What is a VPN?
advertisement

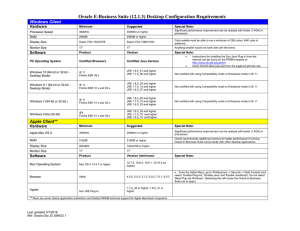
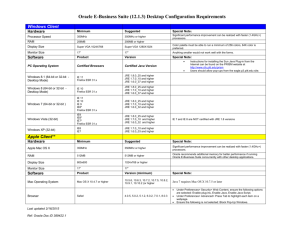
Mike Bayne 15 September 2011 http://www.jmu.edu/computing/security/sslvpn-intro.pptx Virtual Private Network Provides an encrypted tunnel between a client computer and a remote network Remote termination proxies the connection to other resources All or some traffic routed to remote network VPN terminal JMU Border VPN Operation Gain remote access to applications and data deemed too sensitive to expose directly to the Internet ◦ Student Administration system Gain remote access to resources licensed to JMU by IP address ◦ Microsoft site license ◦ Online library resources Required a client ◦ No support for new OSes ◦ No support for mobile devices Tunneled all traffic over UDP ◦ All traffic had to go through JMU, even if not destined for JMU Access required configuration on firewalls Rapidly approaching end-of-life http://www.juniper.net/us/en/products-services/security/sa-series/sa6500/ Support for newer OSes Support for mobile devices Uses web browser for basic access Java clients for advanced access LDAP or Active Directory authentication Access granted based upon roles Platform OS: list of browsers and Java Environment Windows •Windows XP Professional SP3 32 bit: Internet Explorer 7.0, 8.0, and Firefox 3.6, 4.0; Sun JRE 6 •Vista Enterprise SP2 32 & 64 bit : Internet Explorer 7.0, 8.0, 9.0 and Firefox 3.6, 4.0; Sun JRE 6 •Windows 7 Enterprise SP1 32 & 64 bit: Internet Explorer 8.0, 9.0 and Firefox 3.6, 4.0; Sun JRE 6 Mac •Mac OS X 10.6.4, 32 and 64 bit: Safari 5.0, Safari 5.1 Sun JRE 6 •Mac OS X 10.5.8, 32 and 64 bit: Safari 4.0 Sun JRE 6 Linux •OpenSuse 11.3 , 32 bit only: Firefox 3.6, 4.0; Sun JRE 6 •Ubuntu 10.04 LTS, 32 bit only: Firefox 3.6, 4.0; Sun JRE 6 Platform Operating System Browsers and Java Windows Vista with Service Pack 1 or 2 on 32 bit or 64 bit platforms Windows 7 on 32bit or 64 bit platforms XP Professional SP2 or SP3 on 32 bit or 64 bit platforms XP Home Edition SP3 Internet Explorer 9.0 Internet Explorer 8.0 Internet Explorer 7.0 Firefox 3.0 and above Sun JRE 6 and above Mac Mac OS X 10.6.x, 32 bit and 64 bit Mac OS X 10.5.x, 32 bit and 64 bit Mac OS X 10.4.x, 32 bit Safari 3.0 and above Sun JRE 6 and above Linux OpenSuse 10.x and 11.x, 32 bit only Ubuntu 9.10 and 10.x, 32 bit only Red Hat Enterprise Linux 5, 32 bit only Firefox 3.0 and above Sun JRE 6 and above Solaris Solaris 10, 32 bit only Mozilla 2.0 and above iPhone OS 3.0 and above with default Safari Android 2.0 and above Symbian OS 8.1 and above Windows Mobile 6.0 Standard, Classic and Professional: Pocket IE 6.0 Windows Mobile 6.1 Standard, Classic and Professional: Pocket IE 6.0 Windows Mobile 6.5 Standard, Classic and Professional: Internet Explorer Mobile 6.0 Windows Mobile 5.0 based Pocket PC devices: Pocket IE 4.0 NTT I-mode phone AU/KDDI phone : Open wave Mobile Browser Vodafone phone : Open wave Mobile Browser Web Connect WSAM/JSAM Network Connect Junos Pulse (Mobile clients) Default connection Provides access to: ◦ ◦ ◦ ◦ Web resources File Access Remote desktop SSH access Solution for most connections at JMU Windows only Java program or Activex control Inserts a shim into the network stack Network access to preconfigured resources are directed through the VPN Resources MUST be preconfigured on the VPN Java based proxy Maps local port to remote destination through the SSL VPN ◦ Example: hrweb.jmu.edu:443 is mapped to local port 8000 ◦ Connections to https://127.0.0.1:8000 is forwarded to hrweb.jmu.edu:443 Either WSAM or JSAM per role, not both Not currently used at JMU Most impact on JMU and client system Java application Behavior similar to existing Cisco VPN: all traffic is routed through the VPN to JMU’s network Network Connect for mobile devices All traffic tunneled through the VPN Untested Network resources that users are allowed or denied access to Identified by host and port, subnet, URI, etc Can be specific enough to allow access to parts of a website while denying access to others Group of people that share similar access Role membership can be identified by LDAP group membership or attribute Role membership can be enumerated within the SSL VPN ◦ Most roles are enumerated ◦ Want to move to LDAP/AD as identity management matures Users are often assigned multiple roles Logical container containing authentication source and login pages May be accessed either by a new domain name or by a new URL ◦ https://student.sslvpn.jmu.edu ◦ https://sslvpn.jmu.edu/student Roles are added to a realm ◦ Roles may be in more than one domain Resources are added to roles ◦ Both permit and deny resources are added ◦ Default deny of access to unmentioned resource ◦ Users accumulate resources from each role they’re assigned to Moving from enumerated roles to group/attributes in a directory Identifying resources that don’t work with web connect and developing workarounds ◦ Internal JMU applications ◦ Externally licensed resources (750+ through the library alone) Endpoint Security ◦ Malware protection ◦ Antivirus version monitoring ◦ Patch management monitoring Cache Cleaner Two-factor authentication ◦ One-time passwords ◦ Certificates Single Sign-on Restrictions to access from certain subnets Restrictions to browsers