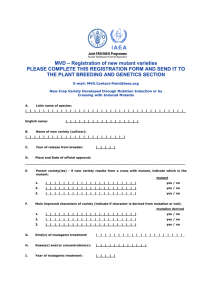
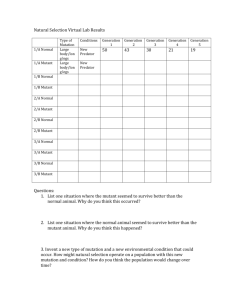
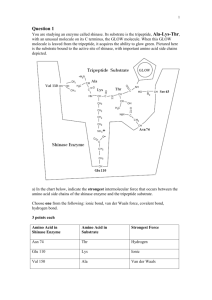
Dengfeng-MUTEC

Hossain Shahriar Mohammad
Zulkernine
One of the worst vulnerabilities in web applications
It involves the generation of dynamic HTML contents with invalidated inputs, which might contain HTML tags, Javescript code and so on.
When invalidated contents are interpreted by browser, unintended and malicious web page behaviors are generated
persistent (or stored) XSS vulnerability
injected code is permanently stored on the target servers, such as in a database, in a message forum, visitor log, comment field, etc.
The victim retrieves the malicious script from the server when it requests the stored information.
The injected code is reflected off the web server, such as in an error message, search result, or any other response that includes some or all of the input sent to the server as part of the request
DOM allow program or script can visit and change web document’s content, structure, and style dynamically
Using DOM, Script program on client side can check and alter web page dynamically without interacting with server side
If the data has not been checked, there might be XSSVs
URL:http://www.mysite.com/welcome.html?name=somename
From welcome web page:
<TITLE>Welcome!</TITLE>
Hi
<SCRIPT> var pos=document.URL.indexOf("name=")+5; document.write(document.URL.substring(pos,document.U
RL.length));
</SCRIPT>
But how about we enter: http://www.mysite.com/welcome.html?name=<script>alert(d ocument.cookie)</script> as URL?
An effective testing of XSSVs helps fixing implementations early and decreasing losses.
After modifying the program’s source code, output behavior of test case should be affected. This is a method of evaluating the quality of test cases.
The paper is focusing on obtaining an adequate test data set, which implies a collection of test cases that can exploit XSSVs.
The process is fault-based
Mutant: Objects being tested are injected with modifications to generate mutants
Mutation Operator: Rule of injecting faults
Kill and Live Mutants: If a test case causes different output between the original program and a mutant, then we say it kills a mutant. Otherwise, the mutant is said to be live.
Denote the original implementation as P, and the mutant as M.
Killing Criterion 1(C1): The number of HTML tags generated in P(N
P
) is not equal to that in the mutant(N
M
). (N
P
!=N
M
)
Killing Criterion 2(C2): The HTML contents displayed in P(H
P
) is different than that in
M(H
M
). (H
P
!=H
M
)
Mutation Score(MS): Ratio of the number of killed mutants to the total number of nonequivalent mutants.
Basic Idea: If our operators are effective:
When test cases are powerful at killing mutants gererated by operators, they should be powerful at distinguishing good apps and malicious apps
Add escape function calls (ADES)
Modify arguments of write function calls, adding escape function, which encodes special punctuation characters into hexadecimal chars, so the injected HTML tags will not be executed.
Remove escape function calls(RESC)
Replace write function with eval (RWWE)
Replace write function call with eval, which can execute JavsScript expressions and statements in string arguments.
Replace innerHTML property with text node addition in DOM(RIHA) innerHTML property of DOM can be used to modify text of HTML tags, which is vulnerable to XSS.
Modify arguments of replace function calls(MARF)
MARF operator injects faults into the search string pattern by modifying
(a)local search with global search (b) case sensitive search to case insensitive
Add htmlspecialchars function calls(AHSC) htmlspecialchars function can replace each character in the accepted string with its HTML equivalent. Mutant can be killed by C1.
Remove htmlspecialchars function calls(RHSC)
Add htmlentities function calls(AHEN)
Similar to AHSC. The function converts all input characters to their corresponding HTML entities
Remove htmlentities function calls(RHEN)
Modify allowable tag parameter in striptags function calls(MALT) striptags function can remove all HTML tags, except for allowable tags. By modifying allowable tag argument, more tags are allowed.
Remove strip_tags function calls(RSTT)
Choose five open source web apps from Open
Source Vulnerability Database(OSVDB), both vulnerable version(bad app) and upgraded or manually fixed version(good app).
Mutants of good apps are generated by the tool.
Collect 303 test cases to form an attack test pool
Each app has an initial test data set composed of 10 test cases, which do not contain attack test cases
Use attack test cases from attack test pool to augment initial test cases, let each app has
50 test cases
For each app, do the procedure: randomly choose 10 out of 50 test cases to construct an initial test data set. Repeatedly add to the set if needed until MS reach 100%.
Repeat the procedure 15 times and calculate the average test set size.
Check whether test data set can distinguish between good and bad apps by checking whether at least one test case in the set can distinguish following either of the killing criterion
Result showed that all the adequate test data sets(with MS 100%) for a bad program can distinguish the corresponding good program.
Operators are proved to be effective.
Extending MUTEC tool to support automatic mutation analysis process
Performing adequate testing of XSSVs on large scale web-based applications
Propose mutation operators for filters implemented using PHP library functions such as preg_replace and preg_search.
Qustions?
Presenter: Dengfeng Xia