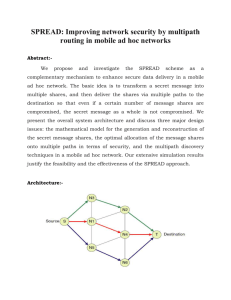
slides - Indocrypt 2011

Secure Message Transmission In
Asynchronous Directed Networks
Kannan Srinathan,
Center for Security, Theory and Algorithmic Research,
IIIT-Hyderabad.
In collaboration with Shashank Agrawal and Abhinav Mehta
Motivation
A B
Faithful messengers but no timing guarantee; may not be able to deliver messages in both directions
Spy S is in a far away land. He wants to send a secret message to R.
Spy R
Not all intermediaries are faithful – who knows what’s on their mind.
Abstraction
Network Model
◦ A directed graph N=(V,E)
◦ Two special nodes S and R in the graph
Timing Model
◦ Completely Asynchronous system
All nodes know
◦ the topology of the network
◦ the protocol specification
Abstraction
Fault Model
◦ An adversary structure
A = {B each B i
1
,B
2
,B
3
,B
4
,…} is a subset of V\{S,R} where
◦ One of the B i
’s can be Byzantine corrupt in an execution
◦ Adversary knows
the topology of the network
the protocol specification
◦ Edges in the network
are secure – messages cannot be read or altered
but messages can be arbitrarily delayed
The problem - PSMT
S wants to send a secret message m chosen from a field to R .
For every corruption B i and every schedule
◦ Reliability: R always terminates with the secret m .
◦ Privacy: Adversary does not know anything about the secret.
Compromising on reliability and/or privacy we can get different flavors of secure message transmission.
Routers or Computational Devices?
Does it matter? YES!
No protocol for SMT if store-and-forward intermediate nodes
SMT protocol exists if routers can compute on their payloads
Secret Sharing – an important tool
We use the simple (k,n) threshold scheme
(n≥k) to create n shares of a secret
Knowledge of any set of at most k-1 shares reveals no information about the secret.
Suppose m shares are available (where k≤m≤n )
◦ The secret can be efficiently reconstructed if at least (m+k)/2 shares are correct.
◦ As long as at least (m-k)/2 shares are correct, an incorrect secret will not be reconstructed.
Reducing Adversary structure’s size
A protocol for an arbitrary sized adversary structure exists iff protocols for all its three sized subsets exist
Going from 3 to size 4
◦ Consider A={B
1
,B
2
,B
3
,B
4
}
◦ Consider 4 subsets of A :
A
1
={B
1
,B
2
,B
3
} , A
2
={B
2
,B
3
,B
4
} , A
3
={B
1
,B
2
,B
4
} , A
4
={B
1
,B
3
,B
4
}
Let P i be the protocol tolerating A i
.
◦ At least 3 A i
’s tolerate the actual corrupt set
◦ S does a (2,4) secret sharing to obtain 4 shares of secret m
◦ The share m i is sent through the protocol P i tolerating A i
◦ R waits till 3 of the 4 protocols terminate with a consistent set of shares, and outputs the reconstructed secret
Assume B
1
is corrupt
S
P
1
P
2
P
3
P
4 m
1 m
2 m
3
R m
4
Paths in a directed graph
Strong path
◦ (the usual path)
Weak path
◦ u
1
, u
2
◦ y
1 blocked nodes head node u
1 y
1 u
2
Minimum connectivity
Adversary structure A={B
1
,B
2
,B
3
}
Theorem
◦ There must exist an honest weak path q
1 every blocked node along the path q
1 avoiding nodes in B
2 and B
3
. such that has a path to R
◦ Similarly, path q
2 and q
3 must exist.
Sub-protocol P
1 using the weak path q
1 k1 k1 k1 k2 m k2 k1+k2
S m+k1
B
1
If B
1 is corrupt, sub-protocols P respectively, terminate securely.
2 and P
3
, which use weak paths q
2 and q
3
R
Impossibility
b1
S b2
R b3
Showing impossibility in this graph suffices.
A passive strategy of b1 coupled with an active strategy of b2 , along with delaying messages from b3 , creates indistinguishability at R .
Efficient protocol for threshold adv.
At most t nodes could be corrupt ( t≤n )
Exponential sized adversary structure containing (n-2) C t subsets
Assume graph is 3t+1 weakly connected and
2t+1 strongly connected
Claim: We can have an efficient protocol for
PSMT between any two nodes.
Assume that a weak path is honest, run a sub-protocol.
Overall, 3t+1 sub-protocols are run out of which 2t+1 terminate securely.
S
Important: Every blocked node now has 2t+1 paths to R k1 k1 k1 k2 m k1+k2 m+k1 k2
R
More results in this work
Minimum connectivity requirements for two variants of (0, ∆)-USMT
◦ Monte Carlo
◦ Las Vegas
Requirements match for Las Vegas (0, ∆)-USMT and (0,0)-USMT (referred so far as PSMT)
Requirements for Monte Carlo (0, ∆)-USMT turn out to be the same as (1, ∆)-USMT – security for free!
Open questions
How connectivity is affected by
◦ Limited topology knowledge
◦ Compromising security a little bit
This variant has recently been studied (ICITS 2011)
Graph Testing: Given a graph, two special nodes in it and the value of t, can we efficiently find out if it has sufficient connectivity for the existence of a protocol