ASYMKCASGCORCOAQSBJHMYMMDFFNOBRHQXCLFCSURBAWTNMMDHMMSQYO GATMASTNFRRQIUSBKMWXIPQOGAKGCVGWMMDFCJFWXIPWCQNKMDZBKSYWO ZBCJDHCLORJGRACNQSDXFUQSLHCSFSPNCZUWENRRXGLNSXNMMDFZAOGWKMD ZBAORCZCOFMVHFNPPNSXNMMDFLXGCRBQCSYMHFACSPVRQWATOLMHFRBPNAY RBQKSRFSCWMMDFCHSQJBBLVGWBMCDYBHCMCLBCKNCRQSPYZYLSZNUJJRWXIP WCQNWQXBWXIPOOAN Key: joy Deciphered Plaintext: BEGLADYOURNOSEISONYOURFACENOTPASTEDONSOMEOTHERP LACEFORIFITWEREWHEREITISNOTYOUMIGHTDISLIKEYOURNOSE ALOTIMAGINEIFYOURPRECIOUSNOSEWERESANDWICHEDINBET WEENYOURTOESTHATCLEARLYWOULDTNOTBEATREATFORYOUDB EFORCEDTOSMELLYOURFEETYOURNOSEWOULDBEASOURCEOFD READWEREITATTACHEDATOPYOURHEADITSOONWOULDDRIVEYO UTODESPAIRFOREVERTICKLEDBYYOURHAIRWITHINYOUREARYOU RNOSEWOULDBEANABSOLUTECATASTROPHEFORWHENYOUWER EOBLIGEDTOSNEEZEYOURBRAINWOULDRATTLEFROMTHEBREEZE YOURNOSEINSTEADTHROUGHTHICKANDTHINREMAINSBETWEEN YOUREYESANDCHINNOTPASTEDONSOMEOTHERPLACEBEGLADYO URNOSEISONYOURFACE Kasiski Attack • The goal is to find the key length • Count the gaps between repeated trigrams in the ciphertext • The key is a divisor of the GCDs of the gaps Kasiski Attack Example Ciphertext: WCZOU LXSSU UQNAH YJPFN JFIAW QNAHY YEDBL ZLQWB SVYXA ULKHG YLWQI TQQYY IRNPH F WOSHM AUCER CELVE RRMJF IAWFN AHBZO STBHW LJCYZ EIYWV SHZOR WBSVY XAEEM -NAH repeated three times -There are 48 letters from the first occurrence of NAH to the second and 8 letters from the second to the third occurrence. -WBSVYZAEEMJFIAWF repeated twice -There are 72 letters between the long groups Kasiski Attack Example · The greatest common divisor of 72,48, and 8 is 8 · The keyword length is likely to be 8, 4, or 2 · A 2 or 4 letter keyword offers little security so it is likely to have the keyword length of 8 References •Principles of Operating Systems: Design and Application, Brian L. Stuart. Course Technology. 2009. •Invitation to Cryptology, Thomas H. Barr. Prentice Hall. 2002.