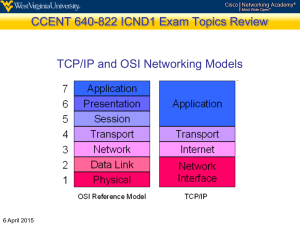
Layer 4 Testing
advertisement

Testing With Your Customer In Mind to Accelerate Product Innovation and Adoption Product Presentation – July 2010 Who is BreakingPoint Systems ? • Founded September 2005 • 285% Revenue growth, 2009 vs. 2008 • 12 Quarters of Consecutive Growth • Breakthrough, award-winning products • Privately held and based in Austin, TX Sales & Support: US, Canada, UK, France, Italy, Spain, Netherlands, Belgium, Israel, Switzerland, Finland, Sweden, Germany, Norway, India Japan, China, Korea, Taiwan, Malaysia, New Zealand, Australia, … What can BreakingPoint Systems Offer ? • BreakingPoint provides New Generation of High Performance Test Equipment at All Inclusive L2, L3, L4, L7, Security and Fuzzing from the same test port at the time using the same Management Software and same Hardware. 3 No License Model – All Features Available by Default What type of tests does BreakingPoint provide ? • Realistic Traffic Emulation Layer 2-7 IPv4 and IPv6 Bit Blaster - Generates Ethernet frames (L2 Tests) Routing Robot - Generates IP packets (L3 Tests) Session Sender - Generates TCP and UDP (L4 Tests) L2 and L4 Recreate – Raw Playback, TCP and UDP PCAP AppSim – 140+ Client and Server Application Protocols (L7 Tests) Layer ClientSim – Interaction with Real Server (L7 Tests) 4-7 • Malicious Traffic Simulation Layer 2-7 IPv4 and IPv6 Security Module – 4,500+ unique attacks, 80+ evasion types Stack Scrambler – Protocol Fuzzing on AppSim Module Protocols 4 No License Model – All Features Available by Default BreakingPoint Systems Key Benefits • New Generation of Hardware Architecture optimized for Layer 2-7: – FPGA and Network Processor • High-Performance Traffic Simulation Layer 2-7 per 4U Chassis: – – – – Up to 80 Gbps L2/L3 Traffic Simulation Up to 40 Gbps L4/L7 Traffic Simulation Up to 1.5 Million New L7 Sessions per Second Up to 30 Million Concurrent L7 Sessions • Flexible and Easy to Use Interface – Web GUI to control L2, L3, L4, L7 Traffic, Security and Fuzzing – Device Under Test Monitoring (SSH, Telnet, SNMP, Serial) – Possibility to mix in the same test on a single test port in same test • L2/L3 Stateless and L4/L7 Stateful traffic • Good Stateless/Stateful and Malicious traffic 5 User Friendly Web Interface 6 Resiliency Score 7 BreakingPoint Storm CTM (Cyber Tomography Machine) BreakingPoint Storm CTM™ • • • • • • 130+ applications 4,500+ live security attacks 80+ evasions 40 Gbps blended application traffic 30M concurrent TCP sessions 1.5M TCP sessions/second Keep Up-To-Date • Application and Threat Intelligence • Frequent and automatic applications and attack updates • Published methodologies • Service, support, and comprehensive maintenance BreakingPoint Resiliency Score Security Performance • Simple method to evaluate network device resiliency under real-world conditions – Performance Stability • Frame rate • Concurrent sessions • New session rate – Security • Susceptibility to direct attack • Optional strike blocking abilities Resiliency Score – Stability • Resistance to fault injection • Fixed standard to evaluate multiple devices • Repeatable measurements 10 Scoring the Target Device or Network 11 Layer 3 Test Routing Robot Module 12 Layer 3 Network Performance Validation • Routing Robot determines if a DUT can handle high volumes of Layer 3 traffic by sending traffic from one interface and monitoring the receiving interface to see if the traffic is successfully received. • Routing Robot can simulate Frame Size from 64 to 9216 Bytes 13 BreakingPoint Routing Robot – Layer 3 Testing 14 BreakingPoint Routing Robot – Layer 3 Testing 15 RFC 2544 GUI 16 Simple RFC2544 GUI 17 Real-Time Stats 18 Real-Time Stats 19 RFC 2544 Test Result Summary 20 Latency Measurement in Microseconds 21 Traffic Overview 22 Layer 4 Test Session Sender Module 23 Layer 4 Network Performance Validation • The Session Sender test component measures the device’s ability to handle a large number