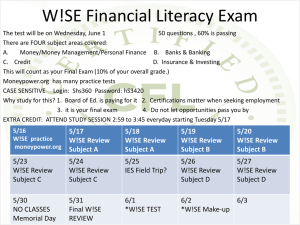
Protect your Small Business Customers They are a
advertisement

SiteLock Internet Security: Big Threats for Small Business Protect your Small Business Customers They are a sizable investment Number of U.S. Small Businesses 26.9 M Percent of U.S. Firm Population (in # of Employees) 91.8% Percent of U.S. Business Revenue Earned by SMB’s 61.4% One-year U.S. SMB Revenue $11.4T Small Business Trends; restating US SBA.gov report Why the SMB Market is at Risk: A closer look • • • • • Over 60% of data breaches are at companies with <100 employees Nearly half involved malware injections ** 98% of ALL applications have holes ** 68% of vulnerabilities found are XSS Over 6,000 websites are blacklisted every day *Verizon , US Secret Service Report **HP Security Report * What Website Security Means • Be proactive • Design and build websites with security in mind • Take additional care to “harden” open-source applications • Sanitize dynamic content to ensure safety of interaction • Identify and repair likely vectors for attacks • Code injections • Weak or unencrypted login pages and credentials • Out-dated applications • Employ non-intrusive security practices to identify and remediate potential problems before hacks occur • React quickly • Detect and clean malware before websites are blacklisted Business Impacts of Poor or Reactive Security • • • • • Small business websites can be shut down Business reputation is damaged Revenue can be lost Customer data is at risk Search engine rankings plummet The Most Common Threats to SMB’s • • • • SQL Injections Poor Server Configuration / Authentication (Credential Theft) SQL Injection combined with Malware Malware UK Security Breach Investigations Report, 2010 The Threat/Vulnerability Evolution • • • • • • Cross Site Request Forgery Cross Site Scripting (XSS) Buffer Overflow SQL Injections Remote File Include (RFI) Denial of Service HP Top Cyber Risks Report, Mid-year 2011 Security is a Challenge for SMB’s InformationWeek Analytics Strategic Security Survey, October 2011 Where do SMB’s Turn for Help? • • • • • • • Read forums and help websites and fixed it myself Tried several approaches, but site is still compromised Followed security company instructions provided Called a security/IT expert/web developer to sort it out Nothing – site seems OK now Abandoned the whole thing and set up a new site with a new provider Other Compromised Websites: an Owner’s Perspective; StopBadware.org, CommTouch, 2012 Response from Hosting Provider • • • • None, never communicated the issue to them Provided assistance at no cost to help fix the compromised site No help provided, or refused to respond Charged additional fees to help fix the compromised site Compromised Websites: an Owner’s Perspective; StopBadware.org, CommTouch, 2012 The Plan to Fight Back Technology - Turn-key - Always on - Business focus, not IT - Secure network - SSL - Firewall Process - Security standards - Strong passwords - File protection - Compliance requirements People - Education & awareness - Test your own site - Update web apps & plug-ins The Ideal Complete Solution When considering internet security partners/providers, look for: • A comprehensive set of security measures designed for prevention or detection. • A range of scans that analyzes all web traffic, network and applications for threats. • A process design, even the most effective protection cannot stop 100% of attacks. • A trial to see if it is easy to use, the most effective toolset is of little use if you can’t figure out how to use it. • Consider solutions with a straightforward user interface or dashboard that will keep a user informed on what’s going on. Key take-away: When it comes to website security, prevention is always the best policy. Thank you Questions & Discussion Email SiteLock: partners@sitelock.com