访问控制列表
Access Control List
深圳职业技术学院计算机系网络专业
© 2006, Shenzhen Polytechnic. All rights reserved.
1
教学目标( Objectives )
1. 访问控制列表(Access Control List)
2.配置标准访问控制列表
( Configure standard IP access lists )
3. 配置扩展访问控制列表
( Configure extended IP access lists )
4.配置命名访问控制列表
( Configure named IP access lists )
5. 验证和监视ACL
( Verify and monitor IP access lists )
© 2006, Shenzhen Polytechnic. All rights reserved.
2
为什么使用ACL?
(Why Use Access Control Lists?)
172.16.0.0
Internet
Token
Ring
FDDI
172.17.0.0
•
•
•
•
当网络访问增长时,管理IP通信
Manage IP traffic as network access grows
当数据包通过路由器时,起到过滤作用
Filter packets as they pass through the router
© 2006, Shenzhen Polytechnic. All rights reserved.
3
ACL作用( Function of ACL )
1.限制网络流量、提高网络性能。
Limit network traffic and increase network
performance.
2.提供对通信流量的控制手段。
Provide traffic flow control.
3.提供网络访问的基本安全手段。
Provide a basic level of security for network access.
4.在路由器接口处,决定哪种类型的通信流量被转发、哪种
类型的通信流量被阻塞。
Decide which types of traffic are forwarded or blocked
at the router interfaces.
© 2006, Shenzhen Polytechnic. All rights reserved.
4
ACL如何工作(ACL How to work)
© 2006, Shenzhen Polytechnic. All rights reserved.
5
ACL条件顺序
(The order in which ACL statements are placed )
© 2006, Shenzhen Polytechnic. All rights reserved.
6
ACL条件顺序
(The order in which ACL statements are placed )
Cisco IOS按照各描述语句在ACL中的顺序,根据各描
述语句的判断条件,对数据包进行检查。一旦找到了某
一匹配条件,就结束比较过程,不再检查以后的其他条
件判断语句。
The Cisco IOS software tests the packet against
each condition statement in order from the top of
the list to the bottom. Once a match is found in the
list, the accept or reject action is performed and no
other ACL statements are checked
© 2006, Shenzhen Polytechnic. All rights reserved.
7
什么是ACL?(What Are Access Lists?)
fa0/0
Incoming
Packet
Access List Processes
Outgoing
Packet
Source
Permit?
S0/0
• 标准 ACL ( Standard ACL )
– 检查源地址(Checks Source address )
– 允许或拒绝整个协议族(Generally permits or denies
entire protocol suite)
© 2006, Shenzhen Polytechnic. All rights reserved.
8
什么是ACL?(What Are Access Lists?)
Fa0/0
Incoming
Packet
Access List Processes
Source
and
Destination
Outgoing
Packet
Protocol
Permit?
s0/0
• 扩展 ACL ( Extended ACL )
– 检查源和目的地址
( Checks Source and Destination address)
– 通常允许或拒绝特定的协议 (Generally permits or
denies specific protocols)
© 2006, Shenzhen Polytechnic. All rights reserved.
9
用扩展ACL检查数据包
(Check Packets with Extended ACL)
© 2006, Shenzhen Polytechnic. All rights reserved.
10
常见端口号
(Known Port Number)
端口号(Port Number)
20
文件传输协议(FTP)数据
21
文件传输协议(FTP)程序
23
远程登录(Telnet)
25
简单邮件传输协议(SMTP)
69
普通文件传送协议(TFTP)
80
超文本传输协议(HTTP)
53
域名服务系统(DNS)
© 2006, Shenzhen Polytechnic. All rights reserved.
11
ACL表号(ACL Number )
协议(Protocol)
IP(Internet协议)
ACL表号的取
值范围(ACL
Range)
1-99
Extended IP(扩展Internet协议)
100-199
AppleTalk
600-699
IPX(互联网数据包交换)
800-899
Extended IPX(扩展互联网数据包交换) 900-999
IPX service Advertising
Protocol(IPX服务通告协议)
© 2006, Shenzhen Polytechnic. All rights reserved.
1000-1099
12
通配符掩码(Wildcard Mask )
1.是一个32比特位的数字字符串(A wildcard mask is a 32-bit
2.0表示“检查相应的位”,1表示“不检查(忽略)相应的位”
quantity)
A zero means let the value through to be checked, the X’s (1’s) mean block the
value from being compared.