of new TCP session per second, concurrent TCP sessions and TCP Bandwidth. • Session Sender can simulate Segment Size until 9146 Bytes 24 BreakingPoint Session Sender – Layer 4 Testing 25 BreakingPoint Session Sender – Layer 4 Testing 26 BreakingPoint Session Sender – Layer 4 Testing 27 BreakingPoint Session Sender – Layer 4 Testing 28 Layer 2 Replay Raw Replay Recreate Module 29 Recreate Captured Traffic • The BreakingPoint Recreate feature replay PCAP exactly as it is based on raw data L2,L3,L4 and L7 information from the original PCAP. BreakingPoint will do Raw Playback. • Layer 2 PCAP Replay give the ability to replicate customer issue on Mobile Protocols decoding. 30 L2 Recreate Mobile Protocol GTP 31 L2 Recreate Mobile Protocol IuUP 32 Layer 4 Replay Mix TCP & UDP Recreate Module 33 Recreate Captured Traffic • The BreakingPoint Recreate feature recreates multi-flow TCP/UDP traffic based on data from PCAP. BreakingPoint does not use a raw playback, instead it will do stateful multiflow allowing possibility to replay stateful TCP & UDP traffic with ability to amplify at High Performance. 34 BreakingPoint Recreate: Capture File Setting 35 BreakingPoint Recreate: Layer 4 Replay TCP/UDP 36 BreakingPoint Recreate: Amplify Replay 37 BreakingPoint Recreate: Layer 4 Replay TCP/UDP 38 Layer 7 Test Application Simulator Module Real Protocols High Performance NOT Replay of PCAP 39 Layer 7 Application Performance Validation • Application Simulator allows you to define 120+ applications protocols to make complex application protocol distributions to simulate real world traffic. • Application Simulator allows you to define in depth each protocol using advanced protocol configuration “SuperFlows”. 40 Partial List of 140 Applications Authentication DIAMETER RADIUS Accounting RADIUS Access Custom Toolkits Applications Raw Security Attacks Chat AIM6 Keyserver AIM6 Rendezvous AIM6 Switchboard AOL Instant Messenger IRC Jabber MSN Dispatch MSN Nexus MSN Notification MSN Passport MSN Switchboard OSCAR OSCAR File Transfer QQ IM Windows Live Messenger Yahoo! Messenger ICQ Data Transfer FTP Gopher HTTP NNTP RSync TFTP Data Transfer / File Sharing IPP NetBIOS NETBIOS DGM NETBIOS NS NETBIOS SSN NFS RPC NFS SMB SMB/CIFS SMBv2 Databases IBM DB2 Informix Microsoft SQL MySQL Oracle PostgreSQL Sybase TDS TNS Distributed Computing Citrix DCE/RPC VMware VMotion Enterprise Applications DCE/RPC Endpoint Mapper DCE/RPC Exchange Directory DCE/RPC MAPI Exchange SAP Games World of Warcraft Email IMAP IMAPv4 Advanced Outlook Web Access POP3 POP3 Advanced SMTP Email AOL Web Mail Gmail GMX Webmail GMX Webmail Attachment Hotmail Hotmail Attachment Orange Webmail Yahoo! Mail Yahoo! Mail Attachment Financial FIX FIXT Partial List of 140 Applications Peer-to-Peer AppleJuice BitTorrent Peer BitTorrent Tracker BitTorrent eDonkey Gnutella Leaf Gnutella Ultrapeer PPLive QQLive Winny Remote Access RDP RFB RLogin Telnet Secure Data Transfer HTTPS SSH Social Networking Twitter MySpace System/Network Admin DNS DNS (Deprecated) IDENT Finger LDAP NTP RPC Bind RPC Mount SNMP SNMPv1 Sun RPC Syslog Time Telephony SMPP MM1 H.323 Testing and Measurement Chargen Daytime Discard Echo OWAMP Control OWAMP Test QOTD TWAMP Control TWAMP Test Voice/Media H.225.0 H.225 RAS H.245 MMS MM1 RTCP RTP RTP Unidirectional Stream RTSP SIP Skype Skype UDP Helper STUN Enterprise Mix Protocols 43 Service Provider Mix Protocols 44 Education Mix Protocols 45 Create your own Mix of L7 Protocols 46 High Level Real-Time Stats L2, L3, L4 and L7 47 Detail Real-Time Stats per L7 Protocols 48 Protocol API Custom Application Toolkit Create your Own Protocol 49 What Is BreakingPoint Custom Application Toolkit? • Protocol API to Create New Protocol • XML-Based Description Language • Ruby API for more advanced programming techniques • Fully integrated with BreakingPoint Hardware BPS Storm CTM to simulate the New Protocol at High Performance with others native L7 Protocols. 