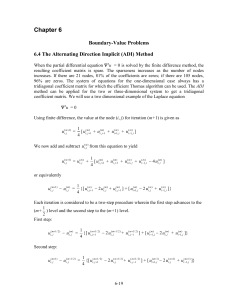
Event –based Trust Framework model in wireless sensor networks
advertisement

Veronica Eyo
Sharvari Joshi
• The nodes are left unattended
• An Adversary can physically compromise the nodes
Solution?
Authentication and cryptographic mechanisms alone
can not solve this problem
The trust system was used for security in the Wireless
sensor network
These systems identify malicious nodes,
computes a trust rating of the node and
exclude the nodes from the network.
First trust based model designed and
developed for sensor networks.
It makes use of the watchdog mechanism to
collect data and monitor different events
going on in the node, to build
reputation(Rij)of the node and then get the
trust rating (Tij)of the node.
Tij = Pj + 1
Pj + Nj + 2
Pj = Positive outcome
Nj = Negative outcome
RFSN can not distinguish between negative and
positive events in the node.
•
•
Addressed the uncertainty issue but
still cooperated with the malicious
nodes.
Has one value of trust rating for
different events.
•
•
•
Event based trust framework is proposed to
detect malicious sensor nodes
A new protocol ESTN is developed
A new direction in trust system for wireless
sensor network is proposed
The trust rating is dependent on different
events in the node
Each event on the sensor node has a different
trust rating
A sensor node has several trust ratings stored
in its neighbor nodes
The agent node
Classifies all the events and then builds a
reputation table of the nodes
A trust table is then computed from the
reputation table and broadcast to all the
nodes.
Event E happened in sensor nodes.
Let E={e1 ,e2 ,e3 ,....en }
Event function.
F={F(ei )| ∀ei ∈E,F(ei) ≥1,F(ei )∈N}
Positive outcome pi
Negative outcome ni
<p ,n > is binary event for a certain event ei
of sensor node.
Define reputation space of event ei
RS(ei )={<pi ,ni>|ti=pi+ni;pi=F(ei ) or ni=F(ei )
∀ei∈E}
P<pi ni> (x)= (pi+ni+1)! Xi ^(pi) (1-Xi)^ni
pi! ni!
Reputation: opinion of one entity about
another
Trust: Expectation of one entity about
another.
Reputation
space to Trust space
Let Ti (<pi ,ni >)=(pti ,nti ,uti ) be the
transformation from binary event <pi ,ni > to
trust rating (pti ,nti,uti )
while True
For all the nodes s and t in the agent node radio
range
For event e1 to en
Agnet node gets the binary event <pi ,ni >
Agent computes the trust rating Tsti;
If (Tsti) < a certain value
Break;
End if
End for
The agent broadcasts the trust rating Tsti;
End for
If the time is the begin of window time
The agent broadcasts all the trust rating Tsti;
End If
End While
Modules used:
◦
◦
◦
◦
◦
Wireless sensor networks (xA, xB…xN)
Agent nodes (xi)
Intruder nodes (xm)
Traffic data ()
Events generator
Need to design a special Agent node
Higher processing power for the agent node
Complex architecture
Protection of agent node
Protect agent node from discovery.
Broadcast trust rating to the remote
monitoring facility.
This trust model can be used in large scale
wireless networks
It provides a more accurate guarantee along
with cryptographic mechanisms in detecting
malicious nodes of different events in sensor
networks
Questions?