© 2006, Shenzhen Polytechnic. All rights reserved.
13
特殊的通配符掩码(Special Wildcard Mask )
1. Any
0.0.0.0 255.255.255.255
2. Host
172.30.16.29 0.0.0.0
Host 172.30.16.29
© 2006, Shenzhen Polytechnic. All rights reserved.
14
Access List 命令( Access List Command )
Step 1:定义访问控制列表(Define the ACL)
Router(config)#
access-list access-list-number { permit | deny } { test conditions }
Router(config)#access-list 1 permit 10.0.0.0 0.255.255.255
© 2006, Shenzhen Polytechnic. All rights reserved.
15
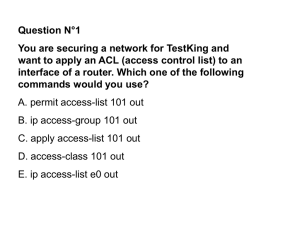
Access List 命令( Access List Command )
Step 2:将访问控制列表应用到某一接口上
(Apply ACL to a Interface)
Router(config-if)#
{ protocol } access-group access-list-number {in | out}
Router(config-if)#ip access-group 1 out
© 2006, Shenzhen Polytechnic. All rights reserved.
16
标准IP ACL实例1(Standard IP ACL Example 1)
172.16.3.0
Non172.16.0.0
S0
E0
E1
172.16.4.0
172.16.4.13
access-list 1 permit 172.16.0.0 0.0.255.255
(implicit deny all - not visible in the list)
(access-list 1 deny 0.0.0.0
255.255.255.255)
interface ethernet 0
ip access-group 1 out
interface ethernet 1
ip access-group 1 out
• 仅允许我的网络(Permit my network only)
© 2006, Shenzhen Polytechnic. All rights reserved.
17
标准IP ACL实例2(Standard IP ACL Example 2)
172.16.3.0
Non172.16.0.0
172.16.4.0
S0
E0
E1
172.16.4.13
access-list 1 deny 172.16.4.13 0.0.0.0
access-list 1 permit 0.0.0.0 255.255.255.255
(implicit deny all)
(access-list 1 deny 0.0.0.0
255.255.255.255)
interface ethernet 0
ip access-group 1 out
• 拒绝特定的主机(Deny a specific host)
© 2006, Shenzhen Polytechnic. All rights reserved.
18
标准IP ACL实例3(Standard IP ACL Example 3)
172.16.3.0
Non172.16.0.0
S0
E0
E1
172.16.4.0
172.16.4.13
access-list 1 deny 172.16.4.0 0.0.0.255
access-list 1 permit any
(implicit deny all)
(access-list 1 deny 0.0.0.0
255.255.255.255)
interface ethernet 0
ip access-group 1 out
• 拒绝特定的子网(Deny a specific subnet)
© 2006, Shenzhen Polytechnic. All rights reserved.
19
标准ACL与扩展ACL比较
(Standard versus External ACL)
标准(Standard)
扩展(Extended)
过滤基于源
过滤基于源和目的( Filters Based
on Source and destination.)
(Filters Based onSource.)
允许或拒绝整个协议族(Permit or
deny entire TCP/IP protocol suite.)
允许或拒绝特定的IP协议或端口
(Specifies a specific IP protocol
and port number.)
范围(1-99)
范围(100-199)
Range is 1 through 99
Range is 100 through 199.
© 2006, Shenzhen Polytechnic. All rights reserved.
20
CASE STUDY
首先使得PC1所在的网络不能通过路由器R1访问PC2所
在的网络。
© 2006, Shenzhen Polytechnic. All rights reserved.
21
扩展ACL配置(Extended IP ACL Configuration)
Router(config)# access-list access-list-number
{ permit | deny } protocol source source-wildcard
[operator port] destination destination-wildcard [
operator port ] [ established ] [log]
参数
参数描述
access-list-number
访问控制列表表号
permit|deny
如果满足条件,允许或拒绝后面指定特定地址的通信流量
protocol
用来指定协议类型,如IP、TCP、UDP、ICMP等
source and destination
分别用来标识源地址和目的地址
source-mask
通配符掩码,跟源地址相对应
destination-mask
通配符掩码,跟目的地址相对应
operator
lt,gt,eq,neq(小于,大于,等于,不等于)
operand
一个端口号
established
如果数据包使用一个已建立连接,便可允许TCP信息通过
© 2006, Shenzhen Polytechnic. All rights reserved.