50 Importing Into BreakingPoint Storm CTM 2. Add “Custom Application” 3. Add “Process Dblock XML” 1. Create a SuperFlow 51 P2P - LimeWire 52 Youtube 53 Layer 7 Test Client Simulator Module Interaction with Real Server 54 Real Web Infrastructure 55 BreakingPoint Test Infrastructure 56 34 Client Simulator Protocols Supported 1. Chargen 2. Daytime 3. DB2 Connectivity 4. Discard 5. DNS 6. Echo 7. eDonkey 8. Finger 9. Gopher 10.HTTP 11.Ident 12.IMAP 13.IPP 14.IRC 15.MMS-MM1 57 16.Microsoft SQL 17.MySQL 18.NetBIOS Session 19.NTP Synchronization 20.POP3 21.QOTD 22.Radius Access 23.Radius Accounting 24.Rlogin 25.SMBv1 26.SMBv2 27.SMTP 28.SNMPv1 29.STUN 30.SunRPC Bind 31.Syslog 32.Telnet 33.TFTP 34.Time 35.SIP Regular Expression to Extract, Insert and Modify 58 SMB Statistics 59 Security Test Security Module Real Attack NO Replay of Attack PCAP 60 Network Security Performance Validation • BreakingPoint Security component can be used to test network security devices – such as IPS, IDS and firewalls. It measures a device’s ability to protect a host by sending 4,500+ Attacks under CVE-ID, BugTraqID, OSVDB and verifying that the device successfully blocks the attacks. 61 BreakingPoint Security Test Component 62 BreakingPoint Security Test Component 63 Security Test Report: High Level 64 Security Test Report: Details 65 Protocol Fuzzing Test Stack Scrambler Module 66 Protocol Fuzzing • Stack Scrambler tests the integrity of different protocol stacks by sending malformed packets to the device under test. It uses a fuzzing technique, which modifies a part of the packet (checksum, protocol options, etc.) to generate the corrupt data. Fuzzing could be done on AppSim Protocols. 67 Packet Capture Exporting Export Compressed Packet Captures Post Processing of Packet Captures use Berkley Packet Filtering Ability to select only a specific range of packets Traffic Impairment 69 Impairment per Subnet 70 Possibility of Impairment 71 Device Under Test (DUT) Real-Time Monitoring 72 Real-Time Device Under Test Monitoring • BreakingPoint offers the ability to connect to a DUT via Telnet, SNMP, SSH, or Serial to monitor the status of a DUT offering the ability to check CPU, Memory, New TCP connections per Second, Concurrent TCP Connections, Bandwidth and Packet per Second. Eliminates manual power-cycle reboots. 73 Device Under Test Monitoring 74 Device Under Test Monitoring 75 Device Under Test Monitoring 76 Test Scenario 77 Mixing Layer 2-3 and Layer 4-7 Traffic • BreakingPoint is the only solution able to send Layer 2-3 and Layer 4-7 traffic from a single test solution with single user interface on same test port. 78 Mixing L2/L3 and L4/L7 Traffic 79 Mixing L3/L7 IPv4 and L3/L7 IPv6 Traffic • BreakingPoint is the only solution able to send L3/L7 IPv4 and L3/L7 IPv6 traffic from a single test solution with single user interface on same test port. 80 Mixing L3/L7 IPv4 and L3/L7 IPv6 Traffic 81 Mixing Good and Malicious Traffic • BreakingPoint properly tests high-performance security devices with the capability to mix good traffic and malicious traffic emulating real world test scenarios. 82 BreakingPoint: Mixing Good and Malicious Traffic 83 Mixing Legitimate Traffic and Fuzzing Traffic • BreakingPoint properly tests high-performance devices with the capability to mix good traffic and fuzzing traffic at the same time from the same test port and monitor the impact on the DUT over SSH, TELNET, SNMP or Serial. 