22
扩展ACL实例1 (Extended ACL Example 1)
172.16.3.0
Non172.16.0.0
S0
E0
E1
172.16.4.0
172.16.4.13
access-list 101 deny tcp 172.16.4.0 0.0.0.255 172.16.3.0 0.0.0.255 eq 21
access-list 101 deny tcp 172.16.4.0 0.0.0.255 172.16.3.0 0.0.0.255 eq 20
access-list 101 permit ip any any
(implicit deny all)
(access-list 101 deny ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255)
interface ethernet 0
ip access-group 101 out
•
•
•
•
拒绝从172.16.3.0到172.16.3.0的经过E0出方向的FTP流量
Deny FTP from subnet 172.16.4.0 to subnet 172.16.3.0 out of E0
允许其他所有的流量
Permit all other traffic
© 2006, Shenzhen Polytechnic. All rights reserved.
23
Extended Access List Example 2
172.16.3.0
Non172.16.0.0
172.16.4.0
S0
E0
E1
access-list 101 deny tcp 172.16.4.0
access-list 101 permit ip any any
(implicit deny all)
172.16.4.13
0.0.0.255
any eq 23
interface ethernet 0
ip access-group 101 out
• 仅拒绝子网172.16.4.0 在E0出方向的流量
• Deny only Telnet from subnet 172.1 172.16.4.0 6.4.0
out of E0
• 允许其他流量(Permit all other traffic)
© 2006, Shenzhen Polytechnic. All rights reserved.
24
使用命名IP ACL(Using Named IP ACL)
• IOS11.2 以后支持的特征
• Feature for Cisco IOS Release 11.2 or later
Router(config)#
ip access-list { standard | extended } name
• 名字字符串要唯一
• Name string must be unique
© 2006, Shenzhen Polytechnic. All rights reserved.
25
使用命名IP ACL(Using Named IP ACL)
Router(config {std- | ext-}nacl)#
{ permit | deny } { ip access list test conditions }
{ permit | deny } { ip access list test conditions }
no { permit | deny } { ip access list test conditions }
• 允许或拒绝陈述条件前没有表号
• Permit or deny statements have no prepended number
• 可以用“NO”命令移去特定的陈述
• "no" removes the specific test from the named access list
© 2006, Shenzhen Polytechnic. All rights reserved.
26
使用命名IP ACL(Using Named IP ACL)
Router(config-if)# ip access-group name { in
• 在接口上激活命名ACL
• Activates the IP named access list on an interface
© 2006, Shenzhen Polytechnic. All rights reserved.
27
放置ACL( Placing IP Access Lists)
S0
E0
B
E0
S0
S1
S1
A
To0
Token
Ring
D
C
E0
E0
E1
• 扩展ACL靠近源
• Place extended access lists close to the source
• 标准ACL靠近目的
• Place standard access lists close to the destination
© 2006, Shenzhen Polytechnic. All rights reserved.
28
验证ACL (Verifying ACL)
wg_ro_a#show ip int e0
Ethernet0 is up, line protocol is up
Internet address is 10.1.1.11/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 1
Proxy ARP is enabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP fast switching on the same interface is disabled
IP Feature Fast switching turbo vector
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
<text ommitted>
© 2006, Shenzhen Polytechnic. All rights reserved.
29
监视ACL陈述条件
(Monitoring Access List Statements)
wg_ro_a#show {protocol} access-list {access-list number}
wg_ro_a#show access-lists {access-list number}
wg_ro_a#show access-lists
Standard IP access list 1
permit 10.2.2.1
permit 10.3.3.1
permit 10.4.4.1
permit 10.5.5.1
Extended IP access list 101
permit tcp host 10.22.22.1 any eq telnet
permit tcp host 10.33.33.1 any eq ftp
permit tcp host 10.44.44.1 any eq ftp-data
© 2006, Shenzhen Polytechnic. All rights reserved.
30
思考题(Questions)
1.访问控制列表的功能是什么?
2.ACL有哪两种类型?各有什么区别?
3.当我们应用访问控制列表时,如何区分in和out方向?
4.ACL的隐含是什么?
5.Any的含义是什么?
6.host的含义是什么?
7.标准ACL应该靠近源还是目的地址?
8.扩展ACL应该靠近源还是目的地址?
9.标准ACL的编号范围是多少?
10.扩展ACL的编号范围是多少?
© 2006, Shenzhen Polytechnic. All rights reserved.
31