84 Mixing Legitimate Traffic and Fuzzing Traffic 85 Automation using Drag and Drop GUI 86 GUI Automation: Run Multiple Layer 2-7 Tests 87 Global Reporting of Layer 2-7 Test Series 88 BreakingPoint Systems Hardware Platform 89 BPS Storm CTM Chassis – 8x 1 GigE Ports • Hardware Information – 1x Blades of 8x 1 GigE Ports SFP – 1x Controller with Management Port and DUT Monitoring Port 90 BPS Storm CTM Chassis – 16x 1 GigE Ports • Hardware Information – 2x Blades of 8x 1 GigE Ports SFP – 1x Controller with Management Port and DUT Monitoring Port 91 BPS Storm CTM Chassis – 4x 10 GigE Ports • Hardware Information – 1x Blades of 4x 10 GigE Ports XFP – 1x Controller with Management Port and DUT Monitoring Port 92 BPS Storm CTM Chassis – 8x 10 GigE Ports • Hardware Information – 2x Blades of 4x 10 GigE Ports XFP – 1x Controller with Management Port and DUT Monitoring Port 93 BPS Storm CTM Chassis – Mix Gigabit / 10 Gigabit Ports • Hardware Information – 1x Blade of 8x Gigabit Ports SFP – 1x Blade of 4x 10 Gigabit Ports XFP – 1x Controller with Management Port and DUT Monitoring Port 94 BPS Storm CTM Hardware Platform Test Possibility 8x Gigabit Blade 4x 10 Gigabit Blade 8x 1 Gigabit 4x 10 Gigabit 8x SFP 4x XFP L2 Test Yes Yes L3 Test Yes Yes L4 Test Yes Yes L7 Test Yes Yes 120+ Protocols 120+ Protocols Yes, 4,500+ Attacks Yes, 4,500+ Attacks Protocol Fuzzing Test Yes Yes Recreate L2 PCAP Yes Yes Recreate L4 PCAP TCP/UDP Yes Yes 8 GB / 1 GB per Port 8 GB / 2 GB per Port Number of Interface Type of Interface Number of Protocols Security Test PCAP Capture Buffer 95 BPS Storm CTM Hardware Platform Performance 1x Blade 8x Gigabit 1x Blade 4x 10 Gigabit L2/L3 Packet/Sec 12 Millions 60 Millions L2/L3 Bandwidth 8 Gbps (64 Bytes) 40 Gbps (64 Bytes) L4/L7 TCP/SEC 500,000 750.000 L4/L7 TCP OPEN 10 Millions 15 Millions L4/L7 Bandwidth 8 Gbps 20 Gbps 2x Blade 16x Gigabit 2x Blades 8x 10 Gigabit L2/L3 Packet/Sec 24 Millions 120 Millions L2/L3 Bandwidth 16 Gbps (64 Bytes) 80 Gbps (64 Bytes) L4/L7 TCP/SEC 1 Million 1.5 Millions L4/L7 TCP OPEN 20 Millions 30 Millions L4/L7 Bandwidth 16 Gbps 40 Gbps 96 What kind of Network Equipment Validation ? BreakingPoint testing tools are used to validate the following network equipments: • • • • • • • • • 97 UTM IDS/IPS QoS Deep Packet Inspection Firewall Web Application Firewall Load Balancer WAN Accelerator Network Probe Lawful Interception • • • • • • • • • SSL Accelerator Traffic Shaper SMTP Relay Anti-SPAM Proxy/Cache URL Filter Content Filter Anti-Virus /Anti-Malware …and more BreakingPoint Application and Threat Intelligence Program 98 BreakingPoint Maintenance The BreakingPoint Application and Threat Intelligence (ATI) Program is an all-inclusive service that provides you with everything you need to maintain the BreakingPoint Storm CTM with new applications, security attacks, features, performance enhancements, service and support. With ATI, you will know that your devices, networks, and data centers are resilient against late-breaking attacks encountered in the wild, as well as emerging application protocols. You will also receive frequent performance enhancements and new features to streamline all of your resiliency measurement initiatives. The BreakingPoint ATI Program features • Access to BreakingPoint's more than 130 application protocols with new applications provided frequently • Current security coverage with 4,500+ security strikes, 80+ evasion techniques and frequent updates • Surveillance and updates from our research team to keep your staff focused on resiliency, not research • Instant access to monthly product updates, new automation features, and management capabilities • Easy access to our problem resolution team, product fixes, and online support •Fast resolution of issues through full service and support Software Updates like Anti-Virus Update “One Click” 101 Frequency New Major Release 2009 102 Frequency New StrikePack 2009 5 4.5 4 3.5 3 2.5 2 1.5 1 0.5 0 Jan-09 103 Feb-09 Mar-09 Apr-09 May-09 Jun-09 Jul-09 Aug-09 Sep-09 Oct-09 Nov-09 Dec-09 Frequency New L7 Protocols 2009 100 90 80 70 60 50 40 30 20 10 0 Jan-09 104 Feb-09 Mar-09 Apr-09 May-09 Jun-09 Jul-09 Aug-09 Sep-09 Oct-09 Nov-09 Dec-09 Frequency New Attacks 2009 4500 4000 3500 3000 2500 2000 1500 1000 500 0 Jan-09 105 Feb-09 Mar-09 Apr-09 May-09 Jun-09 Jul-09 Aug-09 Sep-09 Oct-09 Nov-09 Dec-09 Summary of BreakingPoint Systems Testing Products 106 Summary of Test Possibilities 107 Join the community ! http://www.breakingpointsystems.com/community/ 108 Thank You www.breakingpointsystems.com 109